F5 Distributed Cloud Source | Edit on
Lab 4: Advanced Load Balancer WAF Object Creation¶
Scenario
A security finding indicates that the “send” API endpoint in the Message controller is susceptible to dynamic attacks, such as Cross-Site Scripting (XSS). This vulnerability allows scripts to be rendered within the message window, making them visible to the Customer Service team, an unacceptable security risk.
Implement measures to protect this endpoint, and ensure all APIs are safeguarded against dynamic attacks.
Expected Lab Time: 12 minutes
Task 1: Simulate a Unmitigated Attack¶
In this task, you will follow steps simulating an attack against an unprotected endpoint. The Distributed Cloud (XC) WAF object is pre-built for the next Task, but please review how to create this object via the Advanced Lab 4.
Using another browser tab, navigate to the the following URL.
http://<namespace>.lab-sec.f5demos.com/swagger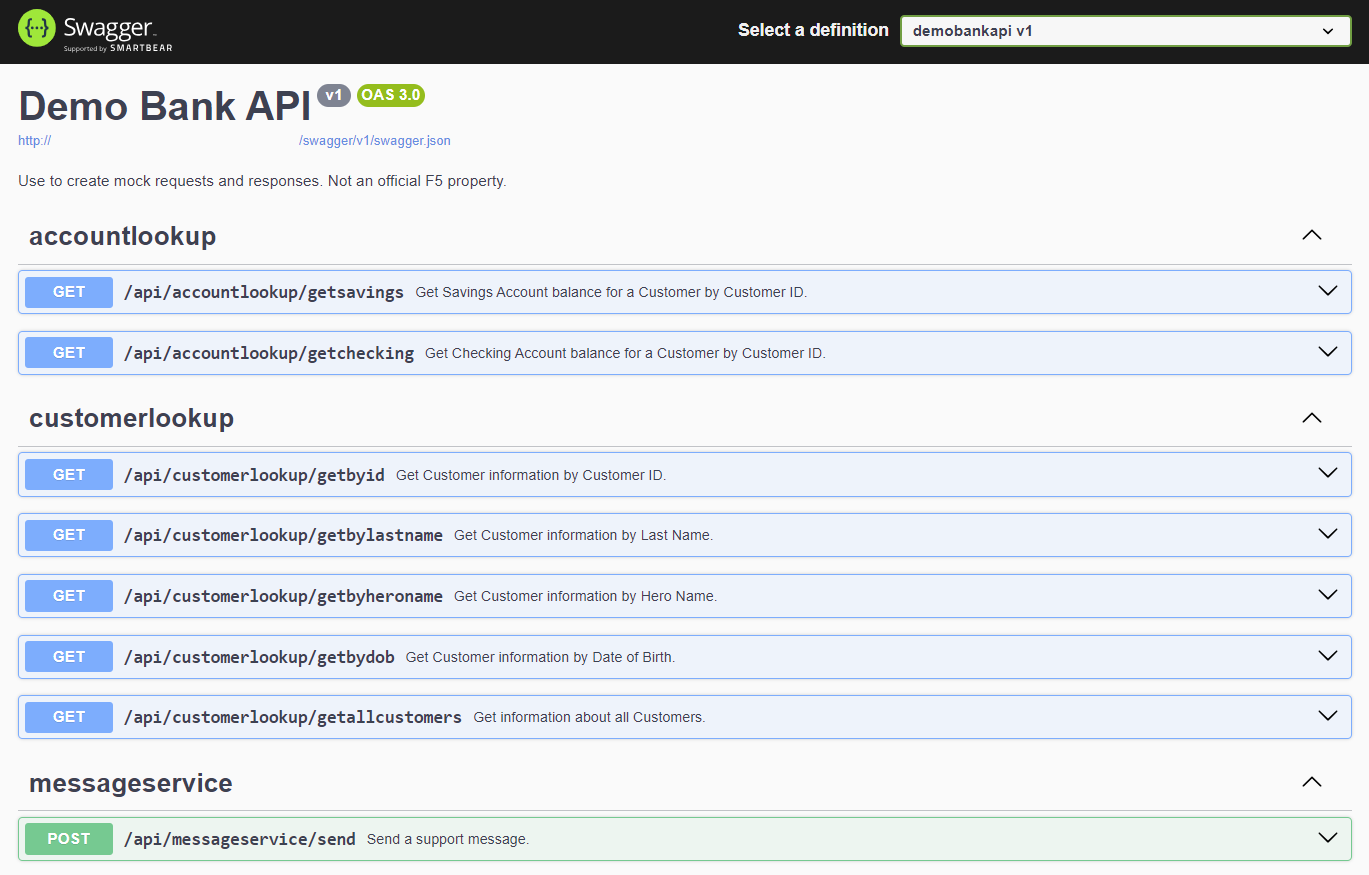
Within the Swagger page navigate and expand the messageservice/send endpoint, and click Try it out.
