F5 IPAM Controller and CIS using Infoblox IPAM Integration¶
Overview of Infoblox IPAM Integration¶
The F5 IPAM Controller is deployed in Kubernetes working with CIS to allocate IP addresses from Infoblox network ranges. The F5 IPAM Controller watches orchestration-specific CRD resources and consumes the hostnames within each resource. The F5 IPAM Controller integrates with Infoblox WAPI via the RESTful web API to allocate the virtual server IP addresses as shown below in the diagram.
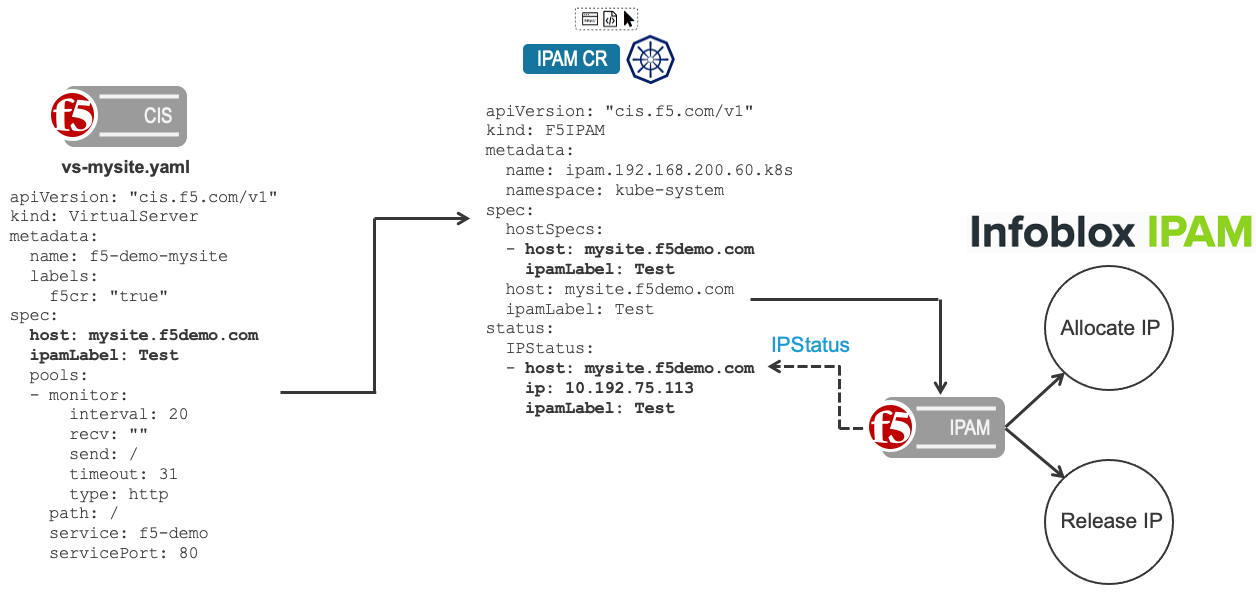
Prerequisites¶
- Recommend AS3 version 3.29
- CIS 2.5
- F5 IPAM Controller
- Read documentation:
Setup options¶
CIS version 2.5 provides two deployment options for using the F5 IPAM controller. You can only use one deployment method per F5 IPAM Controller.
- ip-range - statically specifies the pool of IP address range based on an ipam label when ipam-provider is f5-ip-provider.
- infoblox-labels - Infoblox labels holds the mappings for Infoblox’s netView, dnsView, and CIDR. This option is valid with ipam-provider infoblox.
In this example, we are using the deployment option of Infoblox. In CIS 2.5 the F5 IPAM Controller for Infoblox can:
- allocate IP addresses from Infoblox data management IP address pool based on the
ipamLabelin the Kubernetes CRD. - allocate the IP from the respective IP address pool for the hostname specified in the virtualserver custom resource.
