Solution14 Policy¶
Per-Session Policy Walk-Through¶
This solution requires creation of two access policies. A default allow per-session policy and a per-request policy using two subroutines.
This initial access policy (default allow) is a per-session policy to populate required session variable name and values.
Per-Request Policy Walk-Through¶
This per-request access policy accepts users request and redirect them to one of the two SAML Auth Subroutines configured for sp.acme.com or sp1.acme.com.
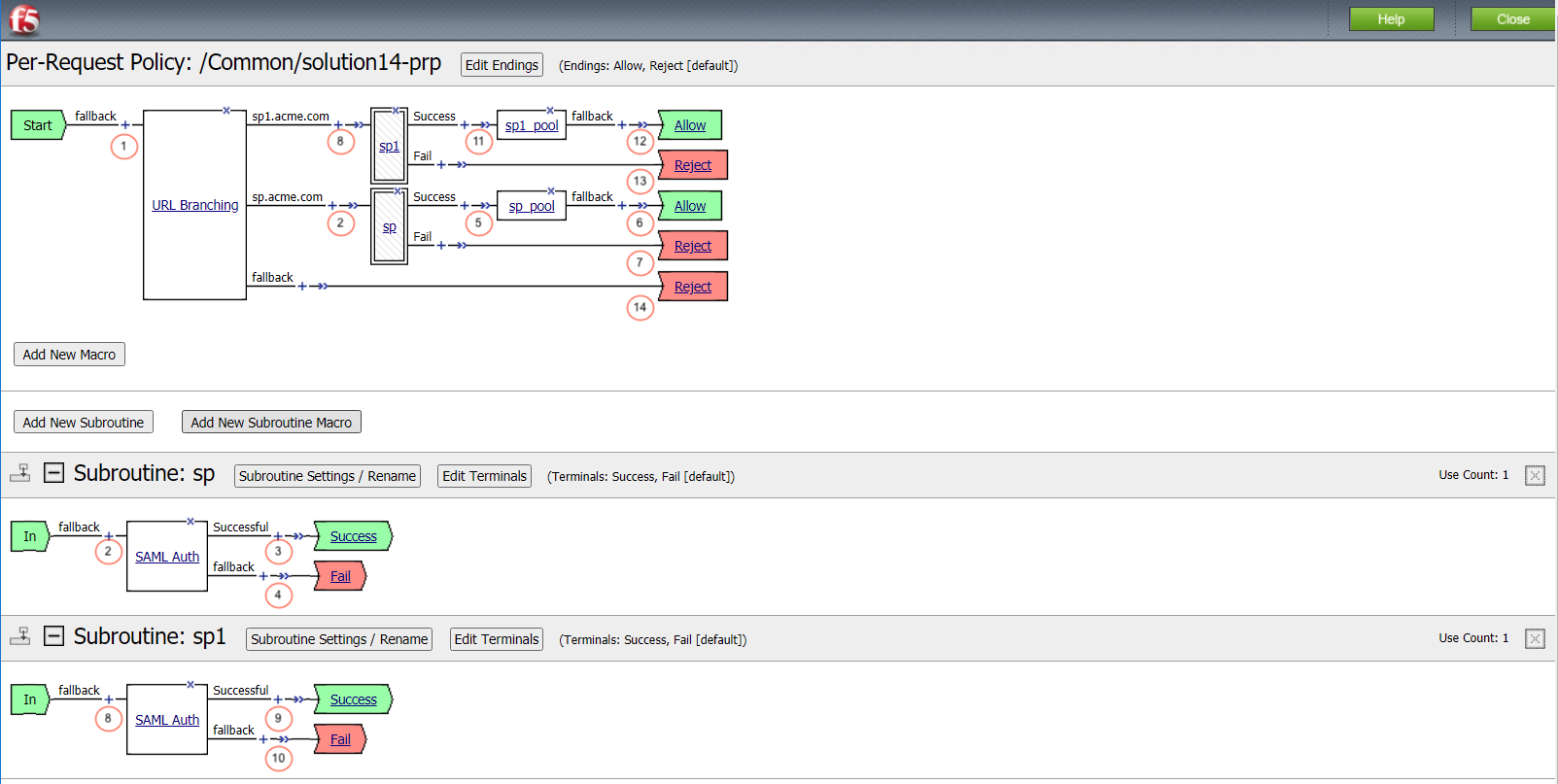
Per-Request Policies are an extension of a per-session policy by enabling fine-grain control over a users session on request by request basis.
This URL Branching action is used to interrogate the service URL and vector it to the appropriate SAML-SP Subroutine.
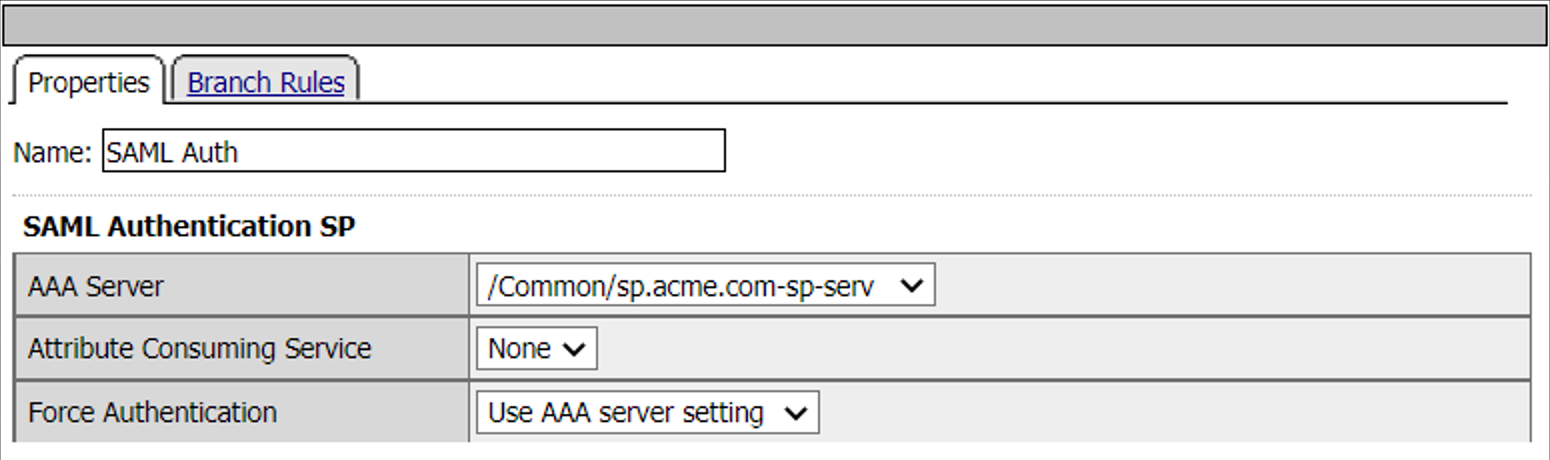
When a user is directed to a SAML Auth agent they are redirected to the IDP selected by the SP Service(sp.acme.com).
Upon successful authentication at the IDP, the user is redirected back to the SP. The SP service consumes the Assertion. The user is directed to the Success Terminal.
Upon unsuccessful authentication, the user proceeds down the fallback branch and directed to the Fail Terminal.
