F5 Identity and Access Management Solutions > Archived Identity & Access Management Labs > 400 Series: Access Automation Source | Edit on
Lab 1: Creating a SAML Service Provider(SP)¶
In this lab you will learn how to work with the SP Service and IdP Connector.
Task 1 - Access the Lab Environment¶
To access your dedicated student lab environment, you will need a web browser and Remote Desktop Protocol (RDP) client software. The web browser will be used to access the Unified Demo Framework (UDF) Training Portal. The RDP client will be used to connect to the jumphost, where you will be able to access the BIG-IP management interfaces (HTTPS, SSH).
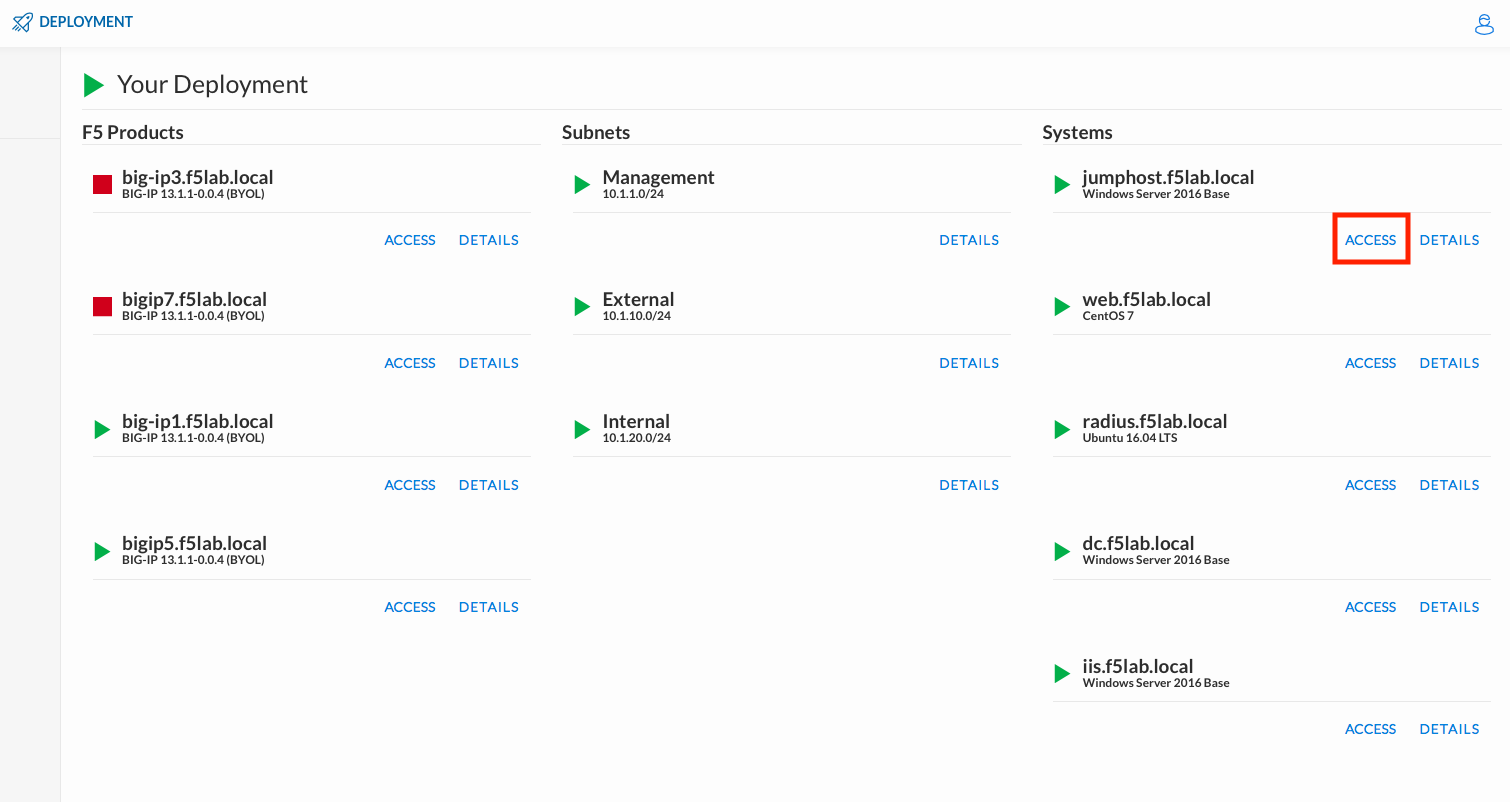
Click DEPLOYMENT located on the top left corner to display the environment
Click ACCESS next to jumphost.f5lab.local
Select your RDP resolution.
The RDP client on your local host establishes a RDP connection to the Jump Host.
