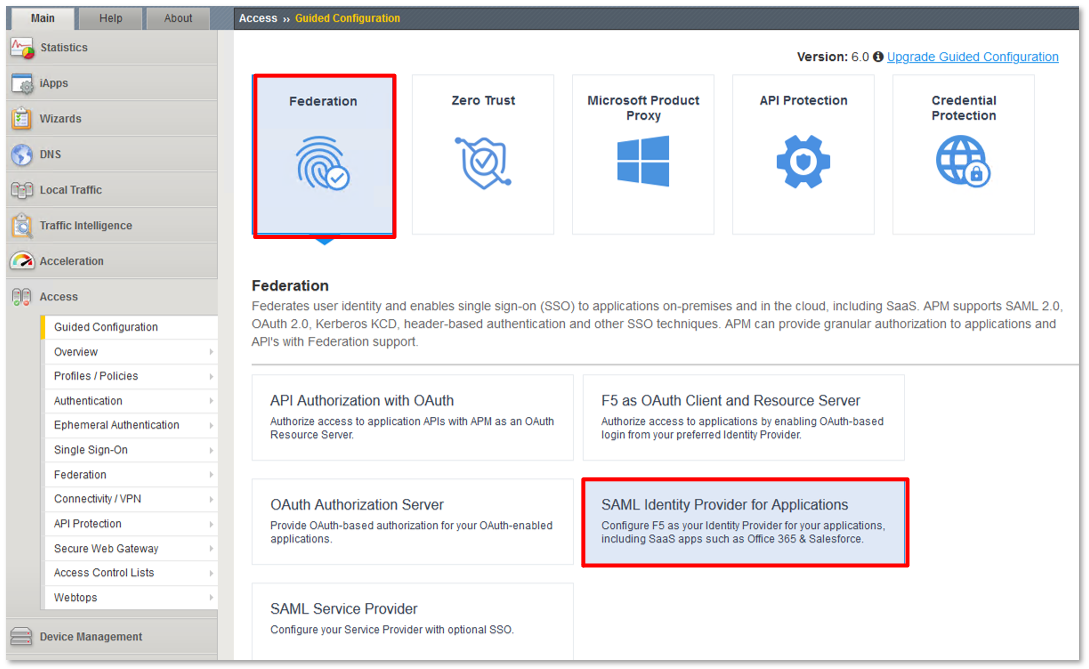
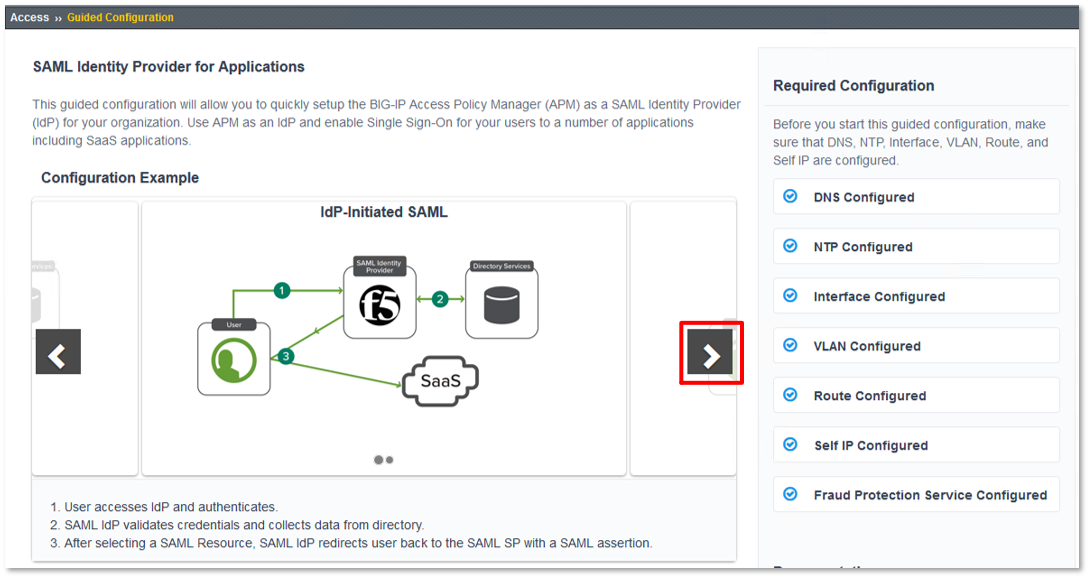
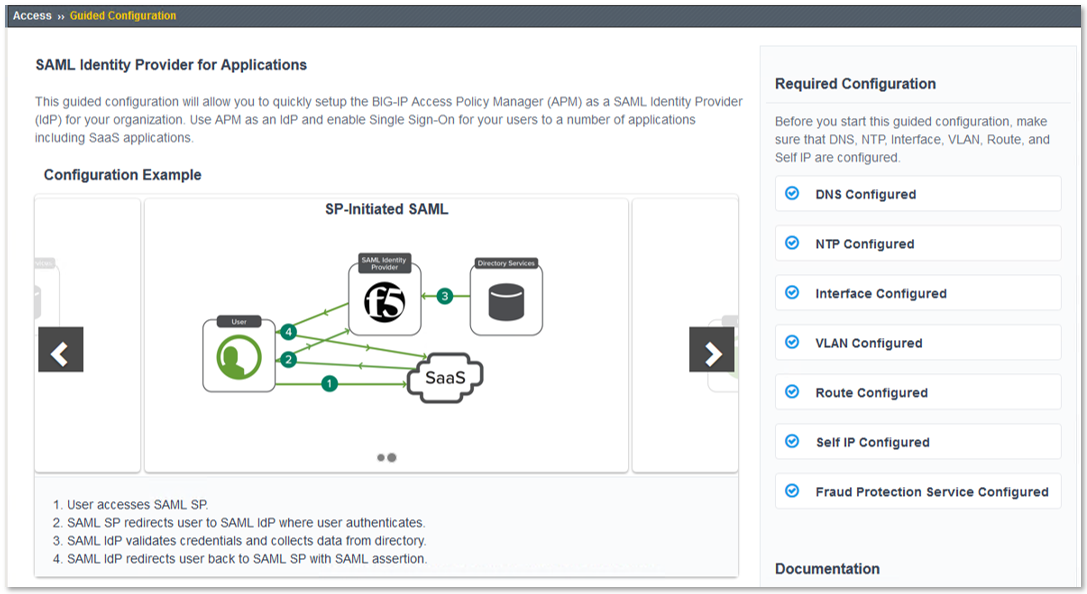
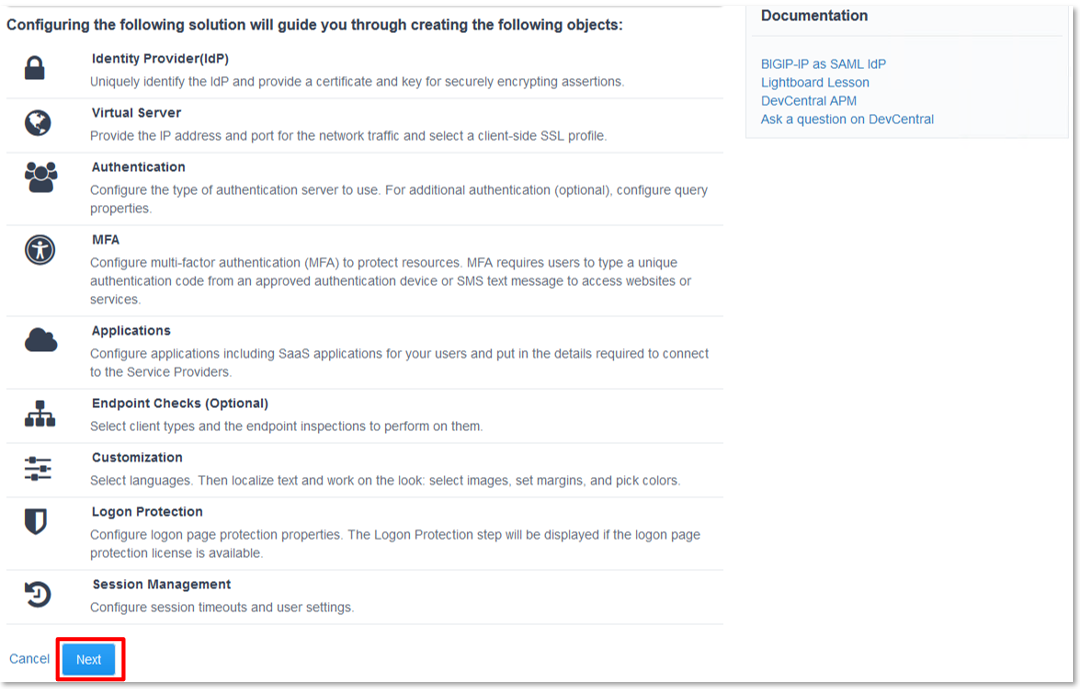
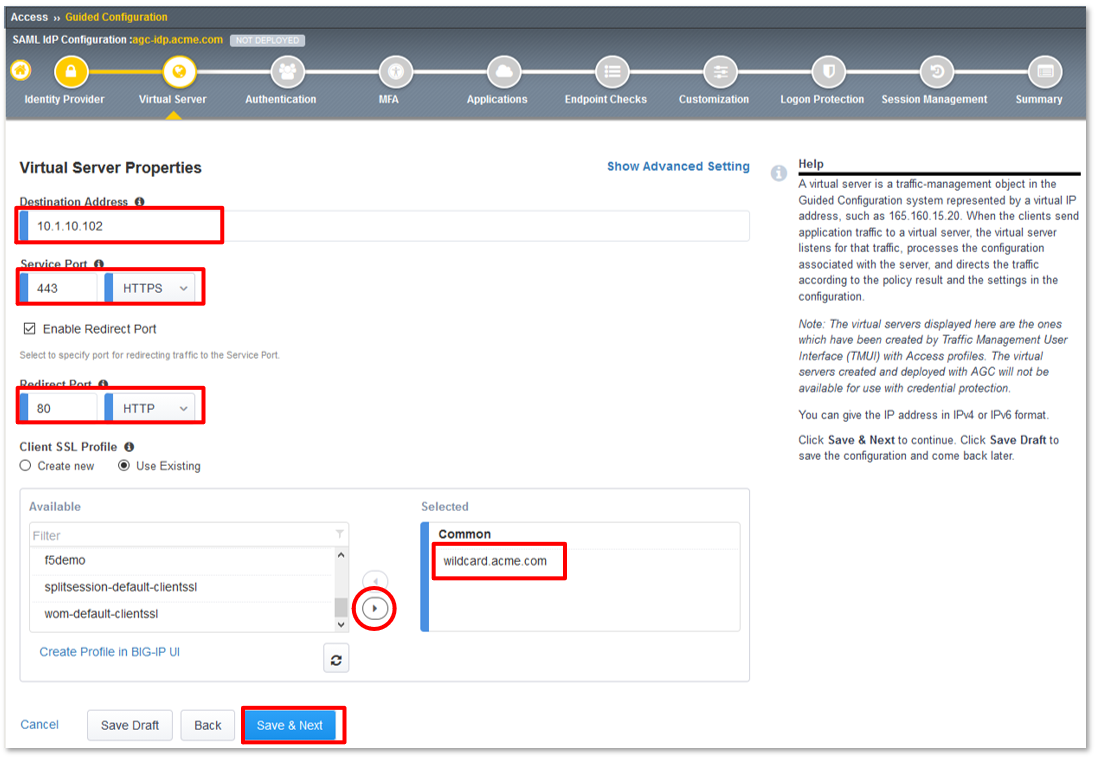
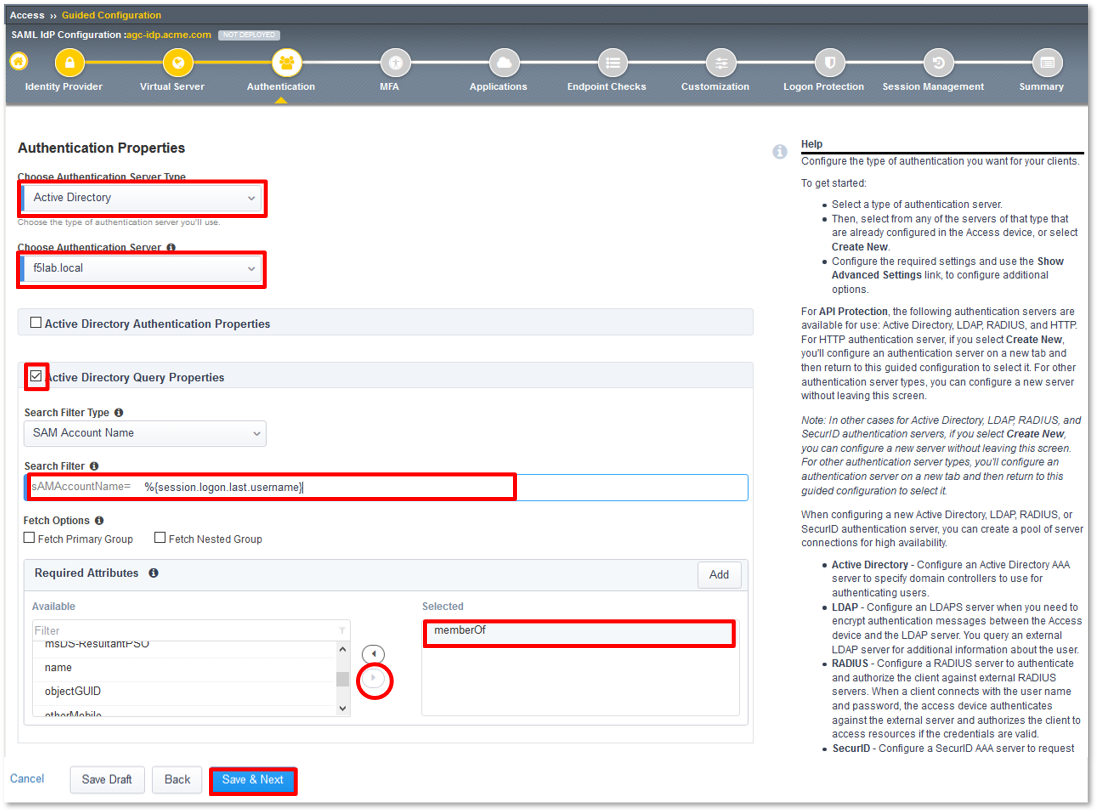
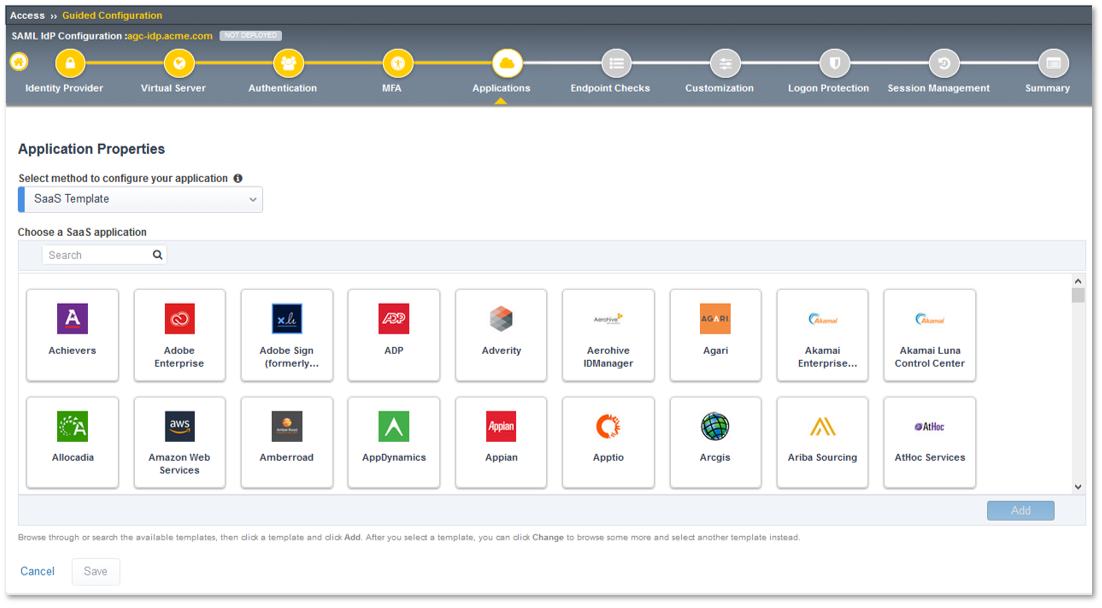
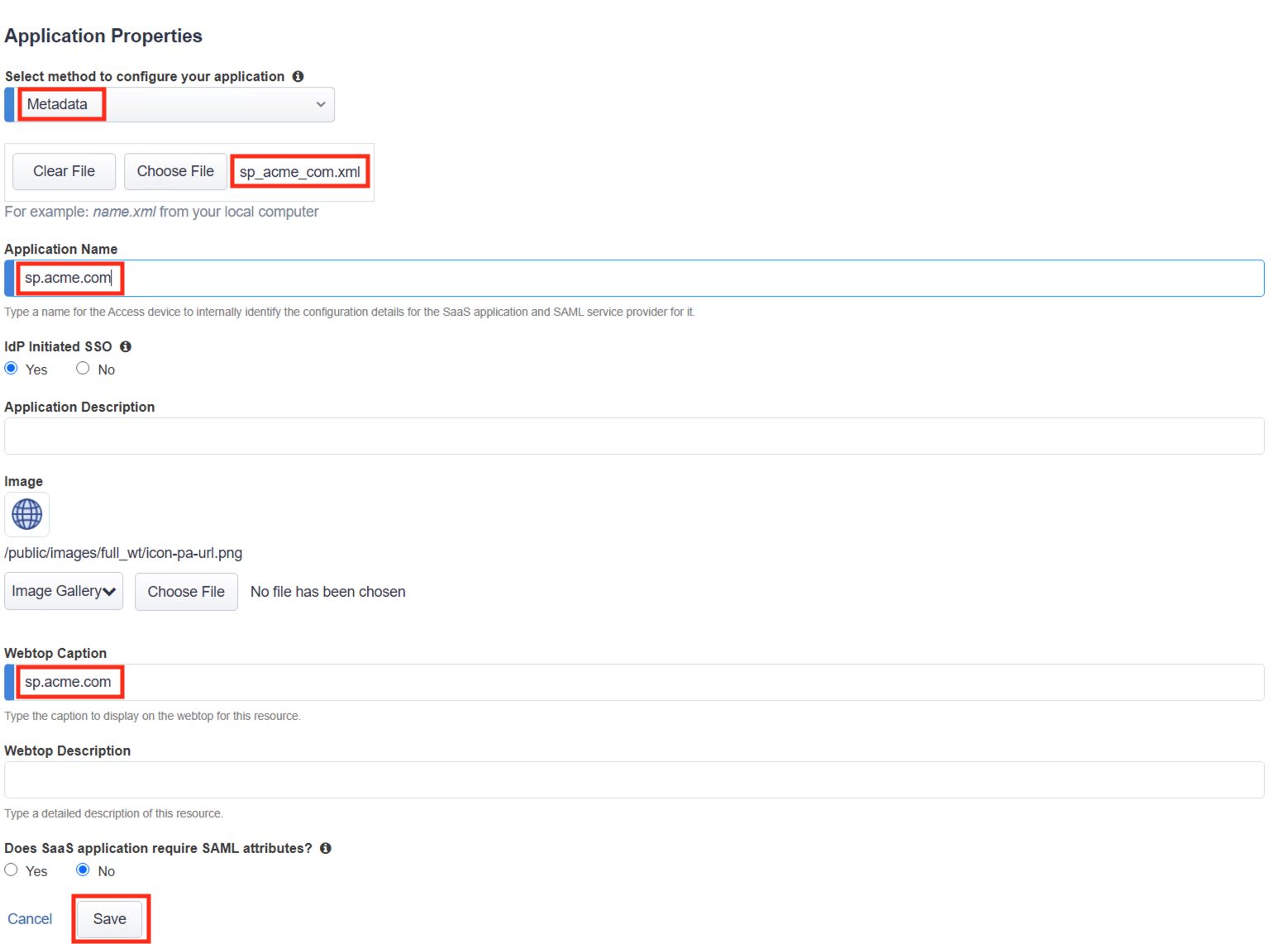
Lab 1: SAML IdP Access Guided Configuration (AGC) Lab
The purpose of this lab is to configure and test SAML Federation Services.
Students will leverage Access Guided Configuration (AGC) to
configure the various aspects of a SAML Identity Provider (IdP), import and bind
to a SAML Service Provider (SP) and test IdP-Initiated SAML Federation.
Objective:
- Gain an understanding of SAML Federation configurations and
their component parts through Access Guided Configuration (AGC)
- Gain an understanding of the access flow for IDP & SP Initiated SAML
Lab Requirements:
- All Lab requirements will be noted in the tasks that follow
- Estimated completion time: 25-30 minutes
Task 1 - Setup Lab environment
To access your dedicated student lab environment, you will need a web browser and Remote Desktop Protocol (RDP) client software. The web browser will be used to access the Unified Demo Framework (UDF) Training Portal. The RDP client will be used to connect to the jumphost, where you will be able to access the BIG-IP management interfaces (HTTPS, SSH).
