Solution 5 Policy¶
Policy Walk-Through¶
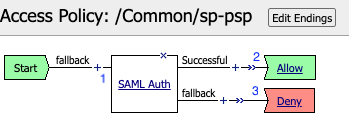
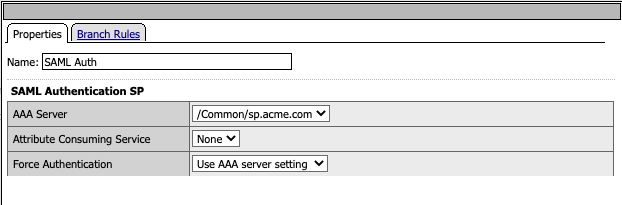
A user accesses a VIP protected by this policy they are redirected to the IDP provider Selected by the SP Service.
Upon successful authentication at the IDP, the IDP redirects the user back to the SP. The SP service consumes the Assertion. The user is granted access via the Allow Terminal
If unsuccessful, the user proceeds down the fallback branch and denied access via the Deny Terminal
Profile Settings¶
All profile settings are left the defaults
Supporting APM Objects¶
SP Service¶
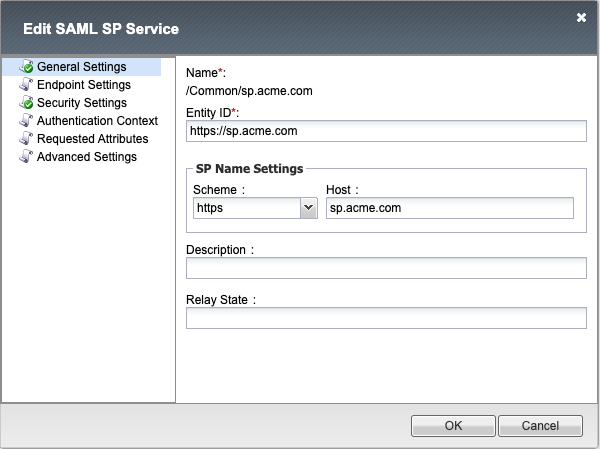
The settings below define all the components of the SP Service
General Settings
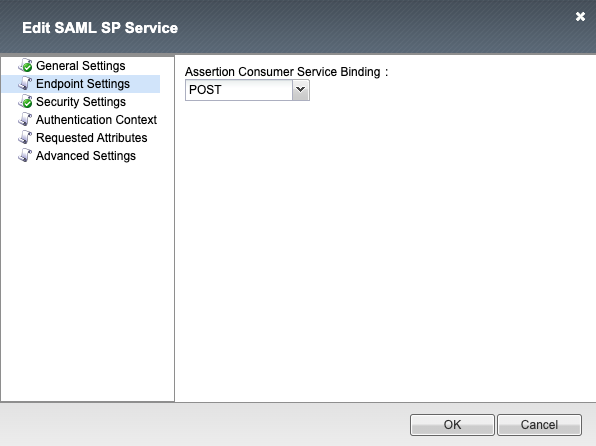
Endpoint Settings
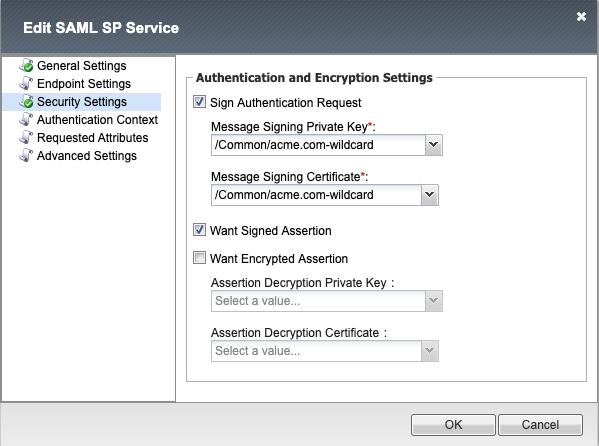
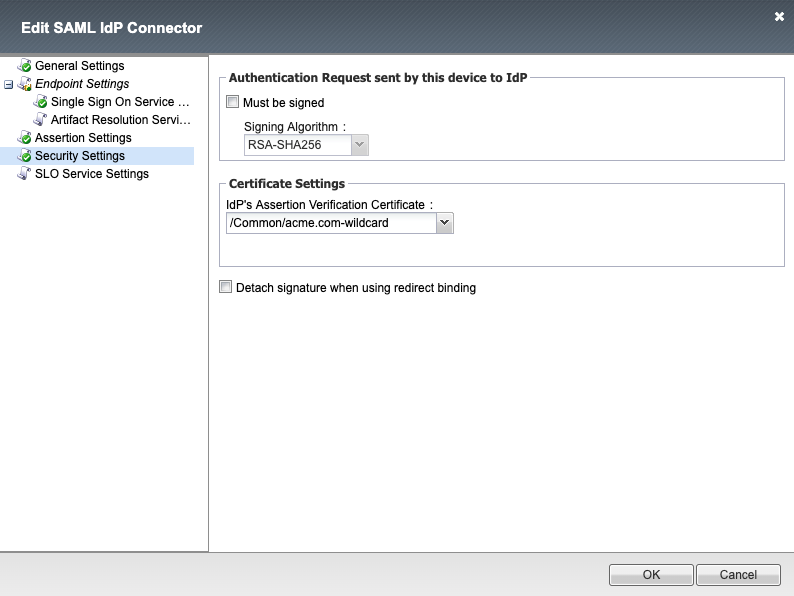