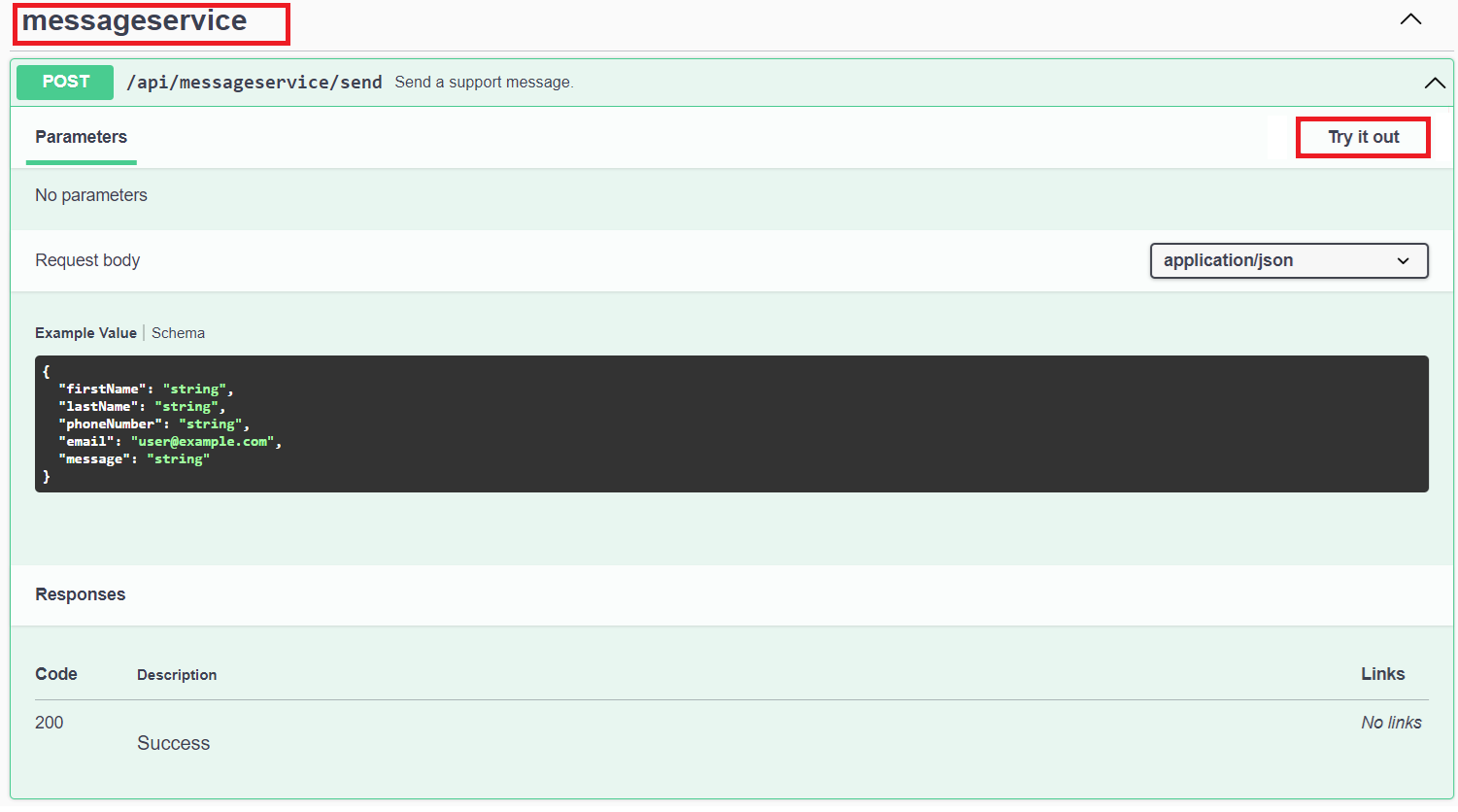
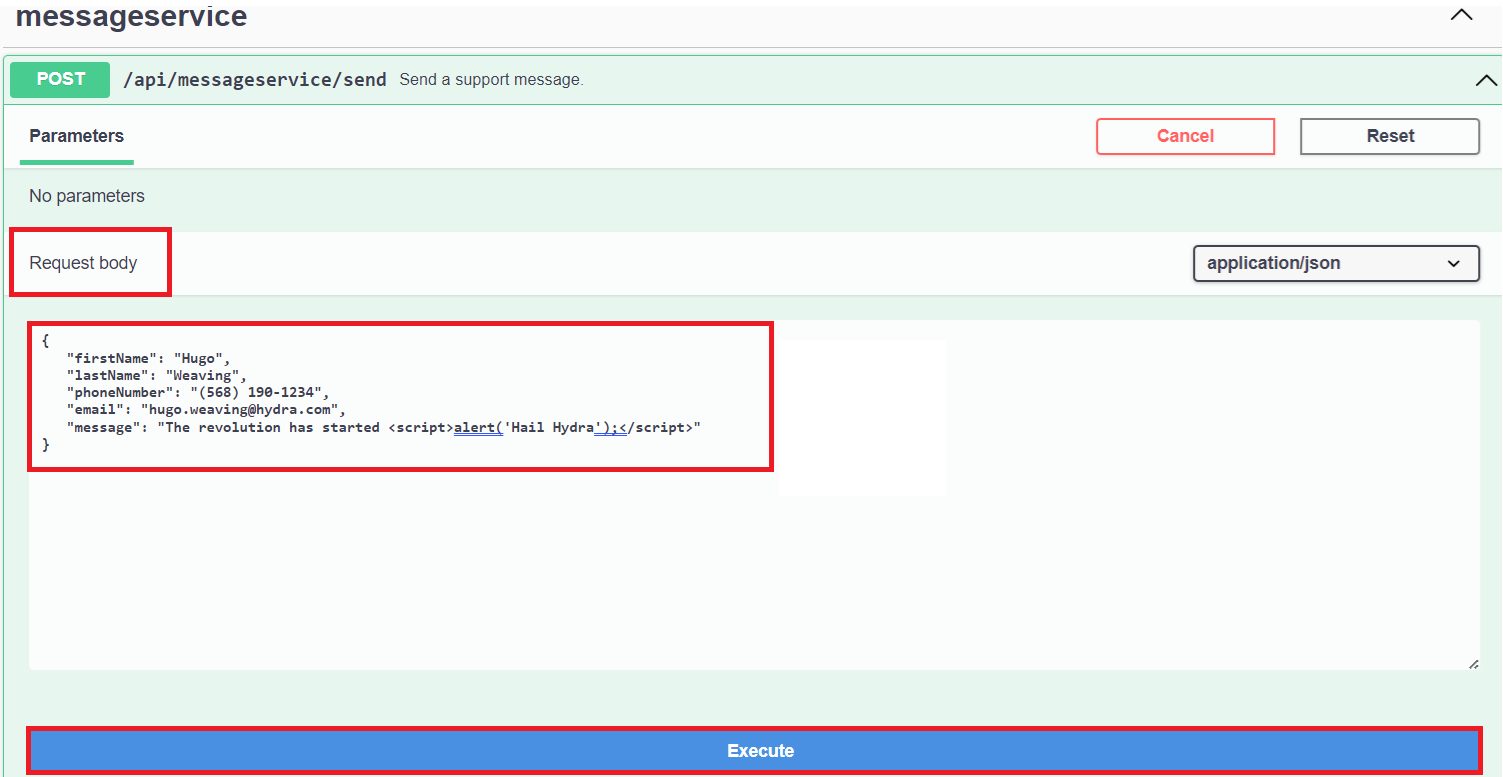
Copy the following JSON, paste within the Request body. Click on Execute.
