F5 BIG-IP Next WAF Labs > Module 1: BIG-IP Next Central Manager signature and Threat Campaigns update Source |
Lab 1.1 - Stay up-to-date with F5’s latest Attack Signature updates and Threat Campaigns by automatically applying those updates¶
Check on latest attack signature and threat campaigns update files¶
- Log into the BIG-IP Next Central Manager via the Windows Jump Host.
- The appropriate RDP credentials can be found under “Components” -> “DETAILS” as explained in “Module 0”.
- Just click on the BIG-IP Next CM Favorite in the Chrome Browser of the the Windows Jump Host.
Note: Module 0 Lab 1 covers how you access the different instances as well as how you find the appropriate credentials.
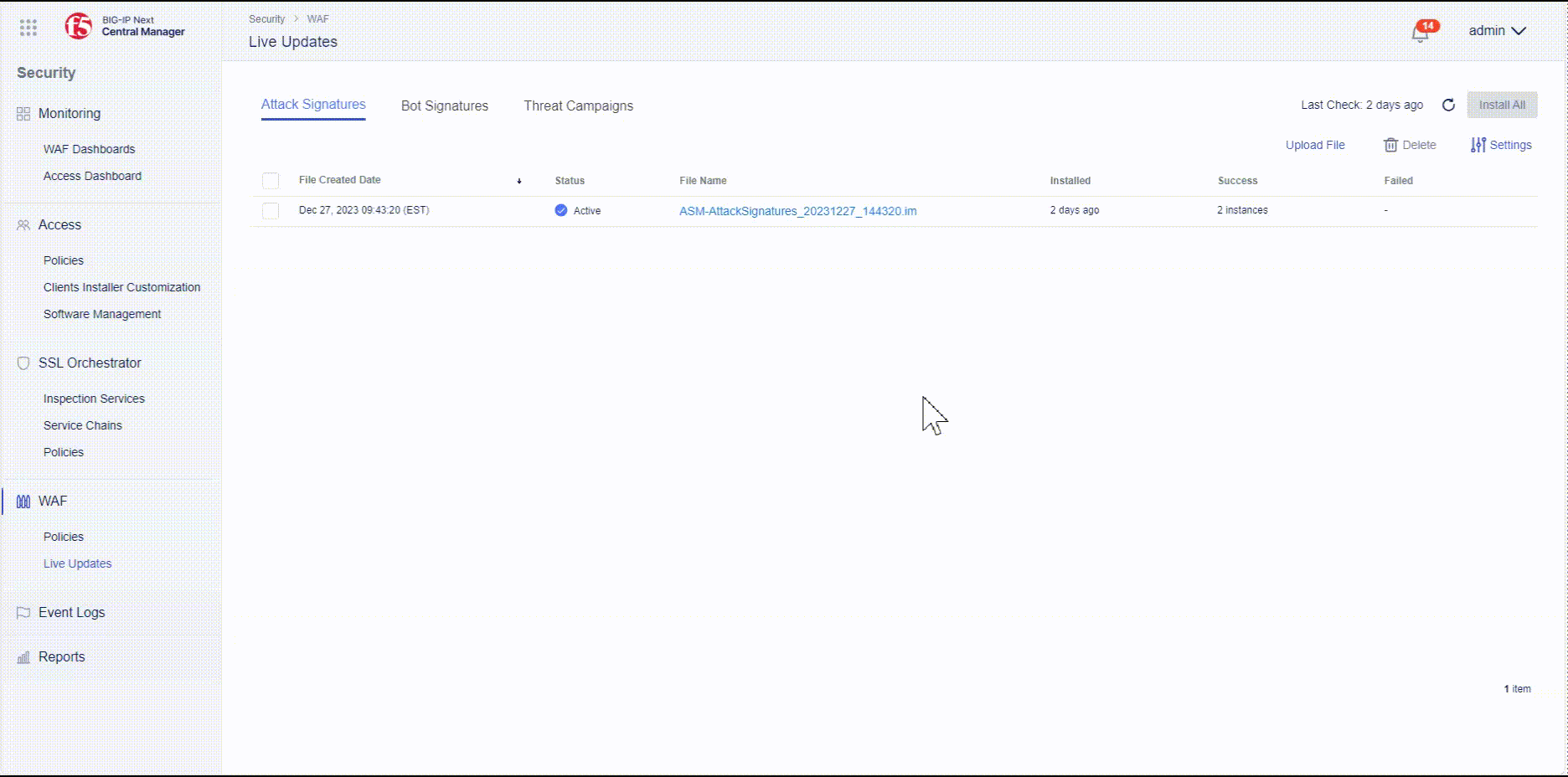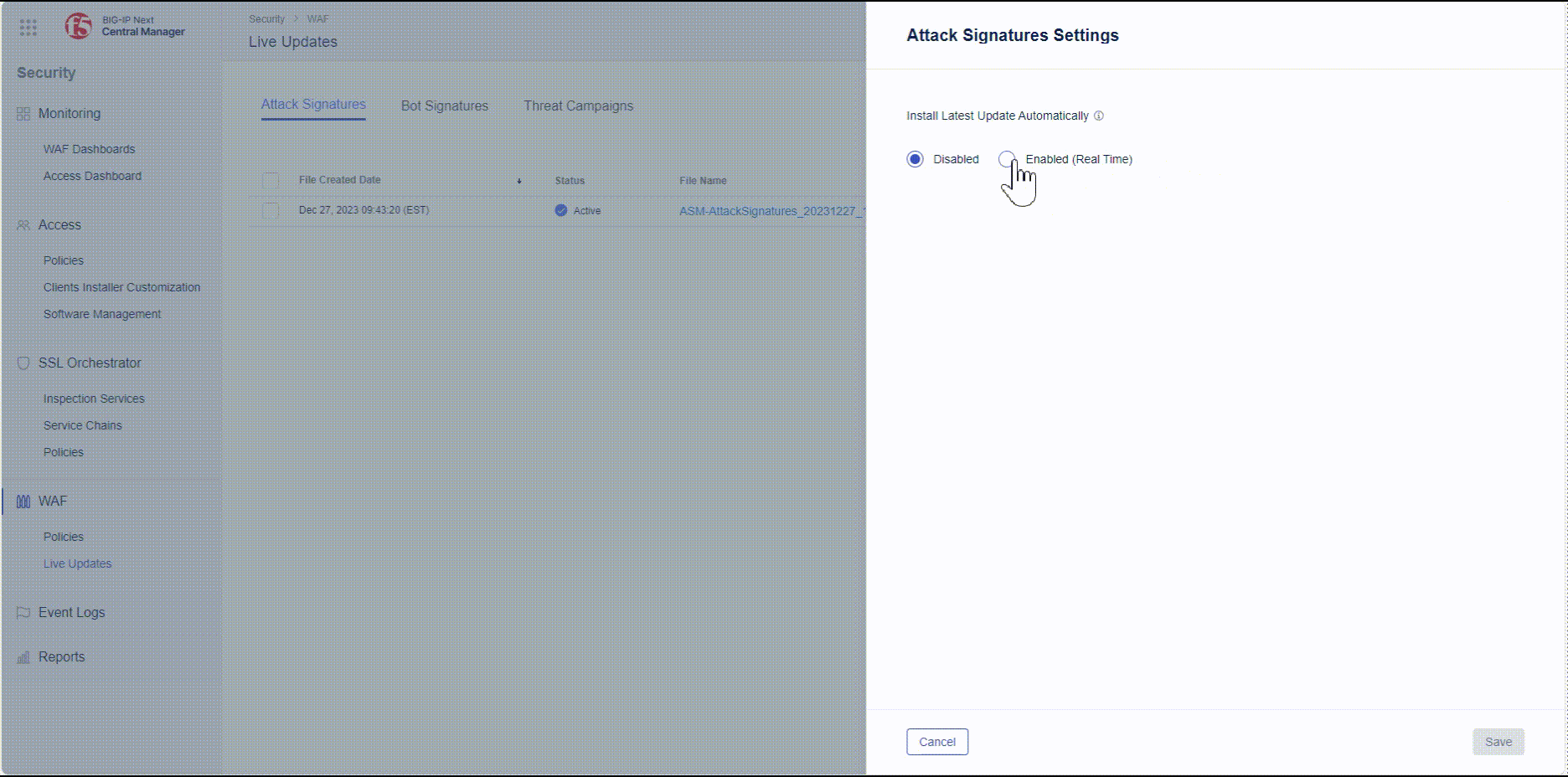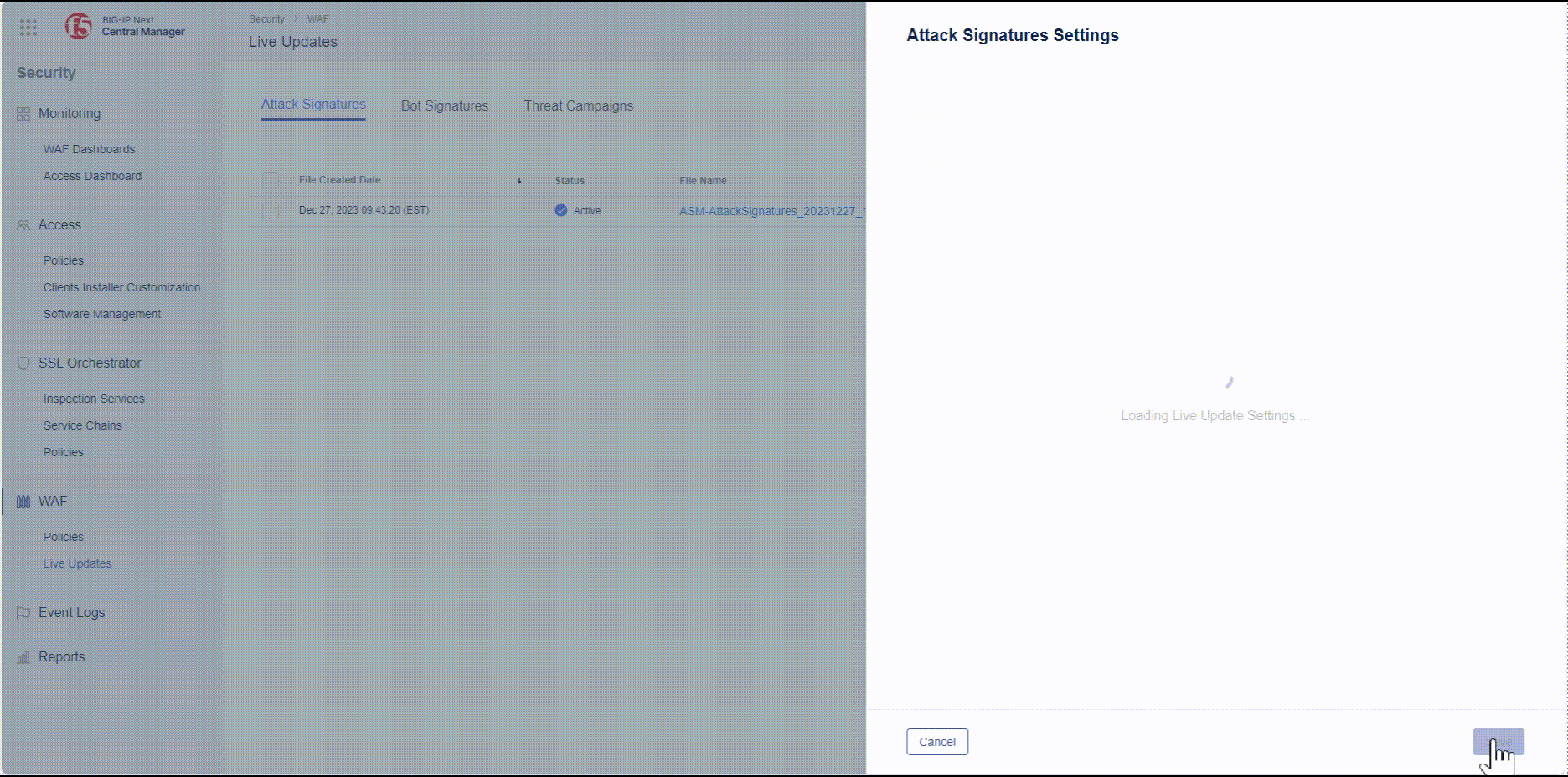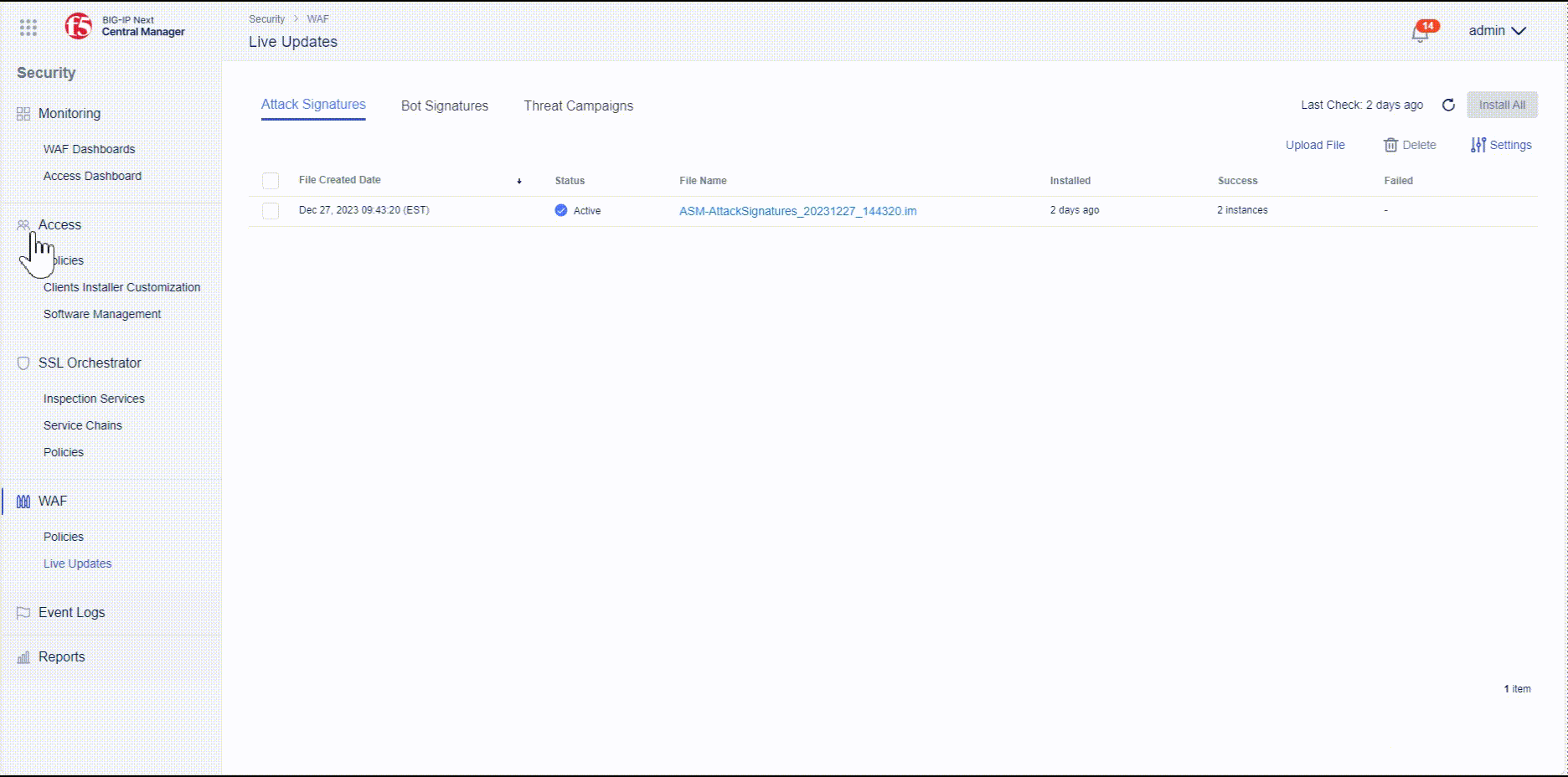
- Go to “Main Menu” and navigate to “Security -> WAF -> Live Updates”.
