Advanced Multi-layer Firewall Protection > AFM DDos and DNS DoS Protections Source | Edit on
Simulating a TCP SYN DDoS Attack¶
The TCP SYN flood attack will attempt to DDoS a host by sending valid TCP traffic to a host from multiple source hosts. This will generate a flood of traffic that could be a surge in site visits or malicious.
- In the BIG-IP web UI, navigate to Security > DoS Protection > Device Protection.
- Expand the Network section header in the vectors list to expand the view.
- Click on TCP Syn Flood vector name.
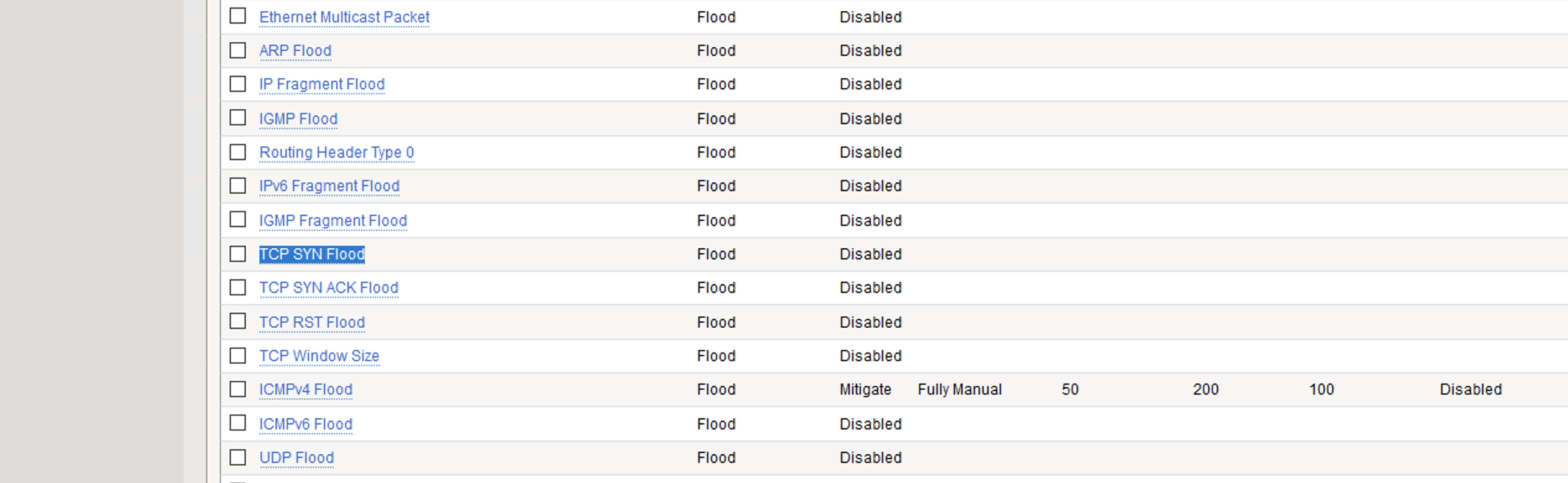
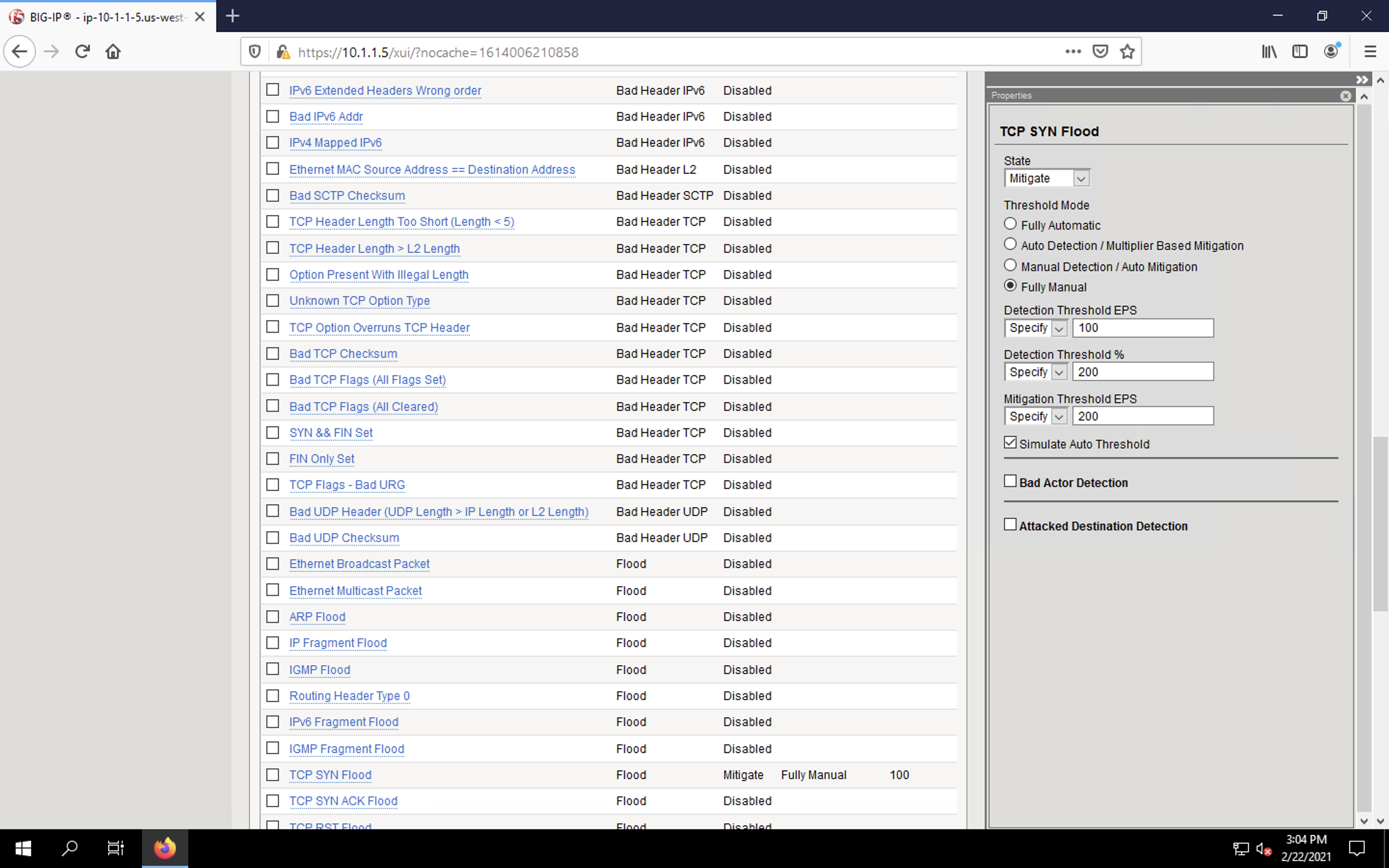
- Configure the vector with the following parameters:
- State: Mitigate
- Threshold Mode: Fully Manual
- Detection Threshold EPS: 100
- Detection Threshold Percent: 200