The idea here is that you specify the ip-range label in the virtualserver CRD, or by using Type LB.
Configuration Steps¶
You can watch a demonstration of these steps in this video:
Step 1: CIS Configuration Options for IPAM Deployment defining the CIDR network label in the VirtualServer CRD¶
Add the parameter --ipam=true in the CIS deployment to provide the integration with CIS and IPAM.
args:
- "--bigip-username=$(BIGIP_USERNAME)"
- "--bigip-password=$(BIGIP_PASSWORD)"
- "--bigip-url=192.168.200.60"
- "--bigip-partition=k8s"
- "--namespace=default"
- "--pool-member-type=cluster"
- "--flannel-name=fl-vxlan"
- "--log-level=DEBUG"
- "--insecure=true"
- "--custom-resource-mode=true"
- "--as3-validation=true"
- "--log-as3-response=true"
- "--ipam=true"
Deploy CIS using the following command:
kubectl create -f f5-cluster-deployment.yaml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 | apiVersion: apps/v1 kind: Deployment metadata: name: k8s-bigip-ctlr-deployment namespace: kube-system spec: progressDeadlineSeconds: 600 replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: app: k8s-bigip-ctlr strategy: rollingUpdate: maxSurge: 1 maxUnavailable: 1 type: RollingUpdate template: metadata: annotations: seccomp.security.alpha.kubernetes.io/defaultProfileName: unconfined seccomp.security.alpha.kubernetes.io/pod: unconfined creationTimestamp: ~ labels: app: k8s-bigip-ctlr name: k8s-bigip-ctlr spec: containers: - args: - "--bigip-username=$(BIGIP_USERNAME)" - "--bigip-password=$(BIGIP_PASSWORD)" - "--bigip-url=192.168.200.60" - "--bigip-partition=k8s" - "--namespace=default" - "--pool-member-type=cluster" - "--flannel-name=fl-vxlan" - "--log-level=DEBUG" - "--insecure=true" - "--custom-resource-mode=true" - "--as3-validation=true" - "--log-as3-response=true" - "--ipam=true" command: - /app/bin/k8s-bigip-ctlr env: - name: BIGIP_USERNAME valueFrom: secretKeyRef: key: username name: bigip-login - name: BIGIP_PASSWORD valueFrom: secretKeyRef: key: password name: bigip-login image: "f5networks/k8s-bigip-ctlr:2.5.0" name: f5-server serviceAccountName: k8s-bigip-ctlr |
Step 2: F5 IPAM Deploy Configuration Options¶
Deployment options for ipam-provider infoblox:
| Parameter | Type | Required | Default | Description |
|---|---|---|---|---|
| infoblox-labels | String | Required | N/A | Infoblox labels holds the mappings for Infoblox’s CIDR. |
| infoblox-grid-host | String | Required | N/A | URL (or IP Address) of Infoblox Grid Host. |
| infoblox-wapi-port | String | Optional | 443 | Port that the Infoblox Server listens on. |
| infoblox-wapi-version | String | Required | N/A | Web API version of Infoblox. |
| infoblox-username | String | Required | N/A | Username of Infoblox User. |
| infoblox-password | String | Required | N/A | Password of above given Infoblox User. |
| infoblox-netview | String | Required | N/A | Netview from which IP addresses needs to be allocated. |
| credentials-directory | String | Optional | N/A | Credentials can be mounted from k8s secrets. |
args:
- --orchestration=kubernetes
- --log-level=DEBUG
- --ipam-provider=infoblox
- --infoblox-grid-host=10.192.75.240
- --infoblox-wapi-port="443"
- --infoblox-wapi-version=2.10.5
- --infoblox-username=admin
- --infoblox-password=infoblox
- --infoblox-netview=default
- --infoblox-labels='{"Dev" :{"cidr": "172.16.4.0/24"},"Test" :{"cidr": "172.16.5.0/24"}}'
Deploy RBAC, schema and F5 IPAM Controller deployment:
kubectl create -f f5-ipam-ctlr-clusterrole.yaml
kubectl create -f f5-ipam-deployment.yaml
See examples in this IPAM deployment repository on GitHub.
