App Hairpinning¶
Overview¶
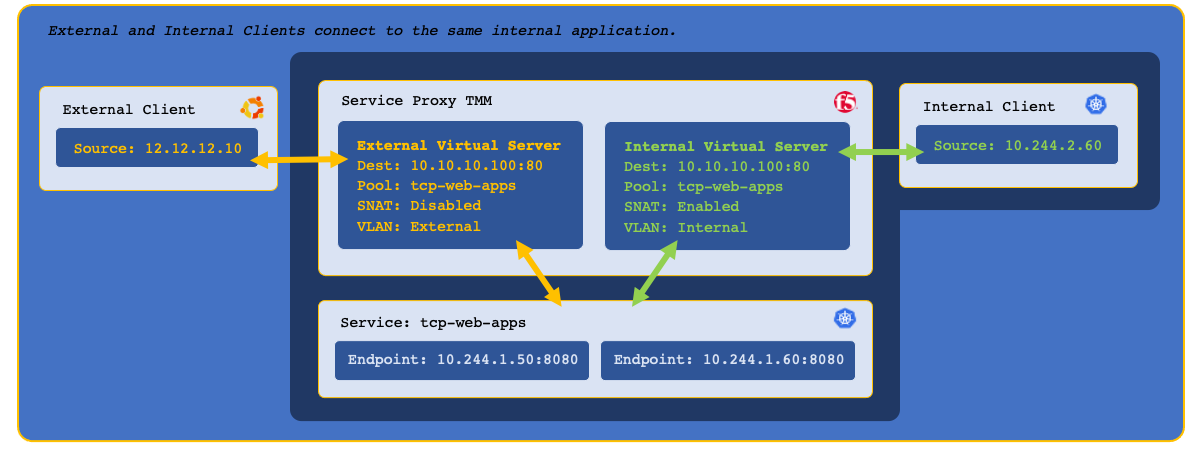
SPK Application Hairpinning enables applications to be exposed to both external client and internal Pods, using the same domain name or IP address. Application Hairpinning accomplishes this by installing two SPK CRs of the same type, for example the F5SPKIngressTCP, both targeting the same Kubernetes Service. Each SPK CR then enables traffic for the specific F5SPKVlan that client ingress traffic is expected. SNAT Automap is also applied internally to ensure Pods connect back through the Traffic Management Microkernel (TMM).
This document guides you through creating a simple Application Hairpinning configuration for a TCP based application.
CR Parameters¶
SPK CRs configure the Service Proxy Traffic Management Microkernel (TMM) to proxy and load balance application traffic using specific parameters. The CR parameter used in this document are described in the table below:
| Parameter | Description |
|---|---|
service.name |
Selects the Service object name for the internal applications (Pods), and creates a round-robin load balancing pool using the Service Endpoints. |
service.port |
Selects the Service object port value. |
spec.destinationAddress |
Creates an IPv4 virtual server address for ingress connections. |
spec.destinationPort |
Defines the service port for inbound connections. |
spec.snat |
Translate the source IP address of ingress packets to TMM's self IP addresses. Use SRC_TRANS_AUTOMAP to enable, and SRC_TRANS_NONE to disable (default). |
spec.vlans.vlanList |
Specifies a list of F5SPKVlan CRs to listen for ingress traffic, using the CR's metadata.name. The list can also be disabled using disableListedVlans. |
spec.vlans.category |
Specifies an F5SPKVlan CR category to listen for ingress traffic. The category can also be disabled using disableListedVlans. |
spec.vlans.disableListedVlans |
Disables, or denies traffic specified with the vlanList or category parameters: true or false (default). |
Example deployment:
Installation¶
You can select either the VLAN lists or Categories installation methods to segment traffic based on the internal and external facing VLANs.
