F5 Identity and Access Management Solutions > Archived Identity & Access Management Labs > 100 Series: Access Foundational Concepts Source | Edit on
Lab 3: Intro to Per-Request Policies¶
Section 1 - Setup Lab Environment¶
To access your dedicated student lab environment, you will require a web browser and Remote Desktop Protocol (RDP) client software. The web browser will be used to access the Lab Training Portal. The RDP client will be used to connect to the Jump Host, where you will be able to access the BIG-IP management interfaces (HTTPS, SSH).
Click DEPLOYMENT located on the top left corner to display the environment
Click ACCESS next to jumpohost.f5lab.local

Select your RDP resolution.
The RDP client on your local host establishes a RDP connection to the Jump Host.
Login with the following credentials:
- User: f5lab\user1
- Password: user1
After successful logon the Chrome browser will auto launch opening the site https://portal.f5lab.local. This process usually takes 30 seconds after logon.
Click the Classes tab at the top of the page.
Scroll down the page until you see 101 Intro to Access Foundational Concepts on the left

Hover over tile Intro to Per-Request Policies. A start and stop icon should appear within the tile. Click the Play Button to start the automation to build the environment
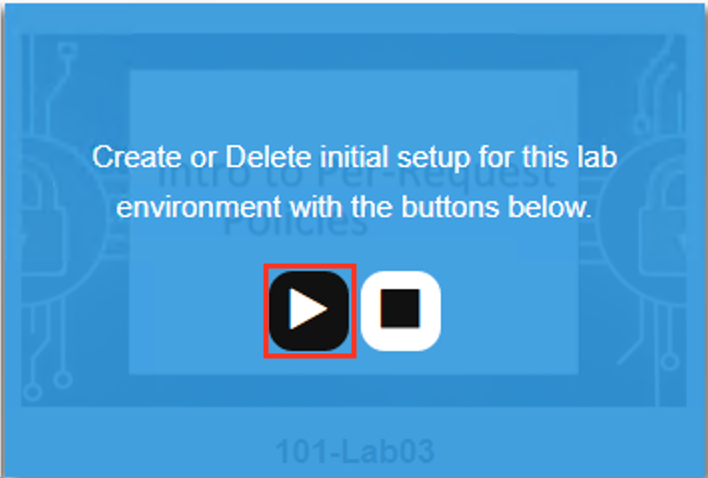
The screen should refresh displaying the progress of the automation within 30 seconds. Scroll to the bottom of the automation workflow to ensure all requests succeeded. If you experience errors try running the automation a second time or open an issue on the Access Labs Repo.
Section 2 - Step-up Authentication¶
Task 1 - Test the existing Configuration¶
From the jumpbox, navigate to https://app.acme.com. You will be redirected to the SAML IdP and be presented a logon page.
Logon with the credentials username: coyote@acme.com password: user1
After a successful logon at the IdP you are redirected to back to https://app.acme.com and presented a portal page.
Click the Admin View button.
You are succesfully logged into admin view without asking for any further credentials. We want to add additional security to the admin view by requiring MFA at the IdP for this portion of the website.
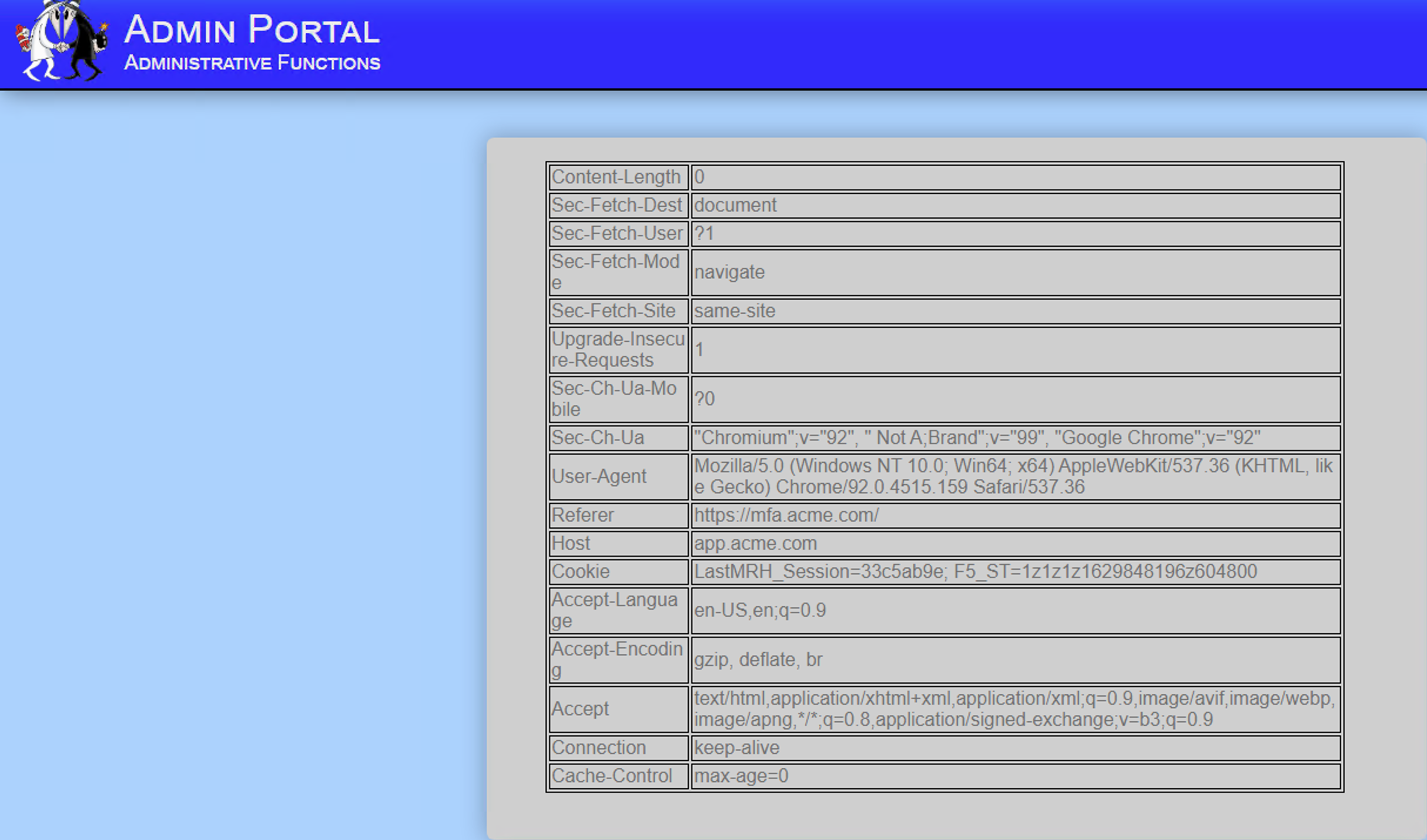
Task 2 - Create a Step-up Authentication Per-Request Policy¶
From a browser navigate to https://bigip1.f5lab.local
Login with username admin and password admin

Navigate to Access >> Profiles/Policies >> Per-Request Policies >> click the Plus Sign(+).

