Solution15 Policies¶
This solution requires creation of three access policies. A default allow per-session policy and a per-request policy using two subroutines for Identity Aware Proxy(IAP). The third policy will be used by a virtual server performing both as a SAML SP to an external IDP along with SAML IDP to the Identity Aware Proxy virtual server.
Primary Identity Provider¶
Per-Session Policy Walk-Through¶
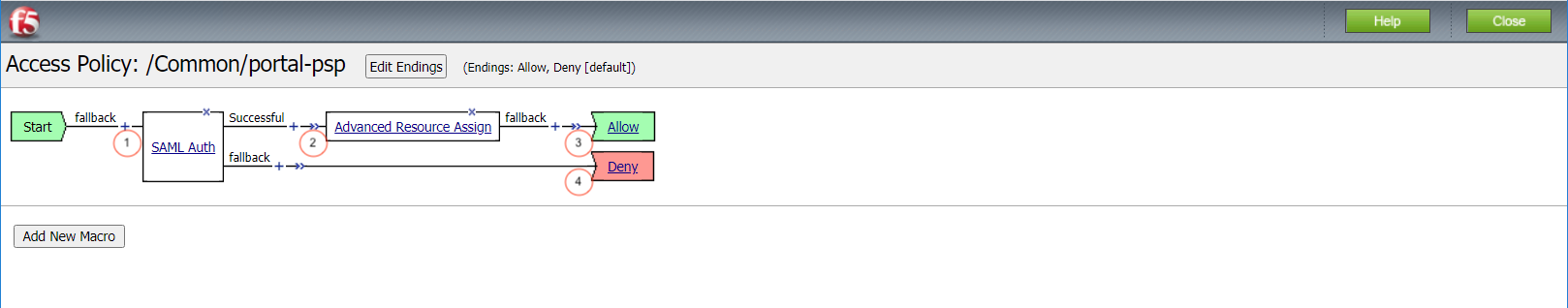
When a user is directed to a SAML Auth agent they are redirected to the IDP(AzureAD) selected by the SP Service(portal.acme.com).
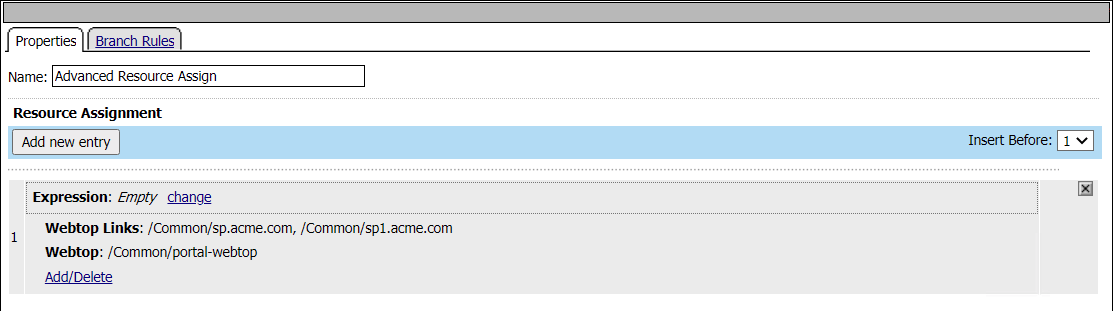
Upon successful authentication at the IDP, the user is redirected back to the SP. The SP service consumes the Assertion. he user is assigned resources defined in the Advanced Resource Assign Agent
After successful Resource Assignment, the user is granted access via the Allow Terminal.
If SAML Authentication is unsuccessful, the user proceeds down the fallback branch to be denied access via the Deny Terminal
Profile Settings¶
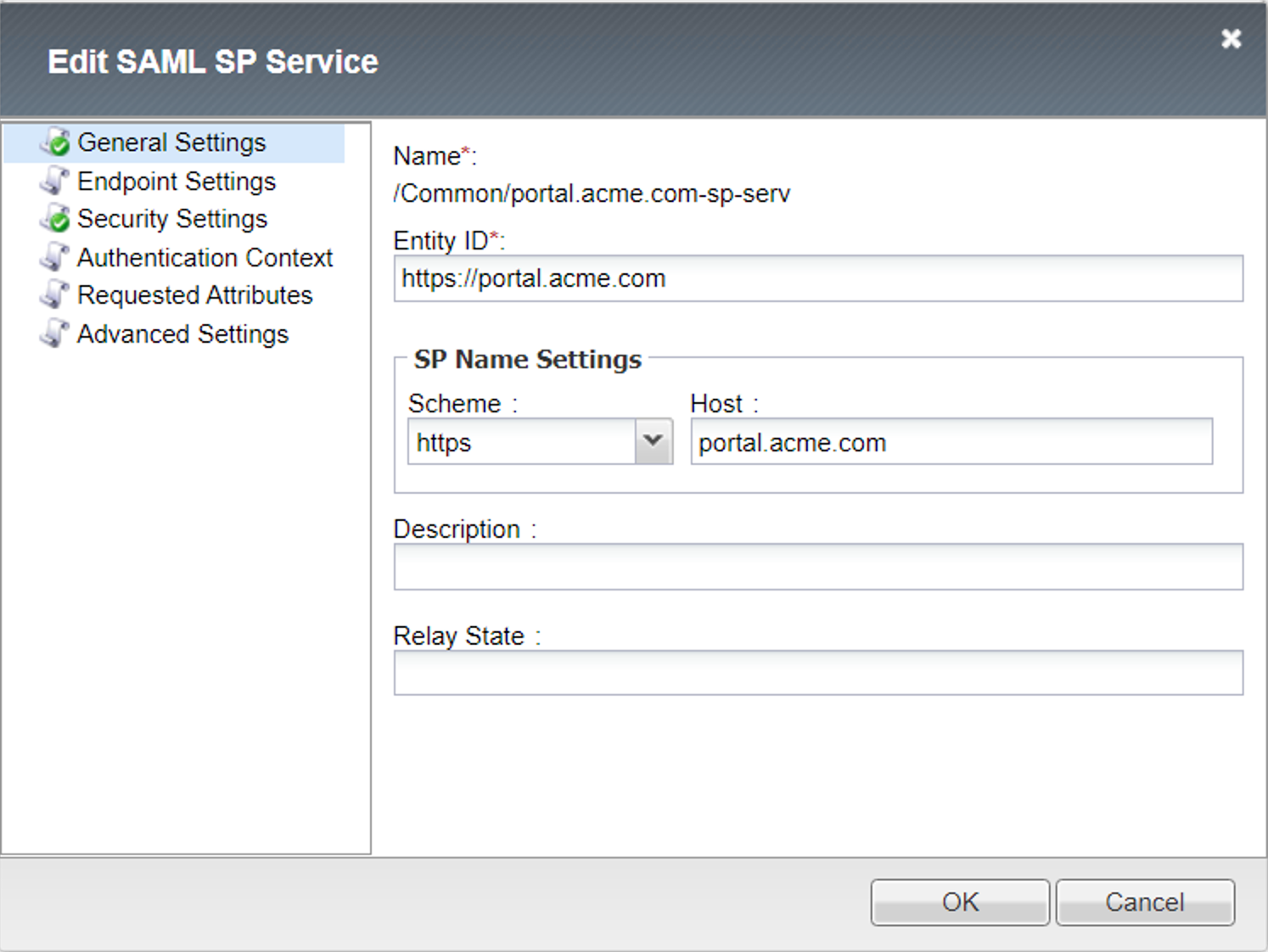
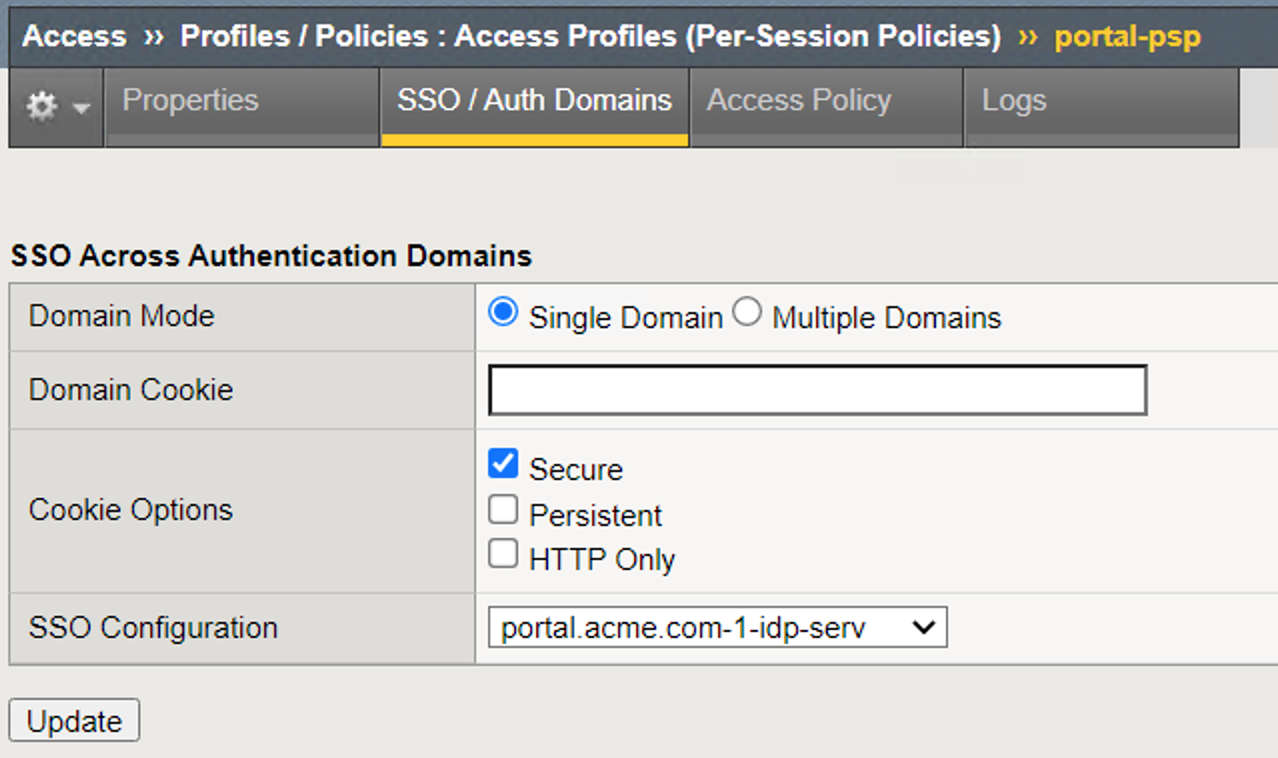
The Portal Profile settings have been modified in order to attach the IdP Service.
Identity Aware Proxy¶
Per-Session Policy Walk-Through¶
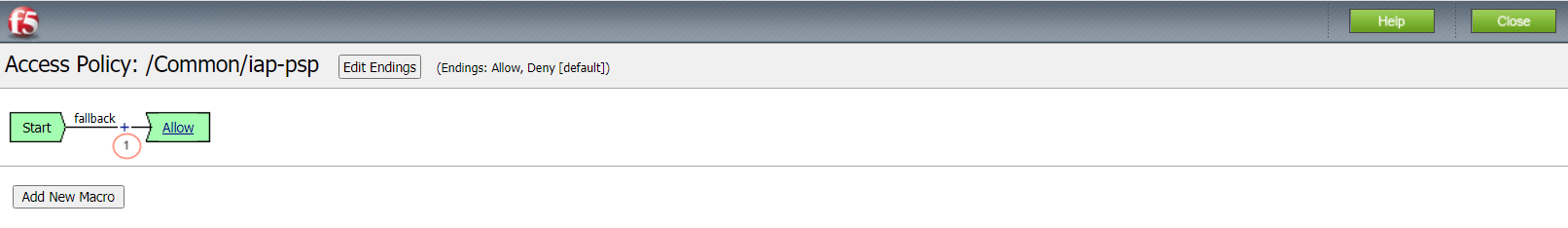
This initial access policy (default allow) is a per-session policy to populate required session variable name and values.
Per-Request Policy Walk-Through¶
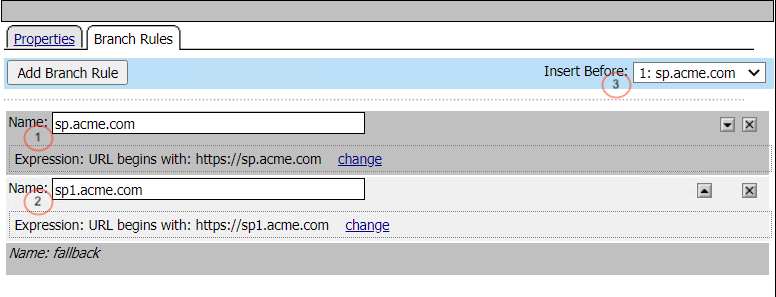
This per-request access policy accepts users request and redirect them to one of the two SAML Auth Subroutines configured for sp.acme.com or sp1.acme.com.