- Mitigation Threshold EPS: 200
- Simulate Auto Threshold: Checked
- Scroll to the top of the page and click Commit Changes to System.
- Open the BIG-IP SSH session and ensure the ltm log file is still being monitored:
tail -f /var/log/ltm
- On the attack host, launch the attack by issuing the following command on the BASH prompt:
sudo hping3 10.1.10.6 --flood --rand-source --destport 80 --syn
- You will see messages showing the attack has been detected in the /var/log/ltm output:
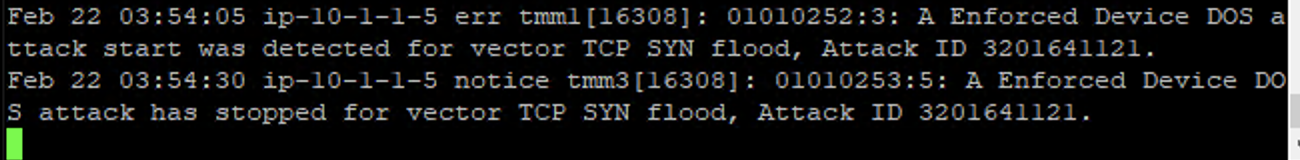
. After about 60 seconds, stop the flood attack by pressing CTRL+C. 9. Return to the BIG-IP web UI and navigate to Security > Event Logs > DoS > Network > Events. Observe the log entries showing the details surrounding the attack detection and mitigation.
