F5 Identity and Access Management Solutions > Archived Identity & Access Management Labs > 300 Series: Advanced Use Cases & Solutions Source | Edit on
Lab 3: Custom Per Request Policy - Extended¶
The purpose of this lab is to change the behavior of the custom Per Request Policies built during Lab 2. Lab attendees will expand policies by incorporating HTTP_Connector agents to query external API’s and incorporate Gating Criteria to enforce policy behavior while accessing the lab application. Students will configure the various aspects of this lab using the Visual Policy Editor, review the configuration and perform tests of the deployment.
Objective:¶
- Gain a deeper understanding of Per Request Policies and their applicability in various delivery and control scenarios.
- Gain a further understanding of Per Request Policy Subroutines and their expandaility with HTTP_Connector and gating criteria.
Lab Requirements:¶
- All Lab requirements will be noted in the tasks that follow
- Estimated completion time: 20 minutes.
Lab 3 Tasks:¶
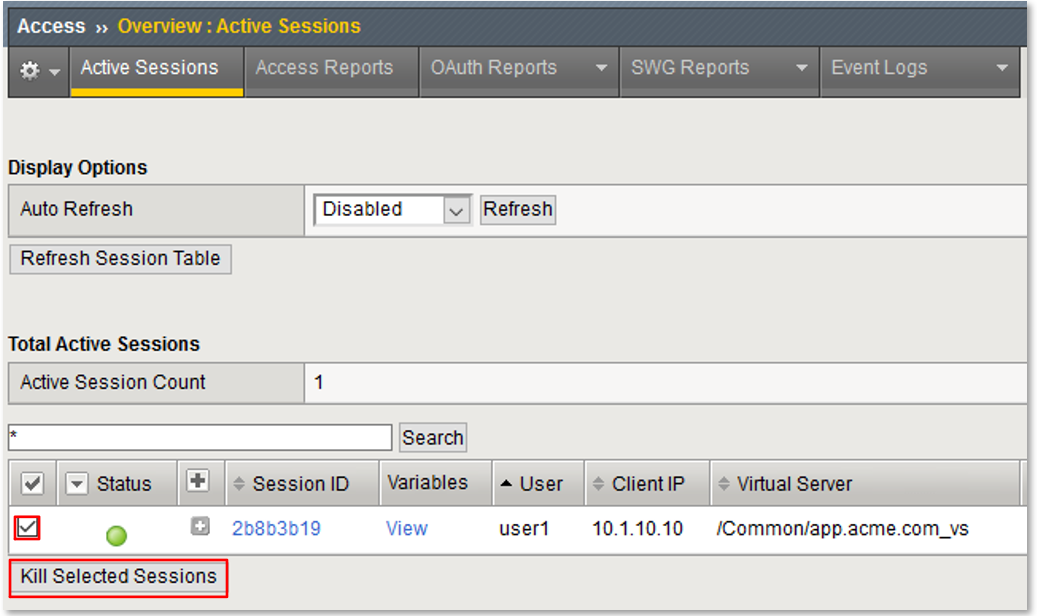
TASK 1: Prepare Lab Environment¶
|
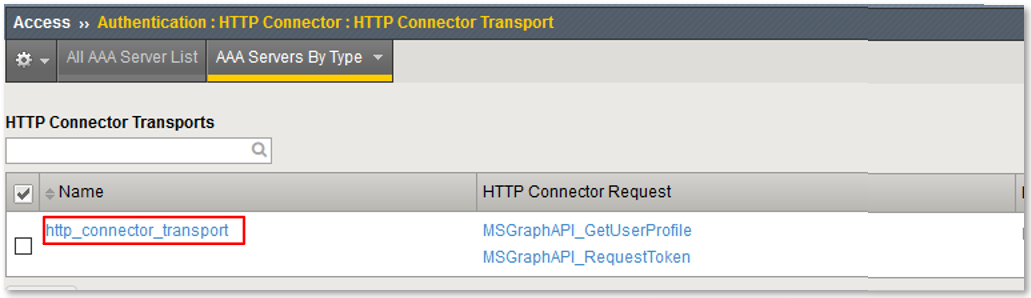
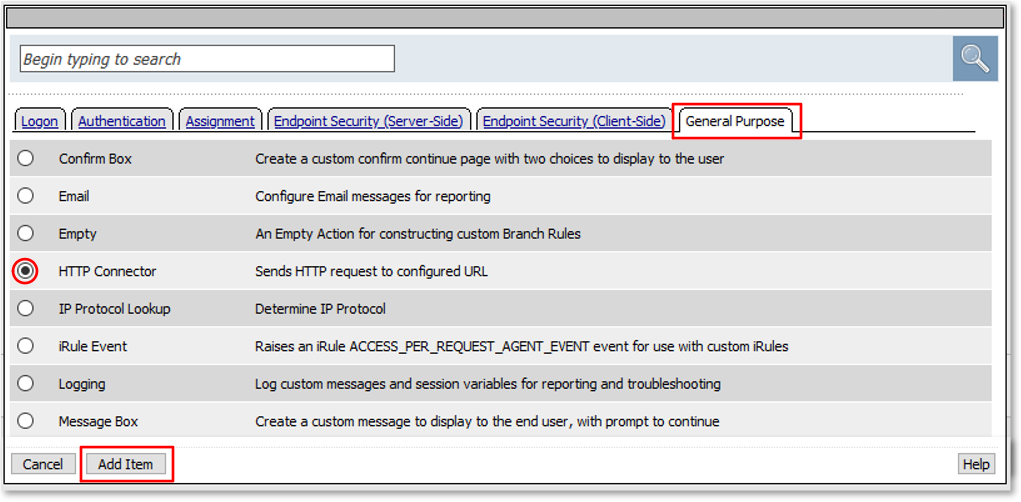
TASK 2: Review HTTP Connector Configuration¶
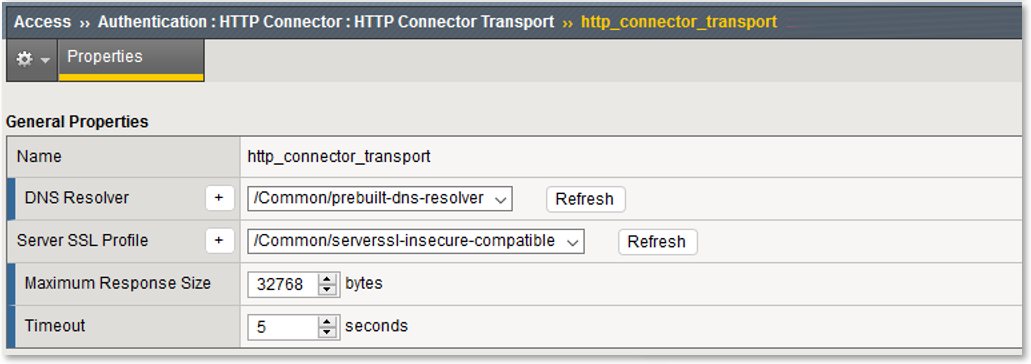
Note: This configured resource provides DNS resolution and HTTPS functionality enabling access to queried Web Service and API endpoints. |
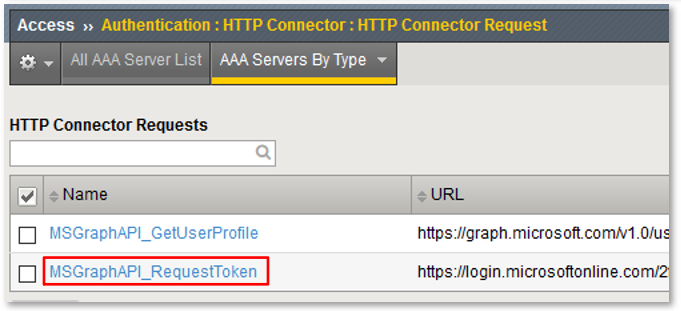
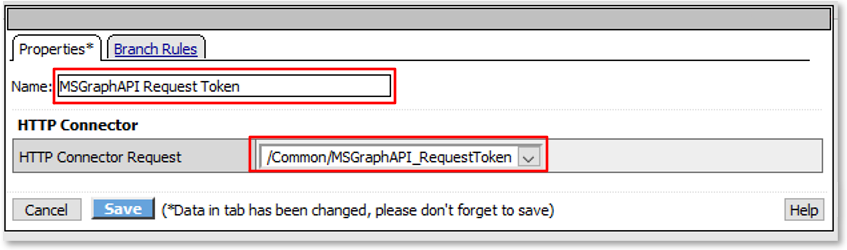