Enter the Name app-prp
Toggle English (en) to the list of Accepted Languages
Click Finished
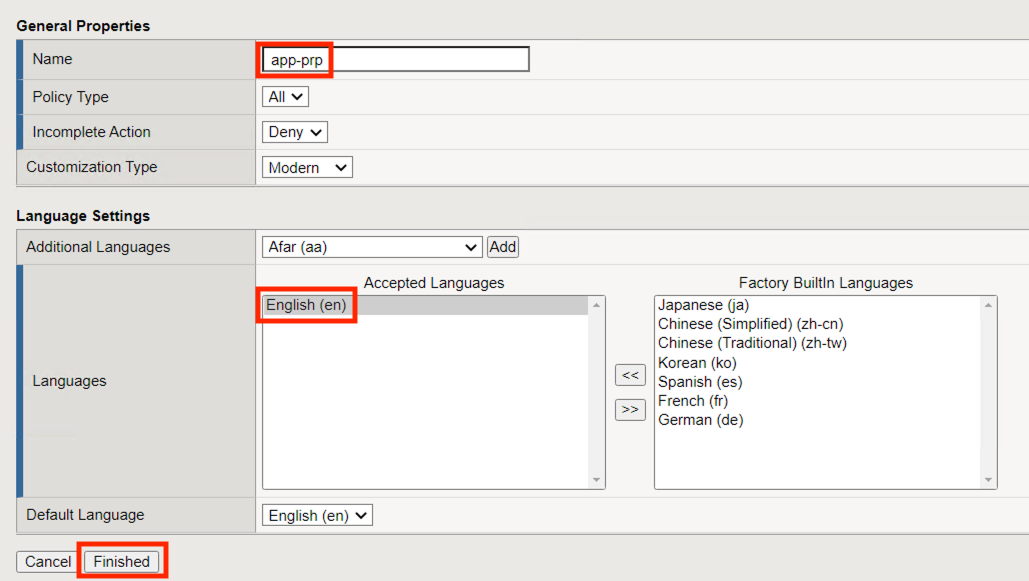
Click Edit
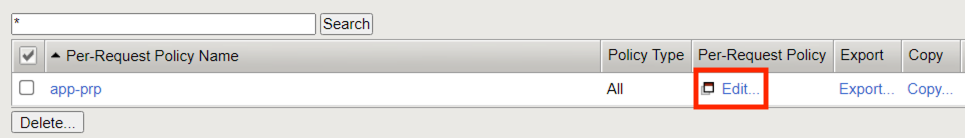
Click Add New Subroutine
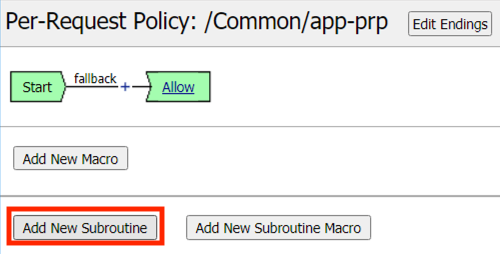
Enter the Name SAML Auth
Click Save
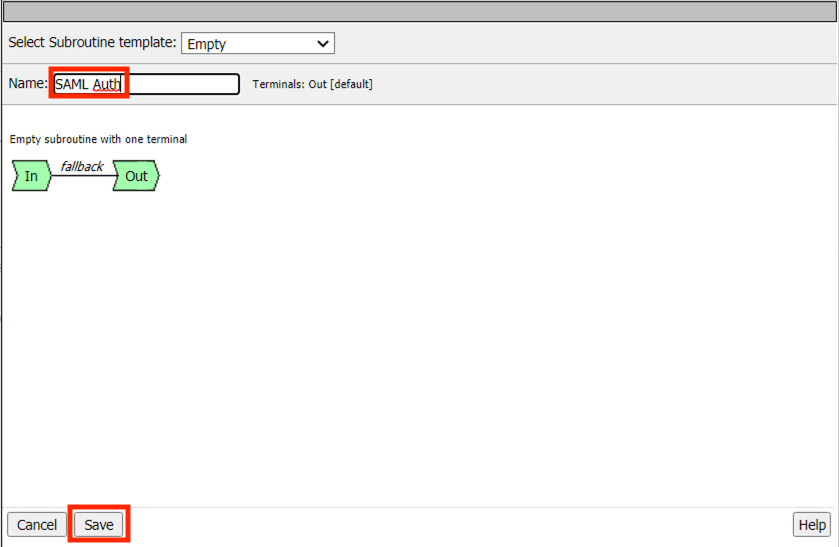
Click Edit Terminals
Click Add Terminal
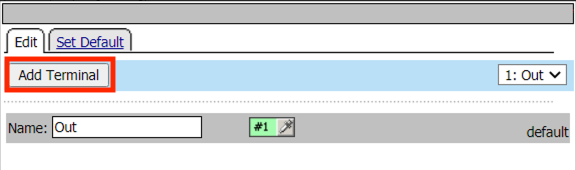
Enter the Name Fail on the line with a red #2
Enter the Name Pass on the line with a green #1
Click the up arrow on the pass line to move it above the Fail Terminal
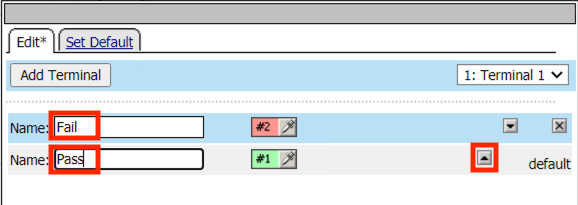
Click the Set Default tab
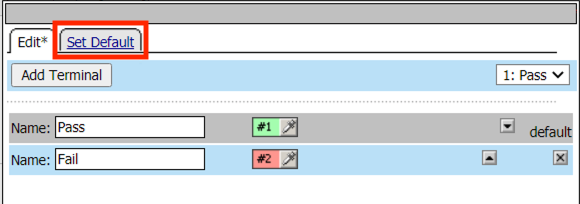
Select Fail as the default
Click Save
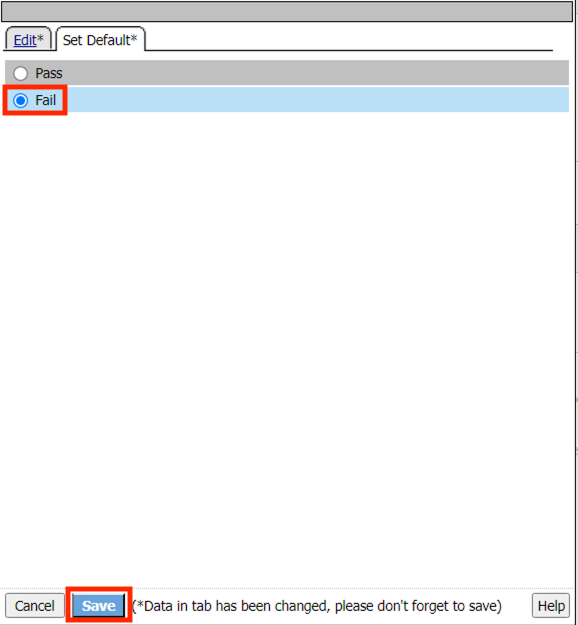
Click the Plus Symbol (+) between In and Pass
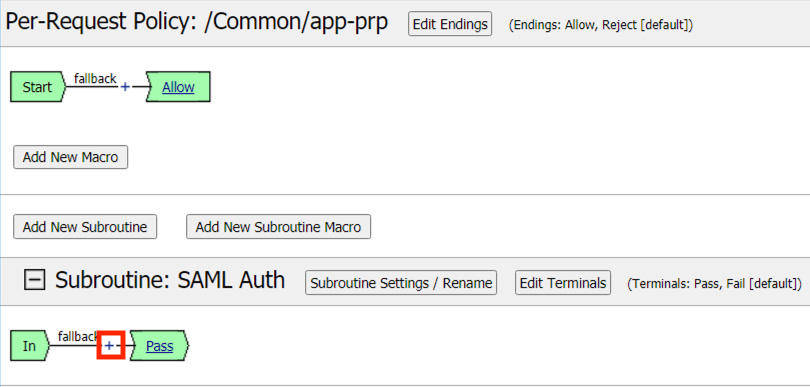
