F5 Web Application Firewall Solutions > WAF 341 – Advanced Protection and Positive Security (Self Guided) > Module 3: DataSafe, Parameter Protection Source | Edit on
Lab 3.2: Protection from Parameter Exploits¶
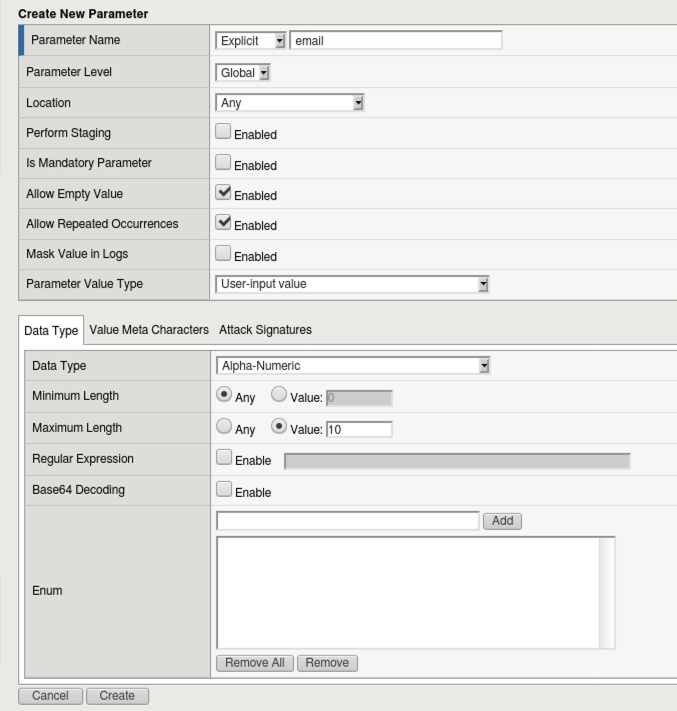
In this lab we will look at the parameter protection capability in F5 WAF. F5 WAF can leverage automatic parameter learning using the automatic policy builder feature however in the interest of time, this lab we will be configuring parameters manually.
See also
For more information on Automatic Policy Builder: https://support.f5.com/csp/article/K75376155
Task 1 - Create Parameters¶
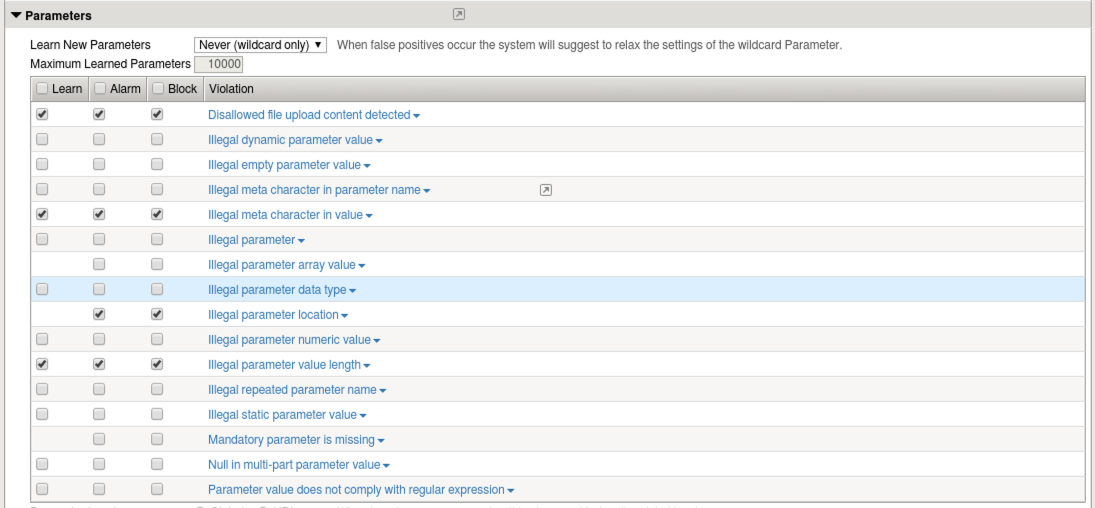
Task 2 - Modify Learning and Blocking¶
Navigate to Security -> Application Security -> Policy Building -> Learning and Blocking Settings and enable the Parameters settings for ‘illegal parameter value length’ and ‘illegal meta character in value’ as seen below in the Policy Building Settings section. After you have finished making the modifications click Apply Policy.
