NextGen Route Examples¶
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | apiVersion: v1 data: extendedSpec: | extendedRouteSpec: - namespace: tenant1 vserverAddr: 10.8.3.130 vserverName: routetenant1 allowOverride: true bigIpPartition: tenant1 - namespace: tenant2 vserverAddr: 10.8.3.132 vserverName: routetenant2 bigIpPartition: tenant2 kind: ConfigMap metadata: labels: f5nr: "true" name: extended-cm namespace: default |
1 2 3 4 5 6 7 8 9 10 11 12 13 | apiVersion: v1 data: extendedSpec: | extendedRouteSpec: - namespace: tenant1 vserverAddr: 10.8.3.137 vserverName: routetenantoverride kind: ConfigMap metadata: labels: f5nr: "true" name: extended-spec namespace: tenant1 |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | apiVersion: v1 data: extendedSpec: | baseRouteSpec: tlsCipher: tlsVersion: 1.2 ciphers: DEFAULT cipherGroup: /Common/f5-default extendedRouteSpec: - namespace: tenant1 vserverAddr: 10.8.3.130 vserverName: routetenant1 allowOverride: true - namespace: tenant2 vserverAddr: 10.8.3.132 vserverName: routetenant2 kind: ConfigMap metadata: labels: f5nr: "true" name: extended-cm namespace: default |
Note
The label f5nr needs to be set to true on extended ConfigMap to be processed by CIS. The parameters ciphers and cipherGroups are mutually exclusive. cipherGroup is for TLS version 1.3 and ciphers is for TLS version 1.2.
CIS args:
- --extended-spec-configmap
- default/extended-cm
- --controller-mode
- openshift
- --route-label
- systest
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 | apiVersion: apps/v1 kind: Deployment metadata: annotations: labels: name: test-bigip-controller name: test-bigip-controller namespace: kube-system spec: selector: matchLabels: app: test-bigip-controller spec: containers: - args: - --bigip-partition - <partition> - --bigip-url - <ip_address-or-hostname> - --bigip-username - <username> - --bigip-password - <password> - --as3-validation=true - --disable-teems=true - --insecure - --route-label=systest - --extended-spec-configmap - default/extended-cm - --controller-mode - openshift - --openshift-sdn-name - /test/vxlan-tunnel-mp - --pool-member-type - cluster command: - /app/bin/k8s-bigip-ctlr image: f5networks/k8s-bigip-ctlr:latest imagePullPolicy: Always name: test-bigip-controller serviceAccount: bigip-controller serviceAccountName: bigip-controller |
Usecase1: Routes in different namespace¶
Create a route in the tenant1 namespace:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23
apiVersion: route.openshift.io/v1 kind: Route metadata: labels: f5type: systest name: svc-oss-edge-spec-1 namespace: tenant1 spec: host: pytest-oss-edge-spec-1.com path: /tenant1 tls: certificate: | -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- key: | -----BEGIN RSA PRIVATE KEY----- -----END RSA PRIVATE KEY----- termination: edge to: kind: Service name: svc-1 weight: 100 wildcardPolicy: None
Create a route in the tenant2 namespace:
Create a route in the tenant2 namespace¶1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23
apiVersion: route.openshift.io/v1 kind: Route metadata: labels: f5type: systest name: svc-oss-edge-spec-2 namespace: tenant2 spec: host: pytest-oss-edge-spec-2.com path: /tenant2 tls: certificate: | -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- key: | -----BEGIN RSA PRIVATE KEY----- -----END RSA PRIVATE KEY----- termination: edge to: kind: Service name: svc-2 weight: 100 wildcardPolicy: None
CIS Logs:
[AS3] posting request to https://10.145.66.20/mgmt/shared/appsvcs/declare/tenant1,tenant2
[AS3] Response from BIG-IP: code: 200 --- tenant:tenant1 --- message: success
[AS3] Response from BIG-IP: code: 200 --- tenant:tenant2 --- message: success
BIGIP-Config:
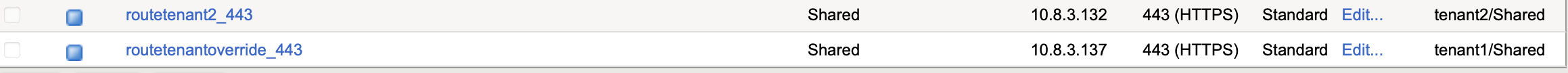
You can observe tenant1 vserverName and vserverAddr are overridden by config provided in namespace based extended ConfigMap.
