F5 BIG-IQ Centralized Management Lab > BIG-IQ All Labs > Class 8: BIG-IQ Web Application Security > Module 2: Tooling and RBAC with WAF management on BIG-IQ Source | Edit on
Lab 2.3: Restrict access to logs and dashboards data based on ownership (new 8.0)¶
Note
Estimated time to complete: 15 minutes
In this lab, we will create a user which will only have access to the Web Application Security Analytics and Events logs related to a specific WAF policy.
Lab environment access¶
If you have not yet visited the page Getting Started, please do so.
Resource Group and Role Creation (david)¶
Let’s first deploy the default Advance WAF policy and Security Logging Profile available in BIG-IQ to SEA-vBIGIP01.termmarc.com.
- Login to BIG-IQ as david.
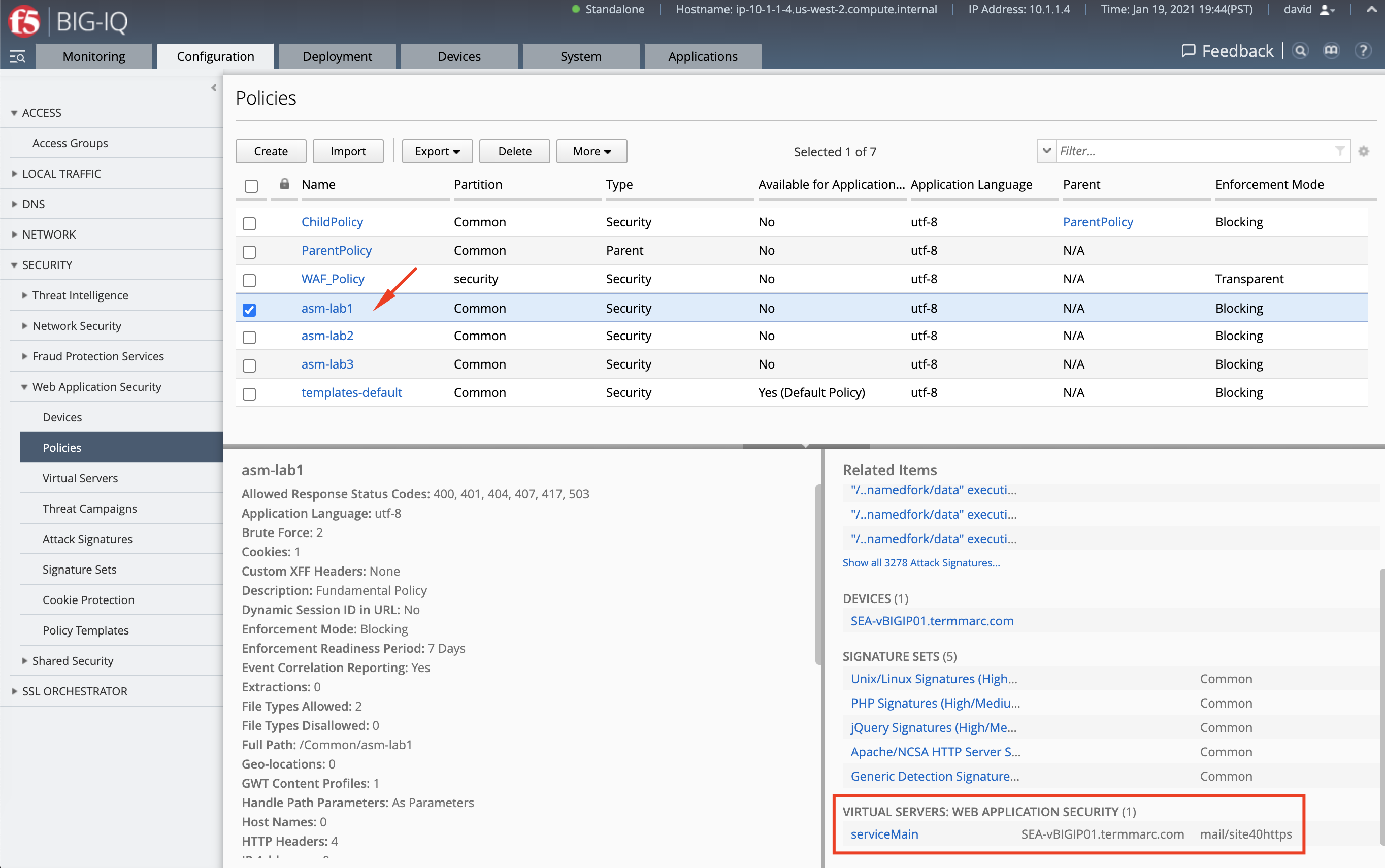
- Go to Configuration > Security > Web Application Security > Policies. For this lab, we are going to use WAF policy called
asm-lab1. Note this policy is in use by the Application Service mail_site40htts.
