F5 BIG-IP Next Access Labs > User Authentication > Lab 2 - SAML Azure authentication with Kerberos SSO Source | Edit on
Lab 2.3 - Create an Application¶
Creating an application and assign an Access policy to the application¶
- Access BIG-IP Next Central Manager if you’re not already logged in.
- Click on the Workspace icon and select Application.
- Click on Start Adding Apps button to create an Application.
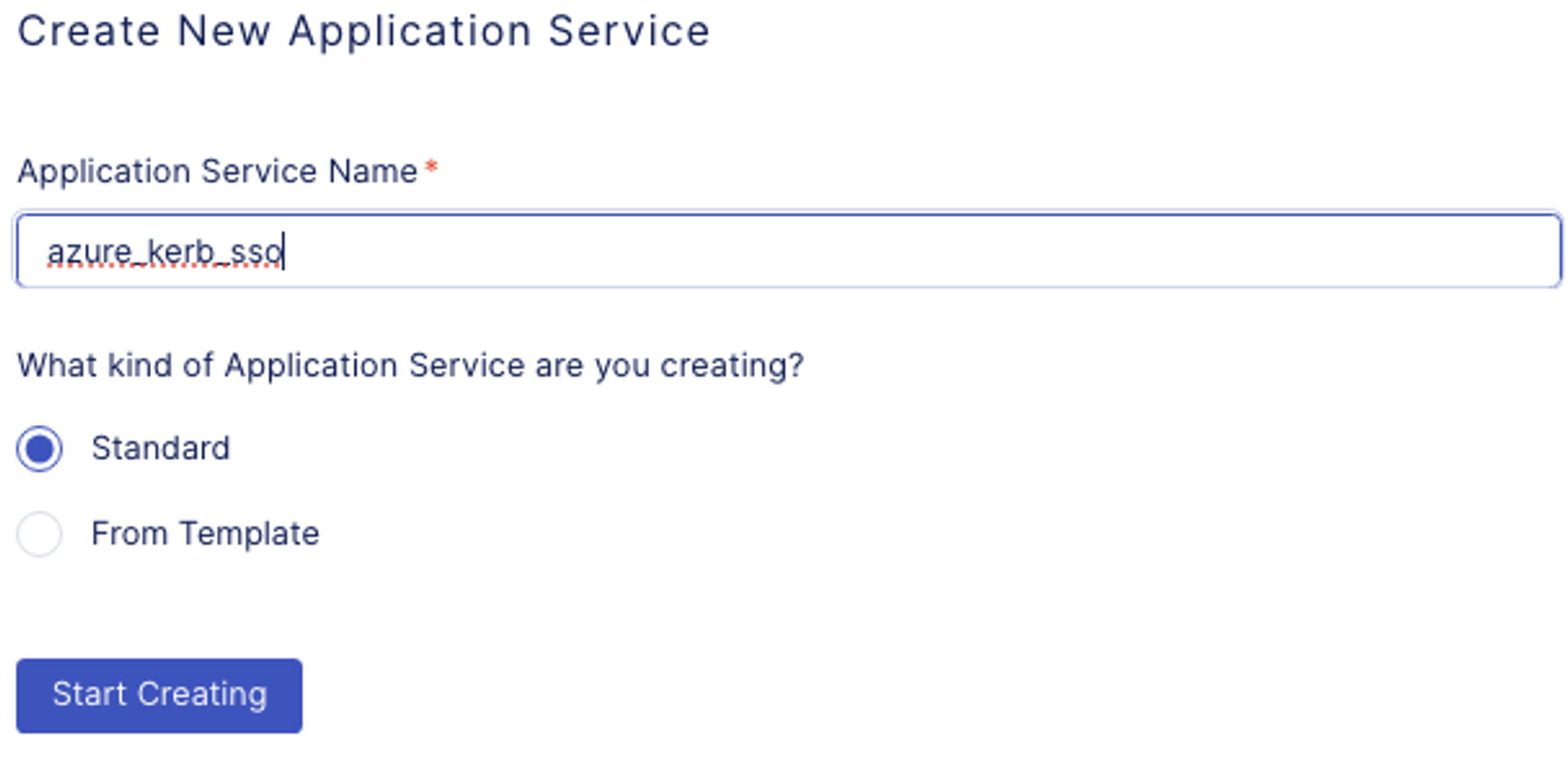
- In the Add Application screen, you can choose to create an application based on a template or create a standard application from scratch. In this lab, we will start with a Standard application.
- In Application Service Name type: azure_kerb_sso
- Under What kind of Application Service are you creating?: select Standard
- Click on Start Creating button
- In the Application Services Properties, click Start Creating.