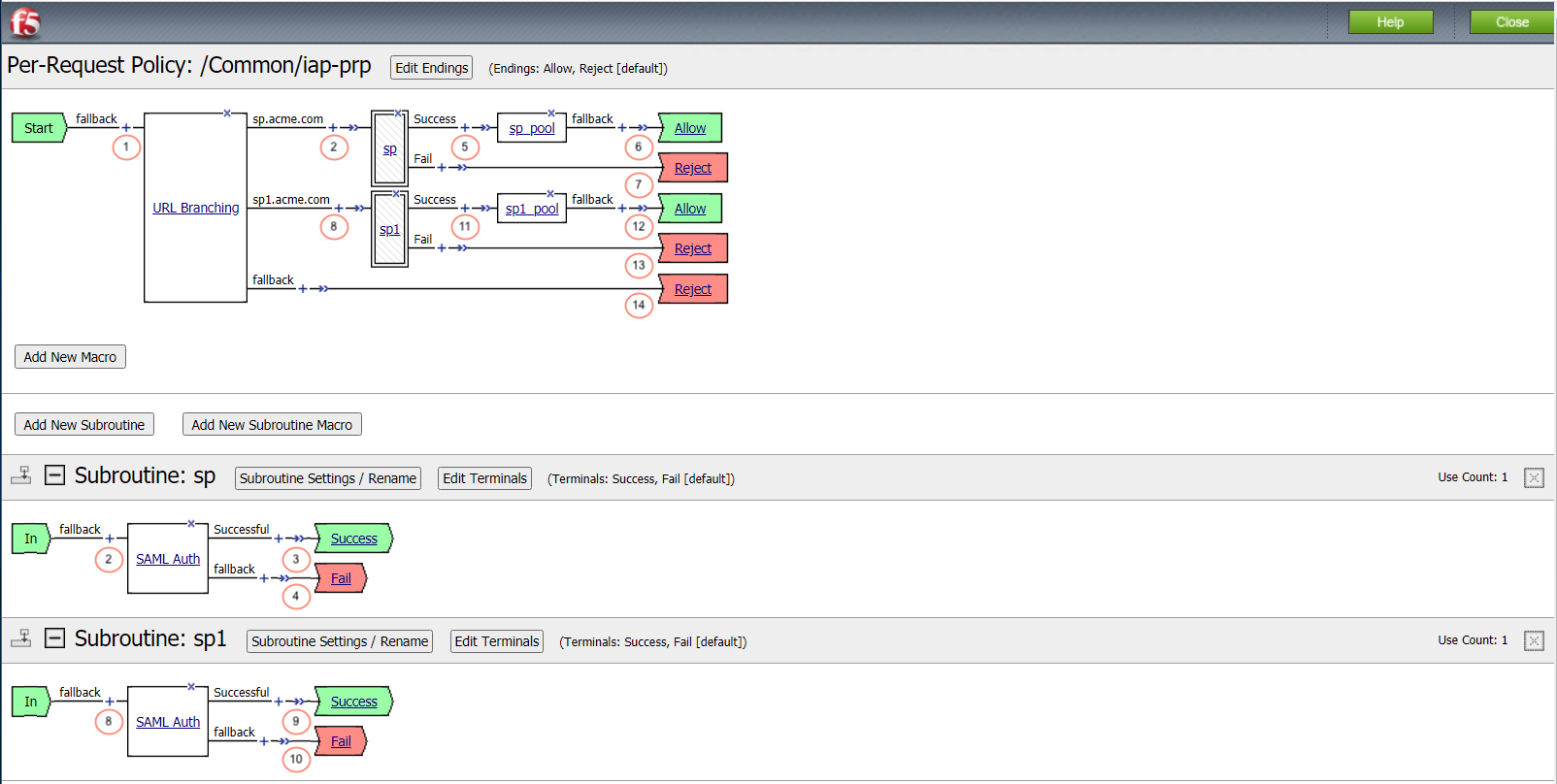
This URL Branching agent evaluates the requests host header to determine the appropriate next path.
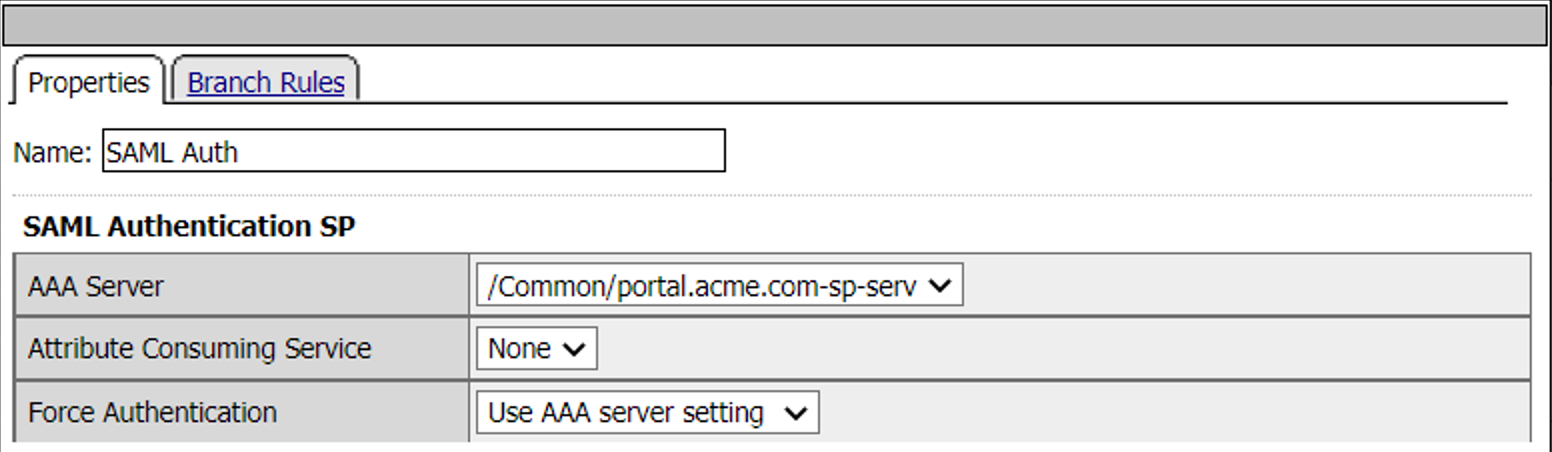
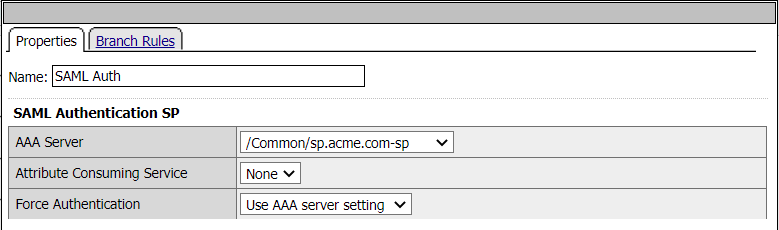
When a user is directed to a SAML Auth agent they are redirected to the IDP(portal.acme.com) selected by the SP Service(sp.acme.com).
Upon successful authentication at the IDP, the user is redirected back to the SP. The SP service consumes the Assertion. The user is directed to the Success Terminal.
Upon unsuccessful authentication, the user proceeds down the fallback branch the Fail Terminal.
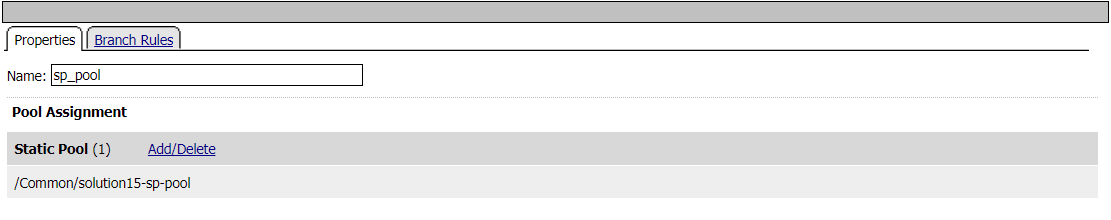
Pool sp.acme.com-pool is assigned to the request for load balancing. Traditional LTM load balancing rules still apply.
