F5 Web Application Firewall Solutions > WAF 341 – Advanced Protection and Positive Security (Self Guided) > Module 2: HTTP Methods, DataGuard, Sensitive Data Source | Edit on
Lab 2.3: Sensitive Data¶
By default, the BIG-IP ASM system logs information about incoming requests to the request log in plain text. In some cases you may want to mask request information in the logs as some requests include sensitive information, such as authorization credentials or credit card information. When you enable Mask Value in Logs for a policy element, the system replaces the sensitive data with asterisks (******). The masked data cannot be viewed by the administrator.
You can mask data in the logs for the following policy elements.
Parameters Masks the parameter value, including the value for positional parameters. The setting does not mask the parameter name.
GET /profiles/******
HTTP headers Masks the header value. The setting does not mask the header name.
GET / HTTP/1.1
Host: Example.com
Connection: Keep-alive
Authorization: ******
Cookie: TS-Cookie
Cookies Masks the values for allowed and enforced cookies types. The setting does not mask the cookie name and does not apply to BIG-IP ASM cookies.
GET / HTTP/1.1
Host: Example.com
Connection: Keep-alive
Cookie: ******
JSON Profiles Masks elements within the JSON data whose values are should considered sensitive.
secID: ******
XML Profiles Masks sensitive data in an XML document. You can specify the element or attribute whose value contains sensitive data and should be masked by the policy.
<secID>******</secID>
See also
More information can be found here https://support.f5.com/csp/article/K52154401
Task 1 - Login Page¶
Open a new Private Browsing window in Firefox .
Go to the to Juiceshop login page and login as f5student@agility.com
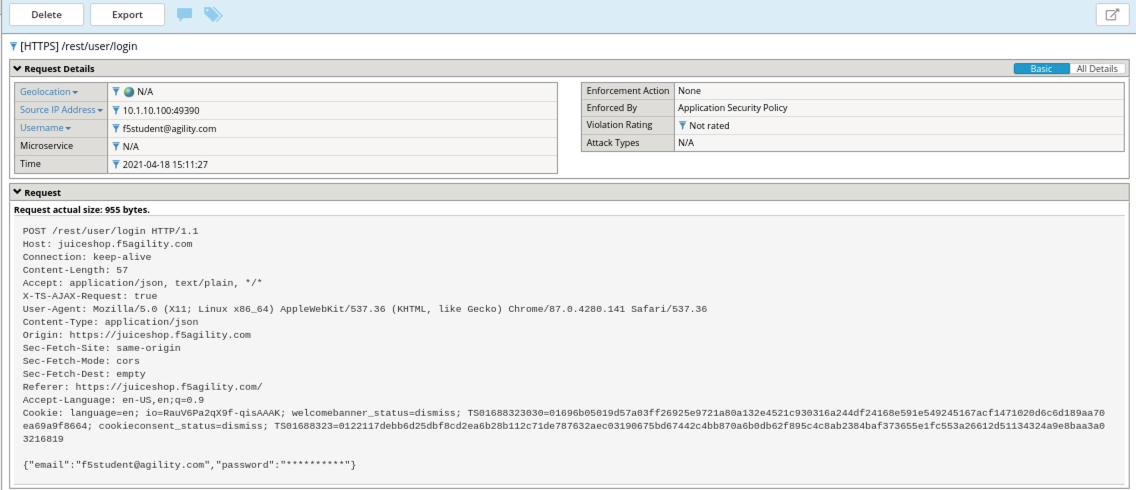
Examine the most recent request in the event logs for /rest/user/login. Notice that you cannot see the password for f5student@agility.com in the request. The password is masked in the logs due to a sensitive parameter setting which is created by the policy automatically.
Open the BIG-IP GUI interface.
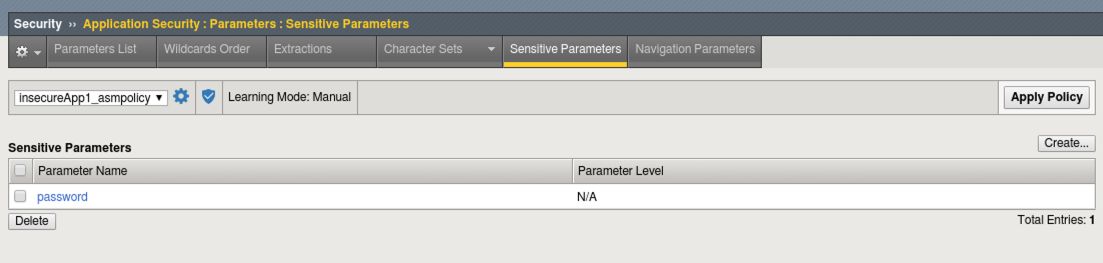
Navigate to Security -> Application Security -> Parameters List and select the Sensitive Parameters tab and view the configuration.
