F5 Identity and Access Management Solutions > Archived Identity & Access Management Labs > 100 Series: Access Foundational Concepts Source | Edit on
Lab 4: Access Logs Overview¶
Access Policy Manager (APM) provides a default-log-setting. When you create an access profile, the default-log-setting is automatically assigned to it. The default-log-setting can be retained, removed, or replaced for the access profile. The default-log-setting is applied to user sessions only when it is assigned to an access profile.
Regardless of whether it is assigned to an access profile, the default-log-setting applies to APM processes that run outside of a user session. Specifically, on a BIG-IP system with an SWG subscription, the default-log-setting applies to URL database updates
Task 1 - Setup Lab Environment¶
To access your dedicated student lab environment, you will need a web browser and Remote Desktop Protocol (RDP) client software. The web browser will be used to access the Unified Demo Framework (UDF) Training Portal. The RDP client will be used to connect to the jumphost, where you will be able to access the BIG-IP management interfaces (HTTPS, SSH).
Click DEPLOYMENT located on the top left corner to display the environment
Click ACCESS next to jumphost.f5lab.local

Select your RDP resolution.
The RDP client on your local host establishes a RDP connection to the Jump Host.
Login with the following credentials:
- User: f5lab\user1
- Password: user1
After successful logon the Chrome browser will auto launch opening the site https://portal.f5lab.local. This process usually takes 30 seconds after logon.
Click the Classes tab at the top of the page.
Scroll down the page until you see 101 Intro to Access Foundational Concepts on the left

Hover over tile Access Logs Overview. A start and stop icon should appear within the tile. Click the Play Button to start the automation to build the environment
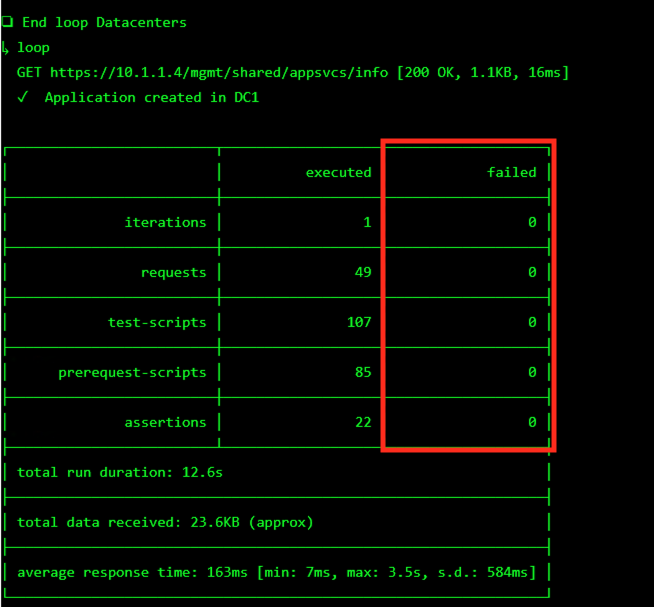
The screen should refresh displaying the progress of the automation within 30 seconds. Scroll to the bottom of the automation workflow to ensure all requests succeeded. If you you experience errors try running the automation a second time or open an issue on the Access Labs Repo.
Task 2 - Active Sessions¶
Open a new tab in browser and then navigate to https://server1.acme.com. You will be redirected to /my.policy and be presented a logon page.
At the logon page enter the Username:user1 and Password:user1
Click Logon
You will be be presented the following website if the logon was successful.
Now that you have fully authenticated session open another tab and navigate to https://bigip1.f5lab.local
Login with username admin and password admin
Navigate to Access >> Overview >> Active Sessions.

This Active Sessions page provides instance feedback on which users have successfully authenticated to APM along with their associated session information.
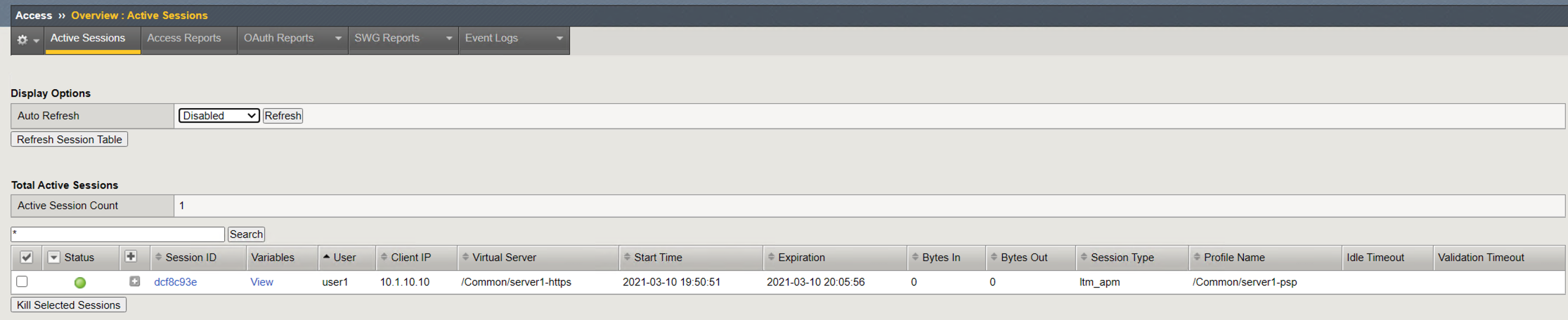
The Auto Refresh timer is disabled by default. Various timers settings can be applied to auto update the Active session page. Select 10 seconds is selected it will immediately begin counting down. Alternatively, the Refresh button and be clicked to immediately update the table.
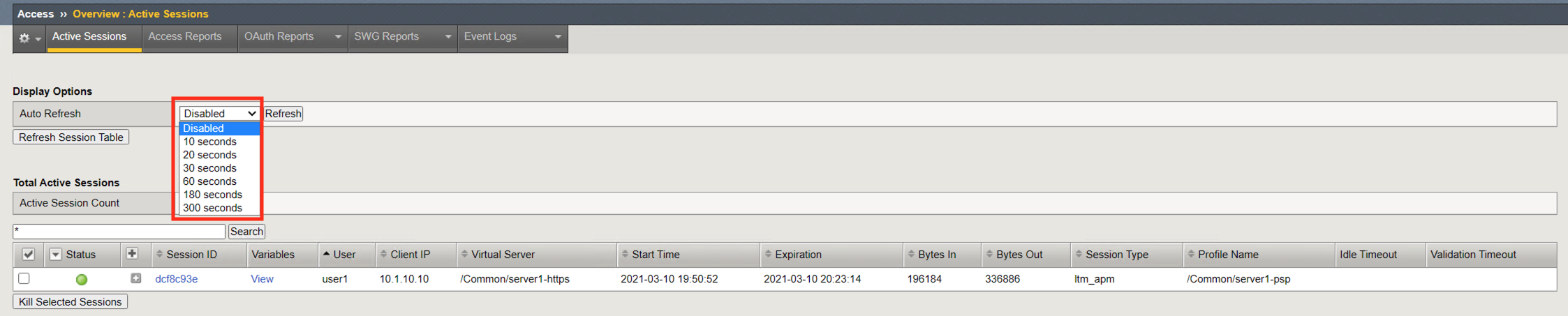
Active Session Count displays the number of completed and inactive sessions. Notice the session count is currently 1.
