Solution10 Policy¶
Policy Walk-Through¶
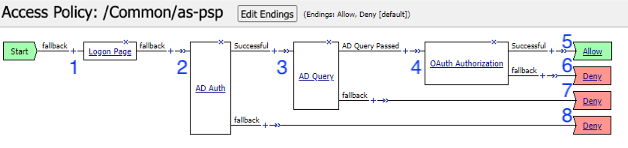
In this policy a user enters their credentials in the logon page agent.
Those credentials are collected, stored as the default system session variables of session.logon.last.username and session.logon.last.password.
The AD Auth Agent validates the username and password session variables against the configured AD Domain Controller.
If AD Auth is successful, an AD Query is performed to retrieve additional AD Attributes
If AD Query is successful, an OAuth Authorization is performed granting the user access to a token.
The user is granted access via the Allow Terminal
If unsuccessful, the user proceeds down the fallback branch and denied access via the Deny Terminal
If unsuccessful, the user proceeds down the fallback branch and denied access via the Deny Terminal
If unsuccessful, the user proceeds down the fallback branch and denied access via the Deny Terminal
Policy Agent Configuration¶
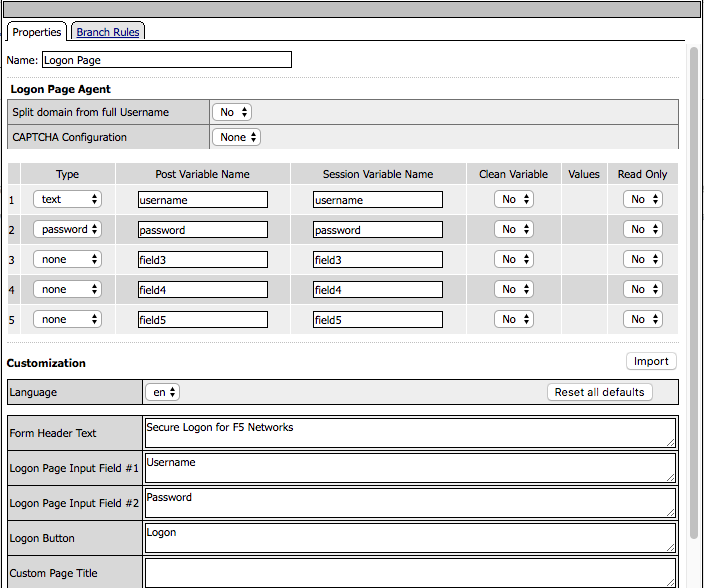
The Logon Page contains only the default setting
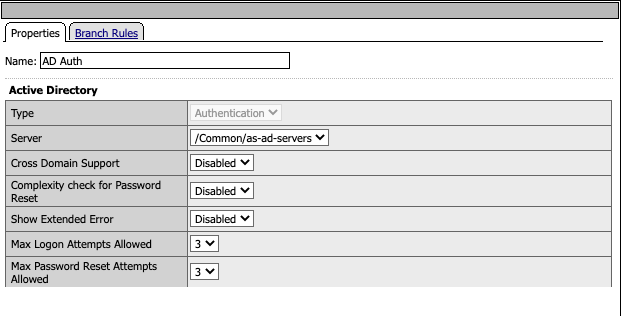
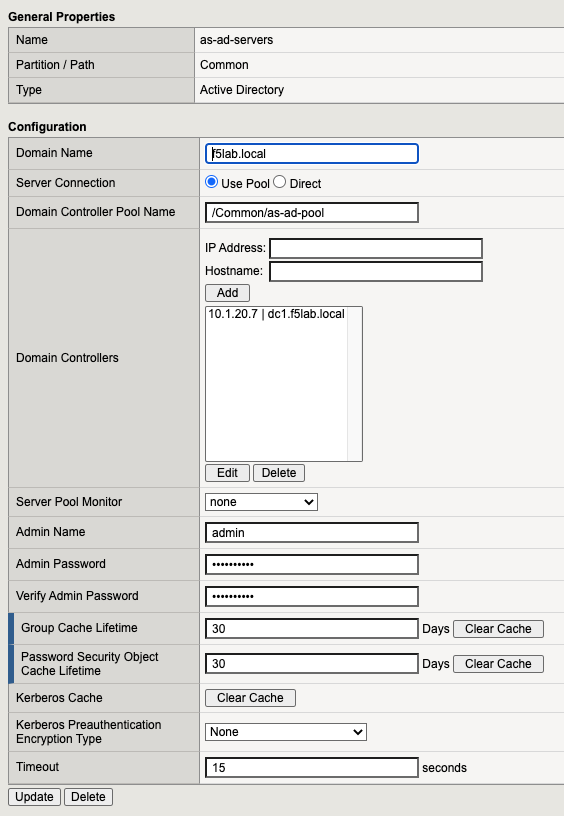
The AD Auth Agent uses a defined the AD AAA Servers that user will be authenticated against. All Setting are the default.