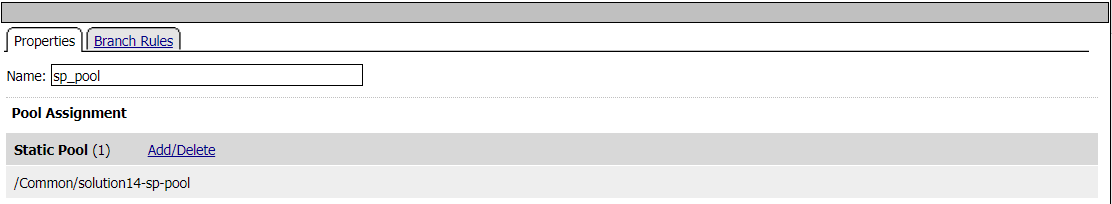
Pool sp.acme.com-pool is assigned to the request for load balancing. Traitional LTM load balancing rules still apply.
The user is granted access via the Allow Terminal.
User credentials failed the selected authentication and is directed to the Reject Terminal.
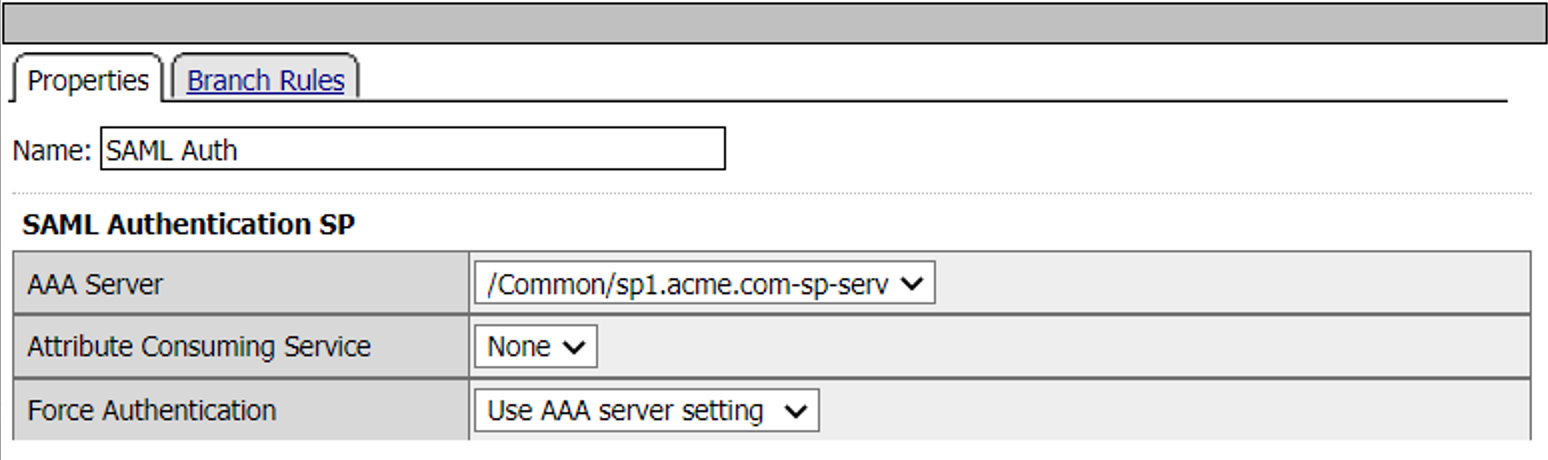
When a user is directed to a SAML Auth agent they are redirected to the IDP selected by the SP Service(sp1.acme.com).
