F5 IPAM Controller¶
Overview of F5 IPAM Controller¶
The F5 IPAM Controller (FIC) is a Docker container that runs in a container environment. It allocates IP addresses from an IPAM system’s address pool for hostnames in an orchestration environment. The F5 IPAM Controller watches orchestration-specific resources and consumes the hostnames within each resource.
IPAM Compatibility Matrix¶
| Resource | Minimum CIS Version Supported |
|---|---|
| Virtual Server CRD | v2.3 |
| Transport Server CRD | v2.4 |
| Service type: Loadbalancer | v2.4 |
| IngressLink CRD | v2.4 |
To see information on the upgrade process for CIS and IPAM releases, see GitHub documentation.
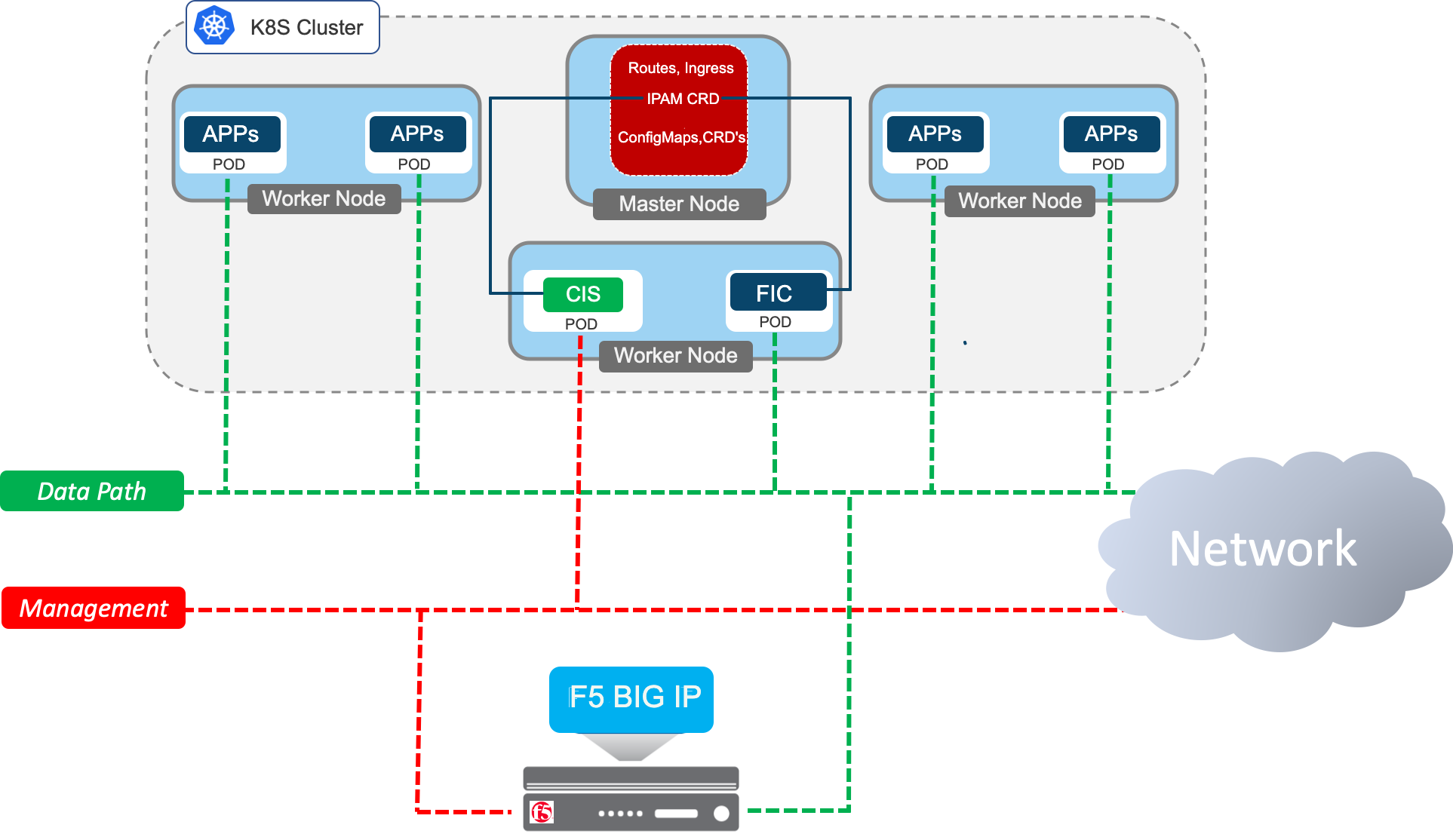
Diagrams¶
This is an architectural diagram of how F5-IPAM-Controller (FIC) fits in the environment:
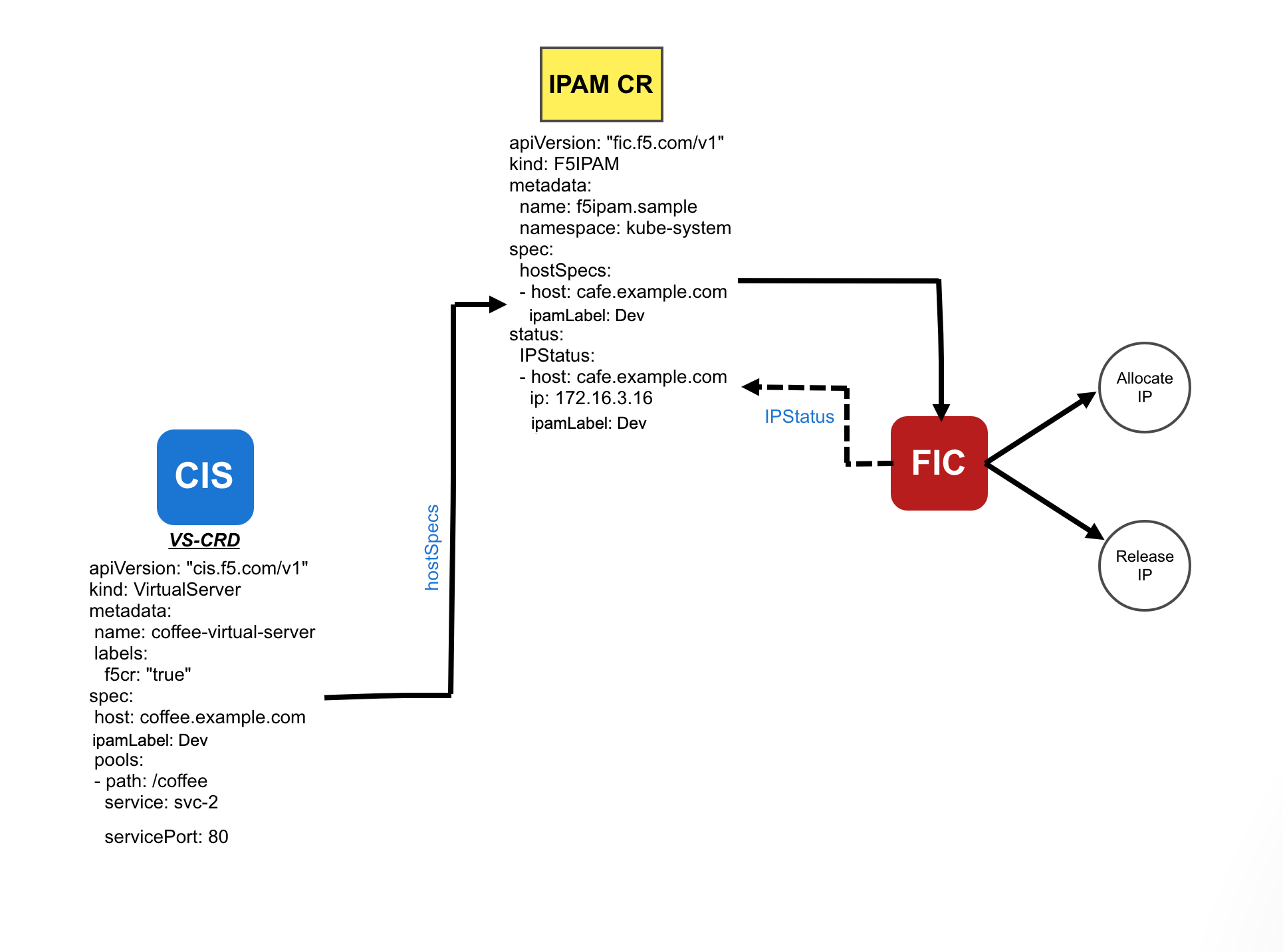
Flow Chart for CIS-FIC:
Note
You must run BIG-IP Container Ingress Services with the options below to interface with FIC.
- Use
--custom-resource-mode=truein your CIS deployment to enable Custom Resource Mode. - Use
--ipam=truein your CIS deployment to interface with FIC. With this parameter set to true, CIS decides if it needs to retrieve an IP address from the IPAM Controller or not.- If a Virtual Server address is specified in the Kubernetes resource, CIS will not leverage the IPAM Controller for IP address even if a CIDR parameter is specified.
- If No Virtual Server address is specified in the Kubernetes resource and the
ipamLabelparameter is specified, CIS will leverage the IPAM Controller for allocation of IP address.
- Limitations when CIS deployed in CRD mode:
- CIS does not watch for Ingress/Routes/ConfigMaps when deployed in CRD Mode.
- CIS does not support the combination of CRDs with any of Ingress/Routes and ConfigMaps.