{ "firstName": "Hugo", "lastName": "Weaving", "phoneNumber": "(568) 190-1234", "email": "hugo.weaving@hydra.com", "message": "The revolution has started <script>alert('Hail Hydra');</script>" }
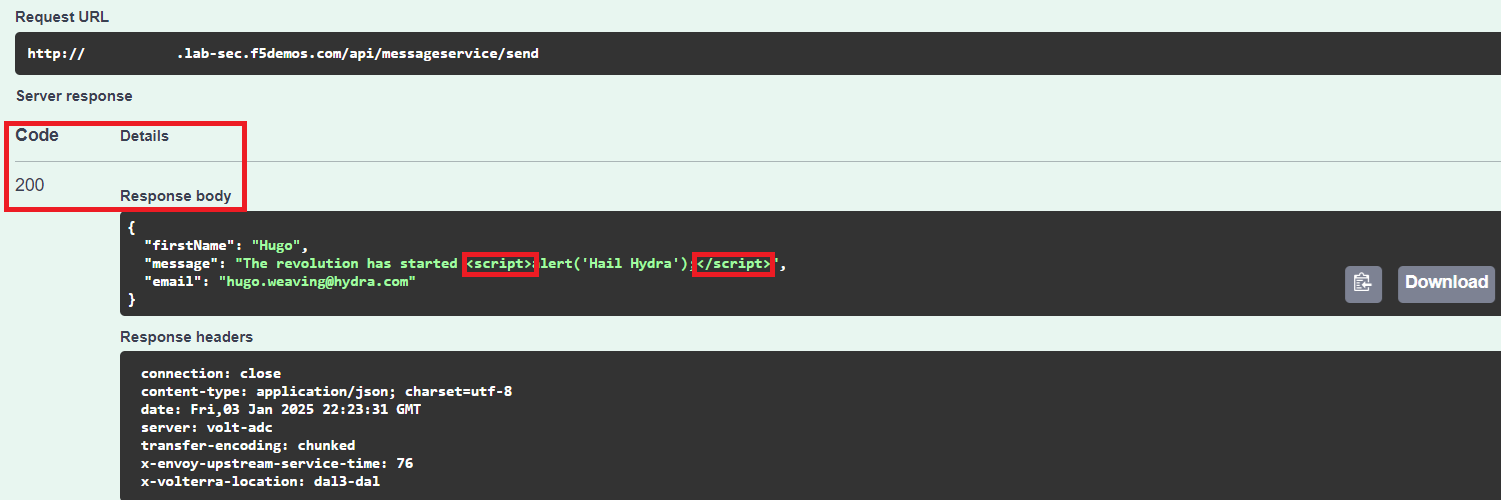
Review the Response, notice how the included <script> was accepted and included in the Reponse Body.
Note
If this endpoint was consumed by an actual ticket management system, the “<script>” could have been rendered in the user’s browser.
Task 2: Create a WAF policy Object¶
In this task, you will perform steps to create a WAF policy object, and apply this to your HTTP Load Balancer.
In the left-hand navigation of the Web App & API Protection service, click on App Firewall under the Manage section.
In the resulting App Firewall window, click on Add App Firewall at the top left or middle of the window.