Upon successful authentication at the IDP, the user is redirected back to the SP. The SP service consumes the Assertion. The user is directed to the Success Terminal.
Upon unsuccessful authentication, the user proceeds down the fallback branch and directed to the Fail Terminal.
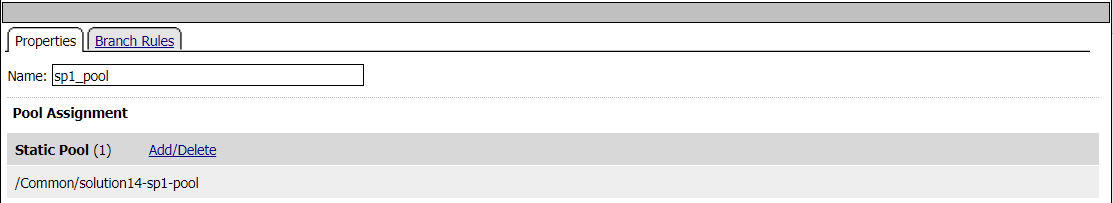
Pool sp1.acme.com-pool is assigned to the request for load balancing. Traitional LTM load balancing rules still apply.
The user is granted access via the Allow Terminal.
User credentials failed the selected authentication and is directed to the Reject Terminal.
Users request did not meet either of Subroutine URI requirements.
Policy Agent Configuration¶
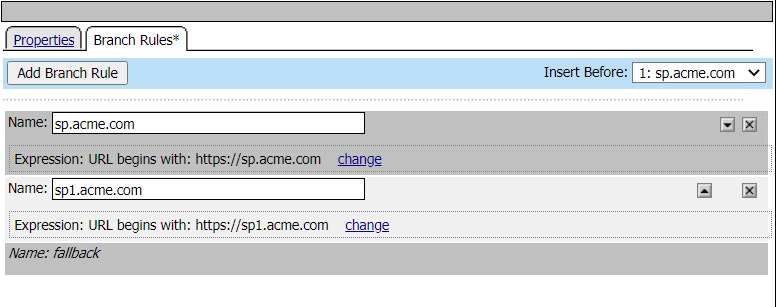
URL Branch Rules
SAML Auth Agent - SP
Pool Assign - sp_pool
SAML Auth Agent - SP1
Pool Assign - sp1_pool
Profile Settings¶
All profile settings are left the defaults