Click thee Authentication tab
Select SAML Auth
Click Add Item
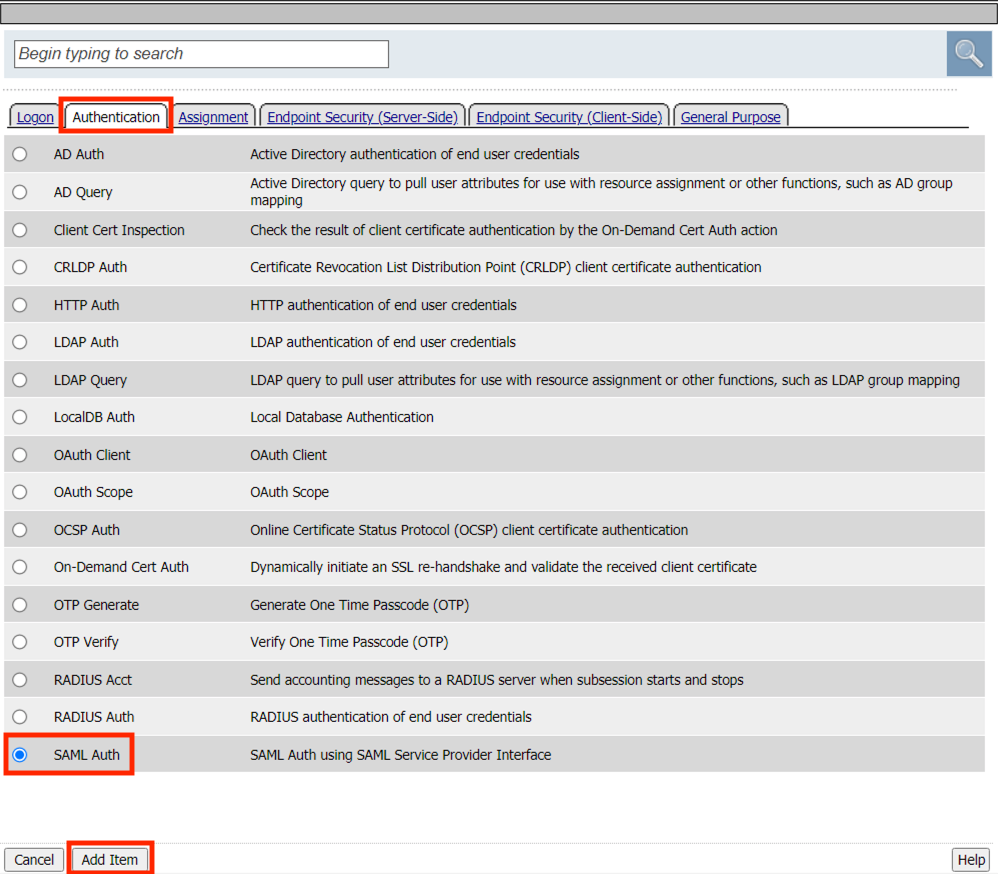
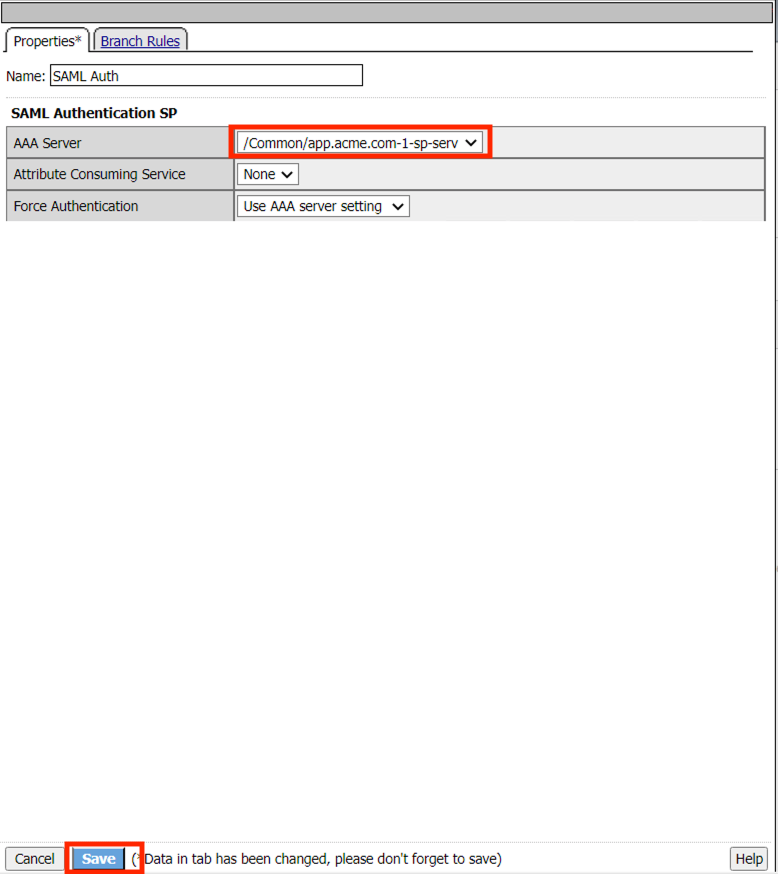
From the AAA Server dropdown select /Common/app.acme.com-1-sp-serv
Click Save
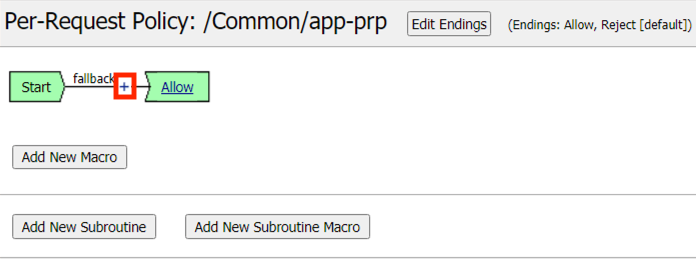
Click the Plus Symbol (+) between Start and Allow
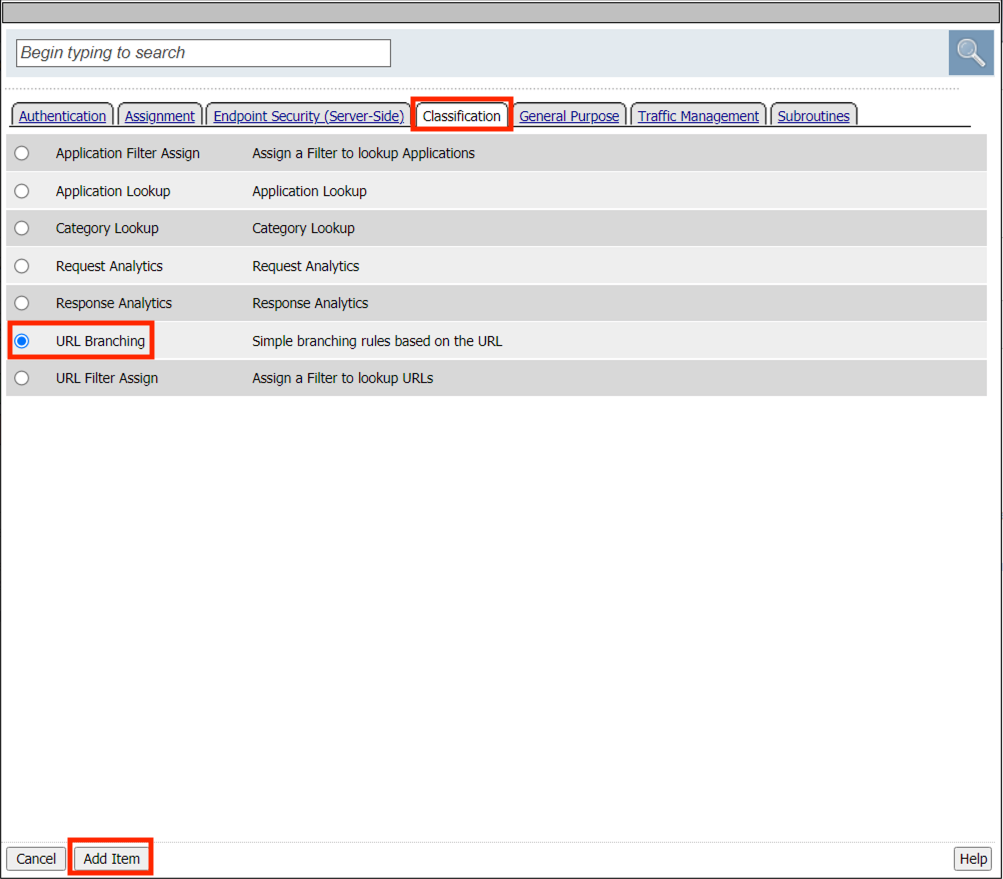
Click the Classification tab
Select URL Branching
Click Add Item
Click the Branch Rules tab
Enter the Name MFA
Click change
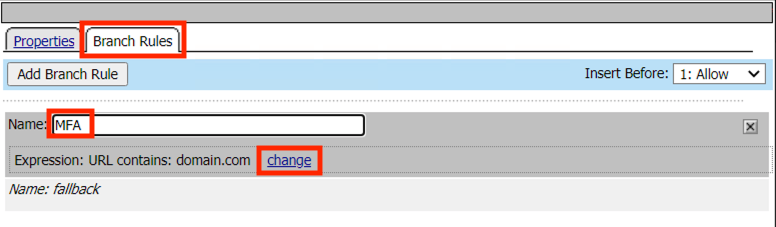
For URL Contains enter https://app.acme.com/admin/
Click Finished
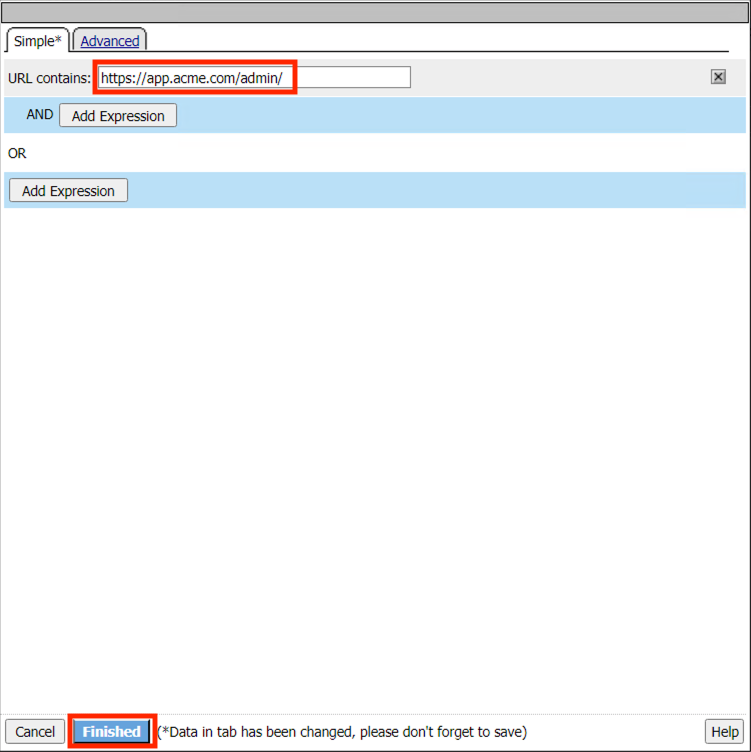
Click Save
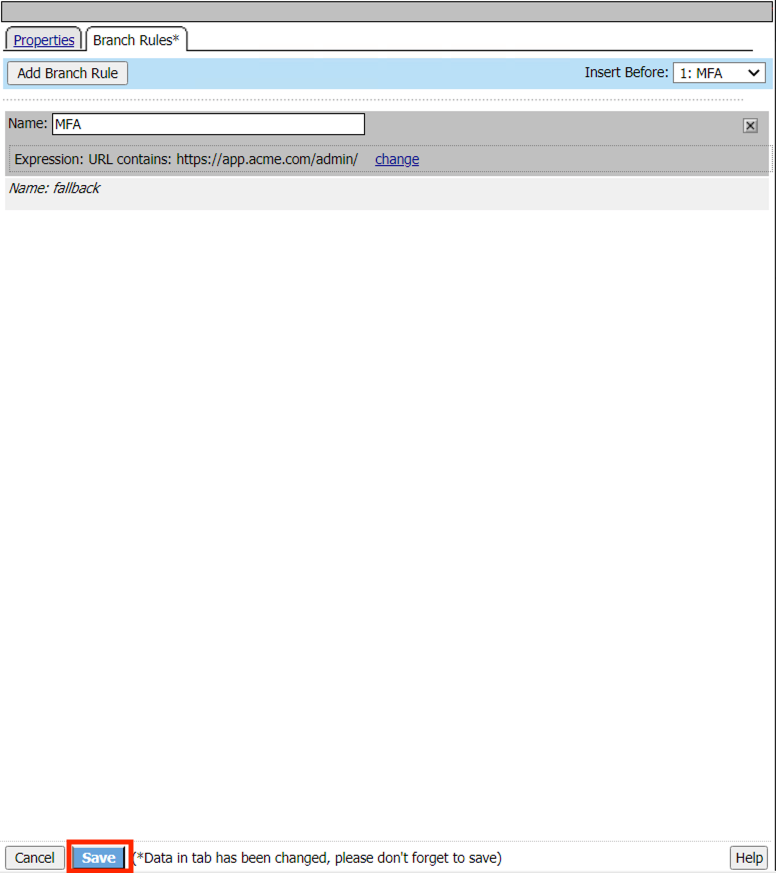
Click the Plus Symbol (+) on the MFA branch between URL branching and Allow
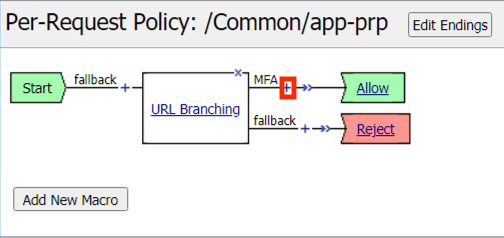
Click the Subrooutines tab
Select SAML Auth
Click Add Item
