F5 BIG-IQ Centralized Management Lab Source | Edit on
Getting Started¶
Starting the Lab¶
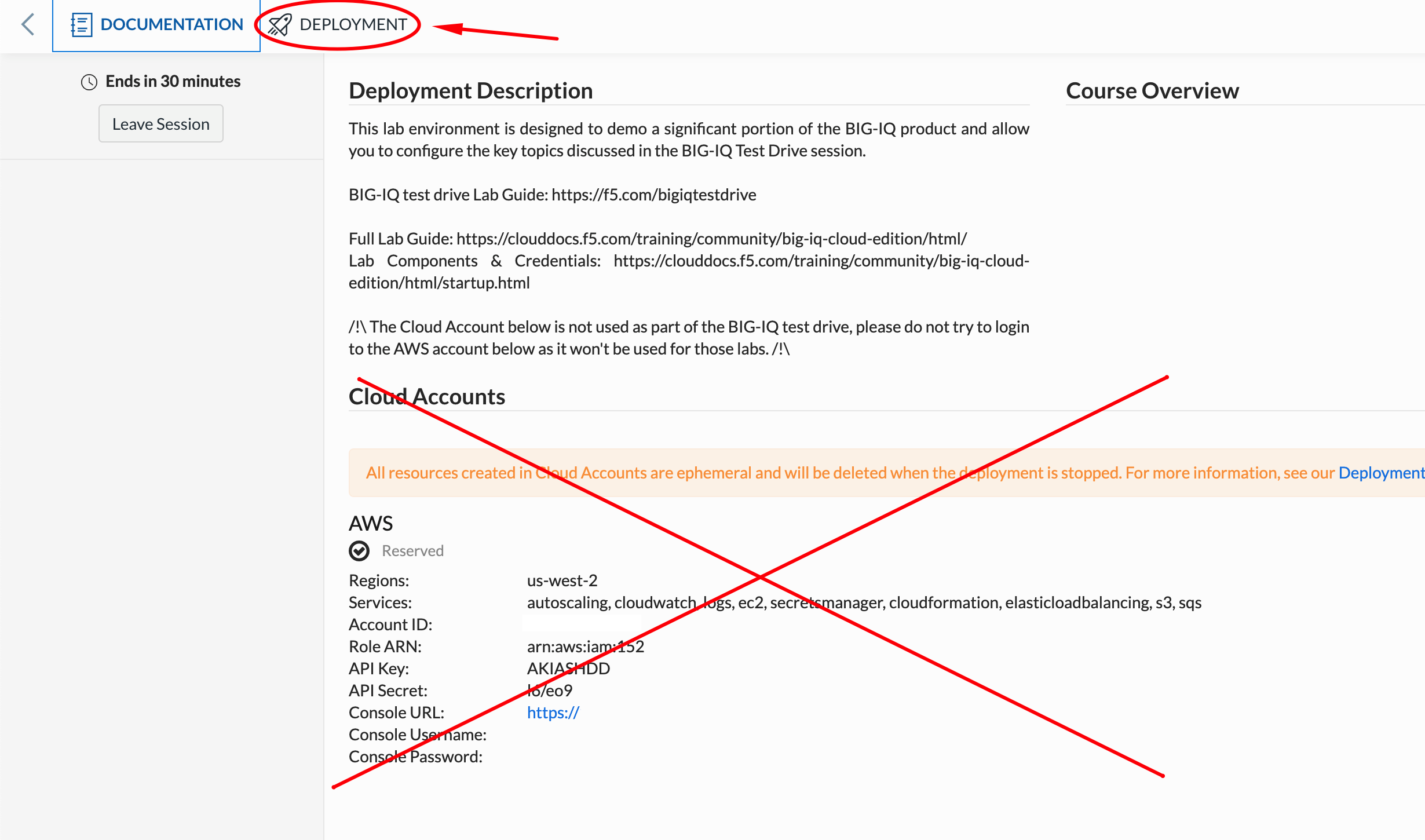
Once you connect to the UDF course portal, you will land on the Documentation tab where you can find the link to the lab guide.