Supporting APM Objects¶
SAML Service Provider List¶
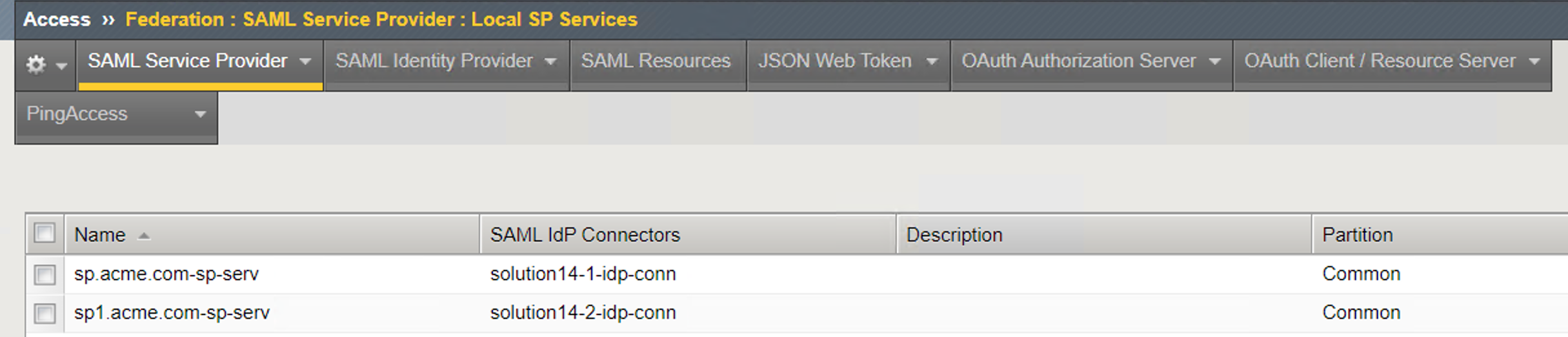
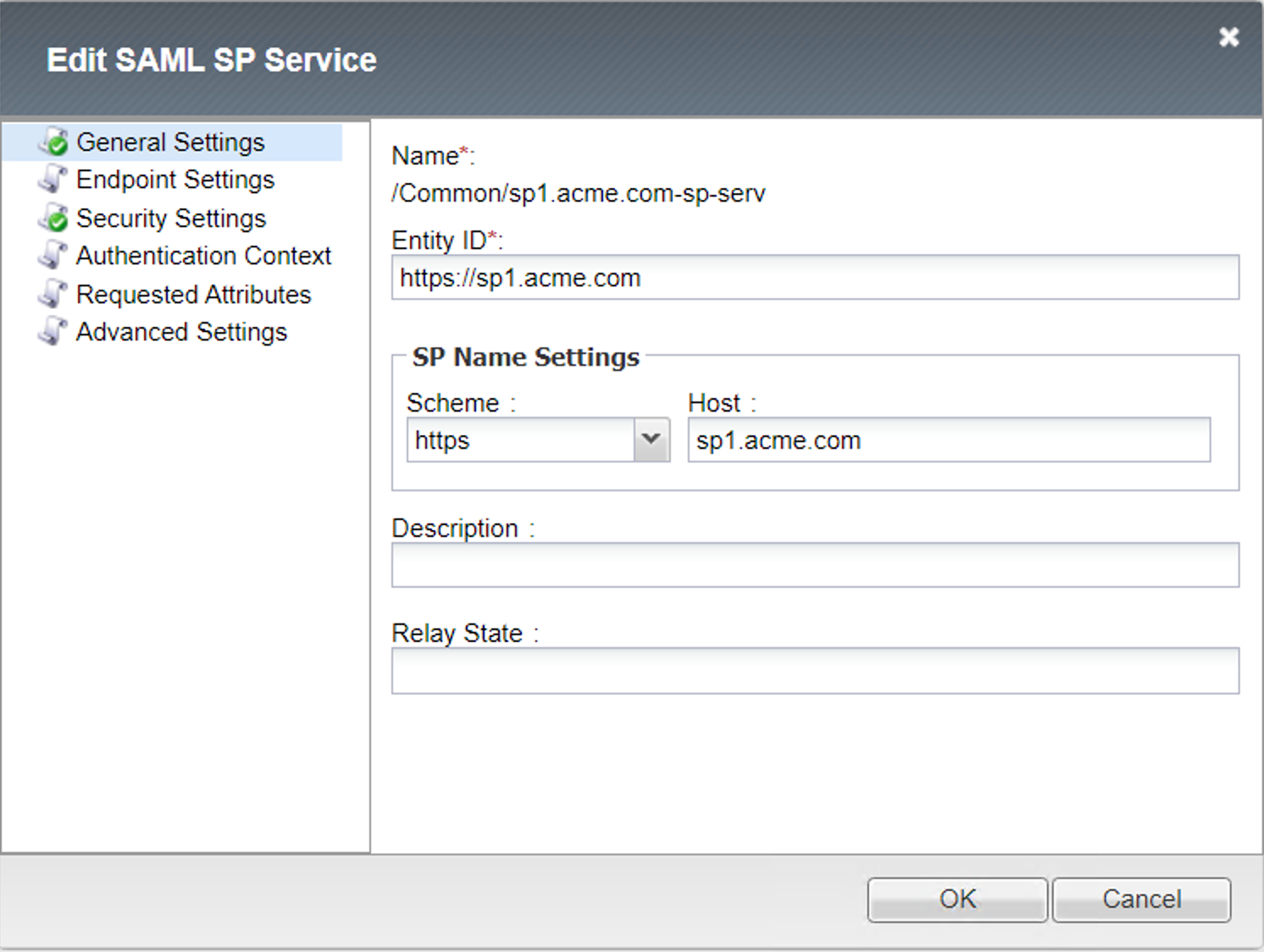
SP Service (sp.acme.com-serv)¶
General Settings
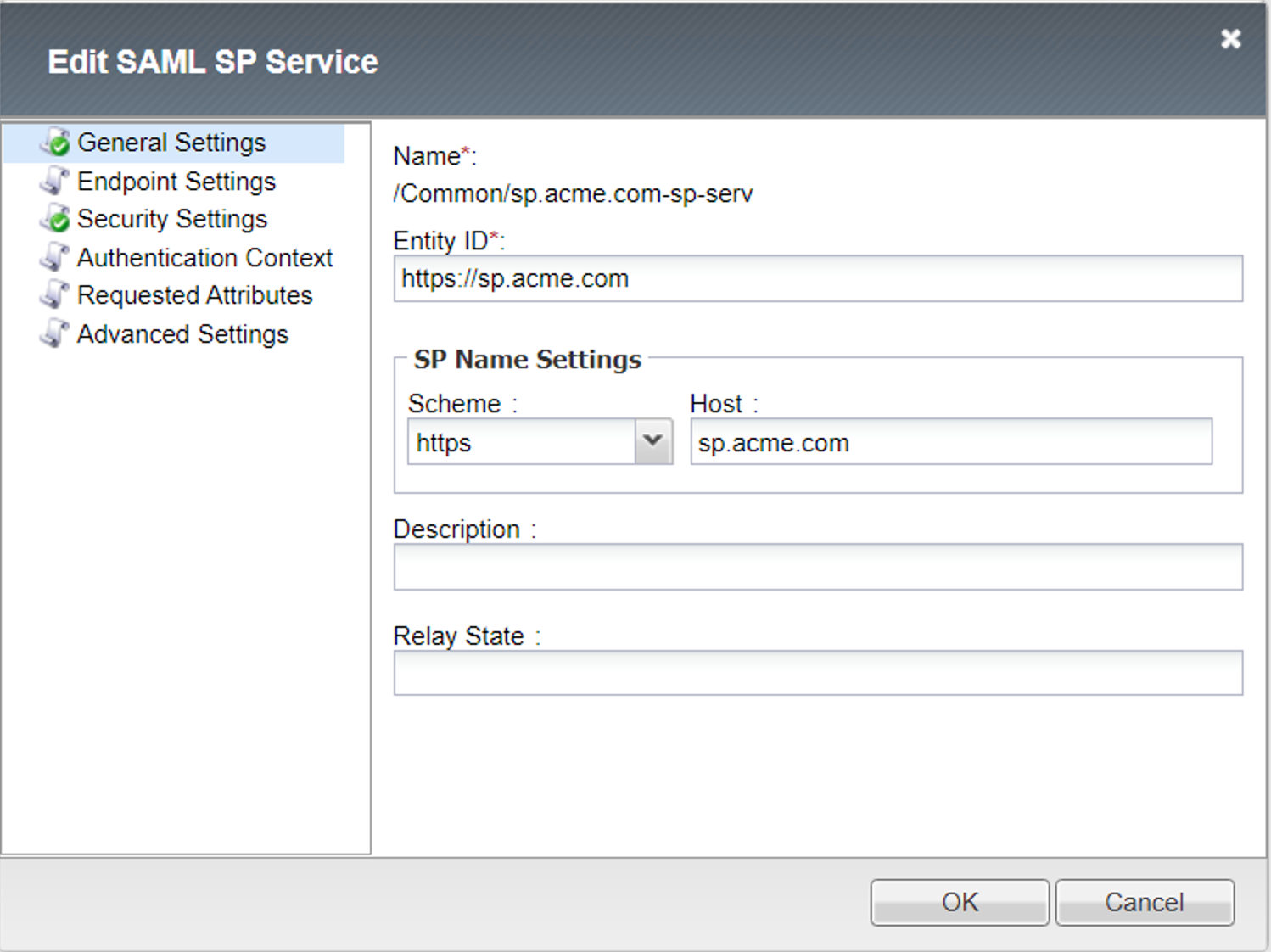
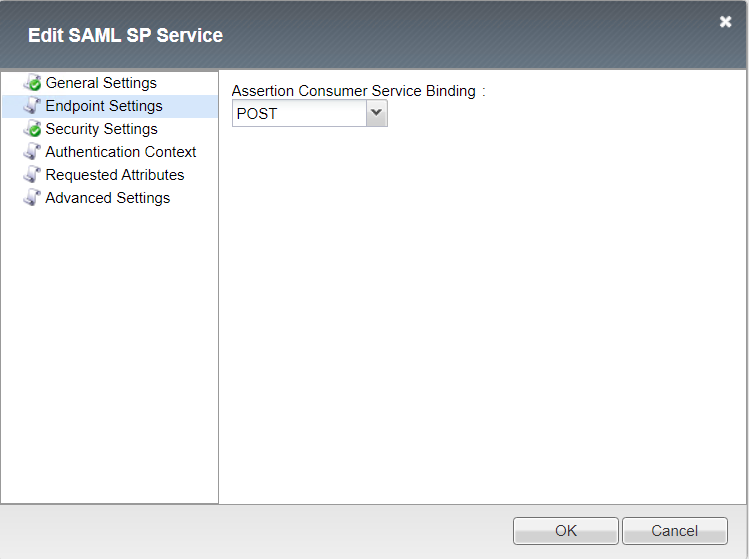
Endpoint Settings
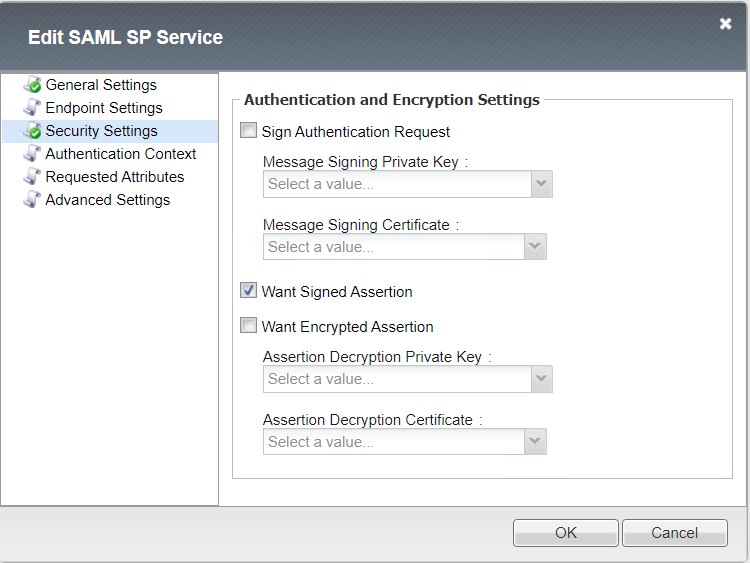
Security Settings
Authentication Context
Advanced Settings
SP Service (sp1.acme.com-serv)¶
General Settings