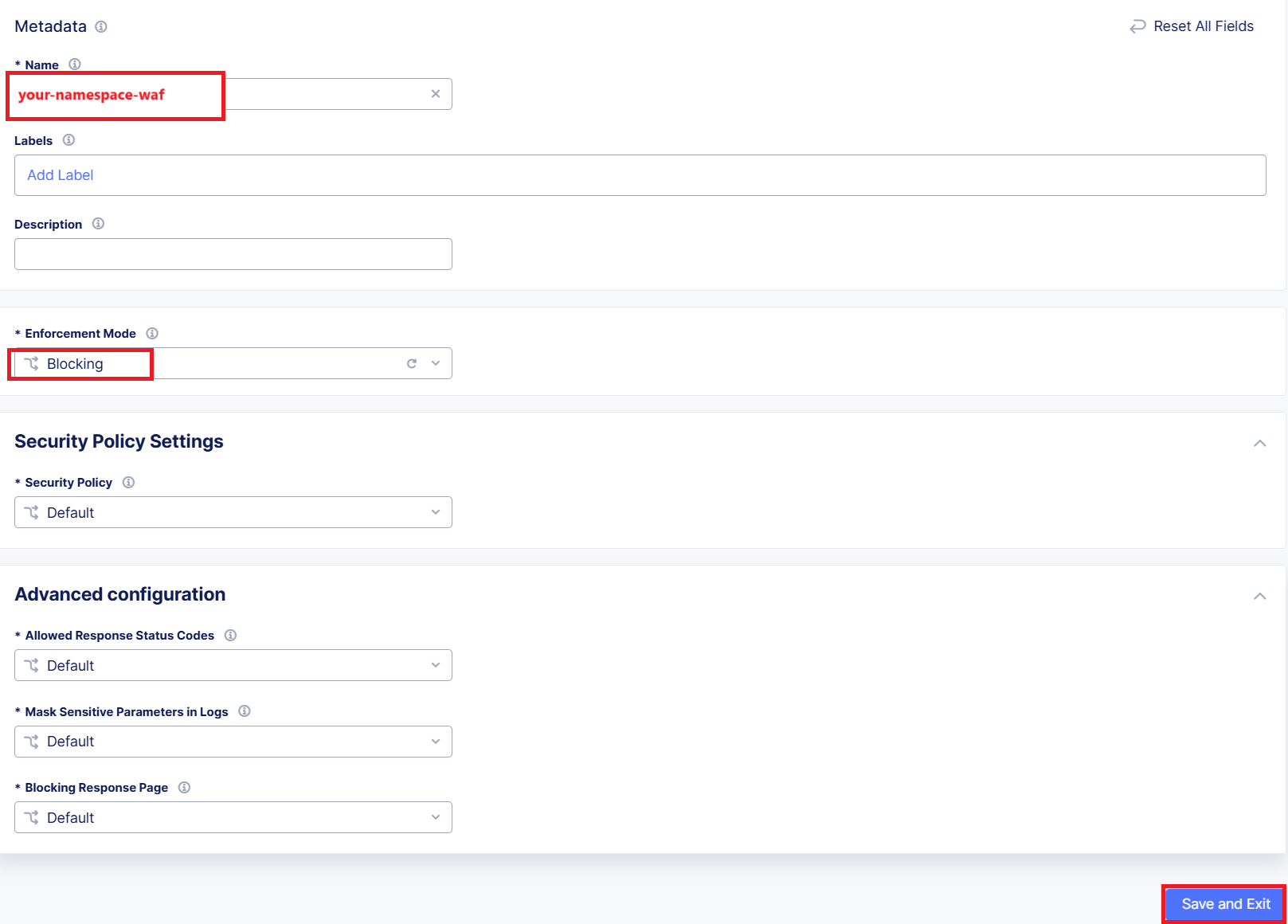
Within the App Firewall object, configure the following. Values where <namespace> is required, use the name of your given namespace.
Metadata:Name:
<namespace>-wafEnforcement Mode:
Blocking
Leave all other settings at default. Click Save and Exit button.
Task 3: Attach WAF policy to your HTTP Load Balancer¶
In this task, you will follow steps to attach a WAF policy to your Load Balancer.