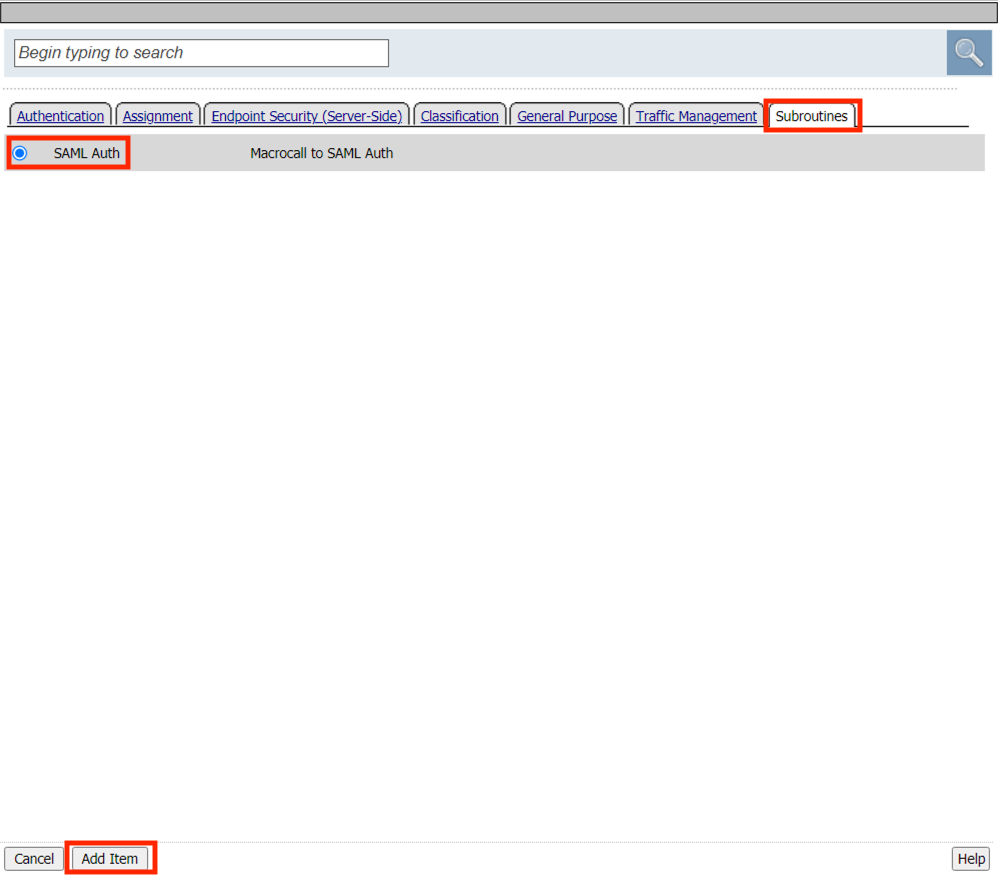
Click the Reject Terminal located at the end of the URL Branching fallback branch
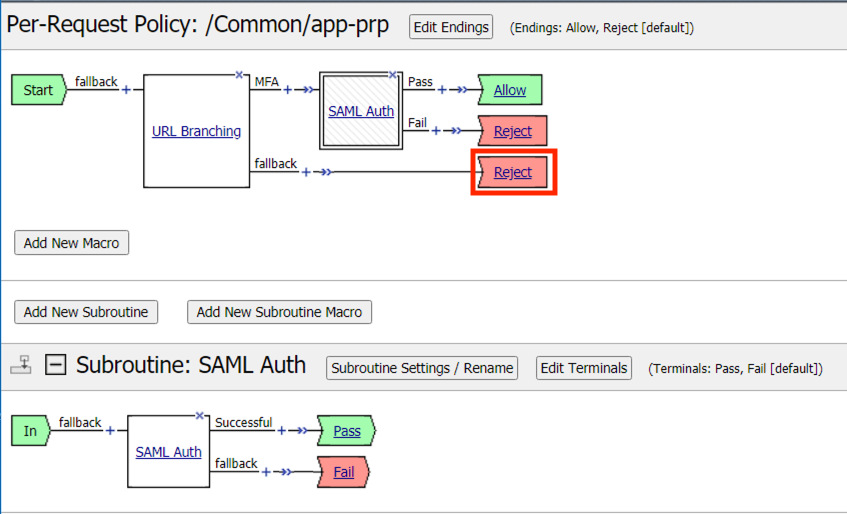
Select Allow
Click Save
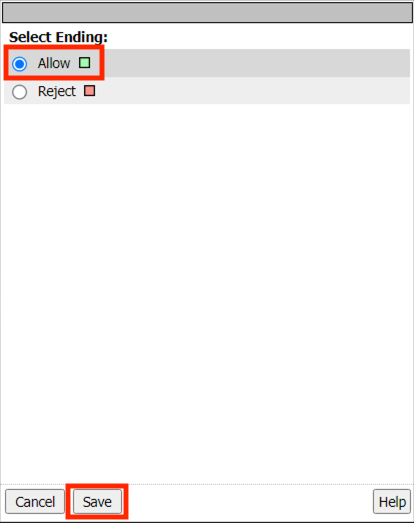
The policy should now look like the one below
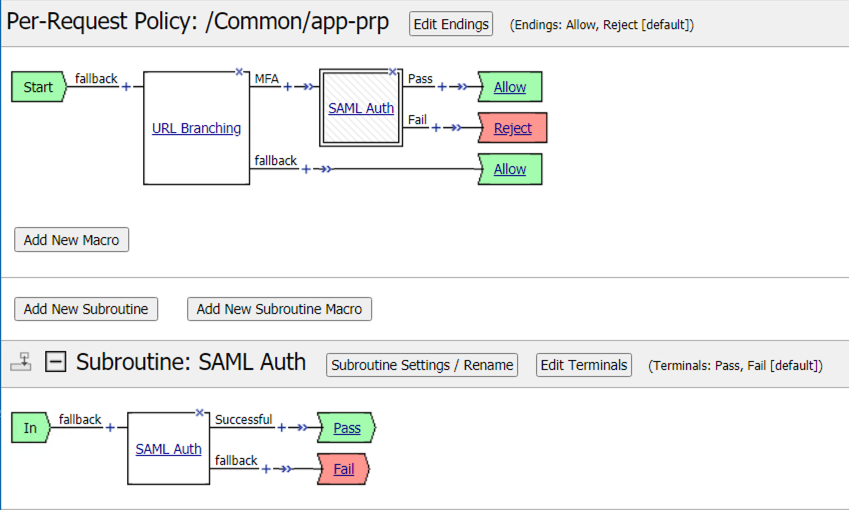
Task 3 - Attach the Per-Request Policy¶
Navigate to Local Traffic >> Virtual Servers >> Virtual Server List. Not the Plus Symbol (+)
Click app-https
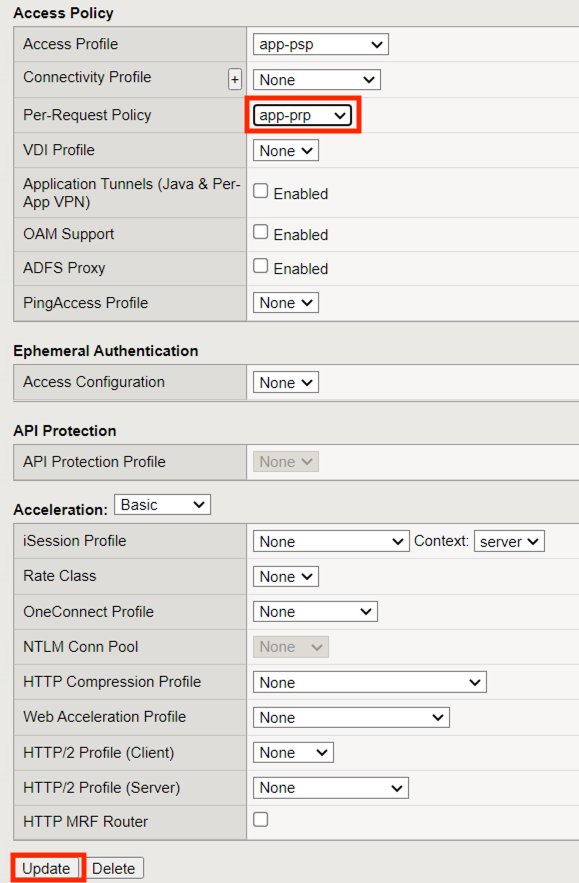
Scroll to the Access Policy section of the virtual server
From the Per-Request Policy dropdown select app-prp
Click Update
Task 4 - Test Step-Up Authentication¶
From the jumpbox, navigate to https://app.acme.com. You will be redirected to the SAML IdP and be presented a logon page.
Logon with the credentials username: coyote@acme.com password: user1