Note: This configured resource retrieves an oAuth Bearer Token to be used to query the Microsoft Graph API. Note: While values like tenant_id, client_id & client_secret have been statically entered for the purposes of this lab, these could have been referenced variables set in the Per Request Policy flow. Screenshot may show different values then your lab. |
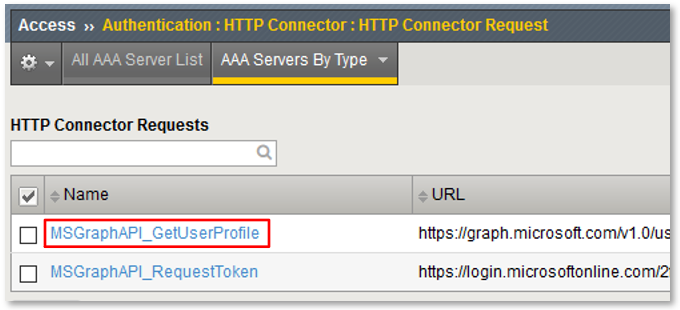
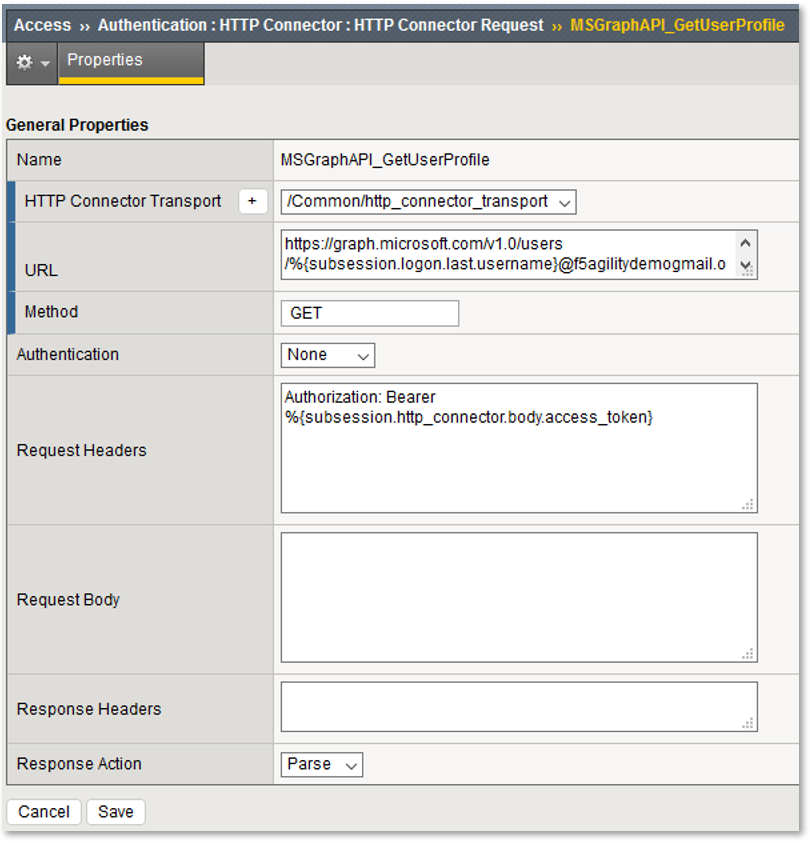
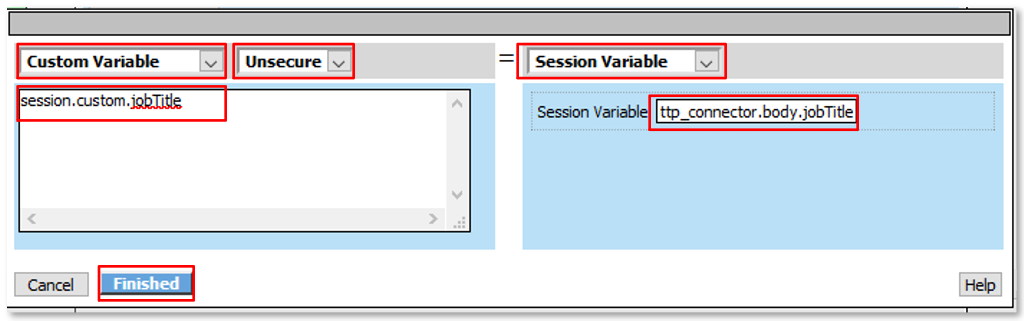