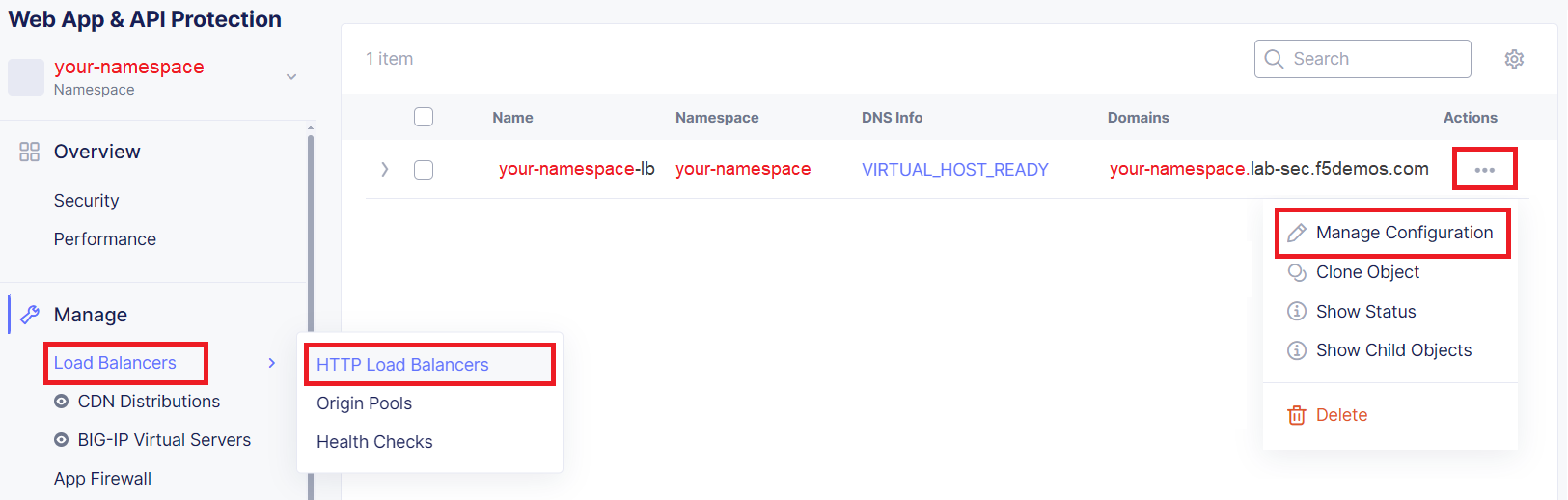
In the left-hand navigation of the Web App & API Protection service under the Manage section, click on Load Balancers > HTTP Load Balancers under the Manage section.
In the resulting Load Balancers window, click on the three dots … in the Action column, and the select Manage Configuration.
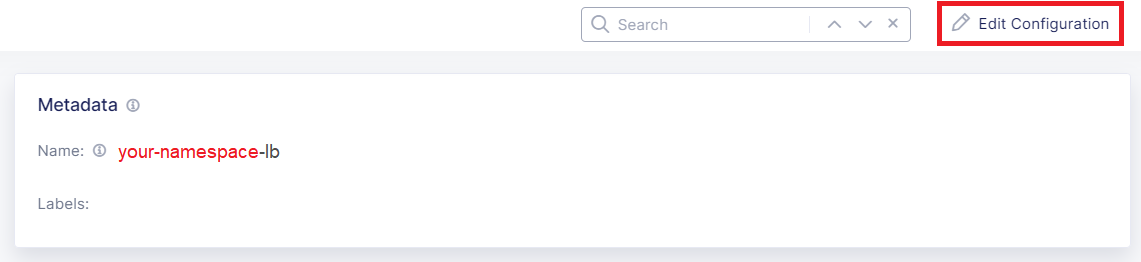
Click Edit Configuration in the top-right corner.
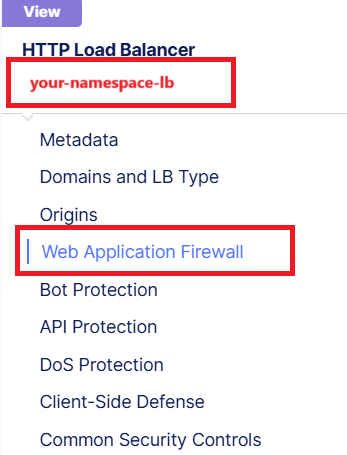
Using the left-hand navigation, click the Web Application Firewall link.