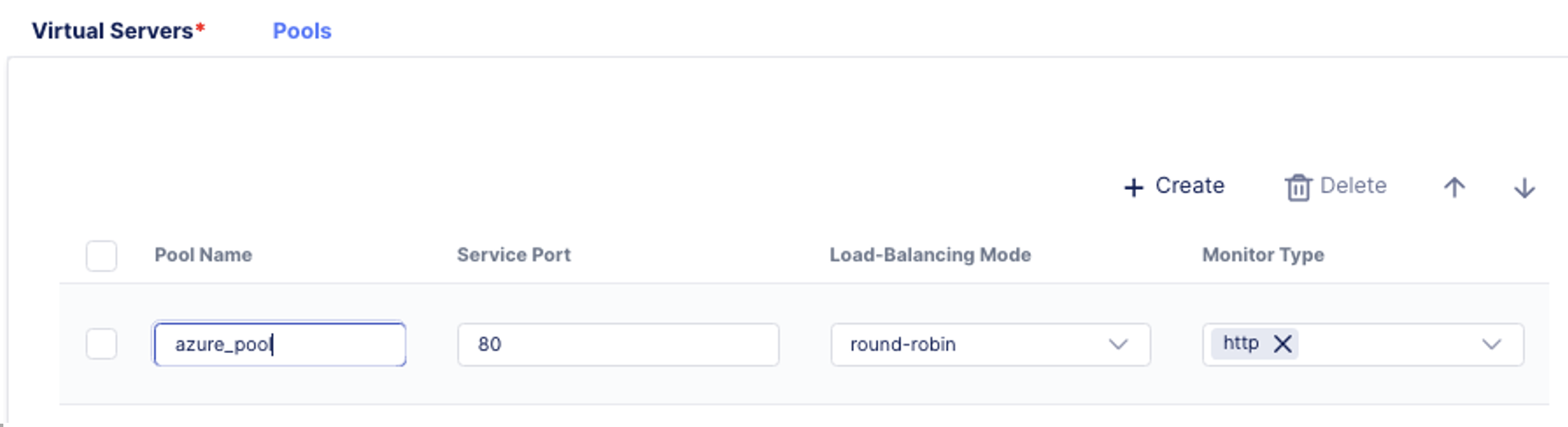
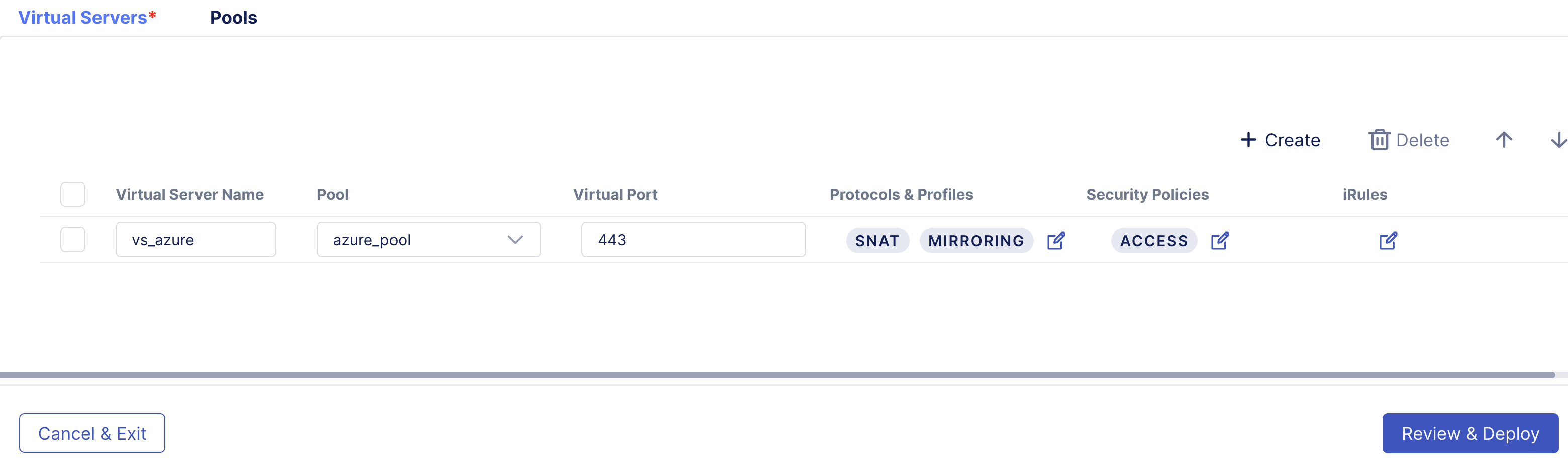
- In the Virtual Servers configuration screen, we will define the Pool first, so click on Pools tab, click Create, and type in Pool Name: azure_pool.
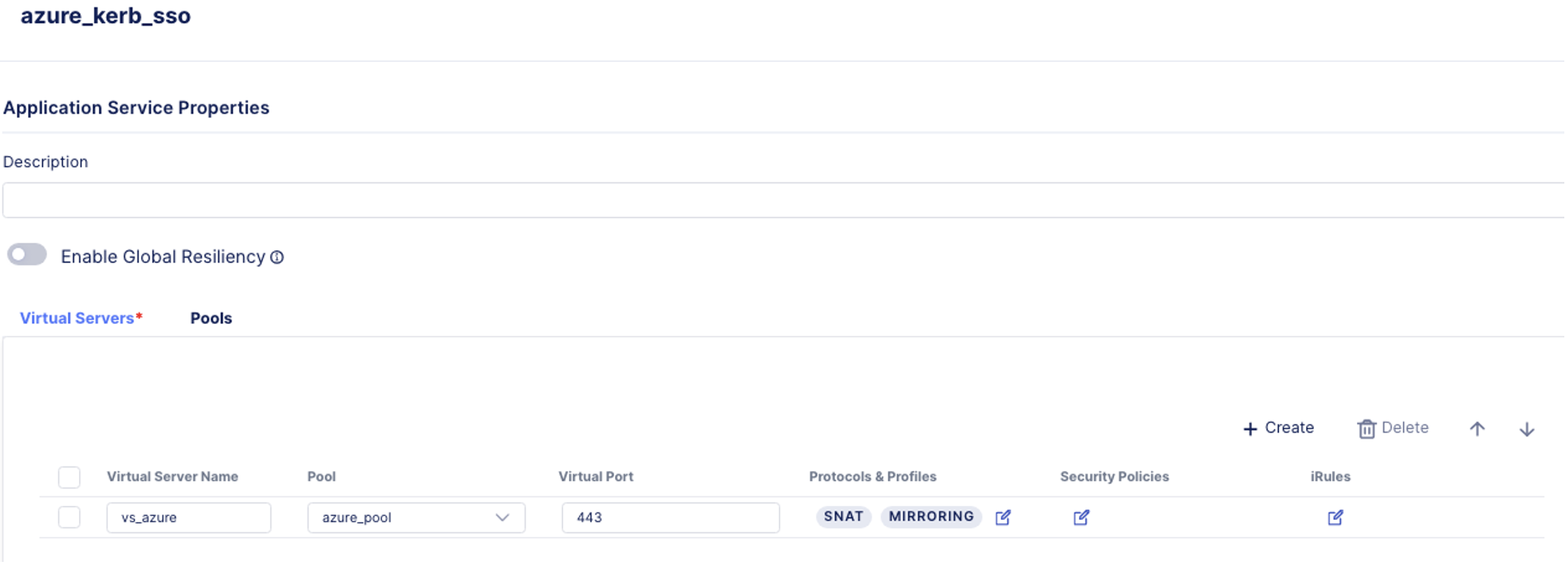
- Switch to the Virtual Servers tab. Now let’s define the Virtual Server properties.