After a successful logon at the IdP you are redirected to back to https://app.acme.com and presented a portal page.
Click the Admin View button.

The page is now requires a new SAML assertion with a higher level authentication context class. The user is now prompted for certificte authentication. Selet the user1 certifcate
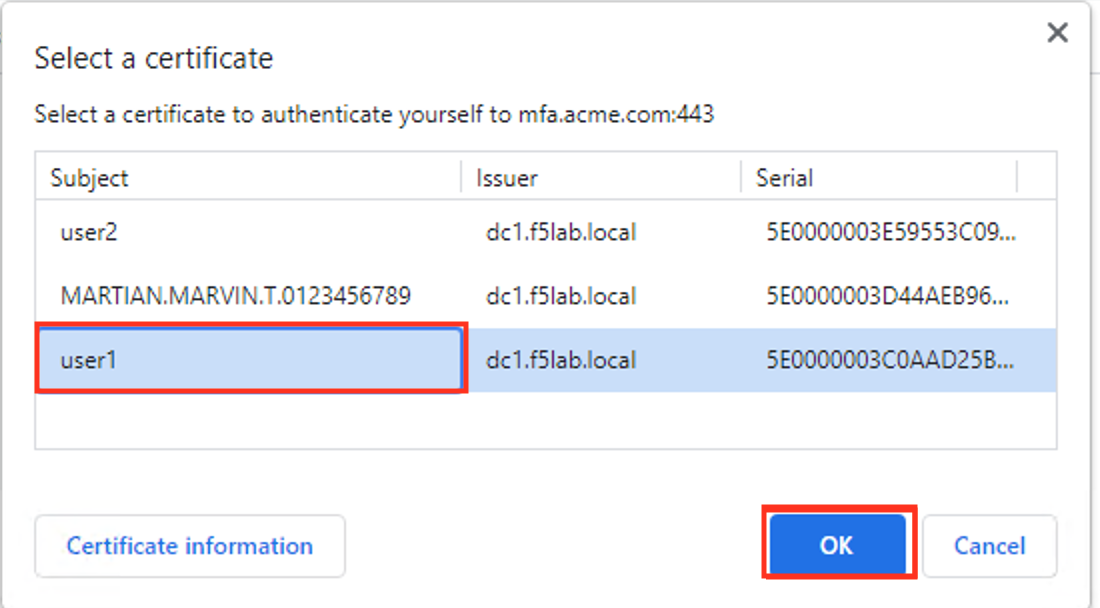
After successfully providing a certificate you kow have access to the admin page.