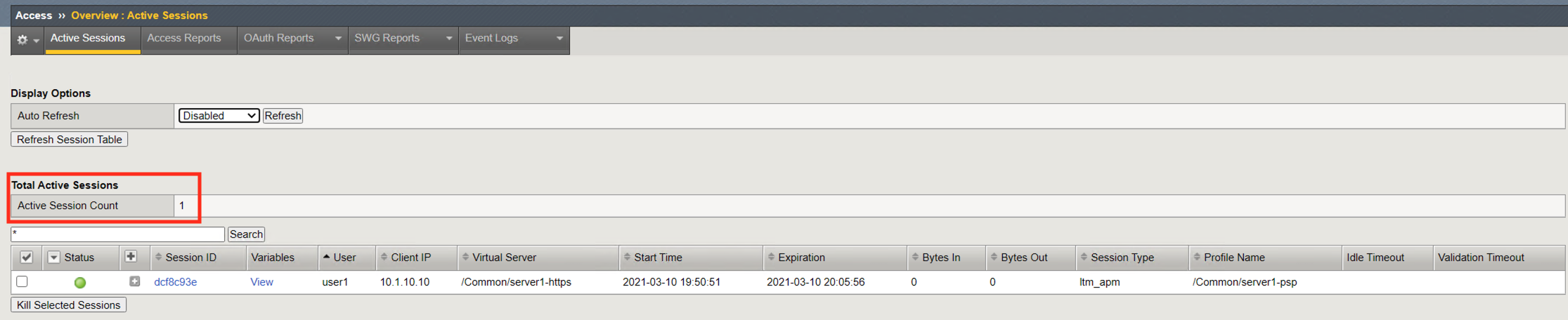
Open a new incognito browser tab and navigate to https://server1.acme.com. Do this will create a new session. Once presented a logon page, DO NOT logon and simply close the incognito browser window.

Return to the BIG-IP active session screen. If auto refresh is still enabled the next time it refreshes a new session will appear. Stop the auto refresh.
Notice the Active Session Count is now 2
Notice the Status of the new session is a blue square rather than a green circle. A green circle means the entire access policy has been completed from beginning to end. A blue circle means the session is not complete and is still in process.
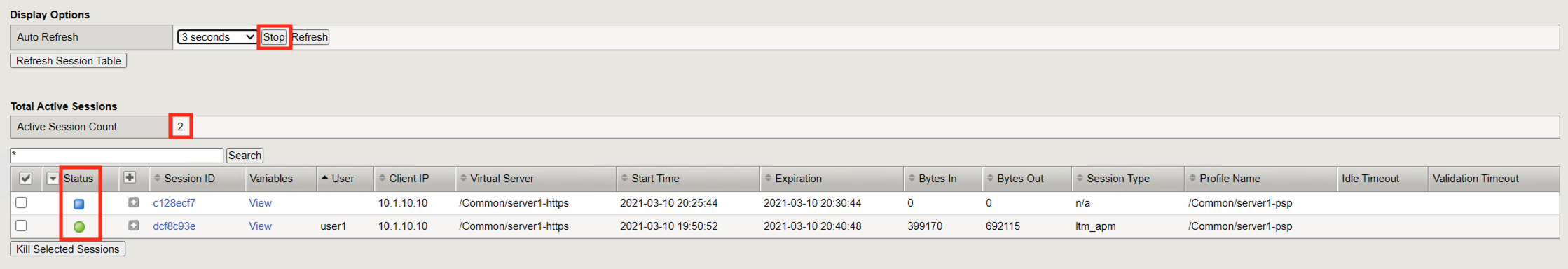
Check the empty square next to the new session with a blue square.
Click Kill Selected Session
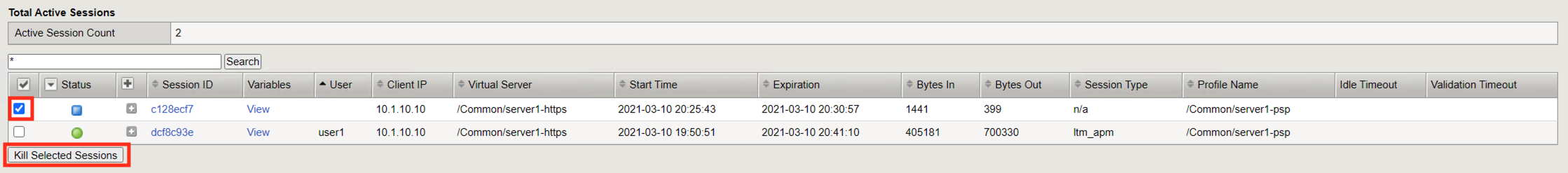
A second screen will appear asking you to confirm you want to delete the session. Click Delete
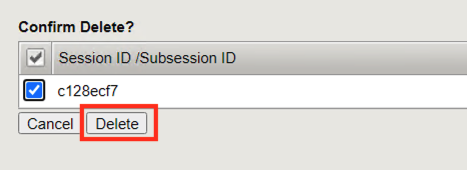
Only 1 Active Session should appear on the screen.
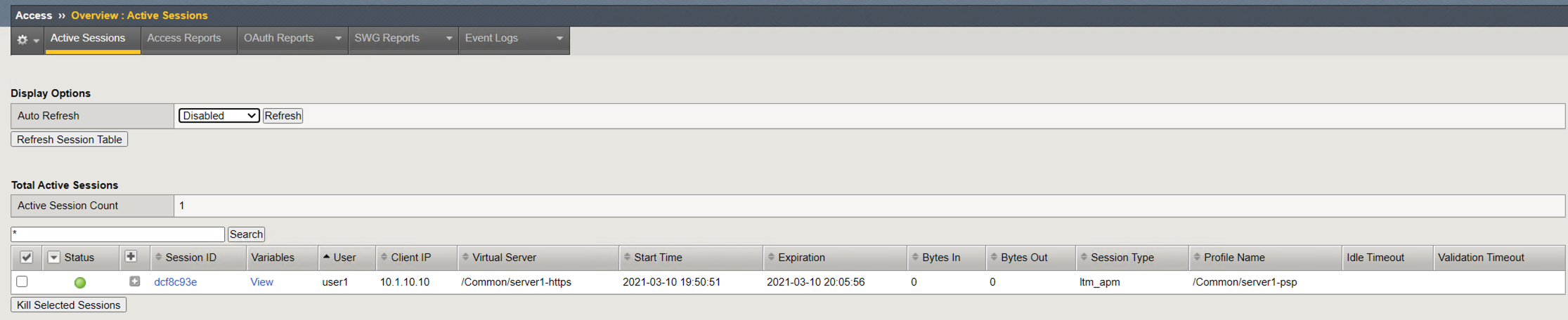
Clicking the + (plus symbol) next to the session ID expands the session to display an subsessions associated with the primary session. Subsessions are created when using a Per-Request Policy that contains a subroutine. Subesssions have their own variables, settings, and timers separate from the primary session.
