Advanced Multi-layer Firewall Protection > [Archive1] AFM - The Data Center Firewall > Lab 2 - AFM Packet Tester, Flow Inspector, Stale Rule Lab Source | Edit on
Advanced Firewall Manager (AFM) Packet Tracer¶
Create and View Packet Tracer Entries¶
In this section, you will generate various types of traffic as you did previously, but now you will view the flow using the network packet tracer. Login to bigip01.f5demo.com
(10.1.1.4), navigate to Security > Debug > Packet Tester.
Create a packet test with the following parameters:
| Protocol | TCP |
|---|---|
| TCP Flags | SYN |
| Source | IP - 1.2.3.4 Port – 9999 Vlan – external |
| TTL | 255 |
| Destination | IP – 10.1.20.11 Port - 80 |
| Trace Options | Use Staged Policy – no Trigger Log - no |
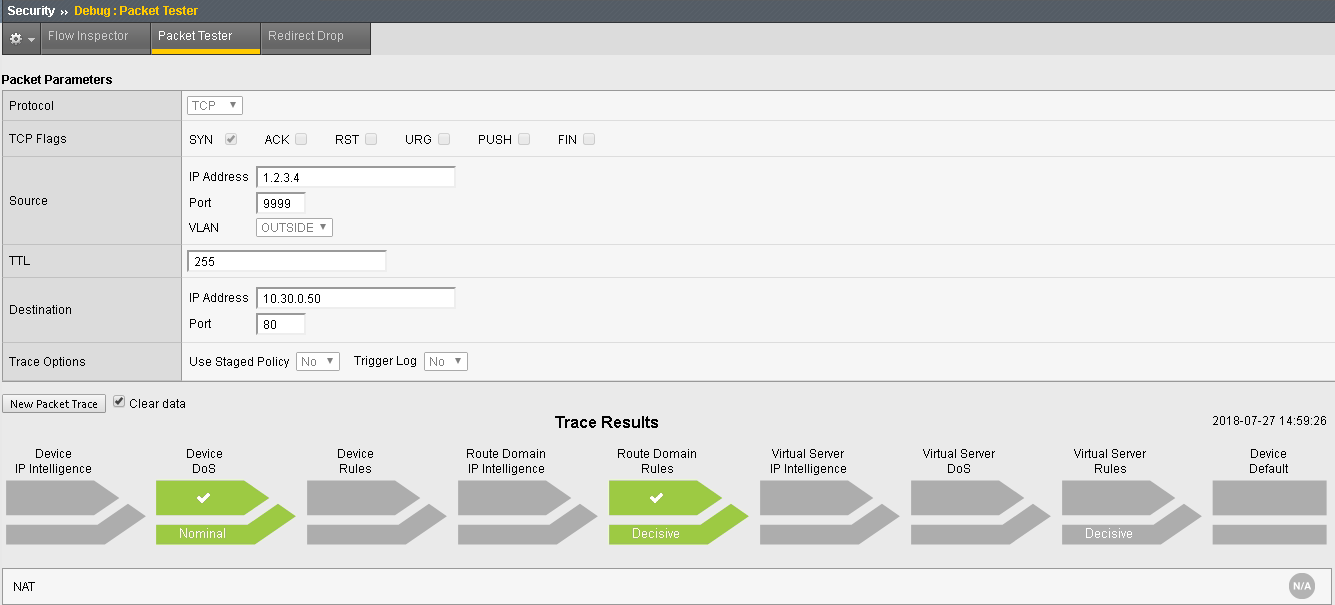
Click Run Trace to view the response. Your output should resmeble the allowed flow as shown below:
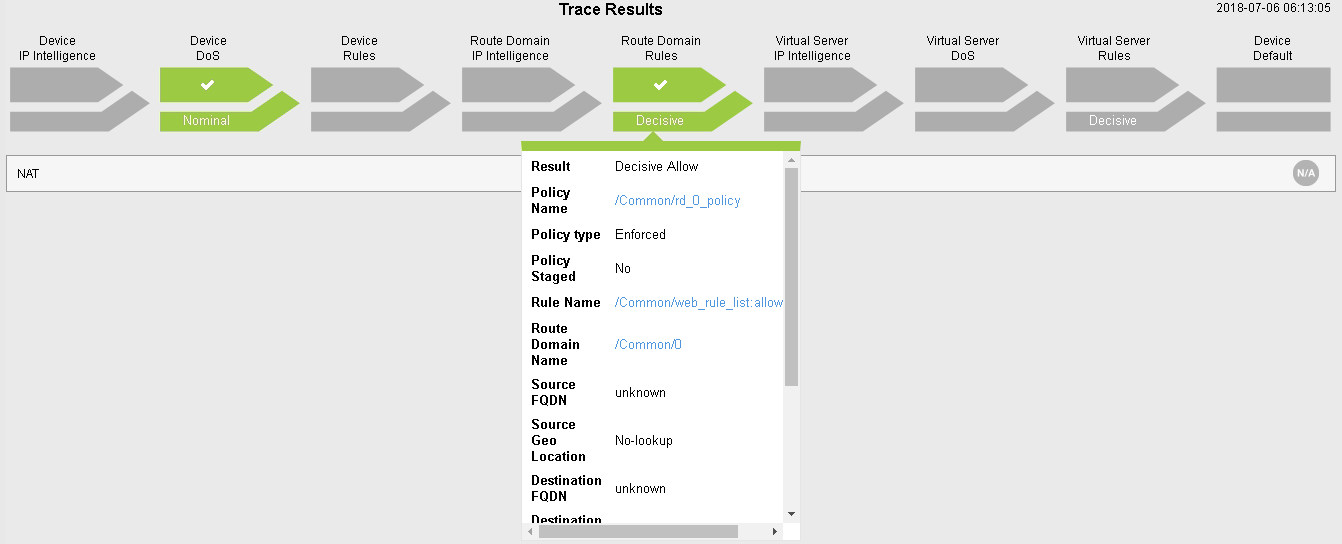
You can also click on the “Route Domain Rules” trace result and see which rule is permitting the traffic.
