F5 Public Cloud Solutions > Secure BIG-IP and Application deployments in AWS documentation! > Securing App with WAF Policy Source | Edit on
Create Credentials Protection WAF Child Policy¶
Task 1 - Simulate credential attacks.
Open browser and go to https://<Elastic IP>/user/login
For Username enter f5student
For Password. enter random incorrect password. Repeat 5 consecutive times using different password to simulate brute force attack
Note
This is a common brute force attack. In this case the application allowed repeated attempts without lockout. Some applications will send “account locked” for a period of time, however user can continue to repeated attempts to elongate lockout period.
Open new incognito browser and open developer tools. (In Chrome for example: View -> Developer ->Developer Tools)
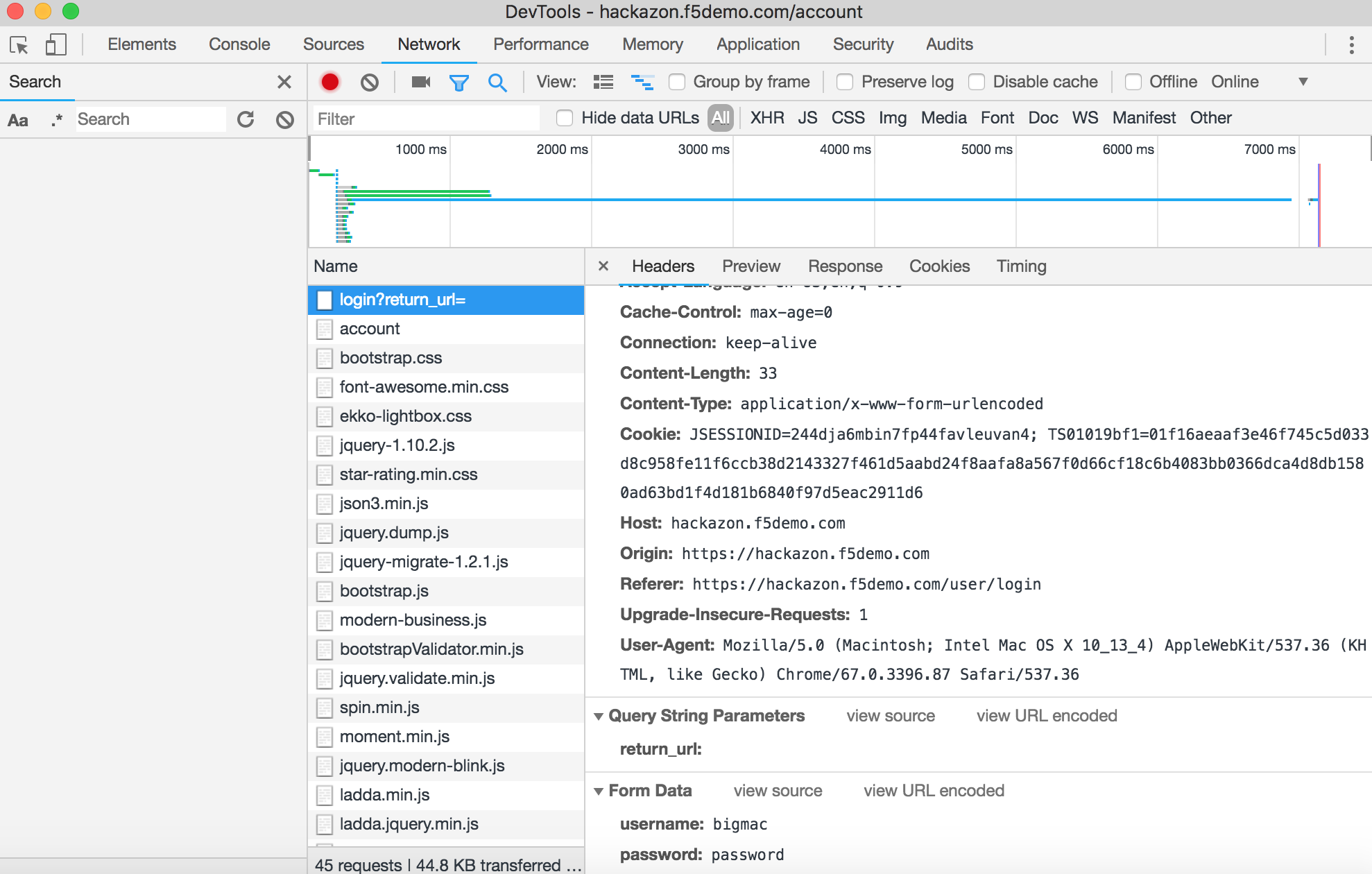
Browse to https://<Elastic IP>/user/login and login with username f5student and password password
Once successfully logged in, review log on Developer Tool.