Note: This configured resource uses a previously obtained oAuth Bearer Token and queries the Microsoft Graph API for the queried user’s profile information. Note: The Application (client_id) has been granted API Permissions for User.Read.All |
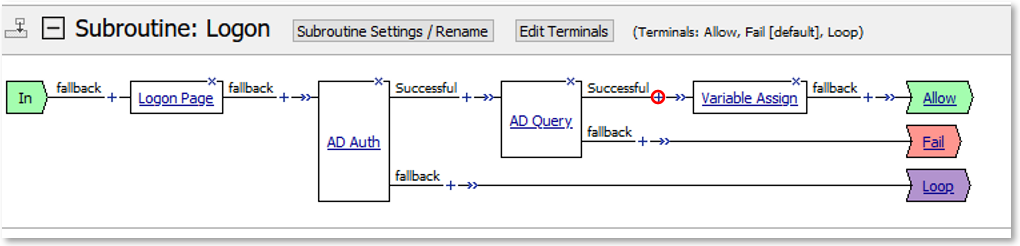
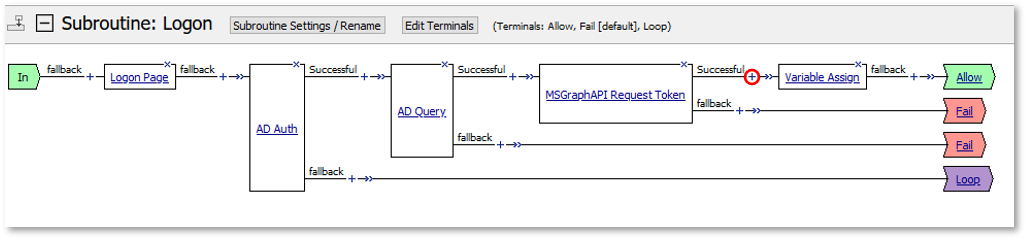
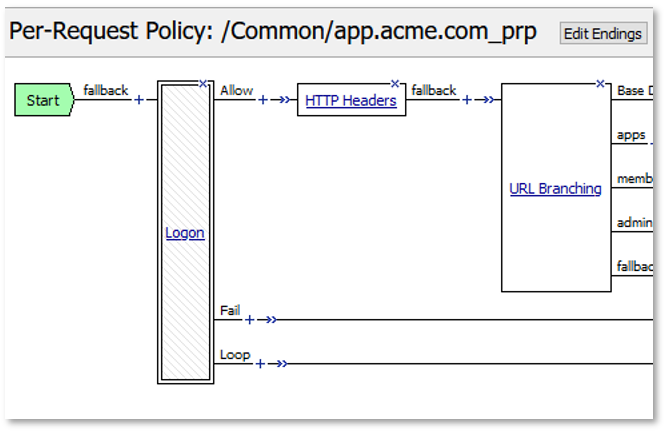
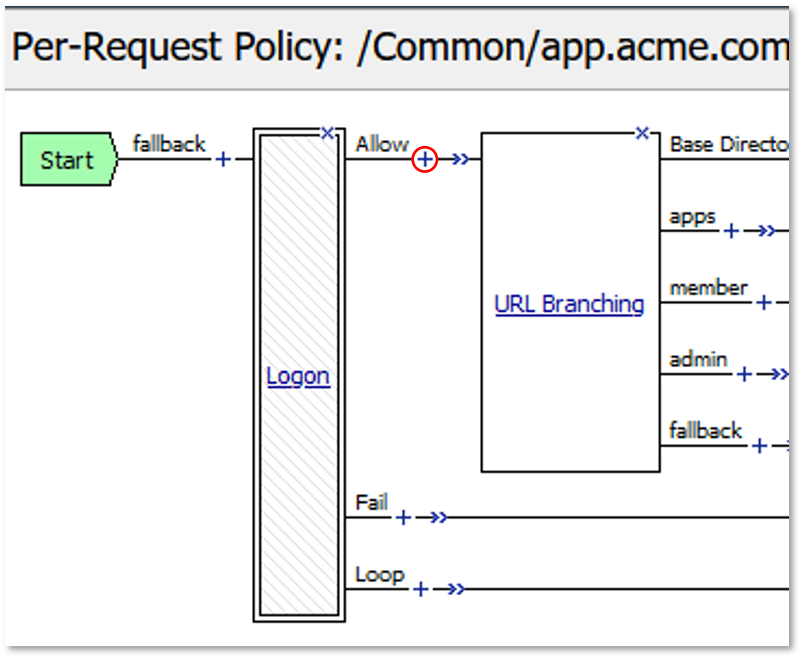
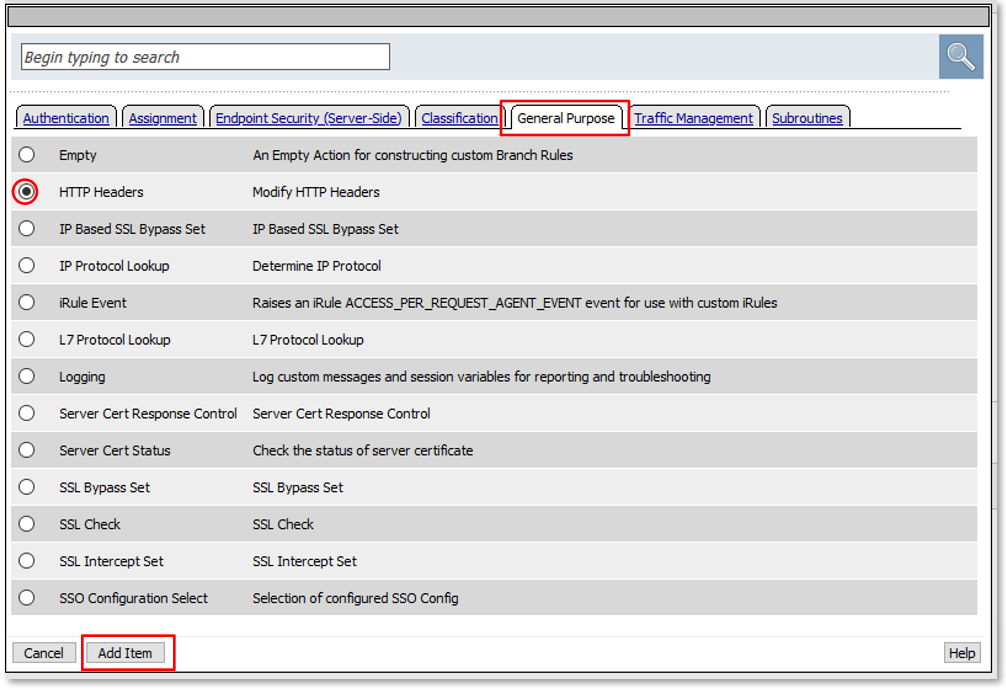
TASK 3: Extended Logon Subroutine¶
Note: This may already be open. |