The user is granted access via the Allow Terminal.
Upon unsuccessful authentication, the user proceeds down the fallback branch to be denied access via the Reject Terminal
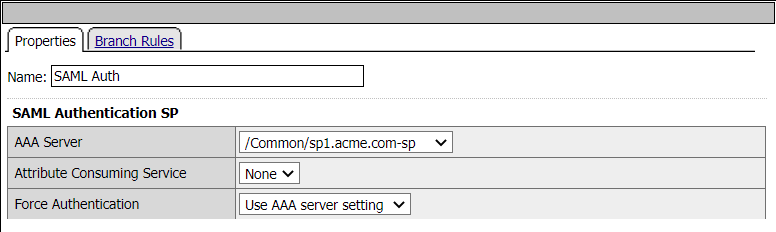
When a user is directed to a SAML Auth agent they are redirected to the IDP(portal.acme.com) selected by the SP Service(sp1.acme.com).
Upon successful authentication at the IDP, the user is redirected back to the SP1. The SP service consumes the Assertion. The user is directed to the Success Terminal.
Upon unsuccessful authentication, the user proceeds down the fallback branch and directed to the Fail Terminal.
Pool sp1.acme.com-pool is assigned to the request for load balancing. Traditional LTM load balancing rules still apply.
The user is granted access via the Allow Terminal.