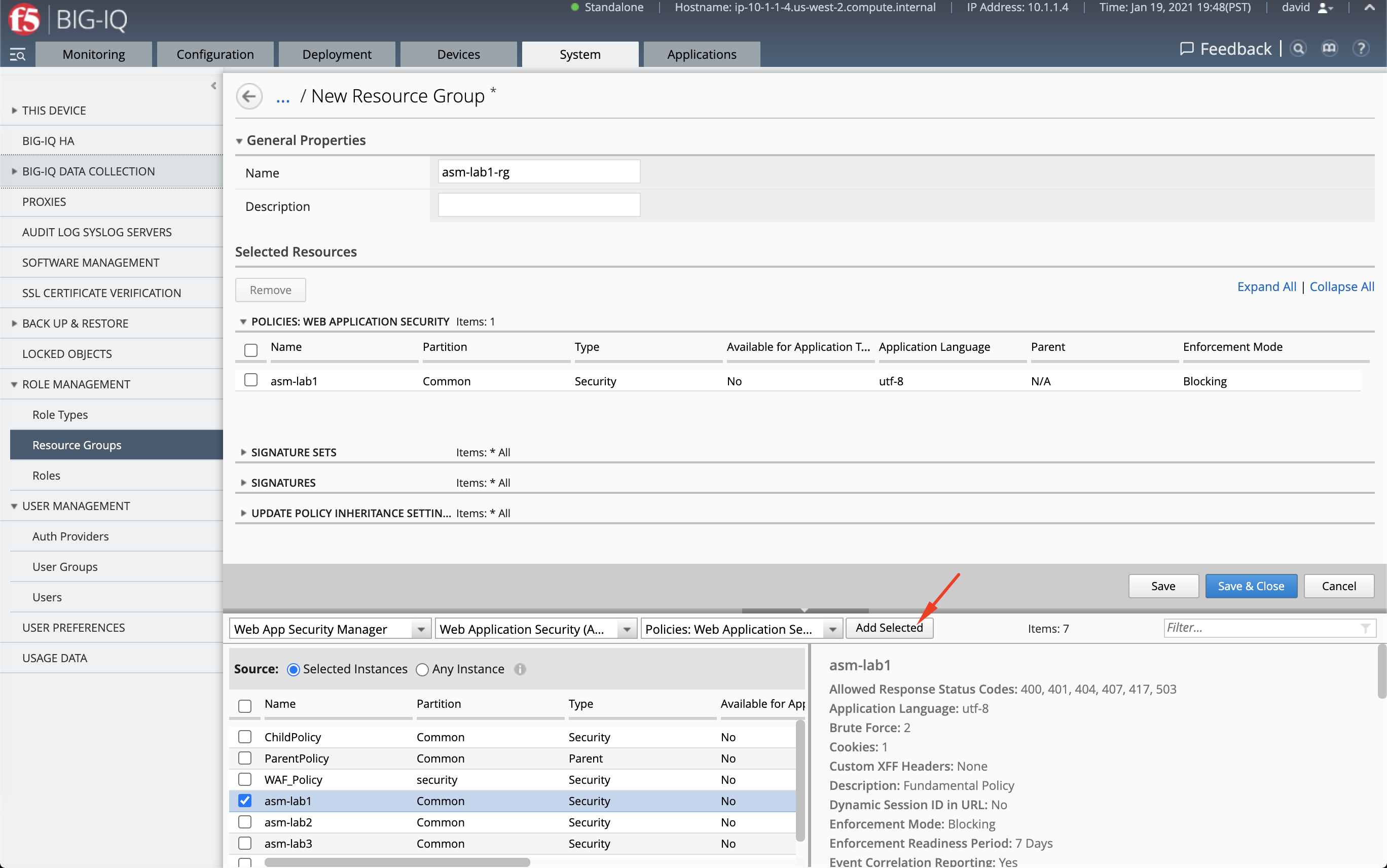
- First, we need to create a resource group and include the
asm-lab1policy.
Navigate under System > Role Management > Resource Groups and click to Create.
Select in the first drop down menu Web Application Security Manager (role type), Web Application Security (ASM) (service),
then Policies (object type). Select asm-lab1 policy and add it to the resource group.
Name the resource group asm-lab1-rg and click on Save & Close.