Click New Packet Trace (optionally do not clear the existing data – aka leave checked).
Create a packet test with the following parameters:
| Protocol | TCP |
|---|---|
| TCP Flags | SYN |
| Source | IP - 1.2.3.4 Port – 9999 Vlan – Outside |
| TTL | 255 |
| Destination | IP – 10.1.20.11 Port - 8081 |
| Trace Options | Use Staged Policy – no Trigger Log - no |
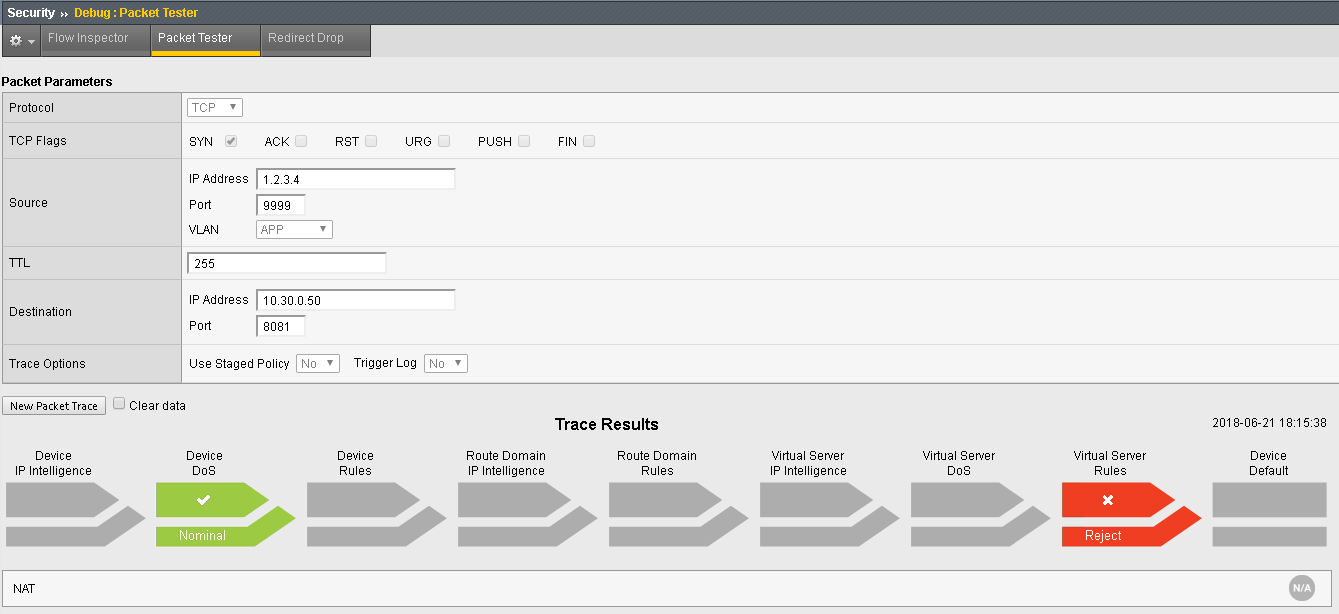
Click Run Trace to view the response. Your output should resemble the allowed flow as shown below:
| Protocol | TCP |
|---|---|
| TCP Flags | SYN |
| Source | IP - 1.2.3.4 Port – 9999 Vlan – Outside |
| TTL | 255 |
| Destination | IP – 10.1.20.11 Port - 443 |
| Trace Options | Use Staged Policy – no Trigger Log - no |
This traffic will be blocked by the default deny rule
This shows there is no rule associated with the route domain or a virtual server which would permit the traffic. As such, the traffic would be dropped/rejected.