Usecase2: Routes in same namespace¶
Routes in the same namespace are grouped under a single virtualserver on BIG-IP.
Create routes in tenant1 namespace:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23
apiVersion: route.openshift.io/v1 kind: Route metadata: labels: f5type: systest name: svc-oss-edge-spec-1 namespace: tenant1 spec: host: pytest-oss-edge-spec-1.com path: /tenant1 tls: certificate: | -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- key: | -----BEGIN RSA PRIVATE KEY----- -----END RSA PRIVATE KEY----- termination: edge to: kind: Service name: svc-1 weight: 100 wildcardPolicy: None
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23
apiVersion: route.openshift.io/v1 kind: Route metadata: labels: f5type: systest name: svc-oss-edge-spec-2 namespace: tenant1 spec: host: pytest-oss-edge-spec-2.com path: /test tls: certificate: | -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- key: | -----BEGIN RSA PRIVATE KEY----- -----END RSA PRIVATE KEY----- termination: edge to: kind: Service name: svc-2 weight: 100 wildcardPolicy: None
CIS Logs:
[AS3] posting request to https://10.145.66.20/mgmt/shared/appsvcs/declare/tenant1
[AS3] Response from BIG-IP: code: 200 --- tenant:tenant1 --- message: success
BIGIP-Config:
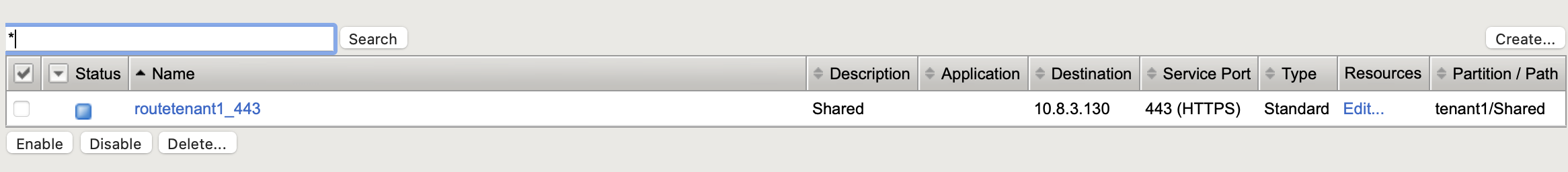
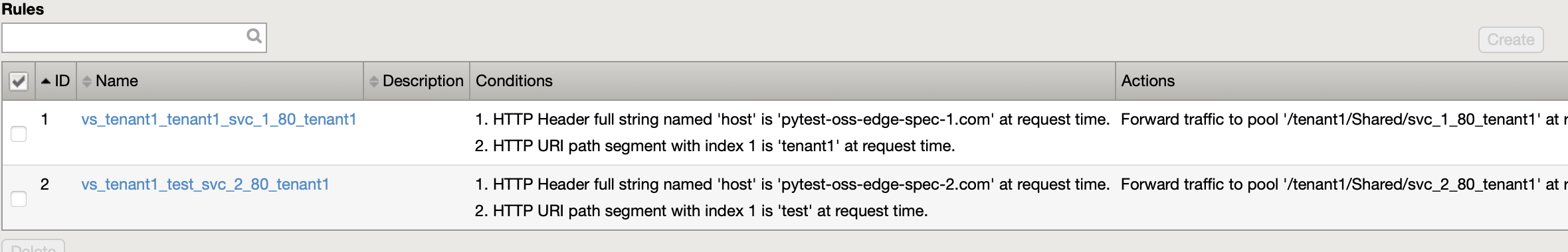
Example extended ConfigMap with namespaceLabel parameter¶
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | apiVersion: v1 data: extendedSpec: | extendedRouteSpec: - namespaceLabel: routegroup=group1 vserverAddr: 10.8.3.130 vserverName: routetenant1 allowOverride: true bigIpPartition: dev - namespaceLabel: routegroup=group2 vserverAddr: 10.8.3.132 vserverName: routetenant2 kind: ConfigMap metadata: labels: f5nr: "true" name: extended-cm namespace: default |
Note
The label f5nr needs to be set to true on extended ConfigMap to be processed by CIS.
