F5 BIG-IQ Centralized Management Lab > BIG-IQ All Labs > Class 9: BIG-IQ Access Policy Manager > Module 1: APM access and per-request policies Source | Edit on
Lab 1.2: Modifying an existing APM access policy using Virtual Policy Editor (VPE)¶
Note
Estimated time to complete: 25 minutes
Lab environment access¶
If you have not yet visited the page Getting Started, please do so.
Access Policy Review¶
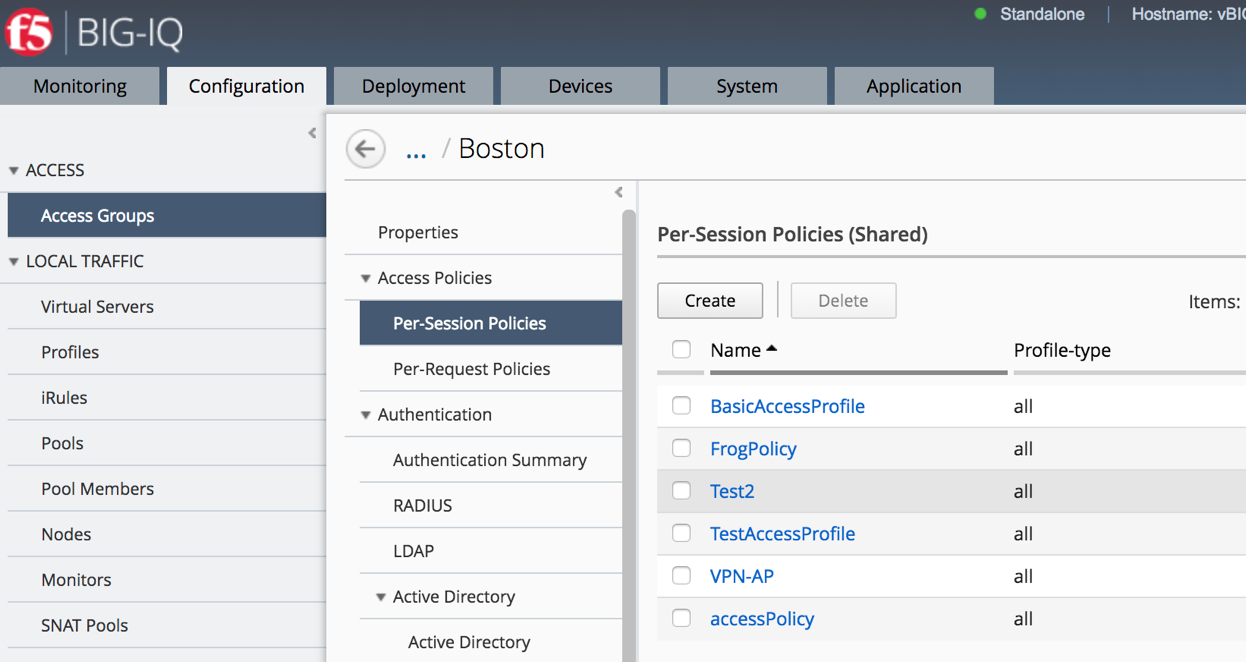
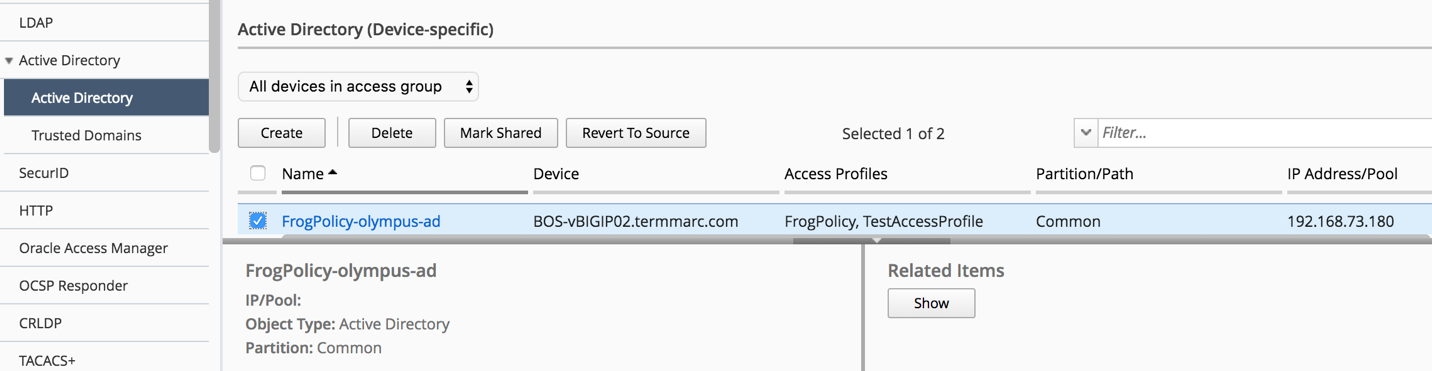