Virtual Server Name: vs_azure Pool: azure_pool Virtual Port: 443
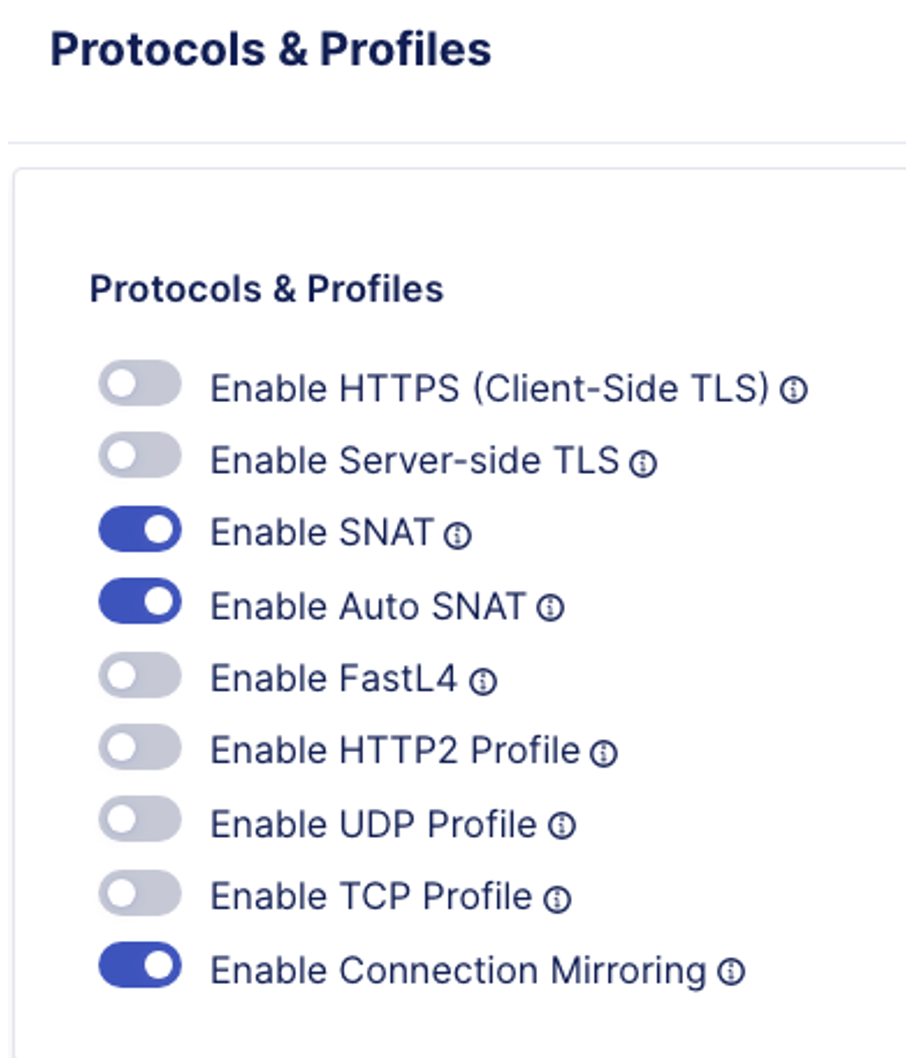
- Click on the Edit button under Protocols & Profiles to enable HTTPS
- In the Protocols and Profiles, tick the slider button for Enable HTTPS (Client-Side TLS)
- This will enable the features under HTTPS. Click on the Add button under the No Client-Side TLS to add a certificate.