Section 3 - Header Injection¶
Task 1 - Add Header Injection to an existing Per-Request Policy¶
BIG-IP APM often has access to information that the application may not have access to natively. Through the power of the per-request policy we can inject additional headers into each request . Let’s explore adding an additional header after the SAML auth subroutine.
From a browser navigate to https://bigip1.f5lab.local
Login with username admin and password admin

Navigate to Access >> Profiles/Policies >> Per-Request Policies.
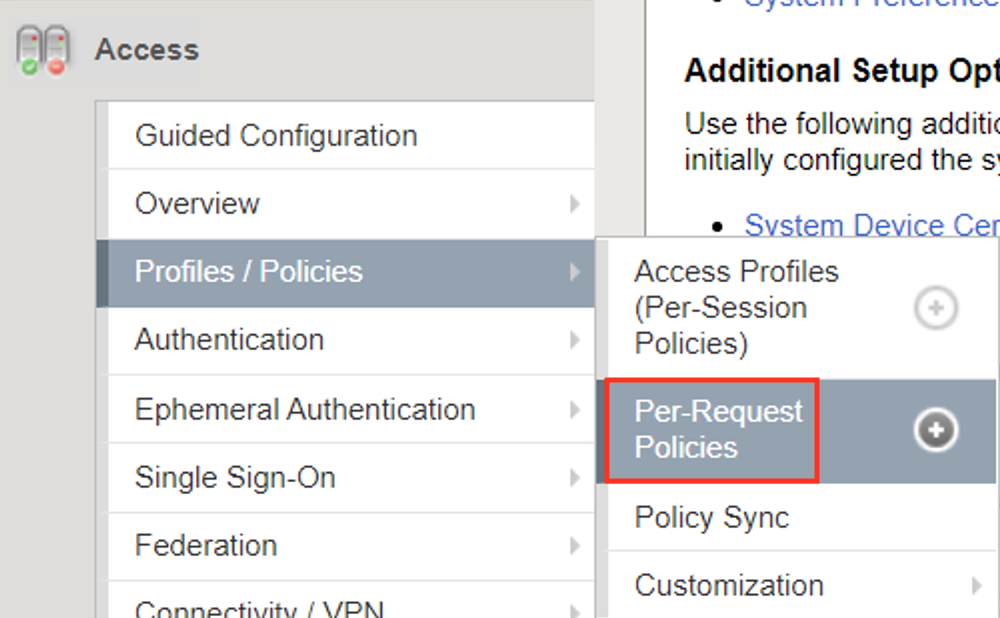
Click Edit to the right of add-prp