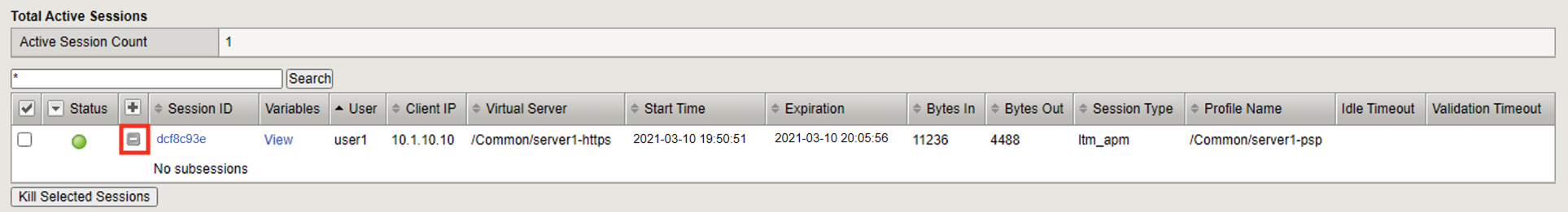
The Session ID is a unique hex value for tracking a user throughout the life of their connection. The sessionID is derived from the last 8 digits of the MRHSession cookie passed to the client. If you click the session ID it will open a session report. Session reports will be covered in Task 3
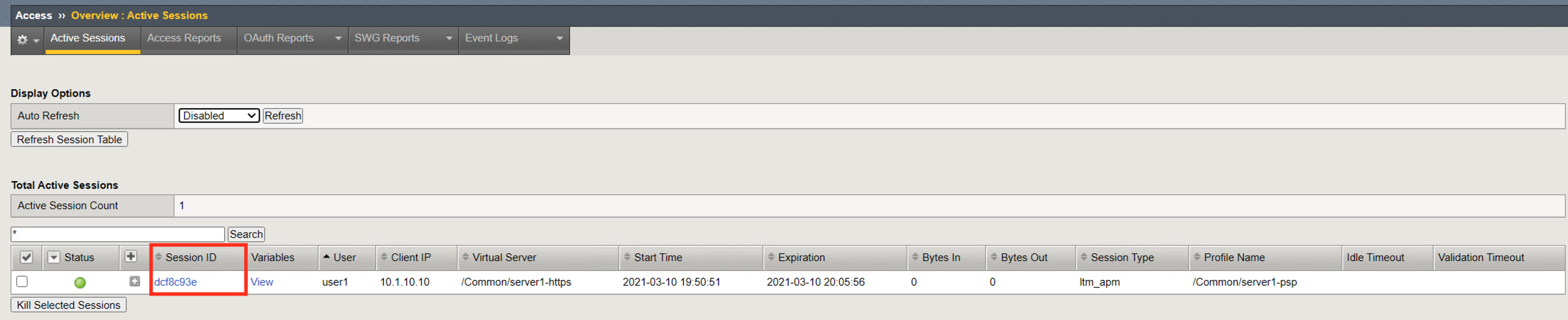
Click Variables to open a new window that displays all the session variables currently associated with the session. A session variable contains a number or string that represents a specific piece of information. This information is organized in a hierarchical arrangement and is stored as the user’s session data.
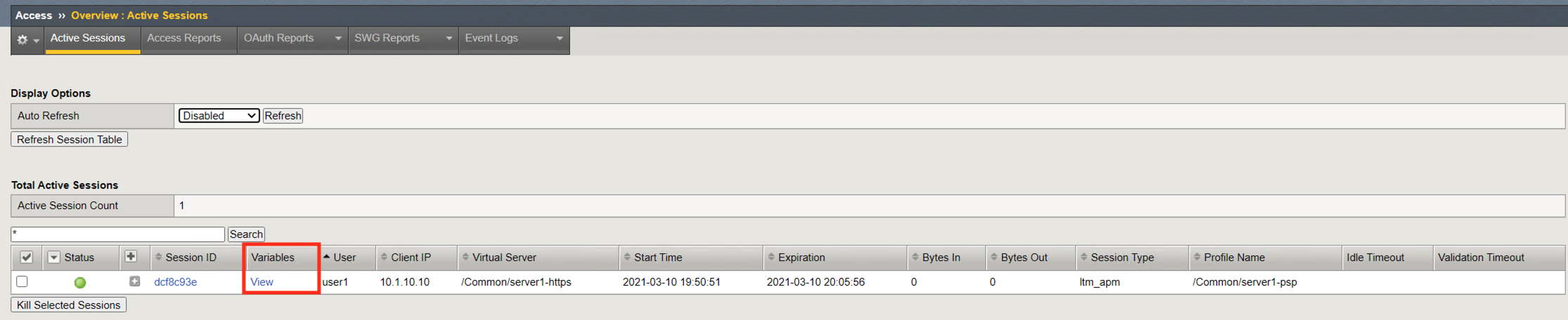
Each variable contains a piece of information that APM gathered during the life of the session. This information can come from various sources such as traffic flow, device Information or user Information. Variables can be created, modified, or deleted throughout the life of a session. Once a variable is defined it can used as condition for access control decisions. Click Cancel to return to the Active Session Screen.