Once you have the lab guide open, click on the Deployment tab to access the various systems in the lab.
In order to complete this lab, you will find 2 ways to access the different systems in this lab.
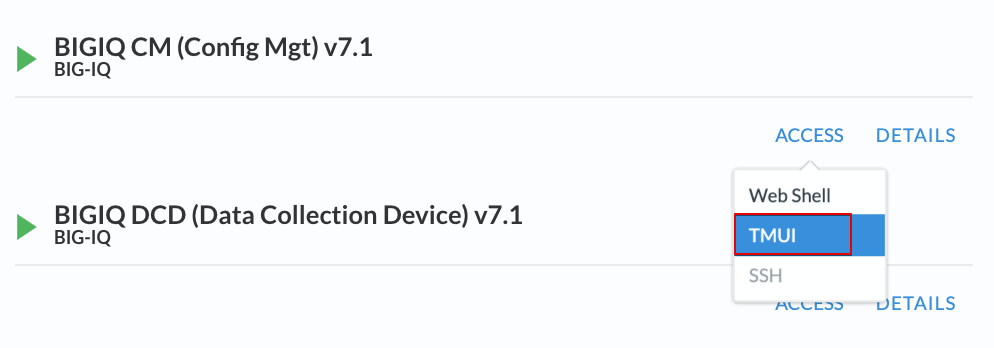
Going directly to the BIG-IQ CM or BIG-IP TMUI or WEB SHELL/SSH (RECOMMENDED).
To access the BIG-IQ directly, click on the ACCESS button under BIG-IQ CM and select TMUI. The credentials to access the BIG-IQ TMUI are
david/davidandpaula/paulaas directed in the labs.To ssh into a system, you can click on WEB SHELL or SSH (you will need your ssh keys setup in the lab environment for SSH).
You can also click on DETAILS on each component to see the credentials (login/password).
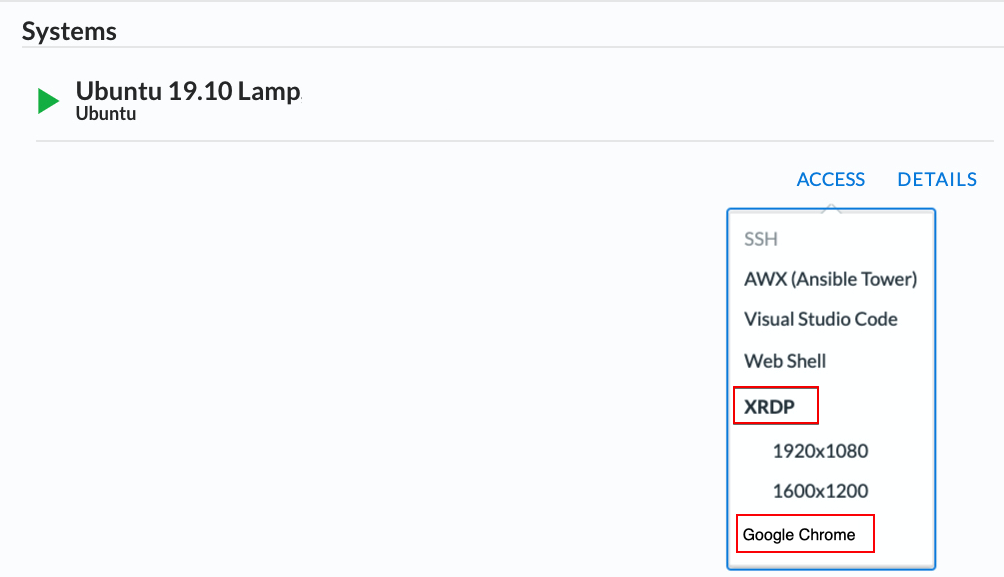
From the lab embeded Google Chrome browser.
In your lab deployment, click on the ACCESS button of the Ubuntu Lamp Server system and click on Google Chrome.
You can also use XRDP as an alternative, click on the resolution that works for your laptop. When the RDP session launches showing Session: Xorg, simply click OK, no credentials are needed. Modern laptops with higher resolutions you might want to use 1440x900 and once XRDP is launched Zoom to 200%.
