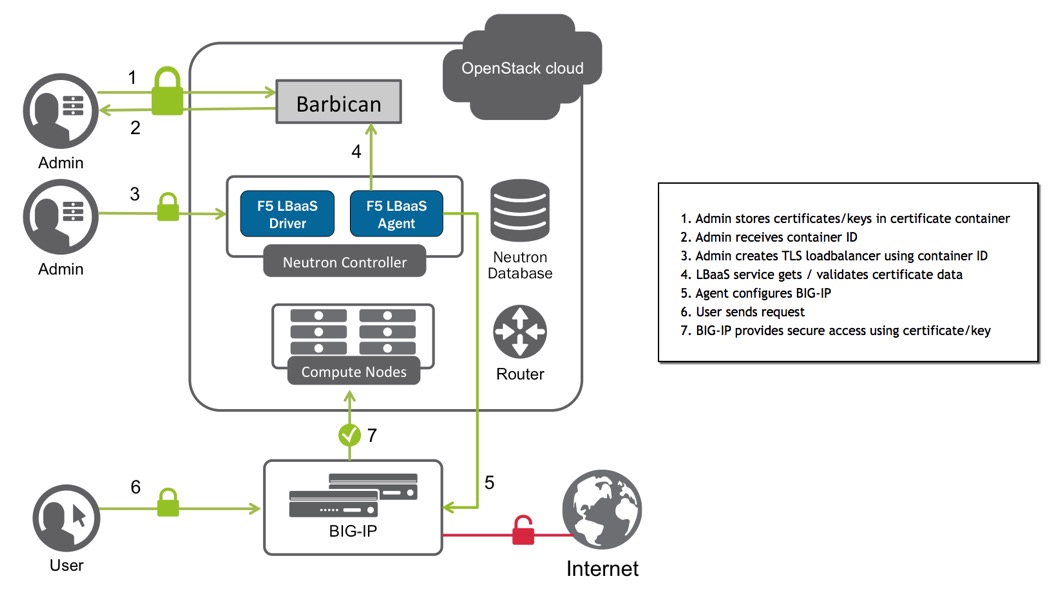
Set up SSL offloading with OpenStack Barbican¶
OpenStack Barbican is OpenStack’s certificate management service. It provides a secure location where users can store secrets such as SSH keys, private keys, certificates, and user passwords. The F5 Agent for OpenStack Neutron can use Barbican certificates to perform BIG-IP SSL offloading.
Prerequisites¶
- Administrator access to both BIG-IP device(s) and OpenStack cloud.
- OpenStack Barbican certificate manager configured and operational.
- Existing BIG-IP SSL profile (optional).
Configure SSL offloading using OpenStack Barbican Secrets¶
Edit the Certificate Manager Settings section of the F5 Agent configuration file.
Enable the F5 Barbican certificate manager.
cert_manager = f5_openstack_agent.lbaasv2.drivers.bigip.barbican_cert.BarbicanCertManager
Provide the Keystone authentication data for your environment.
Keystone authentication data¶ auth_version Keystone version ( v2orv3)os_auth_url Keystone authentication URL os_username OpenStack username os_password OpenStack password os_tenant_name OpenStack tenant name (v2 only) os_user_domain_name OpenStack domain in which the user account resides (v3 only) os_project_name OpenStack project name (v3 only; this is the same data as os_tenant_name in v2) os_project_domain_name OpenStack domain in which the project resides # cert_manager = f5_openstack_agent.lbaasv2.drivers.bigip.barbican_cert.BarbicanCertManager # ... # Keystone v2 authentication: # # auth_version = v2 # os_auth_url = http://localhost:5000/v2.0 # os_username = admin # os_password = changeme # os_tenant_name = admin # # Keystone v3 authentication: # auth_version = v3 os_auth_url = http://localhost:5000/v3 os_username = myusername os_password = mypassword os_user_domain_name = default os_project_name = myproject os_project_domain_name = default #
Set the parent BIG-IP SSL profile.
# f5_parent_ssl_profile = clientssl #
Tip
The profile F5 Agent creates on the BIG-IP device inherit settings from the parent you define. The profile must already existing on the BIG-IP device; if it does not, F5 Agent uses
clientsslas the default parent profile.
Learn more¶
Once you’ve added secrets to a Barbican container, you can reference the container’s URI in neutron lbaas commands.
Use Case¶
When you configure Client SSL or Server SSL profiles and assign them to a virtual server, the BIG-IP device handles the SSL processing. This conserves resources on the destination servers and lets you enforce custom BIG-IP SSL processing rules. When the F5 Agent adds a Barbican certificate to a BIG-IP device, it can either inherit settings from an existing BIG-IP SSL profile or create a new SSL profile on the device.
You can use Client SSL (the most common use case) to decrypt client requests before sending them on to the destination server and encrypt server responses before sending them back to the client.