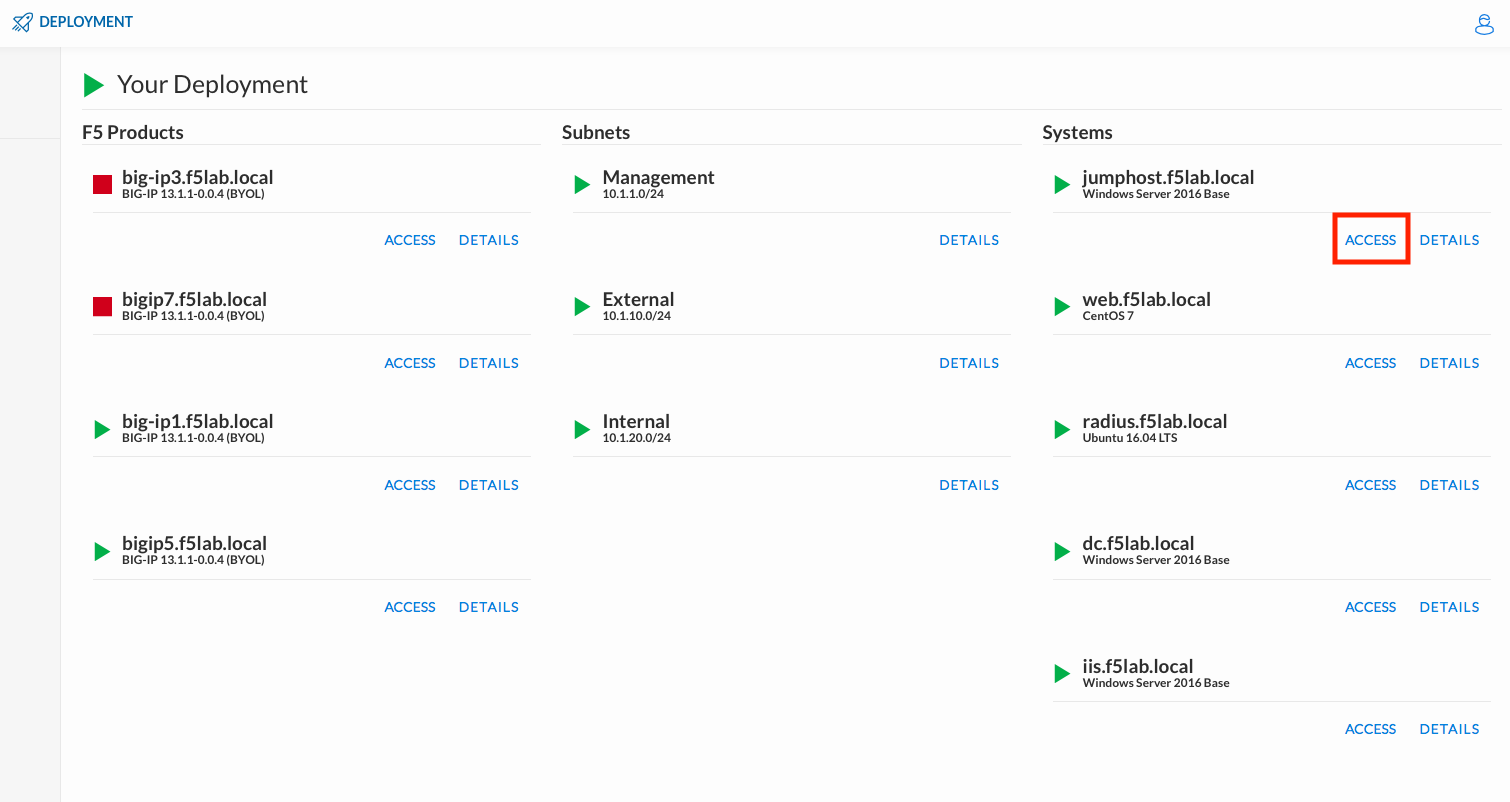
Click DEPLOYMENT located on the top left corner to display the environment
Click ACCESS next to jumpbox.f5lab.local
Select your RDP resolution.
The RDP client on your local host establishes a RDP connection to the Jump Host.
Login with the following credentials:
- User: f5lab\user1
- Password: user1
After successful logon the Chrome browser will auto launch opening the site https://portal.f5lab.local. This process usually takes 30 seconds after logon.
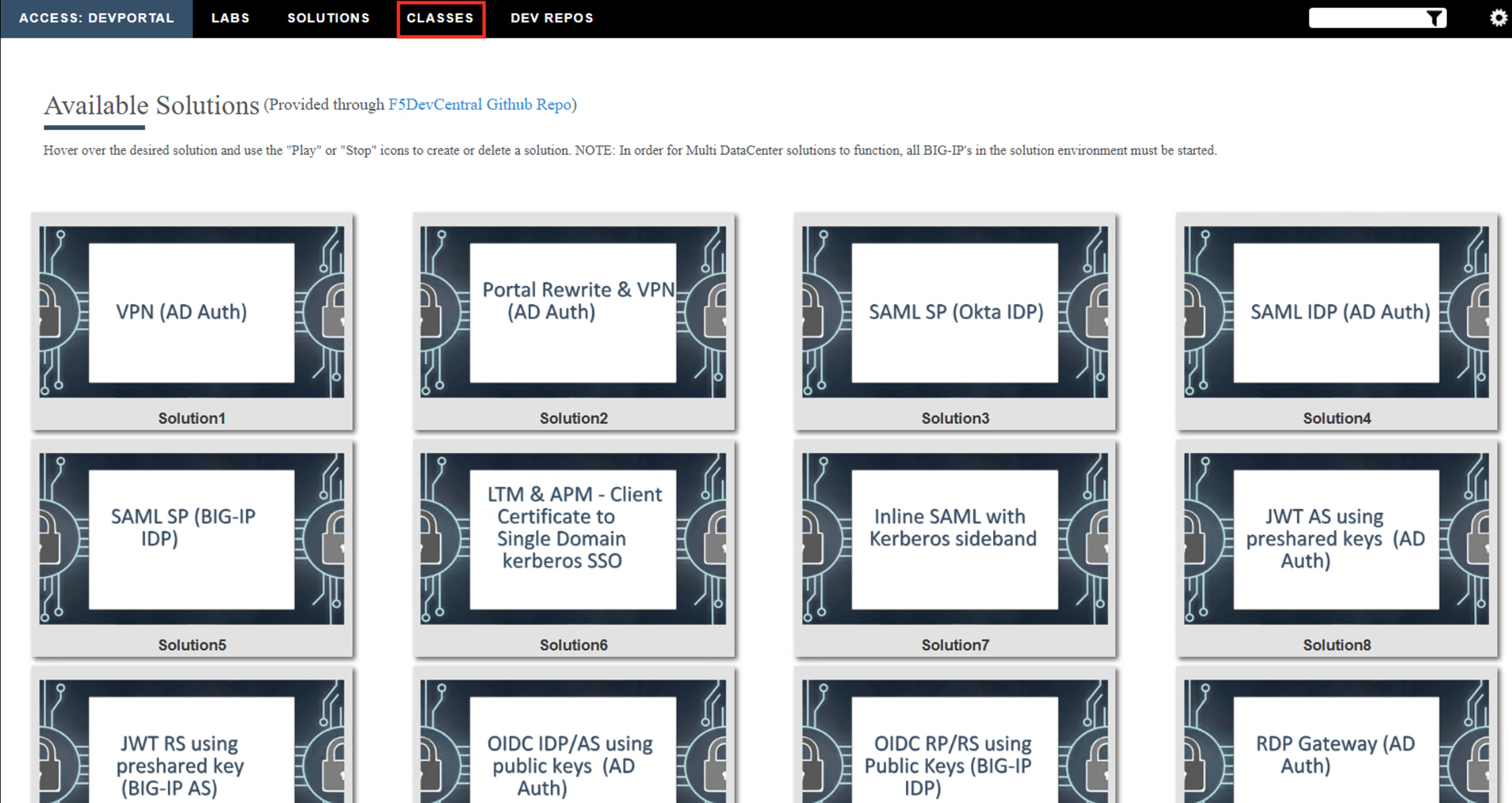
Click the Classes tab at the top of the page.