BIG-IQ User Interface¶
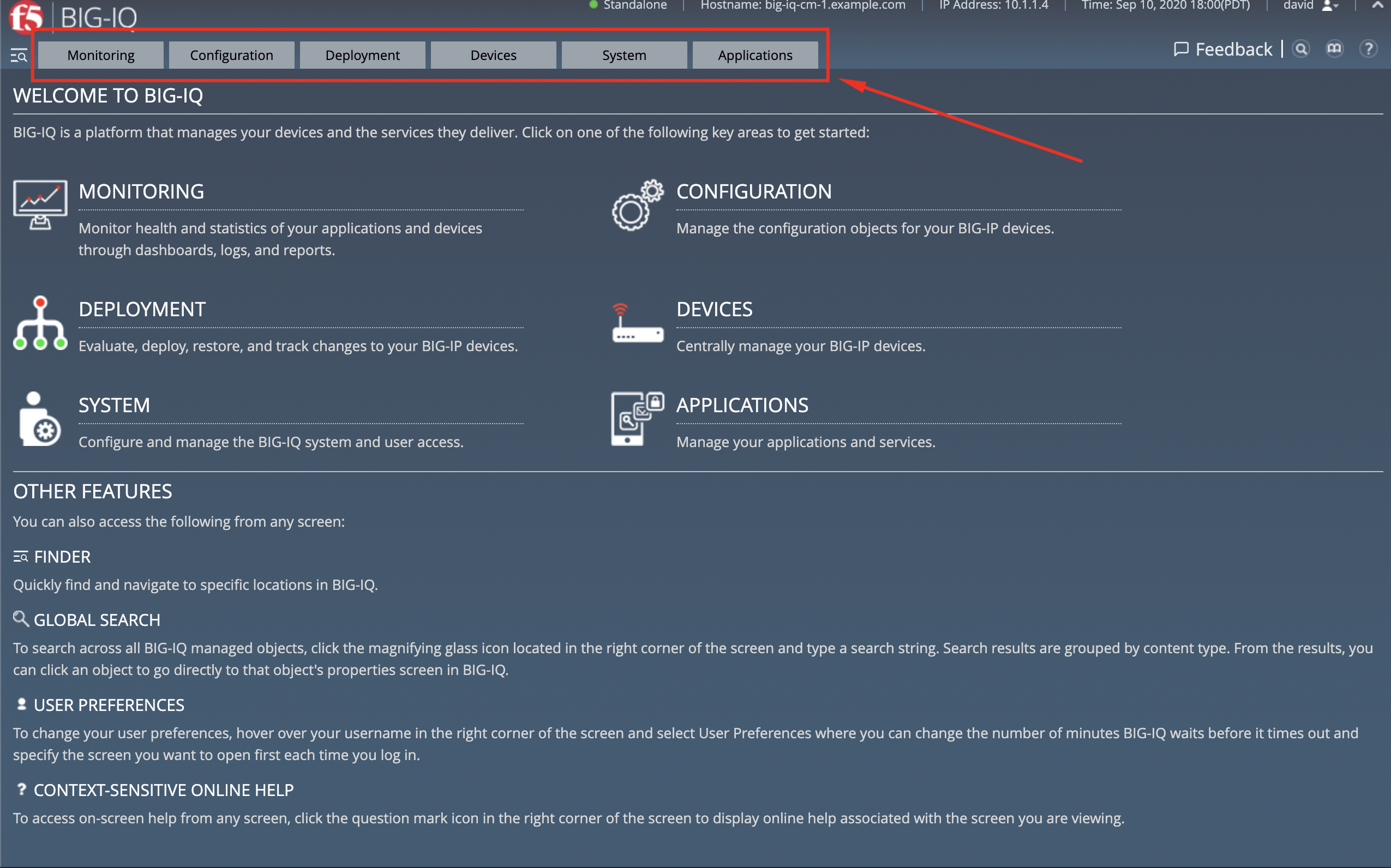
Once you connect to BIG-IQ, you can navigate in the following tabs:
- Applications - Application Management (Legacy, AS3) and Cloud Environment
- System - Manage all aspects for BIG-IQ and DCDs.