VLAN Lists¶
Prior to configuring the Service Proxy TMM for application hairpinning, a few configuration details must be obtained from the application Service Object, and the installed F5SPKVlan CRs. Use the following steps to obtain the object configuration data, and configure Service Proxy TMM for application hairpinning using VLAN lists:
Switch to the application Project:
oc project <project>
In this example, the application is in the tcp-web-apps Project:
oc project tcp-web-apps
Obtain the appication Service object NAME and PORT. These will be used to configure the CR’s
service.specandservice.portparameters:oc get service
In this example, the Service object NAME is tcp-web-app and the PORT is 80:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) tcp-web-app NodePort 10.99.99.99 <none> 80:30714/TCP
Obtain the
metadata.nameparameter values of currently installed F5SPKVlans. These will be used to configure the F5SPKIngressTCP CRspec.vlans.vlanListparameters:oc get f5-spk-vlans
In this example, the two F5SPKVlan
metadata.namevalues are; vlan-external and vlan-internal:NAME vlan-external vlan-internal
Copy the external CR into a YAML file:
apiVersion: "ingresstcp.k8s.f5net.com/v1" kind: F5SPKIngressTCP metadata: namespace: tcp-web-apps name: ext-tcp-cr service: name: tcp-web-app port: 80 spec: destinationAddress: "10.20.100.100" destinationPort: 80 snat: "SRC_TRANS_NONE" vlans: vlanList: - vlan-external
Copy the internal CR into a YAML file:
Note: The internal CR sets the
snatparameter toSNAT_TRANS_AUTOMAP, ensuring the internal Pods connect back through TMM:apiVersion: "ingresstcp.k8s.f5net.com/v1" kind: F5SPKIngressTCP metadata: namespace: tcp-web-apps name: int-tcp-cr service: name: tcp-web-app port: 80 spec: destinationAddress: "10.20.100.100" destinationPort: 80 snat: "SRC_TRANS_AUTOMAP" vlans: vlanList: - vlan-internal
Install the F5SPKIngressTCP CRs:
oc apply -f spk-ext-tcp.yaml
oc apply -f spk-int-tcp.yaml
Verify the CR objects have been installed:
oc get f5-spk-ingresstcp
NAME AGE ext-tcp-cr 1m int-tcp-cr 1m
Categories¶
Prior to configuring the Service Proxy TMM for application hairpinning, a few configuration details must be obtained from the application Service Object, and the installed F5SPKVlan CRs. Use the following steps to obtain the object configuration data, and configure Service Proxy TMM for application hairpinning using Categories:
Switch to the application Project:
oc project <project>
In this example, the application is in the tcp-web-apps Project:
oc project tcp-web-apps
Obtain the appication Service object NAME and PORT. These will be used to configure the CR’s
service.specandservice.portparameters:oc get service
In this example, the Service object NAME is tcp-web-app and the PORT is 80:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) tcp-web-app NodePort 10.99.99.99 <none> 80:30714/TCP
Obtain the F5SPKVlan
spec.categoryparameter values used to configure the F5SPKIngressTCP CRspec.vlans.categoryparameters:In this example, the F5SPKVlans are in the spk-ingress Project:
oc describe f5-spk-vlan -n spk-ingress | grep -E '^Name:|Category:'
In this example, the vlan-external VLAN
categoryvalue is external, and the vlan-internal VLANcategoryvalue is internal:Name: vlan-external Category: external Name: vlan-internal Category: internal
Copy the external CR into a YAML file:
apiVersion: "ingresstcp.k8s.f5net.com/v1" kind: F5SPKIngressTCP metadata: namespace: tcp-web-apps name: ext-tcp-cr service: name: tcp-web-app port: 80 spec: destinationAddress: "10.20.100.100" destinationPort: 80 snat: "SRC_TRANS_NONE" vlans: category: external
Copy the internal CR into a YAML file:
Note: The internal CR sets the
snatparameter toSNAT_TRANS_AUTOMAP, ensuring the internal Pods connect back through TMM:apiVersion: "ingresstcp.k8s.f5net.com/v1" kind: F5SPKIngressTCP metadata: namespace: tcp-web-apps name: int-tcp-cr service: name: tcp-web-app port: 80 spec: destinationAddress: "10.20.100.100" destinationPort: 80 snat: "SRC_TRANS_AUTOMAP" vlans: category: internal
Install the F5SPKIngressTCP CRs:
oc apply -f spk-ext-tcp.yaml
oc apply -f spk-int-tcp.yaml
Verify the CR objects have been installed:
oc get f5-spk-ingresstcp
NAME AGE ext-tcp-cr 1m int-tcp-cr 1m
Connection Statistics¶
The external and internal clients should now be able to connect to the application through their respective F5SPKVlans. After connecting to the application from the external and internal clients, Use the steps below to verify the connection statistics:
 Note: You must have the Debug Sidecar enabled to view connection statistics.
Note: You must have the Debug Sidecar enabled to view connection statistics.
Switch to the Ingress Controller Project:
oc project <project>
In this example, the Ingress Controller is in the spk-ingress Project:
oc project spk-ingress
Log in to the TMM Debug Sidecar:
oc exec -it deploy/f5-tmm -c debug -- bash
View the TMM virtual server connection statistics:
tmctl -d blade virtual_server_stat -s name,serverside.tot_conns
In this example, the external virtual server has 200 connections and the internal virtual server has 22 connections:
name serverside.tot_conns -------------------------------------- -------------------- tcp-web-apps-ext-tcp-cr-virtual-server 200 tcp-web-apps-int-tcp-cr-virtual-server 22
View the TMM pool member connection statistics:
tmctl -d blade pool_member_stat -s pool_name,serverside.tot_conns
In this example, the external pool members have approximately 67 connections each, and the internal pool members have approximately 7 connections each:
pool_name serverside.tot_conns ---------------------------- -------------------- tcp-web-apps-ext-tcp-cr-pool 67 tcp-web-apps-ext-tcp-cr-pool 67 tcp-web-apps-ext-tcp-cr-pool 66 tcp-web-apps-int-tcp-cr-pool 8 tcp-web-apps-int-tcp-cr-pool 7 tcp-web-apps-int-tcp-cr-pool 7
Feedback¶
Provide feedback to improve this document by emailing spkdocs@f5.com.