Navigate to Configuration Access Access Groups BostonAG Access Policies Per-Session Policies TestAccessProfile
The access policy will be displayed in a new screen as shown below. Compare the Access policy in BIG IQ with the policy in BIG IP source device and ensure that they are exactly same. Open the browser shortcut for the BIG-IP01 in a new tab from Chrome.
Location Specific Object Modification¶
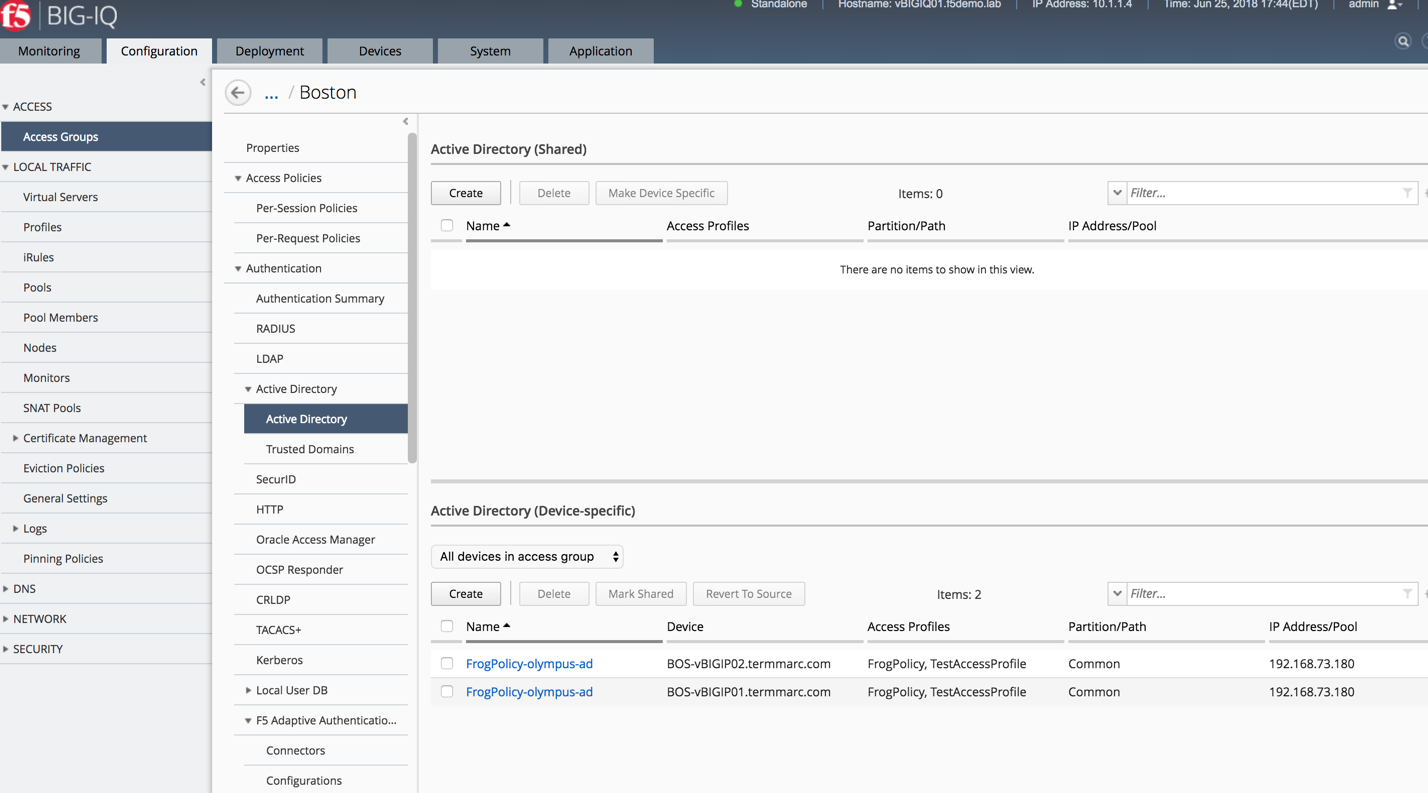
Navigate to Configuration Access Access Groups BostonAG Authentication Active Directory Active Directory