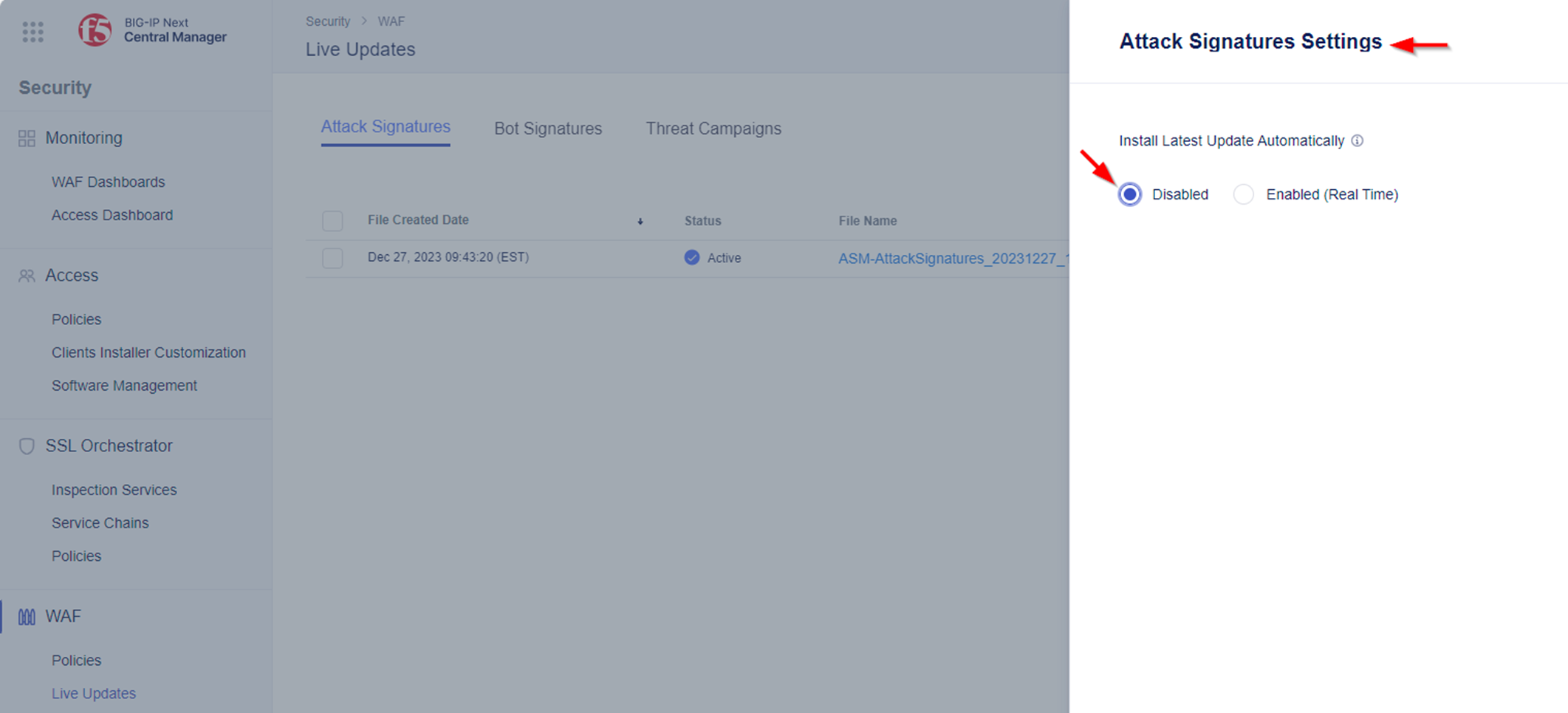
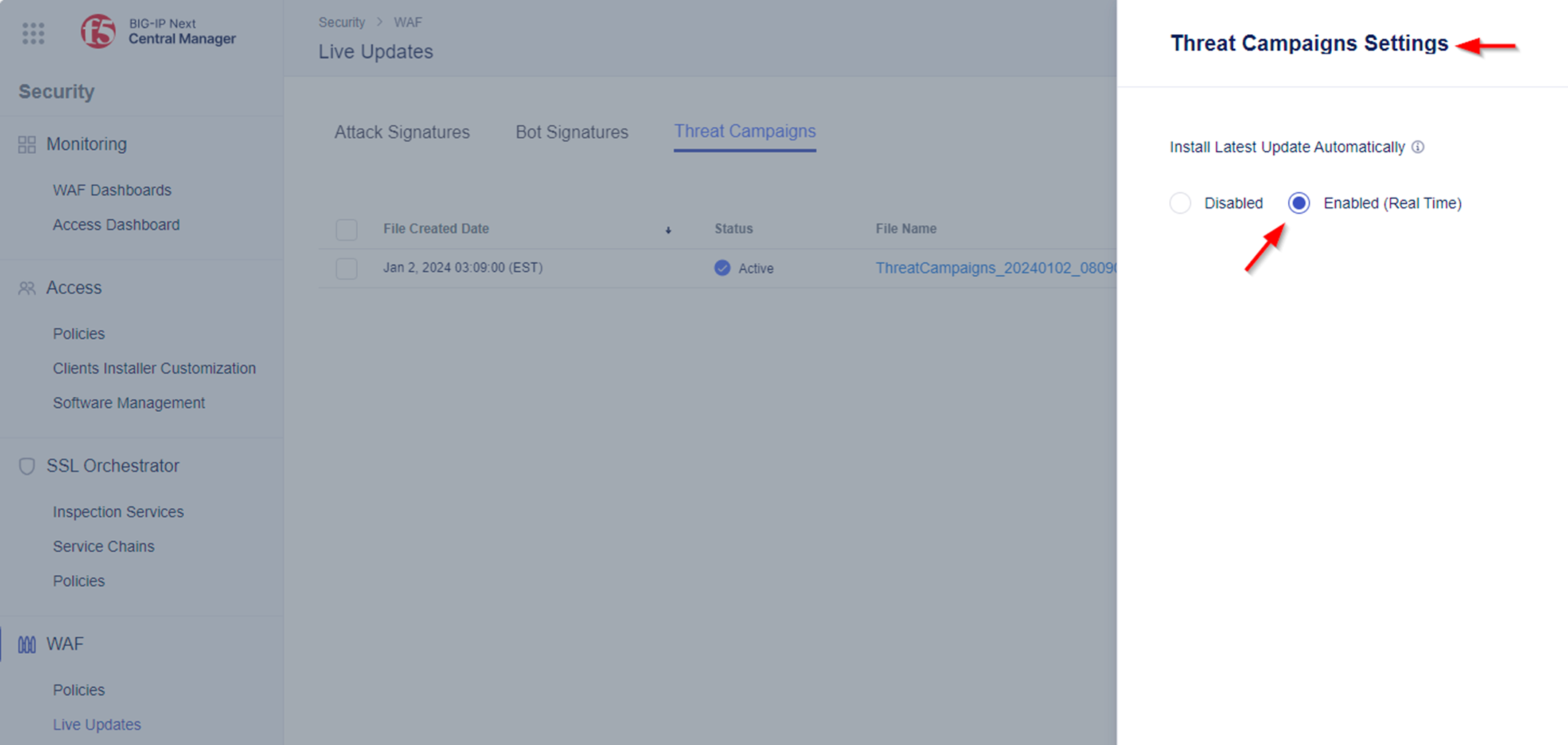
- From here, select Settings and change check “Enabled (Real Time)” to perform auto updates of the latest attack signatures and Threat Campaigns.