- Select Network tab
- Highlight login?return_url=
- On right panel click Headers and scroll to bottom of Form Data to view Username and Password.
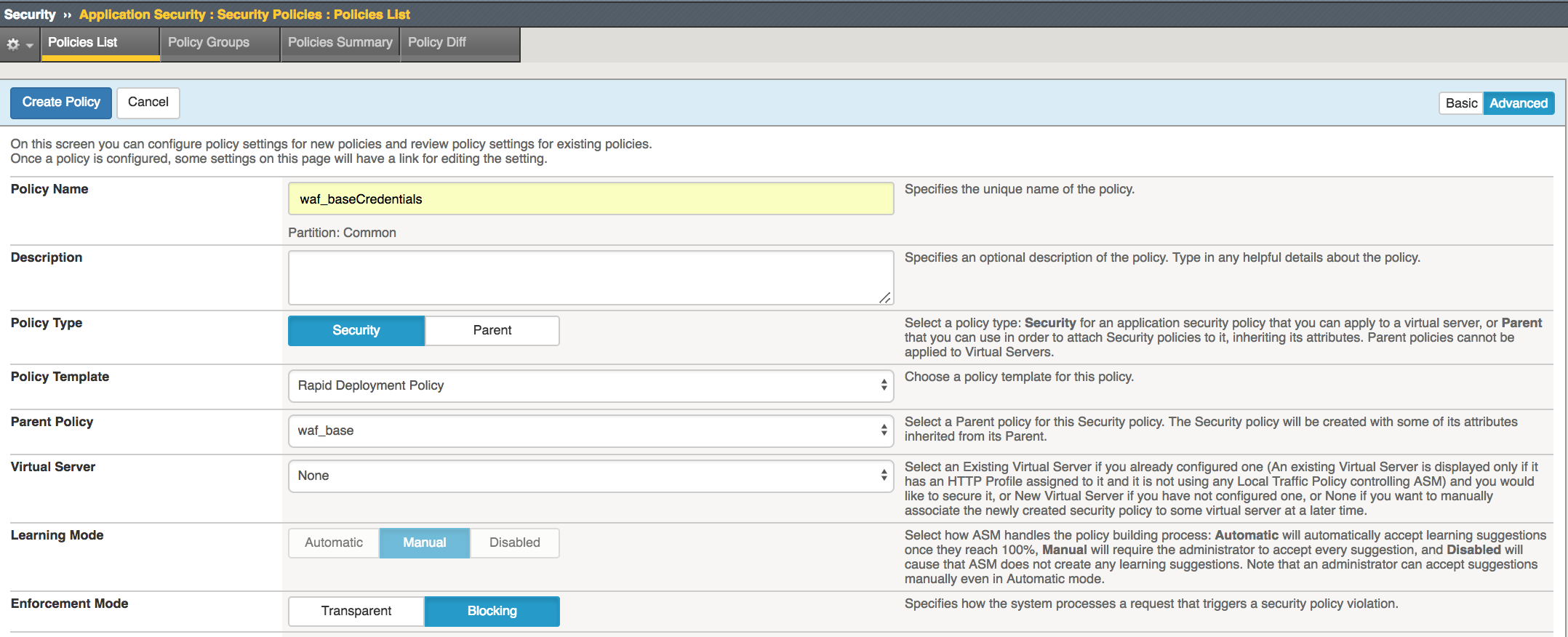
Task 2 - Create new waf policy to mitigate the vulnerabilities using info on table below:
| Policy Name | waf_baseCredentials |
| Policy Type | Security |
| Parent Policy | waf_base |
| Virtual Server | none |
| Enforcement Mode | Blocking |
Select the Security -> Application Security -> Security Policies -> Policies List page
Click Create New Policy then click Advanced and enter info as shown in image below.
