F5 Public Cloud Solutions > Secure BIG-IP and Application deployments in AWS documentation! > Securing App with WAF Policy Source | Edit on
Create Base WAF Child Policy¶
Task 1 - Simulate attacks to demonstrate common web app vulnerabilities.
Open browser and go to https://<Elastic IP> to access the Hackazon website
Under Special selection click on any sale item displayed
Note the product id in the browser address bar
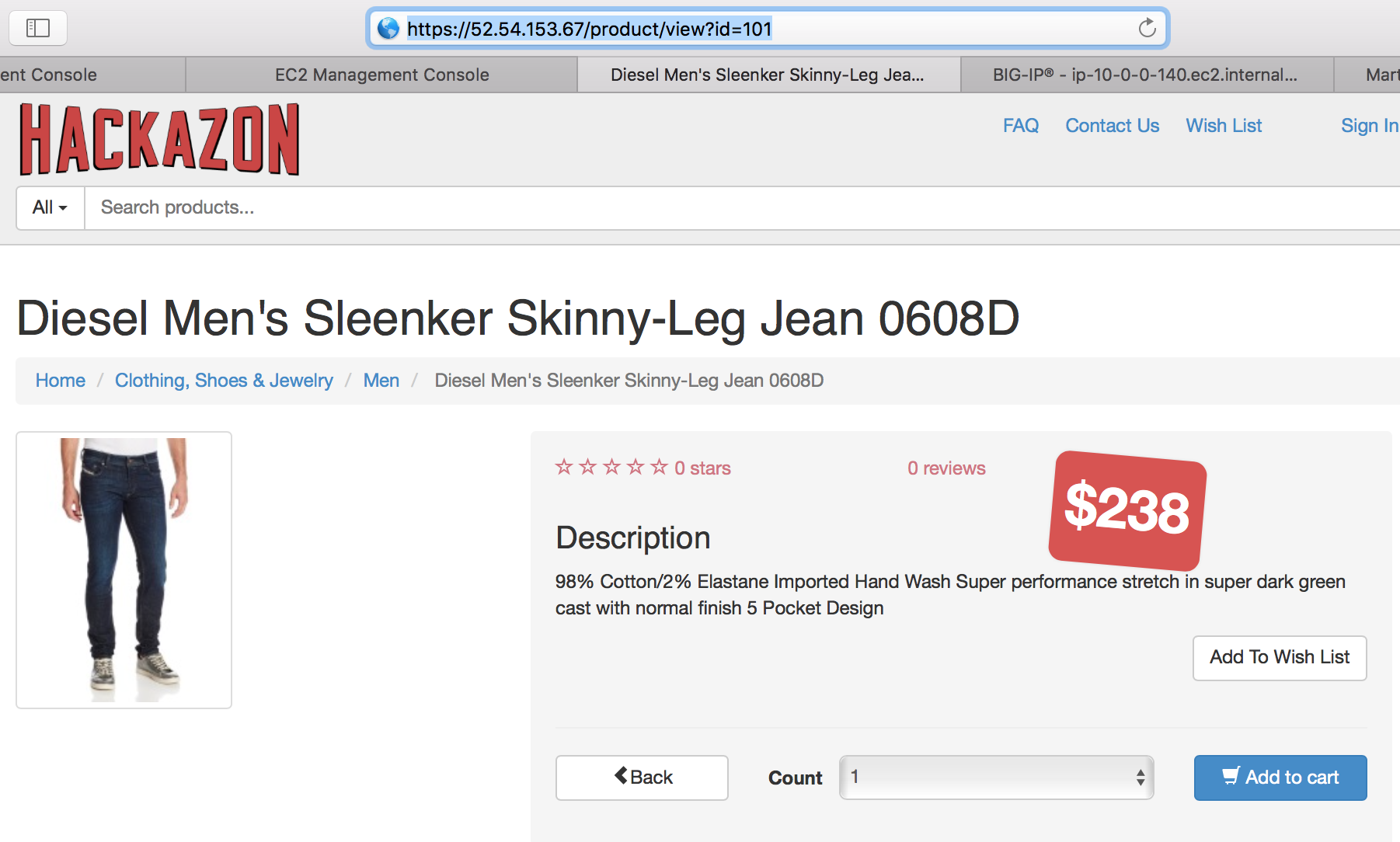
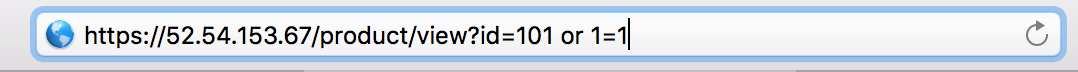
In the browser address bar append or 1=1 then press Enter
Note
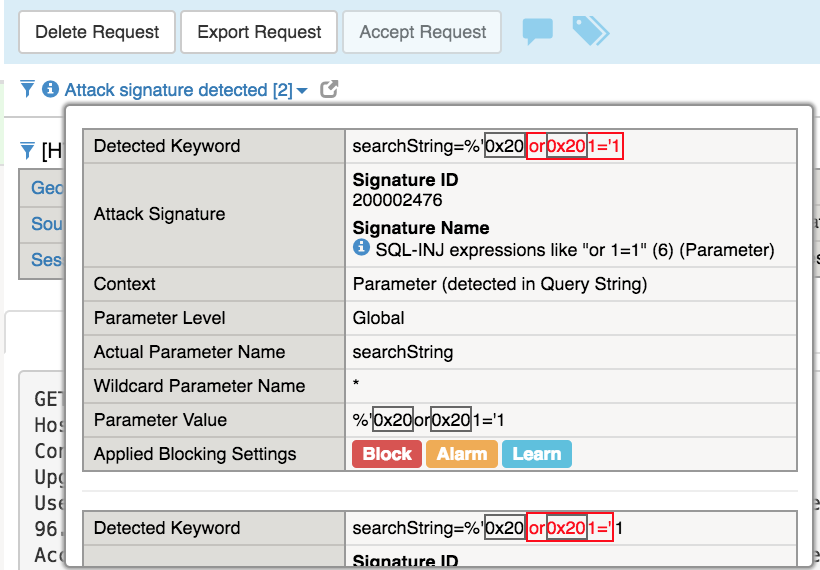
This is a common sql injection attack and although this did not return anything exciting the search request was accepted and processed with response.