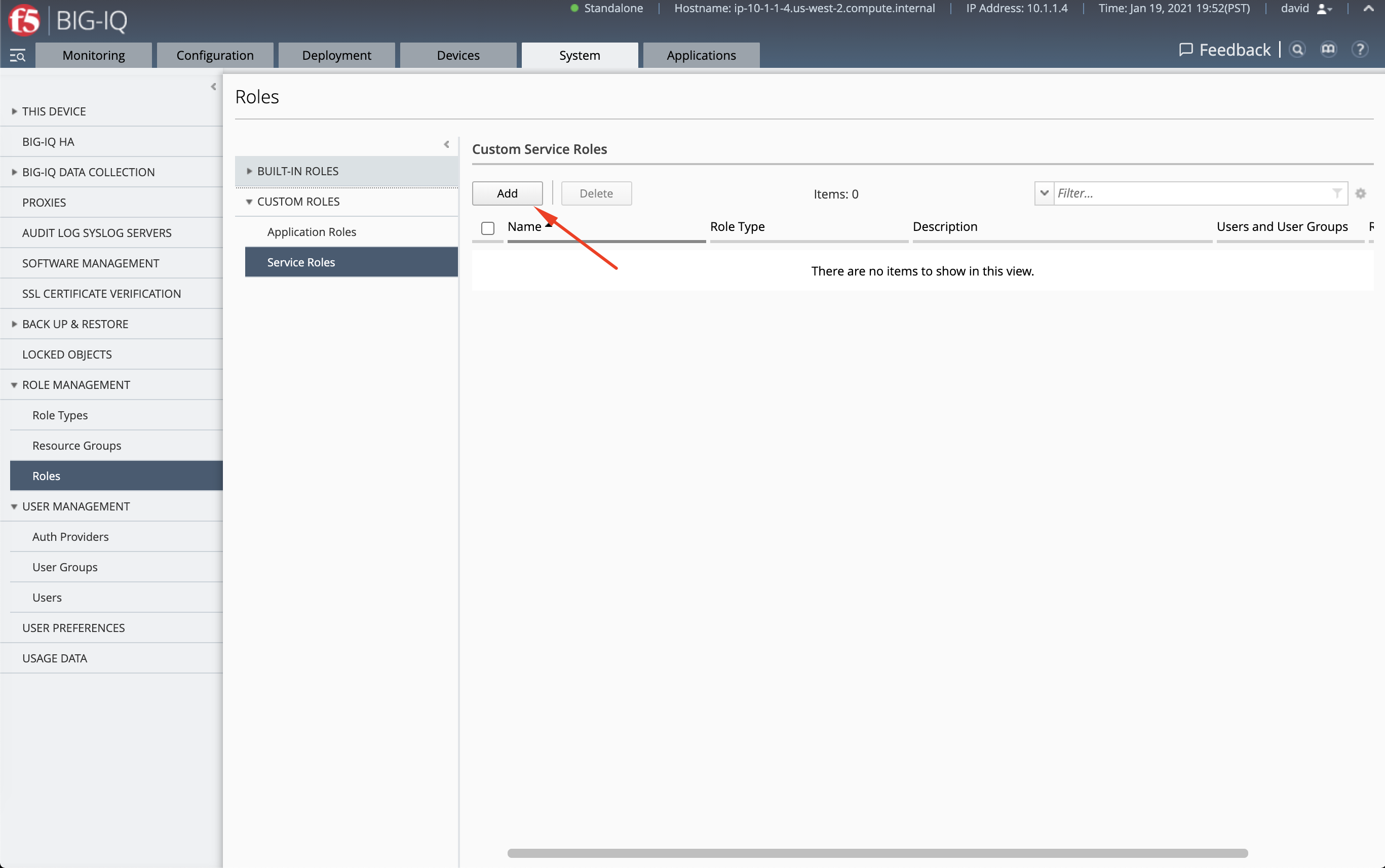
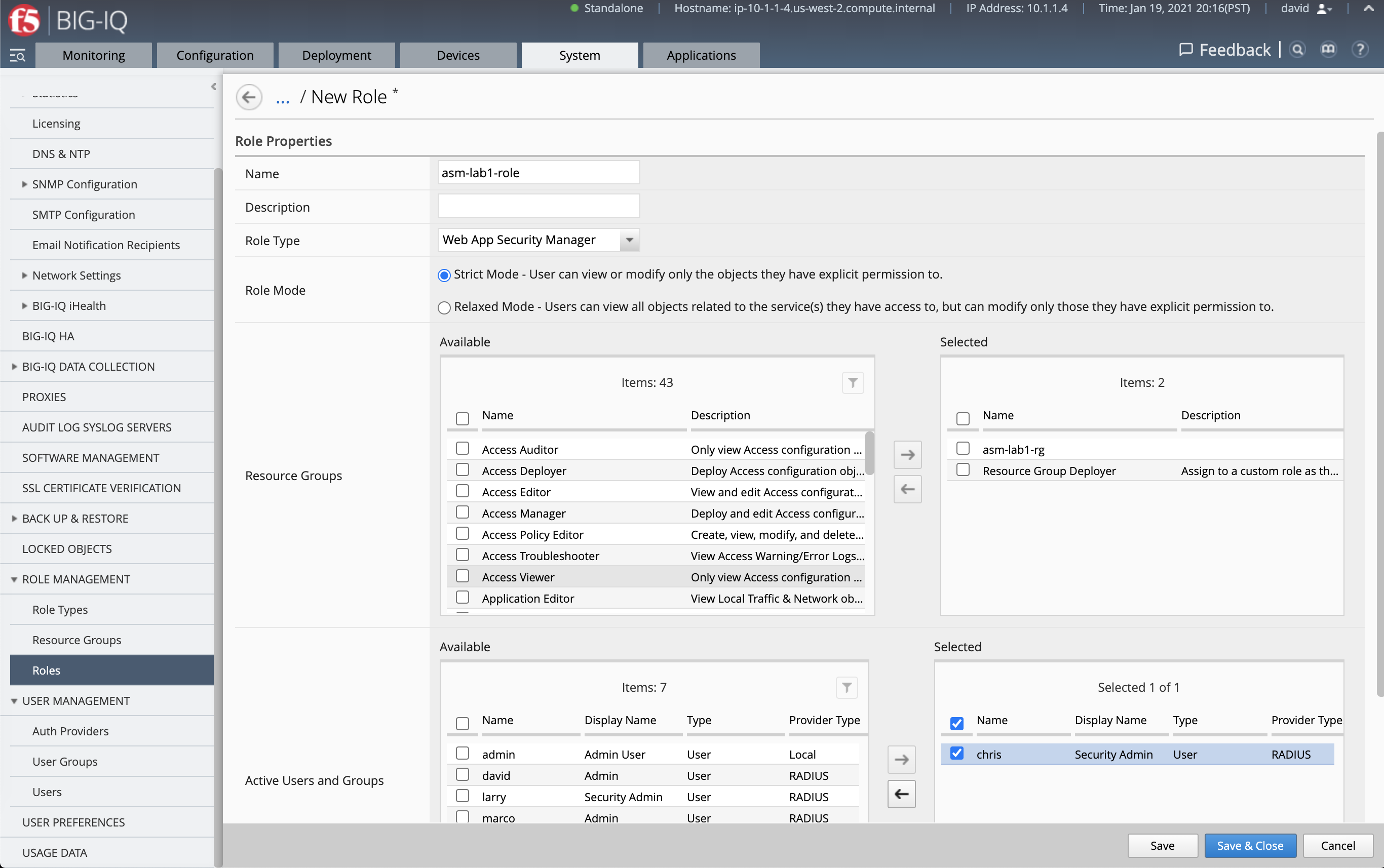
- Let’s now create custom service role. Navigate under System > Role Management > Roles, under Custom Roles > Service Roles, click to Add.
- Assign the resource group previously created
asm-lab1-rgalong with the predefined resource group calledResource Group Deployerused to allow the user to deploy changes to the policy.
Assign the user chris, and name the this custom role asm-lab1-role.