NOTE The ‘Disabled’ or ‘Enabled (Real-time)’ options under ‘Settings’ are per tab/object. This allows you to handle the installation of attack signatures updates differently from Threat Campaigns update.
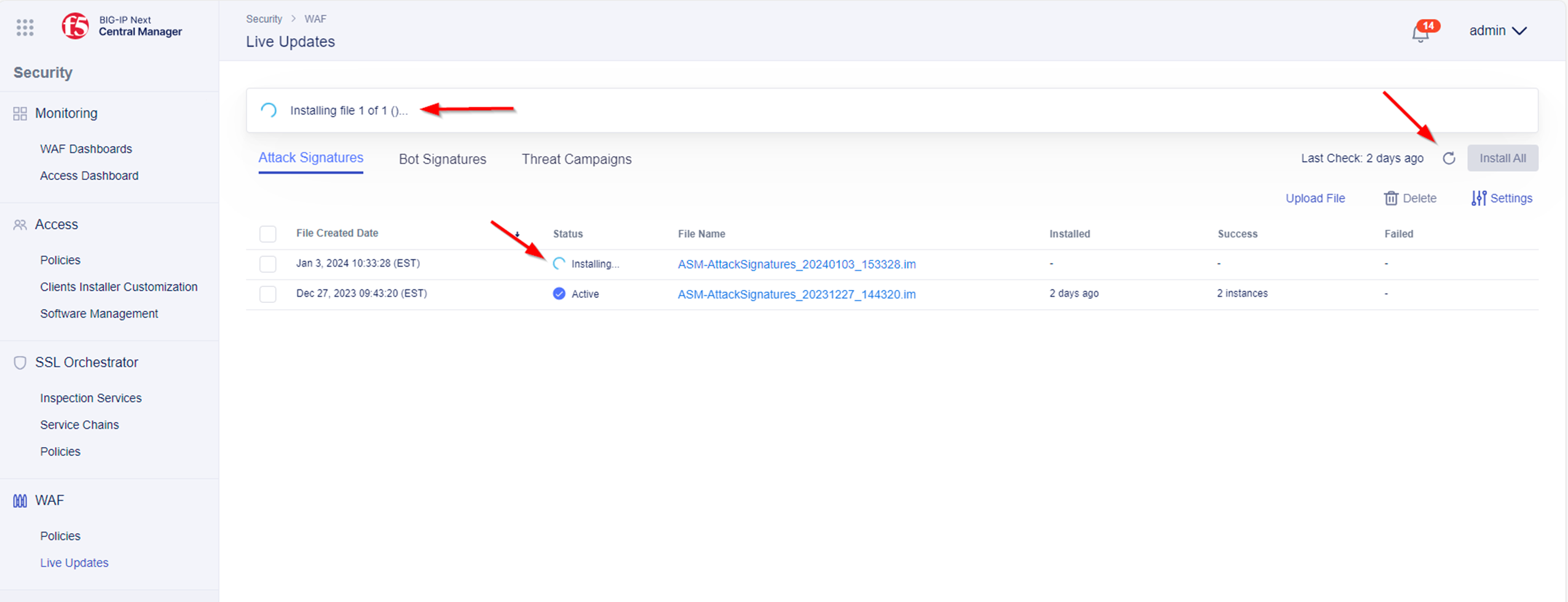
- Now perfrom a check to see if there are latest Attack Signature and Threat Campaigns updates available by selecting the refresh icon. If updates are available, they will be installed automatically.