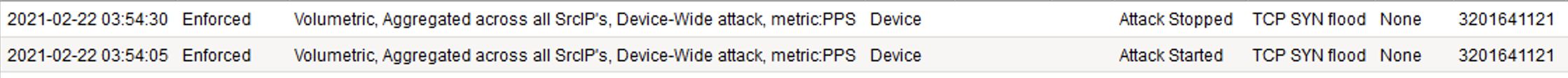
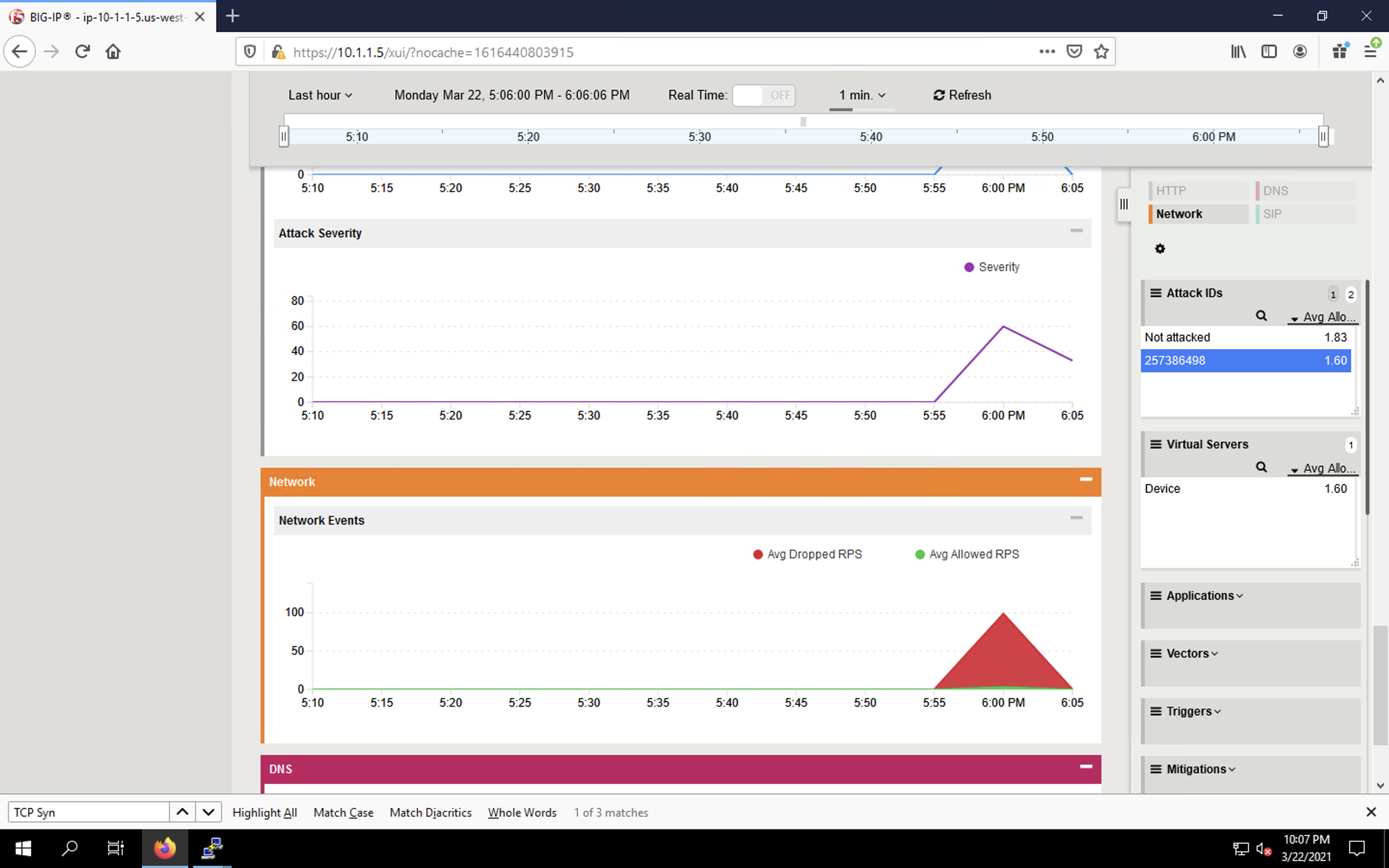
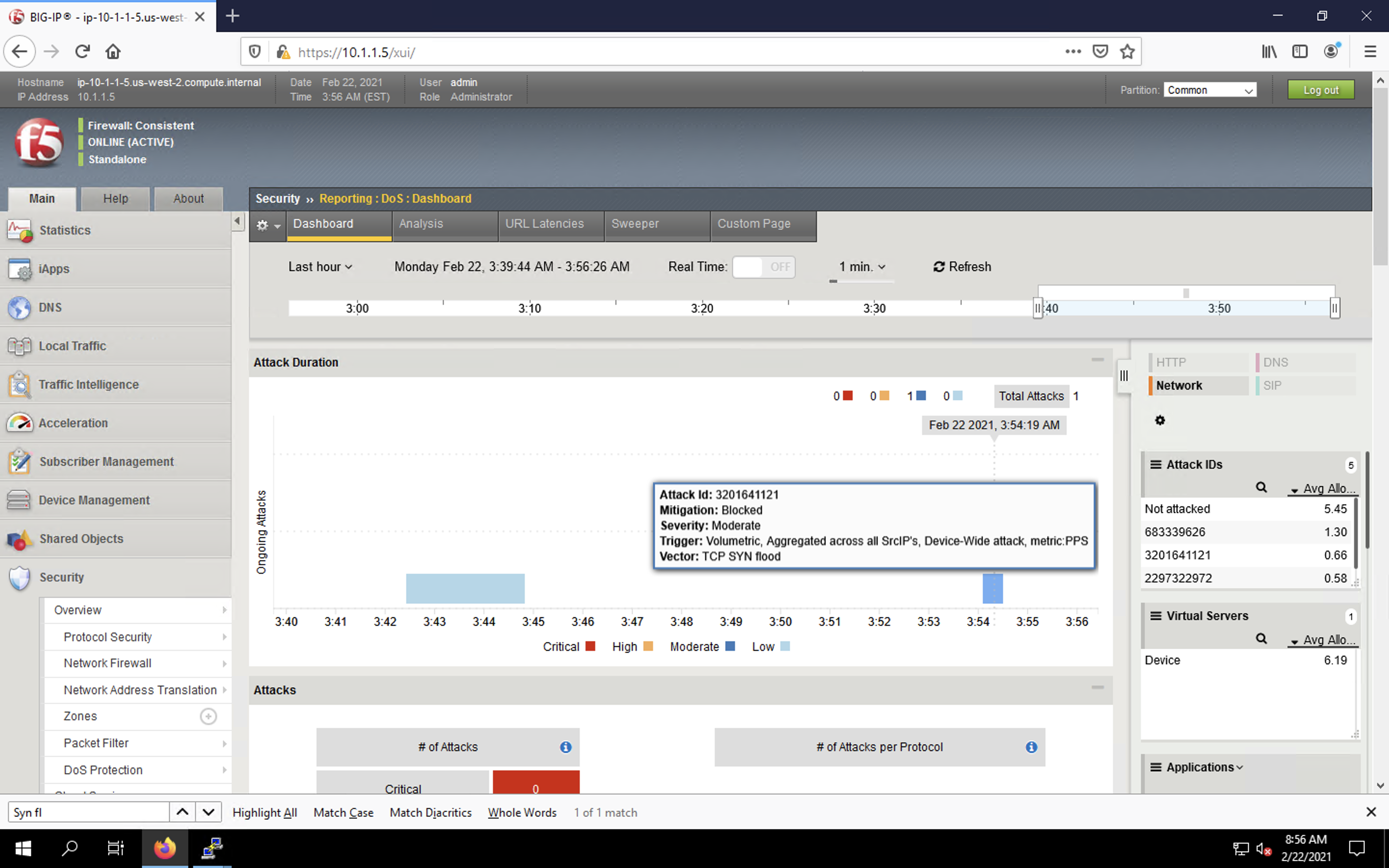
- Navigate to Security > Reporting > DoS > Dashboard to view an overview of the DoS attacks and timeline. You can select filters in the filter pane to highlight the specific attack.
- Finally, navigate to Security > Reporting > DoS > Analysis. View detailed statistics around the attack.