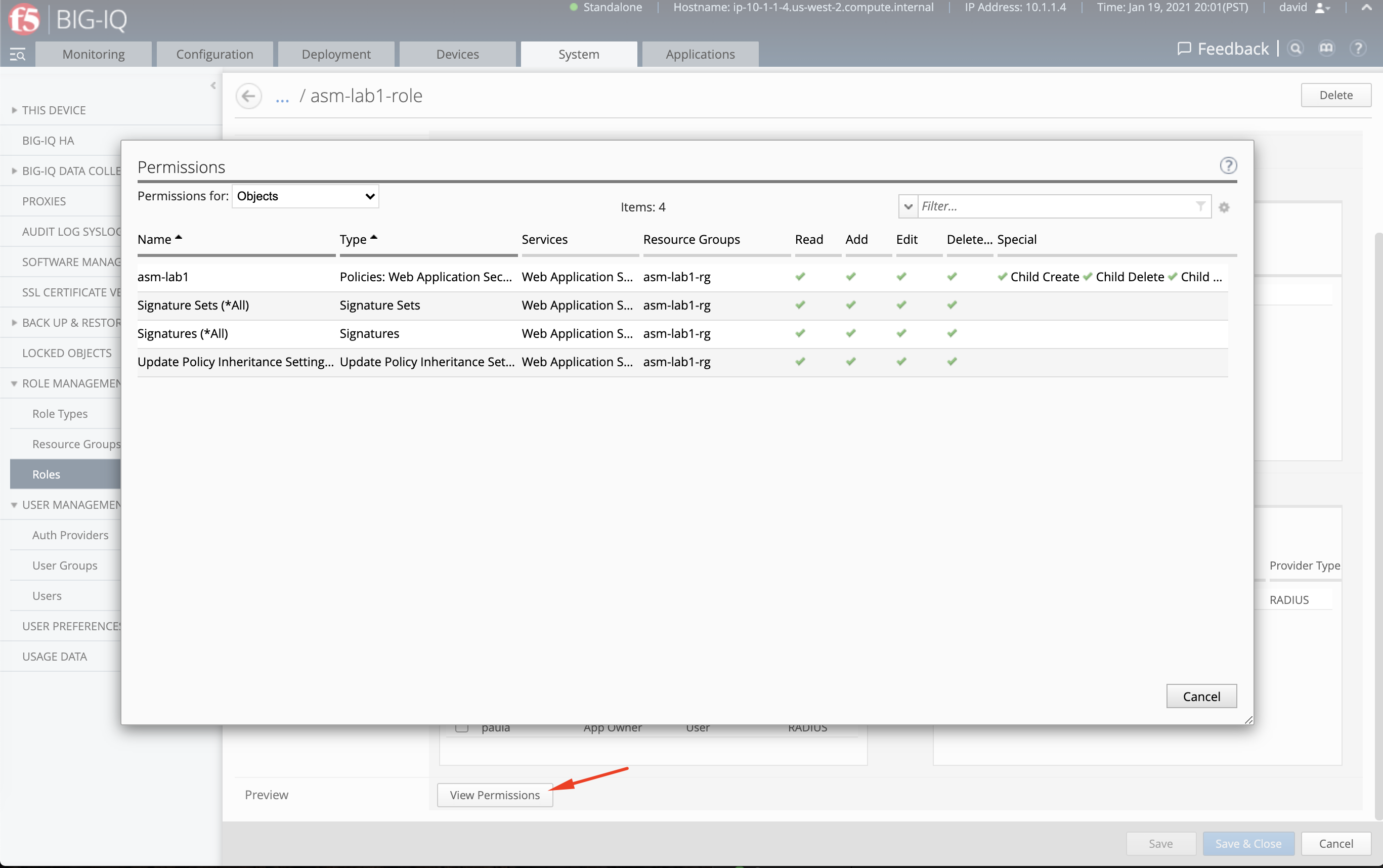
- You can view the permissions by scrolling down and click on the Previous button.
Display all Analytics and Events logs (david)¶
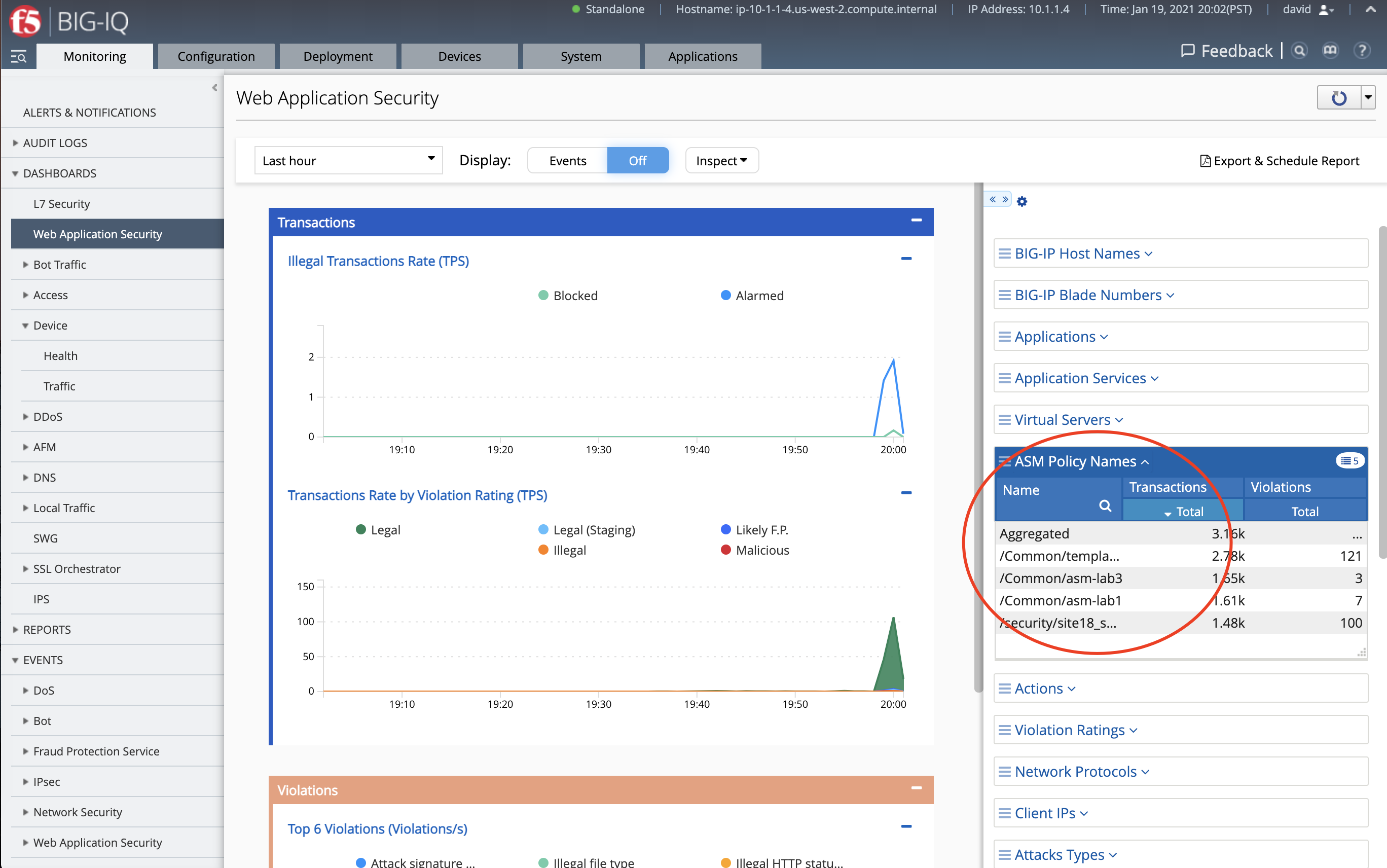
- Login to BIG-IQ as david and navigate under the Monitoring tab under Dashboards > Web Application Security.
David having full admin right to the BIG-IQ can see analytics for all the policies managed by BIG-IQ.
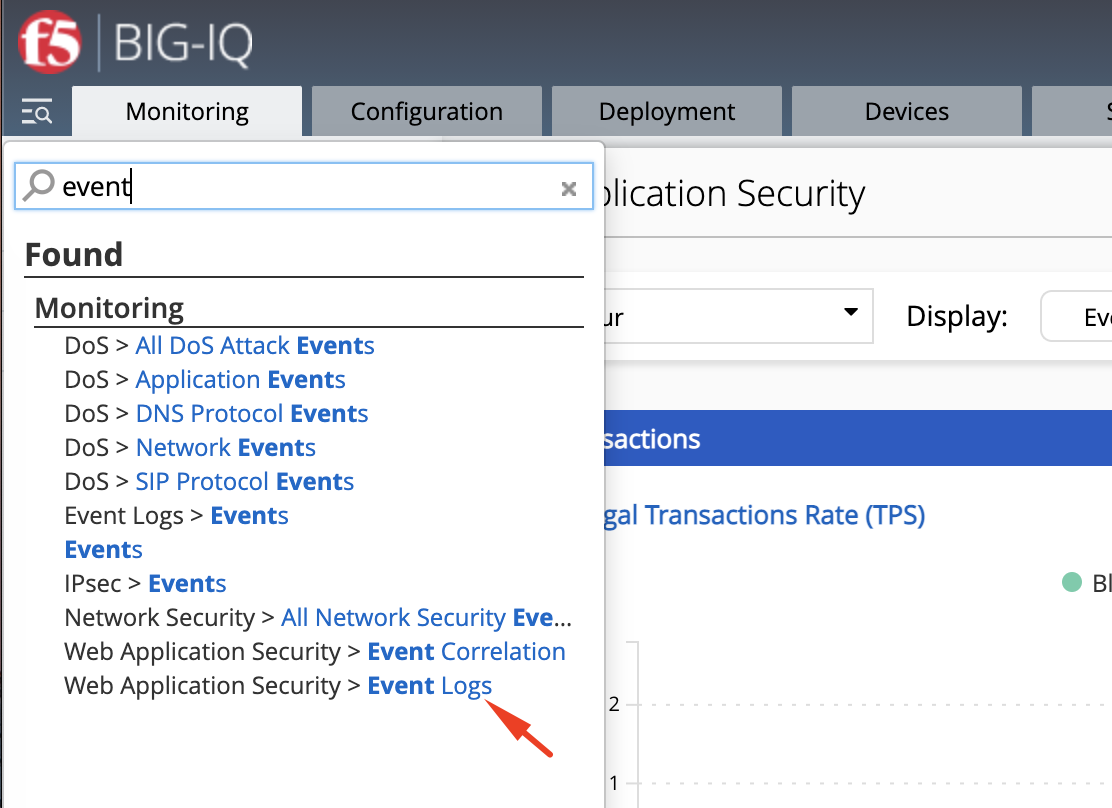
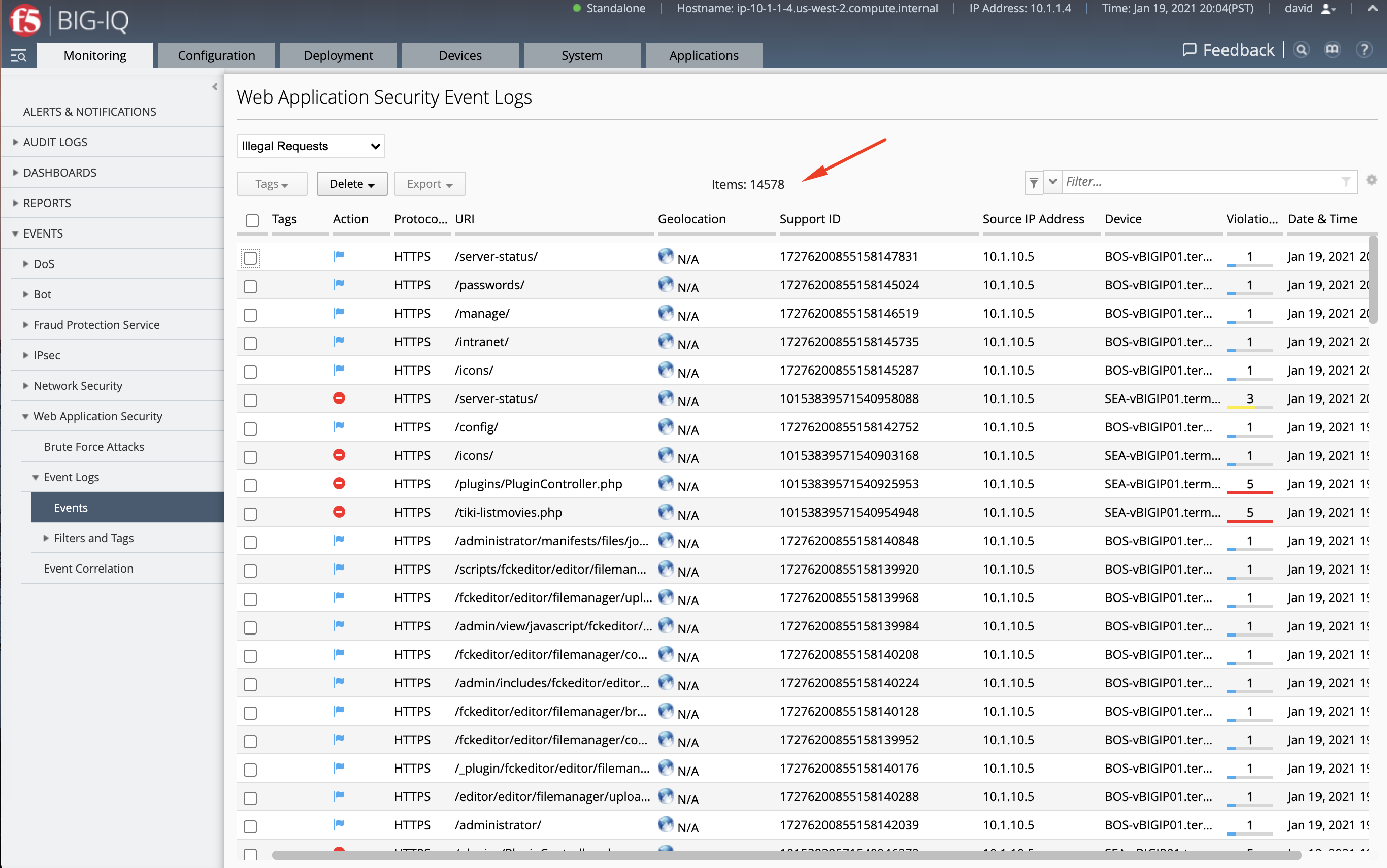