- Devices - Discover, Import, Create, Onboard (DO) and Manage BIG-IP devices.
- Deployment - Manage evaluation task and deployment for Configuration Management (none AS3)
- Configuration - ADC and Security Object Management (ASM, AFM, APM, DDOS, SSLo config/monitoring)
- Monitoring - Event collection per device, statistics monitoring, iHealth reporting integration, alerting, and audit logging.
Manage SSH Keys¶
Note
You can also use the Web Shell to get to the system’s terminals of this lab (if you use the Web Shell, login as f5student first: su - f5student)
- Generate Key pair
If you do not have an existing key pair that you wish to use for access to UDF components, you’ll need to generate a new public / private key pair. On OSX or Linux, this can be done using the ssh-keygen utility:
ssh-keygen -t rsa -b 4096
Follow the prompts to specify the location where the public and private keys will be stored, and to specify a passphrase (if desired).
- Configure SSH Client
Configure your SSH client to use your private key to authenticate when connecting to the UDF SSH endpoint. How to configure this will differ based on which client you use. Please refer to your client’s documentation for detail.
- Add Public Key to UDF
Log in to the UDF, under Tools, click on the link Manage SSH Keys.
Enter your public SSH key (typically generated with a .pub extension) and a name for it, then select Save.
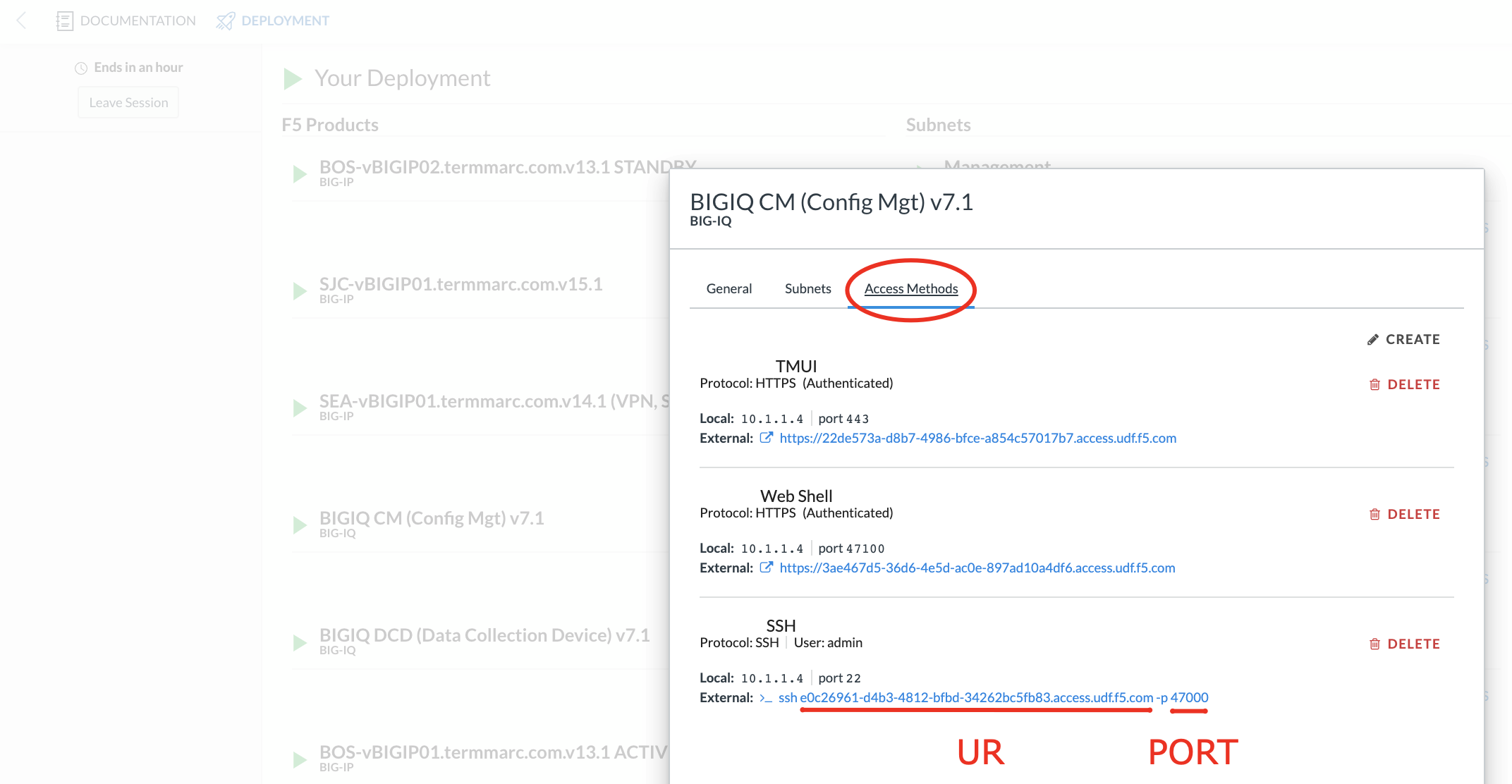
- Connect via SSH
You’ll find the URL and port on your component’s Access Methods tab. It should look similar to this:
- If using OSX or Linux, you can paste this command directly into your terminal.
- If using Windows, you’ll use the noted URL and port to configure a PuTTY session.
Note
Depending on your SSH configuration, you may additionally need to specify which public key to send. The UDF SSH handler only attempts to validate the first key sent.
