F5 BIG-IP SSL Orchestrator Training Lab > All SSL Orchestrator Lab Guides > SSL Orchestrator with Secure Web Gateway (SWG) as a Service > 5. Create a Transparent Forward Proxy SSLO Source | Edit on
5.4. Testing the deployment¶
To test the deployed solution, RDP to the Desktop-Outbound client machine.
- At the Login to xrdp window, click on the OK button.
You will then see the Client desktop.
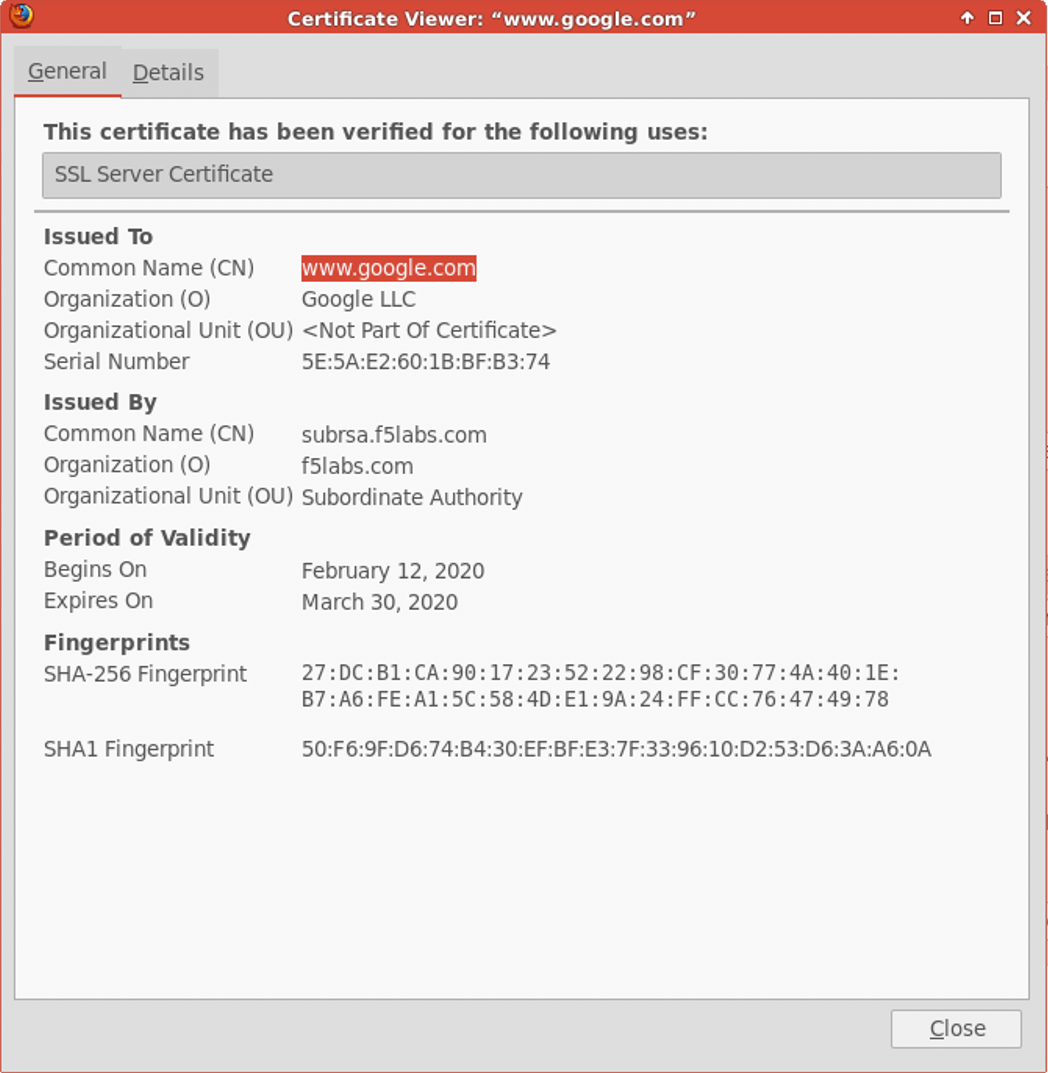
5.4.1. Server certificate test¶
Open a web browser (e.g., Firefox, Chrome) on the outbound client system and navigate to any remote HTTPS site (e.g., https://www.google.com). Once the site opens in the browser, check the server certificate of the site and verify that it has been issued by the local CA configured in SSLO. This confirms that the SSL forward proxy functionality enabled by SSL Orchestrator is working correctly.
5.4.2. Decrypted traffic analysis on the security services¶
Depending on the type of security service, it may be easier to log into the console shell and run a similar tcpdump capture on the inbound or outbound interface. A tcpdump capture usually requires root or sudo access.
Let's check if we see data on the TAP device.
- In the UDF UI, select the Access drop down selection on the Service - TAP VM, then select WEB SHELL.
- In the web shell window, perform a packet capture using tcpdump. The client machine's IP address is 10.1.10.50.
sudo tcpdump -lnni eth1 -Xs0 host 10.1.10.50
- Browse to an HTTPS web site (e.g., https://www.cnn.com) from the Desktop-Outbound machine (RDP session) and notice that the TAP device is receiving traffic unencrypted.
- Return to the web shell and press <CTRL-C> to stop the tcpdump.
Let's check another security device. Perform a tcpdump on the IPS device to observe the decrypted clear text traffic.
- In the UDF UI, select the Access drop down selection on the Service - Inline L3 VM, then select WEB SHELL.
- In the web shell window, perform a packet capture using tcpdump. The client machine's IP address is 10.1.10.50. Recall that port remap was enabled so the unecrypted traffic will be seen on destination port 8181.
sudo tcpdump -lnni eth1.10 -Xs0 host 10.1.10.50 and port 8181
- Browse to an HTTPS web site (e.g., https://www.cnn.com) from the Desktop-Outbound machine (RDP session) and notice that the IPS device is receiving traffic unencrypted.
- Return to the web shell and press <CTRL-C> to stop the tcpdump.
- Close out (exit) all Webshell windows.
Attention
This is the end of the lab module, but before we move on to the next lab we will need to remove all previously configured sslo topologies. This process is accomplished by selecting the SSLO Orchestrator menu, clicking on Configuration, and in the top right corner of the SSLO Guided Configuration UI clicking on the cleanup icon depicted as a trashcan icon which will cleanup all SSLO object.
Note - the sslo cleanup process may take several minutes to complete