Login with the following credentials:
- User: f5lab\user1
- Password: user1
Task 2 - Import Postman Collections¶
From the Jumphost, open Postman via the desktop shortcut or toolbar at the bottom
Note
Dismiss any prompts to update Postman.

Click Yes if prompted for “Do you want to allow this app to make changes to your device?”
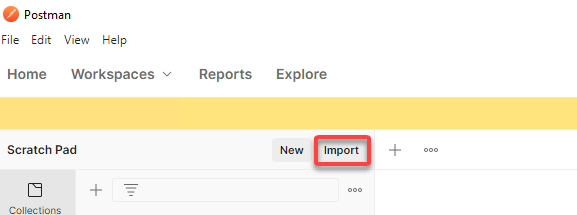
Click Import located on the Scratch Pad menu bar
Click Upload Files
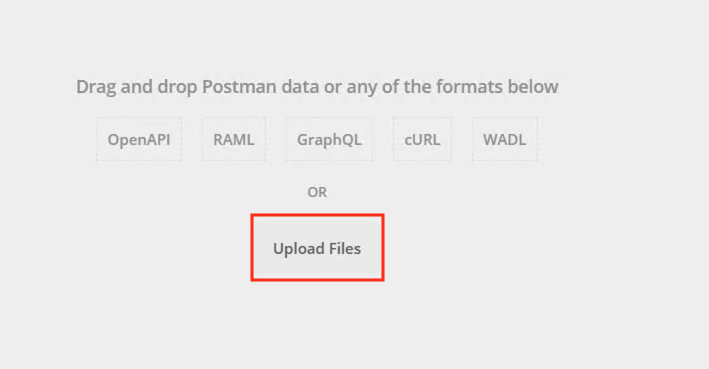
Navigate to C:\access-labs\class4\module1\student_files, select student-class4-module1-lab1.postman_collection.json, and click Open
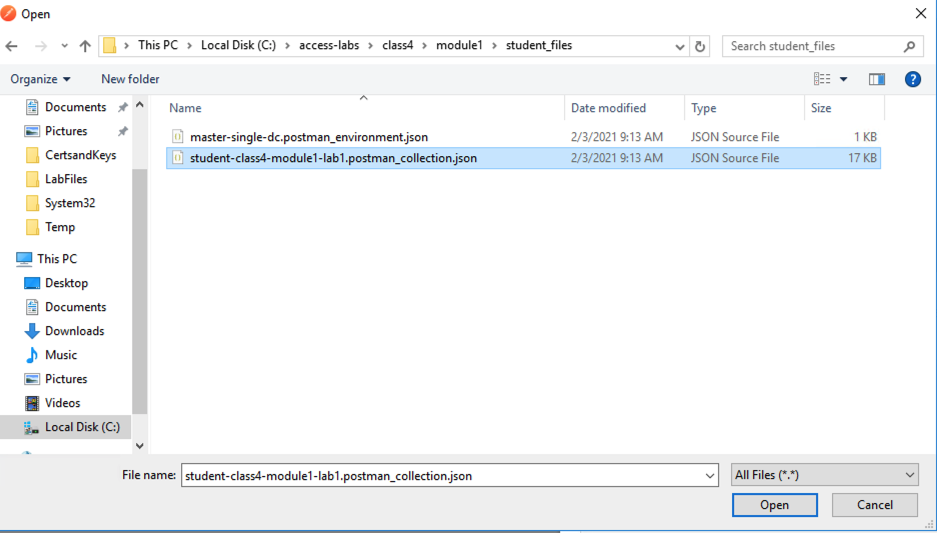
Click Import
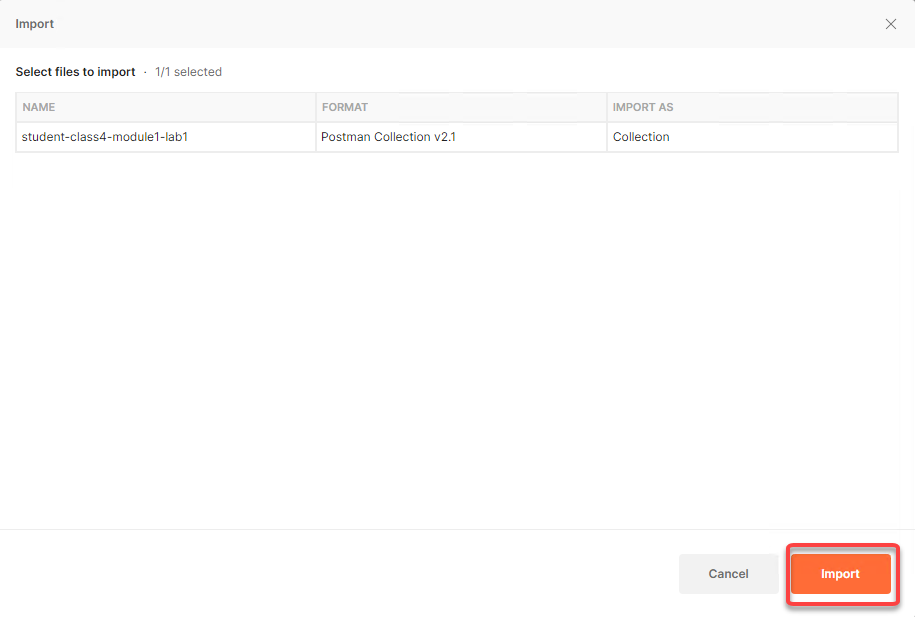
Click on Collections from the left menu and a collection called student-class4-module1-lab1 will be listed
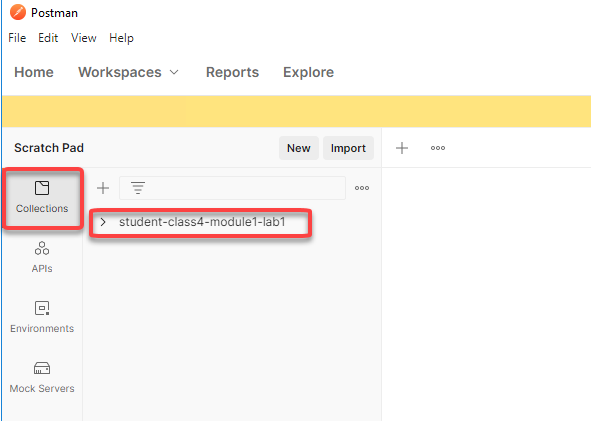
Task 3 - Import IDP Signing Certificate¶