SCP is similar to the above. The example below is from OSX. Note that the default SCP version on OSX uses -P instead of -p to specify port:
scp -P 47000 ubuntu-16.04.2-server-amd64.iso 2ac1868c-8e44-46af-bc66-af5f8e58c282.access.udf.f5.com:/shared/images
API Rest Client in Visual Studio Code¶
In case you need to use an API Rest Client for this lab, follow instructions to use the REST Client for Visual Studio Code.
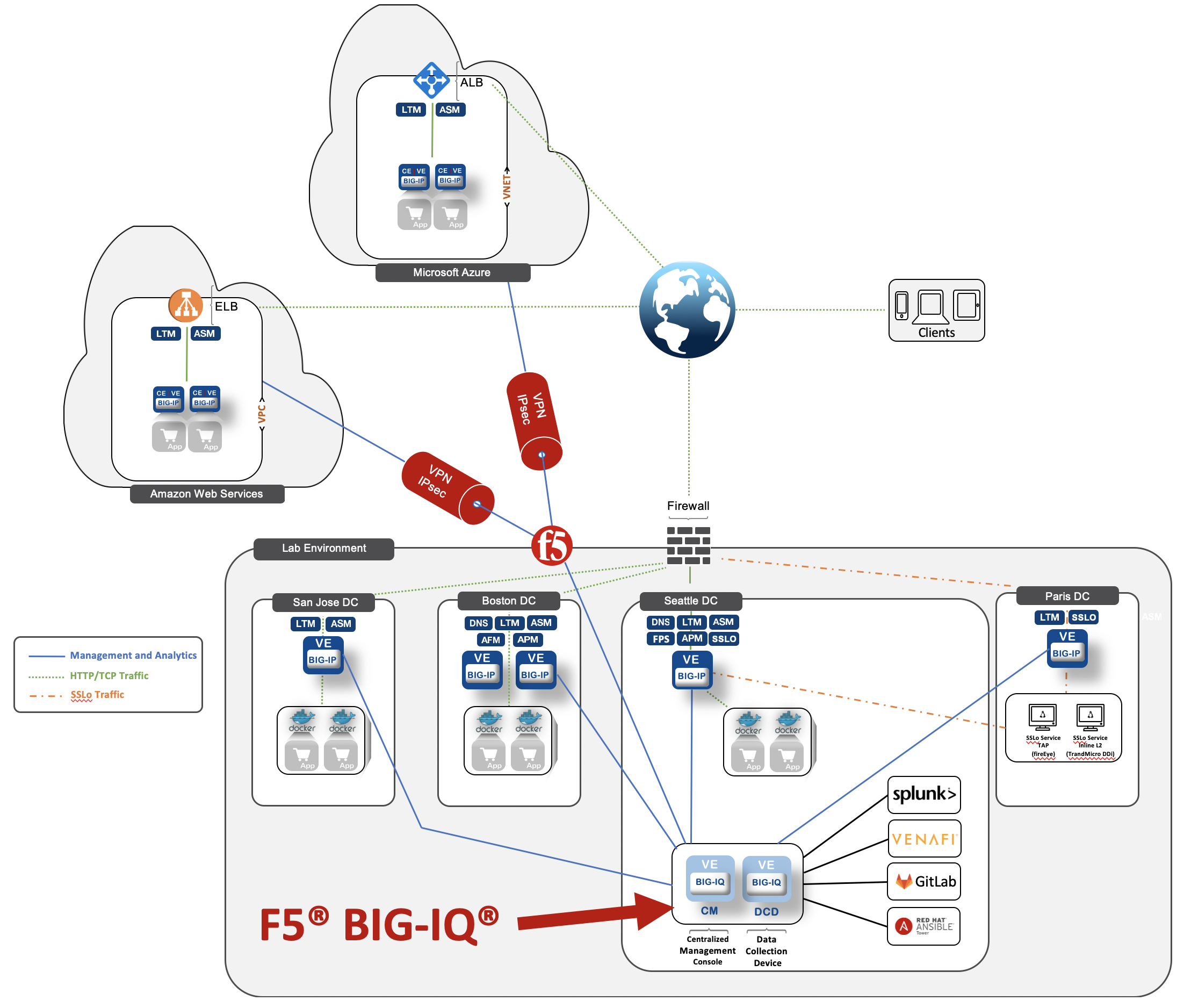
Lab Diagram¶
List of instances & Credentials¶
The following table lists the virtual appliances in the lab along with their credentials to use.
| System | Version | Description | Credentials |
|---|---|---|---|
| BIG-IQ CM 10.1.1.4 | 8.2 | Using BIG-IQ, you can centrally manage your BIG-IP devices, performing operations such as backups, licensing, monitoring, and configuration management. |
|
| BIG-IQ DCD 10.1.1.6 | 8.2 | A data collection device (DCD) is a specially provisioned BIG-IQ system that you use to manage and store alerts, events, and statistical data from one or more BIG-IP systems. | admin/purple123 |
| BIG-IP Boston 10.1.1.8/10.1.1.10 | 16.1 | HA Pair | admin/purple123 |
| BIG-IP Seattle 10.1.1.7 | 16.1 | Standalone | admin/purple123 |
| BIG-IP Paris 10.1.1.13 | 14.1 | Standalone | admin/purple123 |
| BIG-IP San Jose 10.1.1.11 | 15.1 | Standalone | admin/purple123 |
| SSLo Service TAP and L3 10.1.1.14/10.1.1.16 | Maximize infrastructure investments, efficiencies, and security with dynamic, policy-based decryption, encryption, and traffic steering through multiple inspection devices. | ubuntu/purple123 | |
| Venafi Trust Protection 10.1.1.17 | 20.1 | Manages, secures and protects keys and certificates, delivering an enterprise-grade platform that provides enterprise-wide security, operational efficiency and organizational compliance. | venafi/Purple123@123 |
| LAMP Server 10.1.1.5 | Ubuntu 19.04 |
|
f5student/purple123 |
Networks¶
- 10.1.1.0/24 Management Network
- 10.1.10.0/24 External Network