LSO or Location Specific Objects are objects within an access profile/policy that relate to more specific geographic areas normally and are not shared between all devices by default to prevent misconfigurations. As an example, AAA servers are located in all office/data centers globally however if an end user is accessing a policy on an APM in Europe we wouldn’t want their authentication requests to be sent over a WAN link to some Domain Controller in another country and cause a tremendous delay for that user.
Click the check box for the FrogPolicy-olympus-ad for the BIGIP02 device.
Click the Mark Shared button and accept the warning
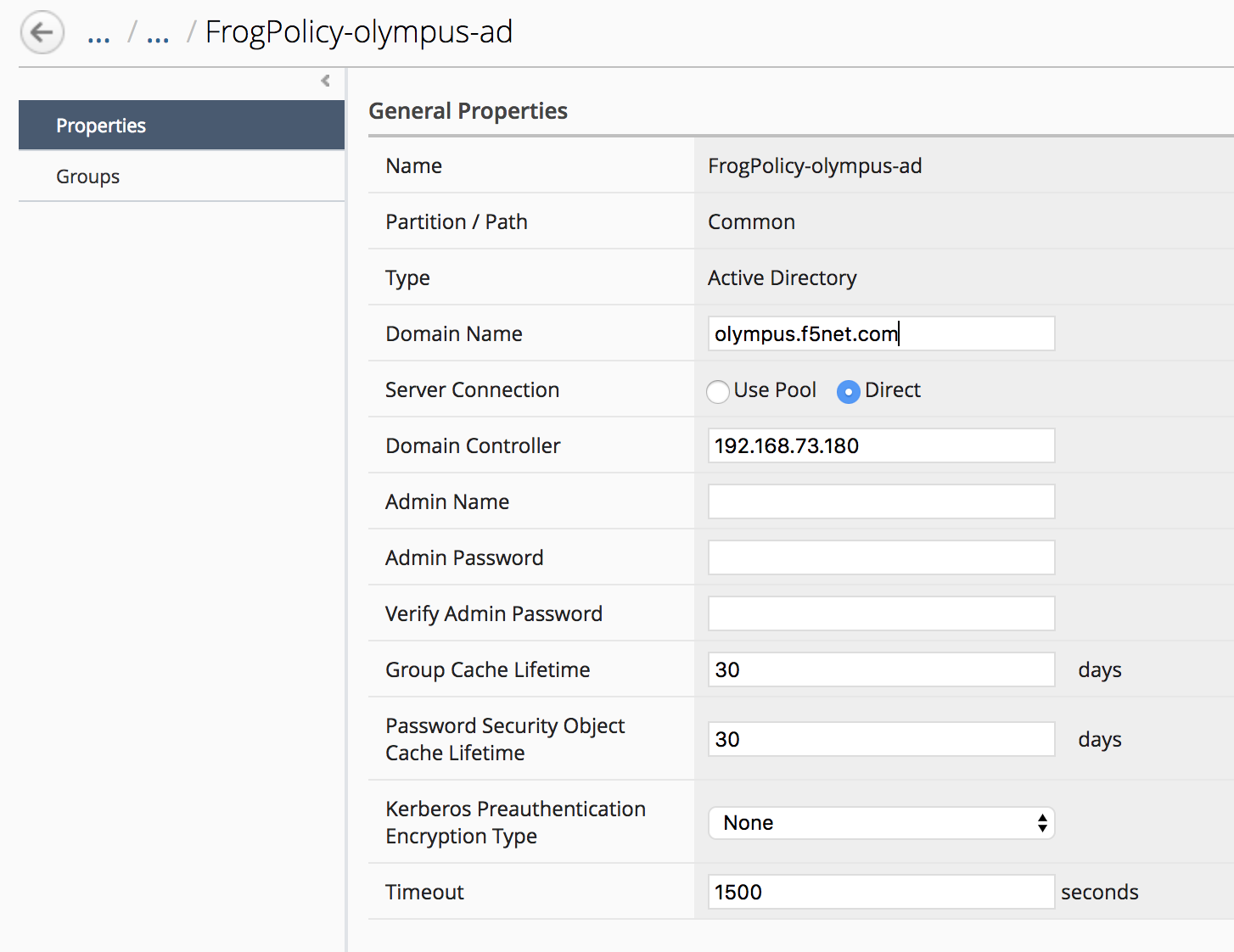
Click on the AAA object to edit the properties
Change the Timeout value from 15 to 1500
Click Save & Close
Modifying an existing APM access policy using VPE¶
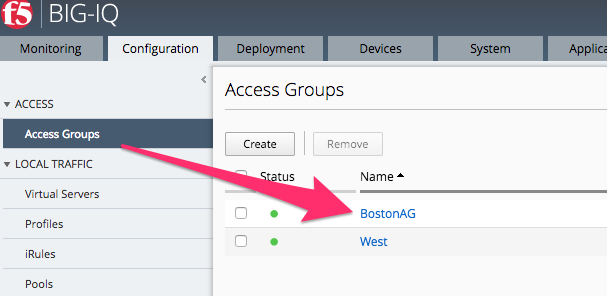
- Navigate to ConfigurationAccessAccess Groups
- Select BostonAG
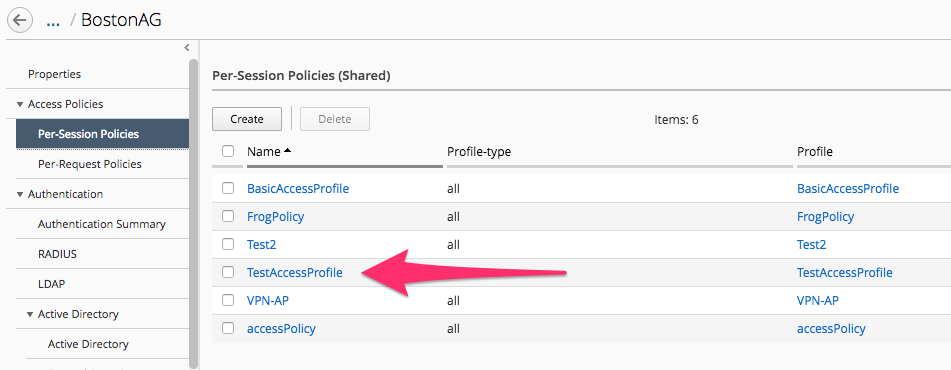
Click on Access Policies -> Per Session Policies:
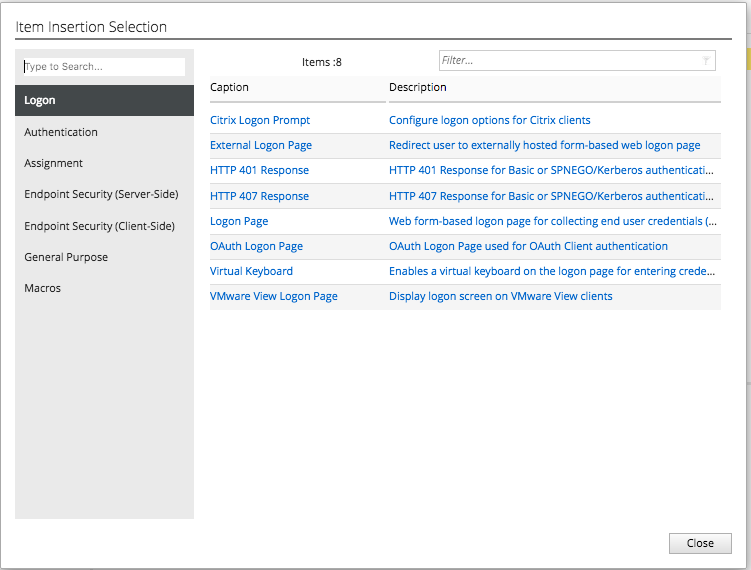