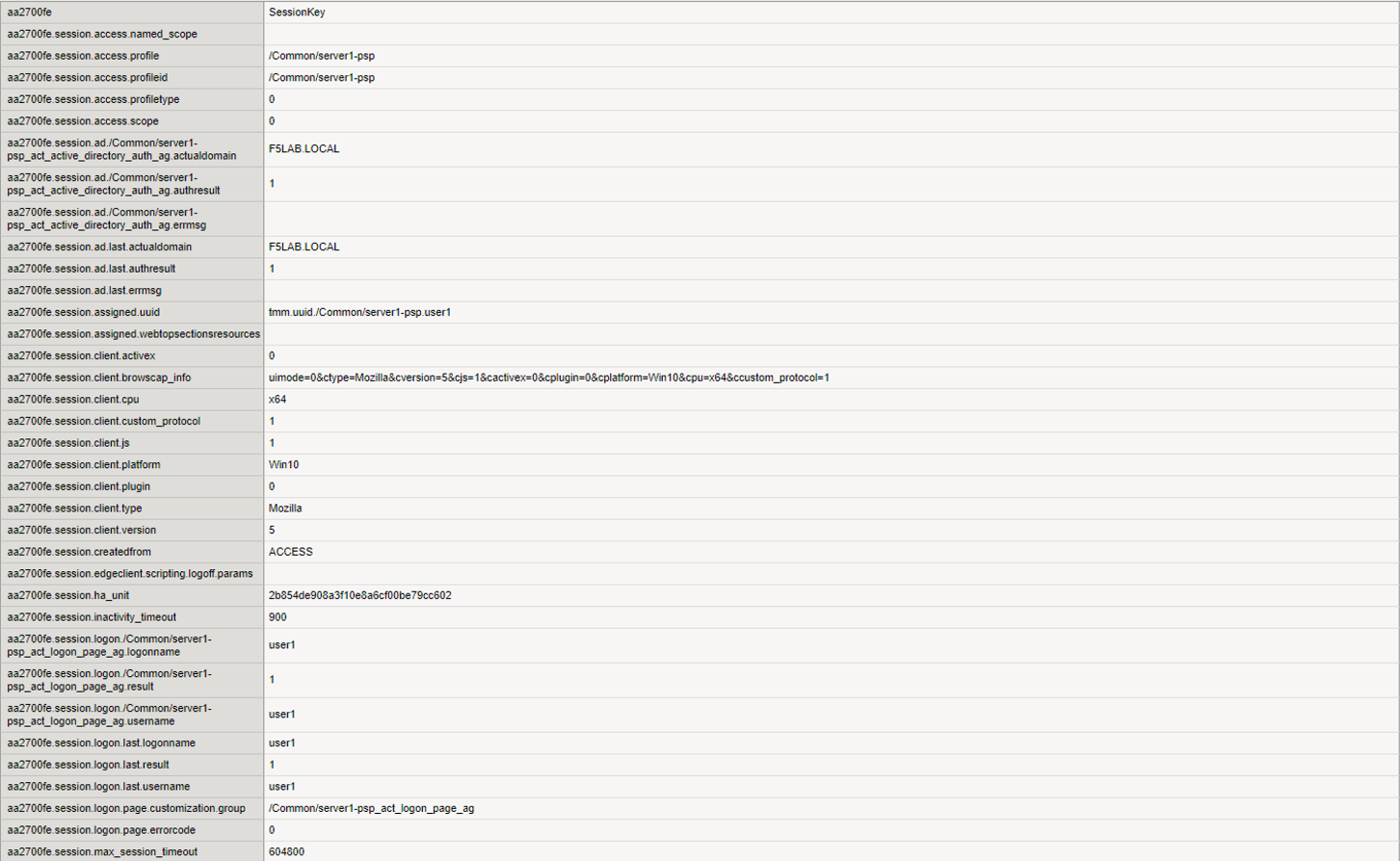
The Username displayed references the username stored in the session variable session.logon.last.username.
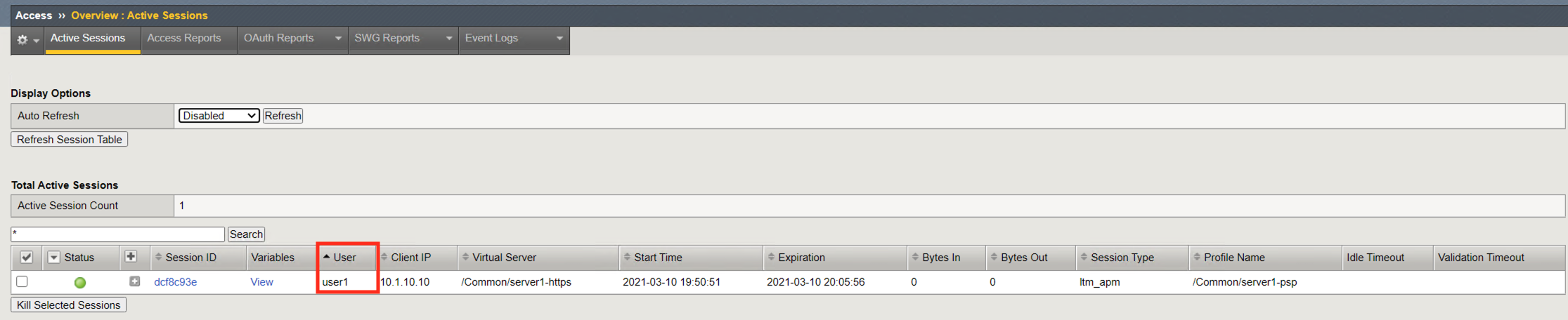
The client IP displayed references the IP Address stored in the session variable session.user.clientip
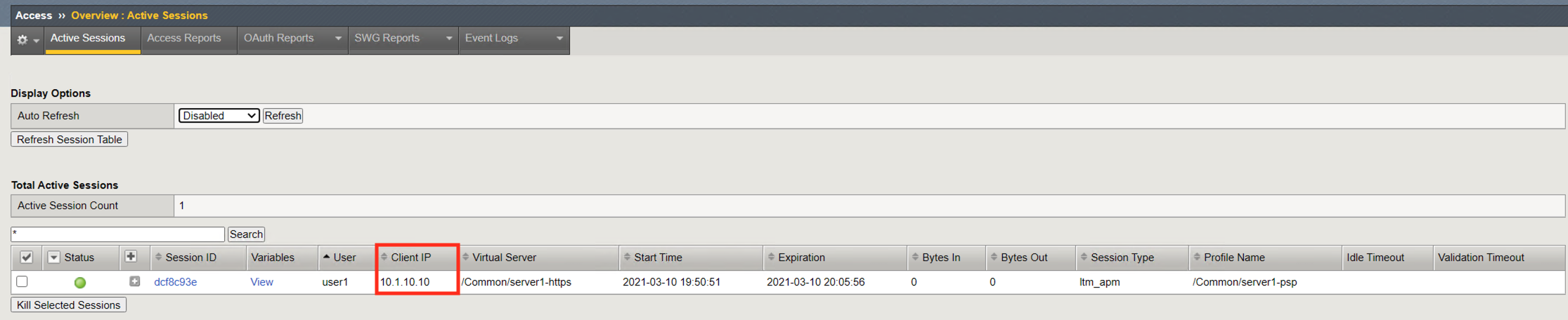
The Virtual Server displayed references the initial virtual server the policy was evaluated on for that session.
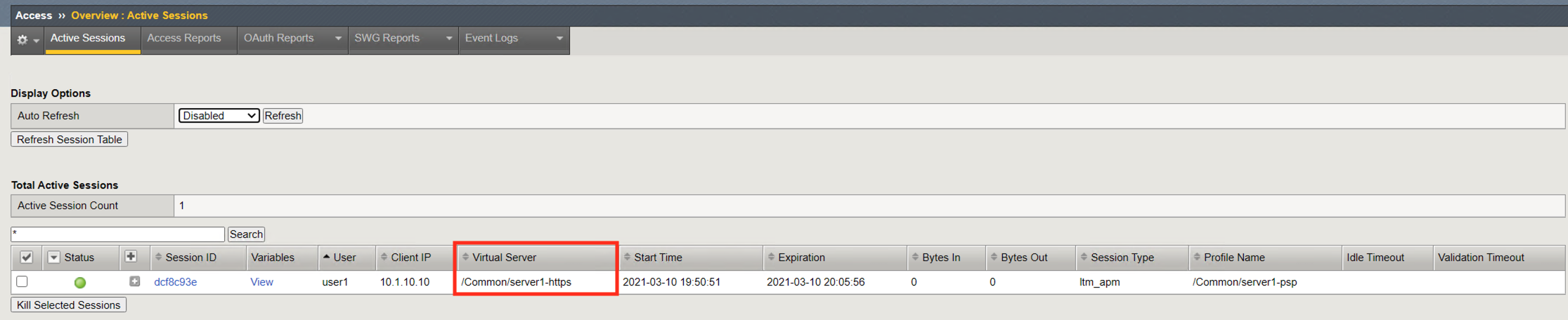
The Start Time for a session is when the initial request was made and the session ID assigned.