Expand the student-class4-module1-lab1 collection to see the subfolders and requests.
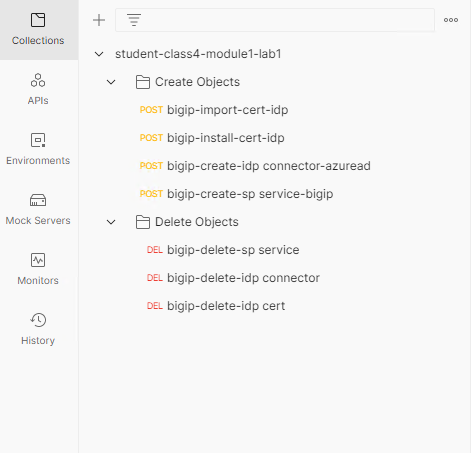
Select the bigip-import-cert-idp request.
Notice the request endpoint is /mgmt/shared/file-transfer/uploads. This endpoint allows us to upload files to the /var/config/rest/downloads directory on the BIG-IP.
Note
If you are unfamiliar with Postman, the information in curly braces are variables that have been defined inside the collection. If you wish to see the variable values simply click the three dots on the collection that allows you display more options. Click Edit and then Variables.
Click Body to display what will be passed in the POST request
Note
The request contains only the PEM formated certificate of our AzureAD Identity Provider.
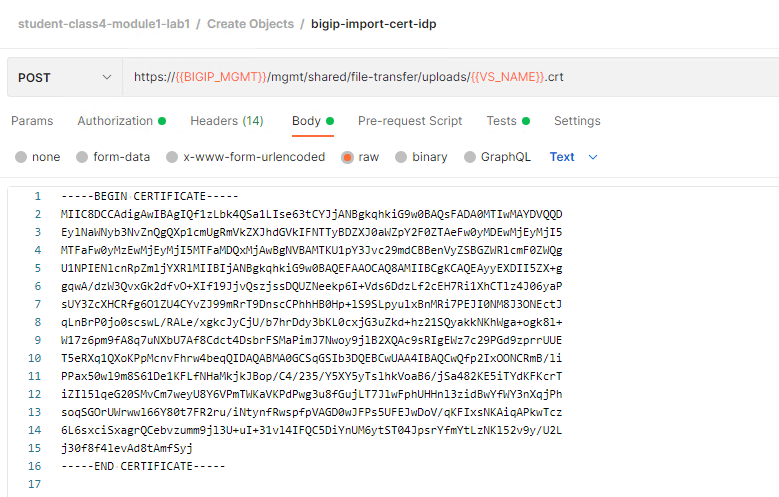
Click the blue Send button in the upper right corner
In the response body we see where the file is stored and its file name.