Select TestAccessProfile and add the following objects:
- Login page (accept default settings)
- AD Auth using FrogPolicy-Olympus-AD
- If AD Auth successful, your allowed access
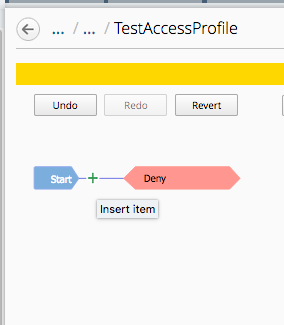
Start by hovering the mouse over the blue line in the policy flow between the Start and Ending points and clicking the Green Plus sign.
Now select the “Login Page” object on the right side of the pop up window. Then click “Save” on the next pop up window.
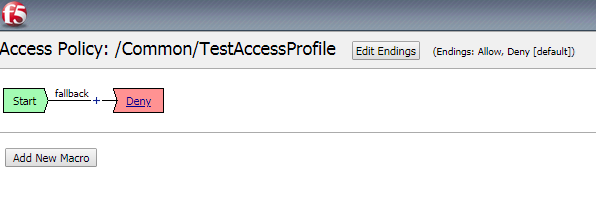
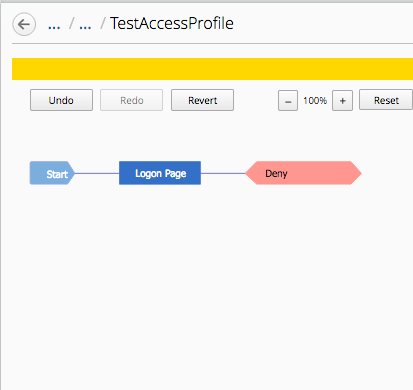