- 10.1.20.0/24 Internal Network
- 10.1.30.0/24 SSLo Inline L3 IN Network
- 10.1.40.0/24 SSLo Inline L3 OUT Network
- 10.1.50.0/24 SSLo TAP Network
- 172.17.0.0/16 Docker Internal Network
- 172.100.0.0/16 AWS Internal Network
- 172.200.0.0/16 Azure Internal Network
Application Services already deployed in this lab¶
| Applications | Application Services | BIG-IQ Template used | IP/WideIP | Location | User Access |
|---|---|---|---|---|---|
| airport_security | security_site18_seattle | AS3-F5-HTTPS-WAF-external-url-lb-template-big-iq-default-v2 | 10.1.10.118 | Seattle | Paula |
| security_site16_boston | AS3-F5-HTTP-lb-traffic-capture-template-big-iq-default-v1 | 10.1.10.116 | Boston | ||
| security_fqdn | AS3-F5-DNS-FADING-A-type-template-big-iq-default-v1 | airports.example.com | Boston | ||
| IT_apps | backend_site24tcp | AS3-F5-TCP-lb-built-in-profile-template-big-iq-v1 | 10.1.10.124 | Seattle | Paula |
| site36.example.com | Legacy App Service (no template used) | 10.1.10.136 | Boston | ||
| media.site42.example.com | Legacy App Service (no template used) | 10.1.10.142 | Seattle | ||
| finance_apps | conference_site41https conference_site41ftp | without AS3 template using API | 10.1.10.141 (https) 10.1.10.141 (ftp) | Seattle | Paul |
| mail_site40https | without AS3 template using API | 10.1.10.140 (https) | Seattle | ||
| tax_site17access | without AS3 template using API | 10.1.10.117 (https) | Seattle |
User Roles¶
| Role Name | AS3 Templates allowed | Devices allowed | Users |
|---|---|---|---|
| Administrator Role | All | All | david marco |
| Security Manager | All | All | larry chris |
| Application Creator AS3 | Allow using AS3 without Template | All | olivia |
| Application Creator Cloud |
|
All | paul |
| Application Creator VMware |
|
Boston BIG-IPs Seattle BIG-IP | paula |
Traffic Generation¶
The Ubuntu Jumphost in the lab environment has multiple cron jobs (run crontab -l to see all scripts used) that are generating traffic that populates the Monitoring tab