Security Settings
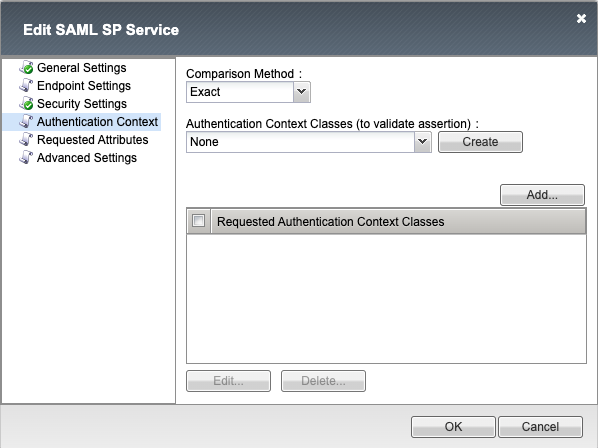
Authentication Context
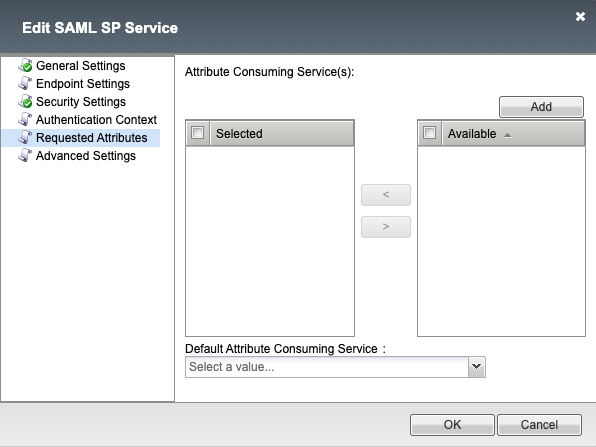
Requested Attributes
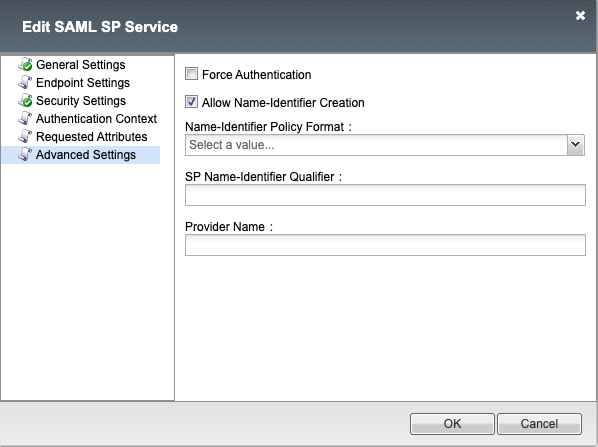
Advanced Settings
IDP Connector¶
The settings below define all the components of the IDP Connector
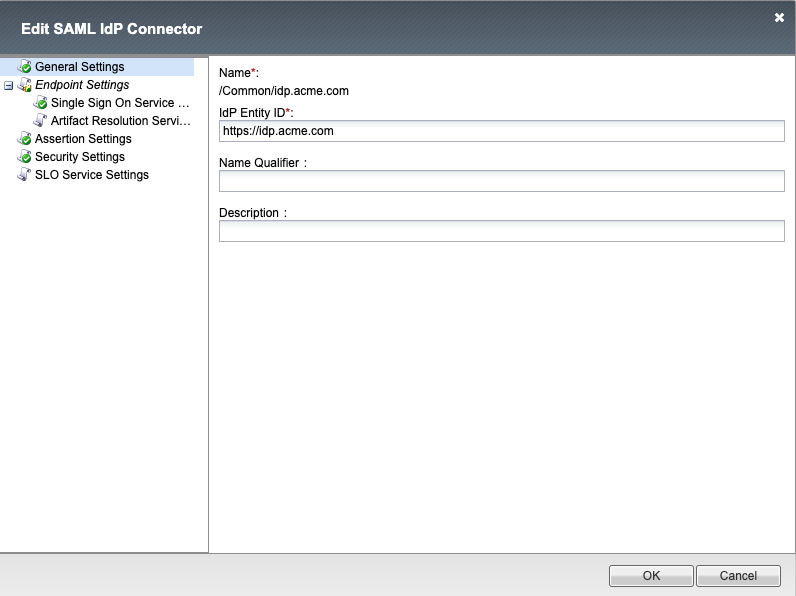
General Settings
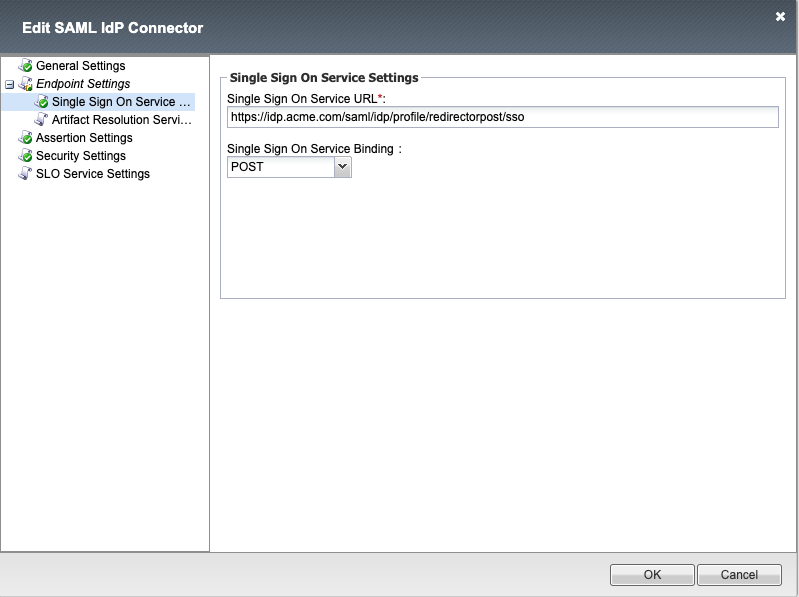
Single Sign On Service
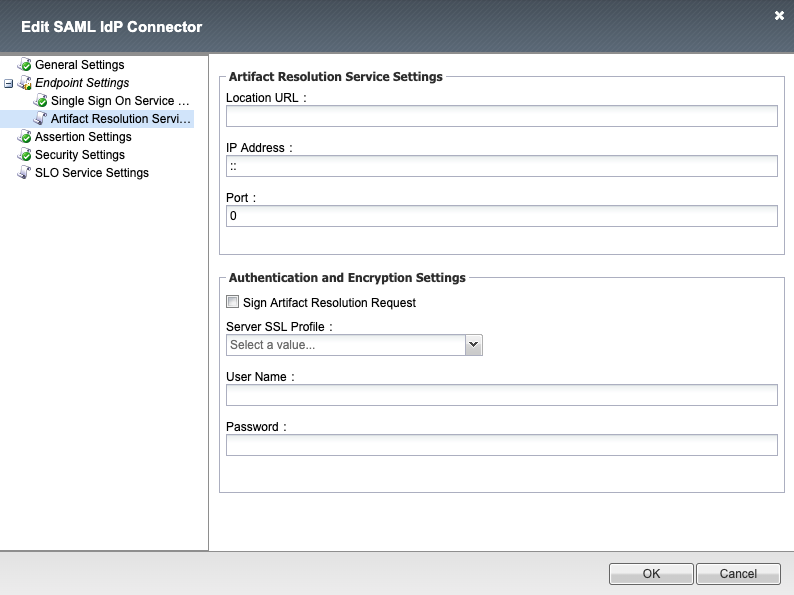
