F5 Web Application Firewall Solutions > WAF 301 - AWAF in a CI/CD Pipeline (Self Guided) > Module 1: AWAF Policy Template Creation on BIG-IP (secops engineer) Source | Edit on
Lab 1.1: Creation of an AWAF base policy¶
We’re going to be working in the BIG-IP to create an ASM template with some specific settings applied that we can use on our VS. Once the template is created, we’ll use AS3 and Postman to add an ASM policy to a VS based on our template to show how to add automation of ASM policies to applications.
1.1.1 Open RDP to the Client linux¶
For users with Mac’s, keystrokes won’t show as you type. Don’t worry, just keep typing and login.
Log into the Linux Client via RDP using the following credentials:
Username: f5student
Password: f5DEMOs4u!
Note
Copy/Paste doesn’t work in XRDP.
1.1.2 Log into the BIG-IP¶
Log into the BIG-IP by opening the FireFox browser in the Linux client and selecting the browser bookmark titled bigip01 using the following credentials:
Username: admin
Password: f5DEMOs4u!
1.1.3 Create a policy¶
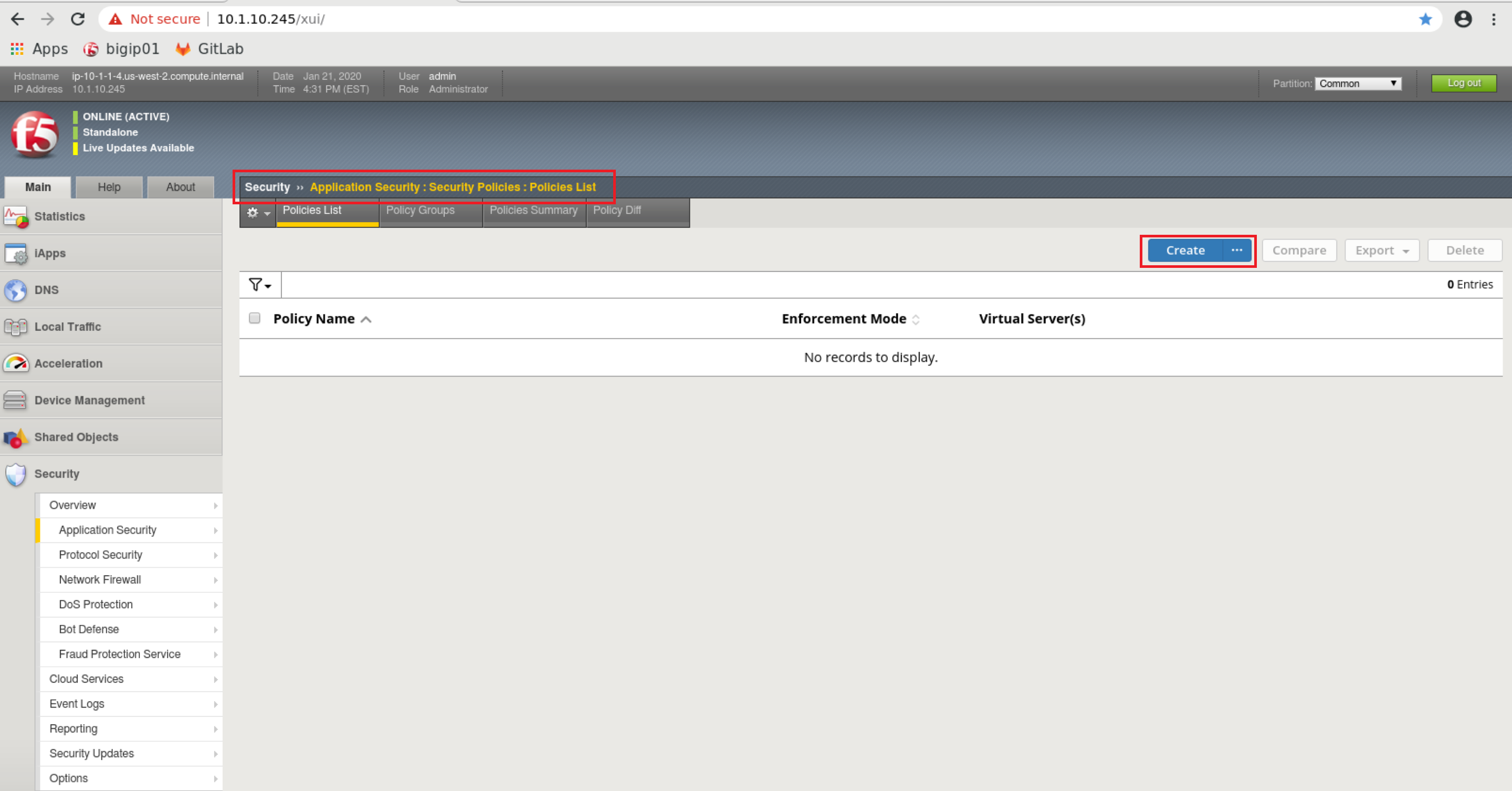
Let’s create an AWAF base policy that we’ll reference later, by navigating to:
Security ›› Application Security : Security Policies : Policies ListClick ‘Create’
1.1.4 Configure policy properties¶
#Please fix all guilabel tags below. They are not rendering correctly in the remainder of this file
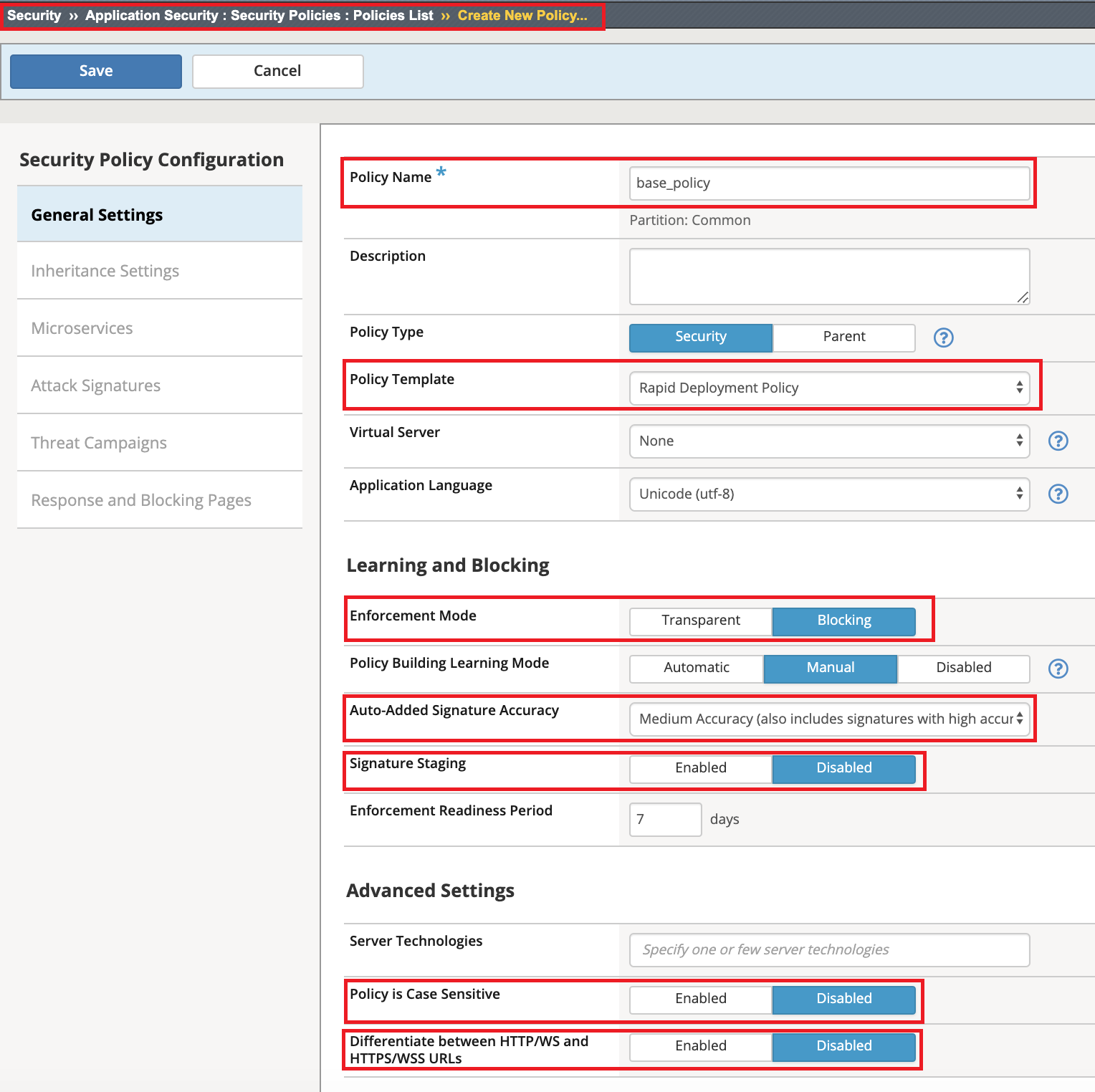
Name the policy base_policy and set the following settings:
policy Name: base_policy
Policy Template: Rapid Deployment Policy
Enforcement Mode: Blocking
Auto-Added Signature Accuracy: Medium
Signature Staging: Disabled
Policy is Case Sensitive: Disabled
Differentiate between HTTP/WS and HTTPS/WSS URLs: Disabled
Click Save to save the policy
Click Save to save the policy
1.1.5 Block traffic from North Korea¶
Navigate to: Security ›› Application Security : Security Policies : Policies List Select: base_policy and scroll to Advanced Settings, Geolocation Enforcement
We’re going to create a Geo enforcement on this policy to block North Korea form accessing our site. From the ‘Allowed Geolocations’ on the right, find ‘Korea, Democratic People’s Republic of’ and bring it to the left window titled ‘Disallowed Geolocations’:
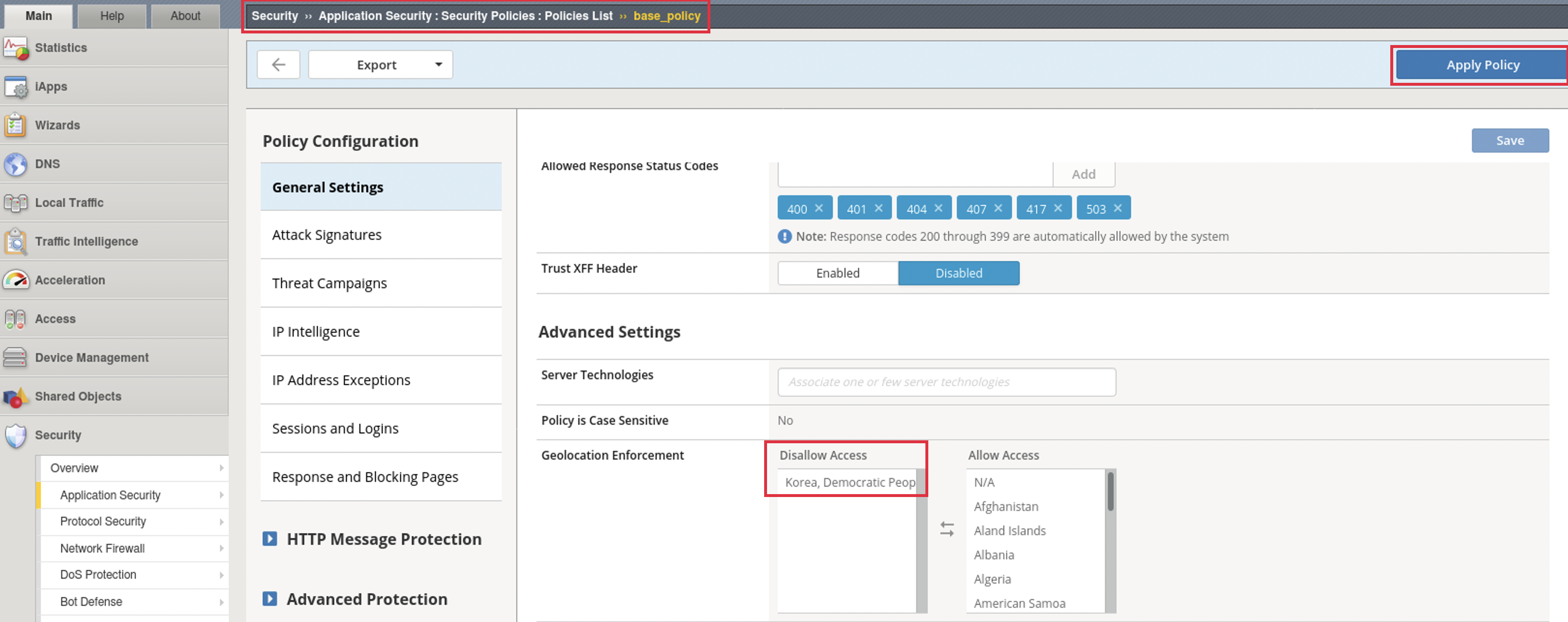
Click Save
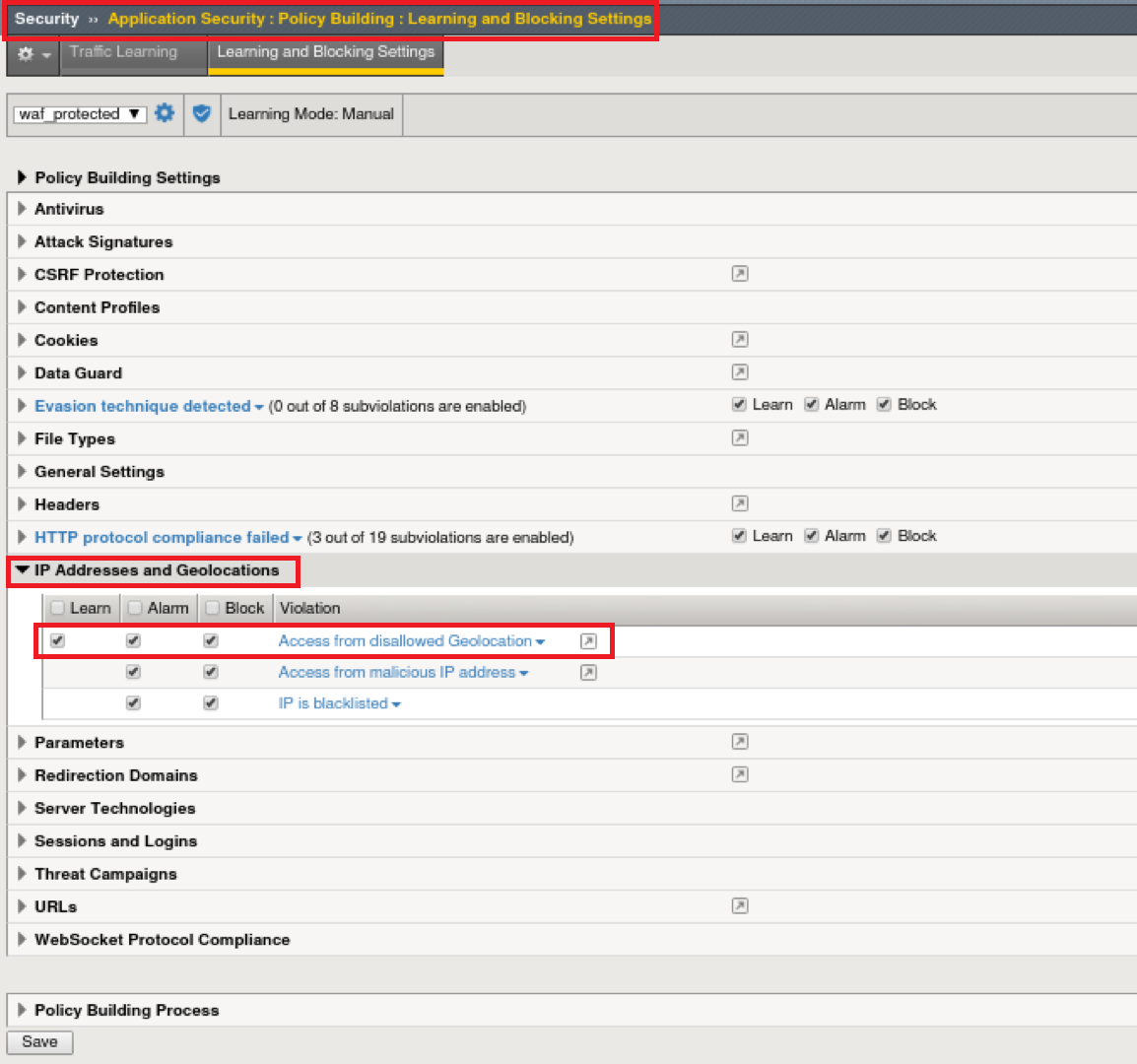
Navigate to: ‘Security ›› Application Security : Policy Building : Learning and Blocking Settings
If you expand IP Addresses and Geolocations you’ll notice that we’re enforcing blocking of the Geolocation that we created in the previous step as well as access from known malicious IP addresses.
On this same screen, under the section File types check the boxes on Illegal file types to ‘learn’, ‘alarm’, and ‘block’ as shown below.
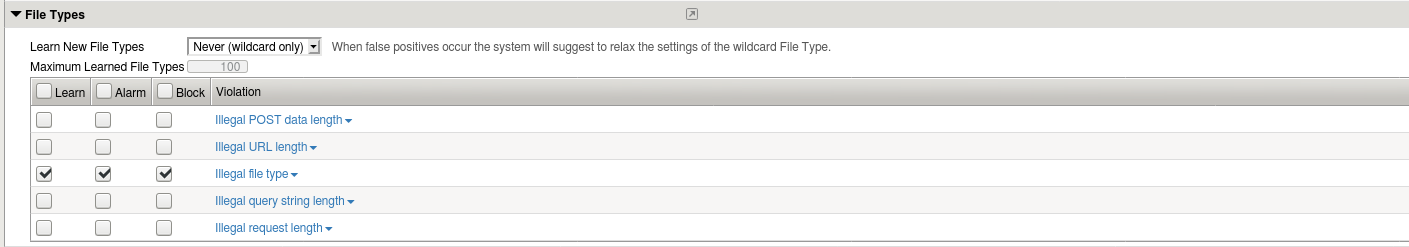
Click Save **at the bottom of this screen to save our changes.
Click Apply policy **at the top right of the screen to save our changes.