Click Create Policy
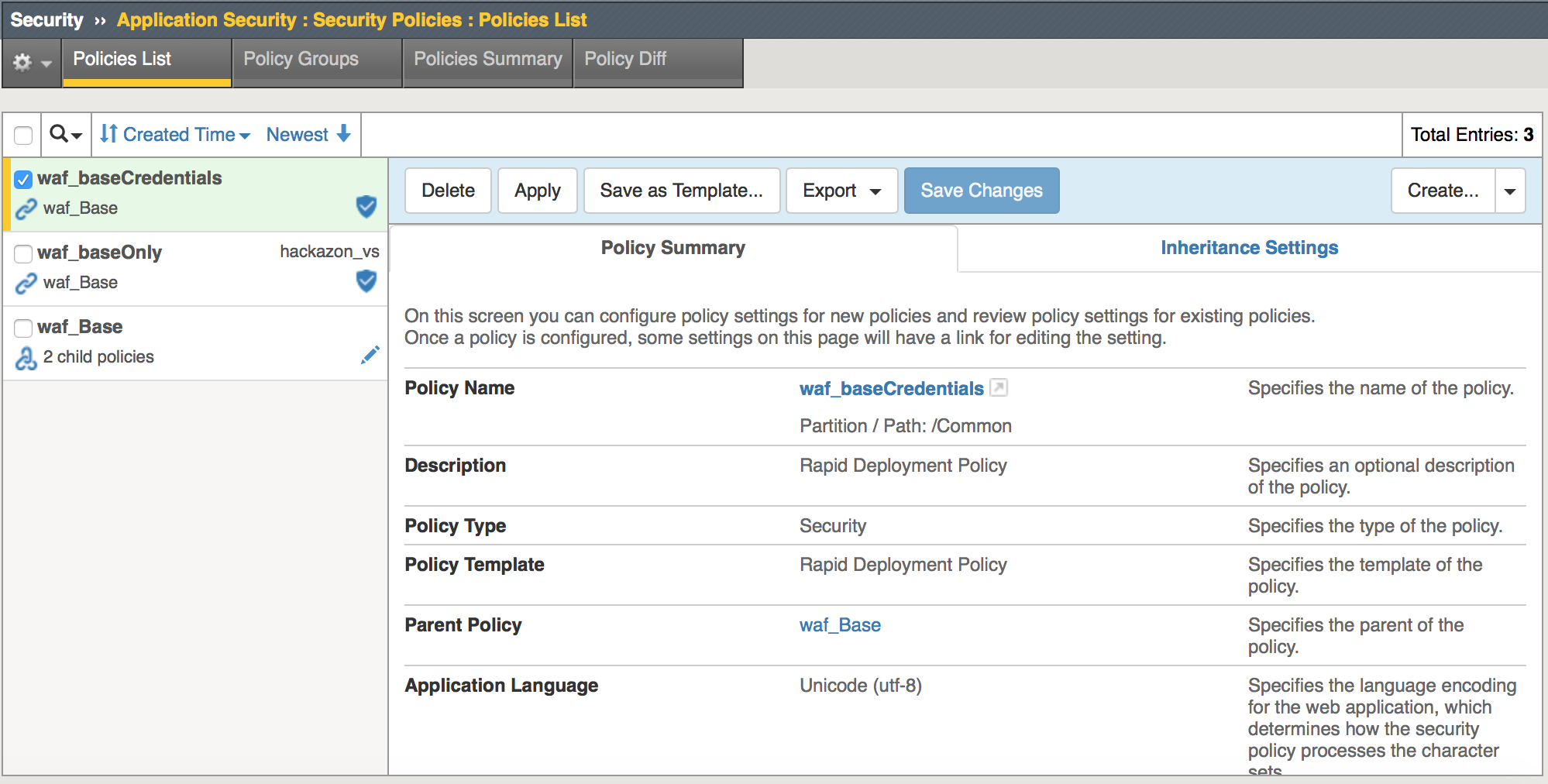
Task 3 - Configure Brute Force Protection
Select Security -> Application Security -> Sessions and Logins -> Login Pages List page
Click Create
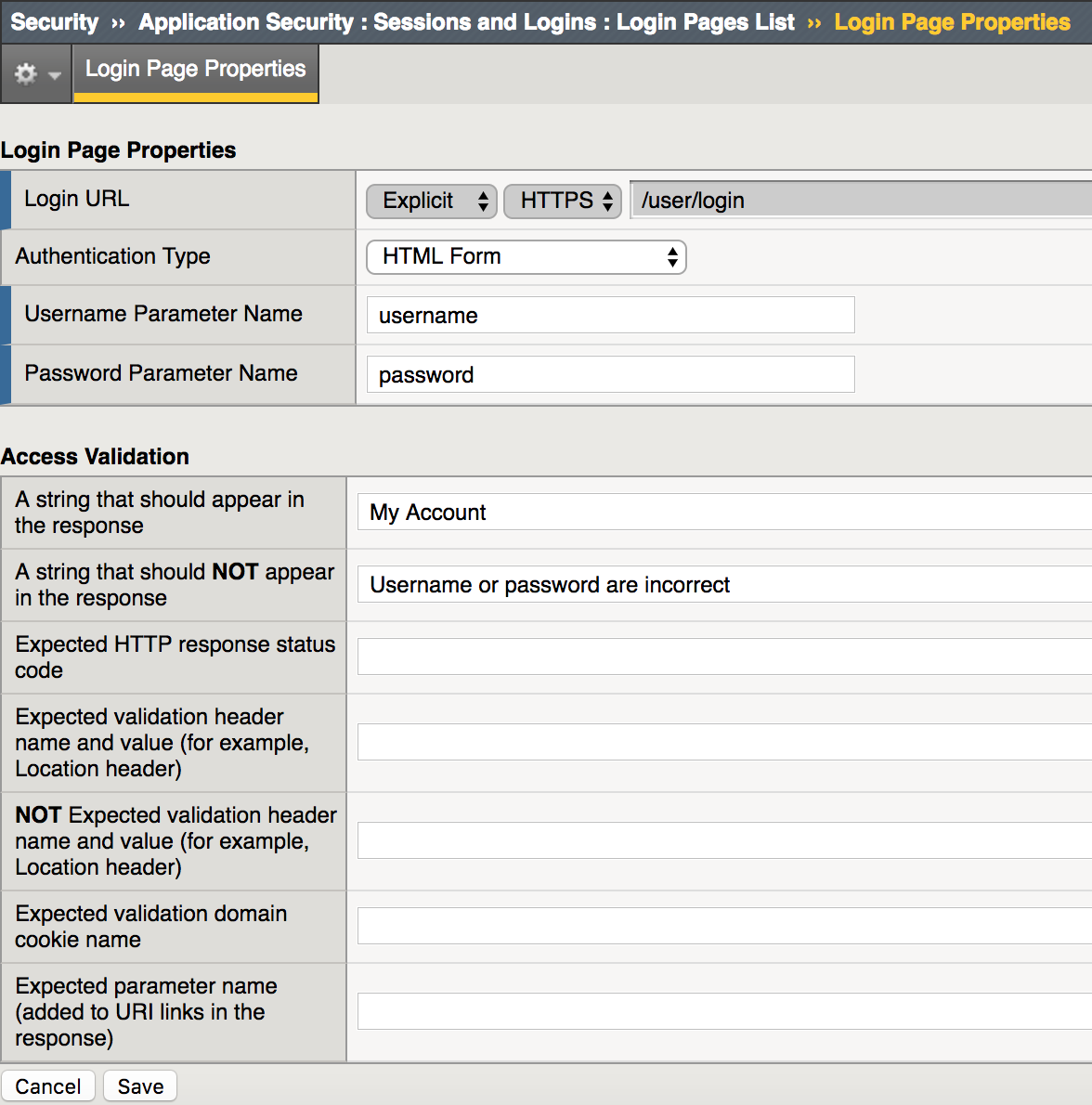
Fill in the details as in the image above and click on Create