Upon unsuccessful authentication, the user proceeds down the fallback branch and directed to the Reject Terminal.
The request does not contain a matching URL causing the request to proceed down the fallback branch to the Reject Terminal
Per-Request Agent configuration¶
URL Branch Rules
Subroutine: SP - SAML Auth
Subroutine: SP1 - SAML Auth
Pool Assign - sp_pool
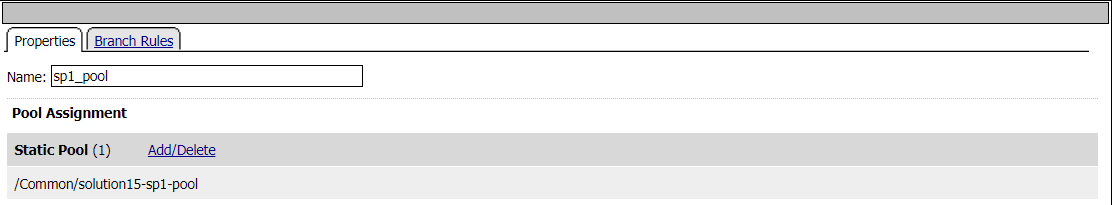
Pool Assign - sp1_pool
Profile Settings¶
The IAP profile settings are the default.
Supporting APM Objects¶
Configurations settings for Federation Services, (SP Services, IdP Connectors, IdP Services, SP Connectors).
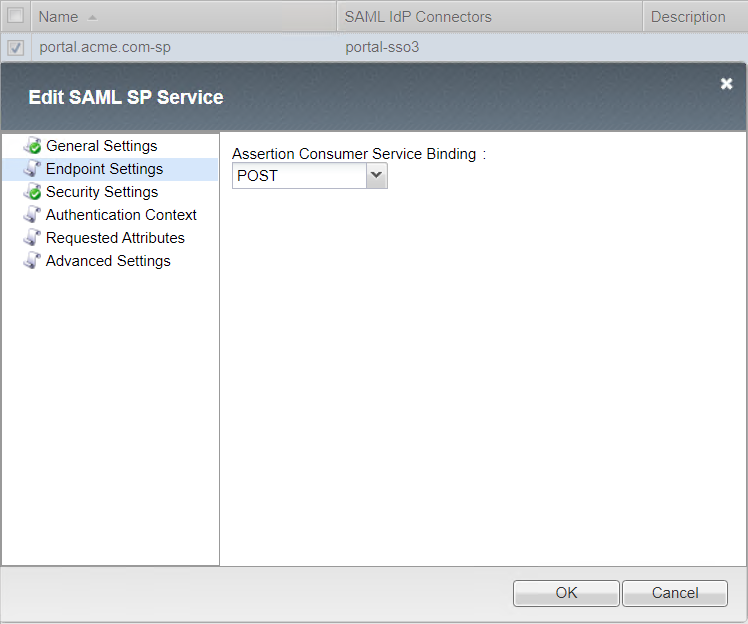
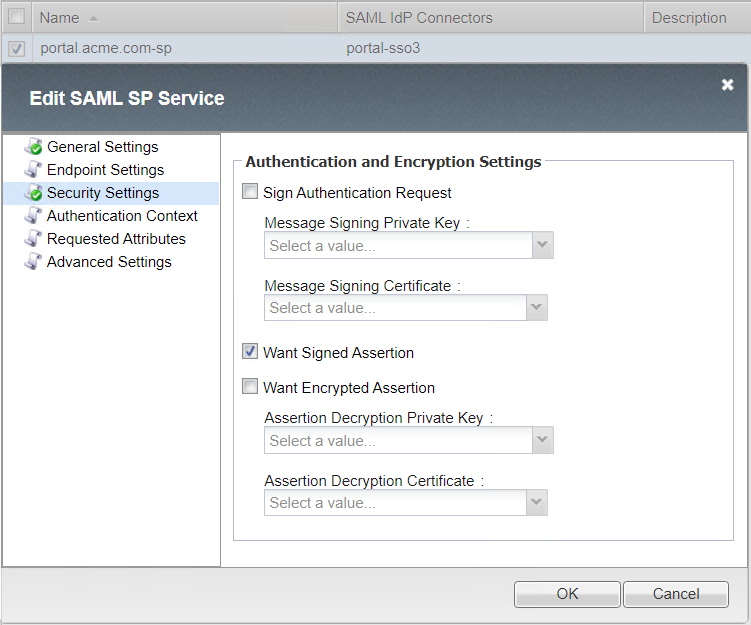
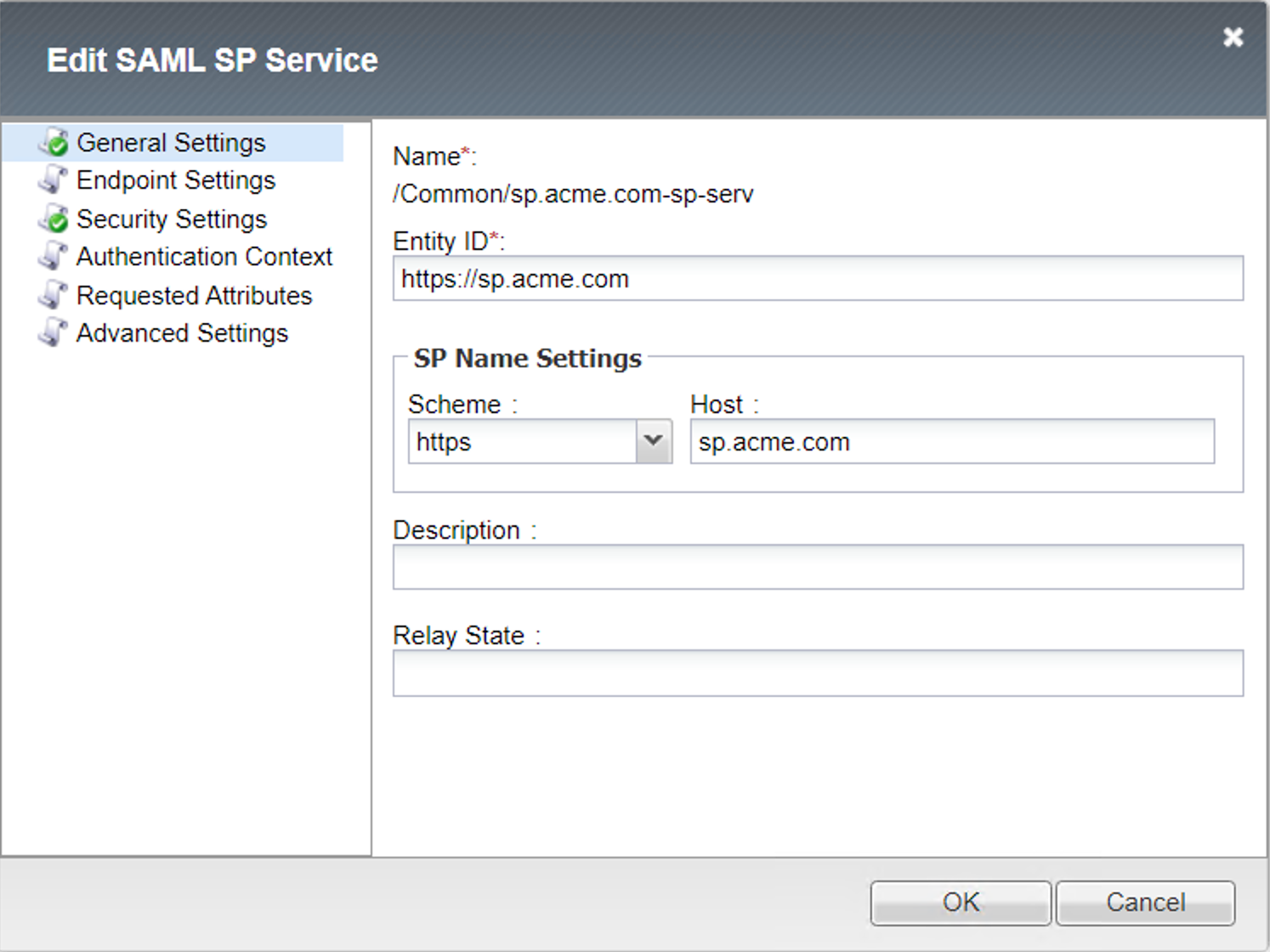
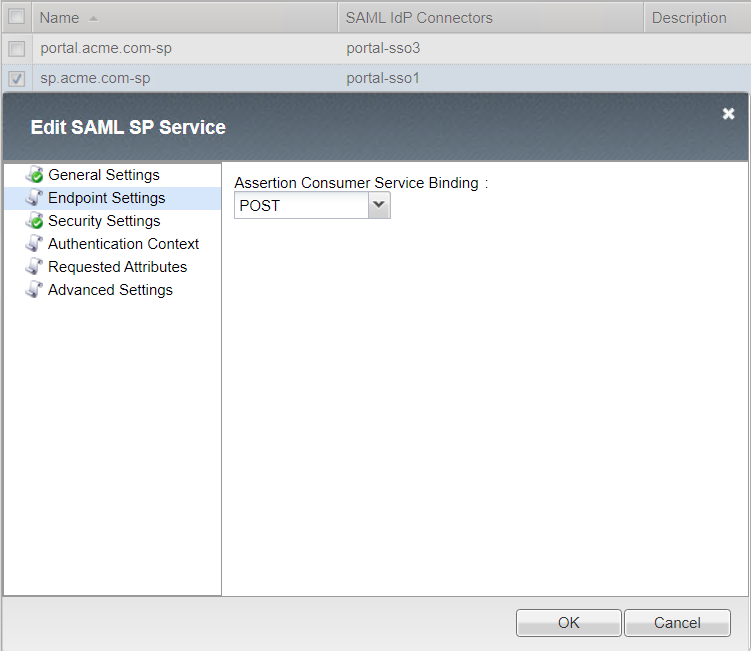