Endpoint Settings
Security Settings
Authentication Context
Advanced Settings
IdP Connector List¶
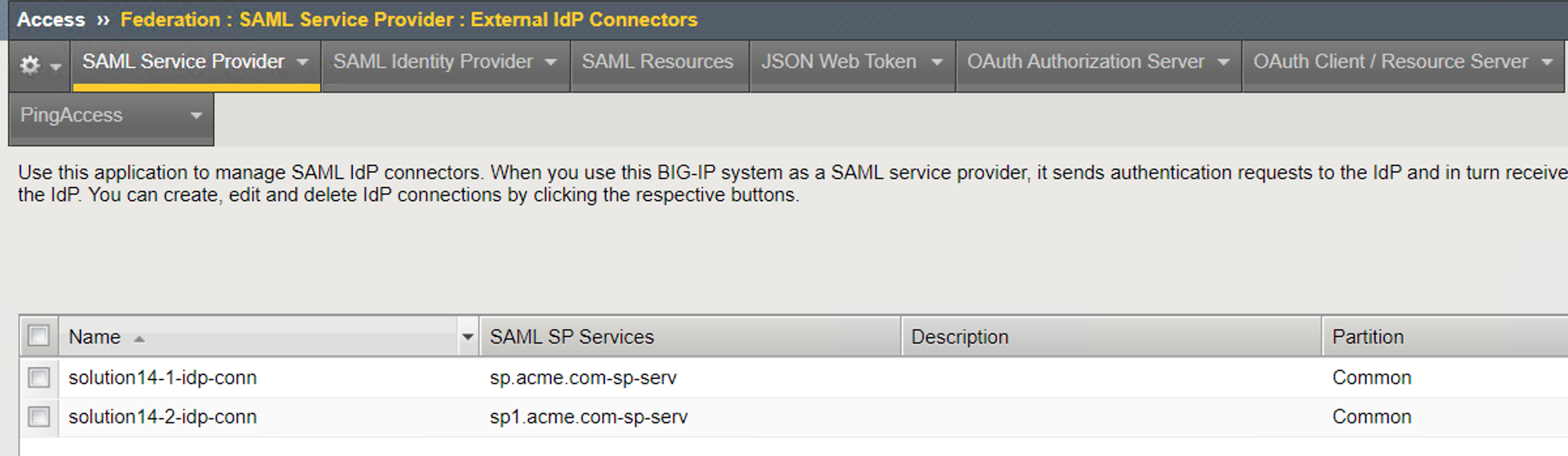
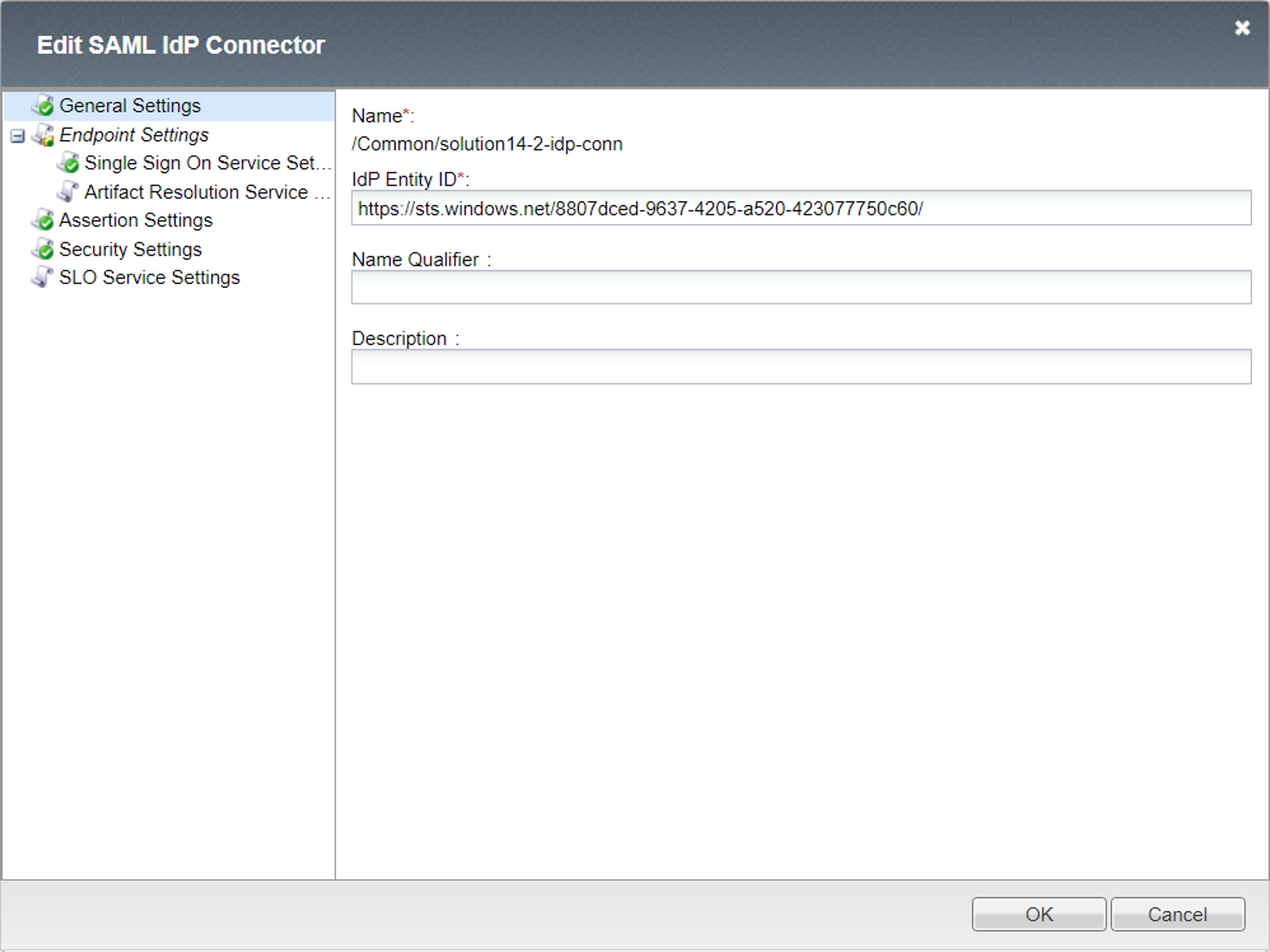
IdP Connector (solution14-1-idp-conn)¶
General settings
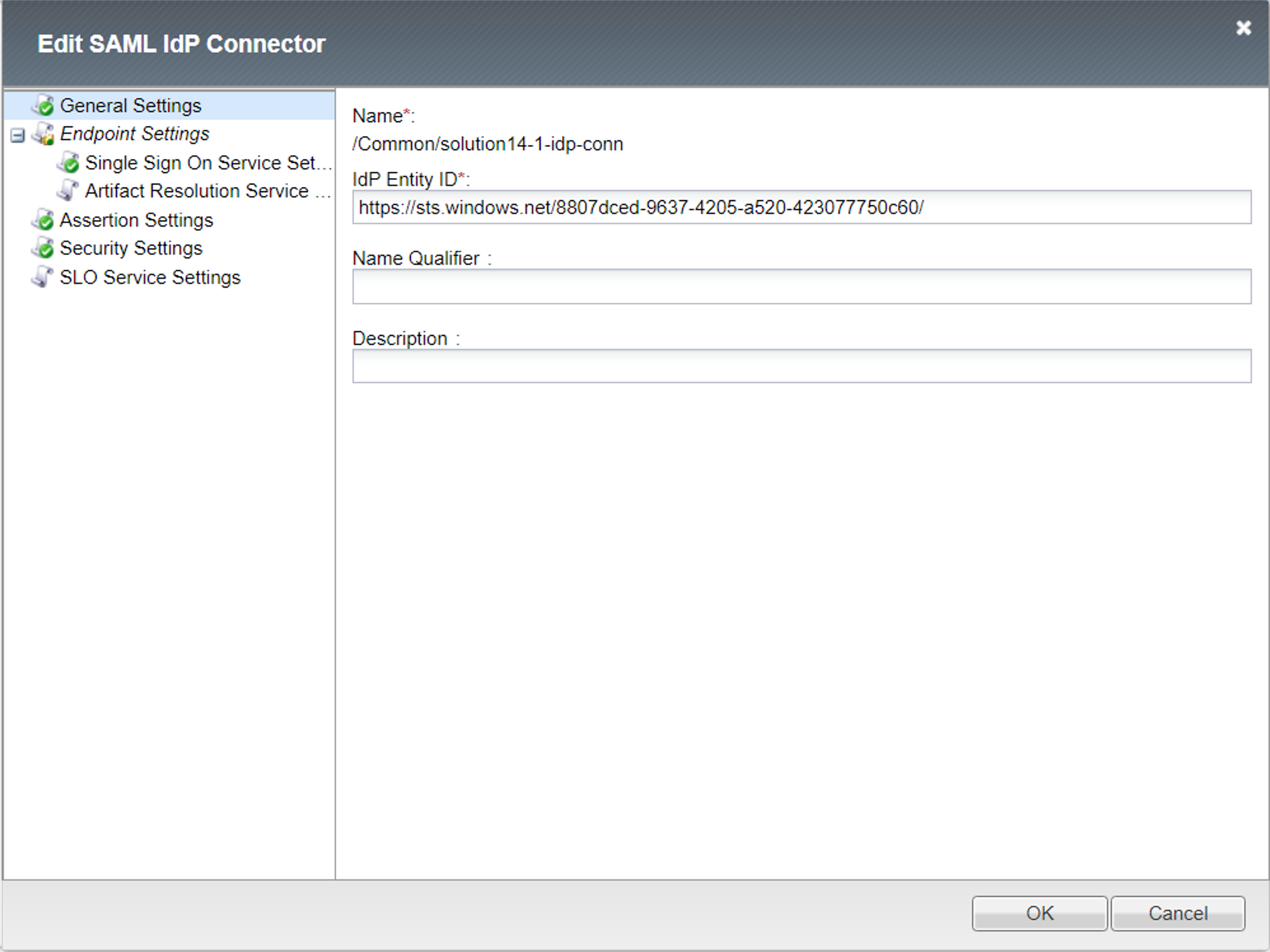
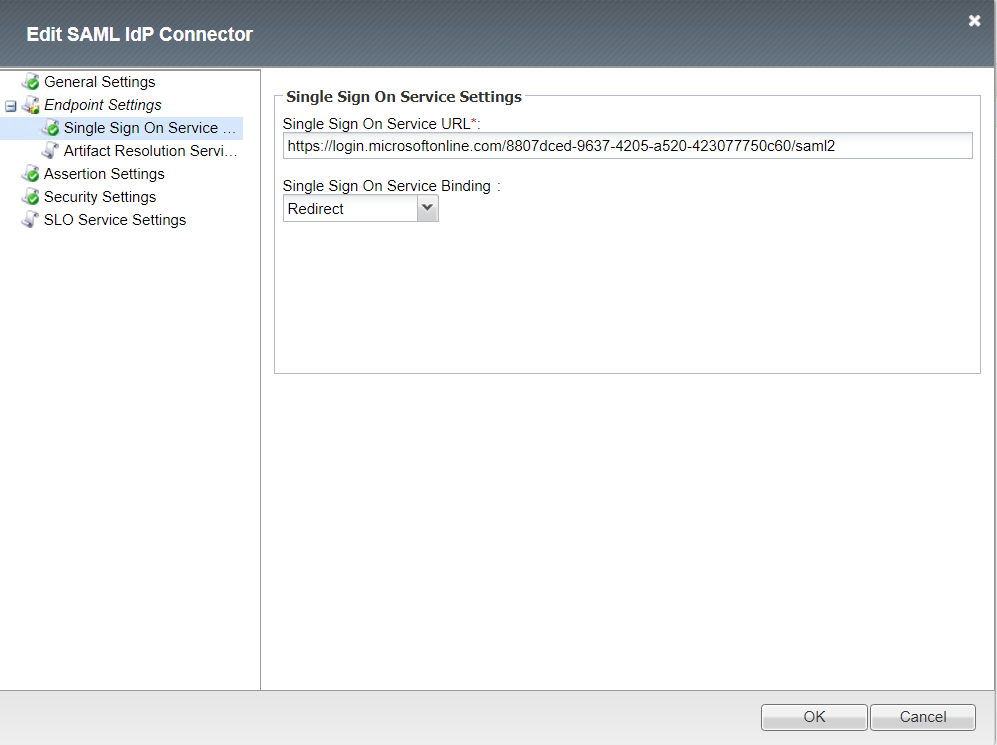
Endpoint Single Sign On Service
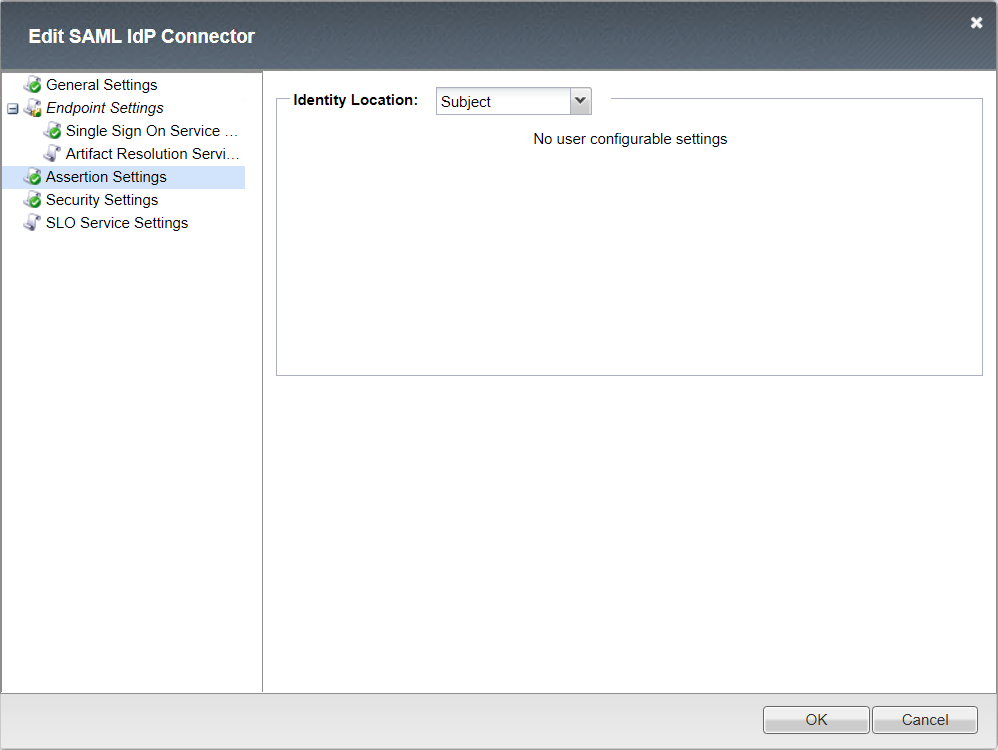
Assertion Settings
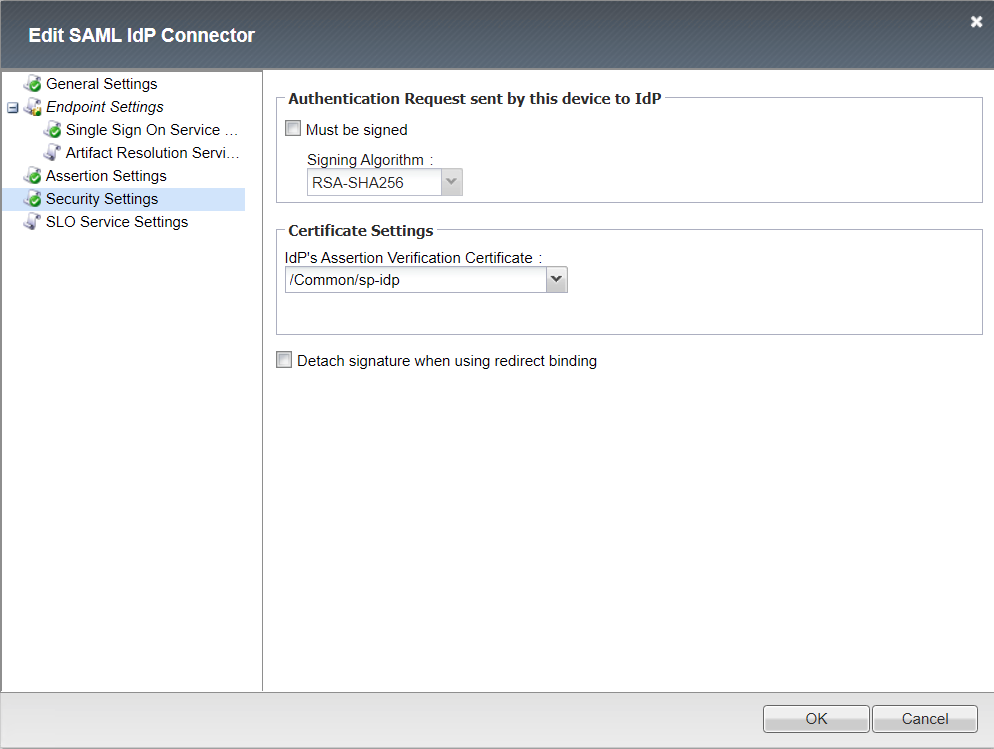