Cis args:
- --extended-spec-configmap
- default/extended-cm
- --controller-mode
- openshift
- --namespace-label=environement=dev
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 | apiVersion: apps/v1 kind: Deployment metadata: annotations: labels: name: test-bigip-controller name: test-bigip-controller namespace: kube-system spec: selector: matchLabels: app: test-bigip-controller spec: containers: - args: - --bigip-partition - test - --bigip-url - <ip_address-or-hostname> - --bigip-username - <username> - --bigip-password - <password> - --as3-validation=true - --disable-teems=true - --insecure - --route-label=systest - --extended-spec-configmap - default/extended-cm - --controller-mode - openshift - --openshift-sdn-name - /test/vxlan-tunnel-mp - --pool-member-type - cluster - --namespace-label=environment=dev command: - /app/bin/k8s-bigip-ctlr image: f5networks/k8s-bigip-ctlr:latest imagePullPolicy: Always name: test-bigip-controller serviceAccount: bigip-controller serviceAccountName: bigip-controller |
Label the namespaces:
oc label namespaces foo environment=dev routegroup=group1 --overwrite=true
oc label namespaces bar environment=dev routegroup=group1 --overwrite=true
oc label namespaces gamma environment=dev routegroup=group2 --overwrite=true
oc label namespaces echo environment=dev routegroup=group2 --overwrite=true
- Routes in namespace foo and bar will be mapped into a single group, and a virtual server will be created in the dev partition on BIG-IP.
- Routes in namespace gamma and echo will be grouped together, and a virtual server will be created in test partition in BIG-IP, which is defined in the CIS deployment.
Example GSLB support for routes in AS3 mode¶
CIS supports only AS3 for GTM in NextGen Routes.
Configure CIS args to AS3 agent:
- args: - --bigip-partition - test - --cccl-gtm-agent=false
Create a route with a host in namespace matching the route group:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
apiVersion: route.openshift.io/v1 kind: Route metadata: labels: name: svc1 f5type: systest name: svc1-route-edge namespace: foo spec: host: foo.com path: "/" port: targetPort: 443 tls: certificate: | -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- key: | -----BEGIN PRIVATE KEY----- -----END PRIVATE KEY----- termination: edge to: kind: Service name: svc1
Create an EDNS resource with domain name:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21
apiVersion: "cis.f5.com/v1" kind: ExternalDNS metadata: name: exdns-foo labels: f5cr: "true" spec: domainName: foo.com dnsRecordType: A loadBalanceMethod: round-robin pools: - name: pytest-foo-1.com dnsRecordType: A loadBalanceMethod: round-robin dataServerName: /Common/DC-SL monitor: type: https send: "GET /" recv: "" interval: 10 timeout: 10
Note
- Before creating EDNS resource, you need to have LTM objects on BIG-IP.
- CCCL mode is not supported.
- Like CRDs, all EDNS resources will be created in the default partition on BIG-IP.
Note
To provide feedback on Container Ingress Services or this documentation, please file a GitHub Issue.