NGINX Modern Apps > Class 5 - NGINX App Protect WAF & DoS Source | Edit on
Module 2 - Protect the Arcadia Finance App with NGINX App Protect WAF¶
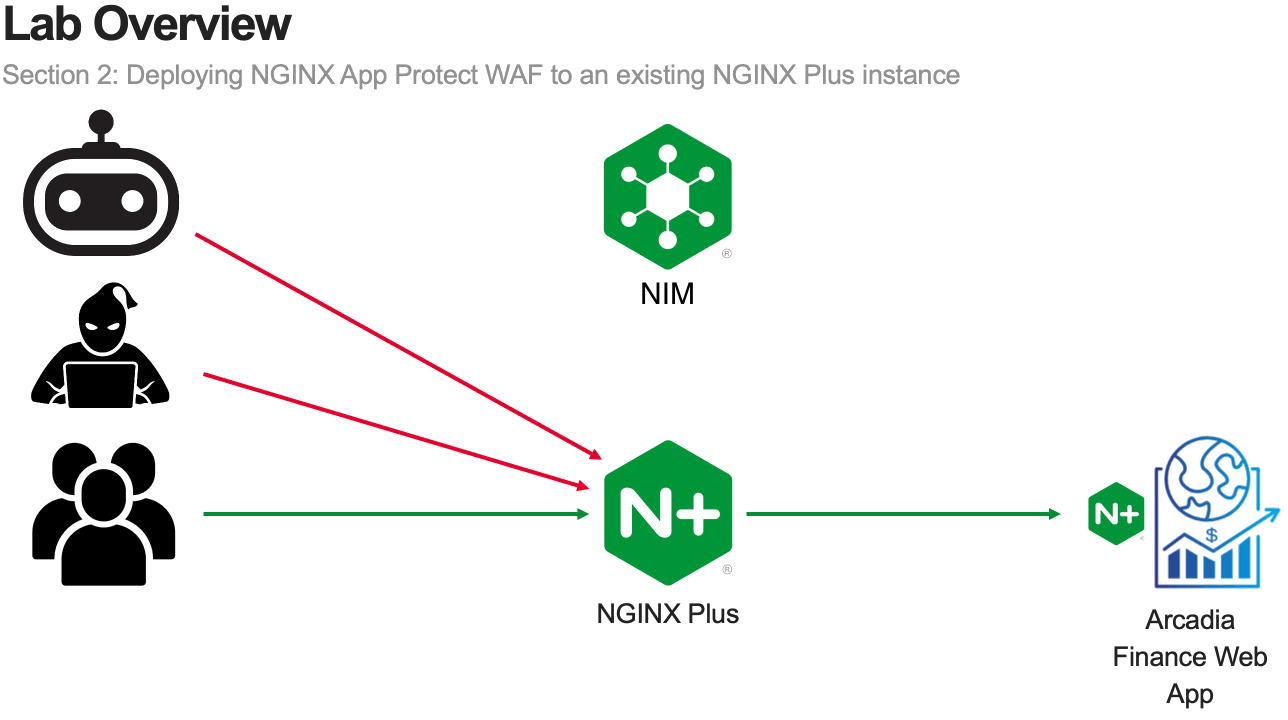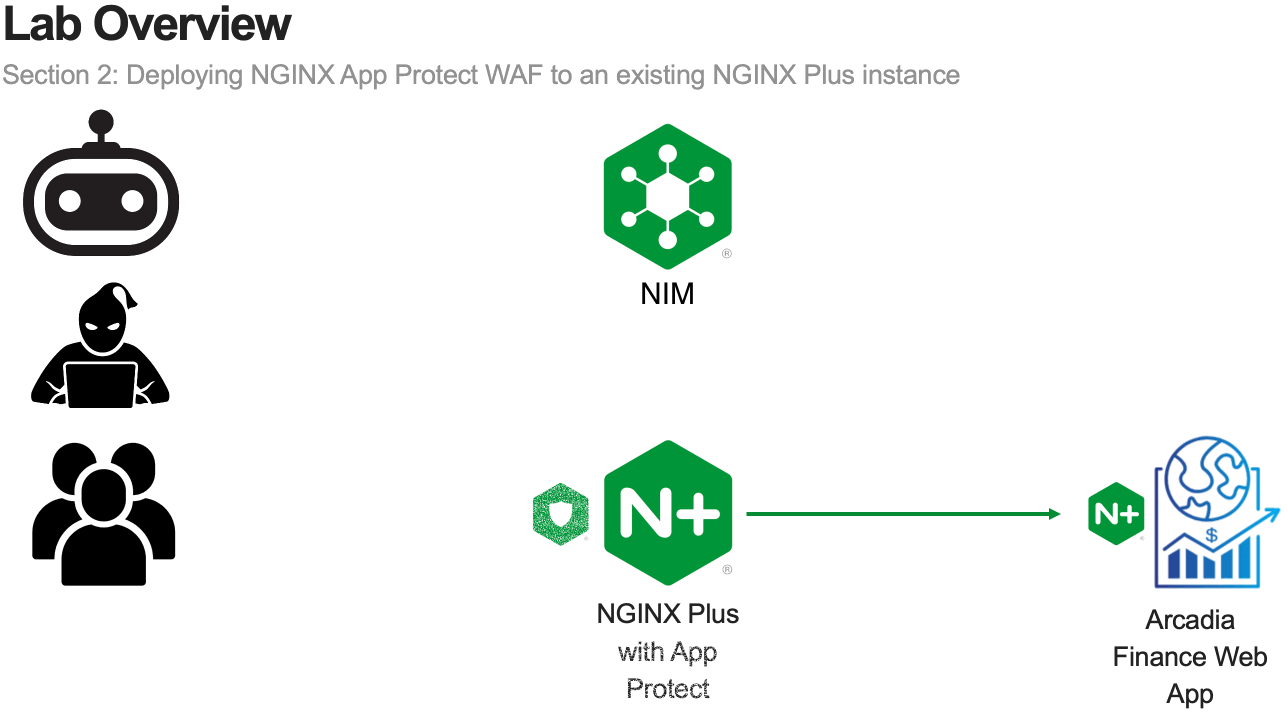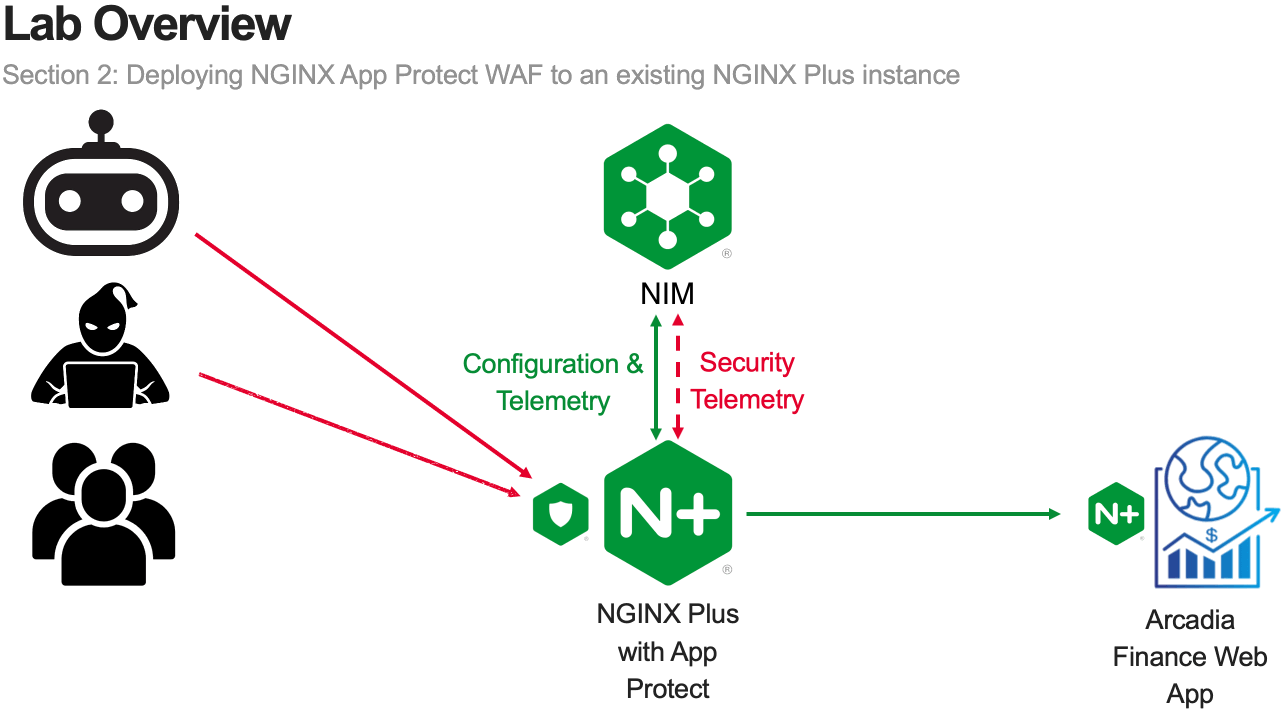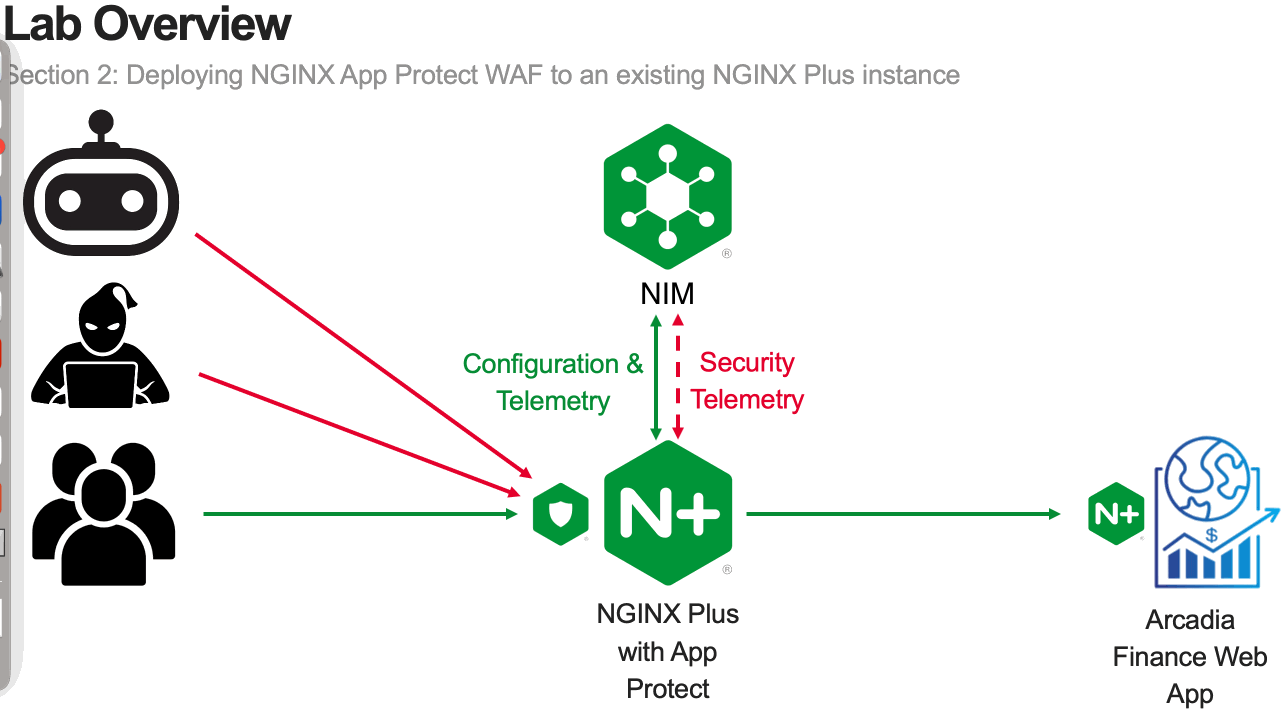
In this module, you will deploy NGINX App Protect WAF on an existing NGINX Plus instance.
Estimated completion time: 15 minutes
Note
The goal of this module is to provide familiarity with the process of adding NGINX App Protect WAF to an existing application.
Content:
- Installing NGINX App Protect on an existing NGINX Plus instance
- Adding the NGINX Plus with App Protect Instance to NGINX Instance Manager
- Test a SQL Injection Attack against the Arcadia Finance App
- Enable NGINX App Protect on the Arcadia Finance App
- Test the WAF Policy by Replicating the SQL Injection Attack
- Module Review - Protect Arcadia with NGINX App Protect WAF