Microsoft Azure: Single NIC F5 BIG-IP Virtual Edition¶
Complete these tasks to deploy F5 BIG-IP Virtual Edition (VE) in a single NIC configuration from the Azure Marketplace.
You can find the latest version of F5 BIG-IP VE in the Azure Marketplace, and find older versions of BIG-IP VE in the F5 BIG-IP Azure Resource Manager (ARM) templates, or find other F5 deployment templates on https://github.com/F5Networks.
Sample single-NIC configuration¶
The following diagram shows a basic single NIC deployment of a BIG-IP VE instance in Microsoft Azure.
When you deploy BIG-IP VE from the Azure Marketplace, only a single NIC is available. All other configurations must use an ARM template.
Follow the steps in this guide to create this deployment.
Note: Alternately, you can use a template to create this deployment. For more information about templates provided by F5, go to https://github.com/F5Networks.
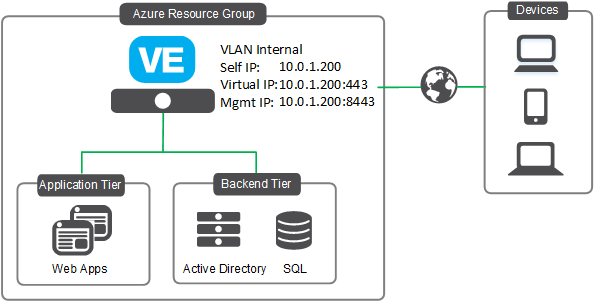
When you first boot into a single NIC instance, the BIG-IP VE default behavior creates networking objects such as, interface 1.0, a VLAN, a self-IP, and a default gateway. In BIG-IP VE version 13.0 and later, the port for the BIG-IP Configuration Utility is set to 8443.
In the previous diagram, all access to the BIG-IP VE appliance uses the same IP address (both management traffic through port 8443 and virtual service traffic on that same IP). However, you can create virtual services either on the same IP as the self-IP (as depicted in the previous diagram) or on different addresses by provisioning Azure secondary IPs on the NIC. If you want to do High Availability (create an active-standby pair), you must provision virtual services on these Azure secondary IPs. See F5 Cloud Failover for more information.
Watch a video of the deploy process:
Step summary¶
This is a specific example, which you can use to test a single NIC deployment. When done, you should be able to send traffic to your application servers through BIG-IP VE.
| Step | Task | Details |
|---|---|---|
| 1 | Prepare to deploy | Choose an F5 BIG-IP license. You can get a trial license if you need one. In Azure, create an application server in a resource group. BIG-IP VE will be in the same resource group. Create a key pair (recommended for production environments). |
| 2 | Deploy a BIG-IP VE instance in Resource Manager | Find an F5 BIG-IP VE image in the Azure Marketplace and create an instance in the same resource group as your application. For BIG-IP VE, choose an Azure instance type that has at least 2 vCPU, 4 G memory. Choose an image with 2 boot locations if you expect to upgrade BIG-IP VE in the future. If you do not need room to upgrade (if you intend to create a new instance when a new version of BIG-IP VE is released), choose an image with 1 boot location. |
| 3 | In Azure, create rules that allow inbound traffic to BIG-IP VE | When you deploy BIG-IP VE, Azure creates a network security group. Add an inbound security rule to allow traffic to port 8443 for the BIG-IP Configuration utility and port 443 for your application. |
| 4 | Set an admin password for BIG-IP VE | If you used a key when you deployed the instance, use SSH to connect to BIG-IP VE and set a password for the admin account. You will use the admin account to access the BIG-IP Configuration utility.
|
| 5 | License BIG-IP VE | Use the admin account to log in to the BIG-IP Configuration utility ( Note: In BIG-IP VE 13.0, the port is |
| 6 | Provision BIG-IP VE | Enable the modules you need. |
| 7 | Change the Config utility port | Prior to BIG-IP VE 13.0 only. Change the Config utility from port 443 to 8443. In BIG-IP VE 13.0 and later, it is port 8443 by default. |
| 8 | Create a pool and add members to it | Create a pool that contains your application servers. Pool name: web_pool |
| 9 | Create a virtual server | Create a virtual server, which provides a destination for your inbound web traffic and points to the pool of web servers.