 |
|
|
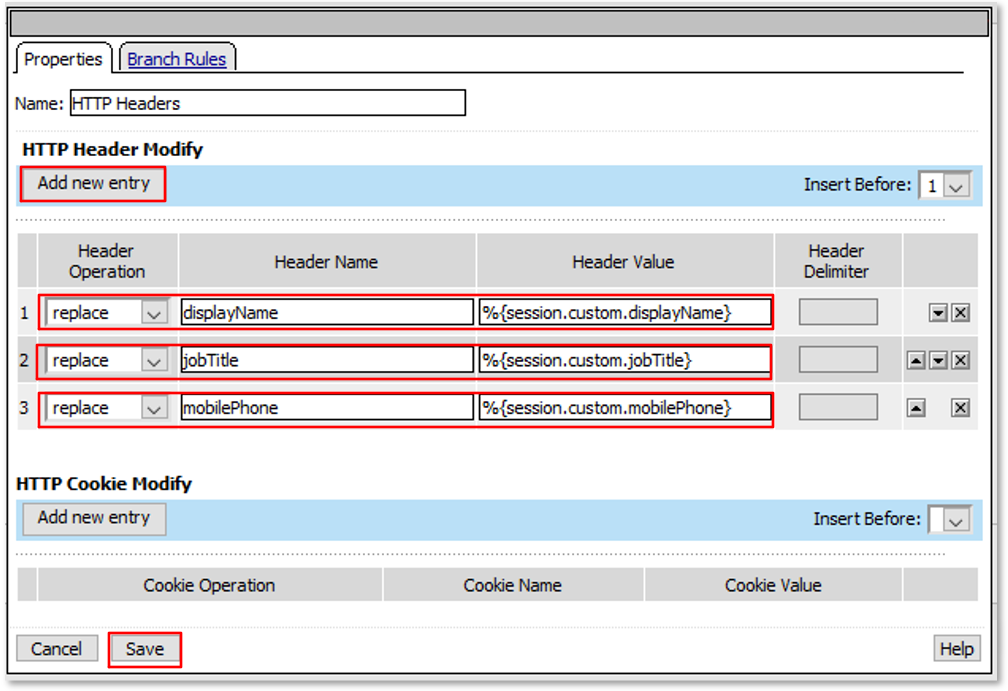
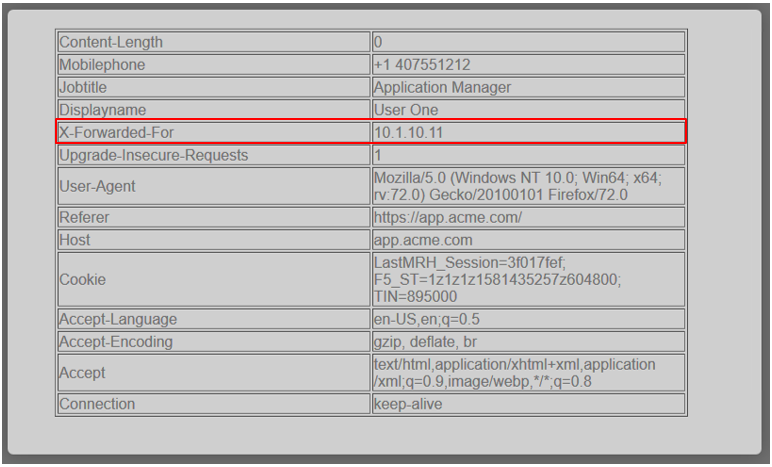
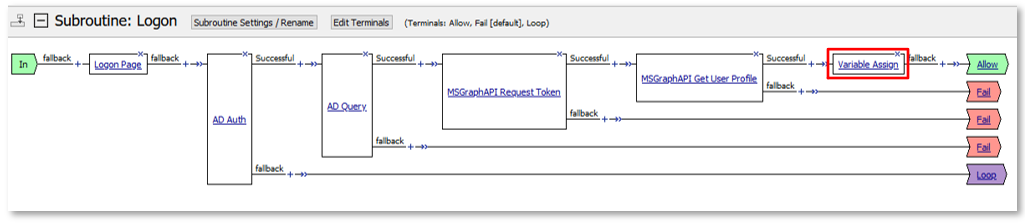
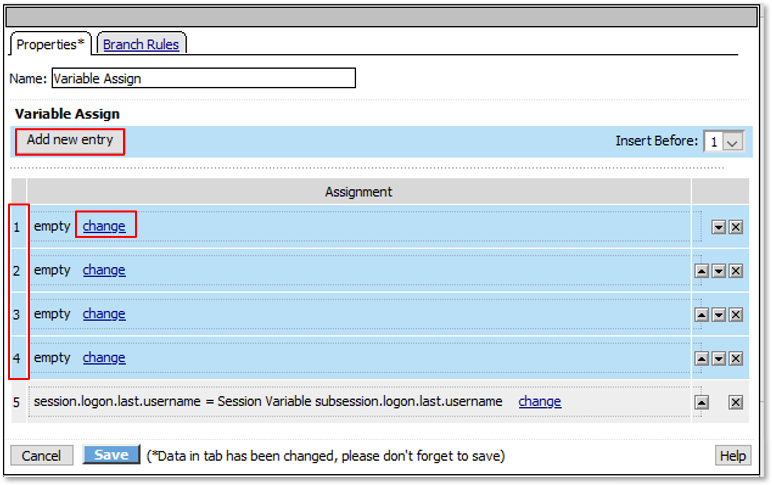
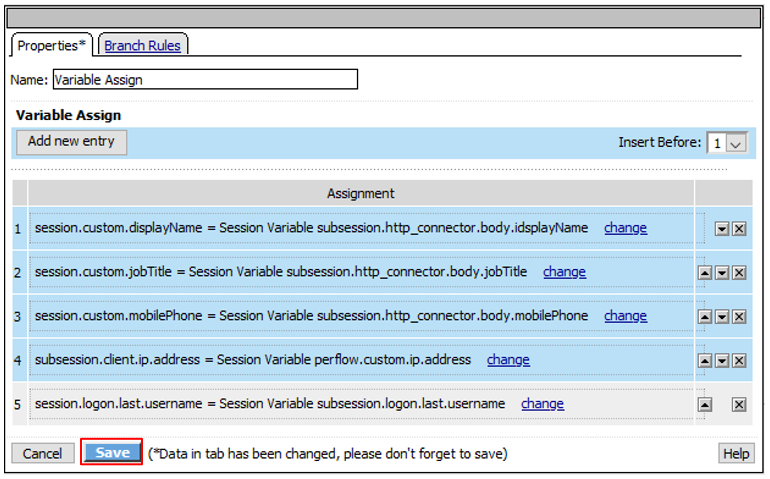
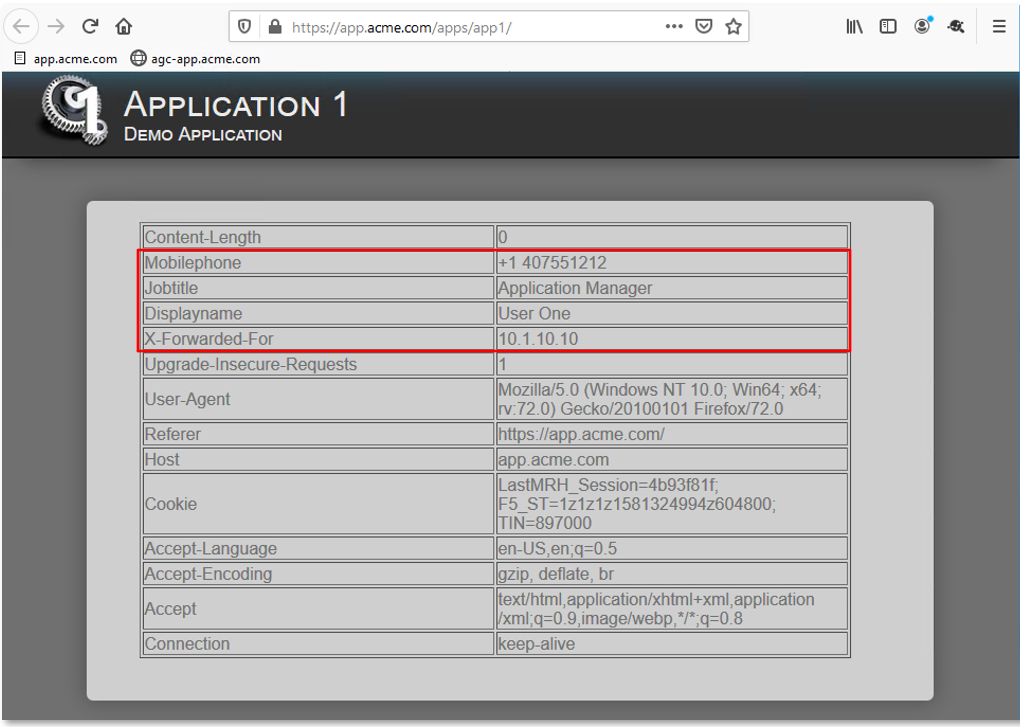
Note: The extending of Per Request Policies using the HTTP Connector can be leveraged to query any Web Service or API endpoint. In this case, MS Graph API is being leveraged to retrieve additional information regarding a logged in user. |