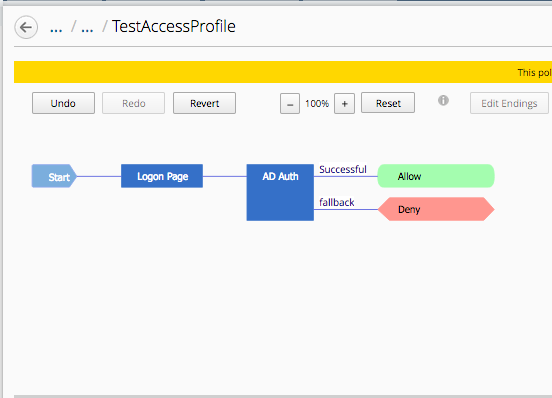
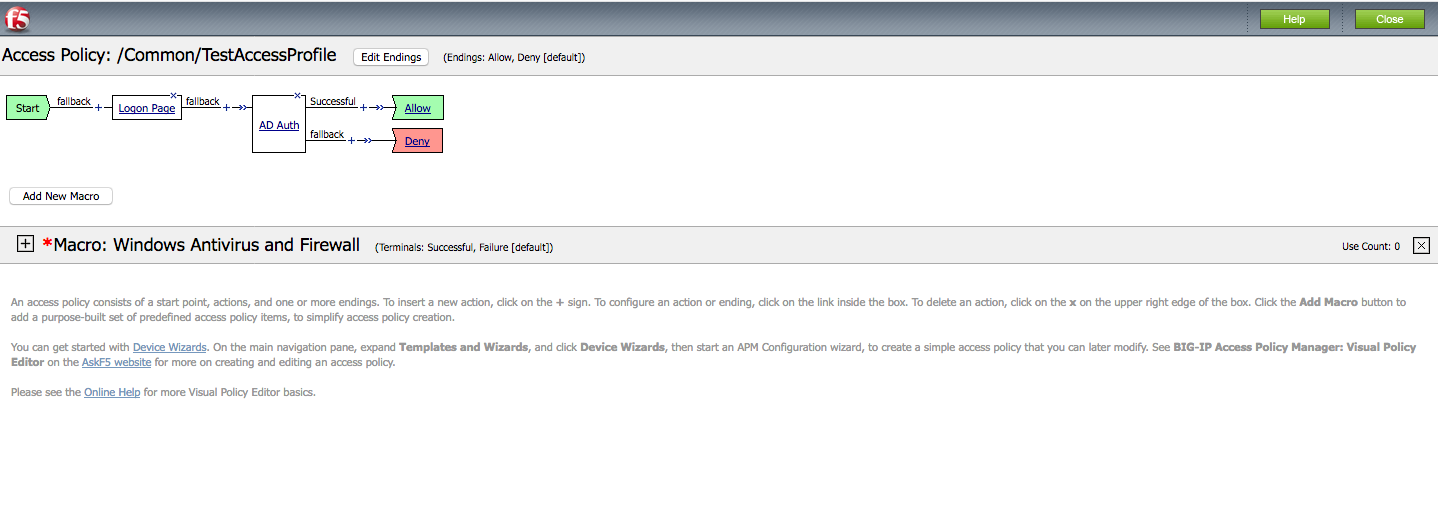
The result should look like the picture below.
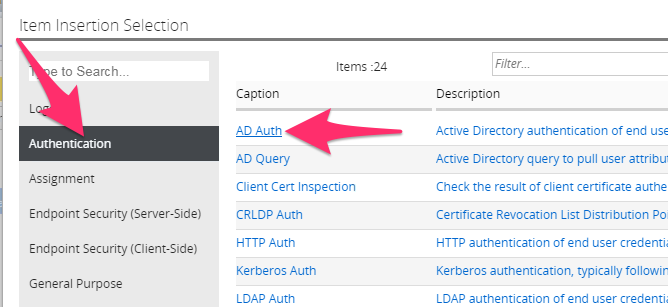
Now repeat the steps by hovering the mouse on the blue line between the Login Page object and the Ending Deny and click the Green plus sign to add the Authentication object of AD Auth.
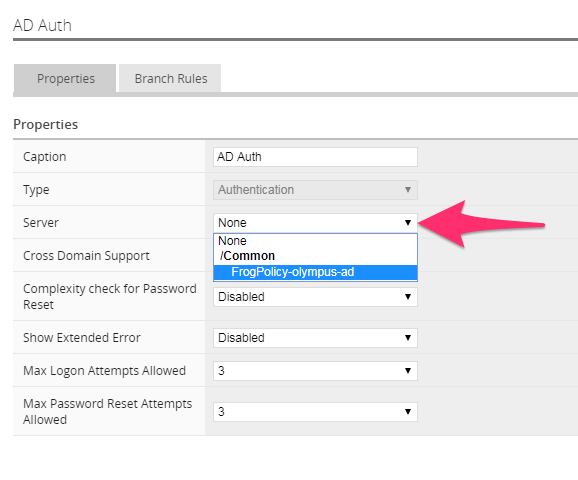
Now click the Server drop down to select FrogPolicy-olympus-ad and then click “Save”.
Change the Ending DENY to ALLOW.