Note: Because IP addresses in Azure may change, use the DNS name of your application server as the pool member. |
Step details¶
Deploy BIG-IP VE in Azure Resource Manager¶
In order to create a virtual machine running BIG-IP VE in Azure, you can deploy BIG-IP VE in the Azure Resource Manager deployment model.
Log in to the Microsoft Azure Portal at https://portal.azure.com.
On the Dashboard, select Marketplace.
In the Filter field, type
F5and press Enter.Choose an image with 2 boot locations if you expect to upgrade BIG-IP VE in the future. If you do not need room to upgrade (if you intend to create a new instance when a new version of BIG-IP VE is released), choose an image with 1 boot location.
From the Select a deployment model list, select Resource Manager and click Create.
On the Basics blade, complete these settings.
Setting Details Name A name for the instance. VM disk type Accept the default or change it. User name A name for the person who will log in to BIG-IP VE. You can’t change or access this field later. Authentication type SSH keys are more secure than passwords. Subscription Accept the default or change it. Resource group A resource group is a logical container of related resources. Accept the default or change it. Location Accept the default or change it. Click OK.
On the Size blade, choose an Azure instance type that has at least 2 vCPU, 4 G memory, and click Select. For each additional vCPU, add 2 G memory.
On the Settings blade, accept the defaults or change them. For Select public inbound ports, select
No public inbound ports. You will open ports later.Click OK.
On the Summary blade, complete the fields and click Create. To check the deployment status, click the notifications bell on the top toolbar.
When done, you will have the following resources:
- A BIG-IP VE instance with one network interface and a public IP address
- A VLAN named
internal - A self IP address named
self_1nic
Note: You do not need to use the BIG-IP Setup wizard to configure networking, because BIG-IP configured basic networking during deployment.
Azure Classic is an older version of the Azure portal that Microsoft is deprecating. If you need instructions for deploying BIG-IP VE in Classic, see this document.
Create inbound traffic rules¶
In order to access the BIG-IP Configuration utility, you must open port 8443. To connect to BIG-IP VE via SSH, open port 22. And to connect to your application through BIG-IP VE, open port 443 (in this example).
In the Azure portal, click .
Filter the list to find your group and click it.
In the left manu, under Settings, click Inbound security rules.
Click Add.
Name Value Source port ranges An IP range on your network. Destination port ranges 22Protocol TCPName A description, like SSH access.Click Add.
Repeat steps 4 & 5, using
8443as the Destination port range. This allows management traffic for port8443to reach BIG-IP VE.Repeat steps 4 & 5, using
443as the Destination port range. This allows traffic for your application (in this example).
Set the admin password for BIG-IP VE¶
Give BIG-IP VE six to ten minutes to finish deploying before you attempt to connect.
The first time you boot BIG-IP VE, you must connect to the instance and create a strong admin password. You will use the admin account and password to access the BIG-IP Configuration utility.
This management interface may be accessible to the Internet, so ensure the password is secure.
Connect to BIG-IP VE.
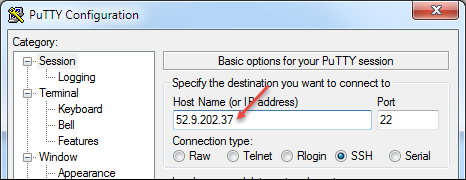
At the command prompt, navigate to the folder where you saved your ssh key and type:
ssh -i <private_key_file.pem> admin@<bigip_public_ip_address>If you prefer, you can open PuTTy and in the Host Name (or IP address) field, enter the external IP address, for example:
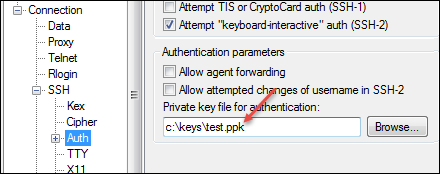
In the Category pane on the left, click .
In the Private key file for authentication field, choose your .ppk file.
Click Open.
If a host key warning appears, click OK.
The terminal screen displays:
login as:.Type
adminand press Enter.
To change to the
tmshprompt, type:tmshModify the admin password:
modify auth password adminThe terminal screen displays the message:
changing password for admin new password:
Type the new password and press Enter.