and Application dashboard in BIG-IQ. Note you can also use locust.io to generate HTTP traffic toward a specific virtual IP address.
Below table shows the list of Virtual Servers and Backend *Web Applications Servers* where various type of traffic
is being sent (check crontab config for more details).
Warning
Make sure the IP address on the external network 10.1.10.0/24 is defined in lab environment on the BIG-IP external interface where you are deploying the application service or VIP.
| Virtual IP addresses where the traffic generator send traffic to | |
|---|---|
| HTTP clean traffic every 5 min | 10.1.10.110-116, 10.1.10.118, 10.1.10.120, 10.1.10.123-142 |
| HTTP bad traffic every 3 hours | 10.1.10.110-116, 10.1.10.118, 10.1.10.120, 10.1.10.123-142 |
| Access traffic (class 9) | 10.1.10.117, 10.1.10.119, 10.1.10.121, 10.1.10.222 |
| DNS traffic (class 10) | 10.1.10.203, 10.1.10.204 |
Note
IPs from 10.1.10.110 to 10.1.10.142 have a corresponding FQDN named from site10.example.com to site42.example.com.
| Backend Web Applications Servers |
|---|
10.1.20.110-123
|
Miscellaneous¶
To run Kali Linux Docker Image: docker run -t -i kalilinux/kali-rolling /bin/bash (run apt-get update && apt-get install metasploit-framework -y after starting Kali Linux).
To connect to a docker instance: docker exec -i -t <container id or name> /bin/sh
3rd party authentication provider available on the Lamp Server:
| Radius |
|
| LDAP |
|
| Tacac+ |
|
Other services available on the Lamp Server:
| Google Chrome |
|
| XRDP |
|
| Visual Studio Code |
|
| AWX (Ansible Tower) |
|
| GitLab |
|
| Splunk |
|
| Locust |
|
| OWASP Zap Attack Proxy |
|
| Samba |
|
Once you are ready to start your BIG-IQ journey, go back to the BIG-IQ Test Drive Labs and start with the first Hands-On Lab.
If you are not following the BIG-IQ Test Drive labs, there are more labs to look at under BIG-IQ All Labs.