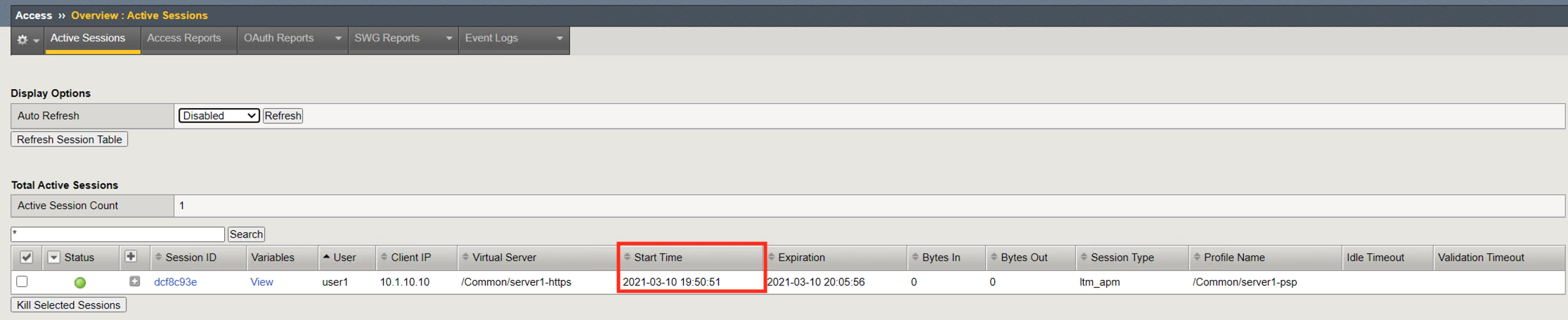
The expiration time’s initial value is be based on the Inactivity Timeout defined on the Access Profile. The default is 15 minutes and can be modified. The Inactivity Timeout setting controls how long (in seconds) a client can keep a live session without sending traffic.
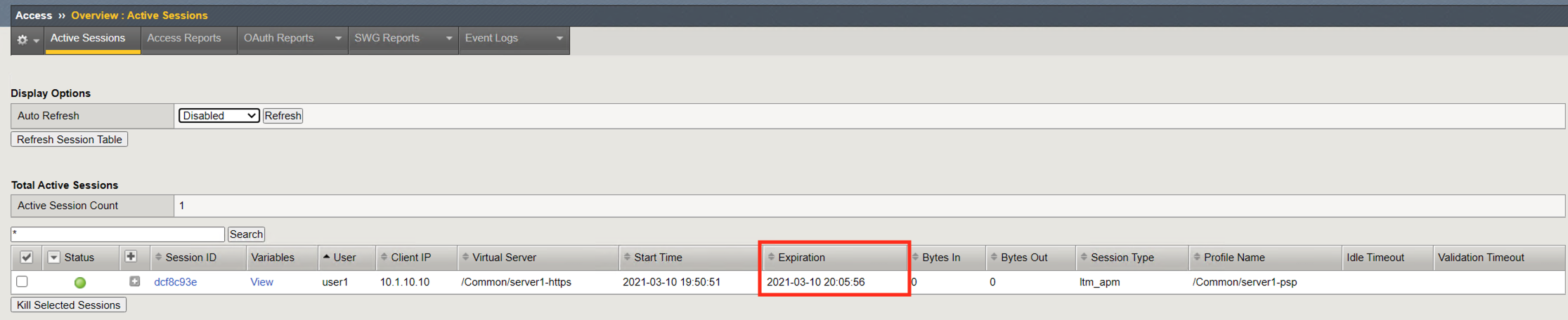
Session Type the type of resources assigned in the session
- n/a: Session completion still pending
- network_access: A webtop with a network access resource (VPN)
- web_application: A virtual server with APM profile and a rewrite profile (APM doing L7 reverse proxy)
- full: A webtop, that can have multiple type of resources: Web Resources, Reverse Proxy, VDI Resources, SSH Resources, and network access resource (VPN)
- ltm_apm: A virtual server with an APM profile. No rewrite profile or webtop attached.
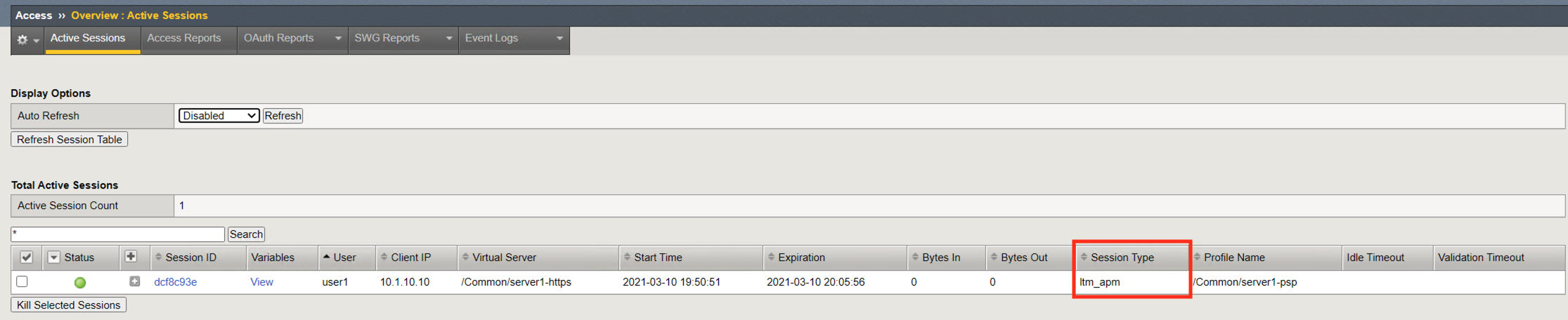
Profile Name shows the Access profile used in the evaluation of the session.
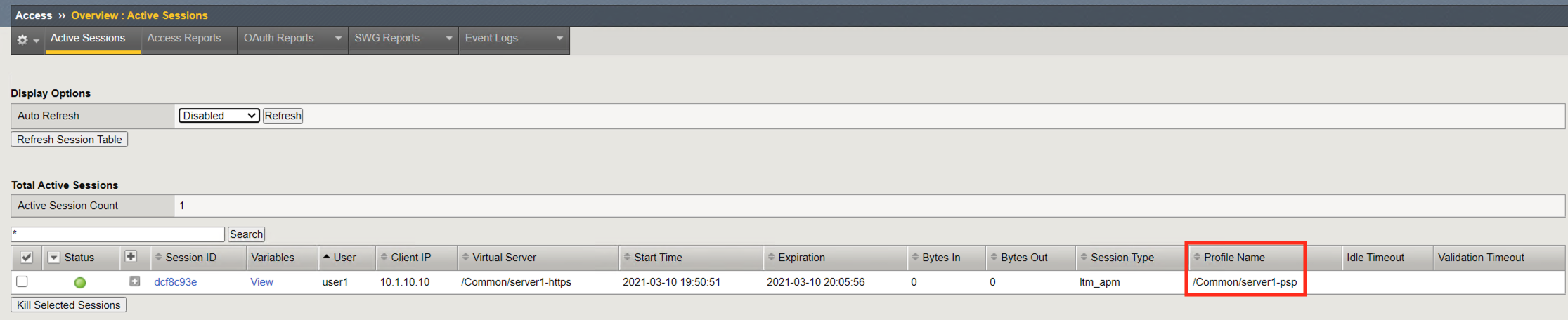
Task 3 - Access Reports¶
Access Reports allow an administrator to quickly locate current and historical session information.
