4.18. Implementing SSL Orchestrator Limited Mode¶
4.18.1. What it is¶
SSL Orchestrator Limited mode provides a capability to enable decrypted traffic inspection to a third party security device under the following restrictions:
The configuration is limited to the creation of a single security service.
Traffic inspection is required for a reverse proxy (inbound) application.
Dynamic, policy-based traffic steering, categorization, and TLS bypass are not required.
SSL Orchestrator Limited mode could be useful in situations where the environment does not require multiple security services and/or robust policy-based traffic steering. The Limited mode configuration allows for the creation of a single inspection device which is then manually attached to a reverse proxy application virtual server. In the event that SSL Orchestrator is licensed, the existing inspection device configuration automatically updates to an SSL Orchestrator-managed service and can then be rolled into dynamic traffic steering policies.
4.18.2. How to build it¶
SSL Orchestrator Limited mode is enabled by provisioning unlicensed SSL Orchestrator. Upon provisioning, the SSL Orchestrator UI menu is enabled. Within the SSL Orchestrator configuration UI, the Services tab allows for the creation of a single security service. Please refer to Section 3 for full details on creating security services.
Depending on the type of security service defined, a number of BIG-IP objects will be created to support this service, including virtual servers, iRules, pools, VLANs, self-IPs, service, split-session, and connector profiles. The enablement of SSL Orchestrator Limited mode focuses on the connector profiles, visible in the BIG-IP UI, under Local Traffic -> Profiles -> Other -> Connector. The connector profile is responsible for attaching the decrypted traffic flow to an “entry” virtual server, which then passes the traffic to the inspection device. Also depending on the type of security service defined, up to four connectors may be created:
Connector profile ending with “-t-4” indicates TCP IPv4.
Connector profile ending with “-t-6” indicates TCP IPv6.
Connector profile ending with “-u-4” indicates UDP IPv4.
Connector profile ending with “-u-6” indicates UDP IPv6.
To use the newly created security service, edit an application virtual server and attach the connector profile to the Connector Profile selection that matches the application traffic flow. For example, if the application virtual server is defined for HTTP traffic with an IPv4 address, use the -t-4 connector profile.
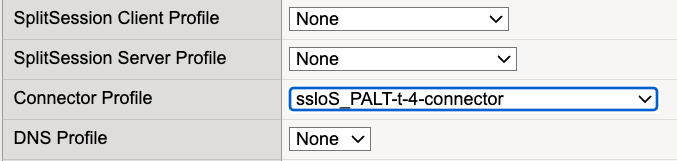
Figure 105: Connector Profile Selection¶
Note that unlike full SSL Orchestrator, the Limited mode assumes that TLS decryption is handled directly by the application virtual server.
4.18.3. How to upgrade to full SSL Orchestrator¶
When the full power and capabilities of SSL Orchestrator are required, it is simple to upgrade:
Remove any connector profiles from application virtual servers.
License SSL Orchestrator. Assuming Limited mode is already in use, SSL Orchestrator should already be provisioned.
Configure SSL Orchestrator as needed. The security service created in Limited mode will be available for immediate use in service chains.
4.18.4. Additional Information¶
When configuring Port Remap for a security service, an additional iRule is required to enable this function. Creation of the security service will also create a new iRule that ends with “-port_remap”. For example, if the service is named “myL2service”, the new iRule will be accordingly named ssloS_myL2service-port_remap. To enable port remap for a security service in SSL Orchestrator Limited mode, attach this iRule to your HTTPS application virtual server. The application virtual server must minimally contain an HTTP profile and client SSL profile.