Notice the Yellow Banner warning that there are un-saved changes. Click the Save button at the bottom of the profile page. Click OK on the Policy Save Conformation pop up window.
After modifying the access profile, go to “Deployment tab- > Evaluate & Deploy -> Access”
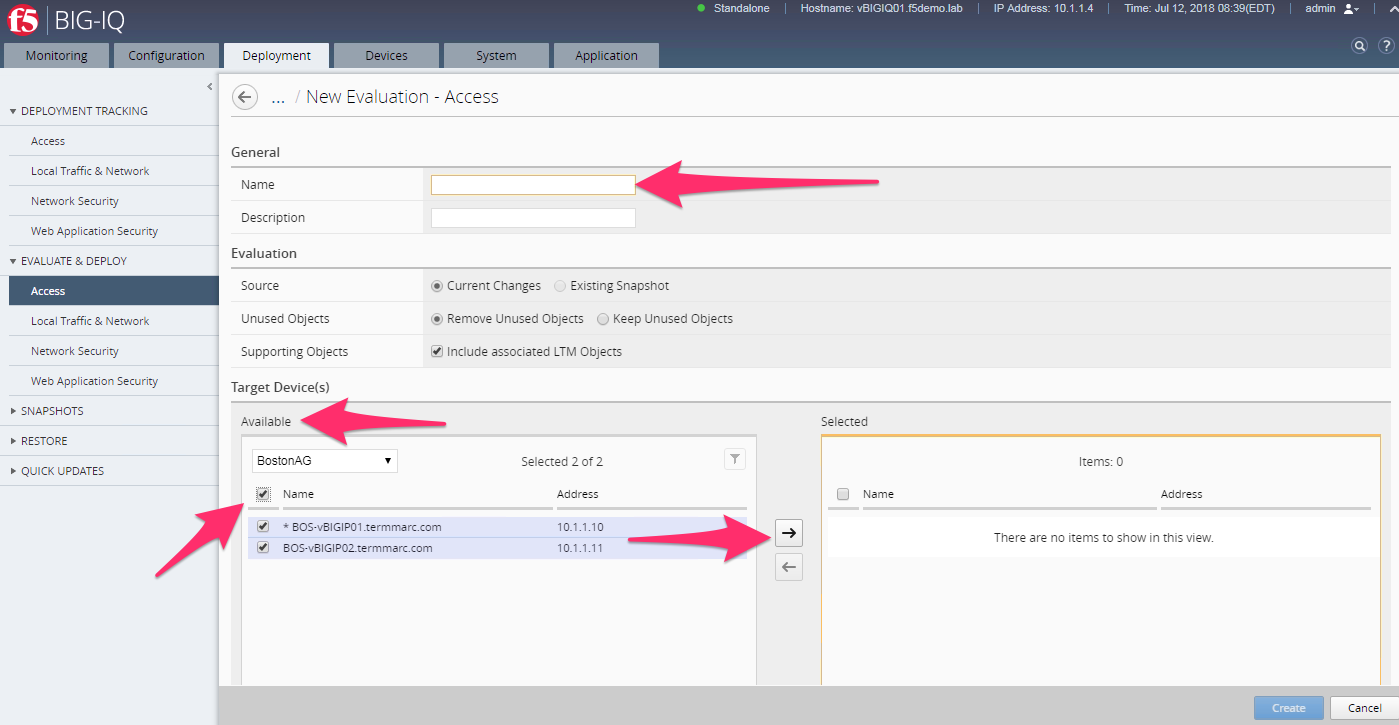
Click on Create in Evaluation section. Enter a name in the Name Field then click the Checkbox in the Available section of Target Devices and Click the arrow to the right to move both BOS BIGIP deivces to the Selected area and then click the Create button at the bottom.