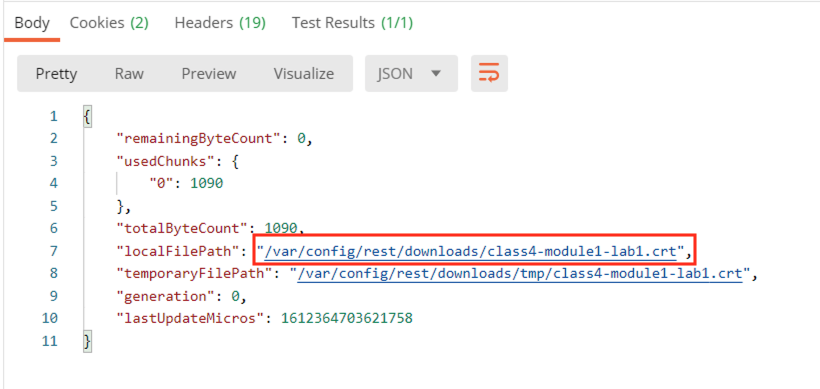
Select the bigip-install-cert-idp request.
Examine the body of this request. This request installs the certificate we previously uploaded to the BIG-IPs crypto store.
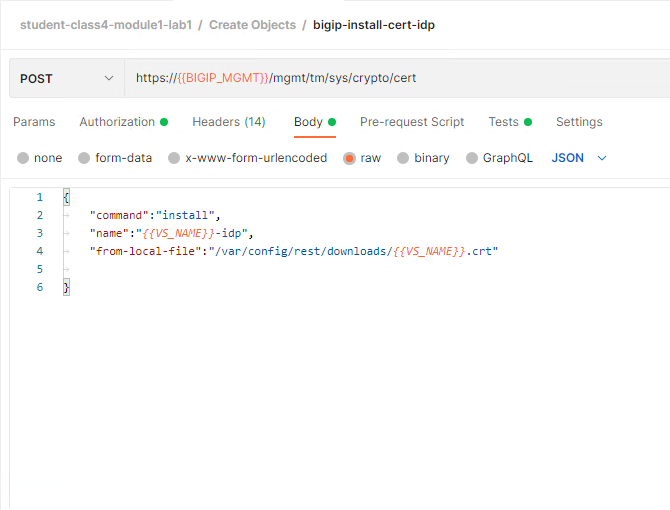
Click the blue Send button in the upper right corner
In the response body we a see certificate named class4-module1-lab1-idp has been installed to the crypto store.
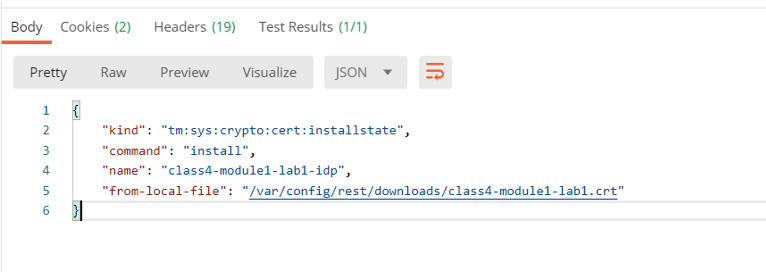
Task 4 - Create an SAML IDP Connector¶
In order to create an SP service the IDP Connector must exist. This is because the SP Service endpoint contains the binding information to the IDP Connector.
Select the bigip-create-idp connector-azuread request
Notice the request endpoint is /mgmt/tm/apm/aaa/saml-idp-connector/.