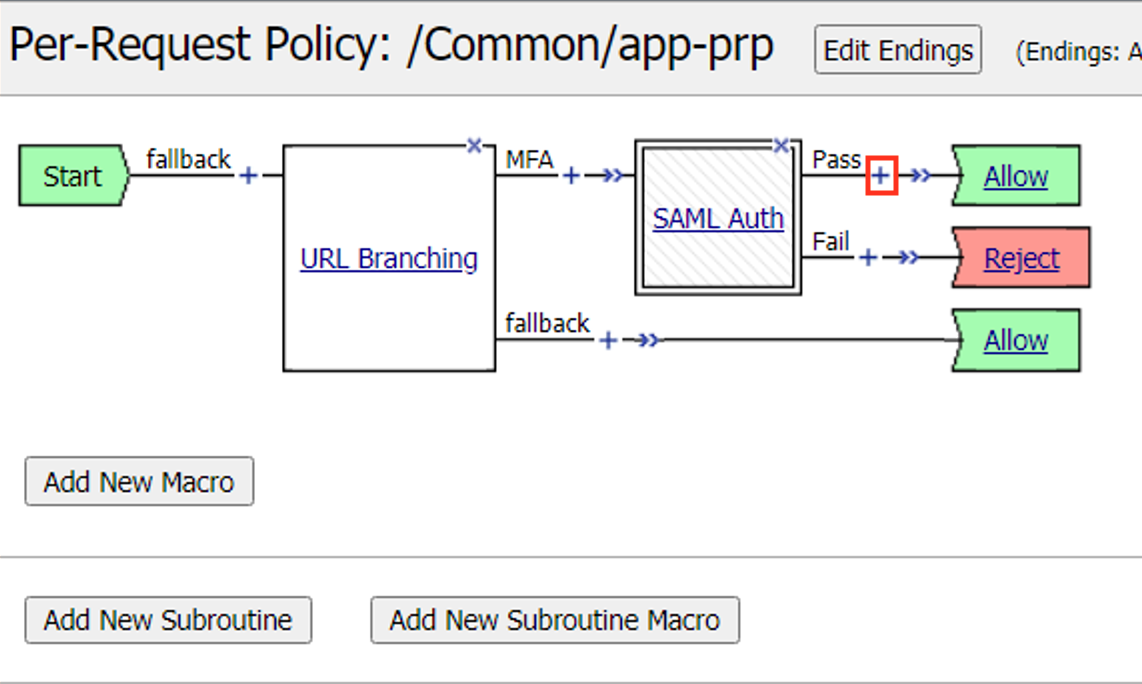
Click the Plus Symbol (+) on the Pass branch between SAML Auth and Allow Terminal
Click the General Purpose tab.
Select HTTP Headers
Click Add Item
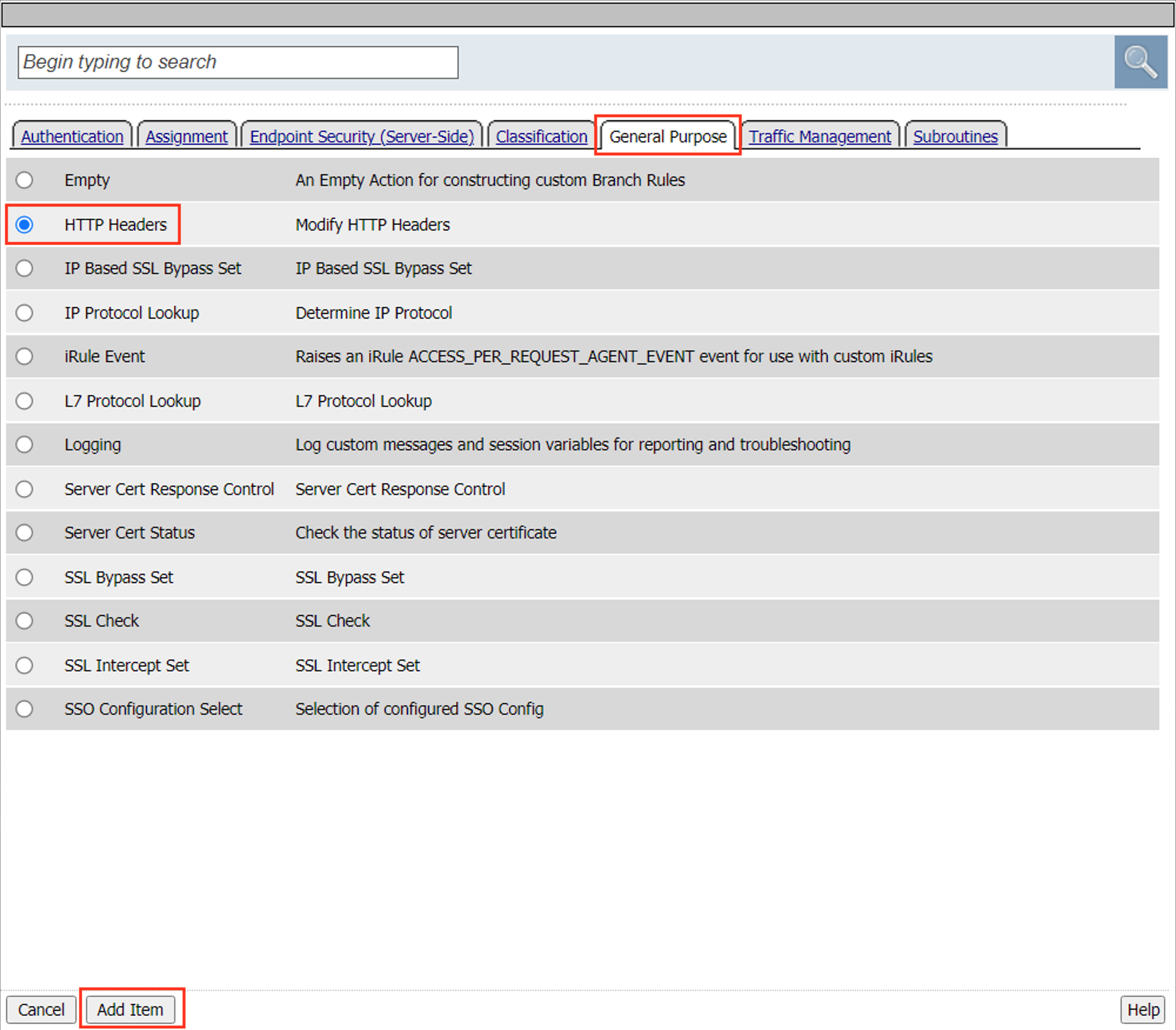
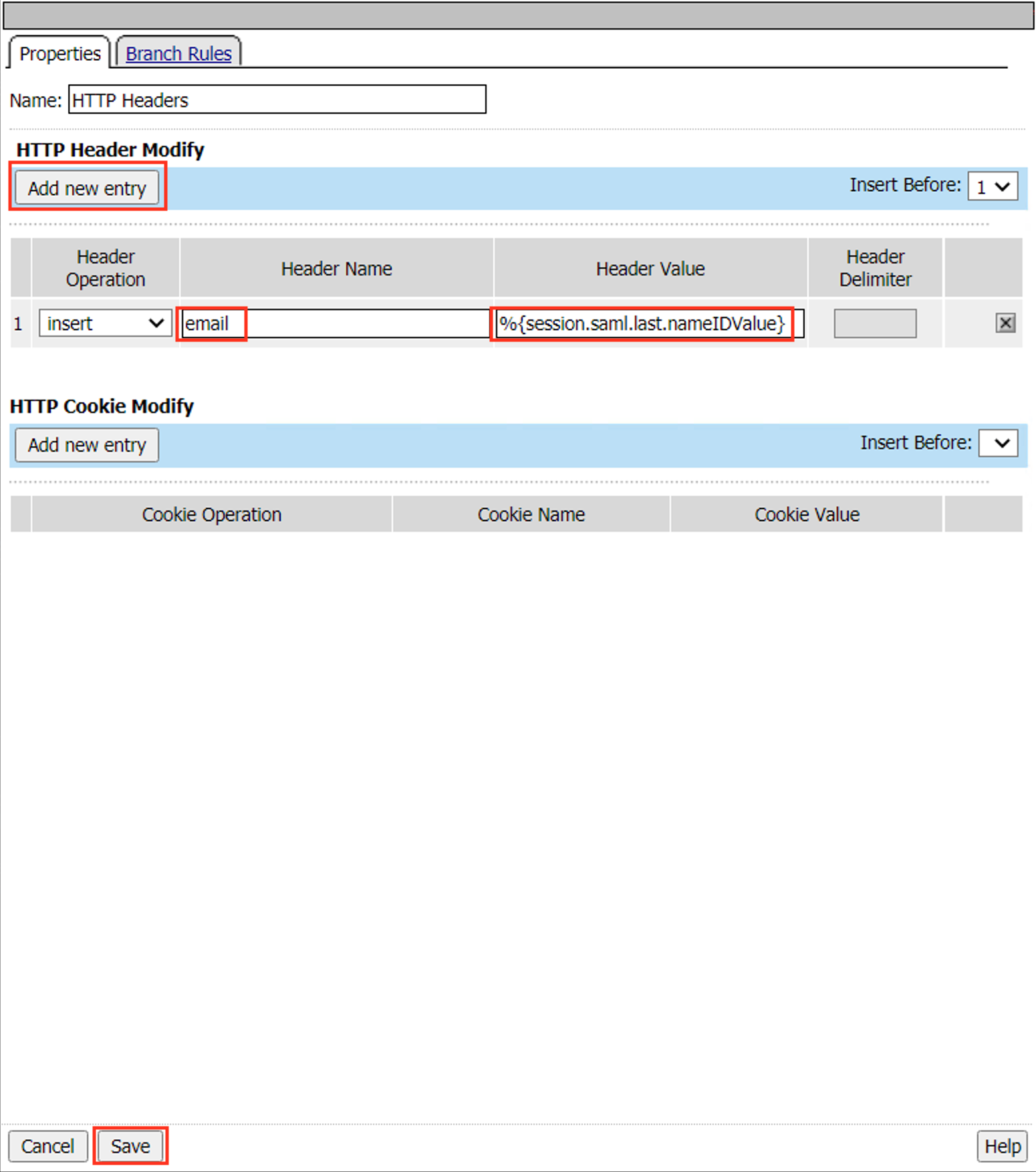
Click Add new entry
Enter the Header Name email
Enter the Header Value %{session.saml.last.nameIDValue}
Click Save
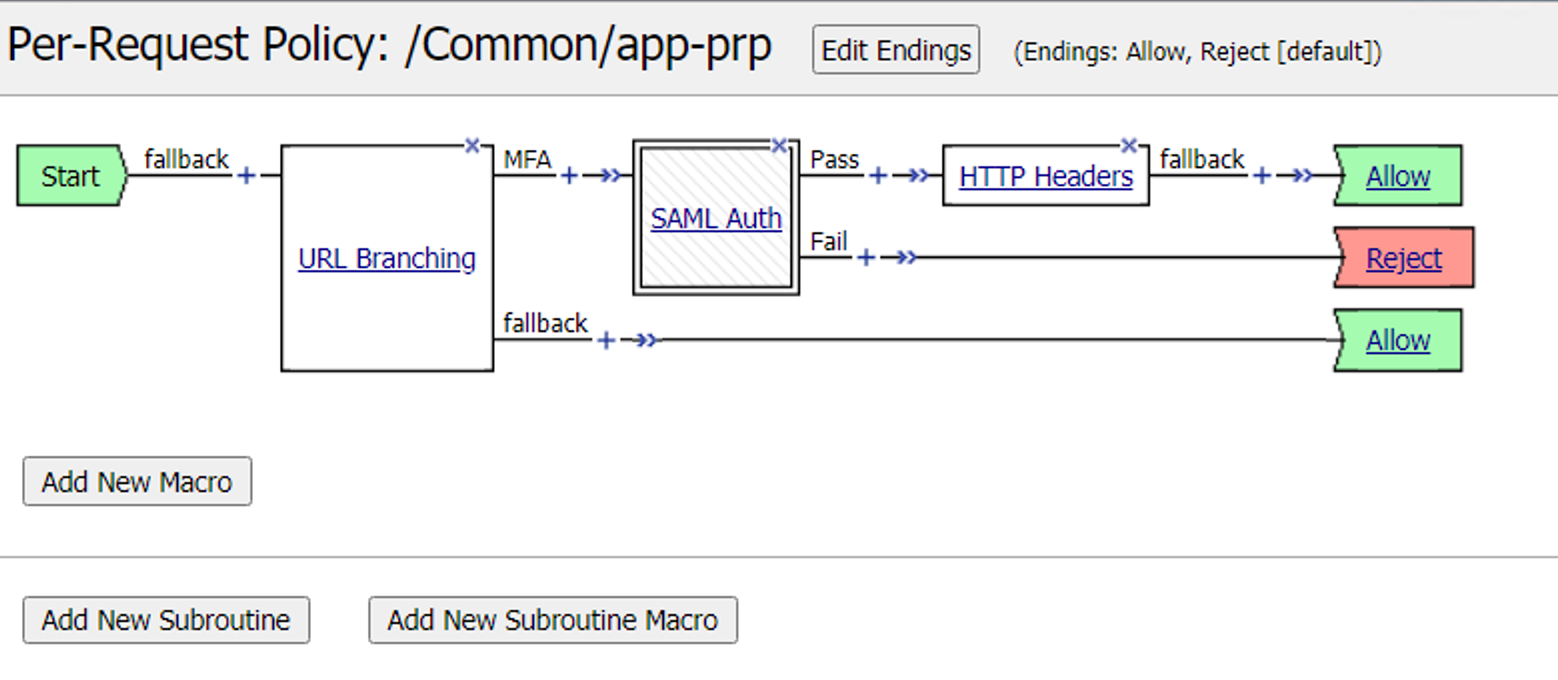
The Per-Request Policy should now look like below
Task 2 - Test Header Injection¶
From the jumpbox, navigate to https://app.acme.com. You will be redirected to the SAML IdP and be presented a logon page.
Logon with the credentials username: coyote@acme.com password: user1