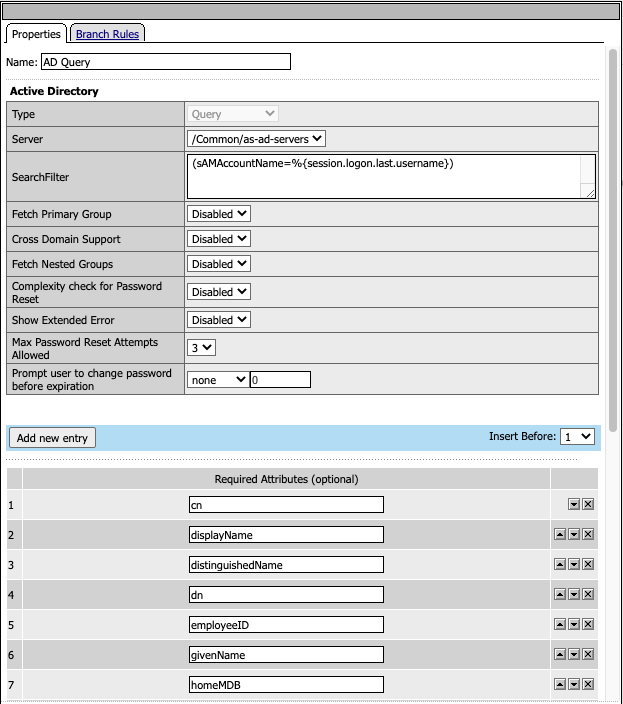
The AD Query Agent uses a defined the AD Servers that user will be for queries against. Additional Attributes we added.
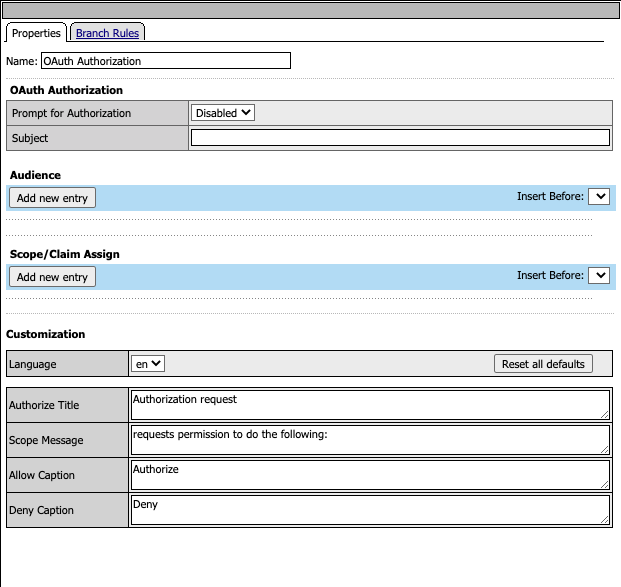
The OAuth Authorization Agent is used to define the Audience and Scope. All Setting are the default.