Navigate to Access >> Overview >> Access Reports.
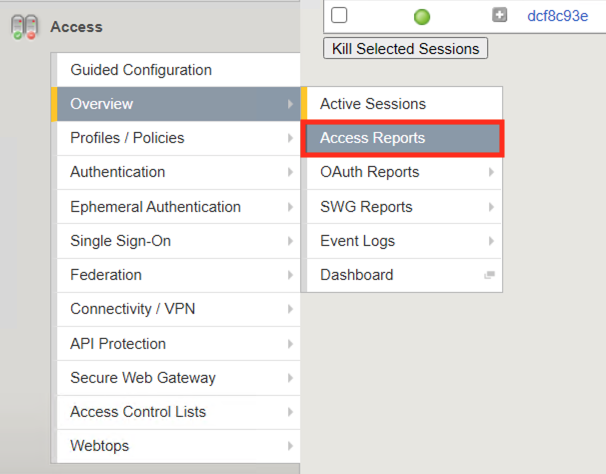
When running a report you can specify the timeframe and then click Run Report
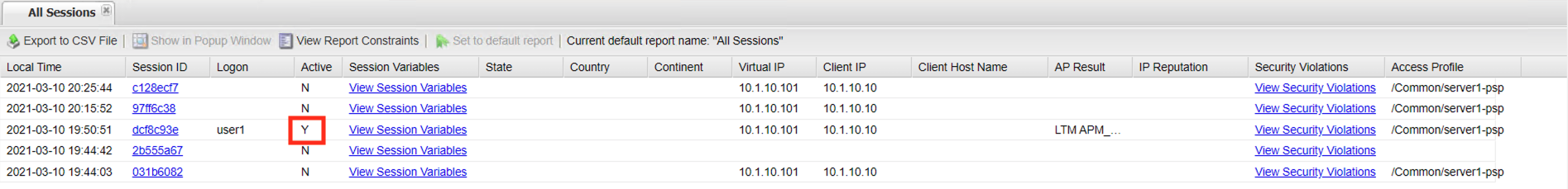
All current and historical sessions are displayed. You can see user1 currently has an Active Session.
Click on user1’s session ID to open a session details report.
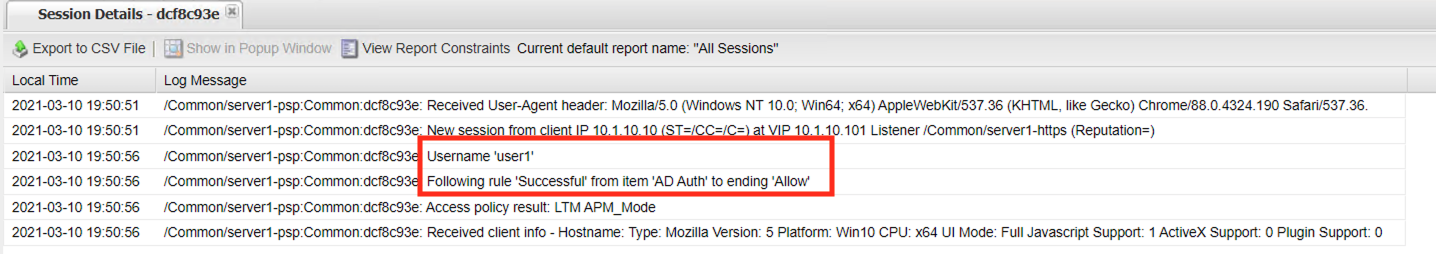
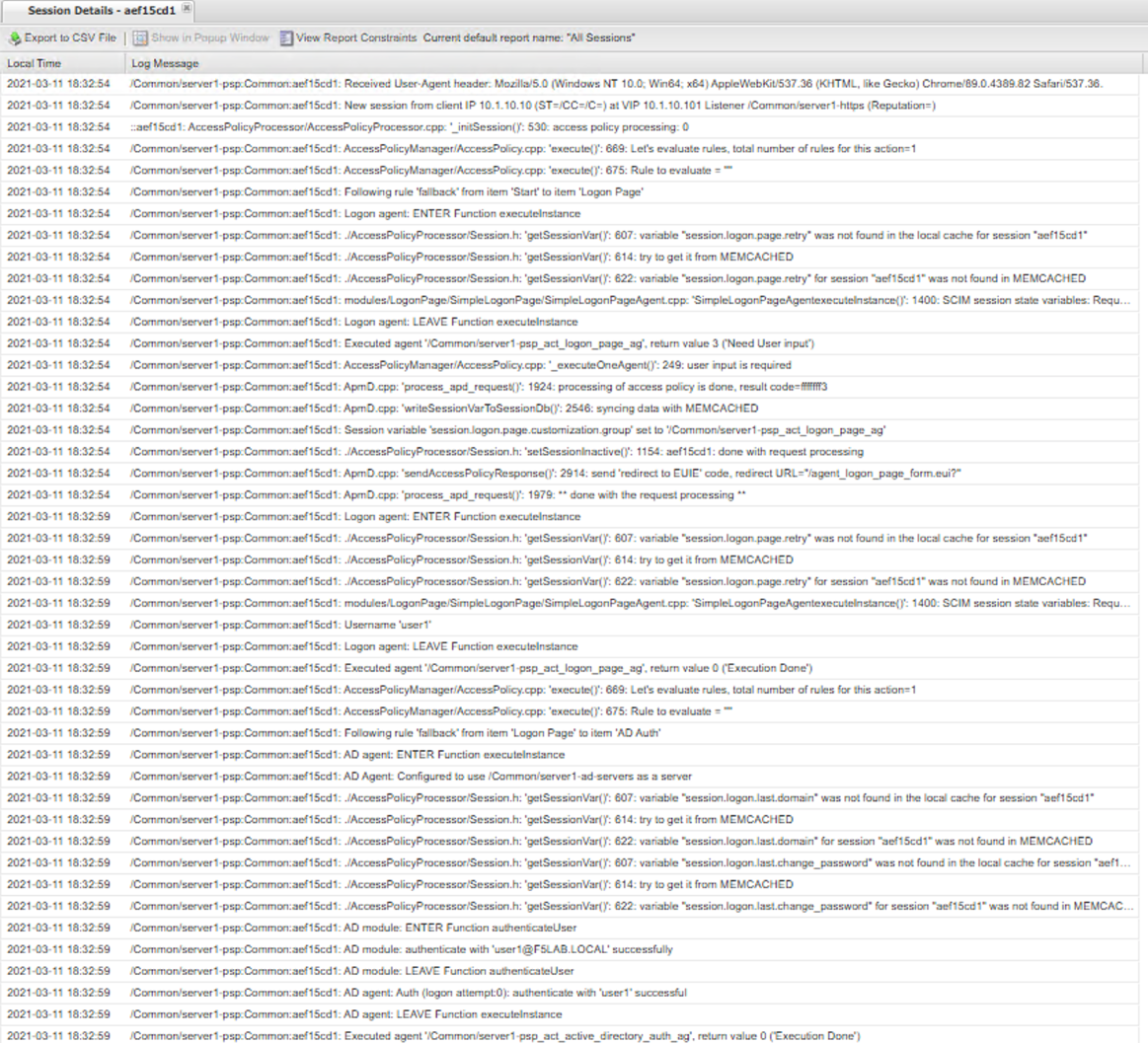
A session details report displays every step of policy evaluation from the start item to the End Terminal. You can see in line 3 that username user1 was collected. Then in line 4 the username and password were authenticated against Active Directory and down the Allow End branch. This makes troubleshooting access control decisions easy because every step is logged and it can be easily seen where the failure is and potential reasons why it happened.