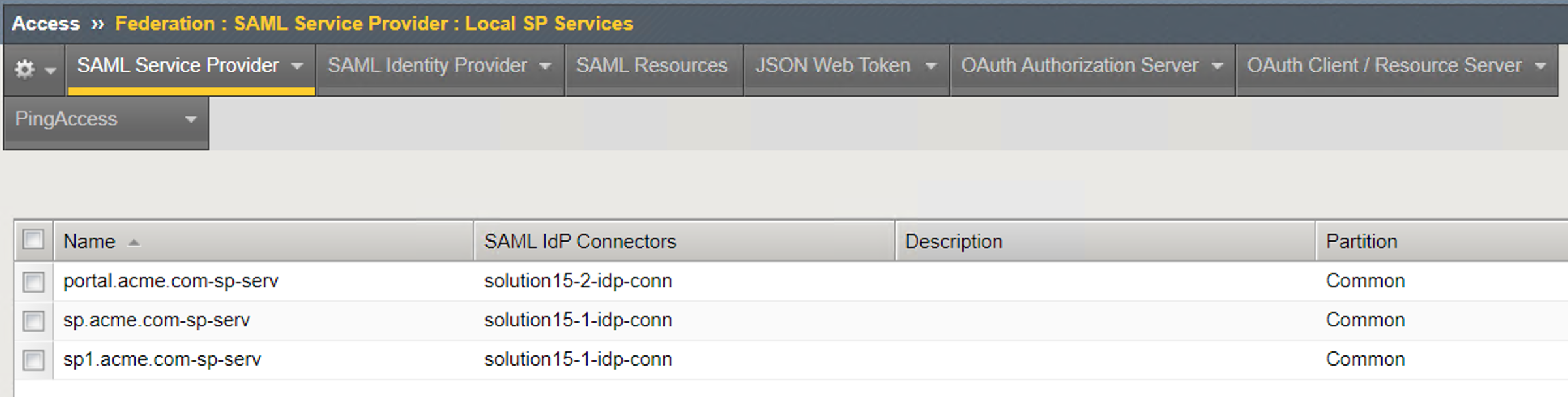
Local SP Services List¶
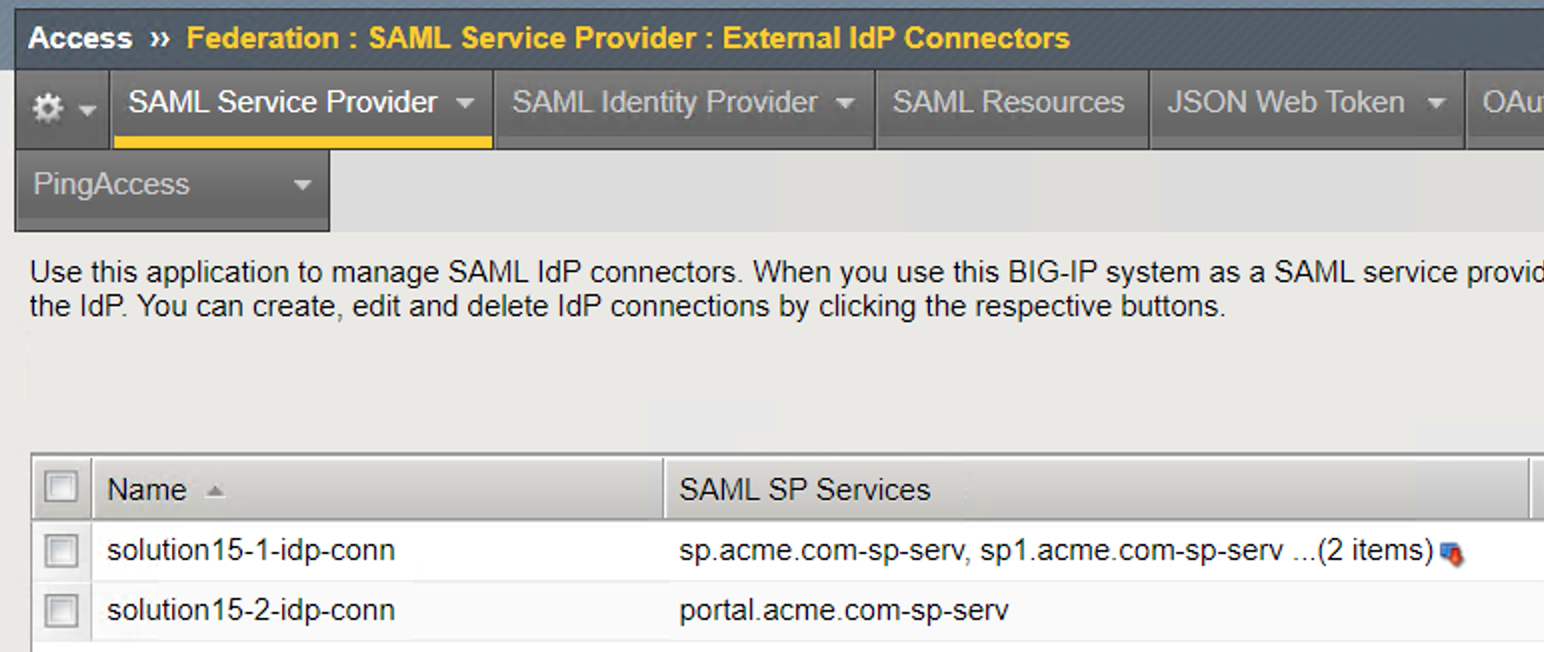
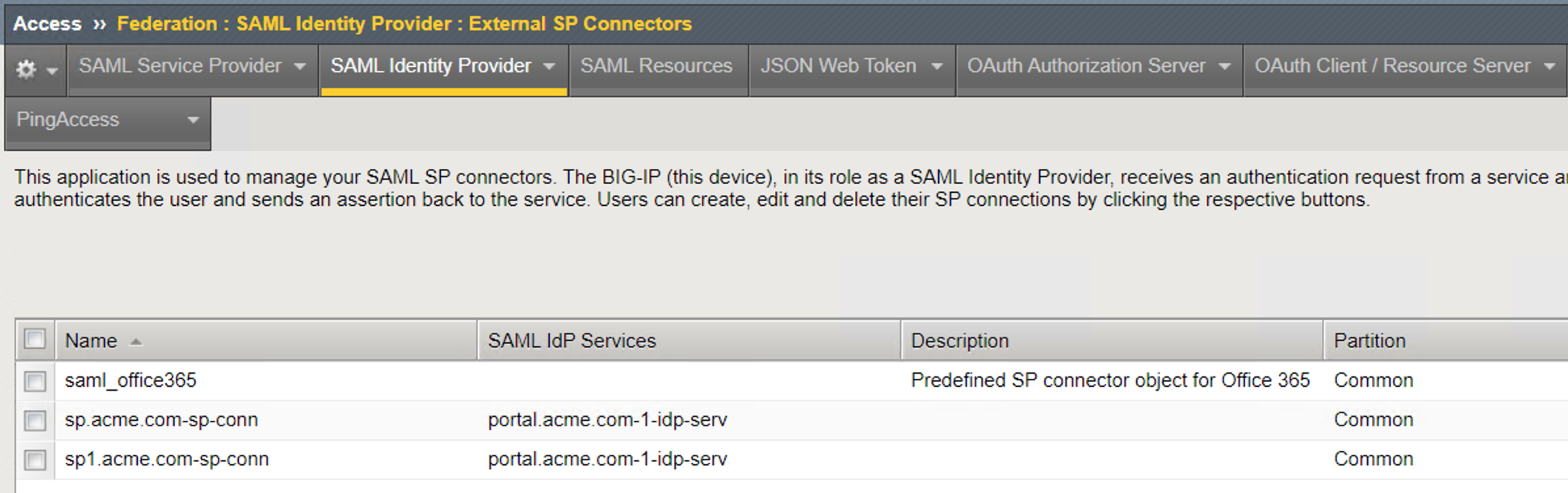
External IdP Connectors List¶
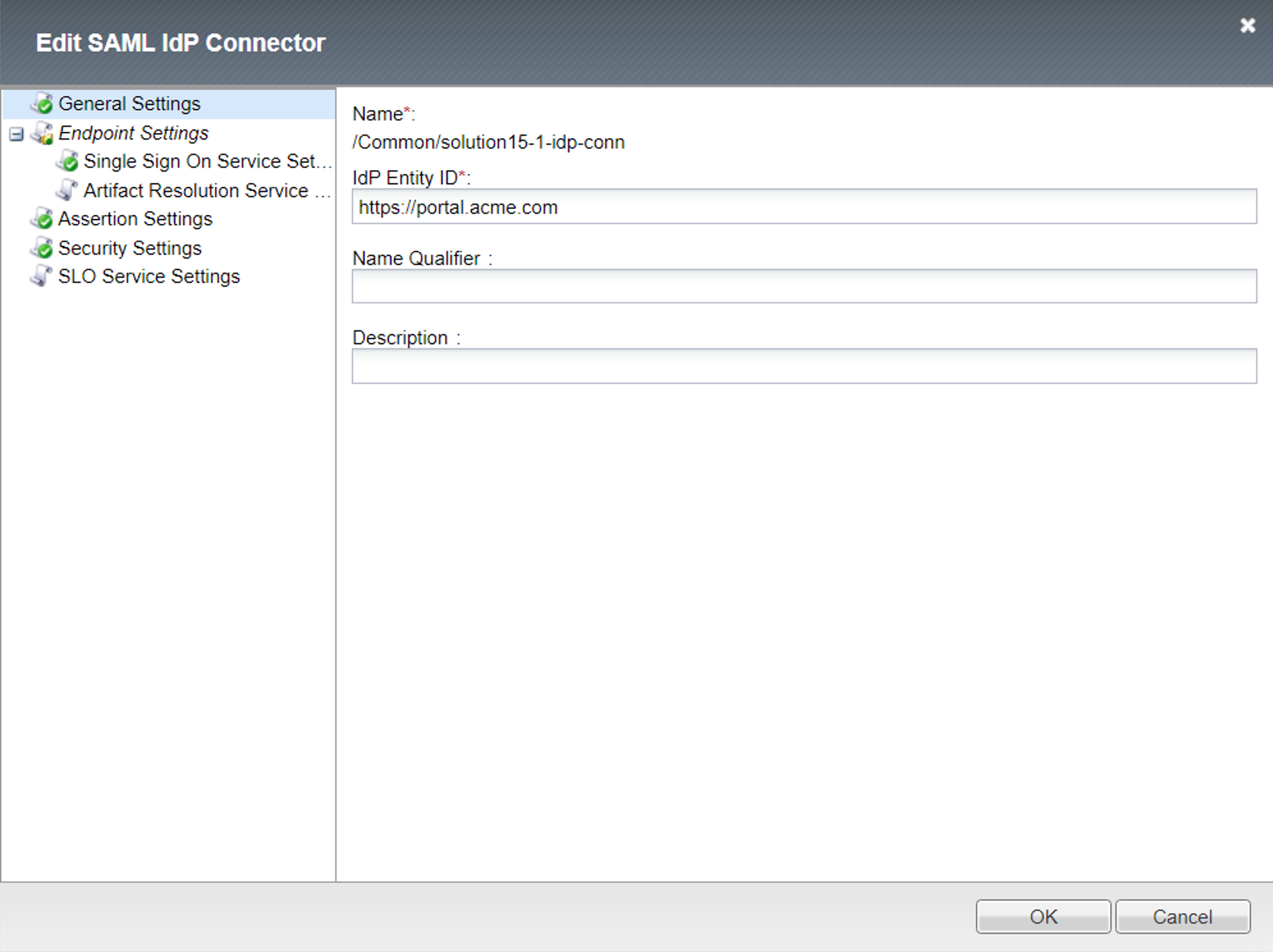
IdP Connector - solution15-1-idp-conn¶
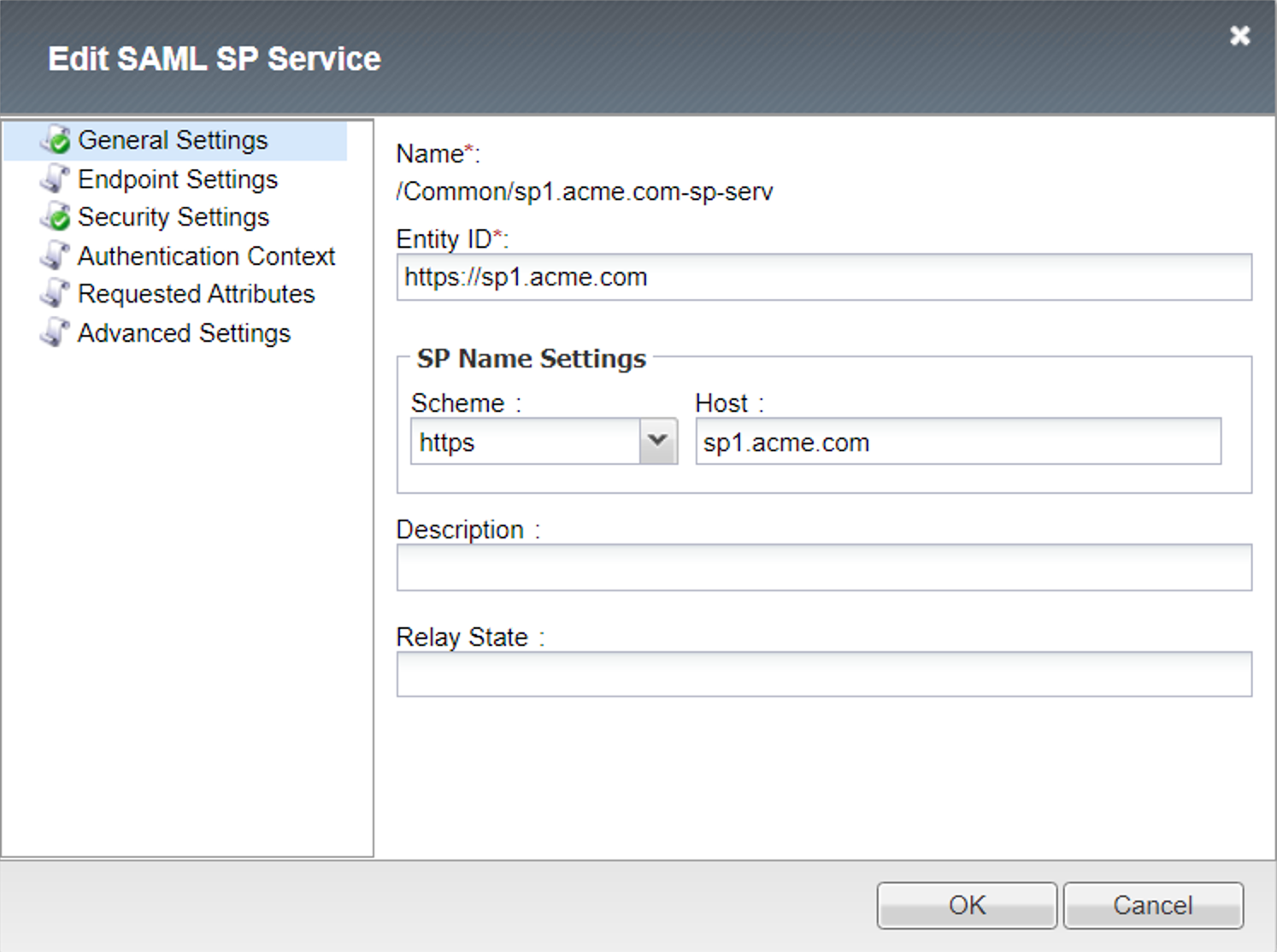
General Settings
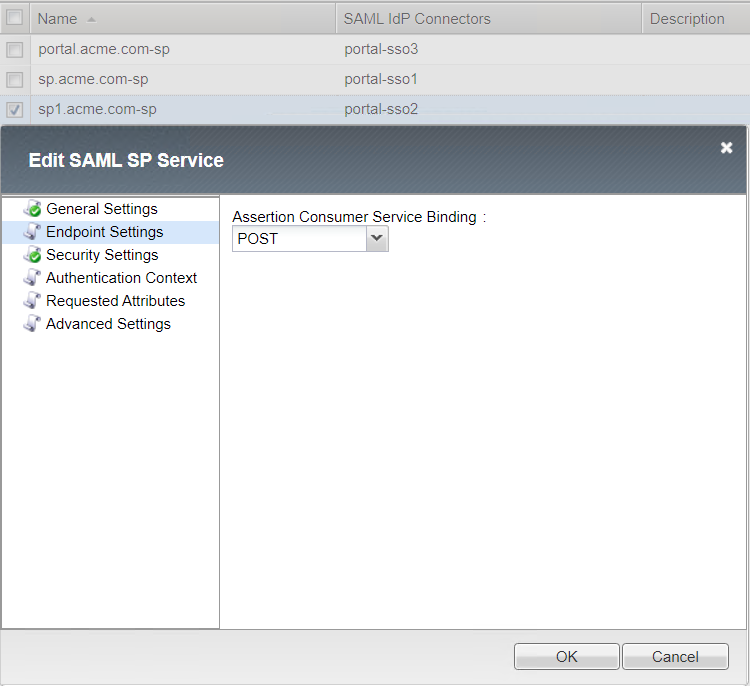
- Endpoint Settings
Single Sign On Service
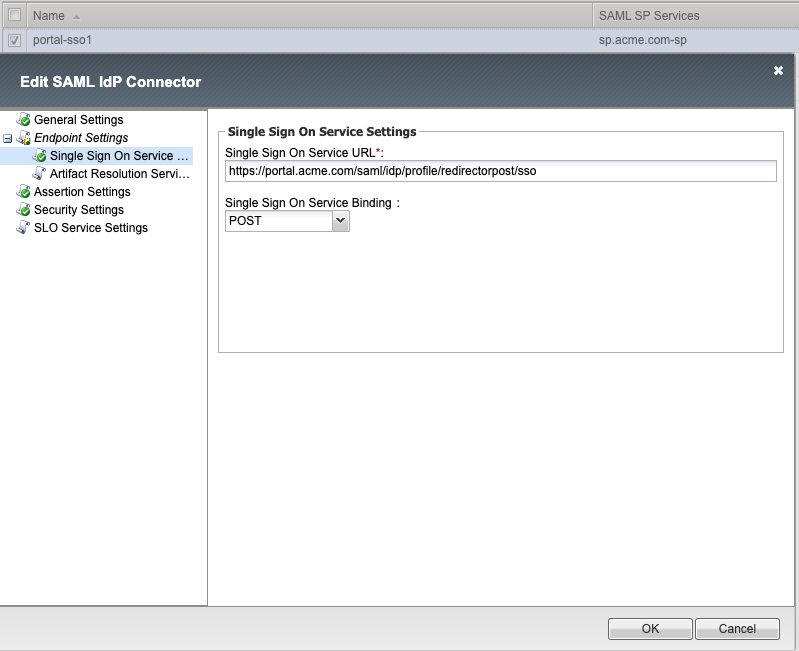
Assertion Settings
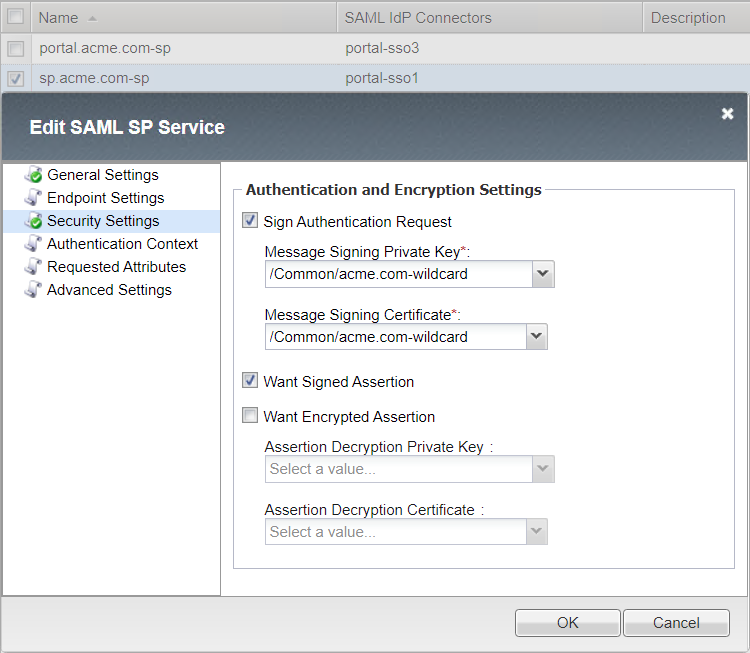
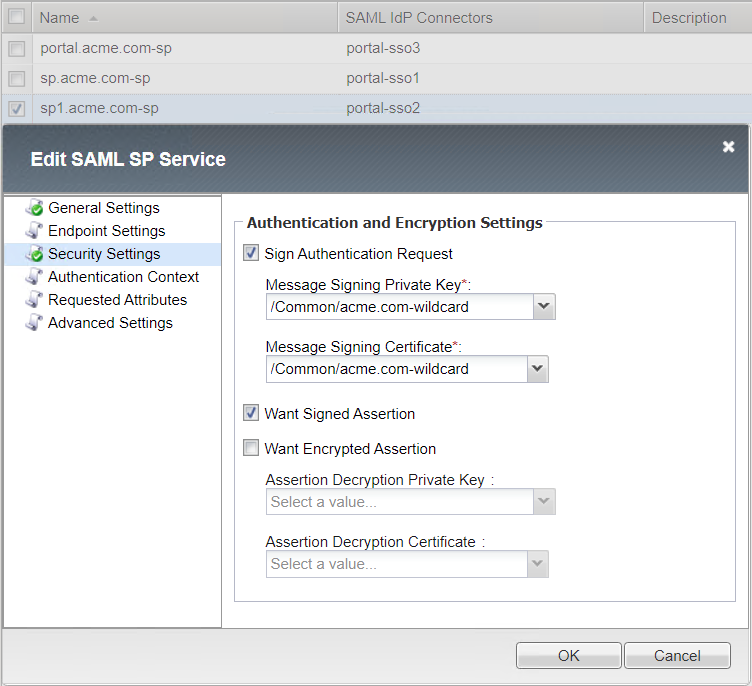
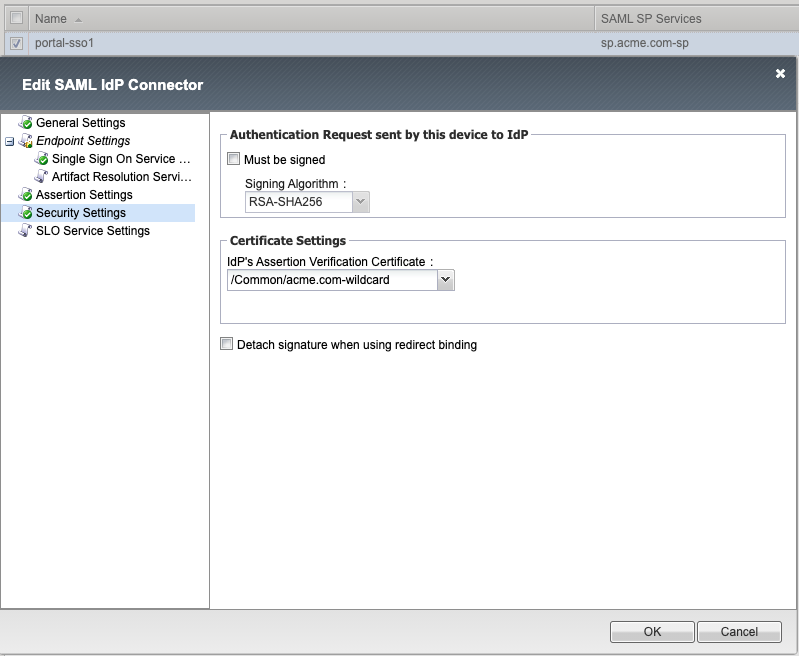
Security Settings
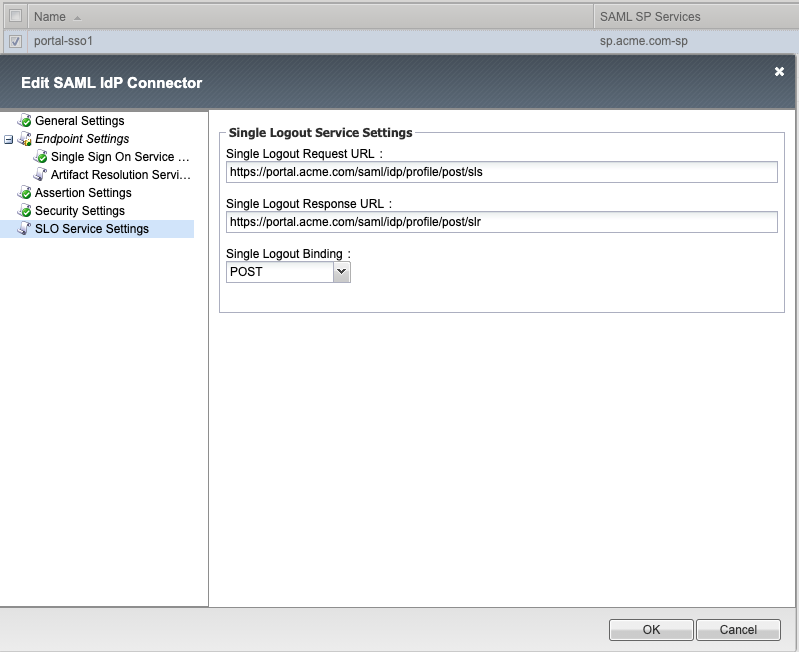
Single Logout Service Settings
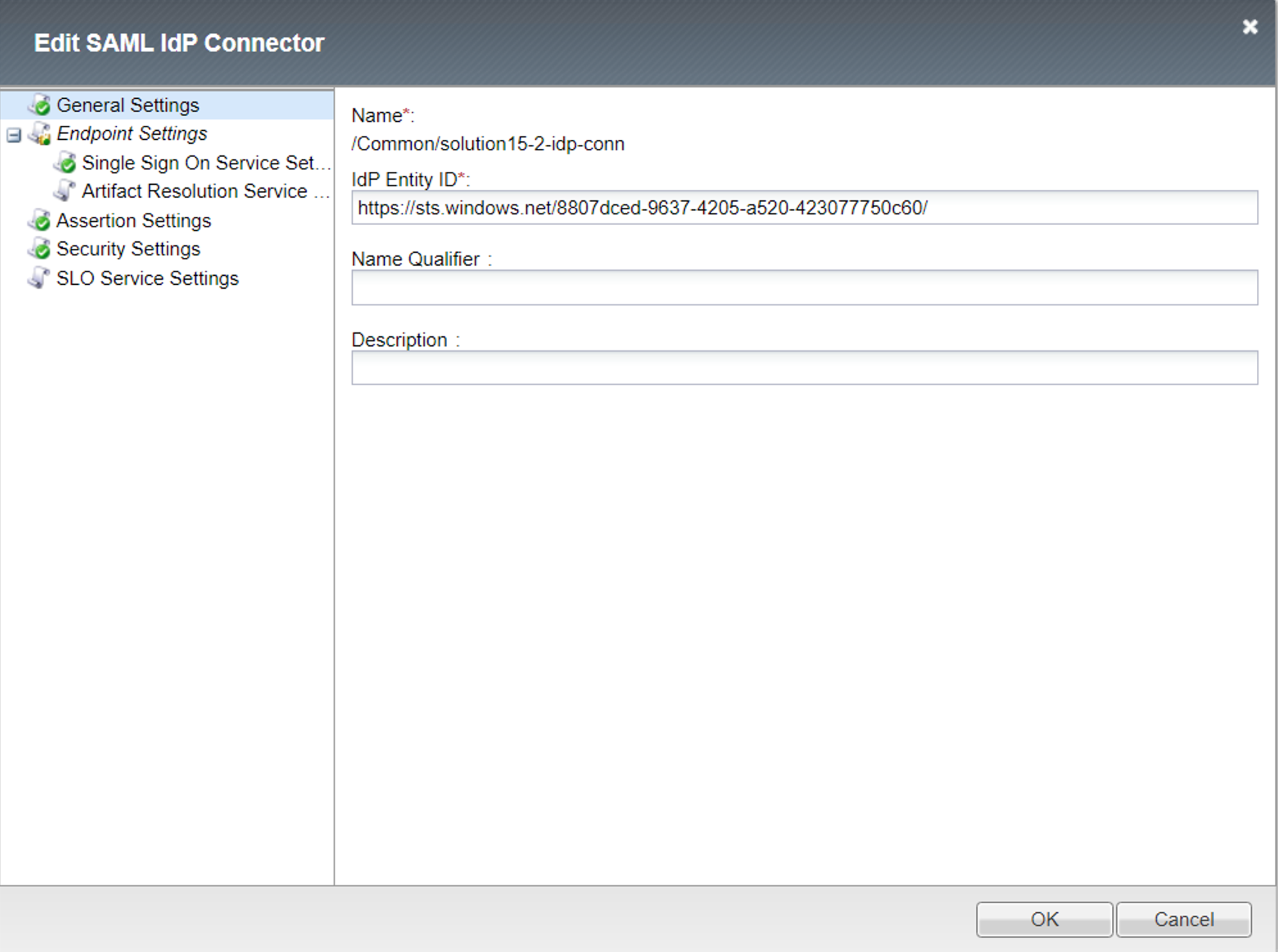
IdP Connector - solution15-2-idp-conn¶
General Settings