Profile Settings¶
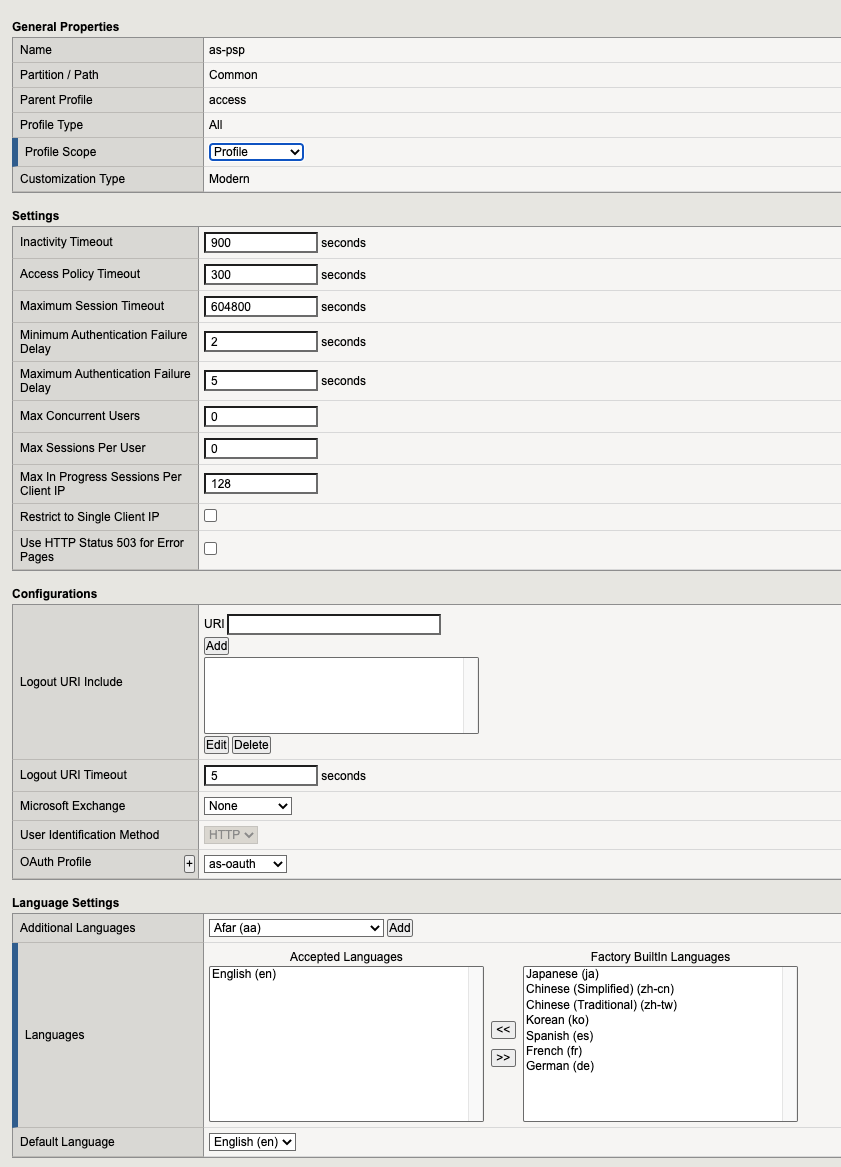
The OAuth Profile used for issuing the JWT token is assigned under the Configuration section.