How to Deploy FIC¶
Configuration Parameters¶
| Parameter | Type | Required | Default | Description |
|---|---|---|---|---|
| orchestration | String | Required | N/A | Holds the orchestration environment. Example: |
| ipam-provider | String | Required | f5-ip-provider | ipam-provider parameter holds the IP provider that holds the ownership of providing IP addresses such as Infoblox, f5-ip-provider. |
| log-level | String | Optional | N/A | Log level parameter specifies various logging levels such as DEBUG, INFO, WARNING, ERROR, CRITICAL. |
Deployment options for Provider f5-ip-provider¶
| Parameter | Type | Required | Default | Description |
|---|---|---|---|---|
| ip-range | String | Required | N/A | The IP address ranges from which FIC creates a pool of IP address range which gets allocated corresponding to the requested resources. Example: Example: |
RBAC for F5 IPAM Controller¶
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 | kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: ipam-ctlr-clusterrole rules: - apiGroups: ["fic.f5.com"] resources: ["f5ipams", "f5ipams/status"] verbs: ["get", "list", "watch", "update", "patch", "create", "delete"] --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: ipam-ctlr-clusterrole-binding namespace: kube-system roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: ipam-ctlr-clusterrole subjects: - apiGroup: "" kind: ServiceAccount name: ipam-ctlr namespace: kube-system --- apiVersion: v1 kind: ServiceAccount metadata: name: ipam-ctlr namespace: kube-system |
Apply this configuration with the following command:
kubectl create -f f5-ipam-rbac.yaml
Note
To provide feedback on Container Ingress Services or this documentation, please file a GitHub Issue.