Scroll down the page until you see 202 - Federation on the left
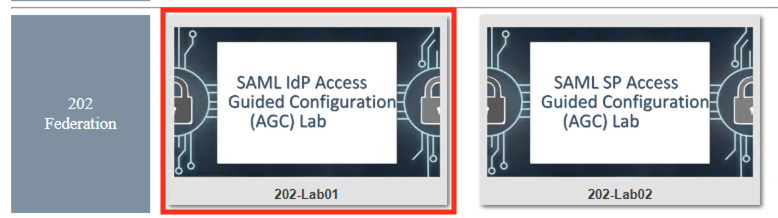
Hover over tile SAML IdP Access Guided Configuration(AGC) Lab. A start and stop icon should appear within the tile. Click the Play Button to start the automation to build the environment

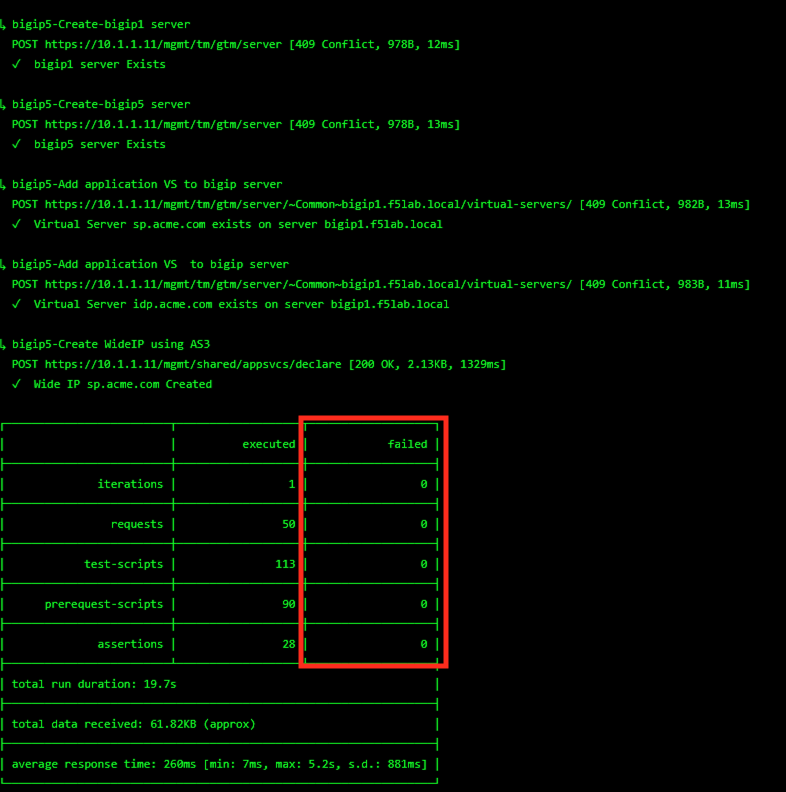
The screen should refresh displaying the progress of the automation within 30 seconds. Scroll to the bottom of the automation workflow to ensure all requests succeeded. If you you experience errors try running the automation a second time or open an issue on the Access Labs Repo.
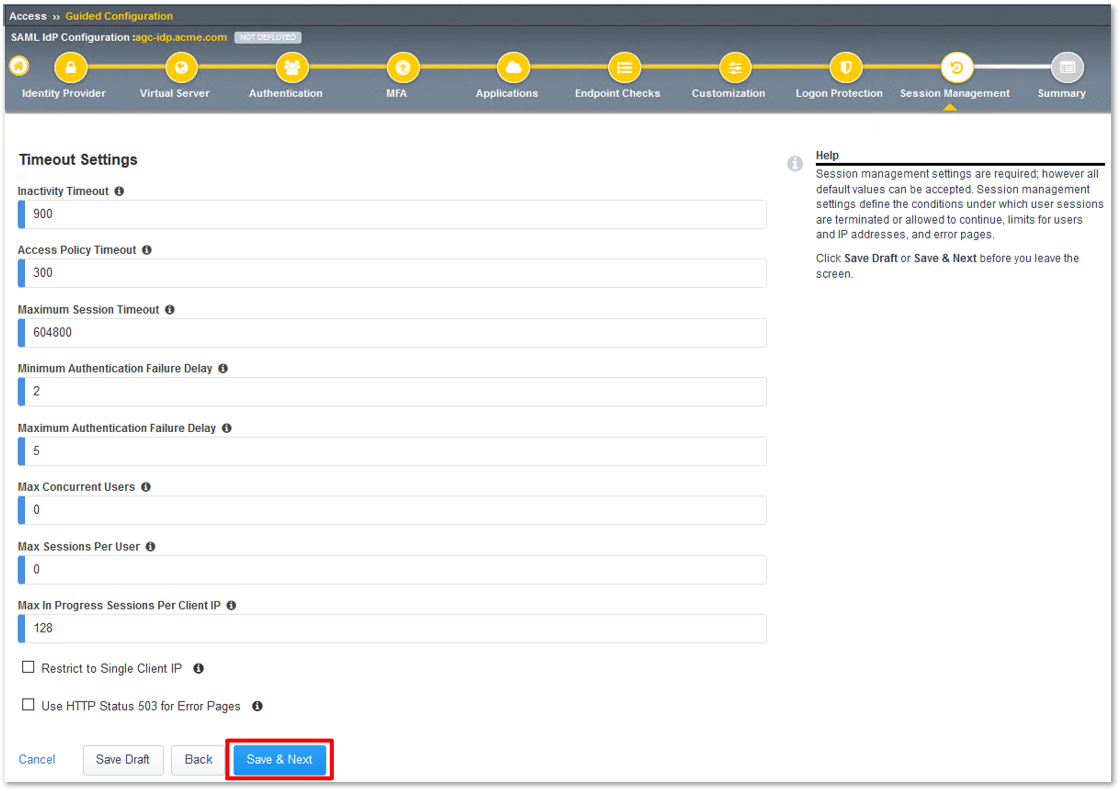
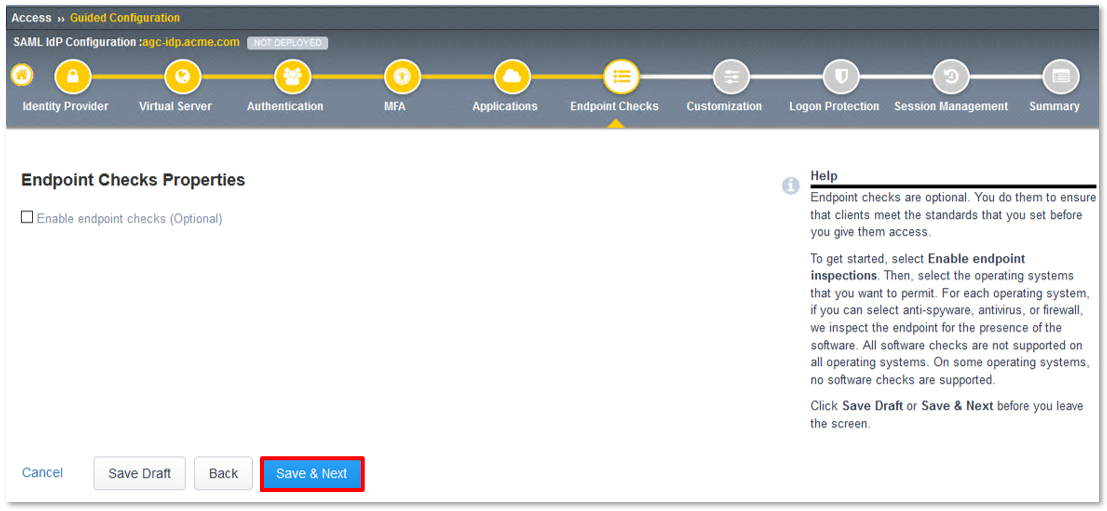