Logging output when deploying the F5 IPAM Controller¶
$ kubectl logs -f deploy/f5-ipam-controller -n kube-system
[kube@k8s-1-19-master xianfei]$ kubectl logs -f deploy/f5-ipam-controller -n kube-system
2021/07/13 17:39:39 [INFO] [INIT] Starting: F5 IPAM Controller - Version: 0.1.5-WIP, BuildInfo: amkgupta-0382461-dirty-20210712172739
2021/07/13 17:39:39 [DEBUG] Creating IPAM Kubernetes Client
2021/07/13 17:39:39 [DEBUG] [ipam] Creating Informers for Namespace kube-system
2021/07/13 17:39:39 [DEBUG] Created New IPAM Client
2021/07/13 17:39:39 [DEBUG] [MGR] Creating Manager with Provider: infoblox
2021/07/13 17:39:40 [INFO] [CORE] Controller started
2021/07/13 17:39:40 [INFO] Starting IPAMClient Informer
I0713 17:39:40.221163 1 shared_informer.go:240] Waiting for caches to sync for F5 IPAMClient Controller
2021/07/13 17:39:40 [DEBUG] Enqueueing on Create: kube-system/ipam.192.168.200.60.k8s
I0713 17:39:40.322244 1 shared_informer.go:247] Caches are synced for F5 IPAMClient Controller
2021/07/13 17:39:40 [DEBUG] K8S Orchestrator Started
2021/07/13 17:39:40 [DEBUG] Starting Custom Resource Worker
2021/07/13 17:39:40 [DEBUG] Starting Response Worker
Step 3: Configuring CRD to work with F5 IPAM Controller for the following hosts¶
- hostname “mysite.f5demo.com”
- hostname “myapp.f5demo.com”
Provide an ipamLabel in the virtual server CRD. Make sure to create the latest CIS virtualserver schema which supports ipamLabel.
apiVersion: "cis.f5.com/v1"
kind: VirtualServer
metadata:
name: f5-demo-myapp
labels:
f5cr: "true"
spec:
host: myapp.f5demo.com
ipamLabel: Production
pools:
- monitor:
interval: 20
recv: ""
send: /
timeout: 31
type: http
path: /
service: f5-demo
servicePort: 80
and
apiVersion: "cis.f5.com/v1"
kind: VirtualServer
metadata:
name: f5-demo-mysite
labels:
f5cr: "true"
spec:
host: mysite.f5demo.com
ipamLabel: Test
pools:
- monitor:
interval: 20
recv: ""
send: /
timeout: 31
type: http
path: /
service: f5-demo
servicePort: 80
Deploy the CRD and updated schema:
kubectl create -f customresourcedefinitions.yaml
kubectl create -f vs-mysite.yaml
kubectl create -f vs-myapp.yaml
See examples in this CRD repository on GitHub.
