Threat Stack Labs > Threat Stack 201: Getting started with Cloud Workload Protection Source | Edit on
Threat Stack Playbooks¶
Spring4Shell Playbook¶
First, Access the Linux Ubuntu 20.04 LTS Box via WebShell.
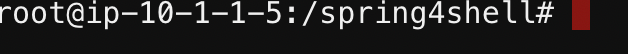
Next, navigate to the /spring4shell/ directory found in root by entering the following command:
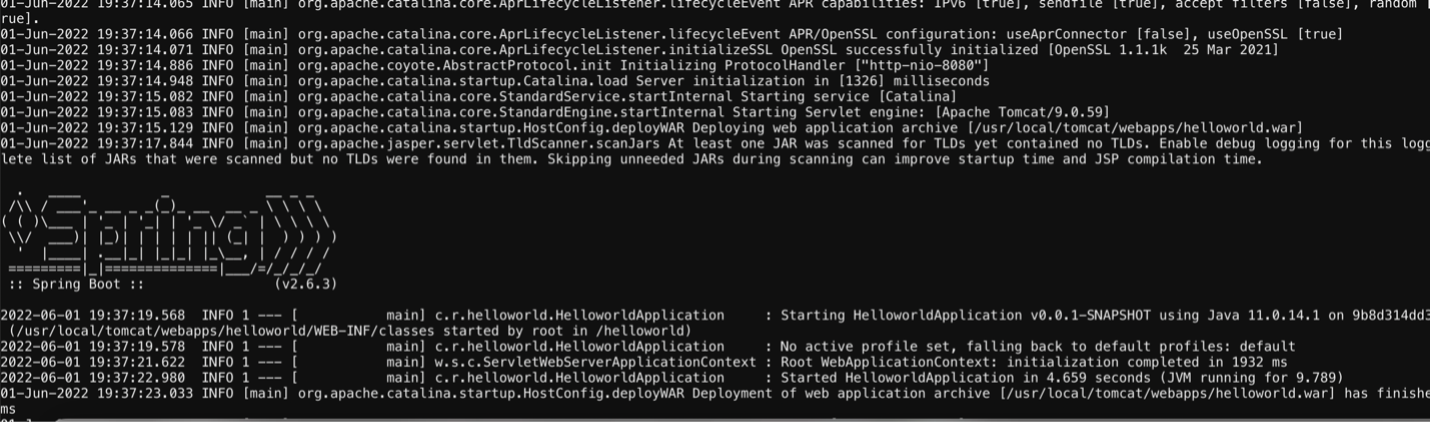
Next, to spin up the vulnerable Spring server, run the following command:
after you run the command, you should see the following screen.
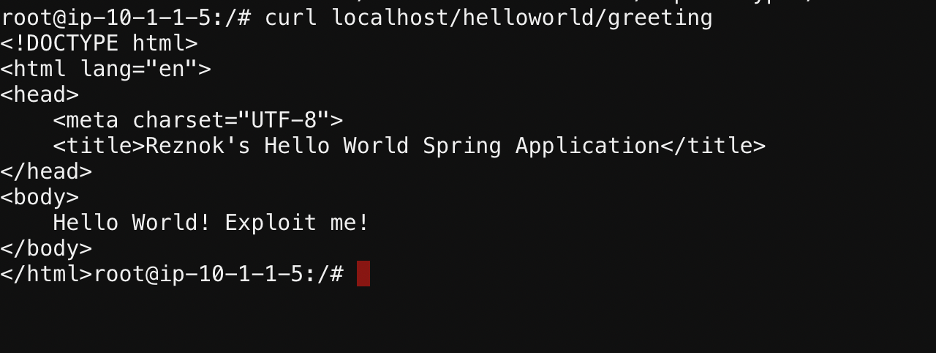
Go back to UDF and open another shell connection the linux host again. Then run the following command
The following output should manifest.
Now to exploit, run the following command in the spring4shell directory. Navigate to the spring4shell directory by running the following commands.
The following output should manifest.