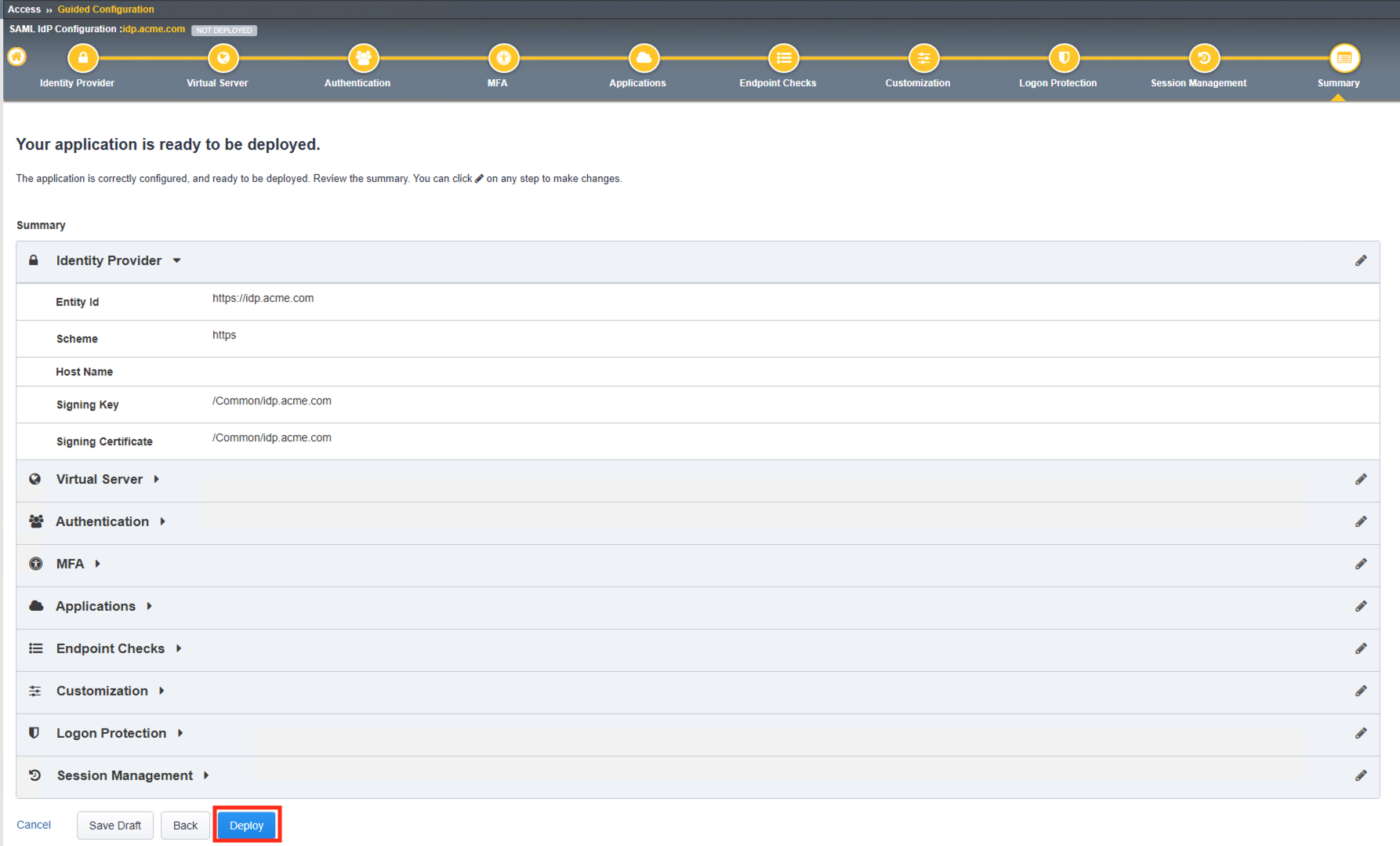
TASK 12: Review the Summary and Deploy
- Review the Summary, then scroll to the bottom of the window and click Deploy.
|
 |
- Once the application is deployed, scroll to the bottom and click Finish.
|
 |
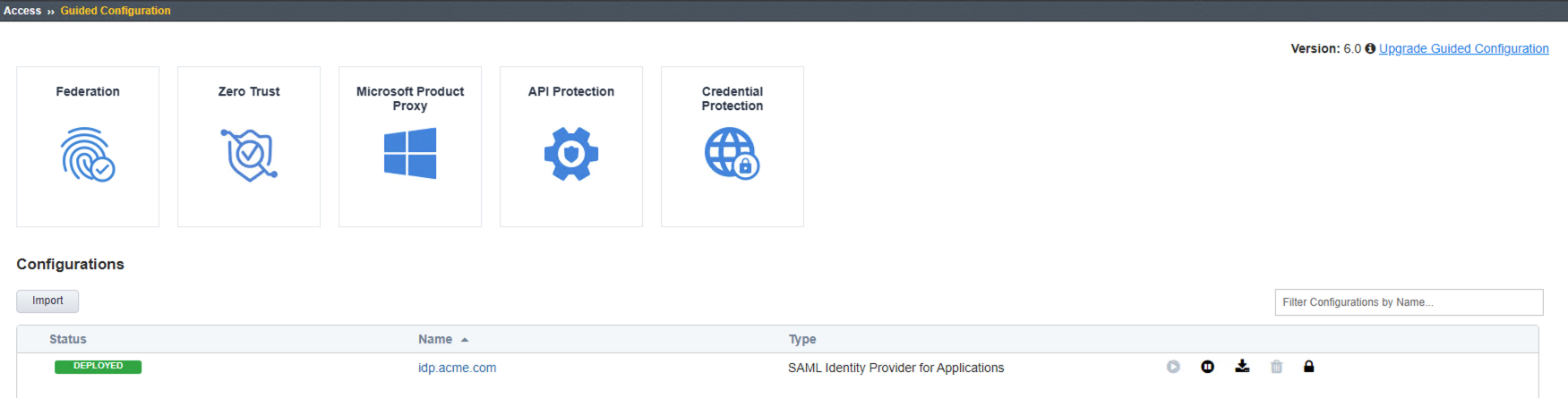
Review the Access Guided Confguration window, Status for idp.acme.com is
DEPLOYED.
|
 |
TASK: 13: Testing the SAML Identity Provider (IdP)
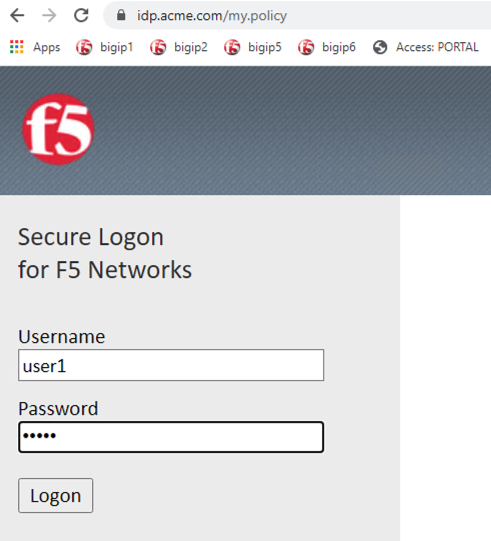
Open Firefox from the Jumphost desktop and navigate to https://idp.acme.com
Once the page loads, enter user1 for username and user1 for password in the
logon form and click the logon button.