After a successful logon at the IdP you are redirected to back to https://app.acme.com and presented a portal page.
Click the Admin View button.

Selet the user1 certifcate

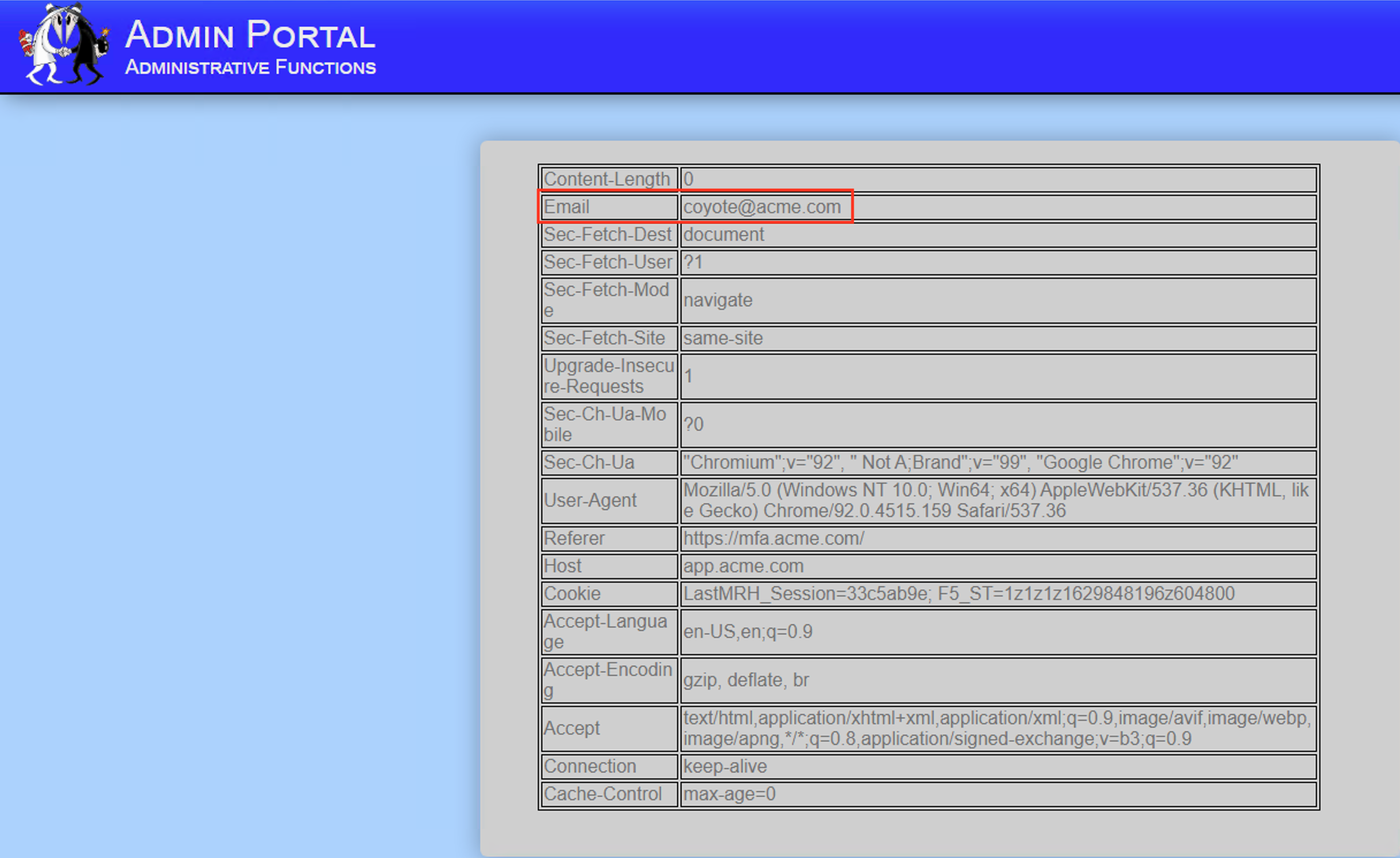
The admin page succesfully parsed the new email header and displays it on the screen
Section 4 - Lab Cleanup¶
From a browser on the jumphost navigate to https://portal.f5lab.local
Click the Classes tab at the top of the page.

Scroll down the page until you see 101 Intro to Access Foundational Concepts on the left

Hover over tile Visual Policy Editor (VPE) Overview. A start and stop icon should appear within the tile. Click the Stop Button to trigger the automation to remove any prebuilt objects from the environment

The screen should refresh displaying the progress of the automation within 30 seconds. Scroll to the bottom of the automation workflow to ensure all requests succeeded. If you experience errors try running the automation a second time or open an issue on the Access Labs Repo.
This concludes the lab.