Artifact Resolution Service
Assertion Settings
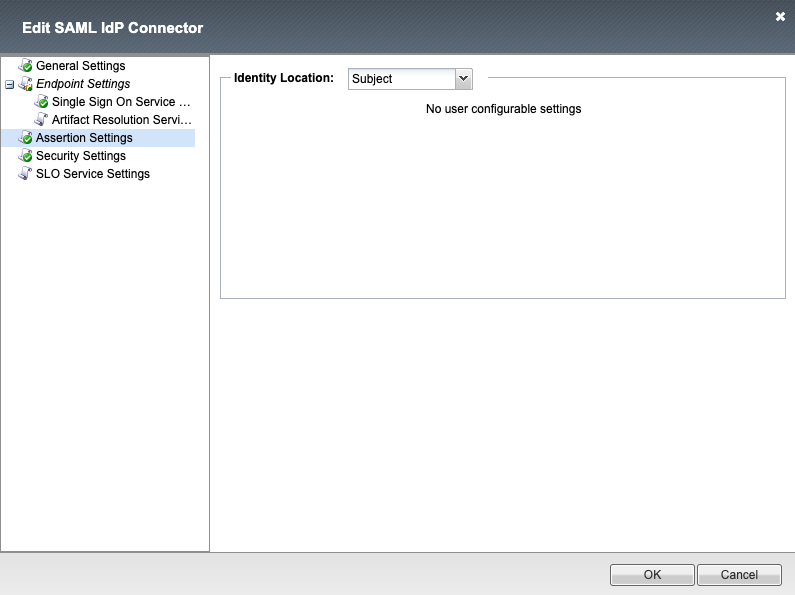
Security Settings
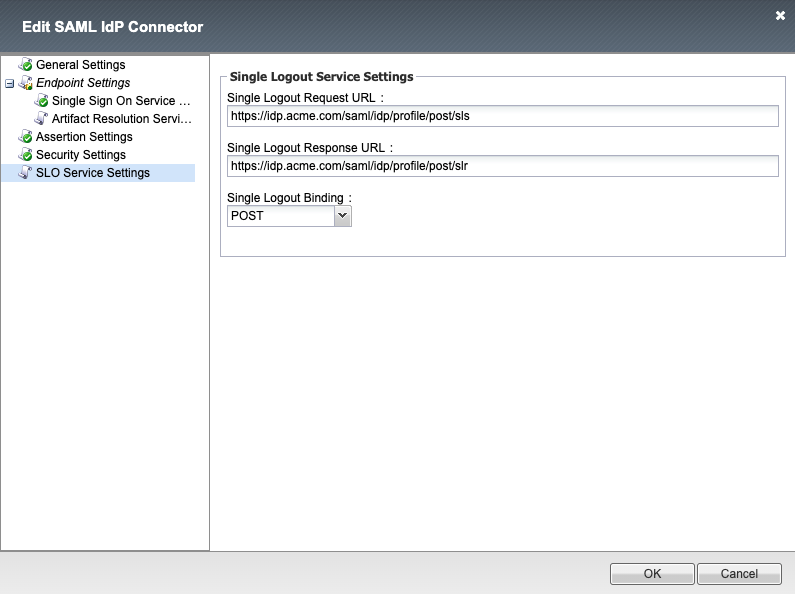
SLO Service Settings
The Policy from a user’s perspective¶
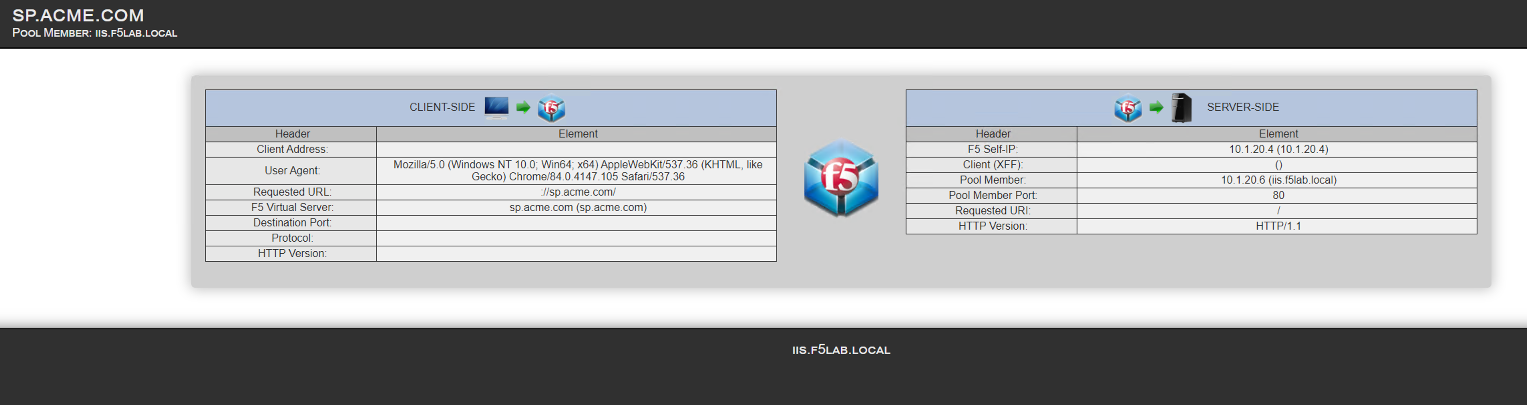
If the user attempts to access https://sp.acme.com they will be redirected to https://idp.acme.com This solution is designed to be integrated with IDP solutions deployed in the UDF Deployment