Note: If you have issues, open Firefox in a New Private Window (Incognito/Safe Mode)
|
 |
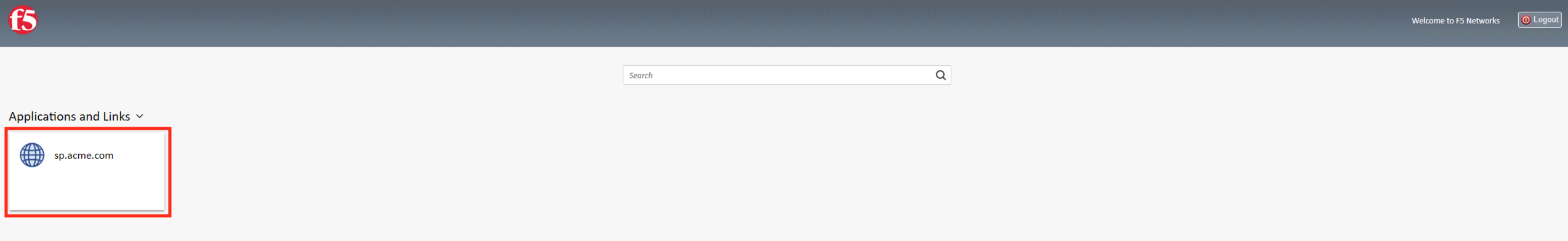
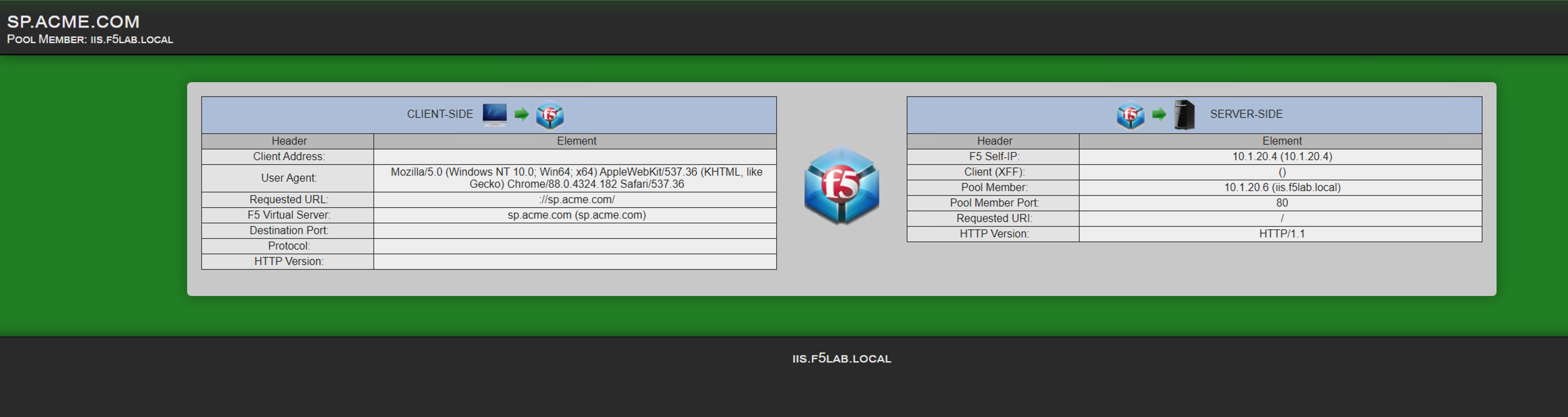
On the presented webtop, click the sp.acme.com link in the Applications and
Links section.
|
 |
The Application will now open if successfully configured. Close the
Application window, navigate to the F5 Dynamic Webtop tab/window and click Logout.
|
 |
TASK 14: Lab CleanUp
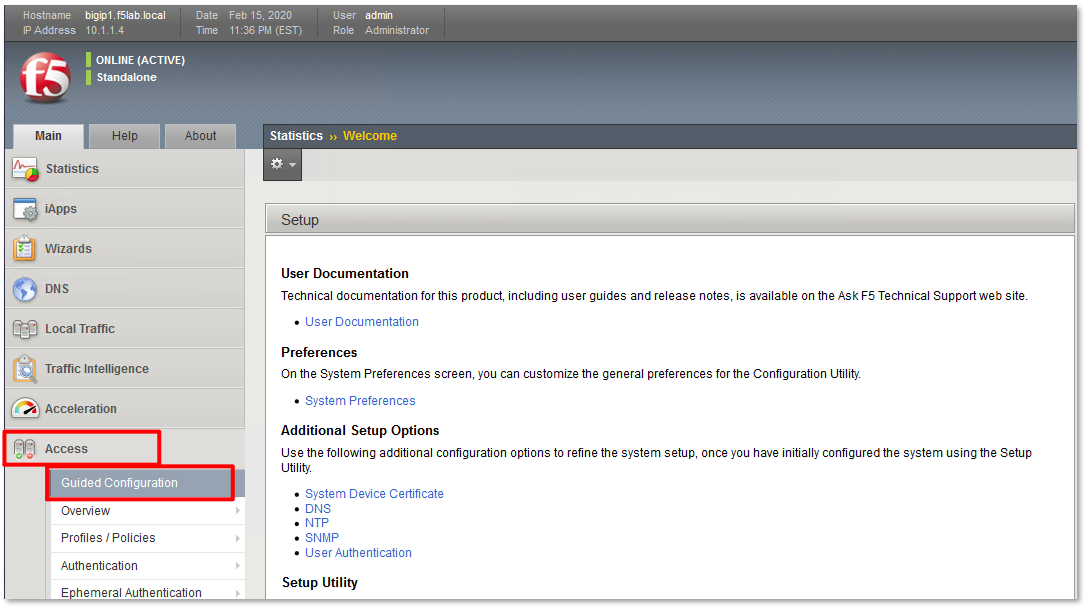
- Navigate to Access -> Guided Configuration in the left-hand menu.
|
 |
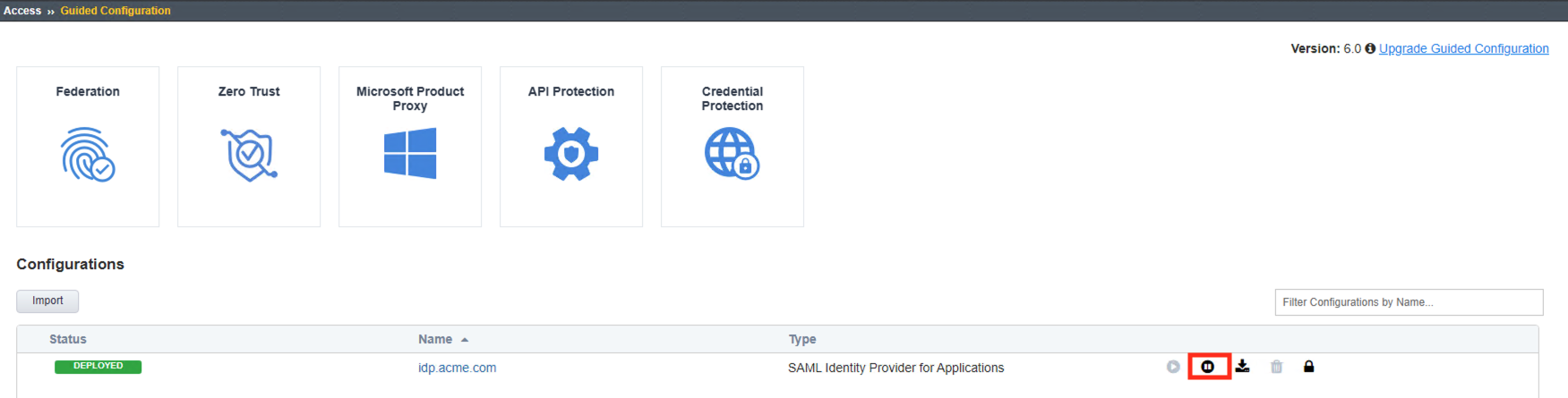
- Click the Undeploy button
|
 |
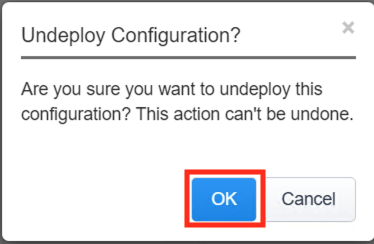
- Click OK when asked, “Are you sure you want to undeploy this configuration?”