The terminal screen displays the message:
confirm passwordRe-type the new password and press Enter.
Ensure that the system retains the password change and press Enter.
save sys configThe terminal screen displays the message:
Saving Ethernet mapping...done
License BIG-IP VE¶
You must enter license information before you can use BIG-IP VE.
Open a web browser and log in to the BIG-IP Configuration utility by using
httpswith the external IP address and port 8443, for example:https://<external-ip-address>:8443. The username isadminand the password is the one you set previously.On the Setup Utility Welcome page, click Next.
On the General Properties page, click Activate.
In the Base Registration key field, enter the case-sensitive registration key from F5.
For Activation Method, if you have a production or Eval license, choose Automatic and click Next.
If you chose Manual, complete these steps:
In the Step 1: Dossier field, copy all of the text and then click Click here to access F5 Licensing Server.
A separate web page opens.
On the new page, click Activate License.
In the Enter your dossier field, paste the text and click Next.
Accept the agreement and click Next.
On the Activate F5 Product page, copy the license text in the box. Now go back to the BIG-IP Configuration utility and paste the text into the Step 3: License field.
Click Next.
The BIG-IP VE system registers the license and logs you out. When the configuration change is successful, click Continue to provision BIG-IP VE.
Provision BIG-IP VE¶
You must confirm the modules you want to run before you can begin to work in the BIG-IP Configuration utility.
Open a web browser and log in to the BIG-IP Configuration utility.
On the Resource Provisioning screen, change settings if necessary and click Next.
On the Device Certificates screen, click Next.
On the Platform screen, in the Admin Account field, re-enter the password for the admin account and click Next.
BIG-IP VE logs you out.
When you log back in, on the screen, in the Advanced Network Configuration area, click Finished.
Change the Configuration utility port¶
The BIG-IP Configuration utility uses port 443 by default. Change the port to 8443 so you can use 443 for application traffic.
Use a secure shell terminal (SSH), like PuTTy, to access the instance; use the key pair you specified when you deployed the instance.
Type
tmshto ensure you are accessing the tmsh prompt.Confirm the SSL port.
list sys httpd ssl-portThe result should be ssl-port
443.Move the port from
443to8443.modify sys httpd ssl-port 8443Confirm the move was successful.
list sys httpd ssl-portThe result should be ssl-port
8443.Add
8443to the default self allow port list.modify net self-allow defaults add { tcp:8443 }Now that the Configuration utility is no longer using port 443, remove the reference to it.
modify net self-allow defaults delete { tcp:443 }Confirm the changes.
list net self-allow defaultstcp:pcsync-httpsis for8443and should be in the list.tcp:httpsis for443and should not be in the list.Save the changes to the system configuration.
save sys configEnd the SSH session.
Open a web browser and go to the BIG-IP Configuration utility by using port
8443, for example:https://<public-ip-address>:8443.
Create a pool and add members to it¶
Traffic goes through BIG-IP VE to a pool. You must add your application servers to this pool.
Open a web browser and go to the BIG-IP Configuration utility, for example:
https://<external-ip-address>:8443.On the Main tab, click .
Click Create.
In the Name field, type
web_pool. Names must begin with a letter, be fewer than 63 characters, and can contain only letters, numbers, and the underscore (_) character.For Health Monitors, move
httpsfrom the Available to the Active list.Choose the load balancing method or retain the default setting.
In the New Members section, in the Address field, type the IP address of the application server.
In the Service Port field, type a service port, for example,
443.Click Add.
The list now contains the member.
Add additional pool members as needed and click Finished.
Create a virtual server¶
A virtual server listens for packets destined for the external IP address. You must create a virtual server that points to the pool you created.
In the BIG-IP Configuration utility, click the Main tab, and then click .
Click Create and complete the following information.
Field Value Name A unique name Destination Address/Mask BIG-IP VE’s private IP address Service Port 443HTTP Profile http SSL Profile (Client) clientssl SSL Profile (Server) serverssl Source Address Translation Auto Map Default Pool web_poolNote
These values are for demonstration only. For details about securing a web application with SSL, see the product documentation at askf5.com.
Click Finished.
Traffic to the BIG-IP VE external IP address will now go to the pool members. To test in a browser, type: https://<external-IP-address>.