In the Search field enter <script>alert(“Your system is infected! Call 999-888-7777 for help.”)</script> and press Enter
Note
This is a common Cross-site scripting (XSS) attack and although this did not return anything exciting the search request was accepted and processed with response.
Also some modern versions of browsers will block this request from displaying a response, but the request was actually sent to the application. If Chrome blocks it you can try on another browser.
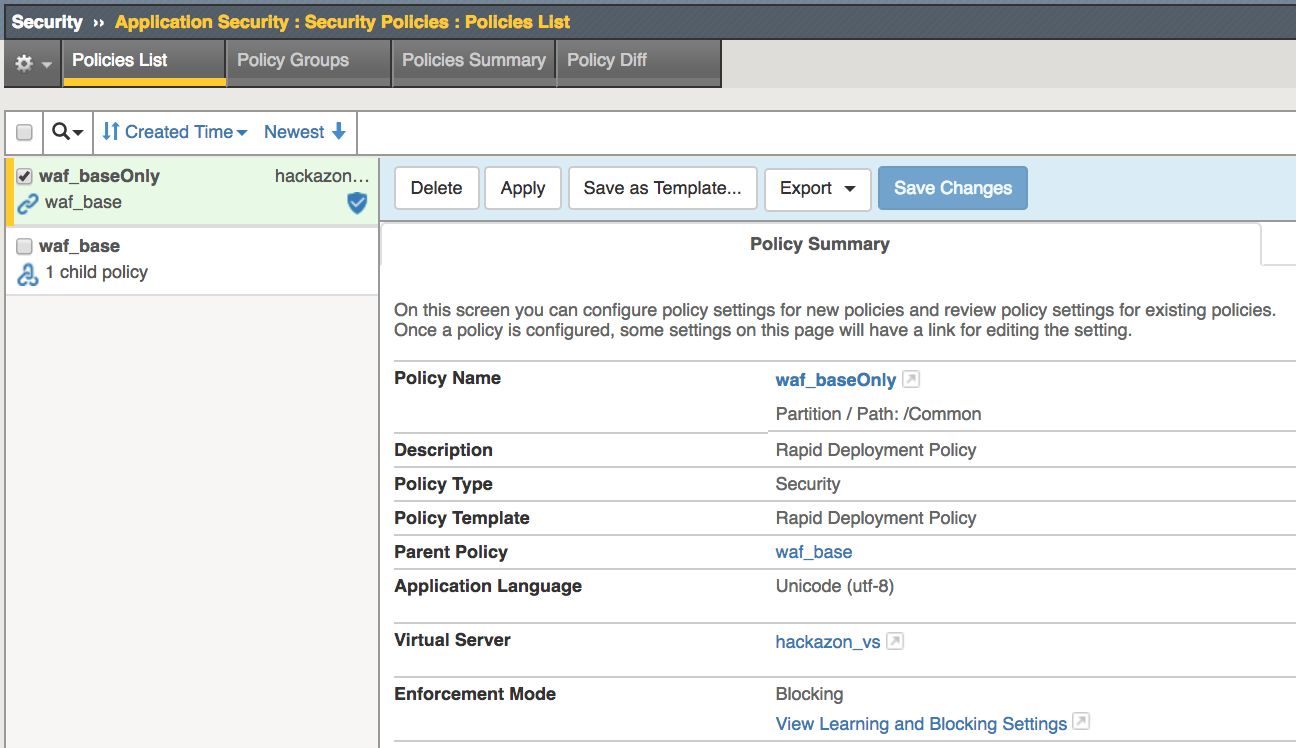
Task 2 - Create new waf policy to mitigate the vulnerabilities using info on table below:
| Policy Name | waf_baseOnly |
| Policy Type | Security |
| Parent Policy | waf_base |
| Virtual Server | hackazon_vs |
| Enforcement Mode | Blocking |