|
 |
- Click the Delete button once the deployment is undeployed
|
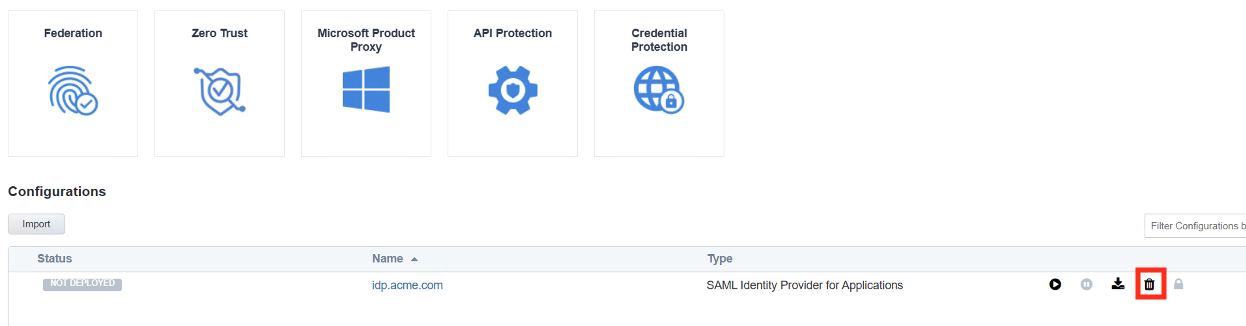 |
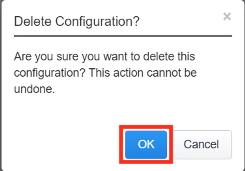
- Click OK when asked, “Are you sure you want to delete this configuration?”
|
 |
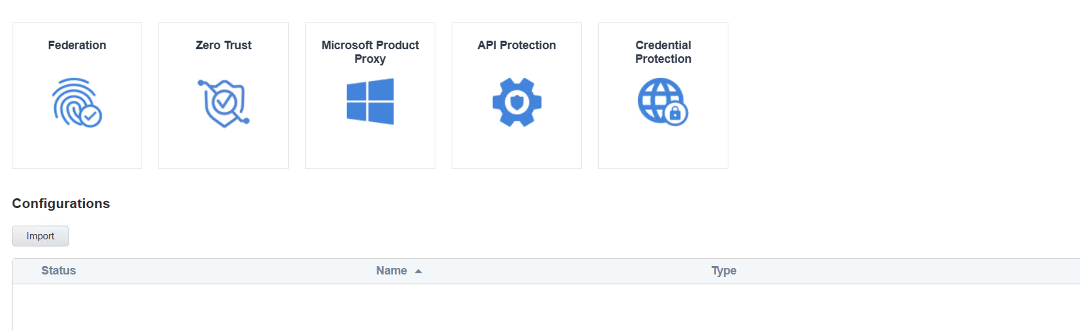
- The Configuration section should now be empty
|
 |
- Scroll down the page until you see 202 - Federation on the left
|
 |
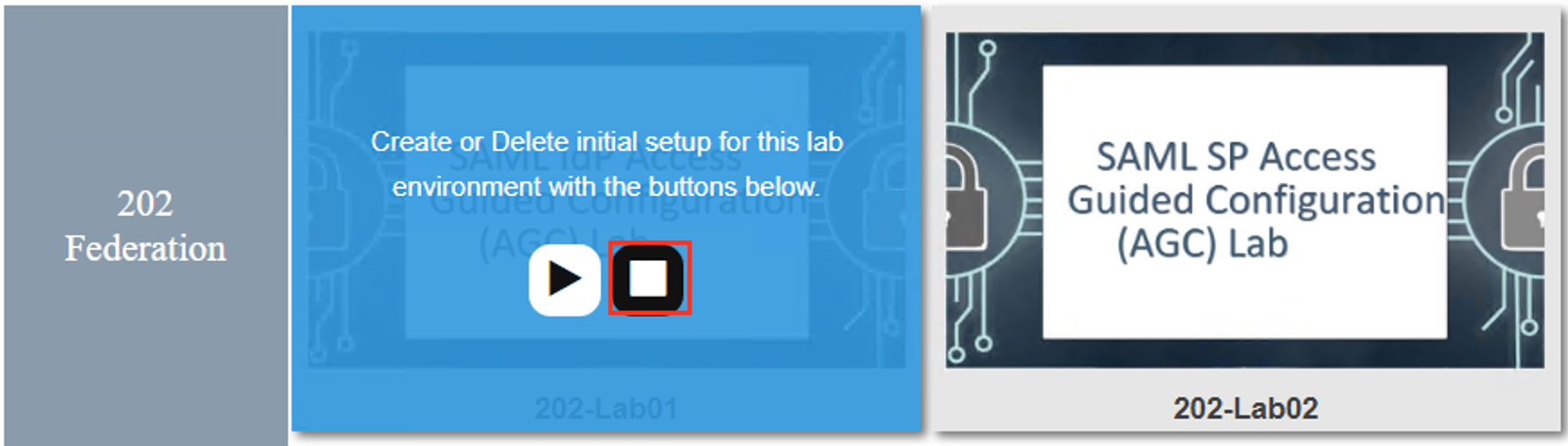
| 10. Hover over the tile SAML IdP Access Guided Configuration(AGC) Lab. A start and stop
icon should appear within the tile. Click the Stop Button to start the automation to
delete any prebuilt objects |
 |
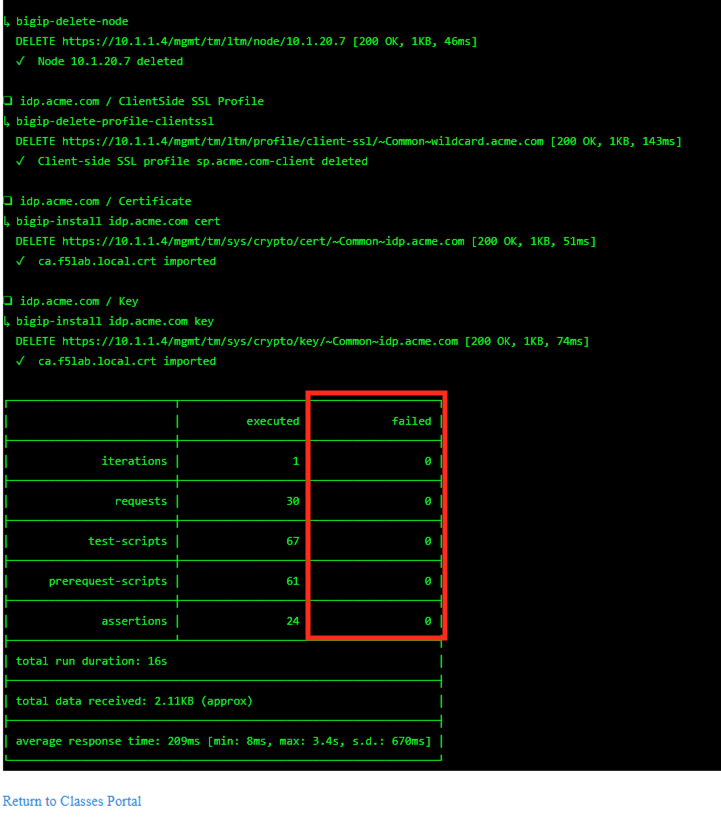
| 11. The screen should refresh displaying the progress of the automation within 30 seconds.
Scroll to the bottom of the automation workflow to ensure all requests succeeded.
If you you experience errors try running the automation a second time or open an issue on
the Access Labs Repo. |
 |
- This concludes Lab1.
|
 |