Task 4 - Log Settings¶
In Task 2, you learned how to view access reports. In this Task you will learn how to modify the existing logging profile. This is sometimes necessary when more detailed logging information is needed due to Organizational requirements or when troubleshooting an issue.
Navigate to Access >> Overview >> Event Logs >> Settings.
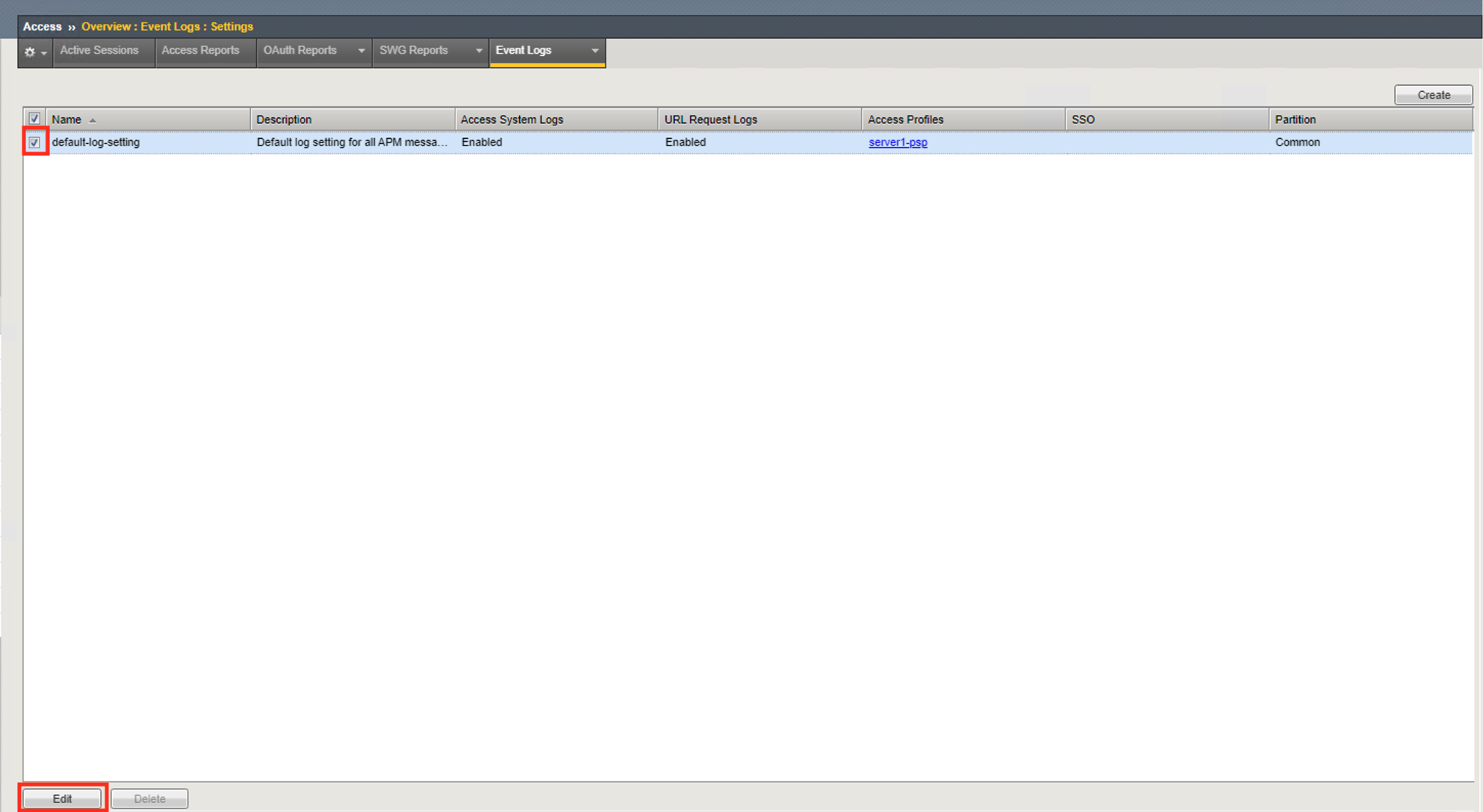
On the screen you see single logging profile names default-log-setting. All Access Policies created will always be associated with this Logging profile. It’s important to understand that if you have multiple policies all sharing the same logging profile that when changes are made it impacts all the profiles associated with it. In many cases it is best practice to create a new logging profile when settings are going to be modified from the defaults and associated with the Access Profile that requires a different in logging capabilities.
Click the checkmark box next to default-log-settings
Click Edit
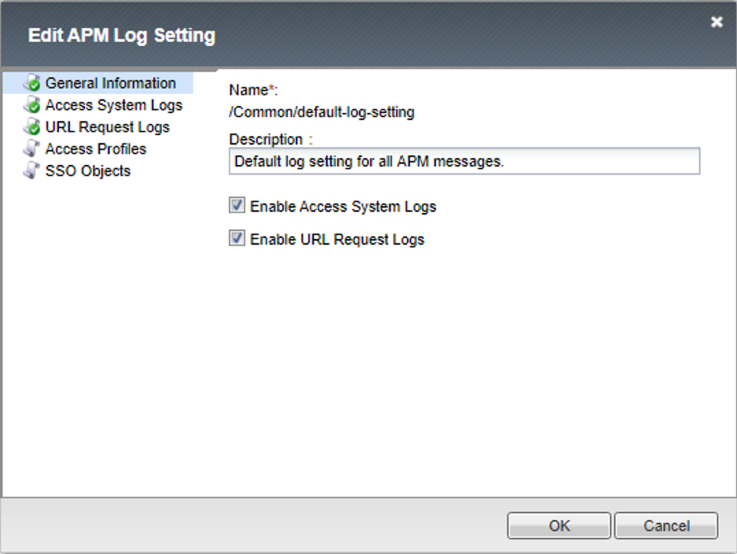
The General Information has two options for enabling or disabling Access System logging and URL Request Logs.
Click Access System Logs
Select Debug from the Access Policy Dropdown
Note
The Publisher defines where log messages are sent. By default they are logged local to /var/log/apm. To learn more about Log publishers and how to configure external logging read Tech Article on High-Speed Logging

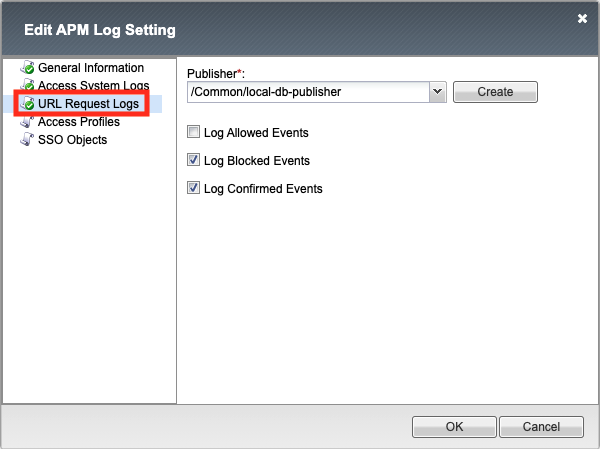
Click URL Request Logs. This section determines what type of events you want to log in SWG deployments
Click Access Profiles. This section allows you to select which Access Profiles will use this logging profile.
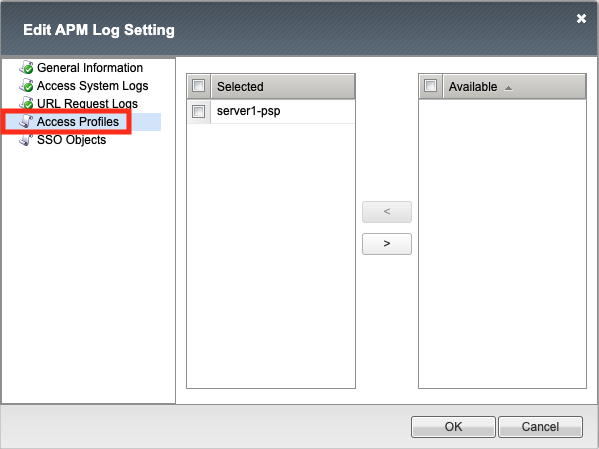
Click SSO Objects. This section allows you to select which SSLO Objects Profiles will use this logging profile.
Click OK
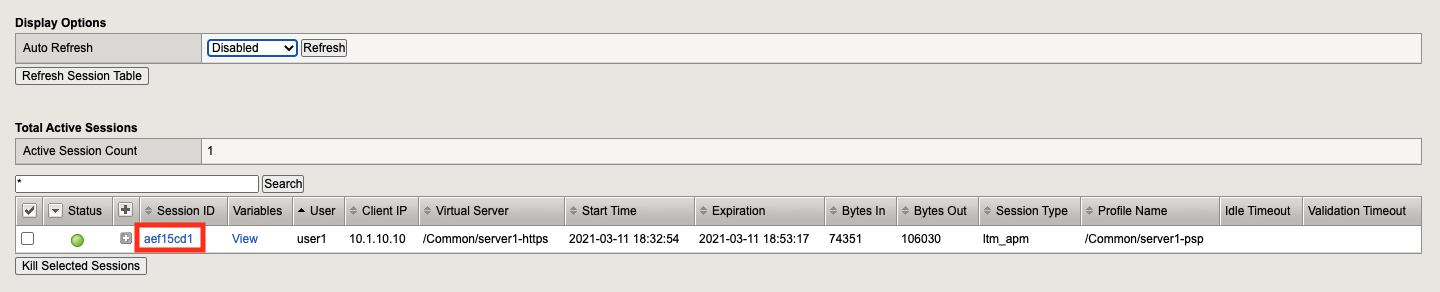
Navigate to Access >> Overview >> Active Sessions. Kill any existing sessions.

Open a new tab in browser and then navigate to https://server1.acme.com. You will be redirected to /my.policy and be presented a logon page.

At the logon page enter the following credentials:
- Username:user1
- Password:user1
Click Logon

You will be presented the following website if the logon was successful.

Return to the BIG-IP GUI and navigate to Access >> Overview >> Active Sessions.

Click the session ID to open its Session Report
Notice a more detailed session report is provided beyond the six lines displayed with only Notice logging enabled.
Note
to learn more about logging levels see https://support.f5.com/csp/article/K24826763
Task 5 - Lab Cleanup¶
From a browser on the jumphost navigate to https://portal.f5lab.local
Click the Classes tab at the top of the page.

Scroll down the page until you see 101 Intro to Access Foundational Concepts on the left

Hover over tile Access Logs Overview. A start and stop icon should appear within the tile. Click the Stop Button to trigger the automation to remove any prebuilt objects from the environment
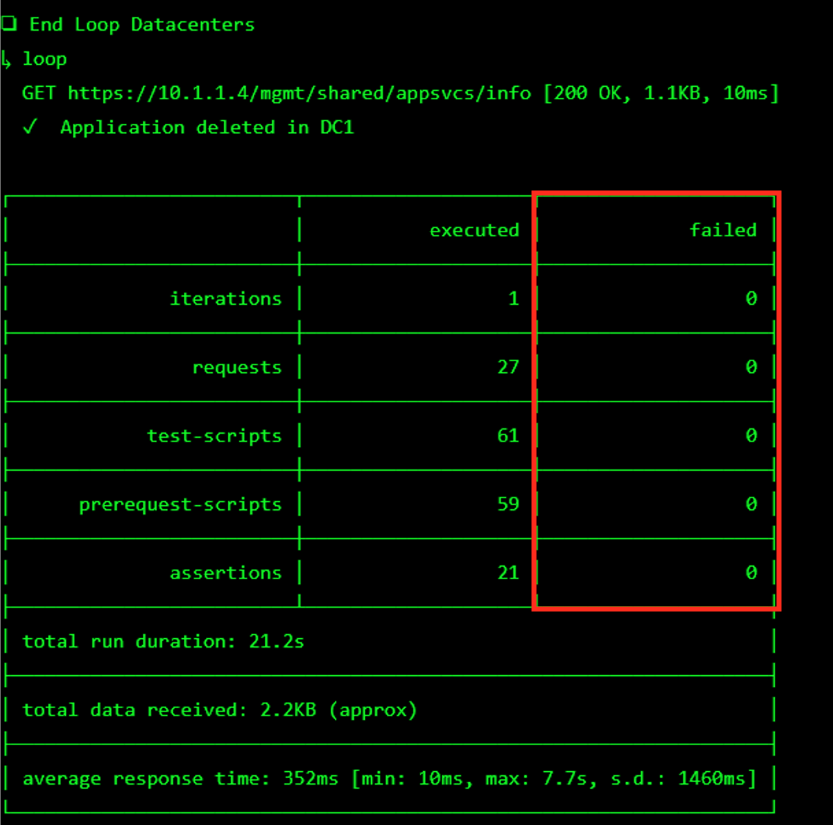
The screen should refresh displaying the progress of the automation within 30 seconds. Scroll to the bottom of the automation workflow to ensure all requests succeeded. If you experience errors try running the automation a second time or open an issue on the Access Labs Repo.
This concludes the lab.