Next we will obfuscate cookies as they could contain sensitive information we would not want an administrator to have access to.
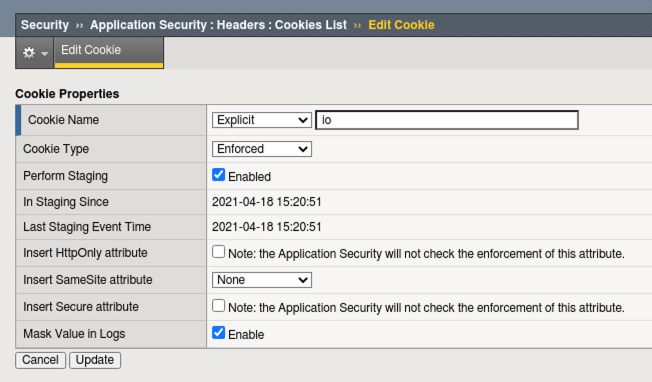
Navigate to Security -> Application Security -> Headers -> Cookies List.
Click Create and create the io cookie as seen below
Click Create and then Apply Policy
Open a new Private Browsing window in Firefox .
Go to the to Juiceshop login page and login
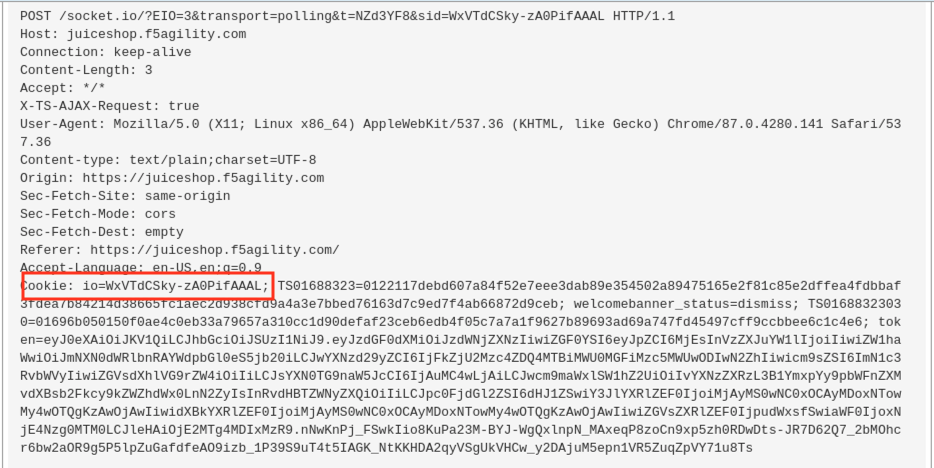
Examine the most recent requests and compare to earlier requests in the event log by navigating to Security -> Event Logs -> Applications -> Requests.
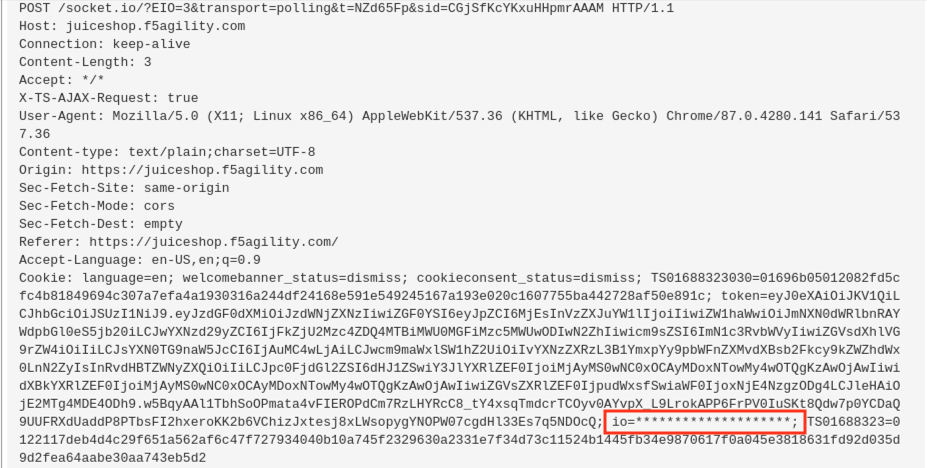
The cookie content is now obfuscated in the Logs when they were visible before.
After applying mask.
This concludes section 2.3