|
 |
|
 |
ROW 2
ROW 3
ROW 4
|
|
 |
|
 |
|
 |
ROW 1
ROW 2
ROW 3
|
TASK 4: Testing & Reviewing the Extended Logon Subroutine¶
|
 |
|
 |
|
 |
|
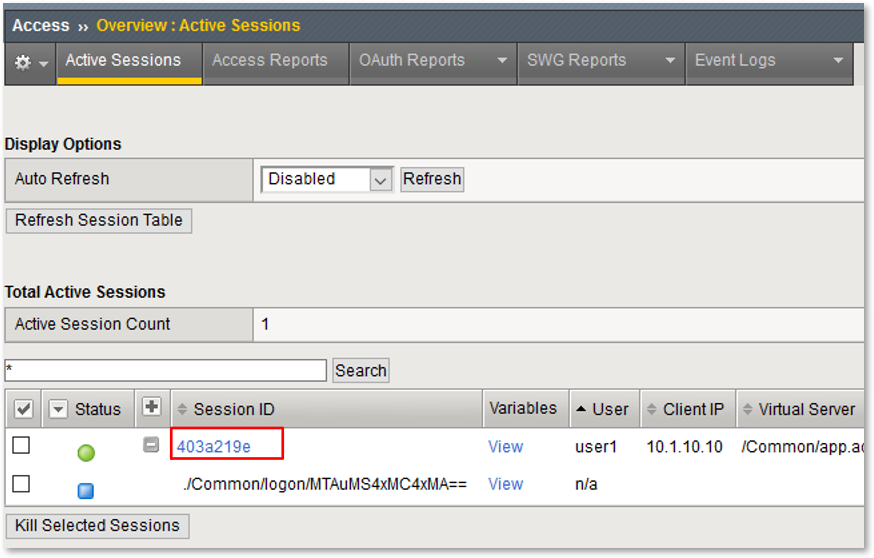 |
|
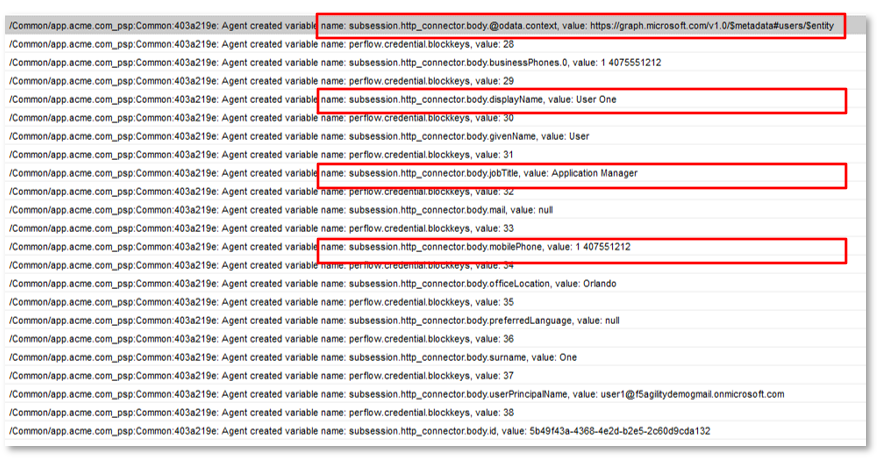 |
TASK 5: Configuring Gating Criteria¶
Note: This may already be open. |
 |
|
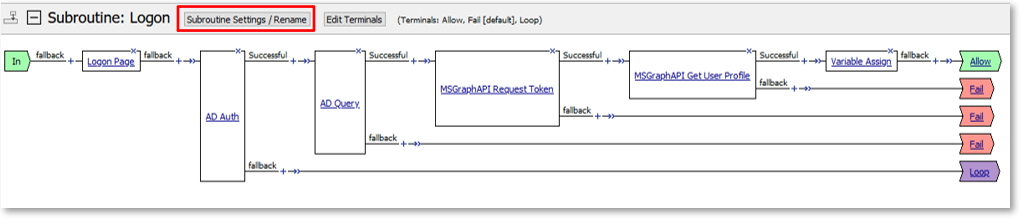 |
|
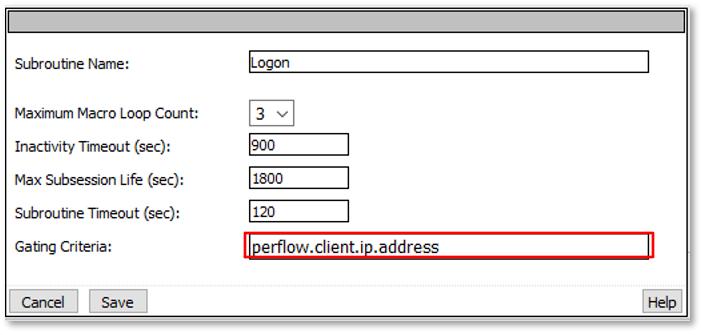 |
TASK 6: Testing Gating Criteria¶
|
|
 |
|
|
|
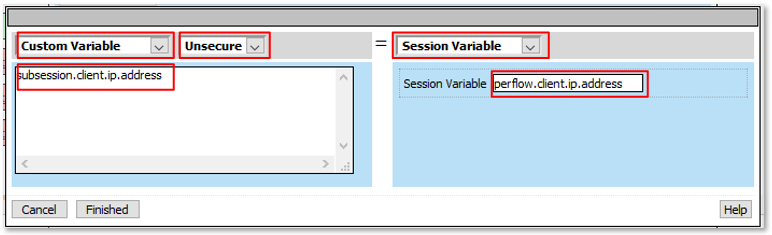