- Using the finder menu at the top right below the F5 logo, let’s now navigate to the WAF event logs.
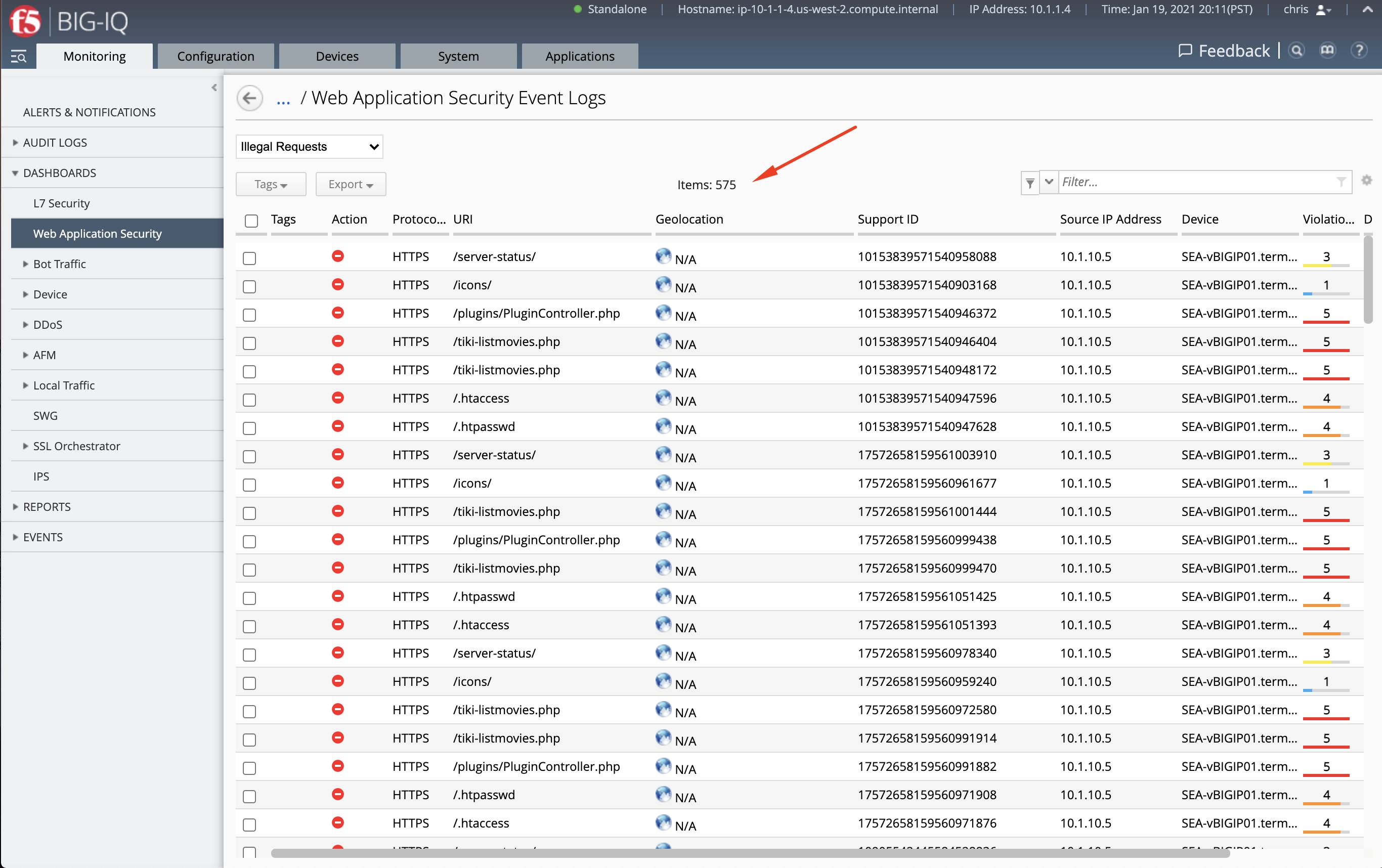
We notice the system has over 14k WAF events.