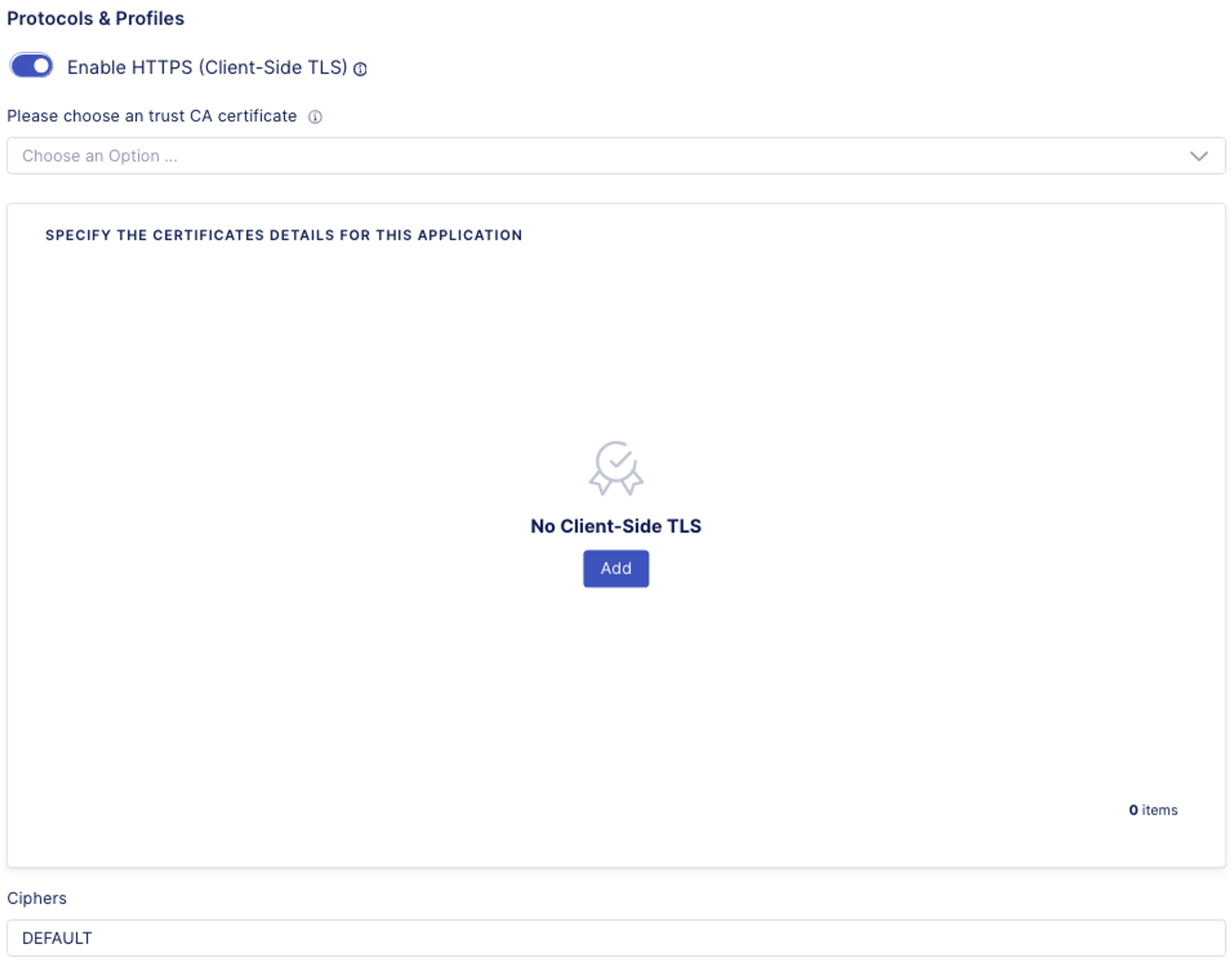
- In the Add Client-Side TLS screen, input the following information
- Name: azure_signed_client_cert
- RSA Certificate: self_demo.f5.com
- Click Save
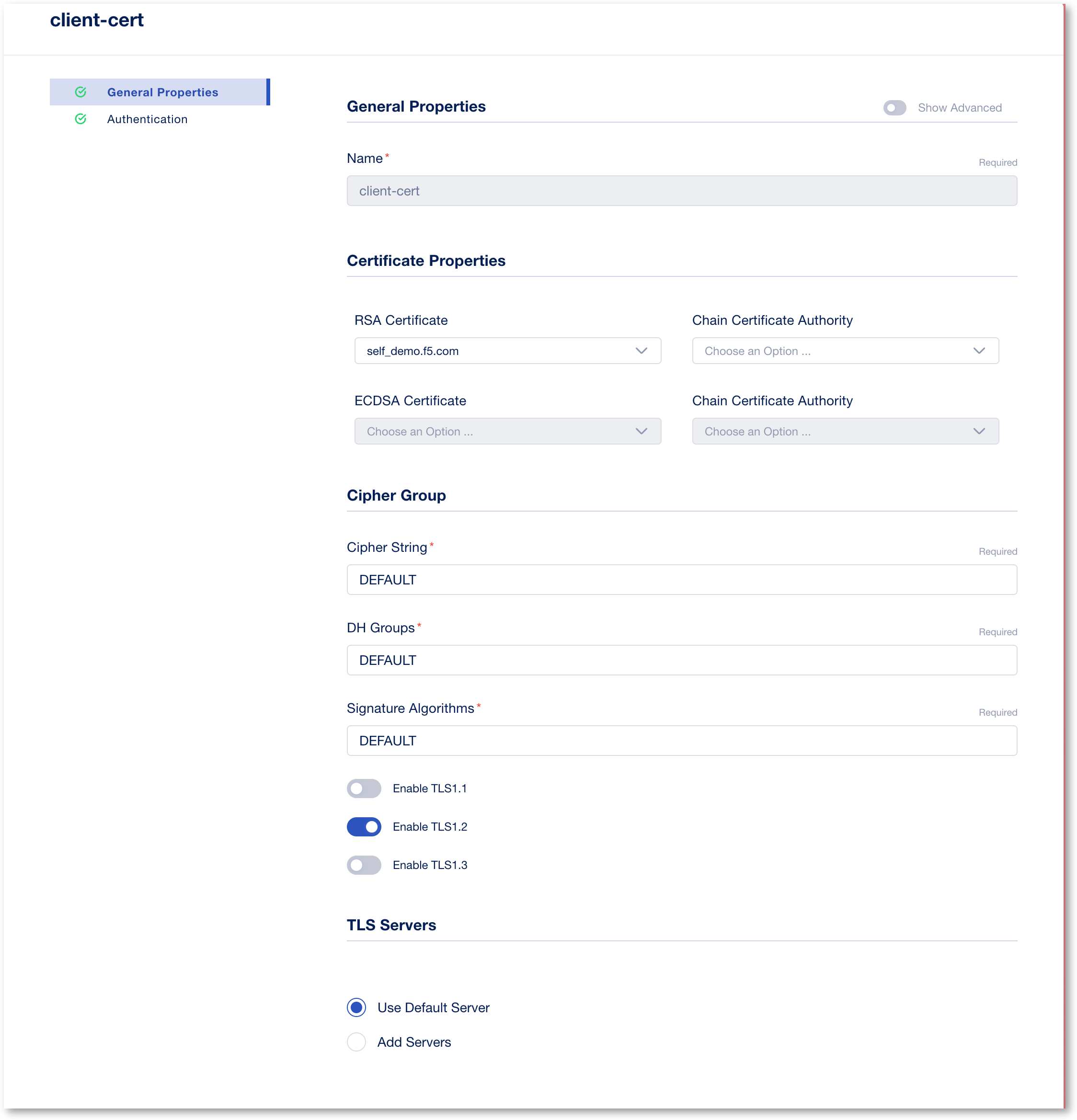
- This will take you back to the Protocols and Profiles screen. Enable HTTP Profile. Click Save.