Logging output from the VirtualServer¶
myapp.f5demo.com
2021/07/13 17:52:21 [DEBUG] Enqueueing on Update: kube-system/ipam.192.168.200.60.k8s
2021/07/13 17:52:21 [DEBUG] Processing Key: &{0xc0001e6160 0xc0001e7ce0 Update}
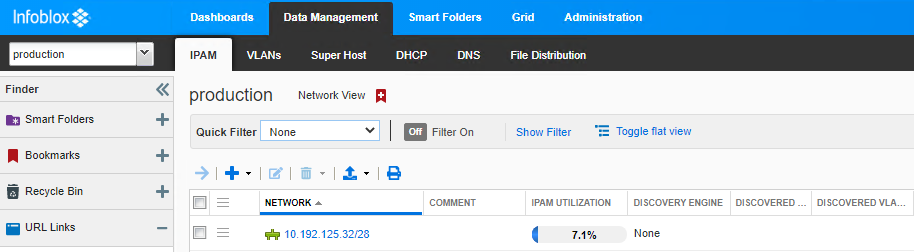
Hostname: myapp.f5demo.com Key: CIDR: 10.192.125.32/28 IPAMLabel: Production IPAddr: Operation: Create
2021/07/13 17:52:21 [DEBUG] [CORE] Allocated IP: 10.192.125.33 for Request:
Hostname: myapp.f5demo.com Key: CIDR: IPAMLabel: Production IPAddr: Operation: Create
2021/07/13 17:52:21 [DEBUG] Updated: kube-system/ipam.192.168.200.60.k8s with Status. With IP: 10.192.125.33 for Request:
Hostname: myapp.f5demo.com Key: CIDR: IPAMLabel: Production IPAddr: 10.192.125.33 Operation: Create
ipamLabel: Production Infoblox setup
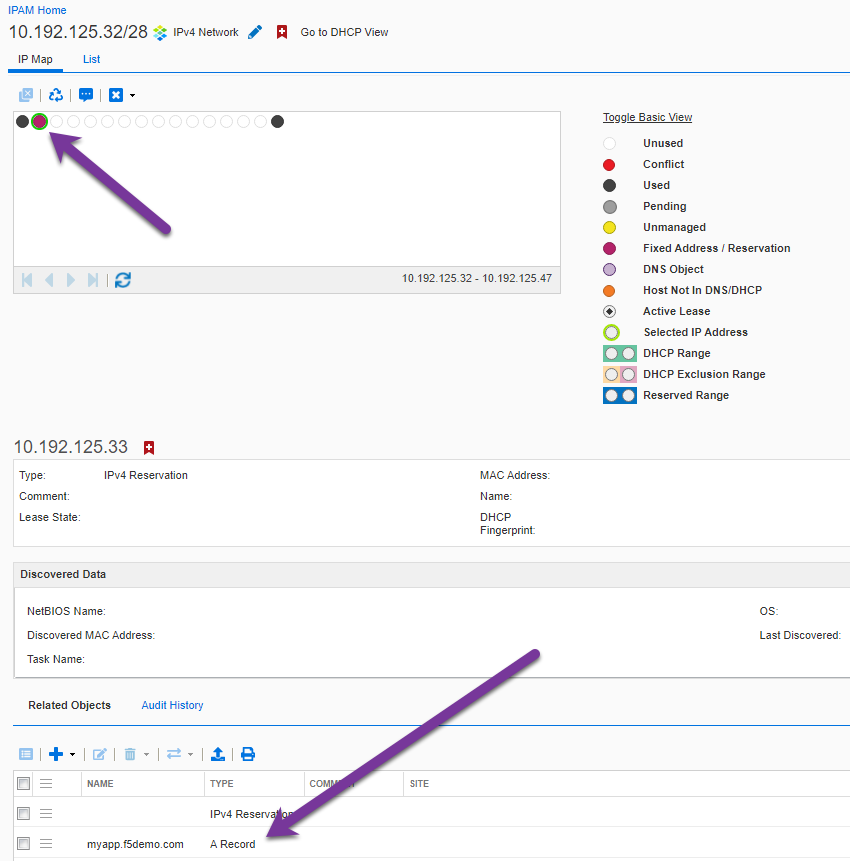
ipam status for CRD
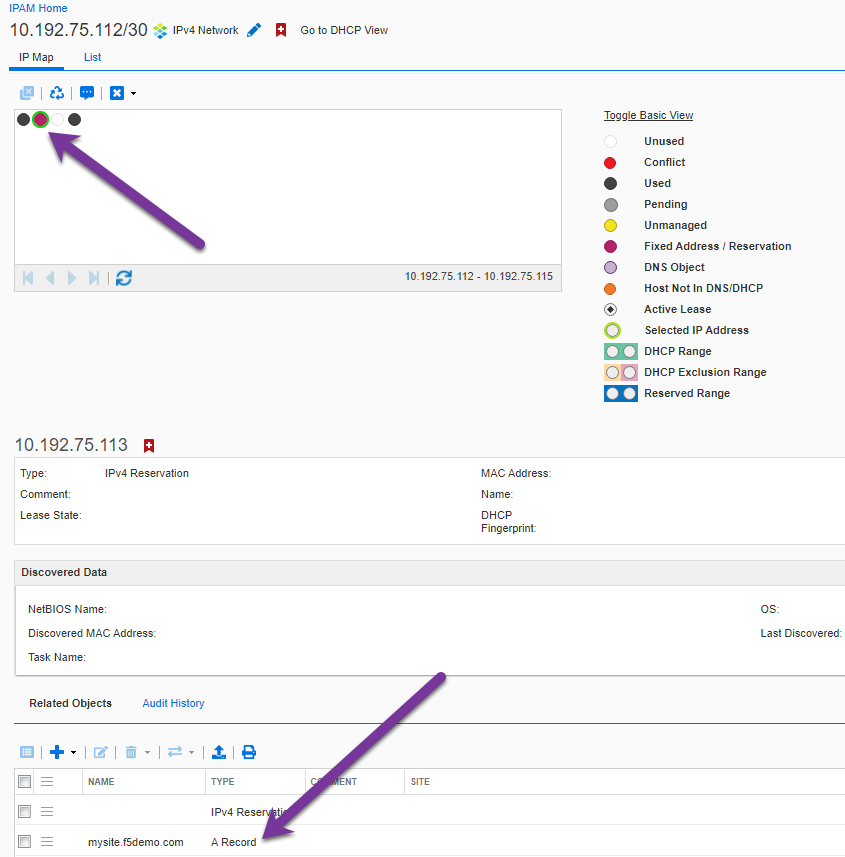