Display user privilege-based Analytics and Events logs (chris)¶
- Login to BIG-IQ as chris.
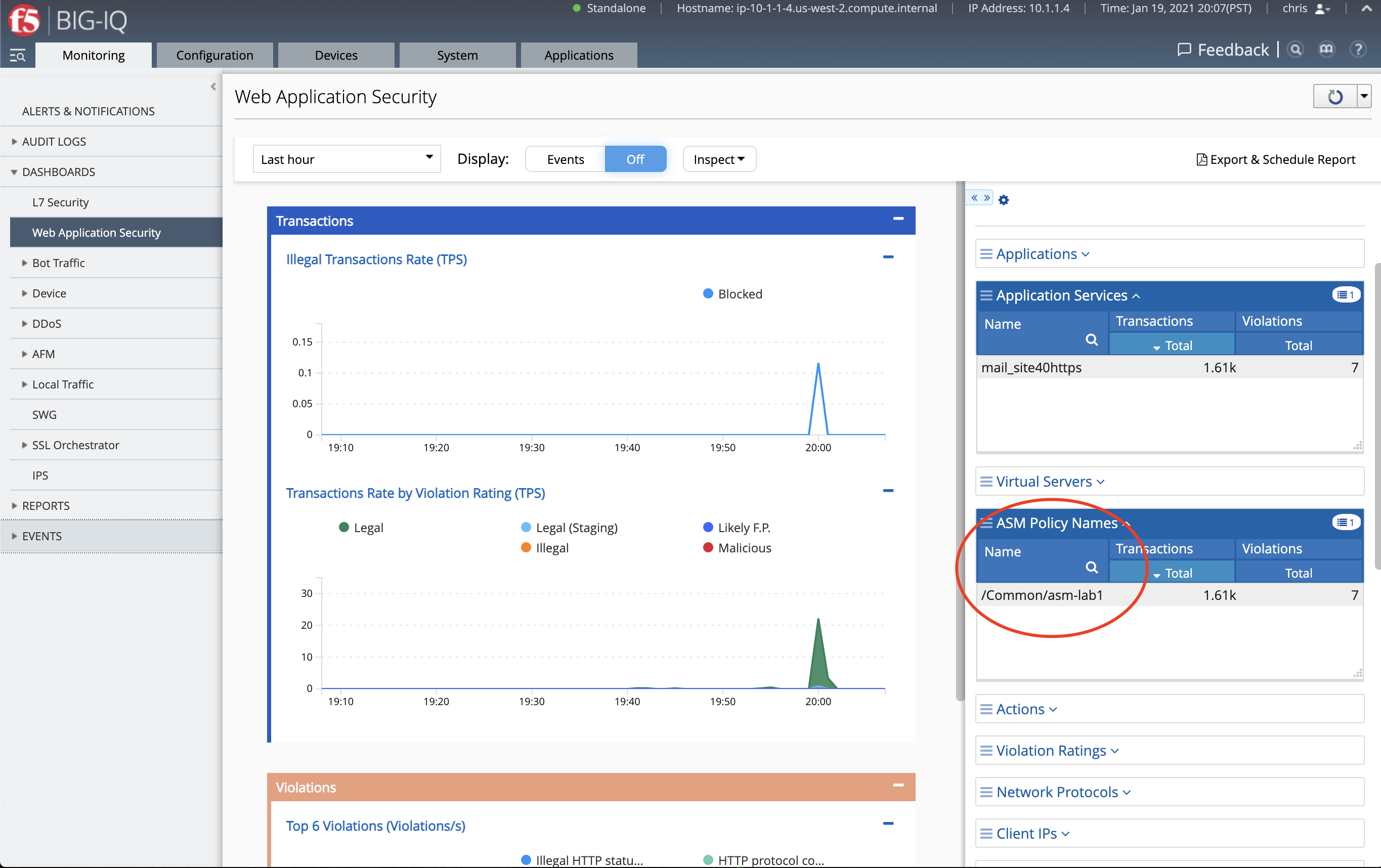
- Navigate under Monitoring tab under Dashboards > Web Application Security. Notice this time, chris is able to see only security analytics related to its policy assigned through the custom role.
- You can navigate to the WAF events from this page by clicking on Inspect, then Events logs.
