F5 BIG-IP SSL Orchestrator Training Lab > All SSL Orchestrator Lab Guides > [Archived] SSL Orchestrator v5 (Ravello | 4 hours) > Module 1 - Create a Transparent Forward Proxy SSLO Source | Edit on

Lab 1.11: Summary¶
The summary page presents an expandable list of all of the workflow-configured objects. To expand the details for any given setting, click the corresponding arrow icon on the far right. To edit any given setting, click the corresponding pencil icon. Clicking the pencil icon will send the workflow back to the selected settings page.
- When satisfied with the defined settings, click Deploy.
Upon successfully deploying the configuration, SSL Orchestrator will now display a Dashboard view:
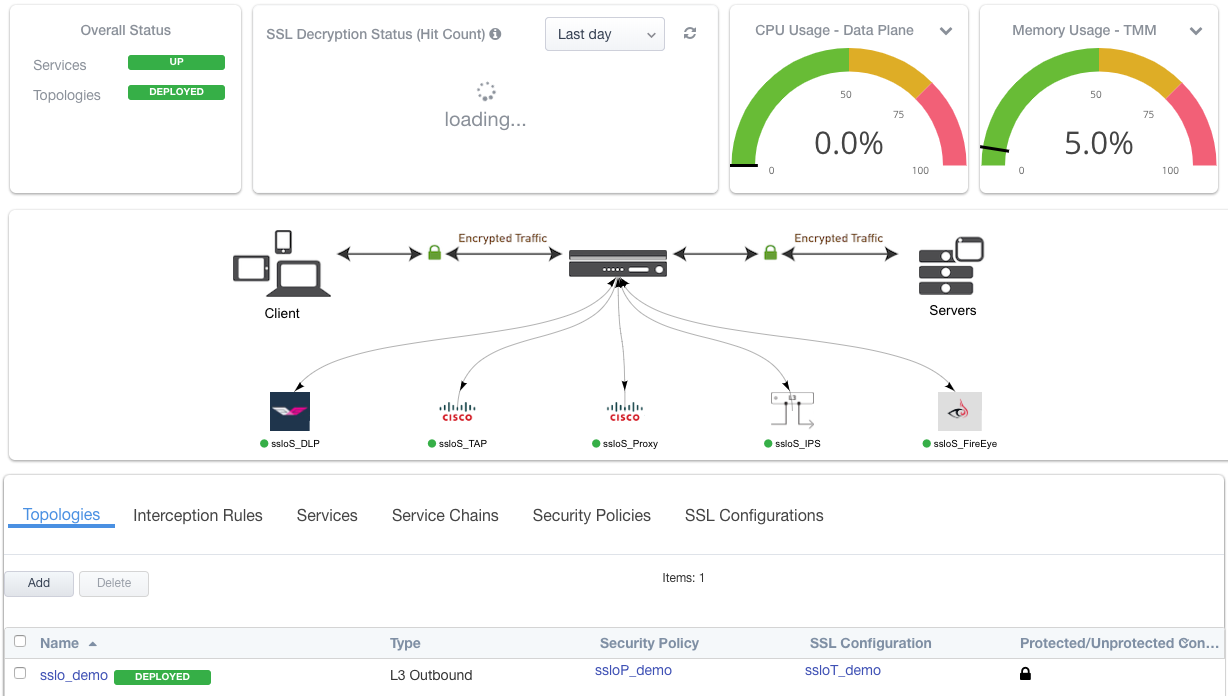
The Interception Rules tab shows the listeners that were created per the selected topology.
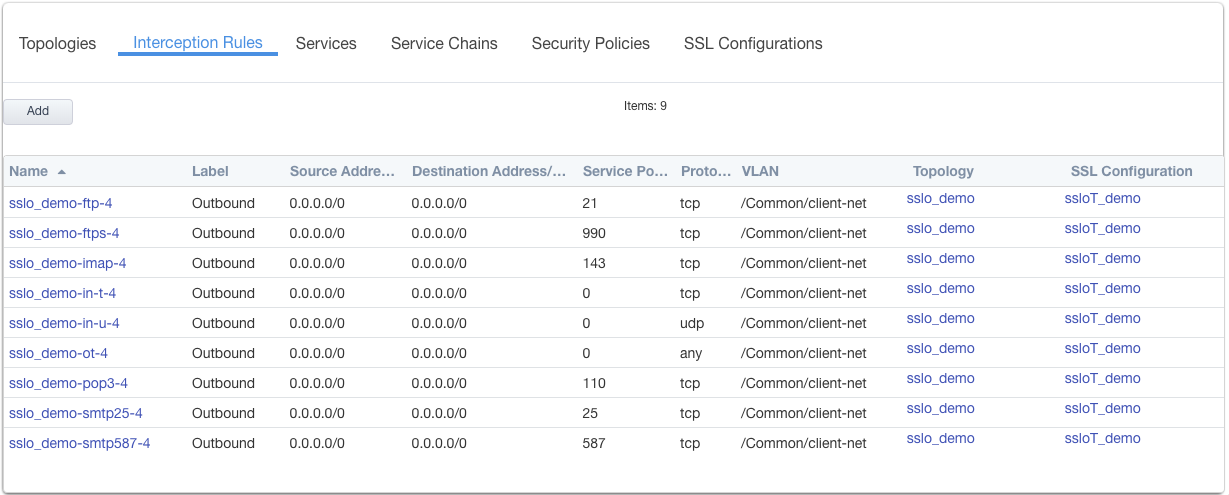
In the above list:
- The -in-t-4 listener defines normal TCP IPv4 traffic.
- The -in-u-4 listener defines normal UDP IPv4 traffic.
- The -ot-4 listener defines normal non-TCP/non-UDP IPv4 traffic.
- The -ftp, -ftps, -pop3, -smtp25, -smtp587 listeners create paths for each respective protocol.
Attention
This completes the configuration of SSL Orchestrator as a transparent forward proxy. At this point an internal client should be able to browse out to external (Internet) resources, and decrypted traffic will flow across the security services.