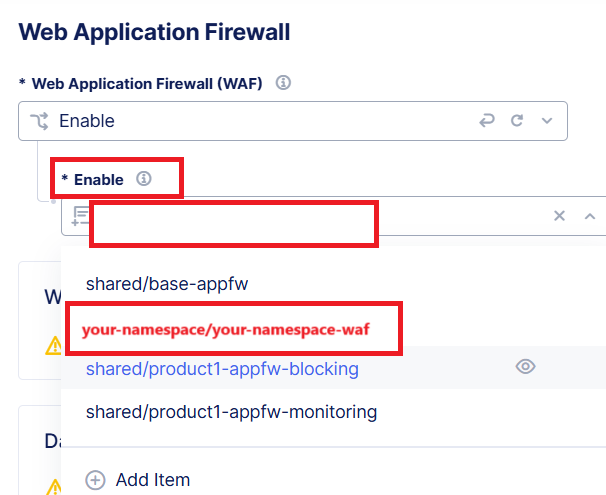
Under the Web Application Firewall (WAF) drop-down, Select Enable
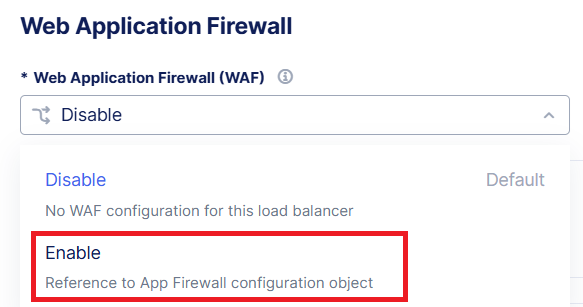
Under the Enable menu drop-down, select your <namespace>-waf object you just created.
Scroll to the bottom of the HTTP Load Balancer configuration page, and select Save and Exit
Task 4: Simulate a Mitigated Attack¶
In this task you will follow steps simulating an attack againt a protected endpoint.
Using another browser tab, navigate to the the following URL.
http://<namespace>.lab-sec.f5demos.com/swagger
Within the Swagger page navigate and expand the messageservice/send endpoint, and click Try it out.

Copy the following JSON, paste within the Request body. Click on Execute.
{ "firstName": "Hugo", "lastName": "Weaving", "phoneNumber": "(568) 190-1234", "email": "hugo.weaving@hydra.com", "message": "The revolution has started <script>alert('Hail Hydra');</script>" }

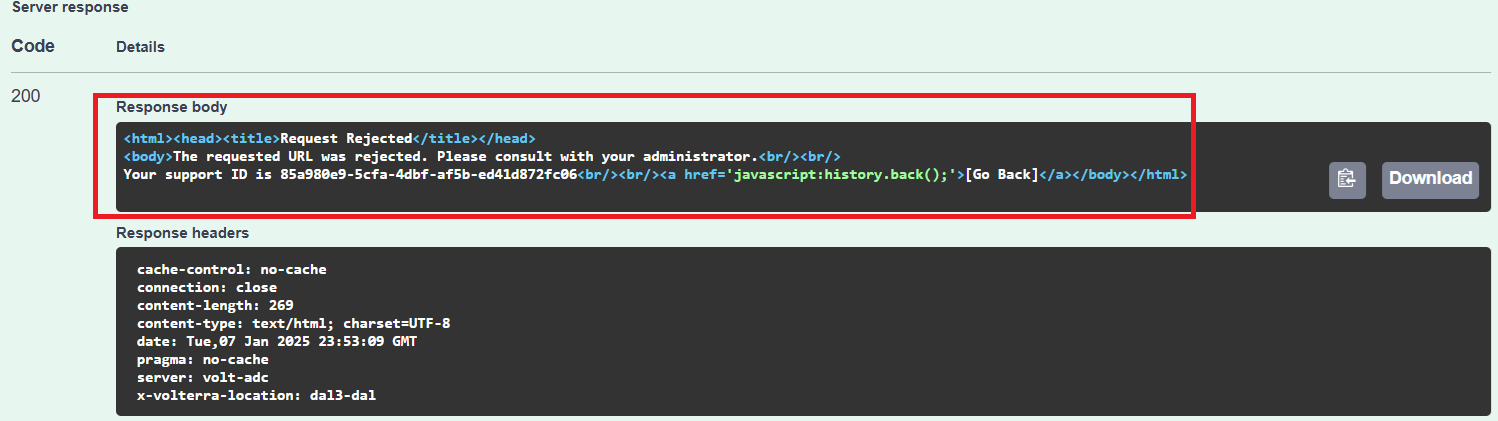
Review the Server Response; notice how a block message was presented within the Server Response body.
End of Lab