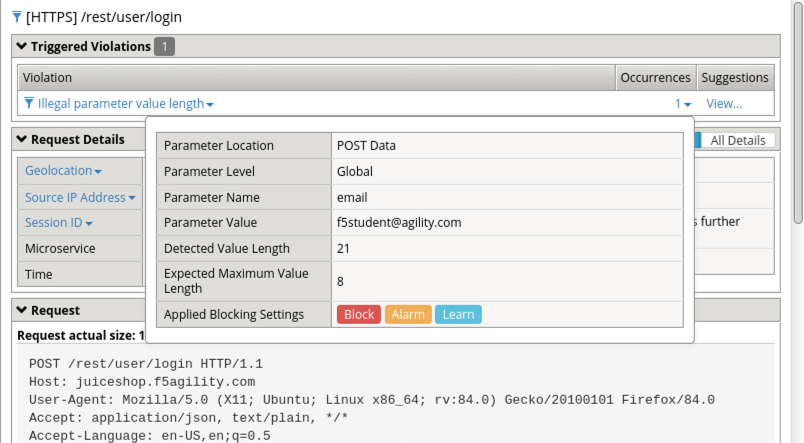
Task 3 - Test Configuration¶
Open a new Firefox Private Browsing window and go to the Juiceshop login and login as f5student@agility.com.
Your login attempt should be unsuccessful.
Examine the recent event logs under Security -> Event Logs -> Application -> Requests for the /rest/user/login events.
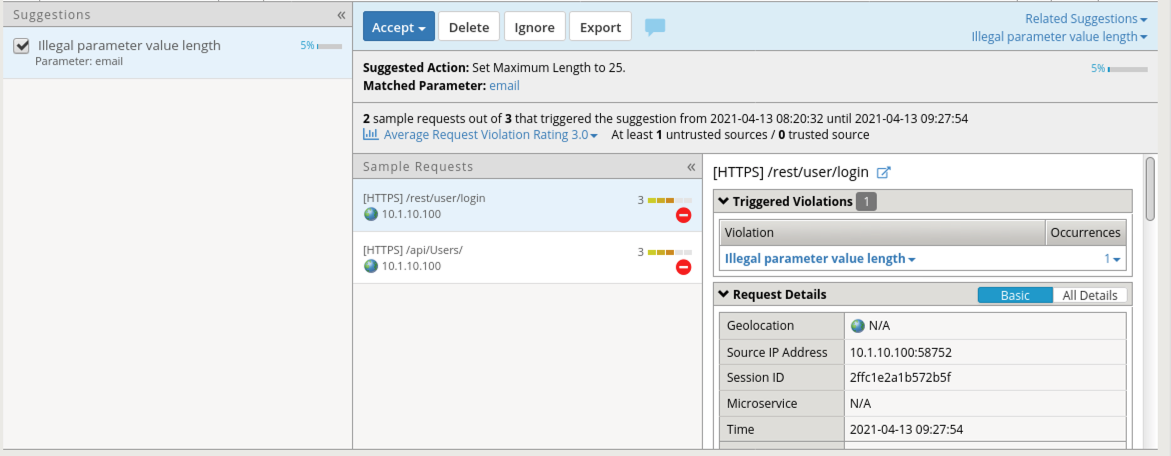
Navigate to Security -> Application Security -> Policy Building -> Traffic Learning
Review the entry for illegal parameter value length.
Click Accept Suggestion and then click Apply Policy
Open a new Firefox Private Browsing window and go to the to Juiceshop login as f5student@agility.com
Your login should be allowed.
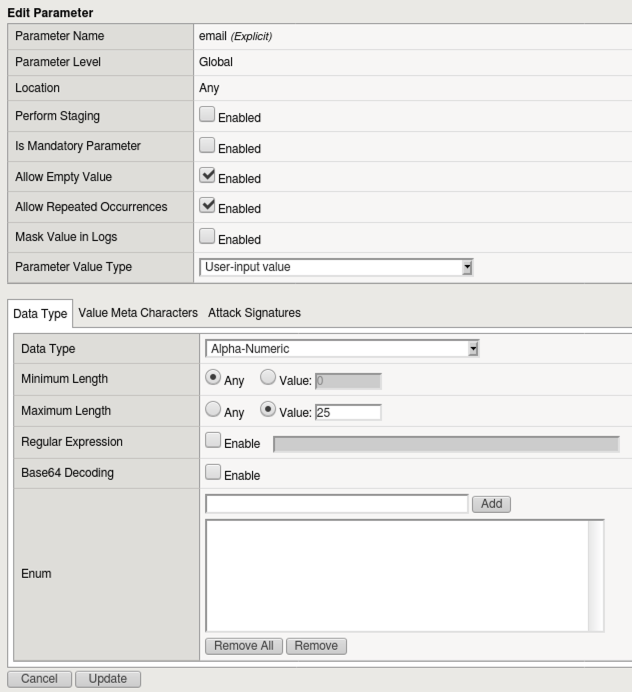
Return to Security -> Application Security -> Parameters List Notice that accepting the suggestion for the username parameter has adjusted the maximum-length value to 25.
This concludes Lab 3.2