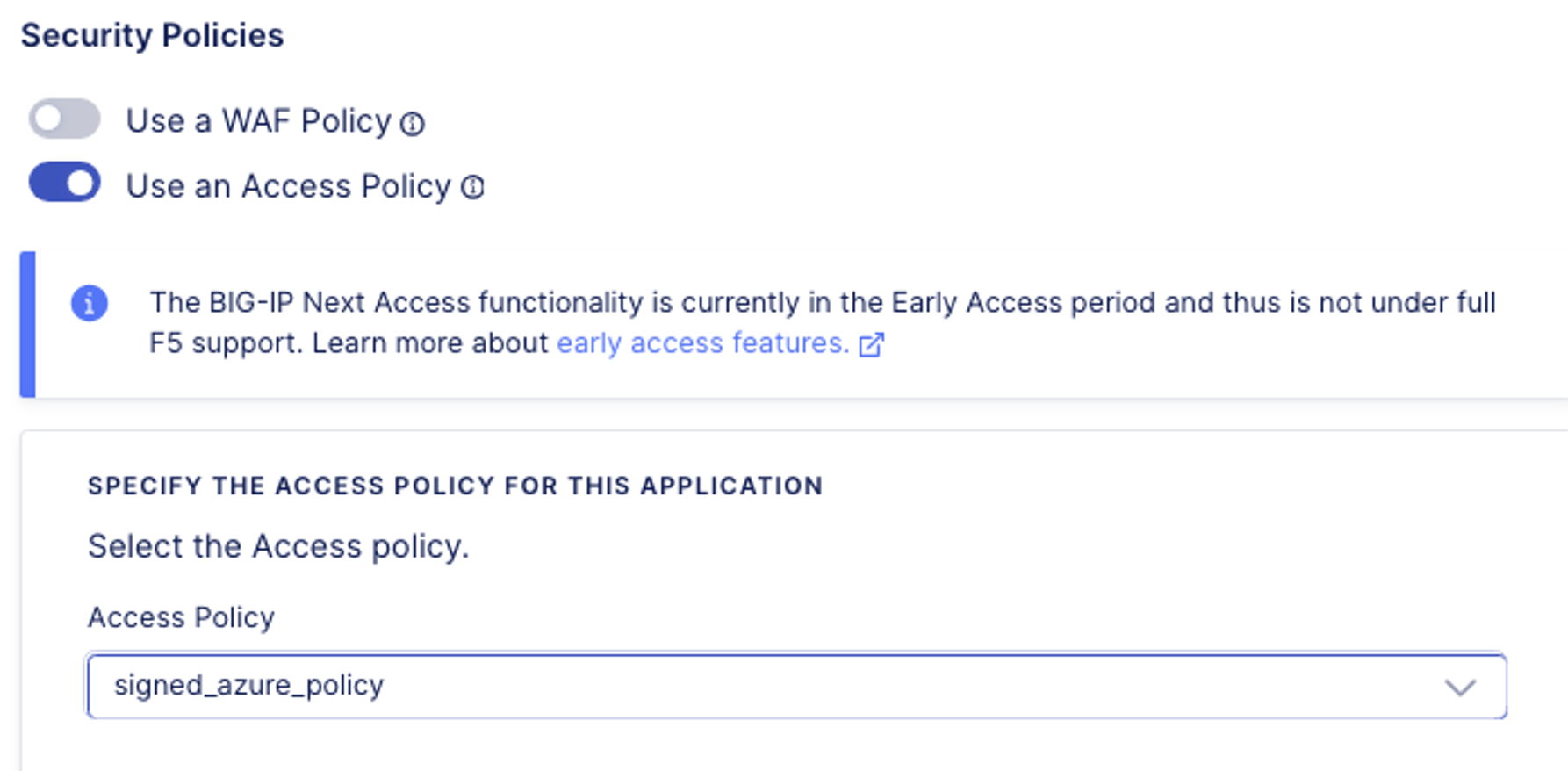
- This will take you back to the Virtual Server screen. Now we will attach the Access Policy we created previously to this application. Click on the Edit button under Security Policies.
- This will open the Security Policies screen. Slide the button next to Use an Access Policy. Under Specify the Access Policy for this Application, click the drop-down box and select the signed_azure_policy created previously. Click Save.
- After clicking Save, you should be returned to the Virtual Server property page. Click on Review & Deploy at the bottom right-hand corner.
- In the Deploy screen, this is where you define which BIG-IP Next instance to deploy the application. Click on Start Adding to select a BIG-IP Next Instance.
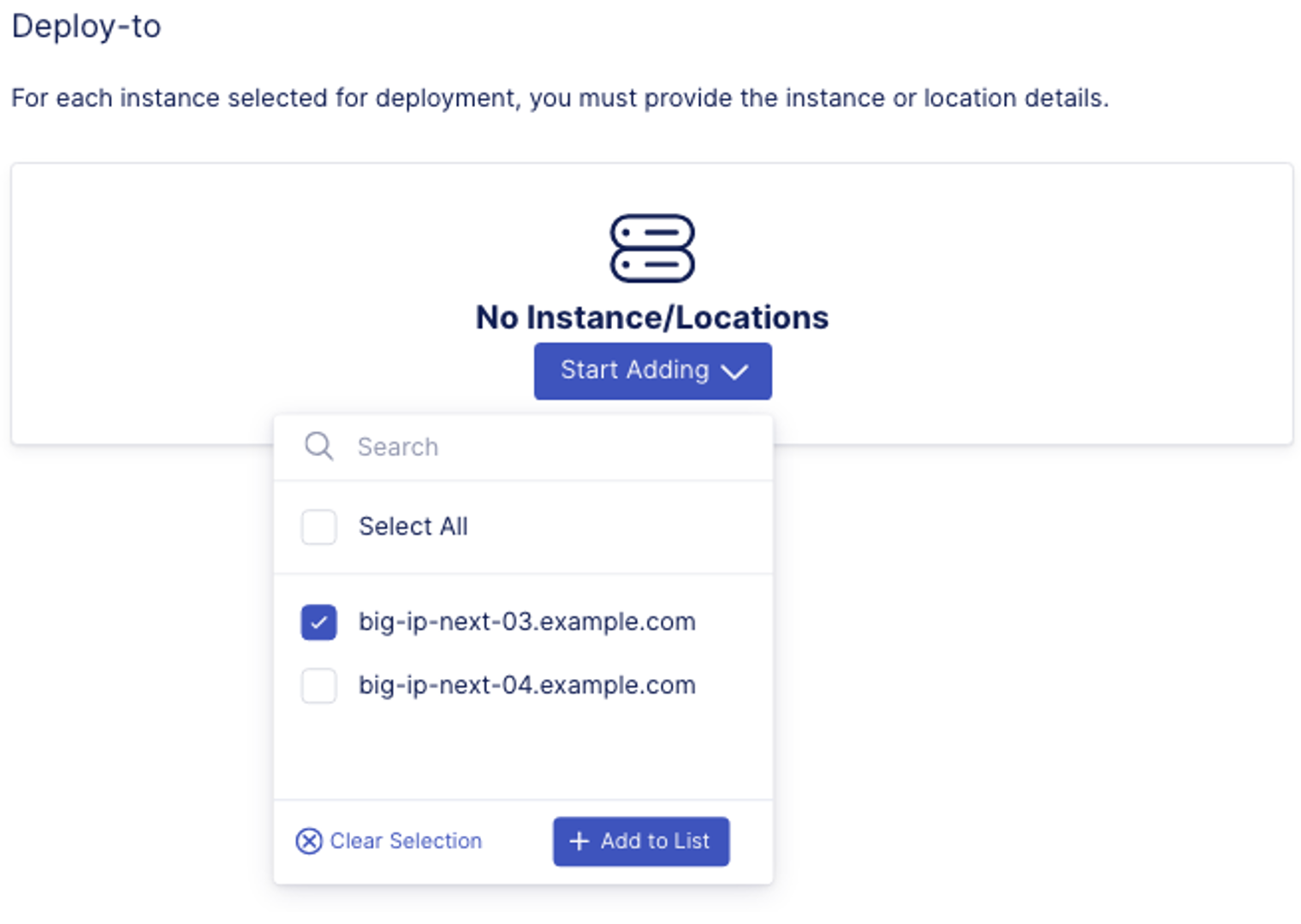
- In the drop down box, select big-ip-next-03.example.com, then click on Add to List button.
- In the Virtual Address: box type: 10.1.10.100 to associate with the virtual server vs_azure.
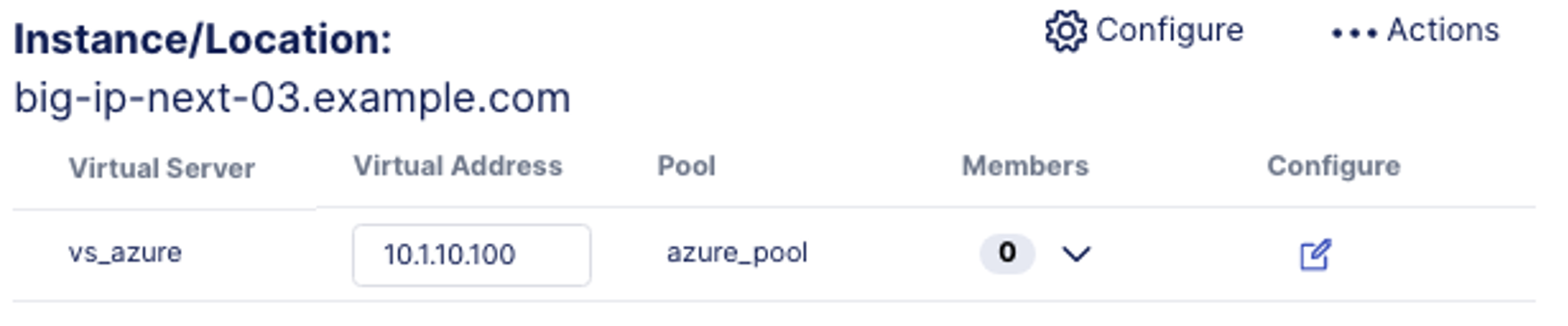
- Click on the drop down arrow under the Members column. This is where you can add the backend pool members to the virtual server.
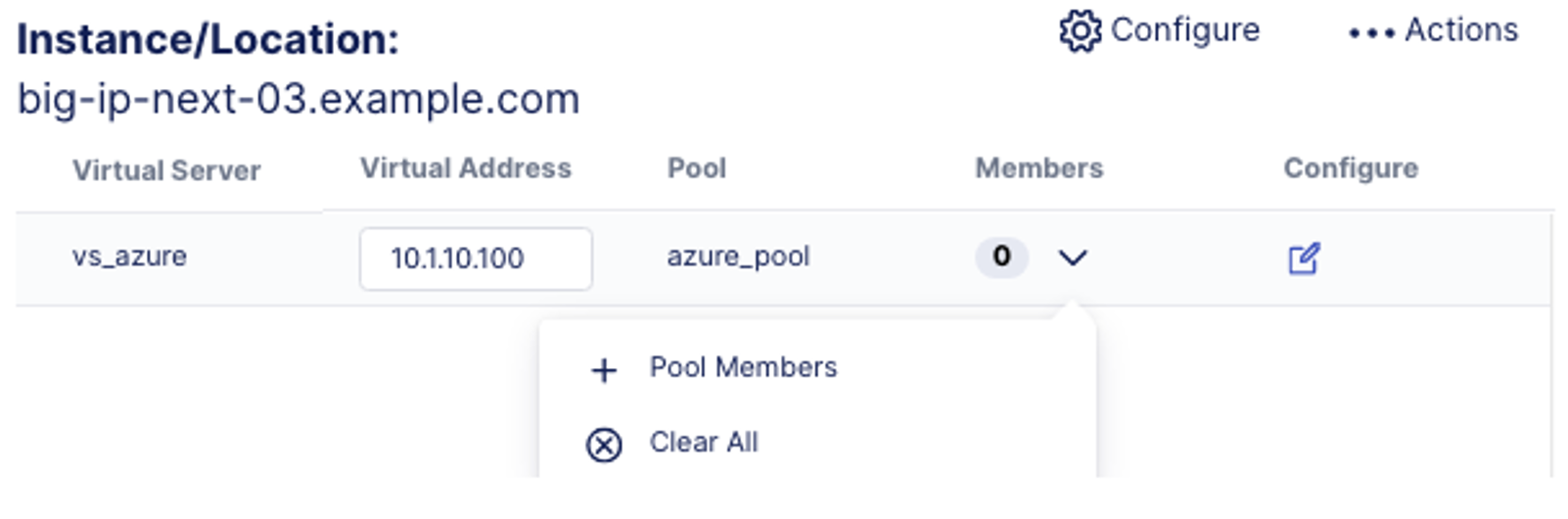
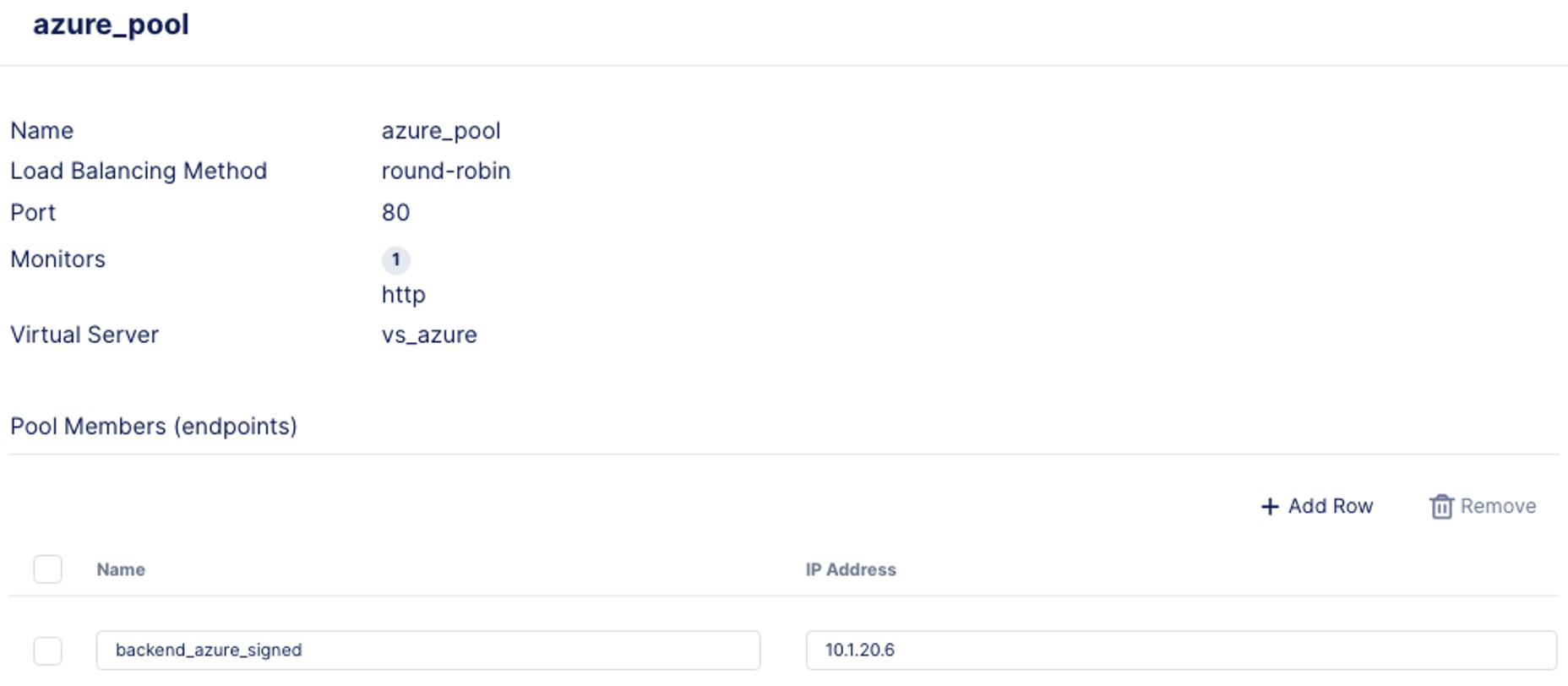
- In the azure_pool screen, click on Add Row, and enter the following information for the pool member.
- Name: backend_azure_signed
- IP Address: 10.1.20.6
- Click Save
- Now you’re ready to Deploy your application. Click on Deploy Changes at the bottom right-hand corner.
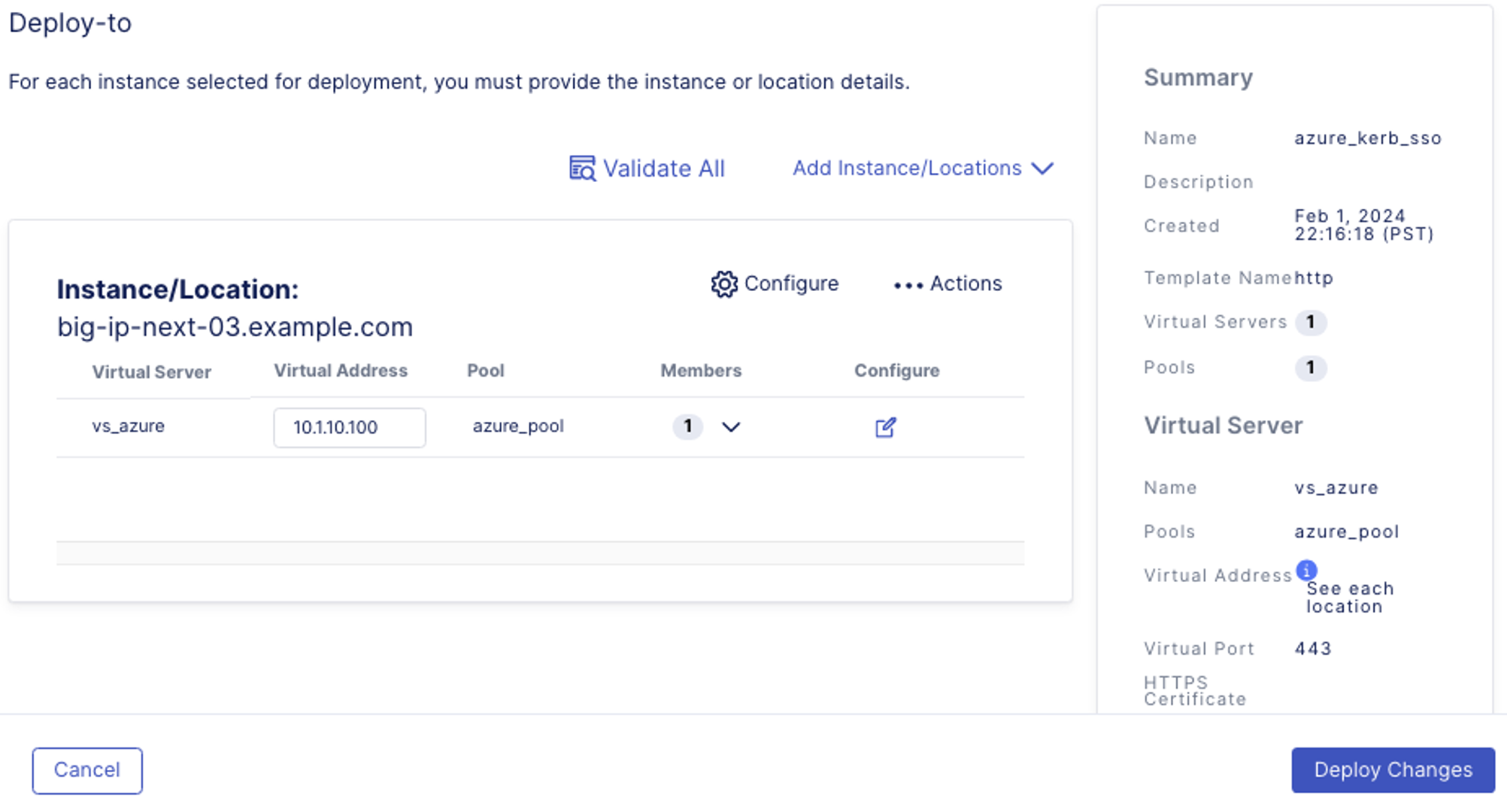
- Confirm in the pop-up window that you’re deploy to big-ip-next-03.example.com instance.