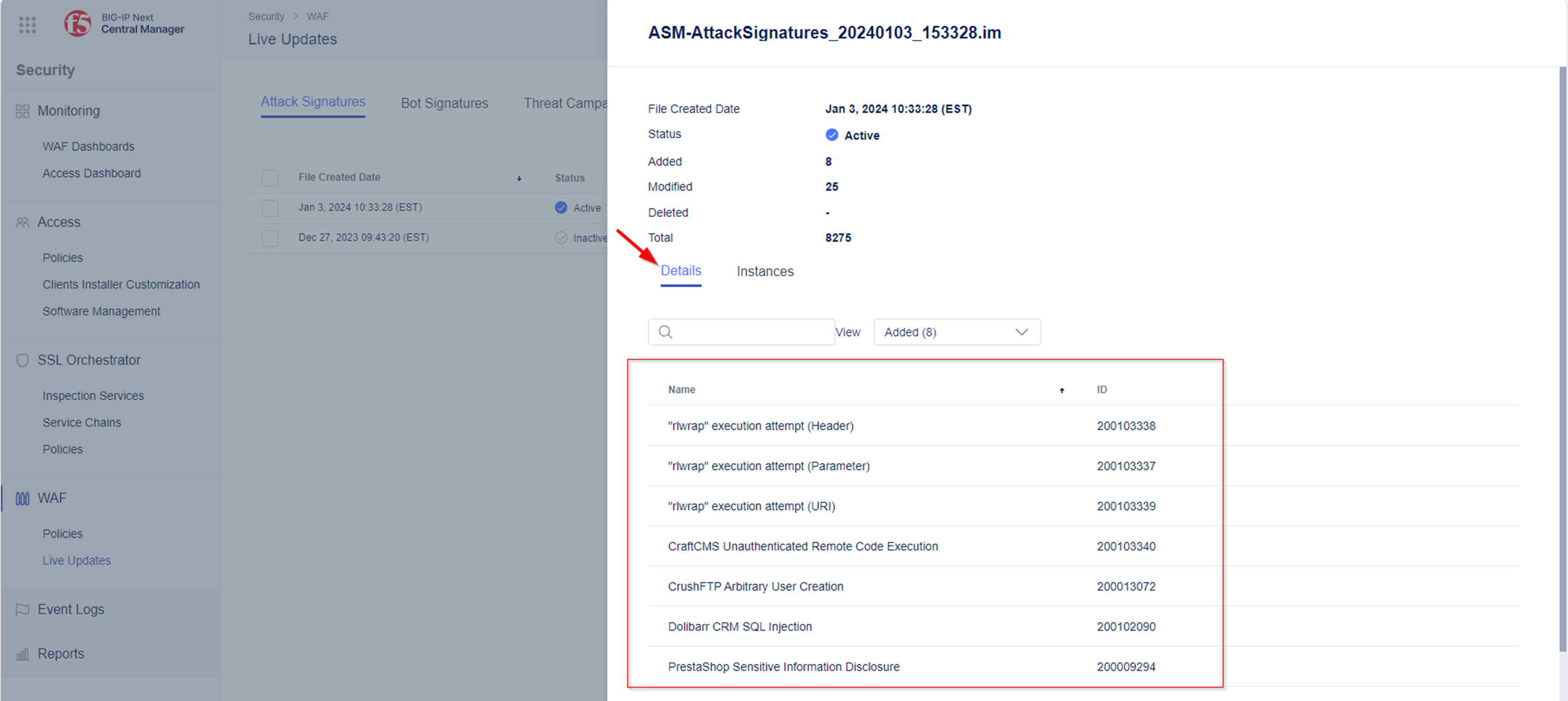
- If there happens to be an update available the Attack Signatures and/or Threat Campaigns will be updated. Once the update is complete, you will be prompted with a successful message. The status of the updated package will change to Active, and the installation date will change to the date the update file was created.
- Click on the filename, e.g. ASM-AttackSignatures_20240103_153328.im (The name might be different based on latest signature date), to get more details about the changes introduced by the update.
General remark:
Within this lab, we showed you how to enable live updates of Attack Signatures and Threat Campaigns. Users also have the option to manually upload Attack Signatures or Threat Campaigns. To do this, you just have to select the “Upload File” button in each tab. This is not required for the lab, but keep in mind that this option is available to you.
Congratulations - You have finished Module 1