Select Security -> Application Security -> Anomaly Detection -> Brute Force Attack Prevention then click Create
Change Login Page drop down box to [HTTPS]/user/login then click Create
Click Apply Policy then OK to commit changes
Task 4 - Configure Credential Encryption
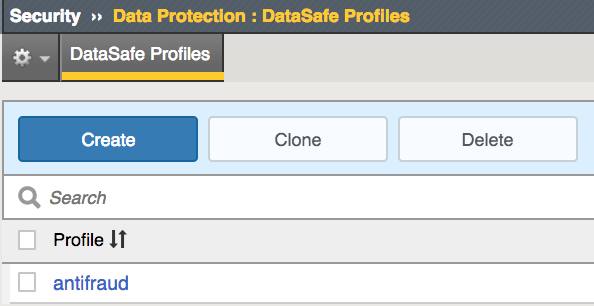
Select Security -> Data Protection -> DataSafe Profiles
Click Create
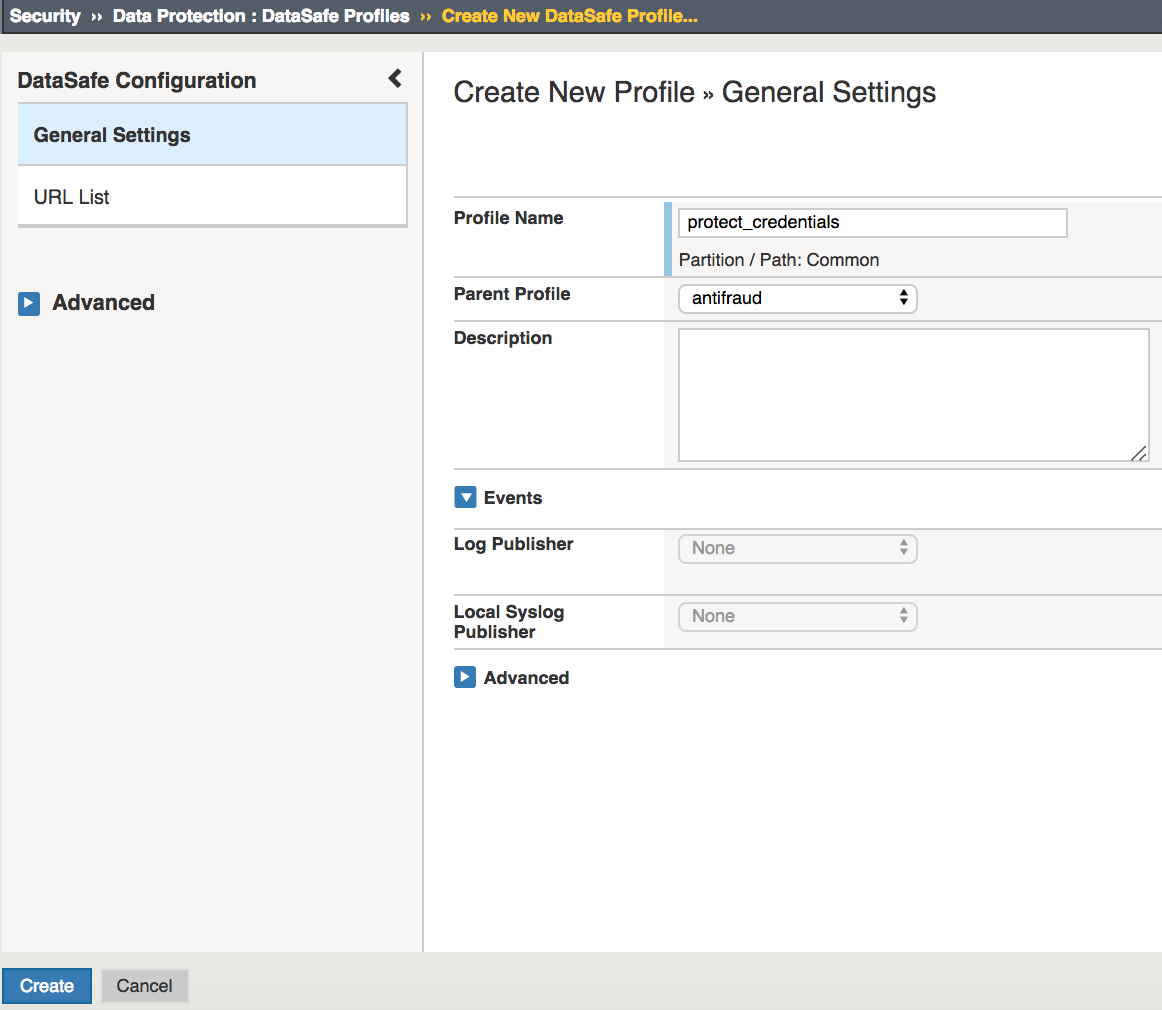
For Profile Name enter protect_credentials
Click on the `>` next to Create New Profile to expand menu.