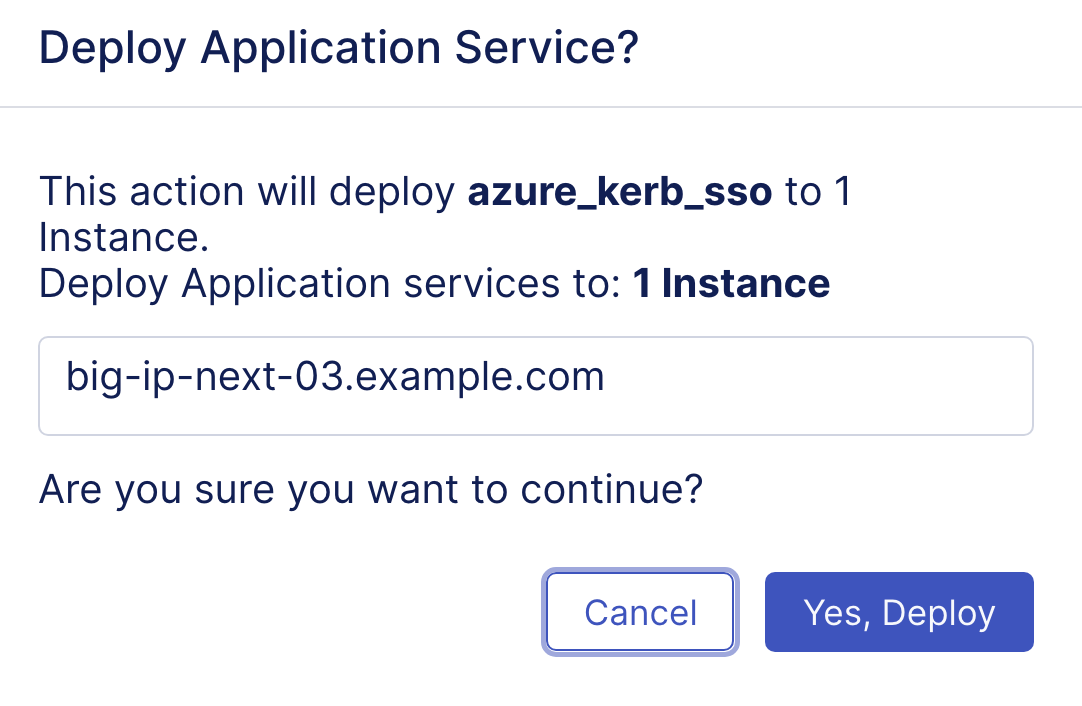
Click on Yes, Deploy
- You will get a status pop up window, and after a few seconds the screen should refresh and show you the My Application Service dashboard, with a confirmation that Deployment Complete.
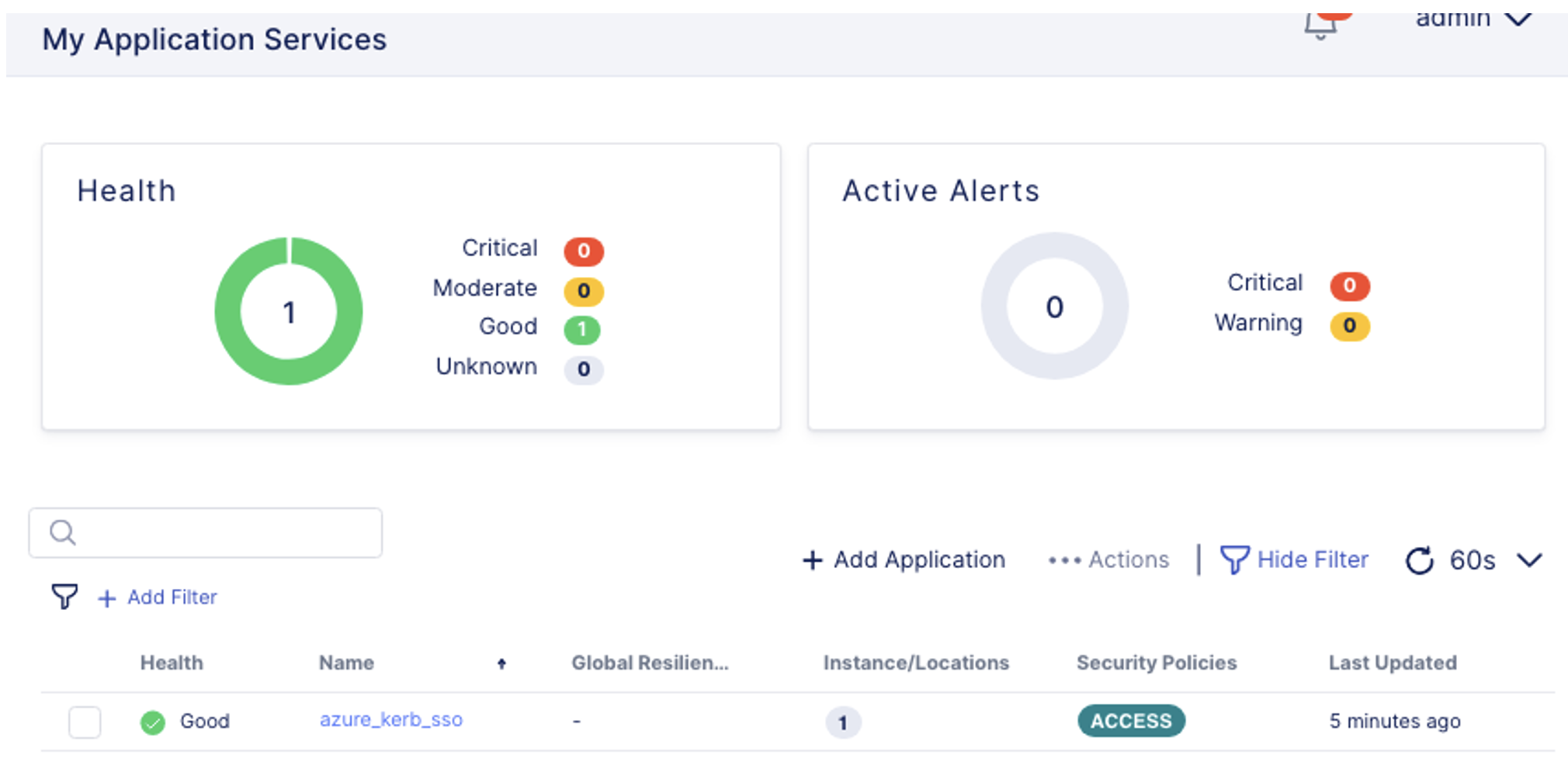
- My Application Services Dashboard should show you one application has been deployed, and Health is Good.
You have successfully created an application and assigned an access policy to it. Let’s test the application!