Security Settings
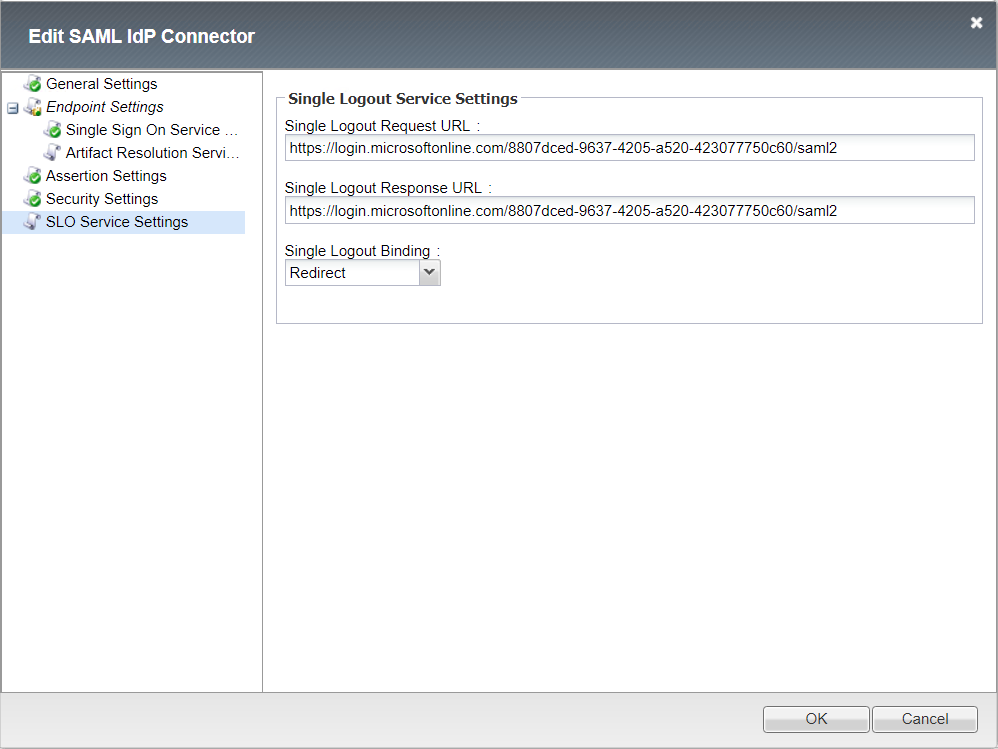
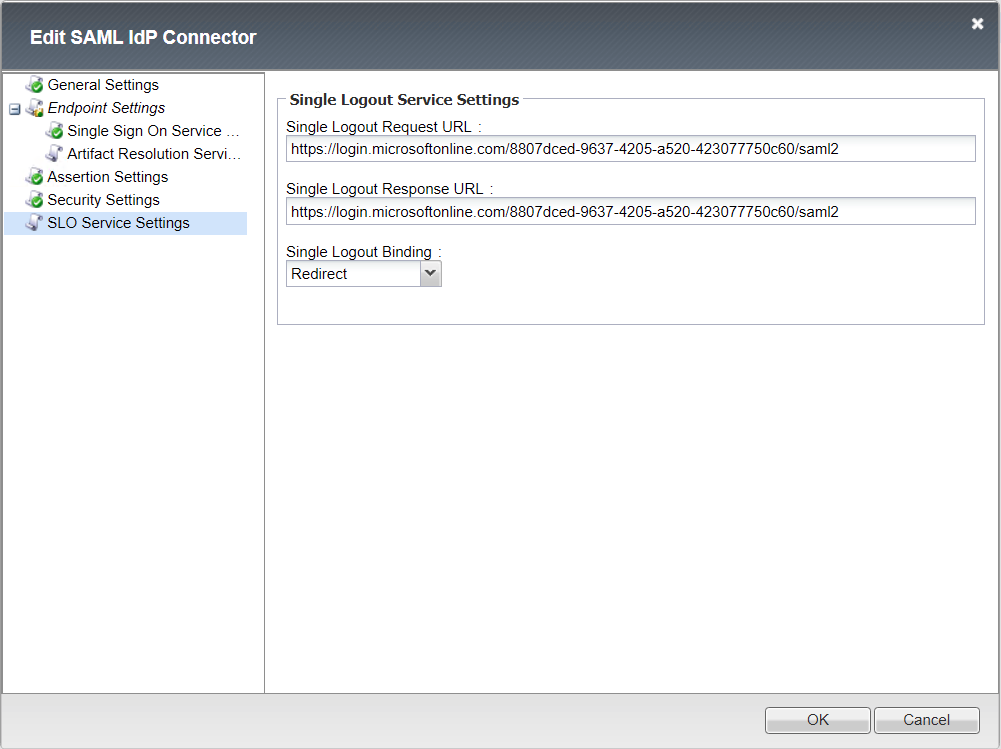
Single Logout Service Settings
IdP Connector (solution14-1-idp-conn)¶
General settings
Endpoint Single Sign On Service
Assertion Settings
Security Settings
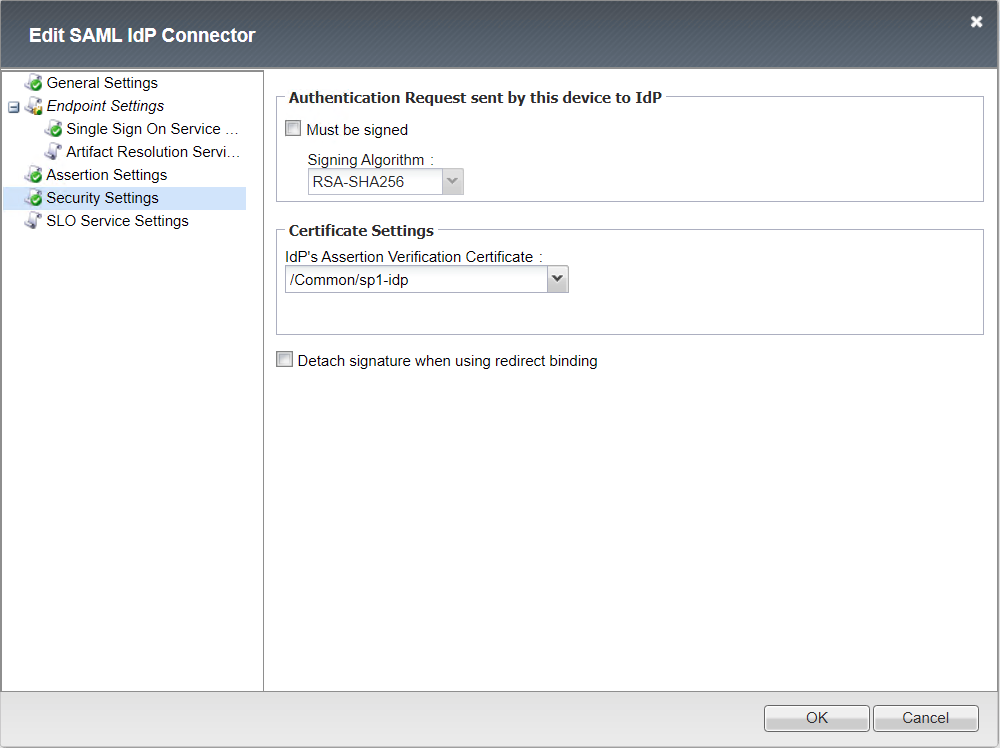
Single Logout Service Settings
User’s Perspective¶
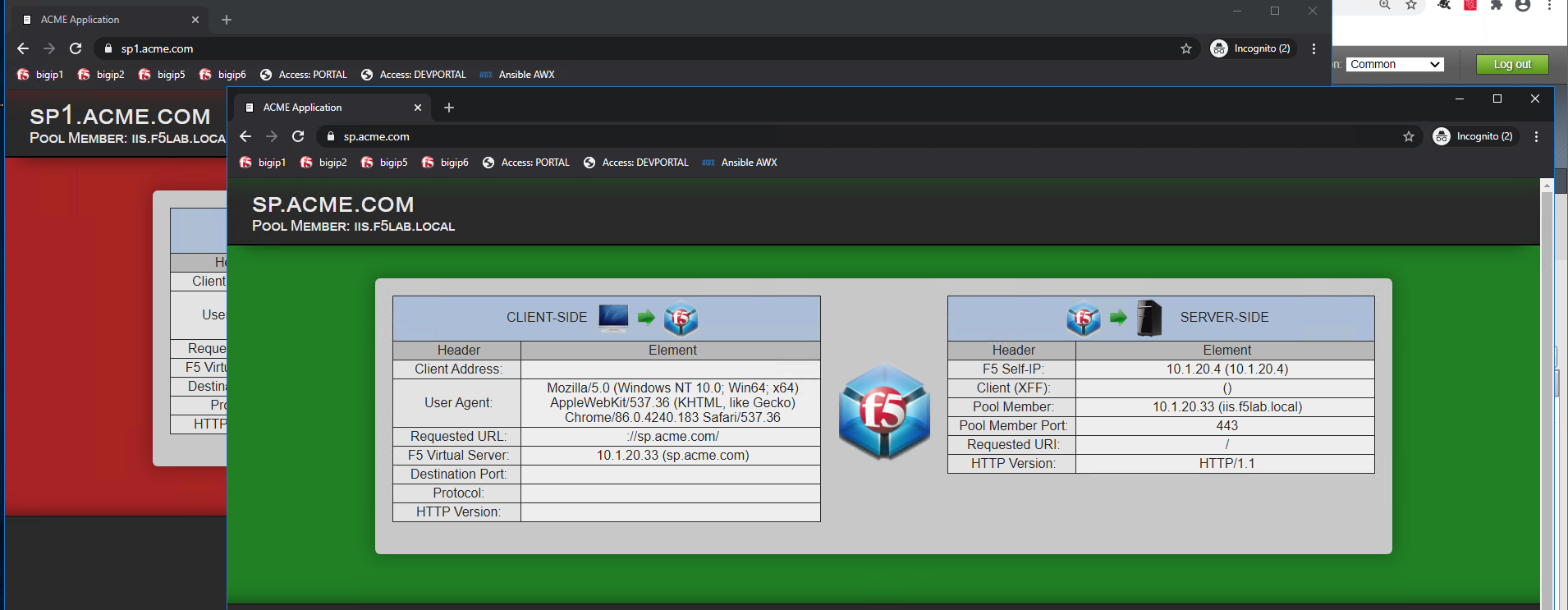
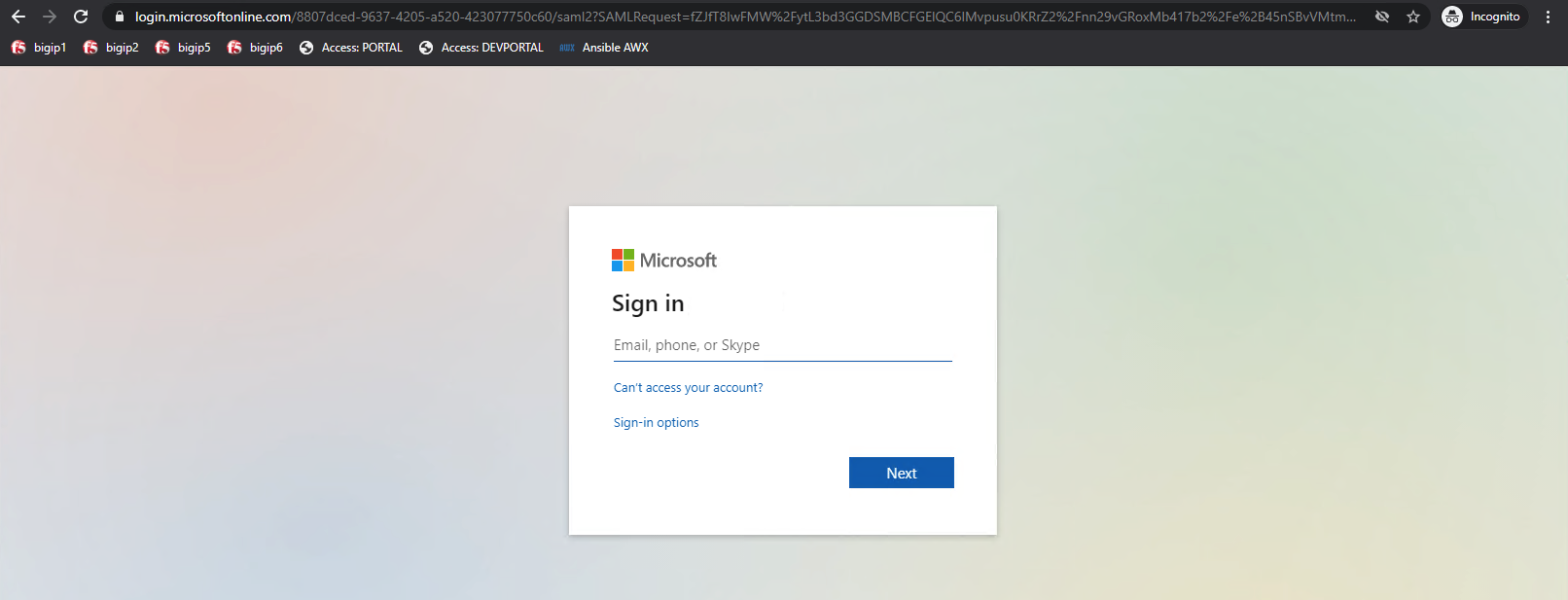