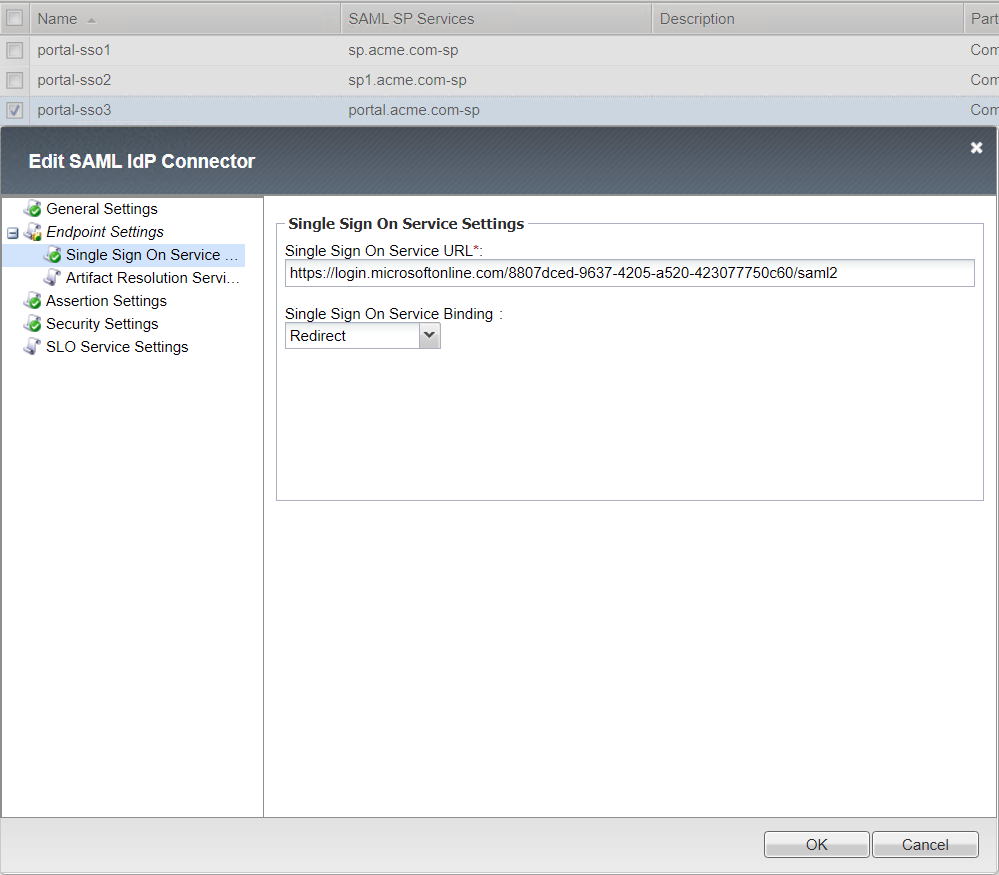
- Endpoint Settings
Single Sign On Service
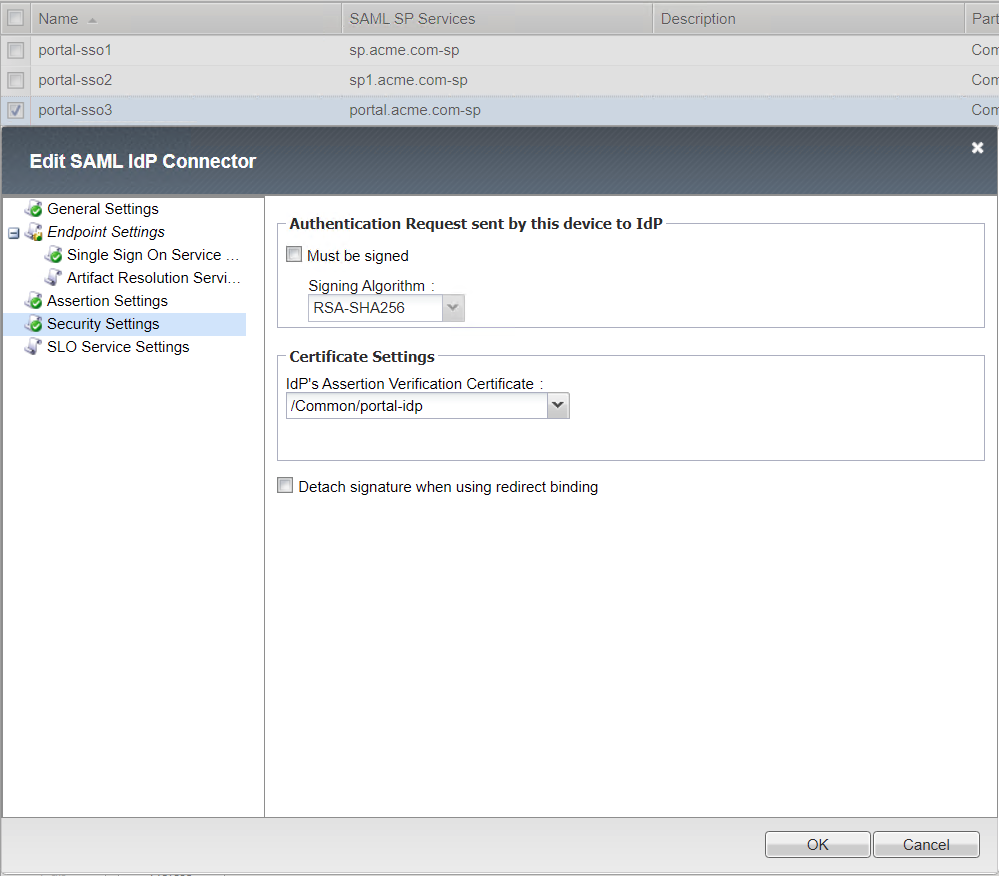
Security Settings
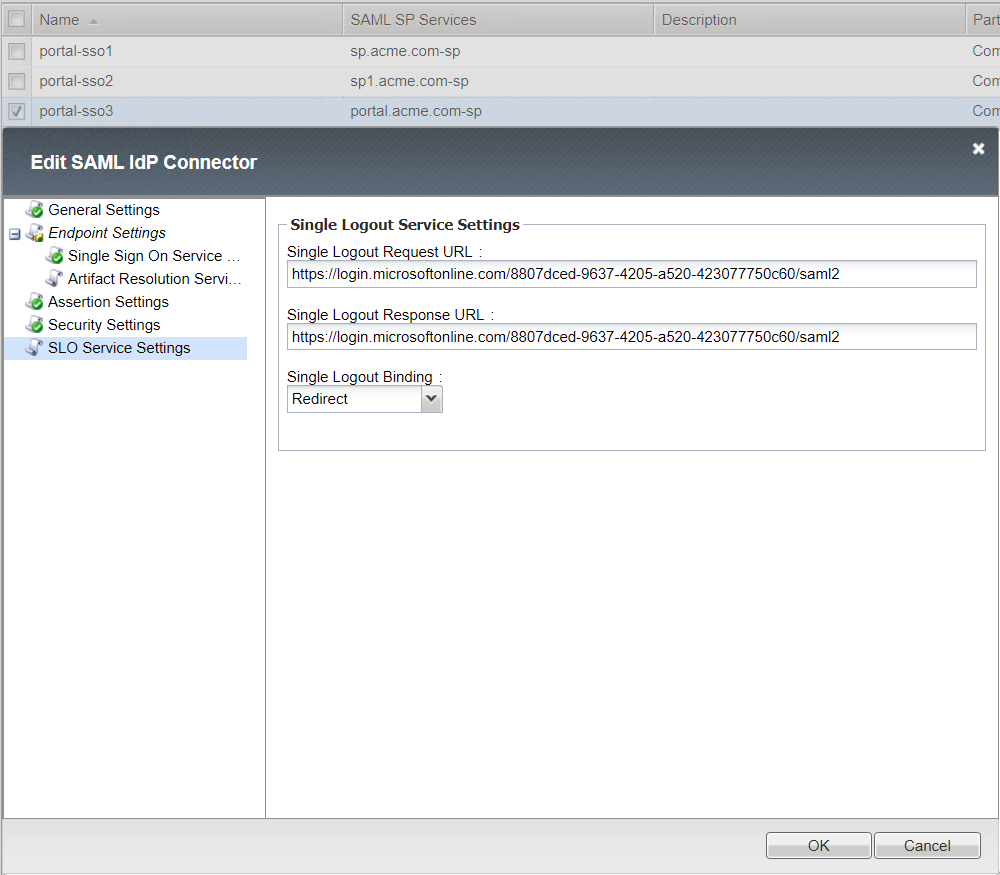
Single Logout Service Settings
Local IdP Service List¶
Local IdP Service - portal.acme.com-1-idp-service¶
General Settings
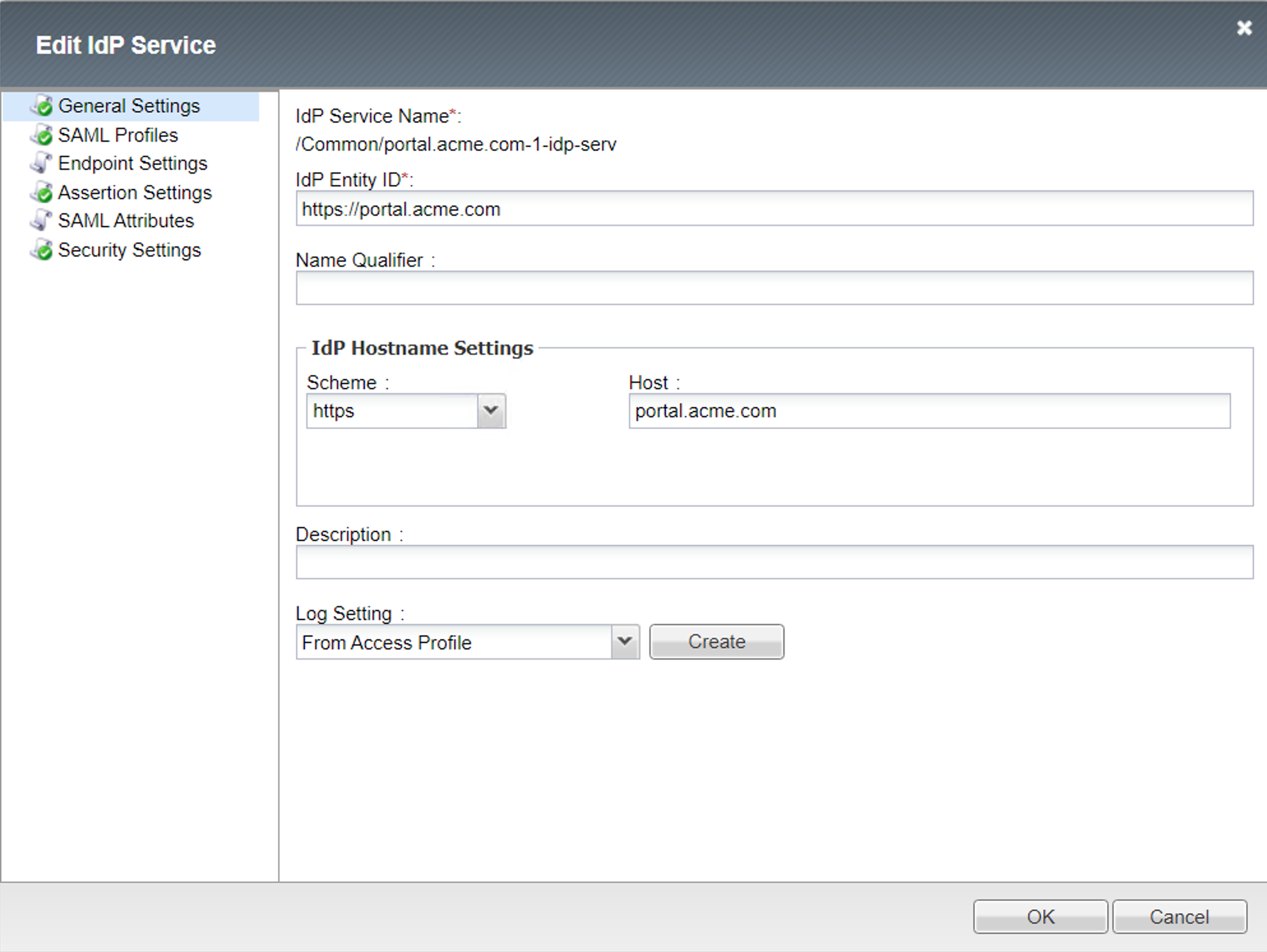
SAML Profiles
Endpoint Settings
Assertion Settings
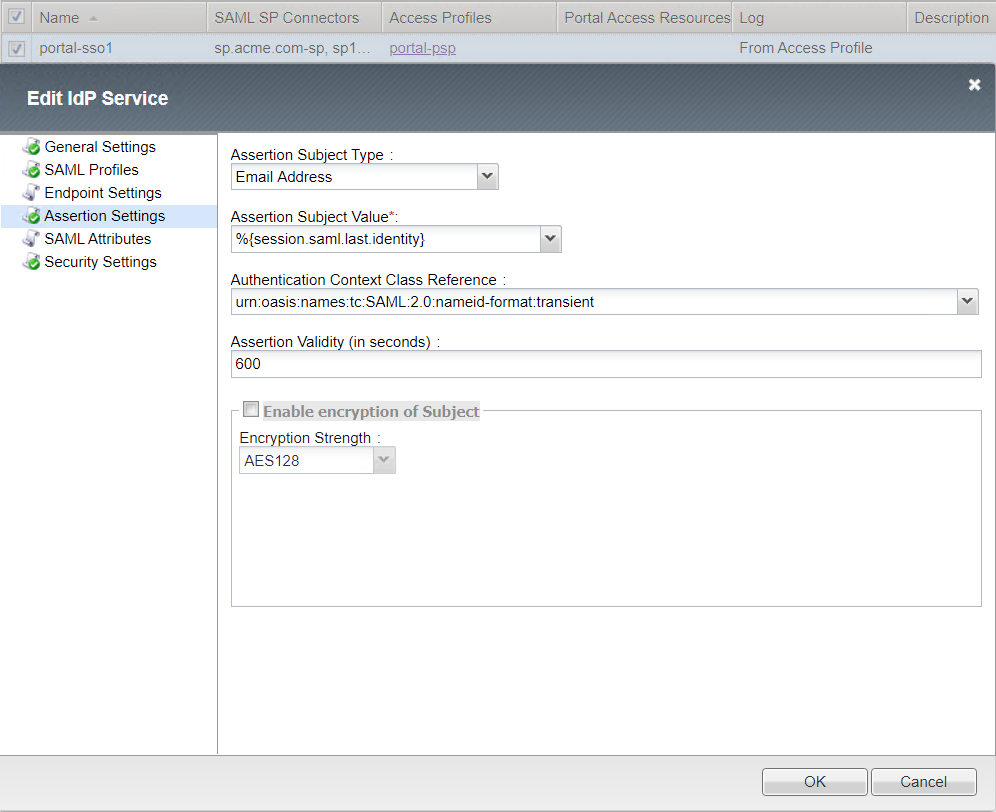
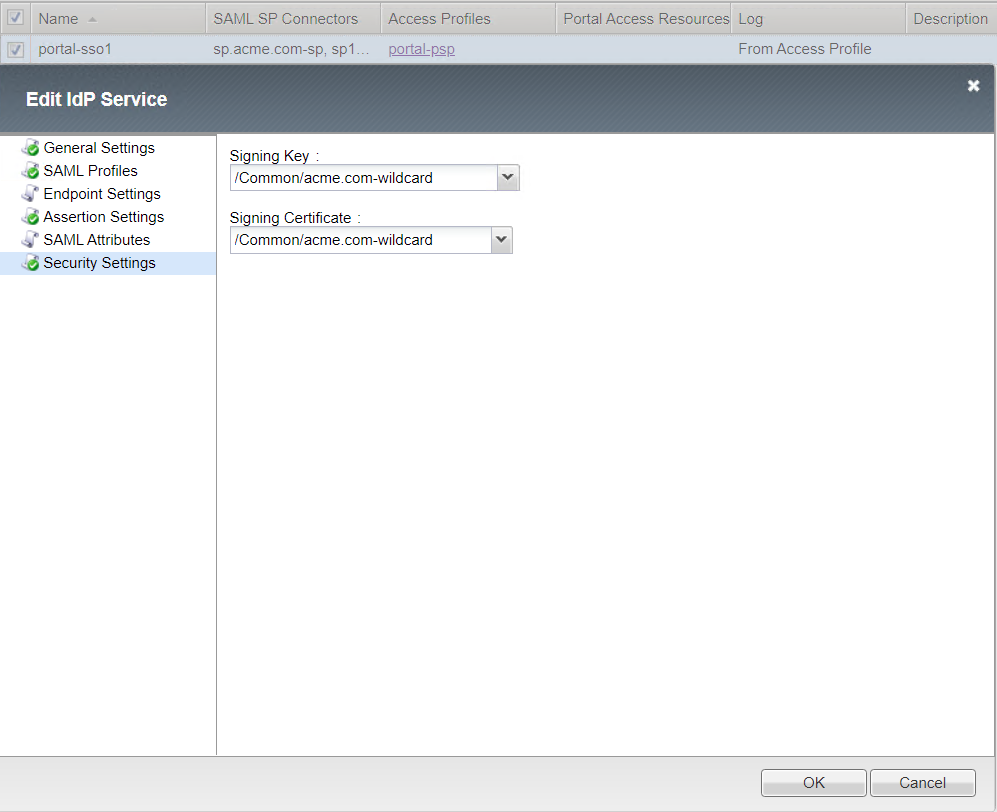
Security Settings
External SP Connector List¶
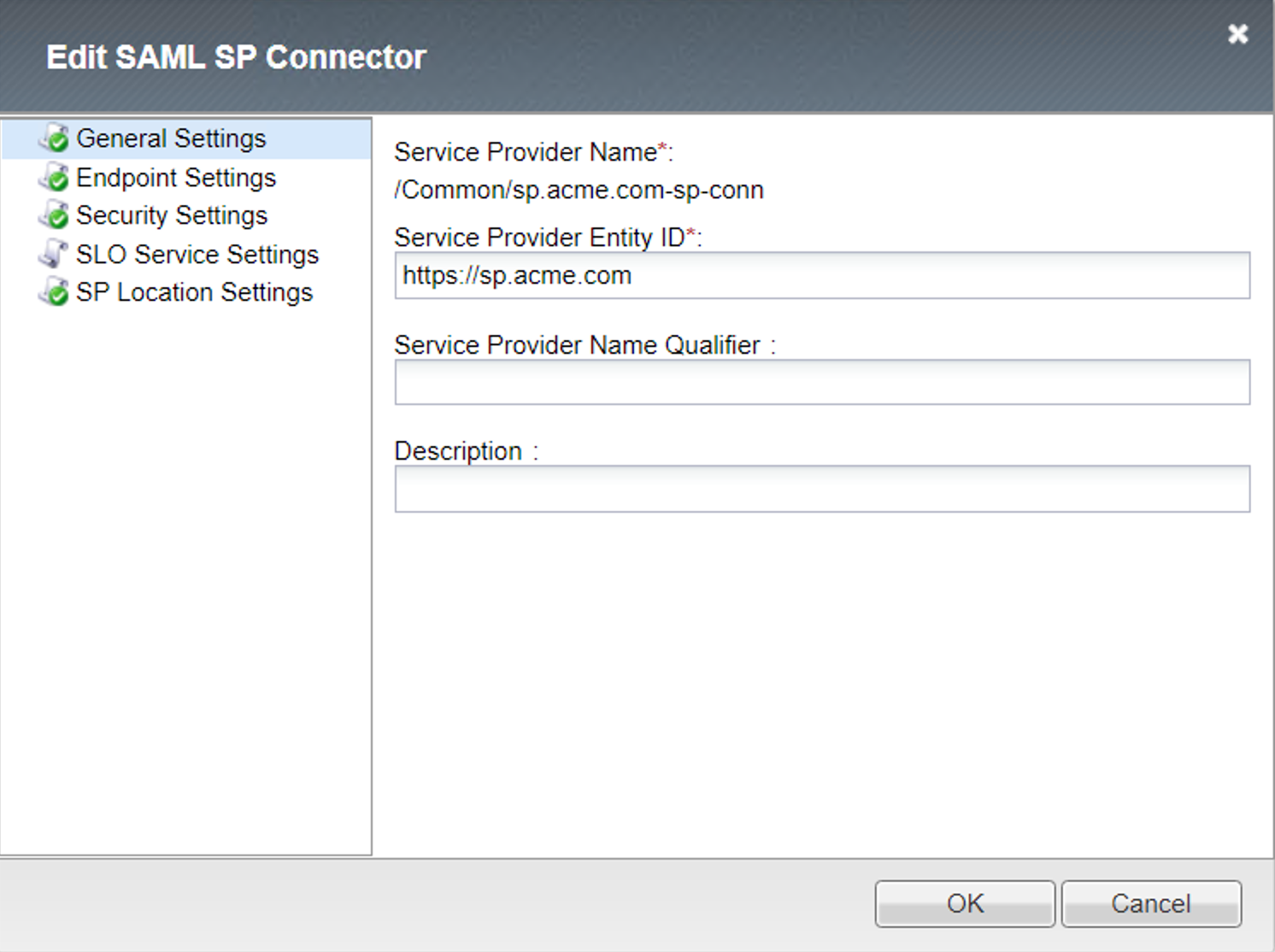
SP Connector - sp.acme.com-sp-conn¶
General Settings
Endpoint Settings
Location URL : https://sp.acme.com/saml/sp/profile/post/acs
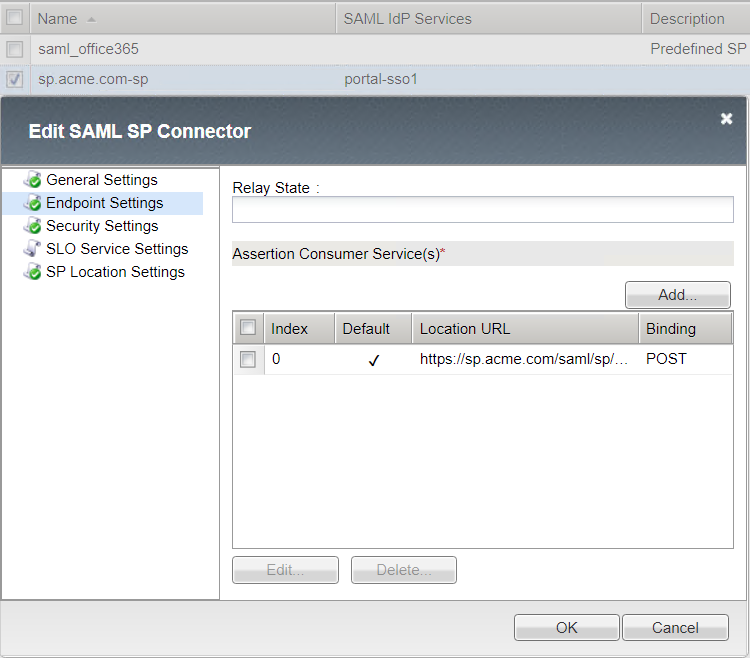
Security Settings