Select URL List and click Add
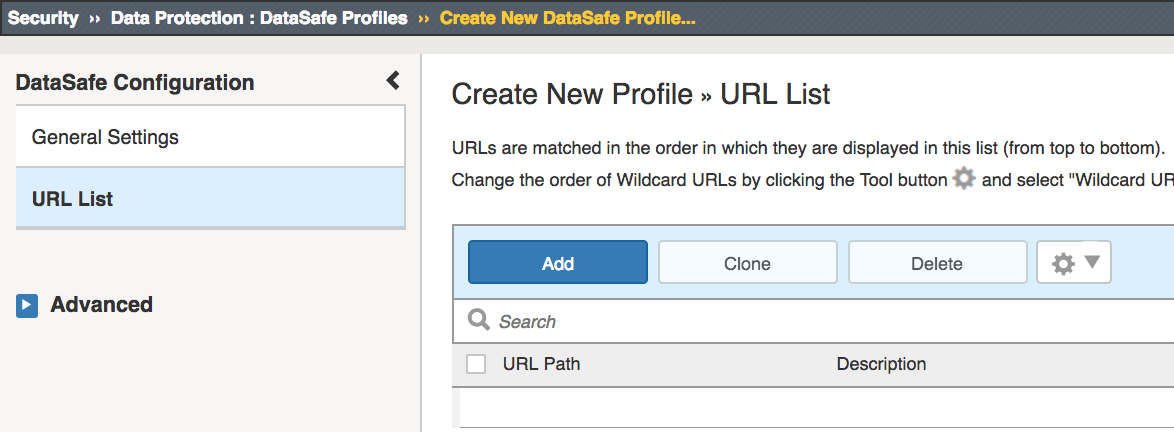
For the URL path enter /user/login
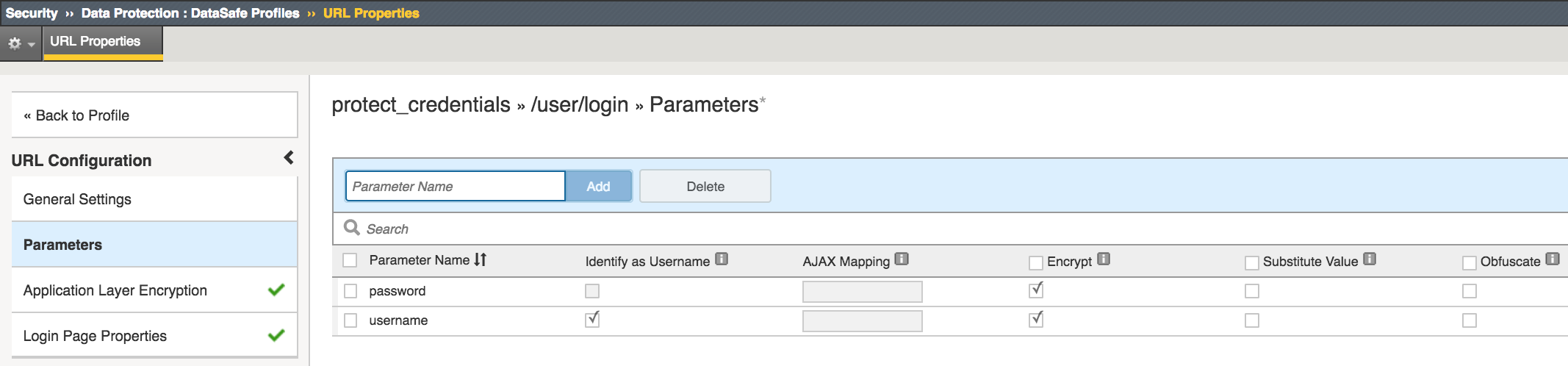
Expand the Menu again and Select Parameters
In the Parameter Name enter username and click Add
Check Identify as Username and Encrypt check boxes
In the Parameter Name enter password and click Add
Check Encrypt check box
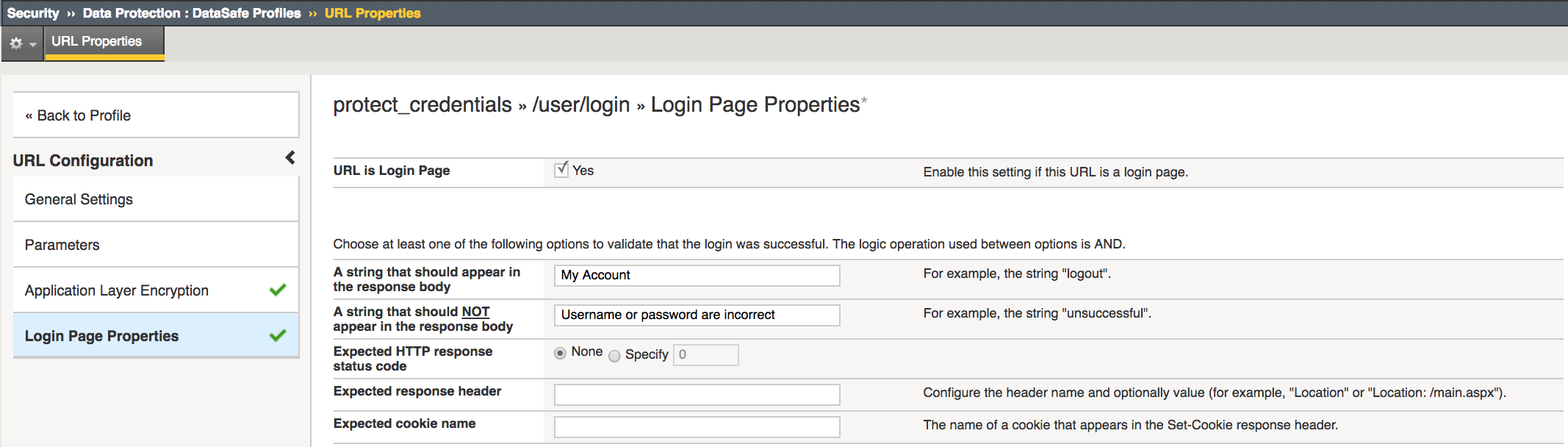
Click Login Page Properties
For URL is Login Page check Yes box
For A string should appear enter My Account
For A string that should NOT appear enter Username or password are incorrect
Click Create
Task 5 - Assign policies to protect Hackazon App
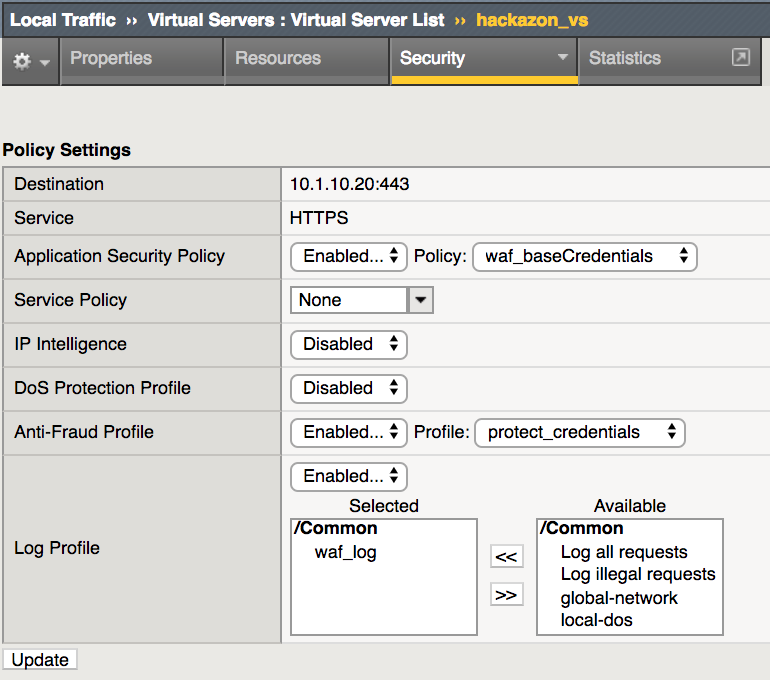
Select Local Traffic -> Virtual Servers -> Virtual Servers List and click on hackazon_vs
Select Security then Policy tab
Change Application Security Policy to waf_baseCredentials
Enable Anti-Fraud Profile and select protect_credentials
Click Update
Task 6 - Repeat simulated credential attacks
Open browser and go to https://<Elastic IP>/user/login
For Username enter f5student
For Password enter random incorrect password. Repeat multiple times using different password to simulate brute force attack. You should receive a captcha challenge after 3 failed attempts.
Enter captcha challenge then enter correct credentials to login in successfully.
Open new incognito browser and open developer tools. (View->Developer-Developer Tools)
Browse to https://<Elastic IP>/user/login and login with username f5student and password password
Once successfully logged in, review log on Developer Tool.
- Select Network tab
- Highlight login?return_url=
- On right panel click Headers and scroll to bottom of Form Data to view Username and Password.