Select the Security->Application Security->Security Policies->Policies List page
Click Create New Policy
Select Advanced options
For Policy Name enter waf_baseOnly
For Policy Type select Security
For Parent Policy enter waf_base
Select OK to accept warning
For Virtual Server select hackazon_vs
Change Enforcement Mode to Blocking
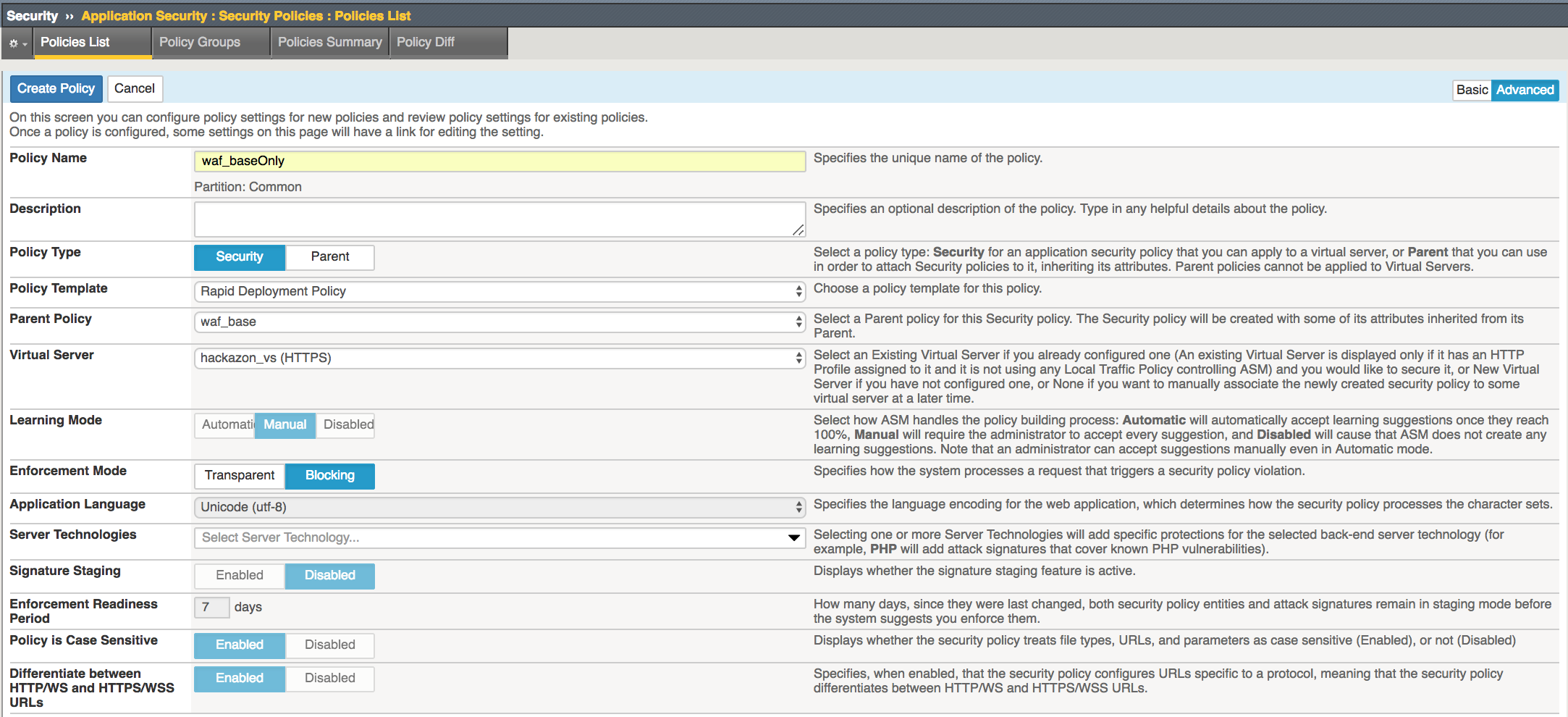
Click Create Policy
Note
This creates a child security policy which inherits the settings from the waf_base Parent Policy. The parent policy settings was created using Rapid Deployment Template which includes several common security measures and thousands of attack signatures. Signature Staging is Disabled for this lab demo but most likely will be enabled for production environments.