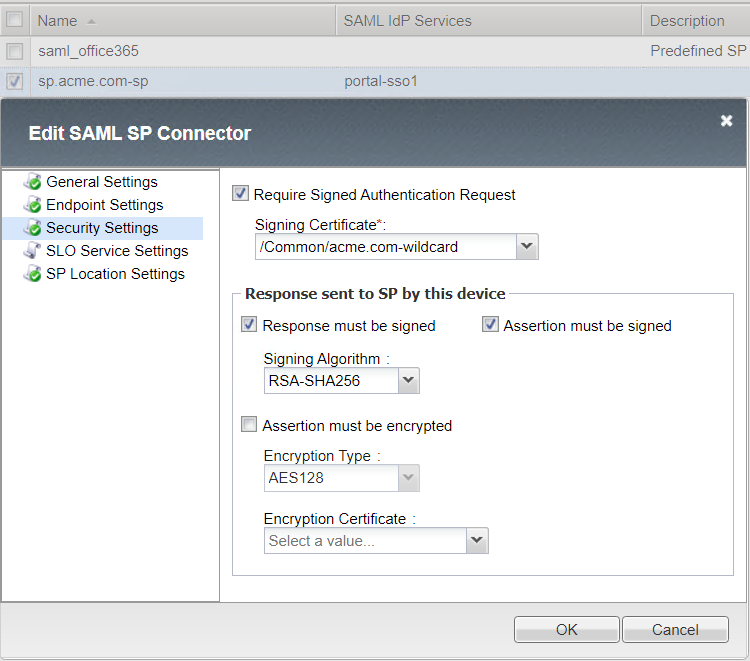
Single Logout Service Settings
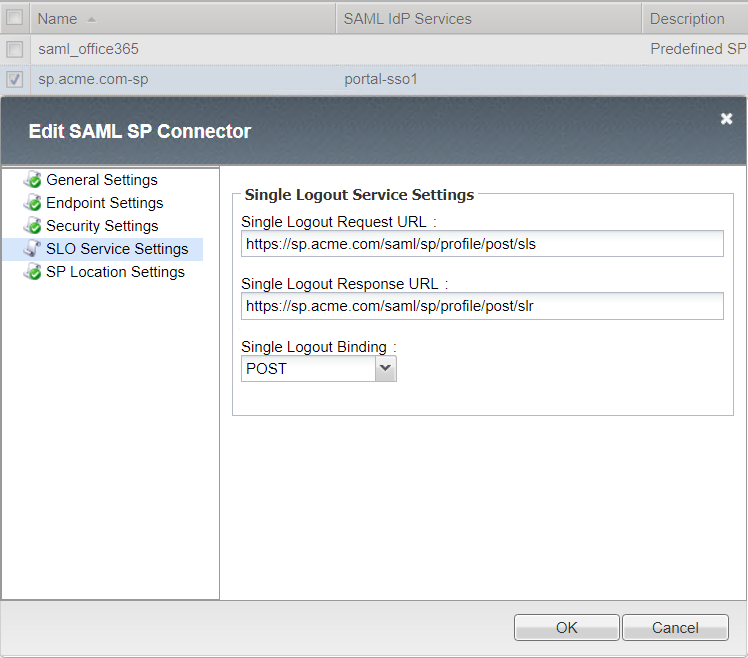
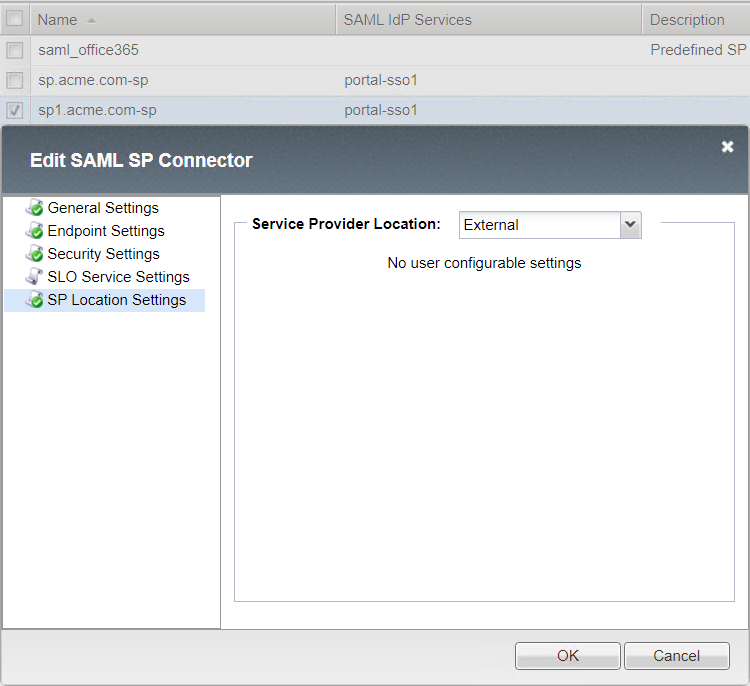
SP Location Settings
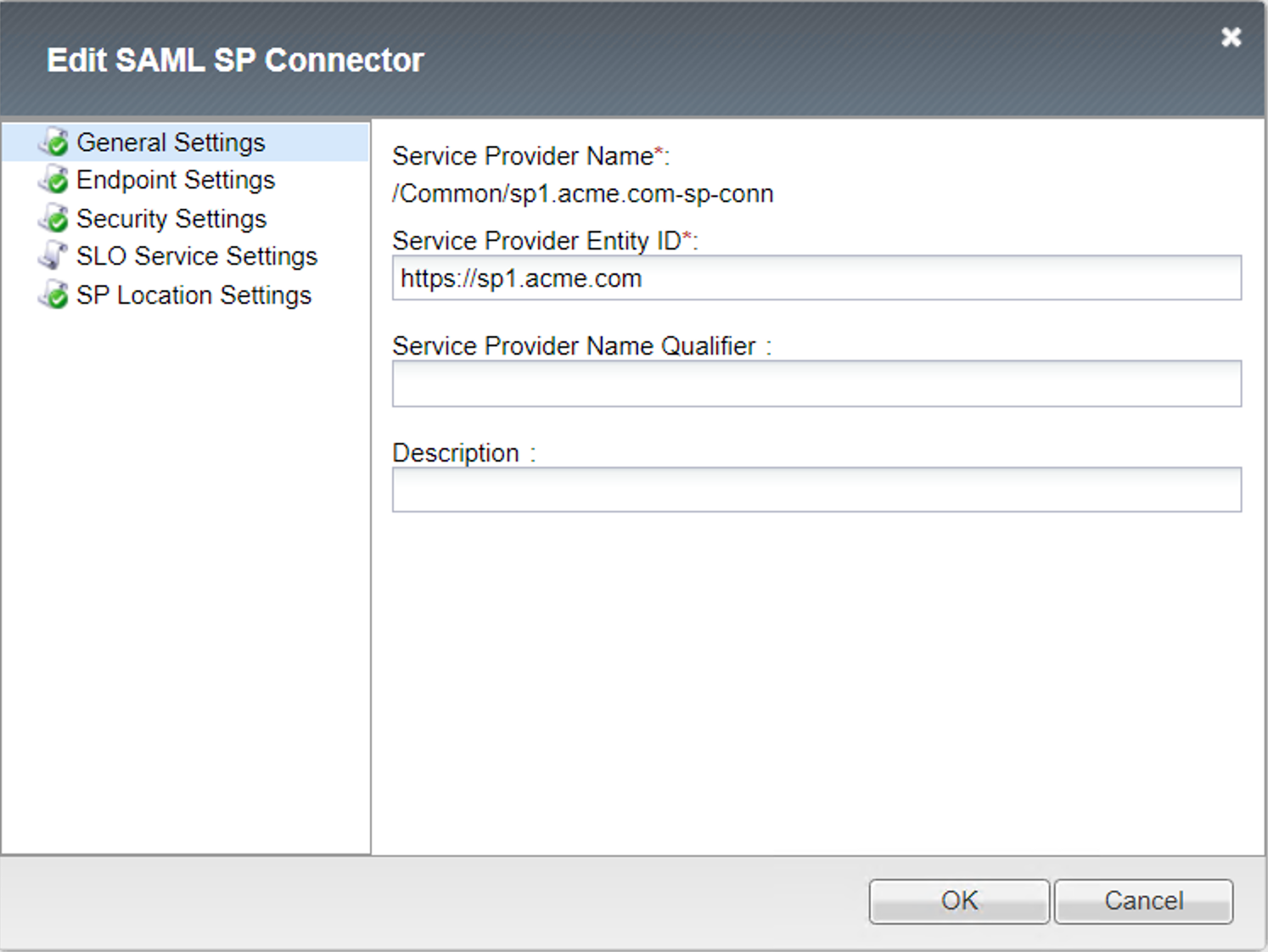
SP Connector - sp1.acme.com-sp-conn¶
General Settings
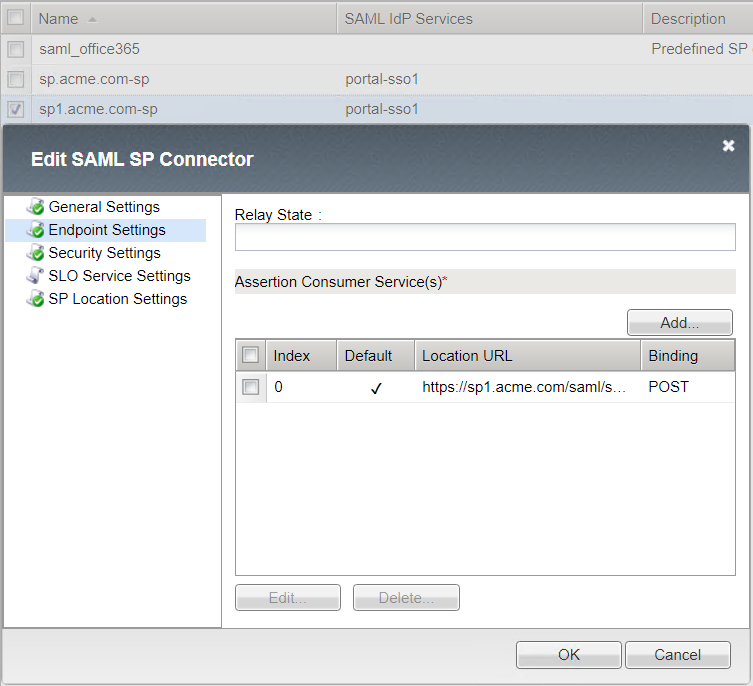
Endpoint Settings
Location URL : https://sp1.acme.com/saml/sp/profile/post/acs
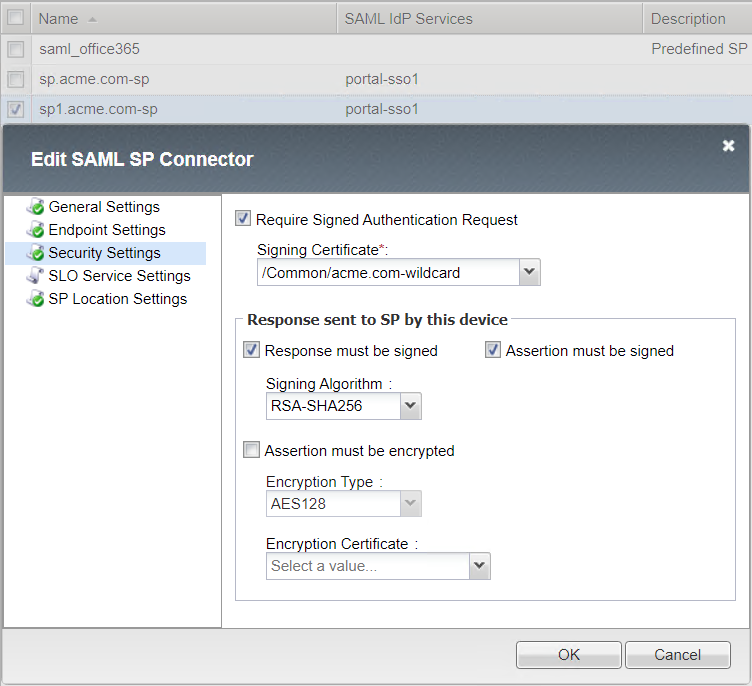
Security Settings
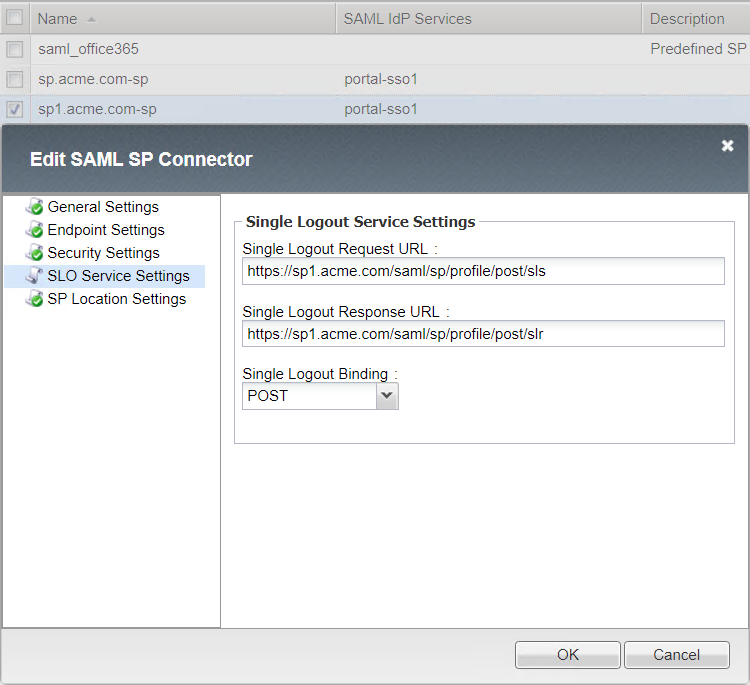
Single Logout Service Settings
SP Location Settings
User’s Perspective¶
Accessing an Application Directly¶
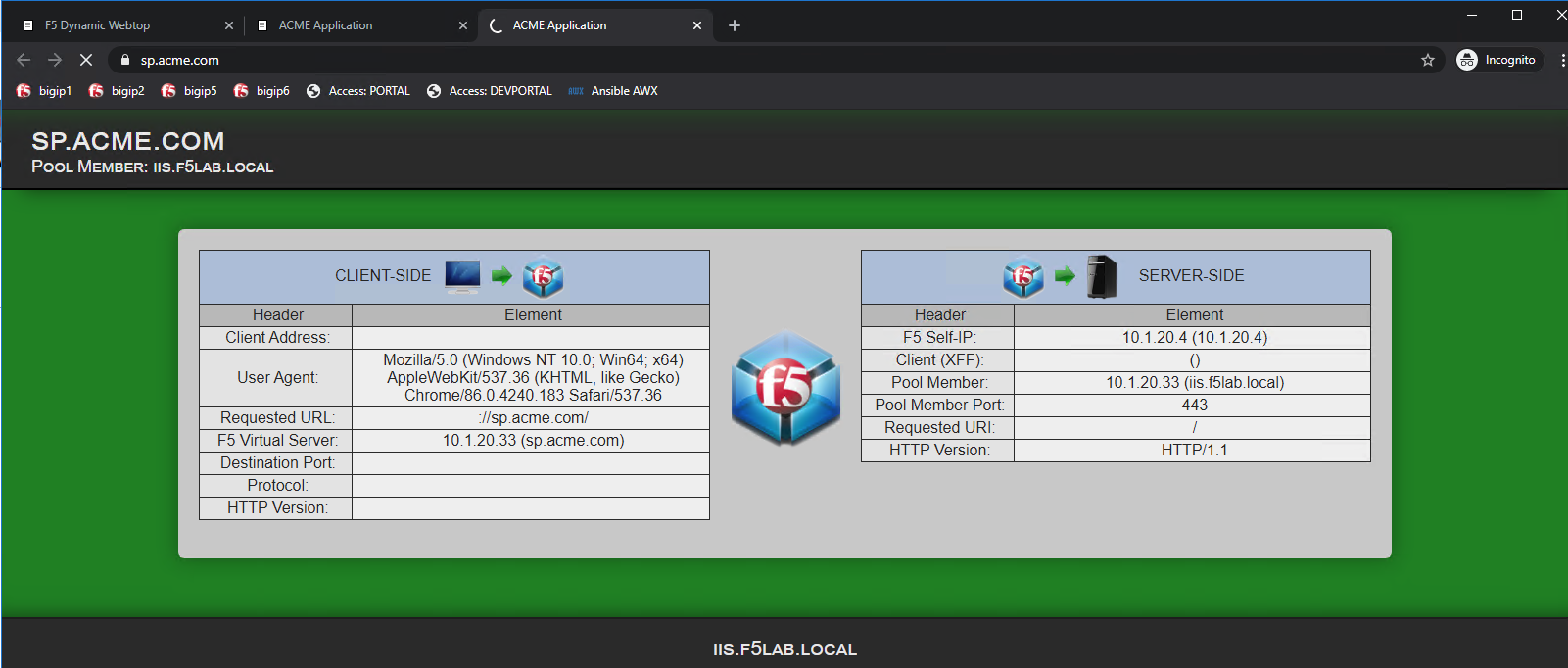
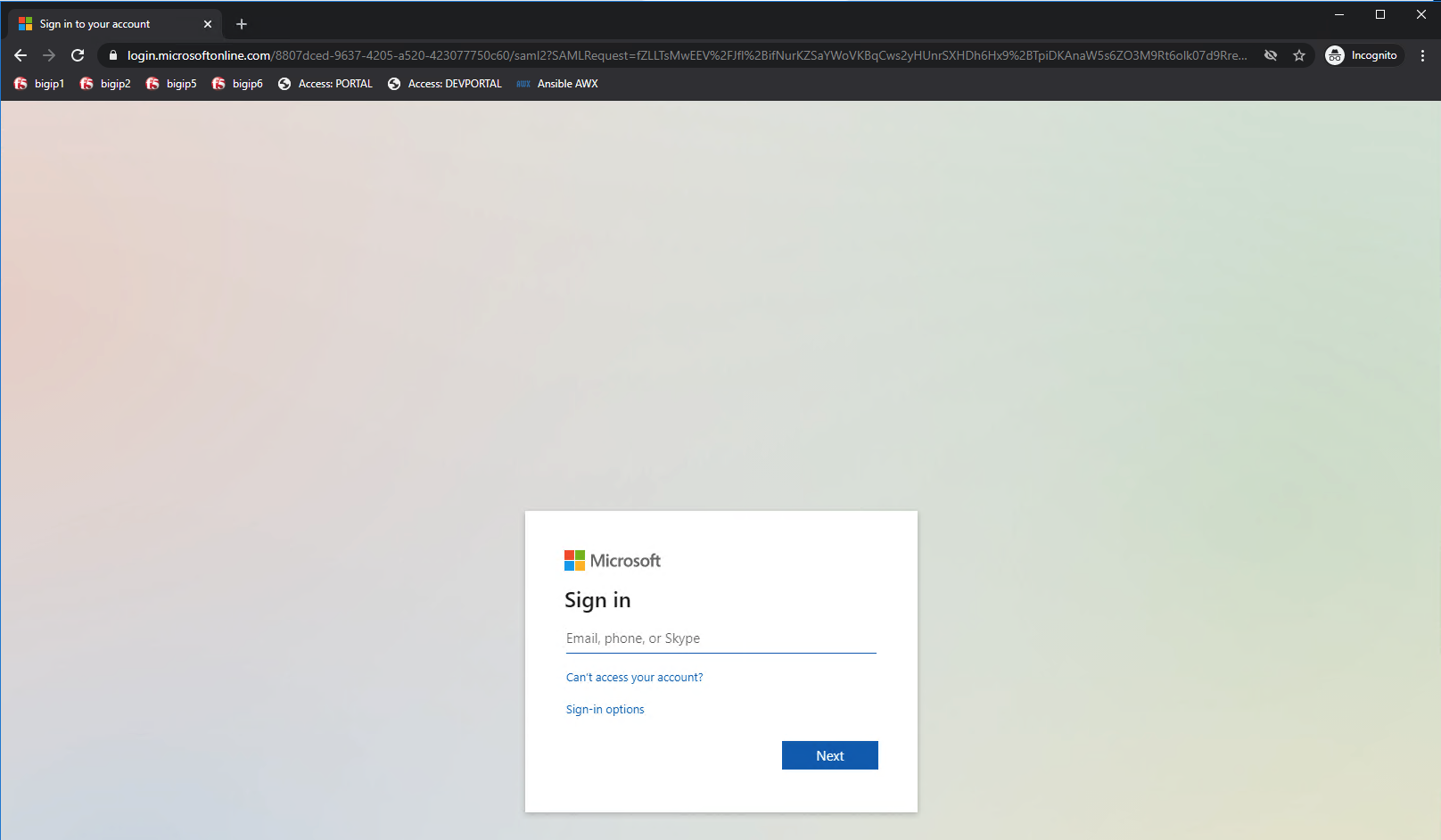
The user attempting to access https://sp.acme.com or https://sp1.acme.com is directed to portal.acme.com. Then, seamlessly redirected again to AzureAD for authentication.