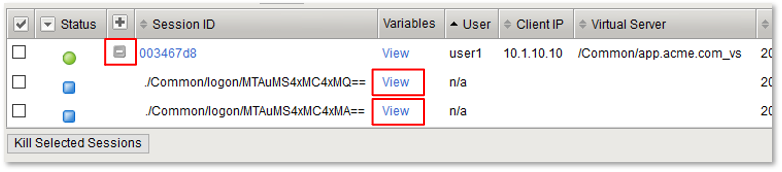
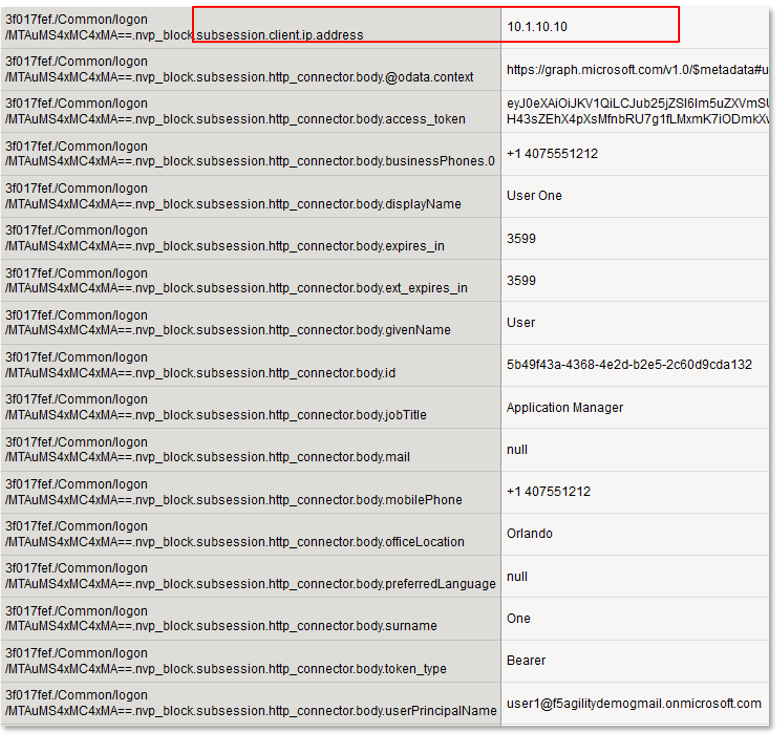
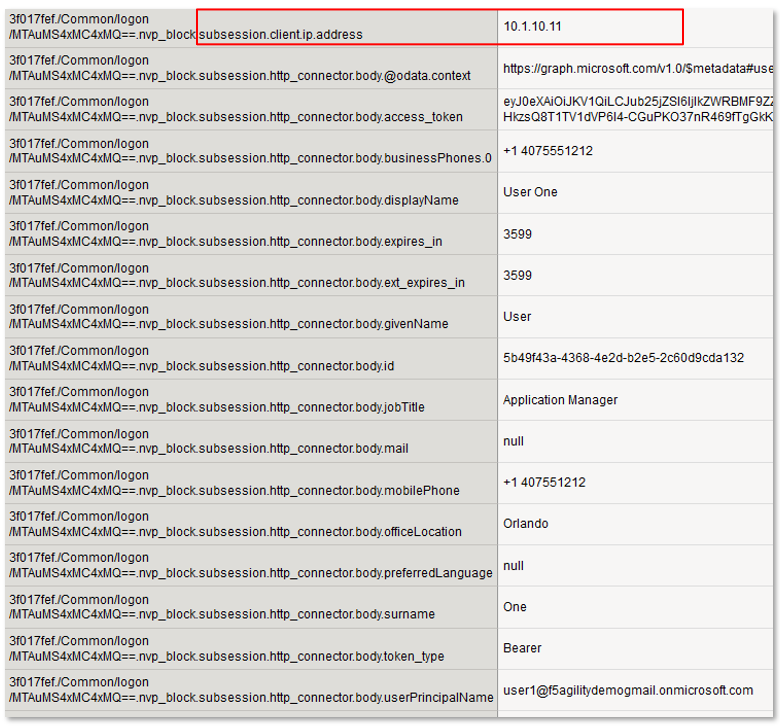
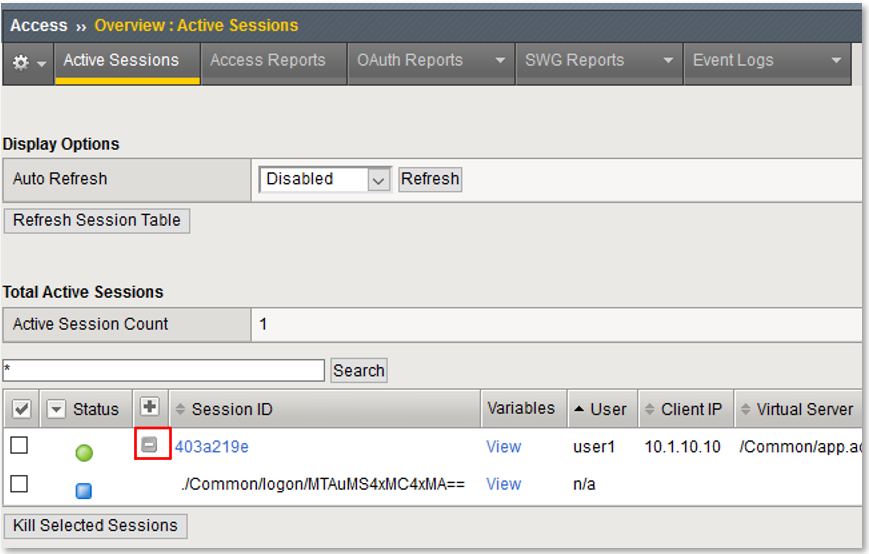
Note: The are multiple examples of Gating Criteria. In this example, client IP was used to show that any changes in the connecting entity can result in establishing a new subsession. What happens in new subsessions, the number of subsessions and how they are controlled is based on the individual customer/application need. |
TASK 7: End of Lab3¶
|
 |