Click Body to display what will be passed in the POST request. The body contains all the necessary setting in order to integrate with AzureAD.
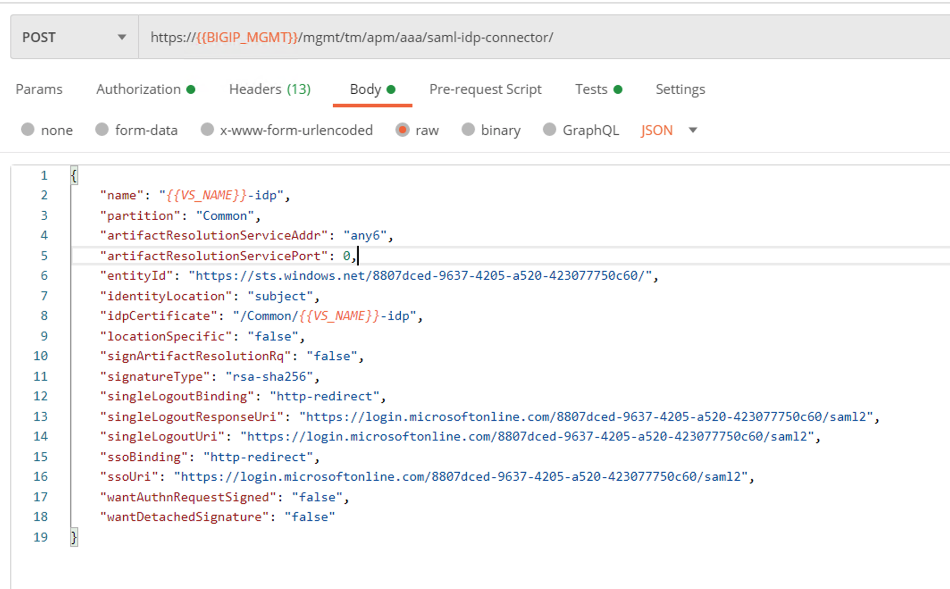
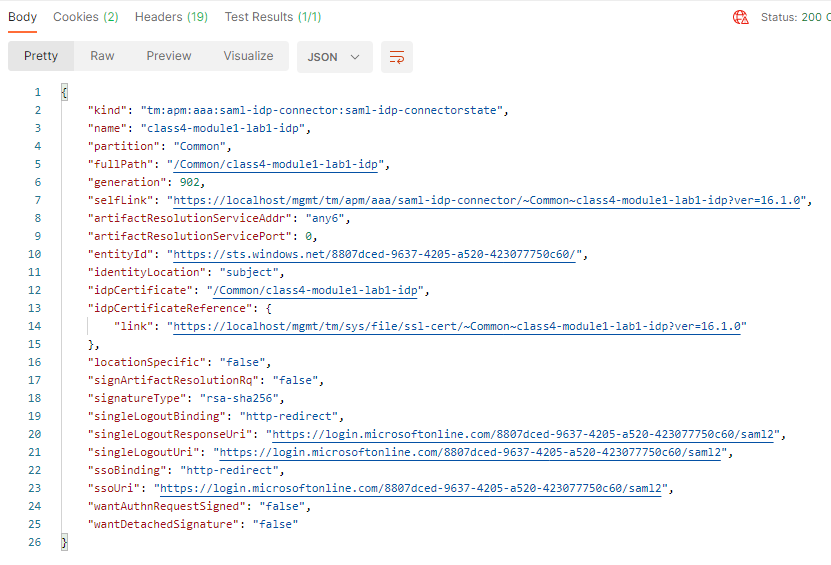
Click the blue Send button in the upper right corner
The response body contains all of the information related the connector and links to other endpoints that are related to this connectors configuration.
Task 5 - Create an SAML SP Service¶
Select the bigip-create-sp service-bigip
Notice the request endpoint is /mgmt/tm/apm/aaa/saml/.
Click Body to display what will be passed in the POST request. The body contains all the necessary setting for the SP service, plus a binding to the IDP Connector we just created.
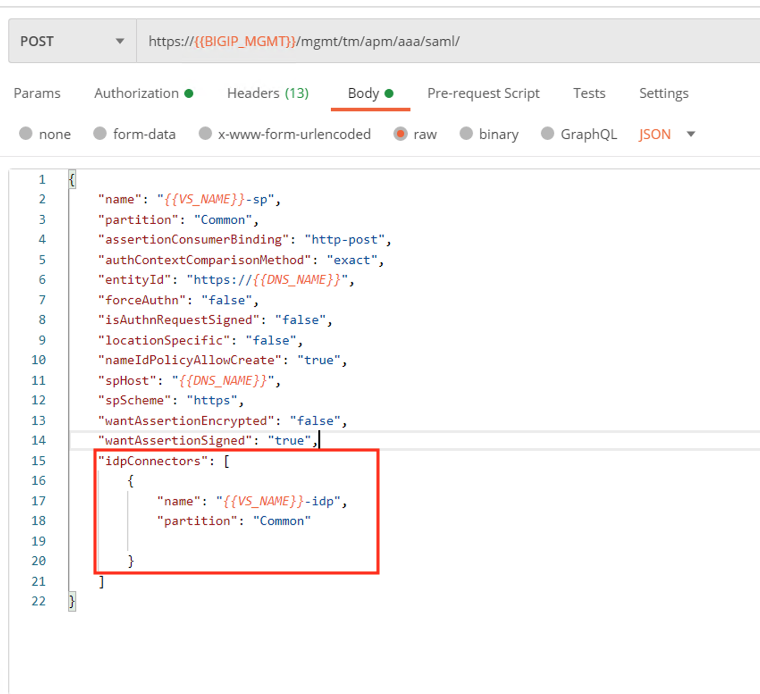
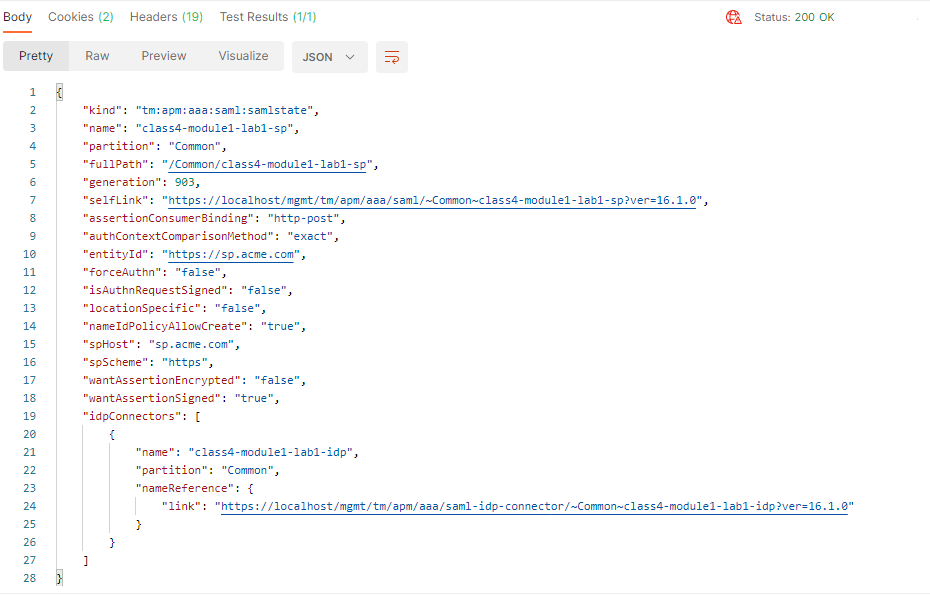
Click the blue Send button in the upper right corner
The response body contains all of the information related the SP Service and links to other endpoints that are related to this SP Services configuration.
Task 6 - Explore configuration via the BIG-IP GUI¶
From the jumphost, open a browser and navigate to https://bigip1.f5lab.local
Login to the BIG-IP GUI with the following credentials:
- Username: admin
- Password: admin
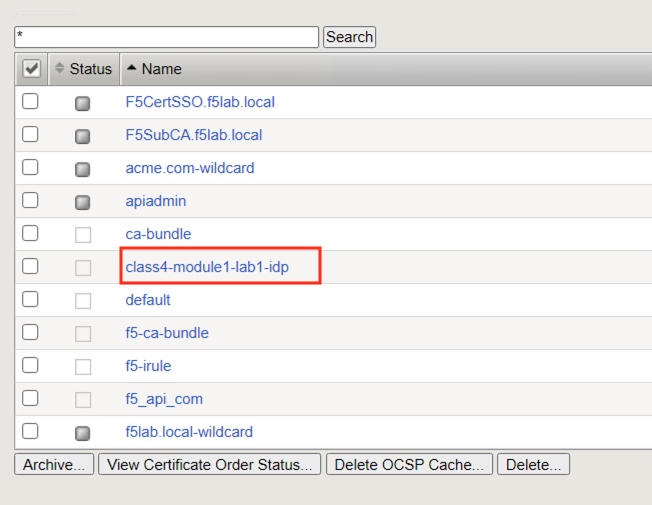
Navigate to System -> Certificate Management -> Traffic Certificate Management -> SSL Certificate List. Click on SSL Certificate List and not the + plus symbol.
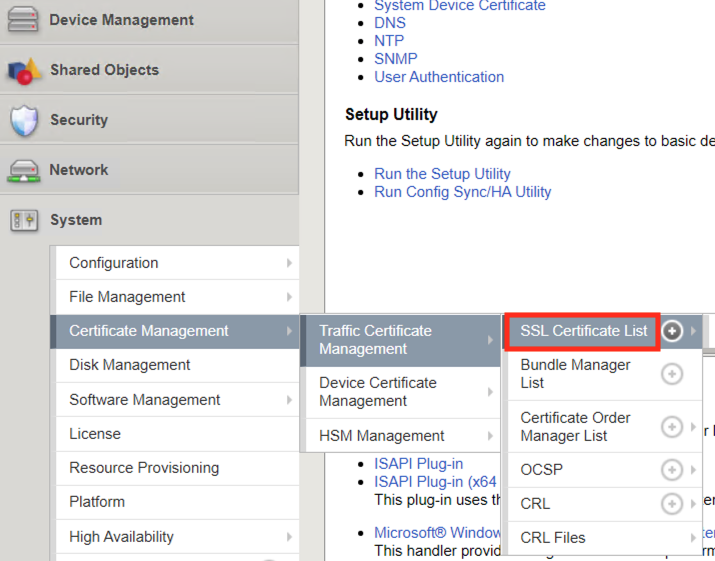
You can see the certificate class4-module1-lab1-idp from Task 1 was successfully imported.