Task 3 - Test WAF policy.
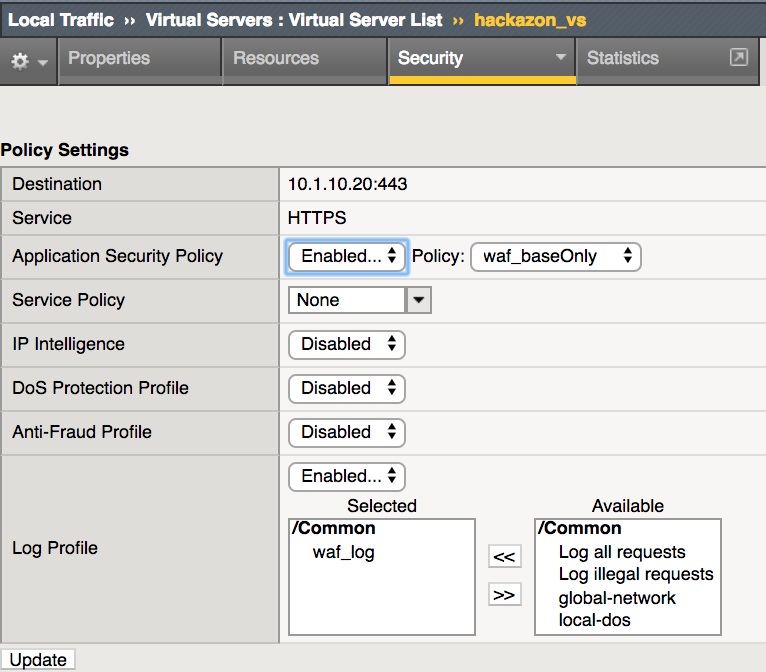
Select the Local Traffic->Virtual Servers->Virtual Servers List page
Click the hackazon_vs to display Virtual Server Properties
Click the Security->Policies tab to display Policy Settings
In the Log Profile ensure waf_log profile is selected
Select update
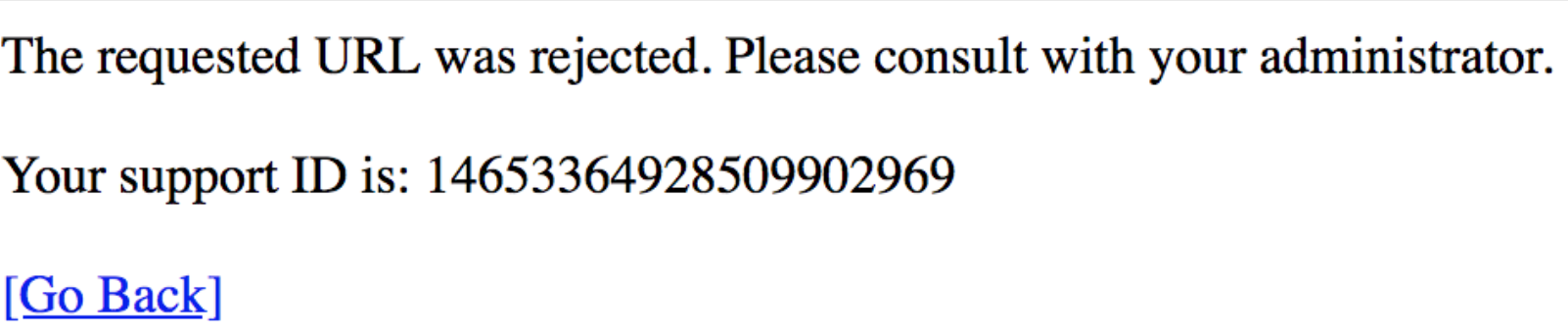
Open browser and go to https://<Elastic IP>/product/view?id=101 or 1=1. You should receive a block message similar to below. Take note of the Support ID number.