mysite.f5demo.com
2021/07/13 17:41:06 [DEBUG] Enqueueing on Update: kube-system/ipam.192.168.200.60.k8s
2021/07/13 17:41:06 [DEBUG] Processing Key: &{0xc0001e7080 0xc000195340 Update}
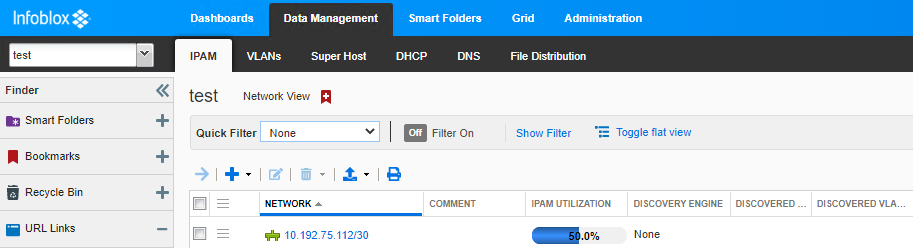
Hostname: mysite.f5demo.com Key: CIDR: 10.192.75.112/30 IPAMLabel: Test IPAddr: Operation: Create
2021/07/13 17:41:07 [DEBUG] [CORE] Allocated IP: 10.192.75.113 for Request:
Hostname: mysite.f5demo.com Key: CIDR: IPAMLabel: Test IPAddr: Operation: Create
2021/07/13 17:41:07 [DEBUG] Updated: kube-system/ipam.192.168.200.60.k8s with Status. With IP: 10.192.75.113 for Request:
Hostname: mysite.f5demo.com Key: CIDR: IPAMLabel: Test IPAddr: 10.192.75.113 Operation: Create
ipamLabel: Test Infoblox setup
ipam status for CRD
Note
To provide feedback on Container Ingress Services or this documentation, please file a GitHub Issue.