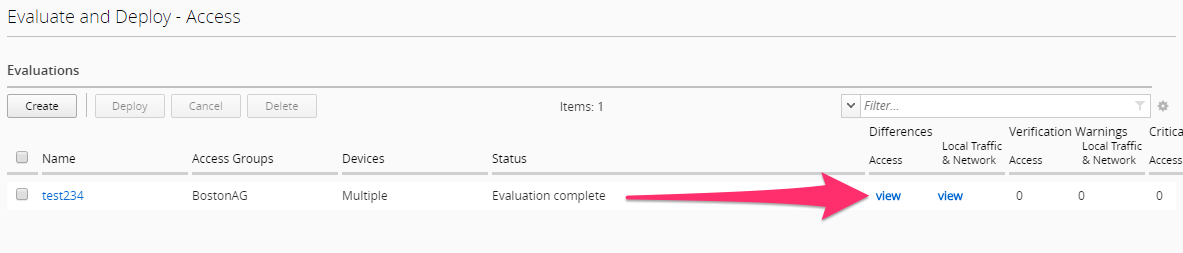
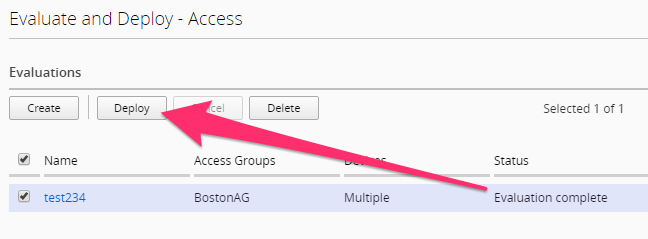
The BIG-IQ will now start evaluating the configurations on the BIG-IP devices and provide a comparison of the changes between the stored configuration within the BIG-IQ versus the current running configurations on the BIG-IP systems. When the evaluation completes you will see a screen like the one below. Click the “VIEW” link under the Access column.
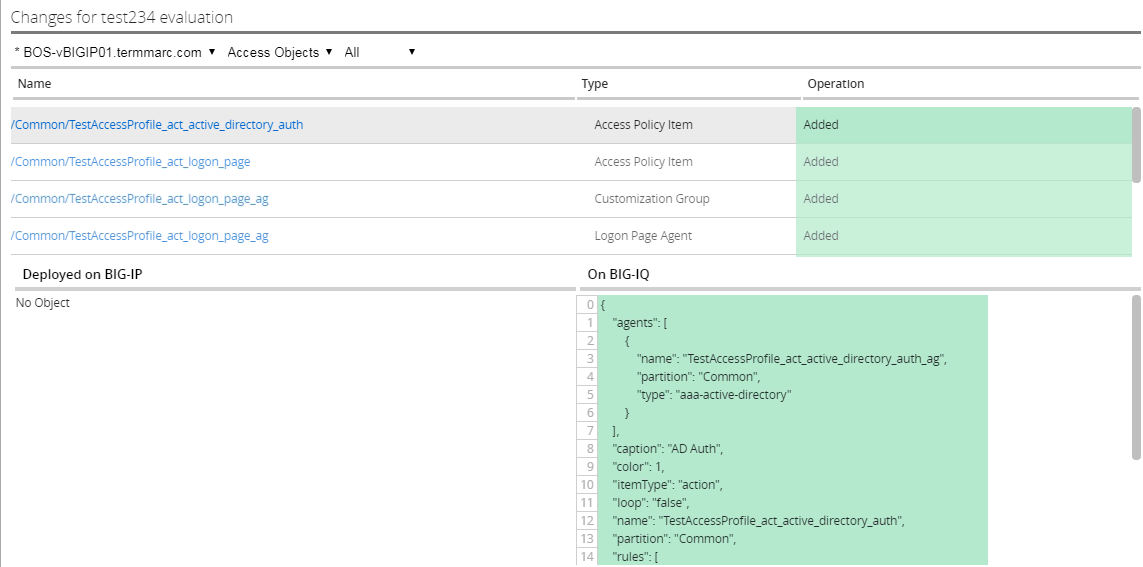
In the evaluation section, you will be able to view the added/changed items. After reviewing click the Cancel button at the bottom of the pop up window.
Now click the Deploy button in the Evaluations section and wait for the Deployment tast to complete.
You can verify on BIG-IP that the access profile changes were pushed: