F5 Public Cloud Solutions > Secure BIG-IP and Application deployments in AWS documentation! > Securing App with WAF Policy Source | Edit on
Update Parent WAF Policy¶
Task 1 - Simulate attacks to demonstrate newly discovered vulnerability.
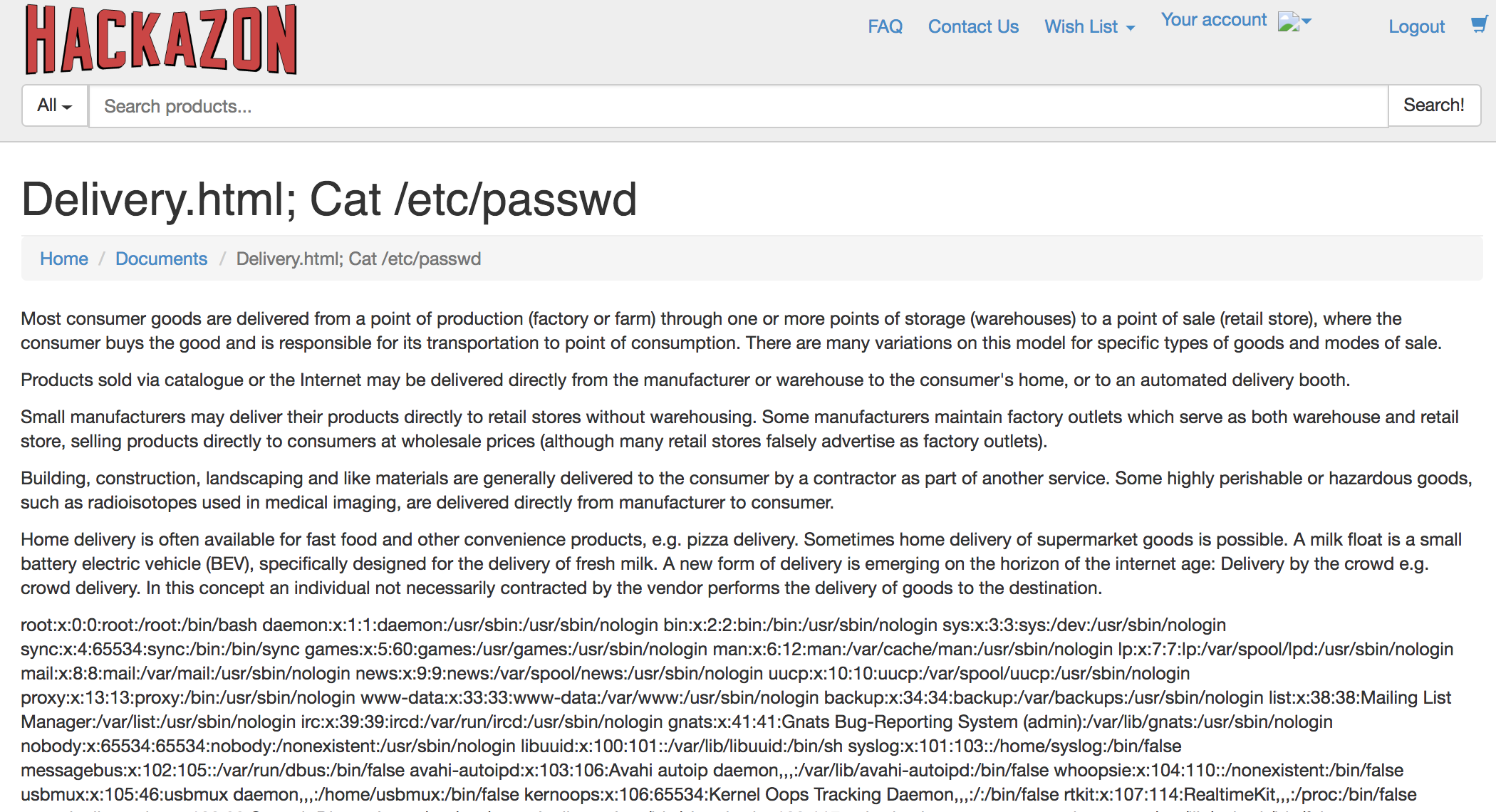
Open browser and go to https://<Elastic IP>/account/documents?page=delivery.html;%20cat%20/etc/passwd
Enter credentials to login successfully.
Note
This is a common OS command injection attack. Upon successful login it displayed the desired page along with the results for cat /etc/passwd.
Task 2 - Modify the parent waf policy to mitigate the command injection vulnerability
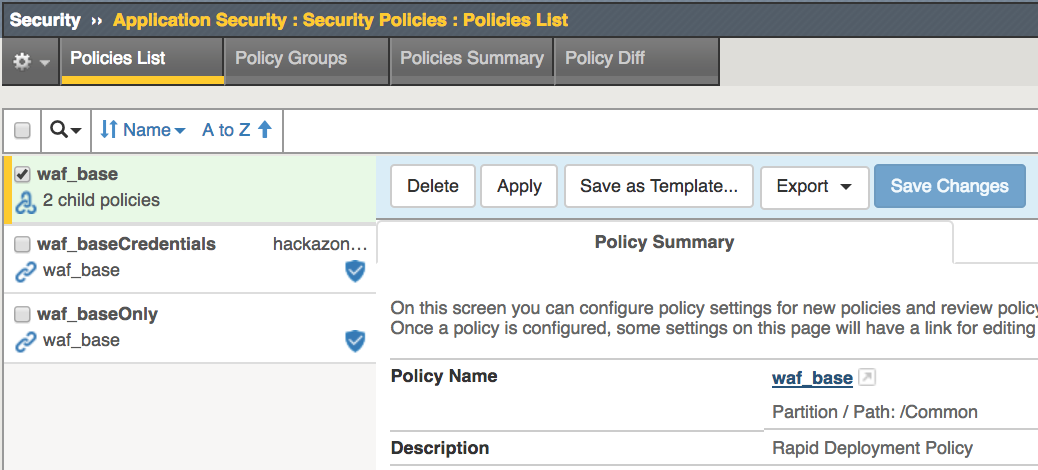
Open the Security -> Application Security -> Security Policies -> Policies List page
Select waf_base then click waf_base to view properties
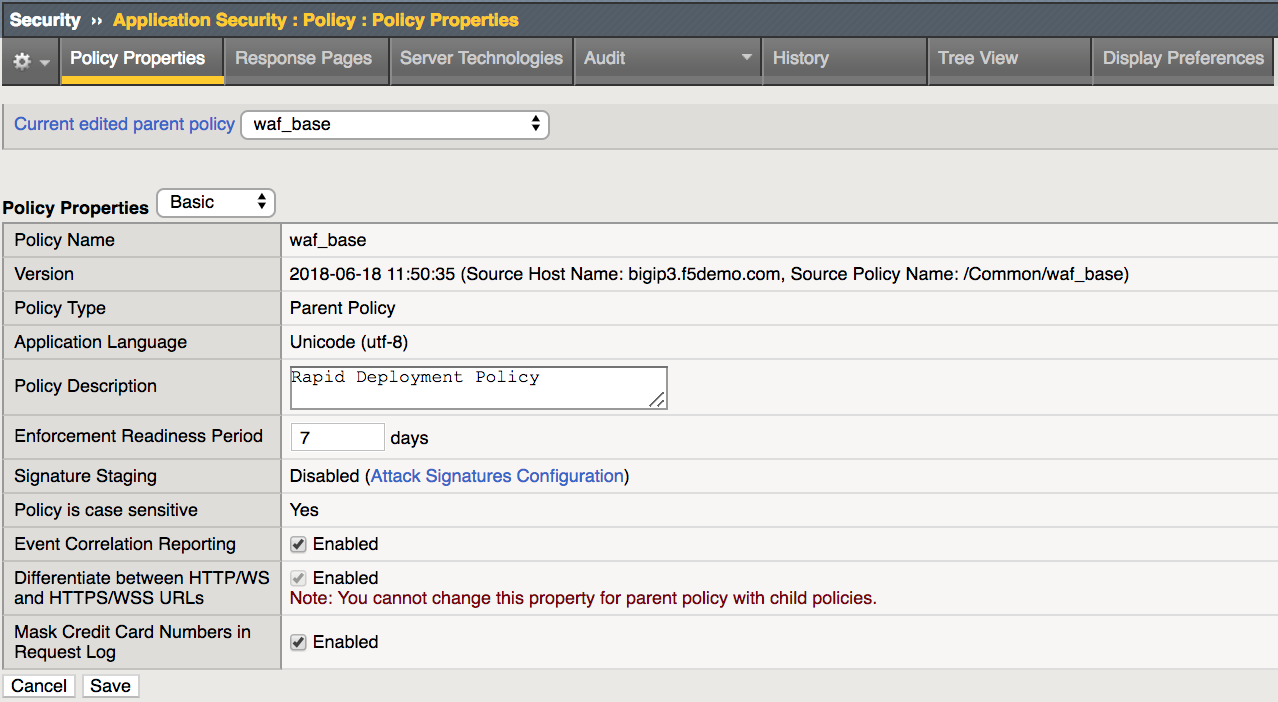
Click on Attack Signatures Configuration
On the Attack Signatures section click Change
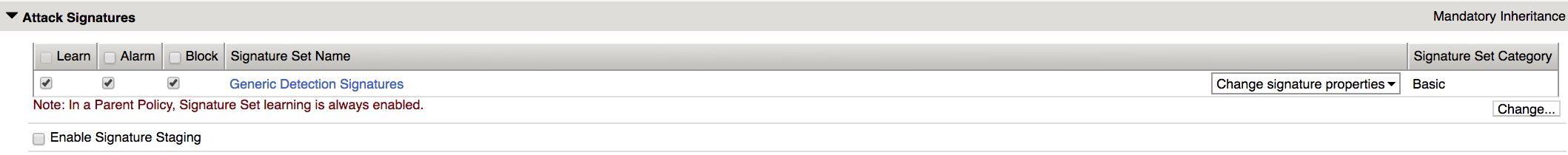
Click OS Command Injection Signatures check box then click Change
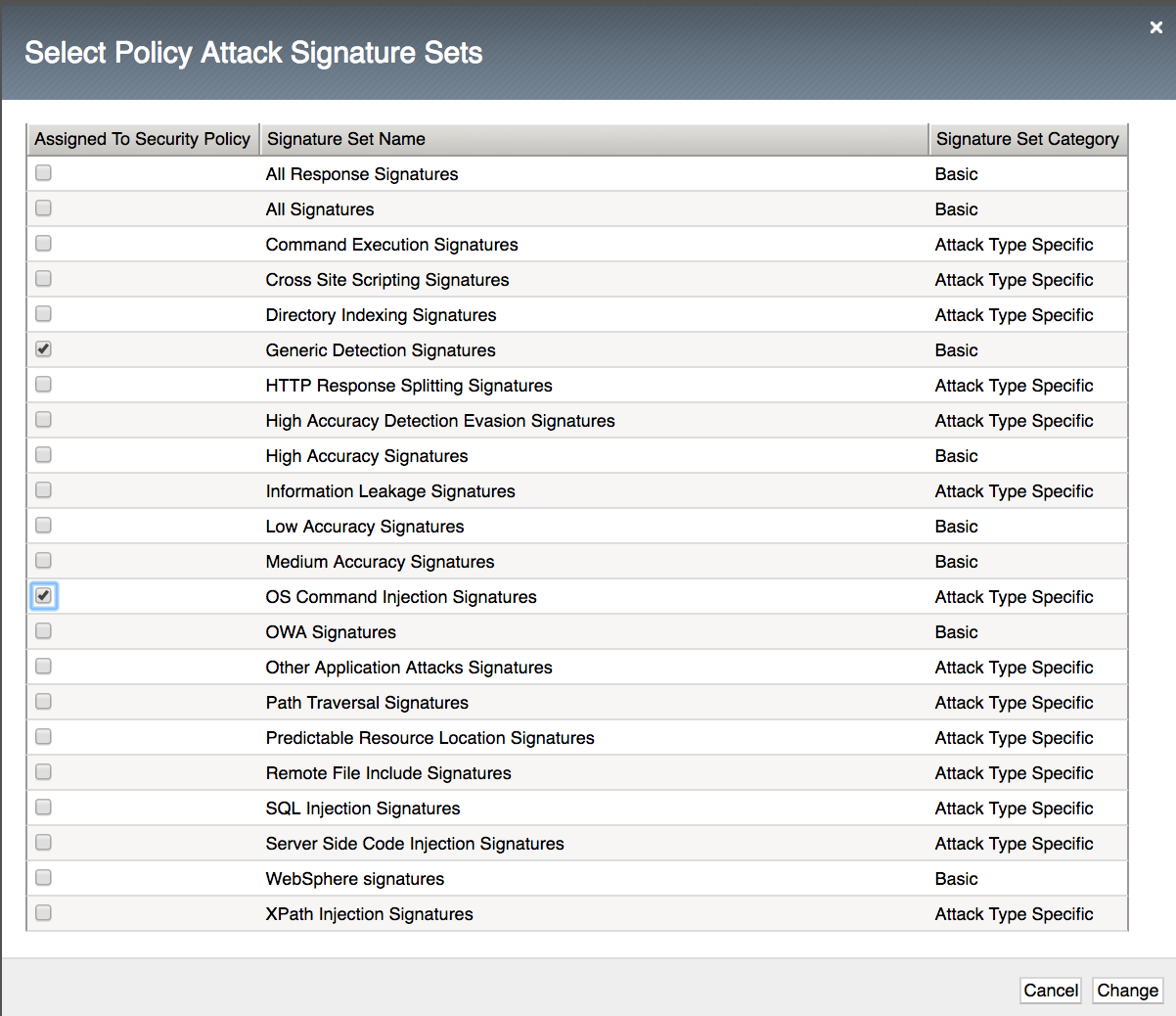
Click Save at the bottom of the properties page
Click Apply Policy to commit changes
Task 6 - Repeat simulated command injection attack
Open browser and go to https://<Elastic IP>/account/documents?page=delivery.html;%20cat%20/etc/passwd
Your request should be rejected.
Note
Updates to the Parent policy will be inherited by the Child policies based on the Inheritance configuration. Since waf_base parent policy Attack Signatures was Mandatory all Child policies inherited the changes.