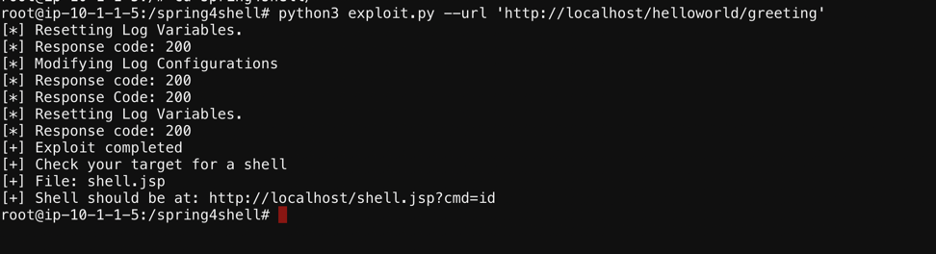
Now run the following command via shell
Note
Run the –output flag as this is required for the output to display
then run:
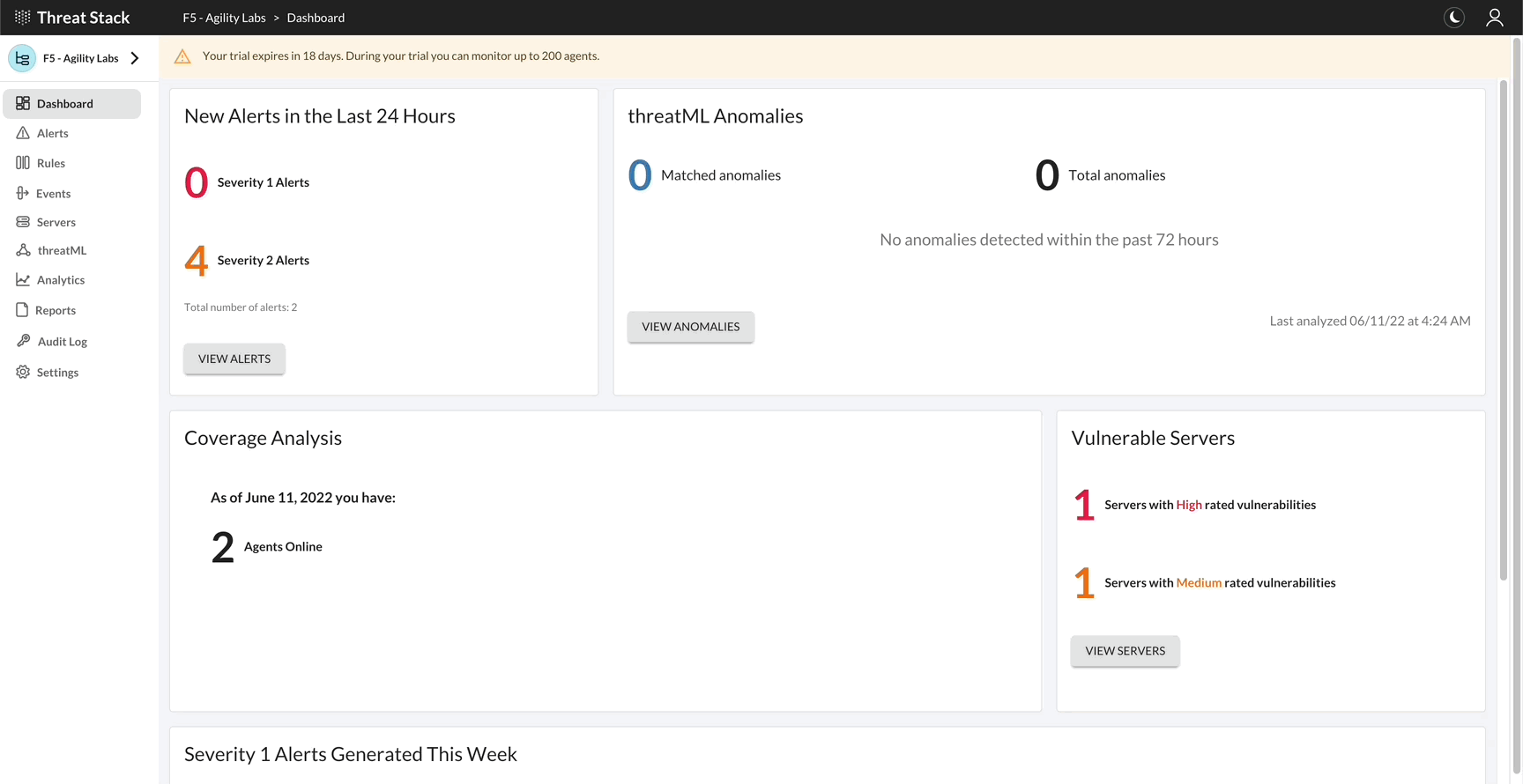