The user attempting to access https://sp1.acme.com is directed to AzureAD for authentication.
Username: user1@f5access.onmicrosoft.com
Password: F5twister$
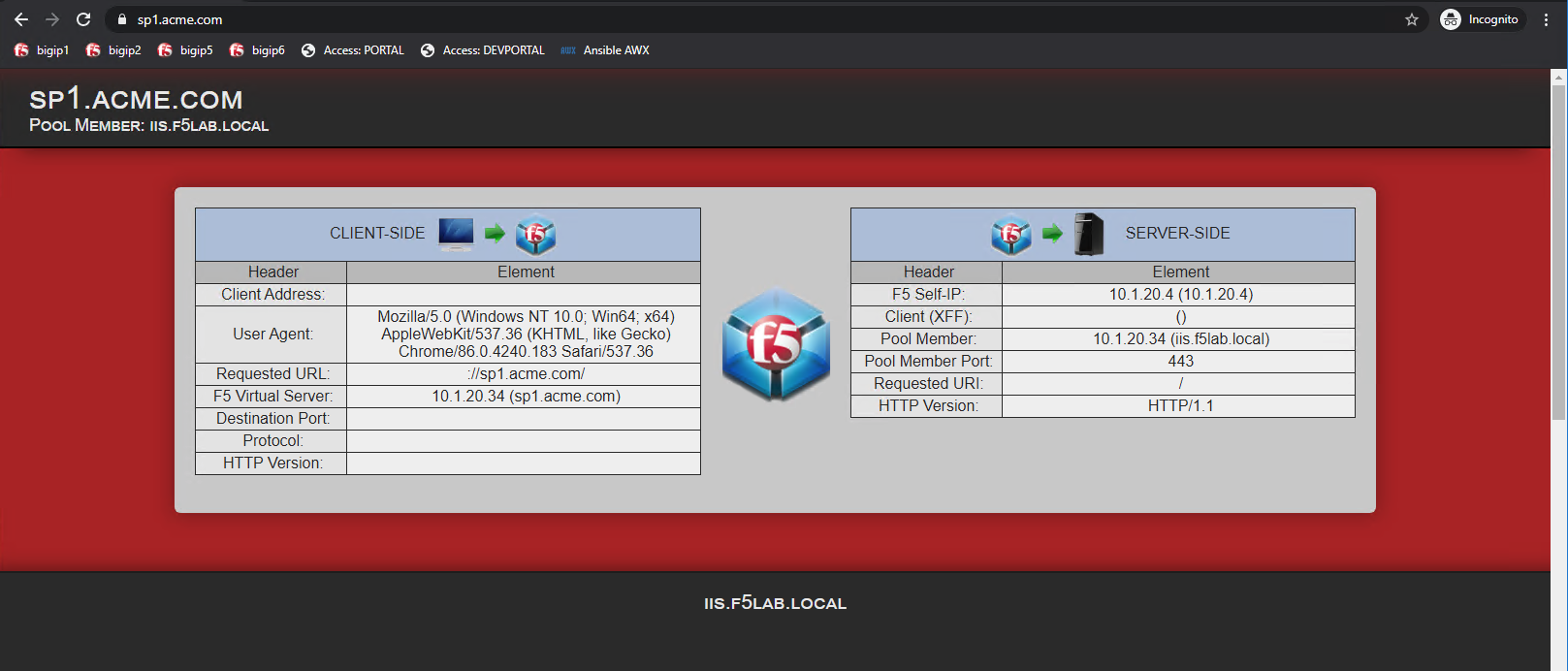
Once the user is authenticated they are transparently redirected back to the resource. In this case, it is sp1.acme.com
Once the user in authenticated at the Identity Provider, they are allowed access to sp.acme.com without need to re-authenticate.