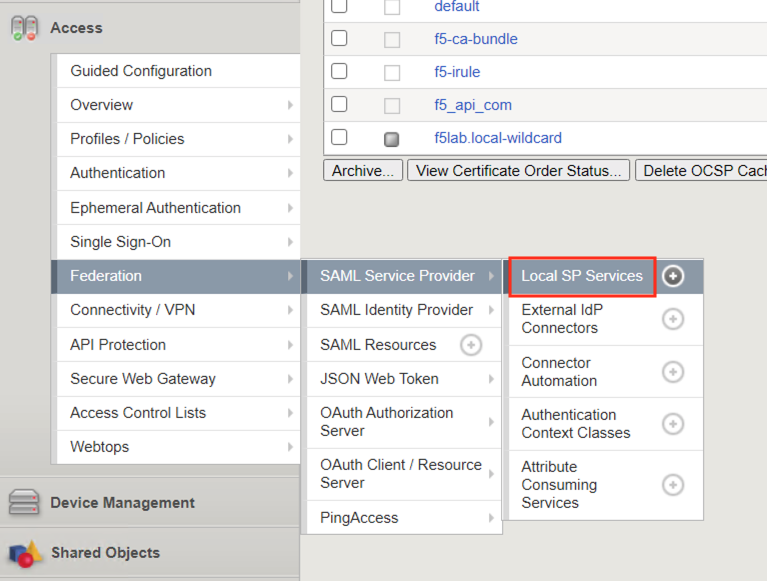
Navigate to Access >> Federation >> SAML Service Provider >> Local SP Services. Click on Local SP Services and not the + (plus symbol).
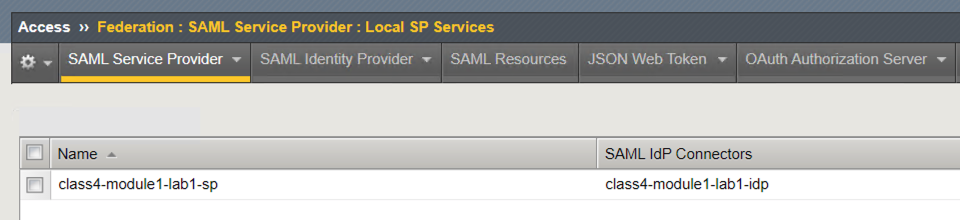
You can see a SP service object was created with the name class4-module1-lab1-sp and successfully bound to an IDP Connector named class4-module1-lab1-idp.
Task 7 - Deleting a SAML Service Provider(SP) Service Configuration¶
With imperative call objects must be deleted in the reverse order they are typically created in. This is because objects that are currently in use cannot be deleted.
From Postman, inside the collection Student-class4-module1-lab1 open the subfolder Delete Objects
Click bigip-delete-sp service
Notice the body is empty. Also, the endpoint we are using is the same endpoint we used to create the SP service plus the partition and object name.
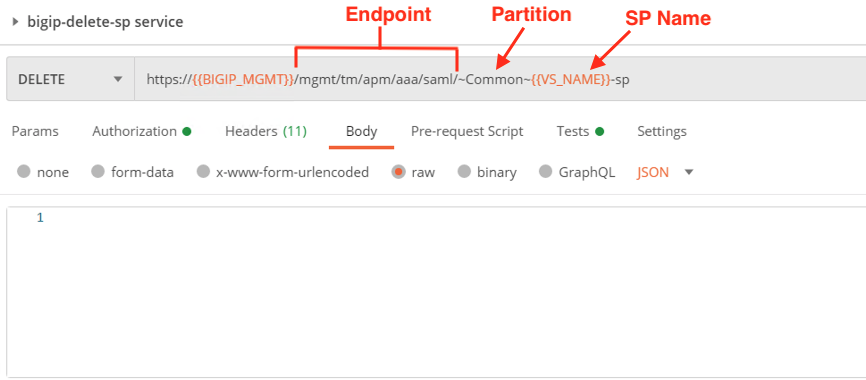
Click the blue Send button in the upper right corner.
Notice nothing is returned in the response body but the Response code is a 200 OK.

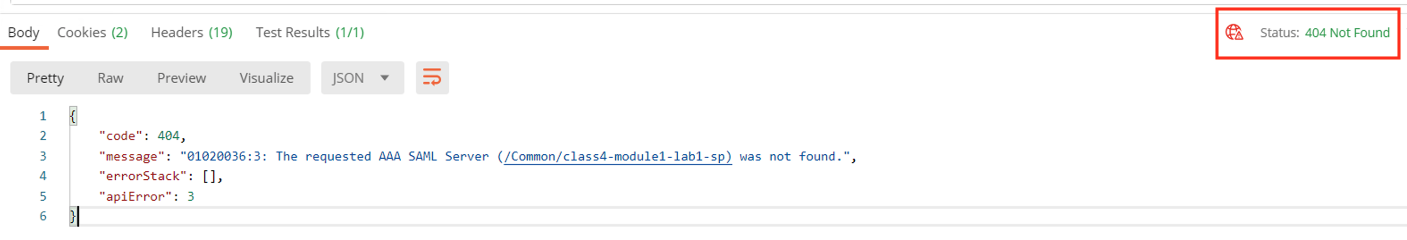
If you click Send a second time you will you get a message back stating the object is not found and a Status Code of 404. That’s because the object was deleted with the prior request.