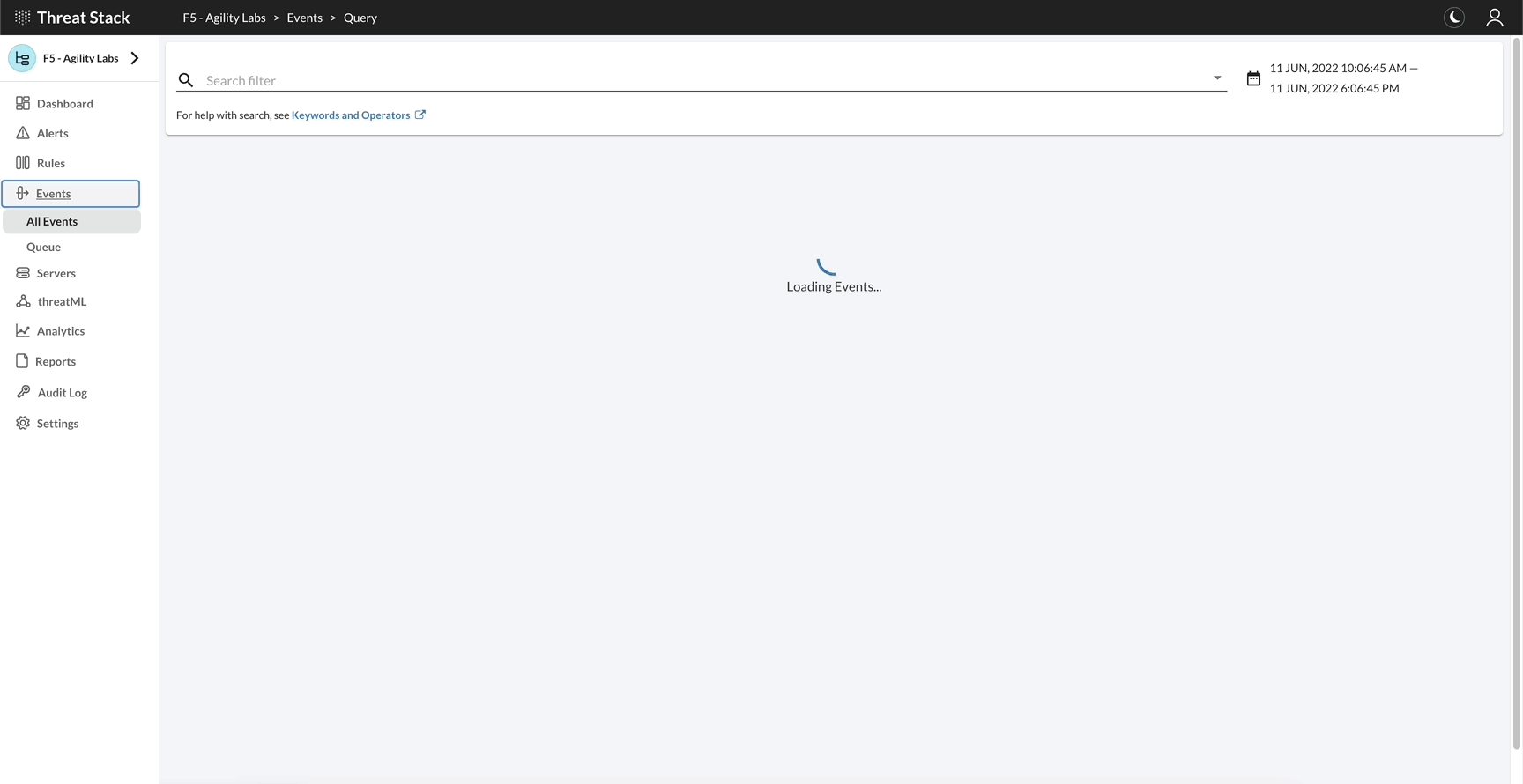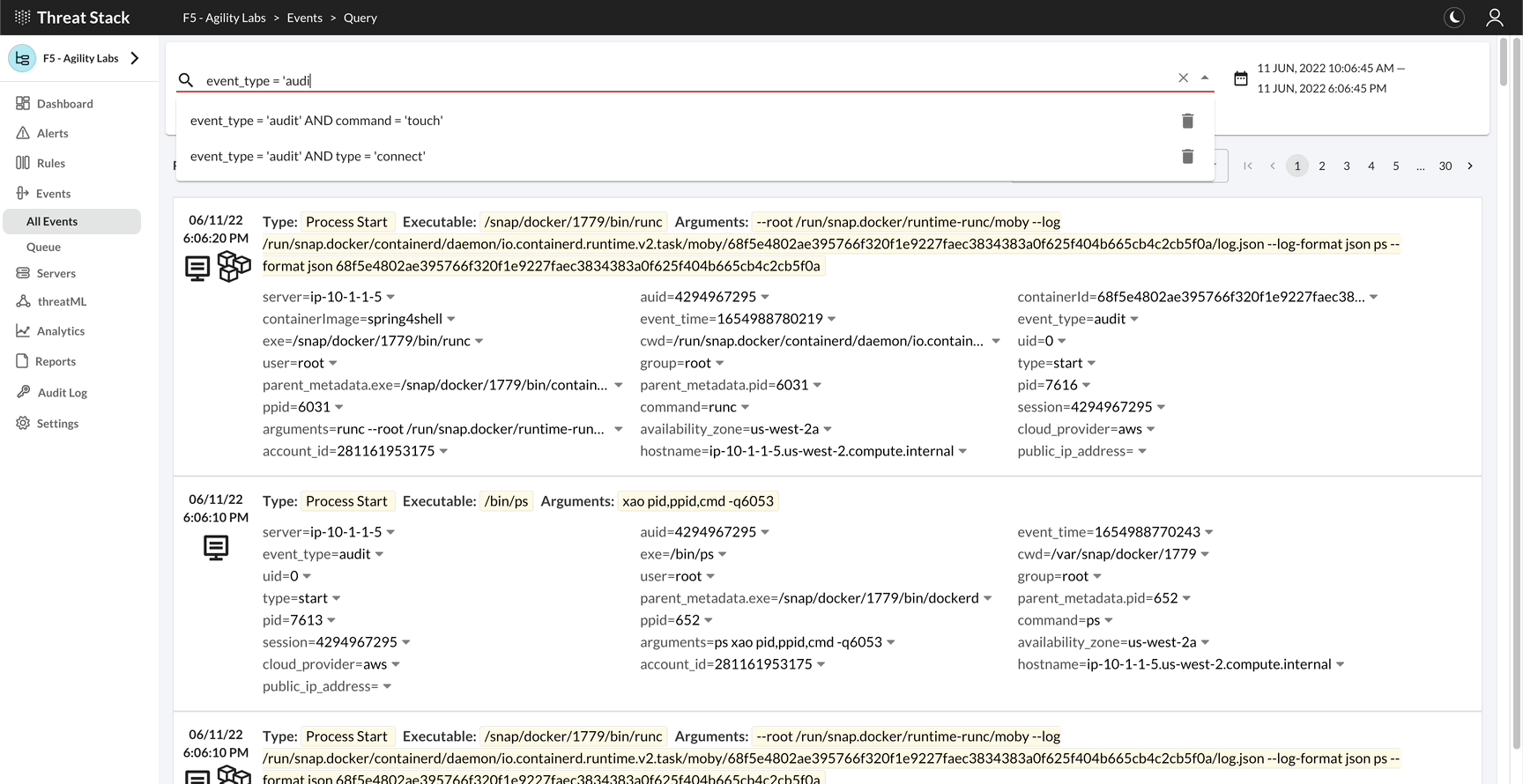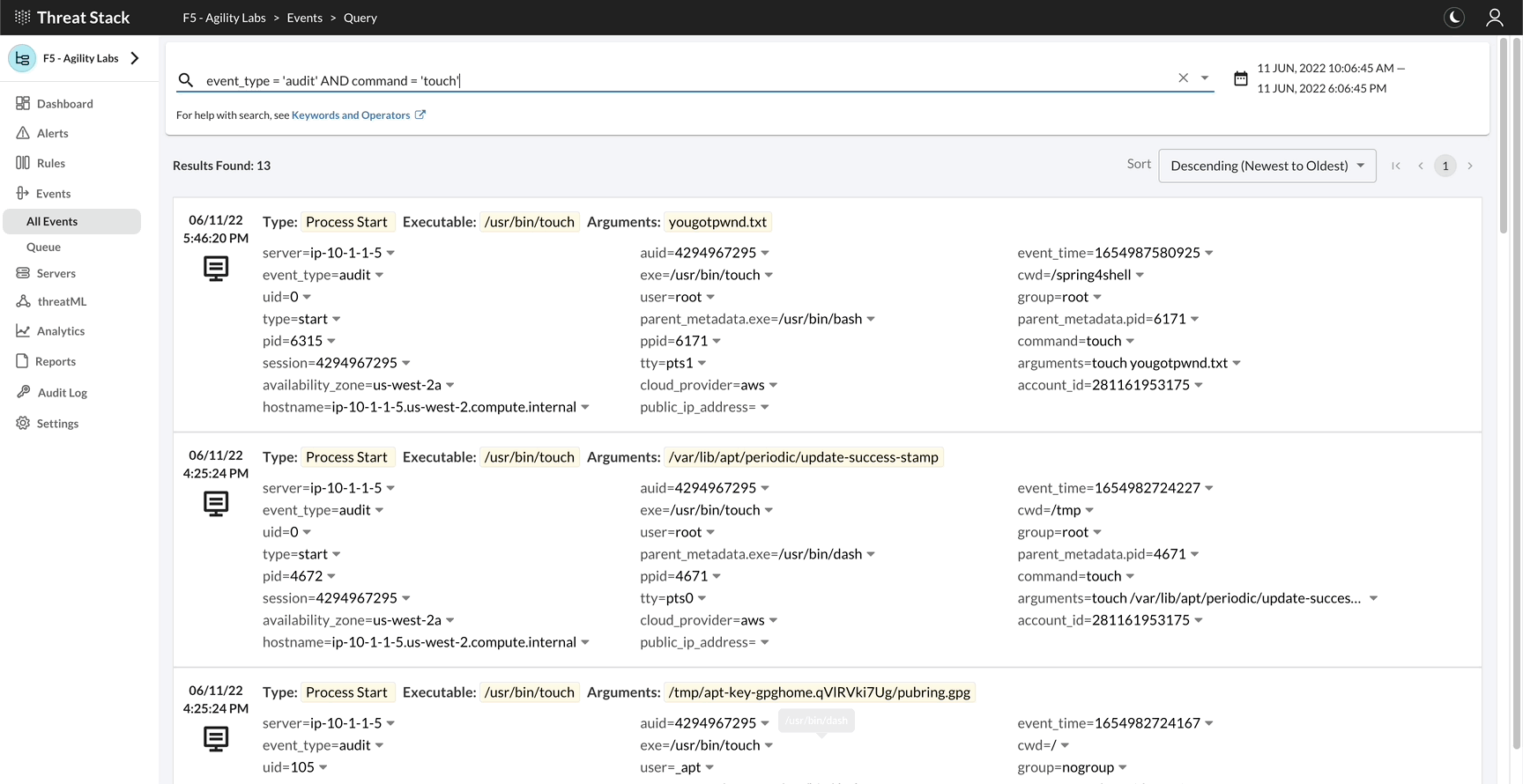
If you navigate to event search and enter the following query and event search, you will see your command.