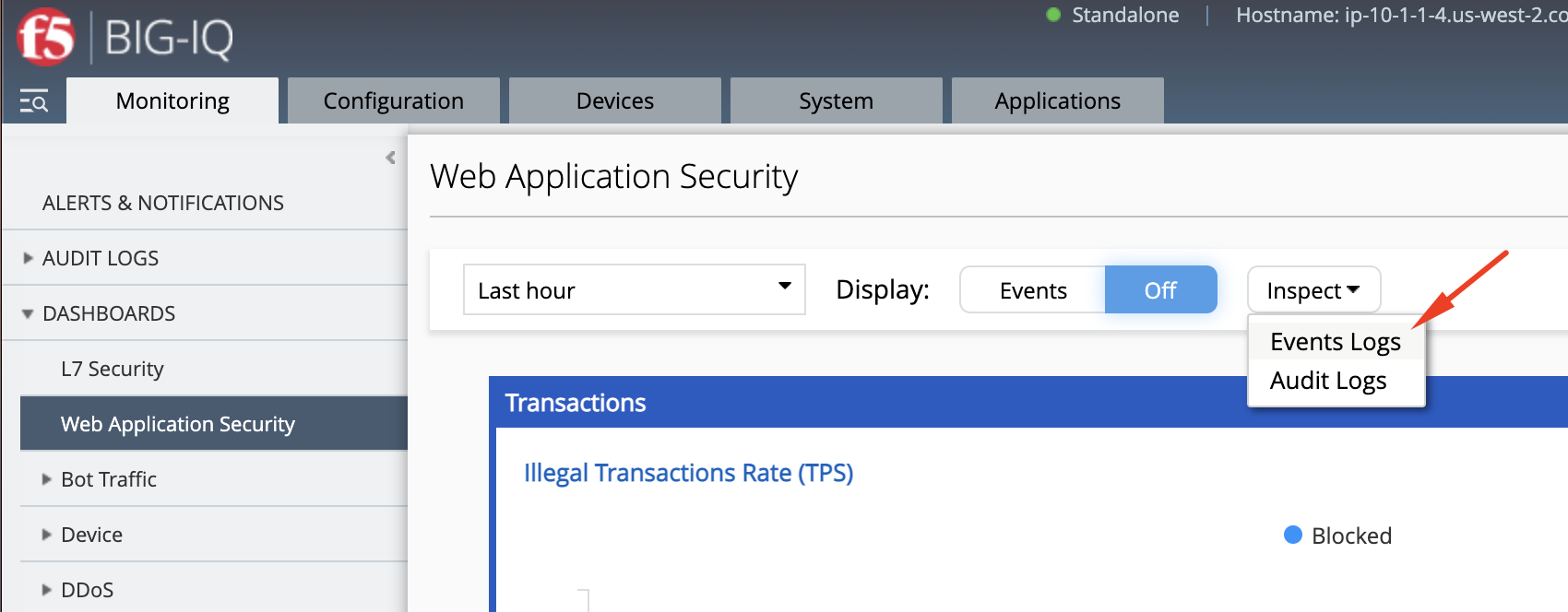
- We can confirm user chris is only able to see WAF events related to his policy
asm-lab1.
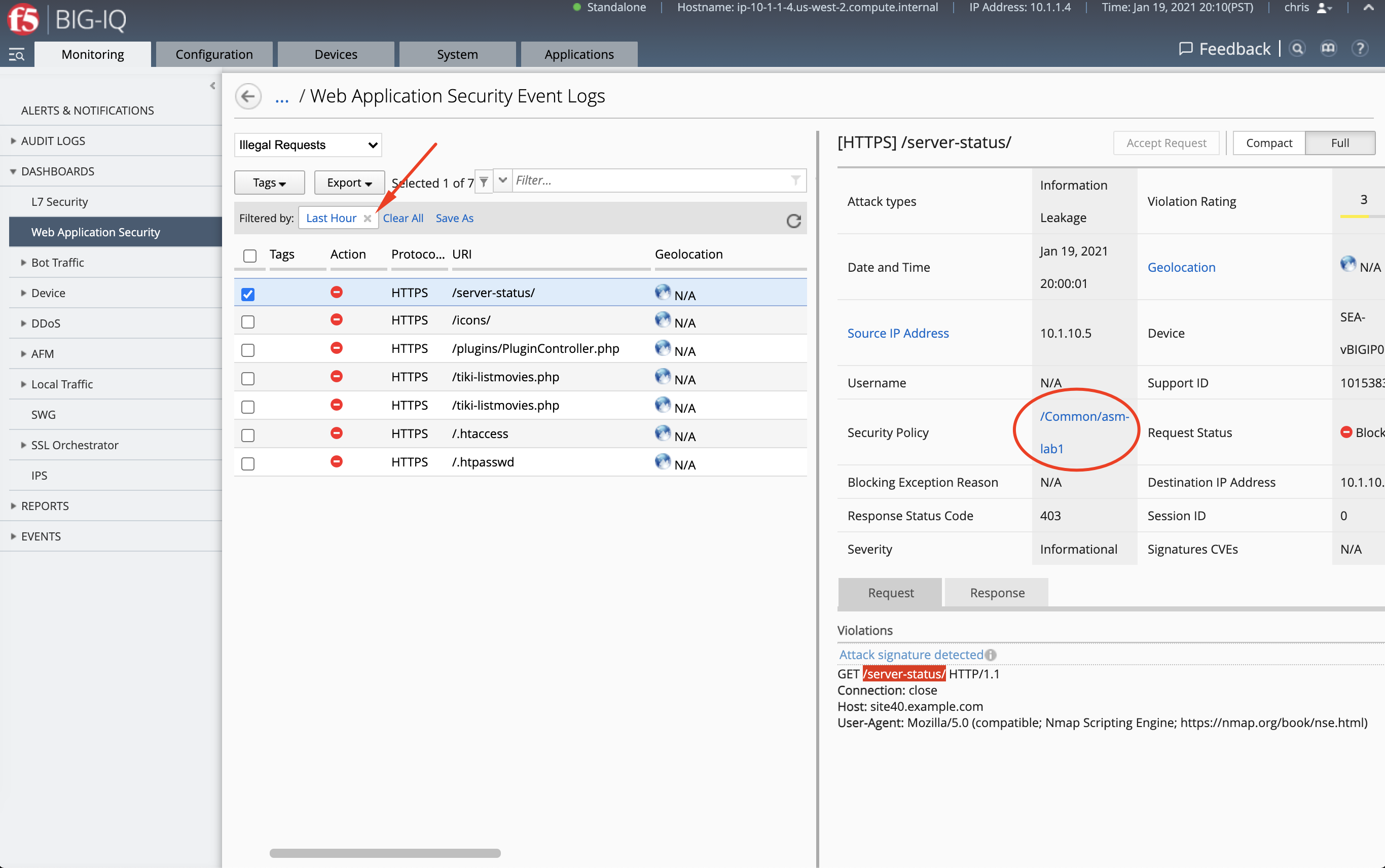
- Let’s now remove the time filter and see how many events is showing. Compare this value to the previous value when connected as david.
- Know that chris can also make changes to his policy and deploy those changes to the BIG-IP.