Username: user1@f5access.onmicrosoft.com
Password: F5twister$
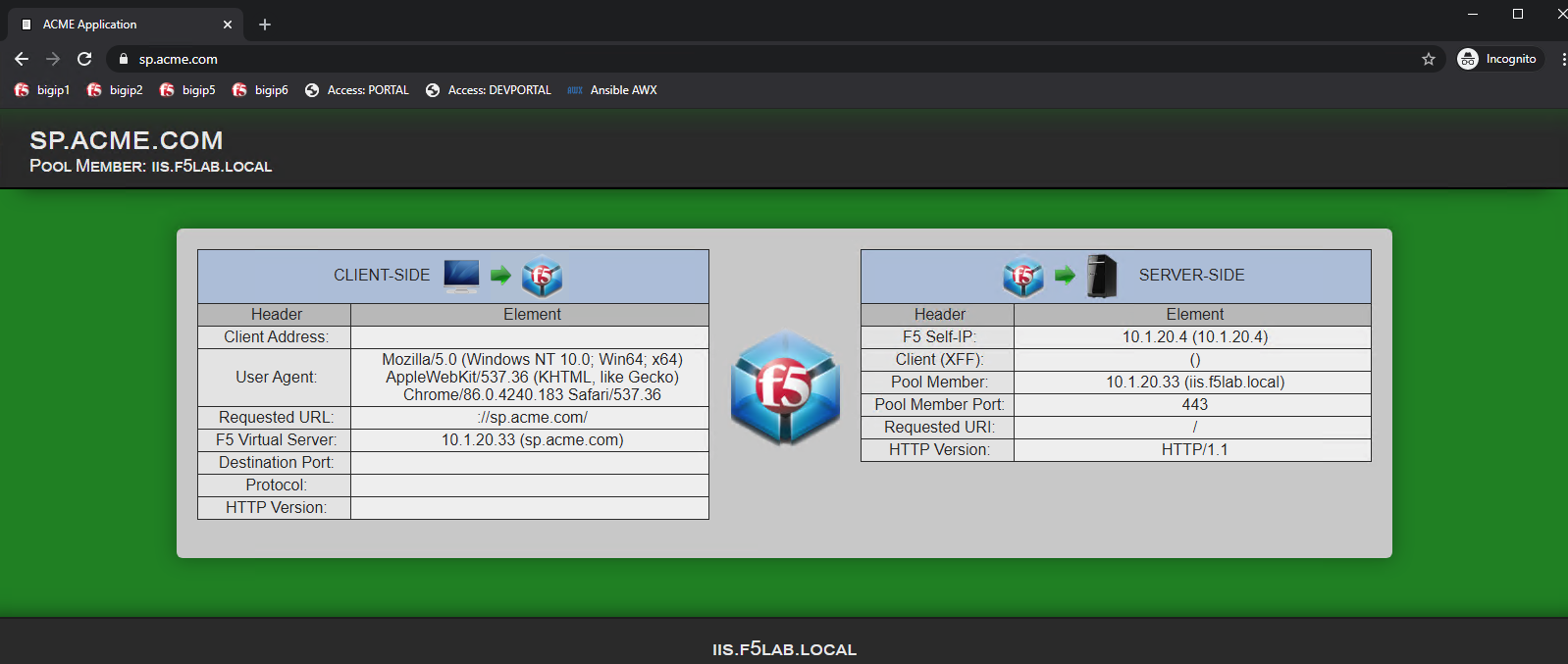
Once the user is authenticated they are transparently redirected back to the resource. In this case, it is sp.acme.com
Accessing an Application via Portal¶
Users attempting to access https://portal.acme.com are redirected to AzureAD for authentication.
Username: user1@f5access.onmicrosoft.com
Password: F5twister$

Once the user is authenticated they are transparently redirected back to the resource. In this case, it is the Webtop Portal.
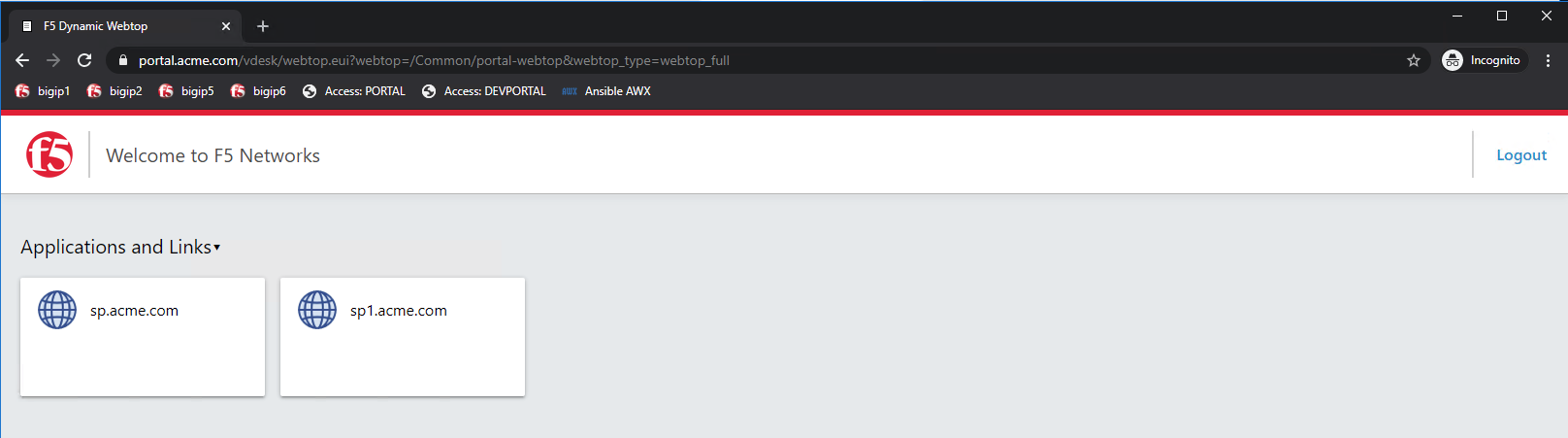
Now that the user is authenticated at the IDP, when the user attempts to access sp.acme.com they are not prompted for further logon information.