Click bigip-delete-idp connector
Click the blue send button in the upper right corner.
You will receive a response code of 200 OK.

Click bigip-delete-idp cert
Click the blue send button in the upper right corner.
You will receive a response code of 200 OK.

Task 8 - Ensure objects were removed via GUI¶
Return to the jumpbox’s browser and navigate to https://bigip1.f5lab.local
Login to the BIG-IP GUI with the following credentials:
- Username: admin
- Password: admin
Navigate to System >> Certificate Management >> Traffic Certificate Management >> SSL Certificate List. Click on SSL Certificate List and not the + (plus symbol).

Notice the certificate class4-module1-lab1-idp was deleted
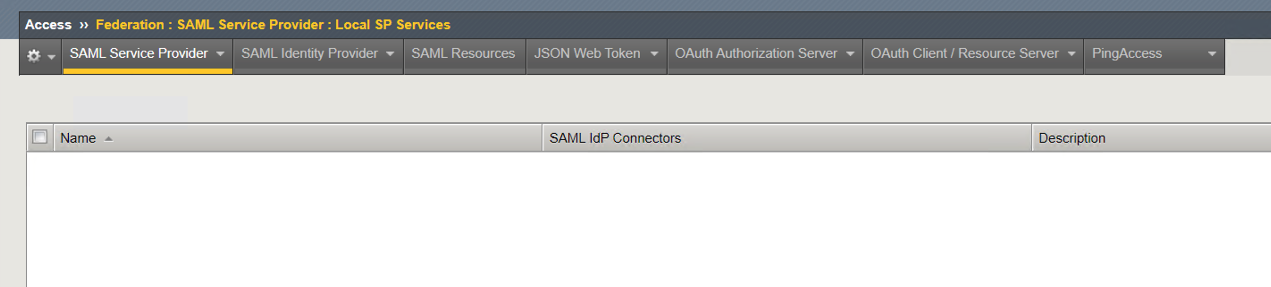
Navigate to Access >> Federation >> SAML Service Provider >> Local SP Services. Click on Local SP Services and not the + (plus symbol).

Notice the SP Service was deleted
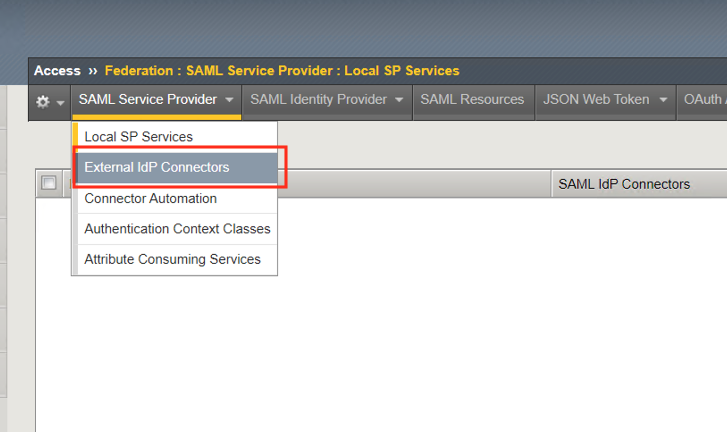
Mouse over SAML Service Provider on the top of the screen and click External IdP Connectors.
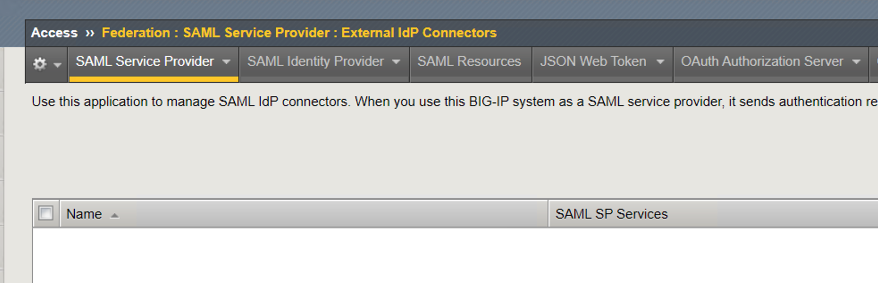
Notice the IDP Connector was deleted.
Task 9 - Lab Clean up¶
From Postman, Mouse over the title of the collection and click the 3 dots next to student-class4-module1-lab1 Collection.
Click Delete
This concludes the APM lab on creating and deleting APM objects via iControlREST.