Supporting APM Objects¶
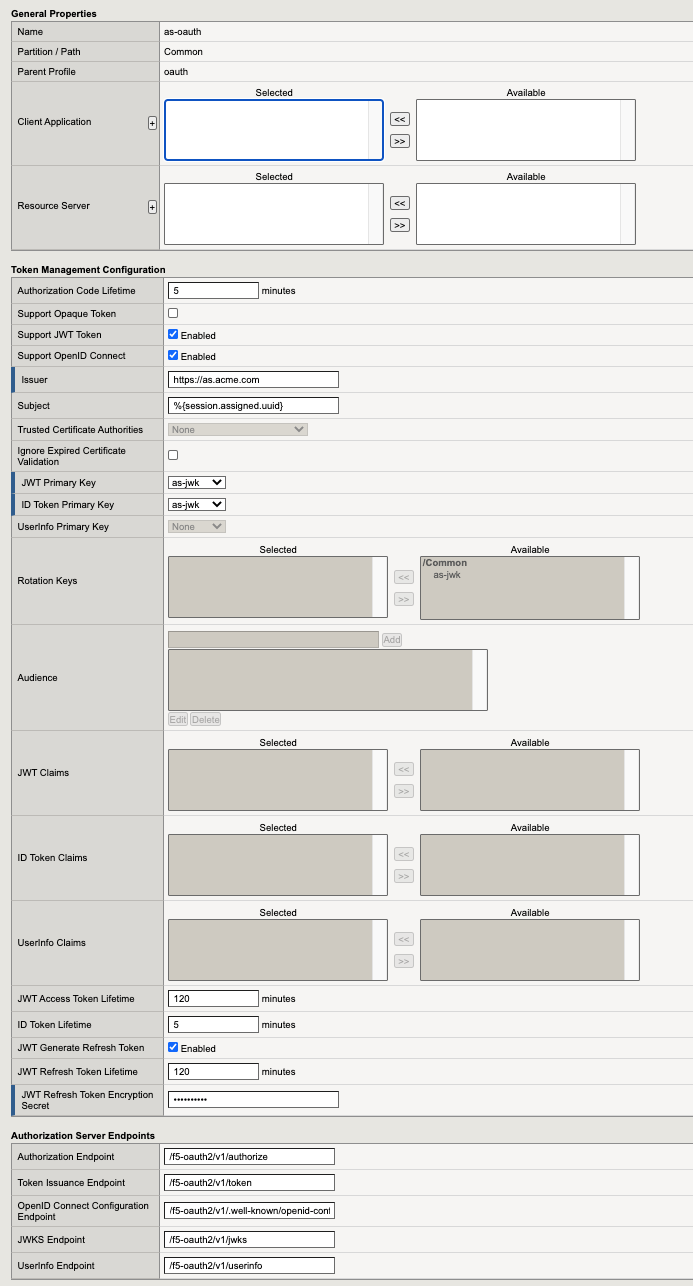
The settings below define all the components of the OAuth Profile
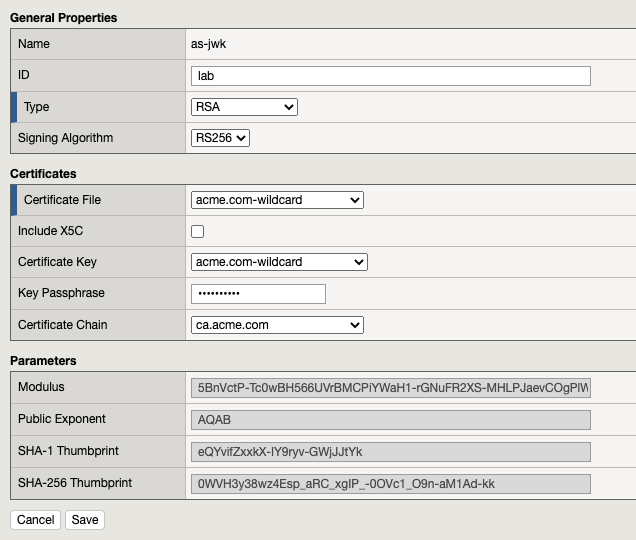
JWT Key¶
AAA AD Servers¶
The Policy from a user’s perspective¶
If the user attempts to access https://as.acme.com they will be redirected to a logon page. This solution is designed to be integrated with other solutions in the UDF deployment that require an Authorization Server.