Return to hackazon main page
In the Search field type <script>alert(“Your system is infected! Call 999-888-7777 for help.”)</script> and press Enter. You should see a similar block message. Take note of the Support ID number.
Task 4 - Review WAF event logs on BIG-IP GUI.
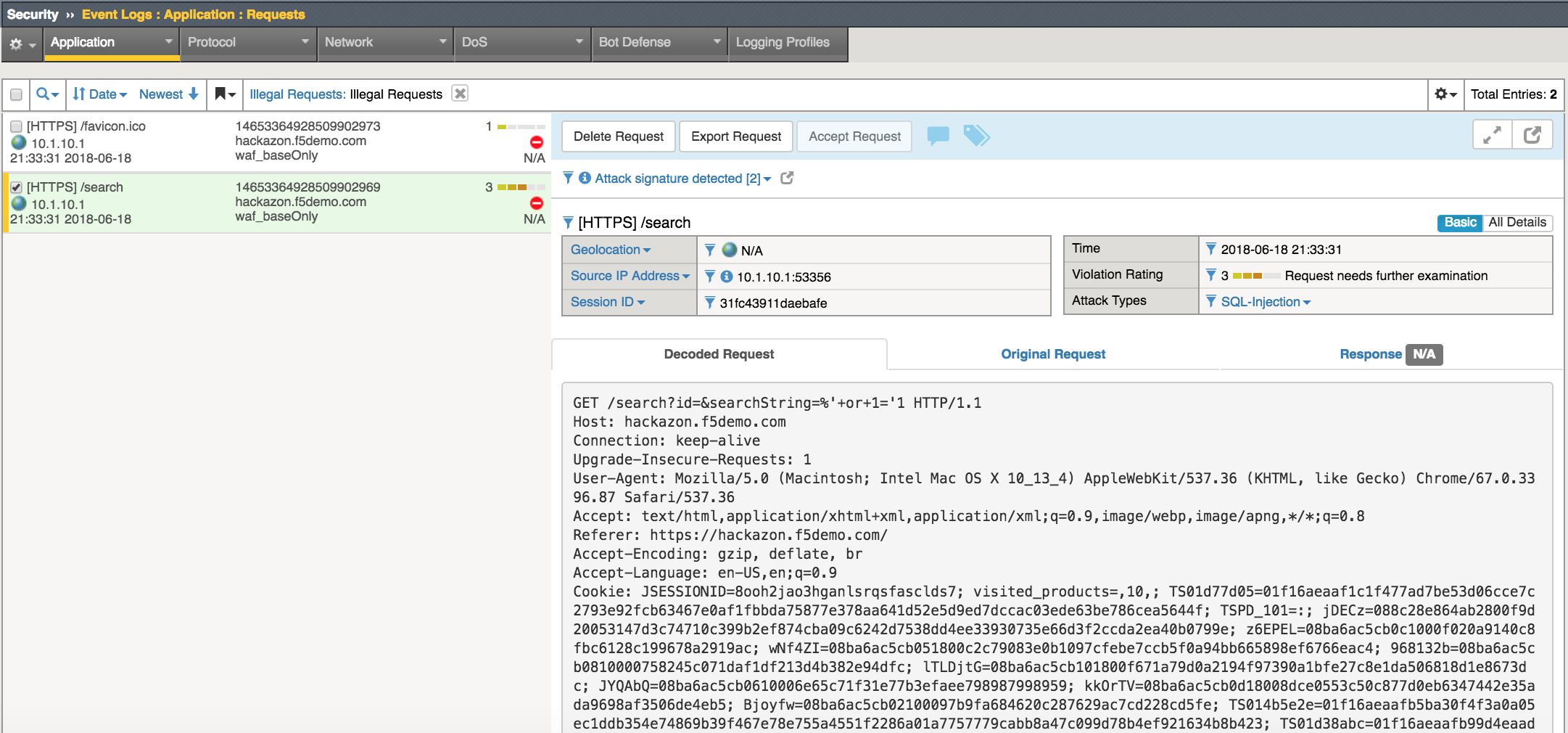
Select the Security->Event Logs->Application->Requests page
Select the Event with the matching Support ID noted on the block pages
Note
You can view the “Decoded Requests” and the “Original Request” however the “Response” is not captured by default.
Select Attack Signatures Detected to view details of the request that triggered the violation.