F5 BIG-IQ Centralized Management Lab > BIG-IQ Solo Use Cases Source | Edit on
Lab 1.2: Create a self-signed SSL certificate & key on BIG-IQ¶
Note
Estimated time to complete: 10 minutes
Lab environment access¶
If you have not yet visited the page Getting Started, please do so.
SSL Certificate & Key creation on BIG-IQ¶
- Navigate to Configuration > Local Traffic > Certificate Management > Certificates & Keys.
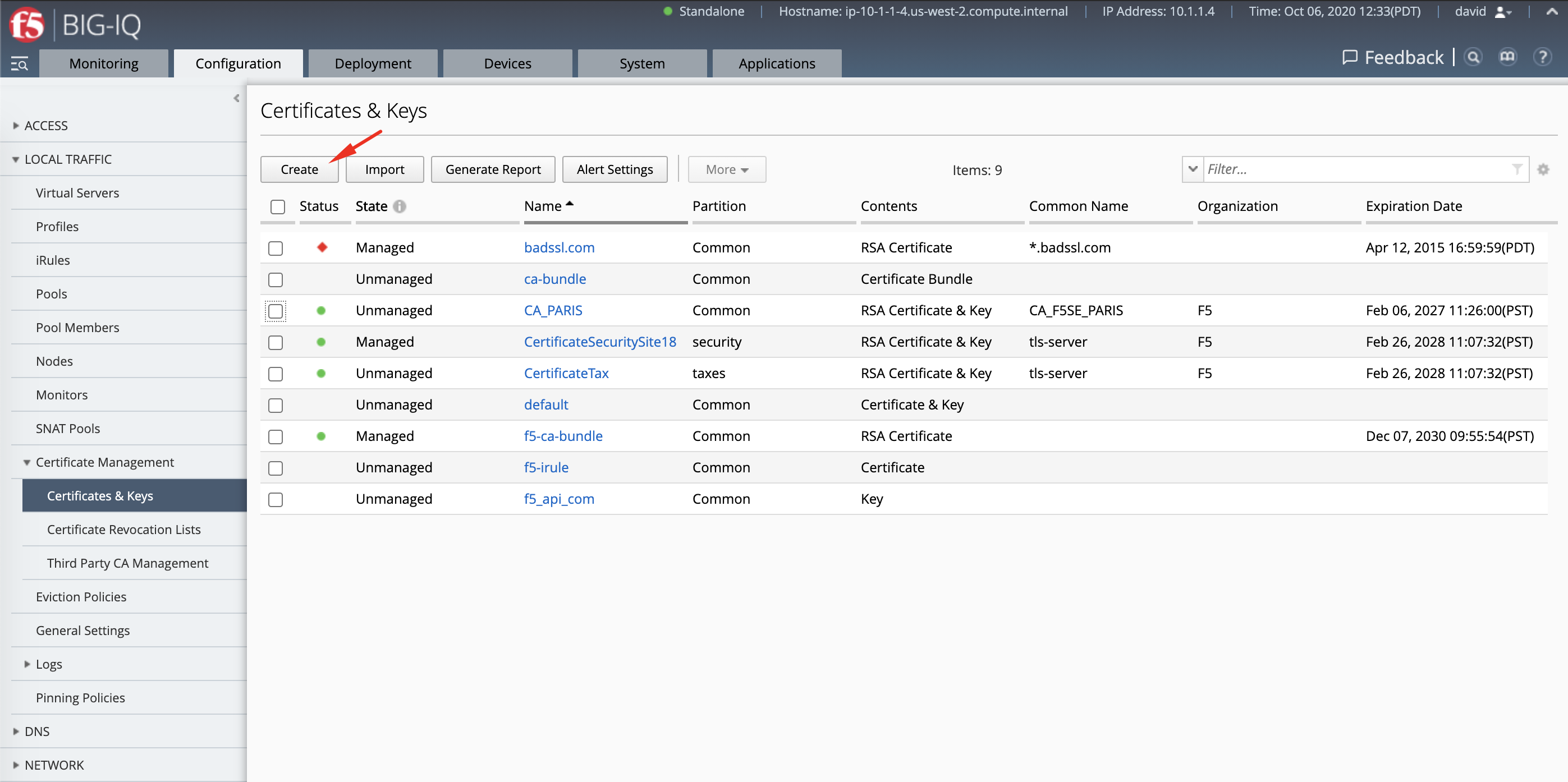
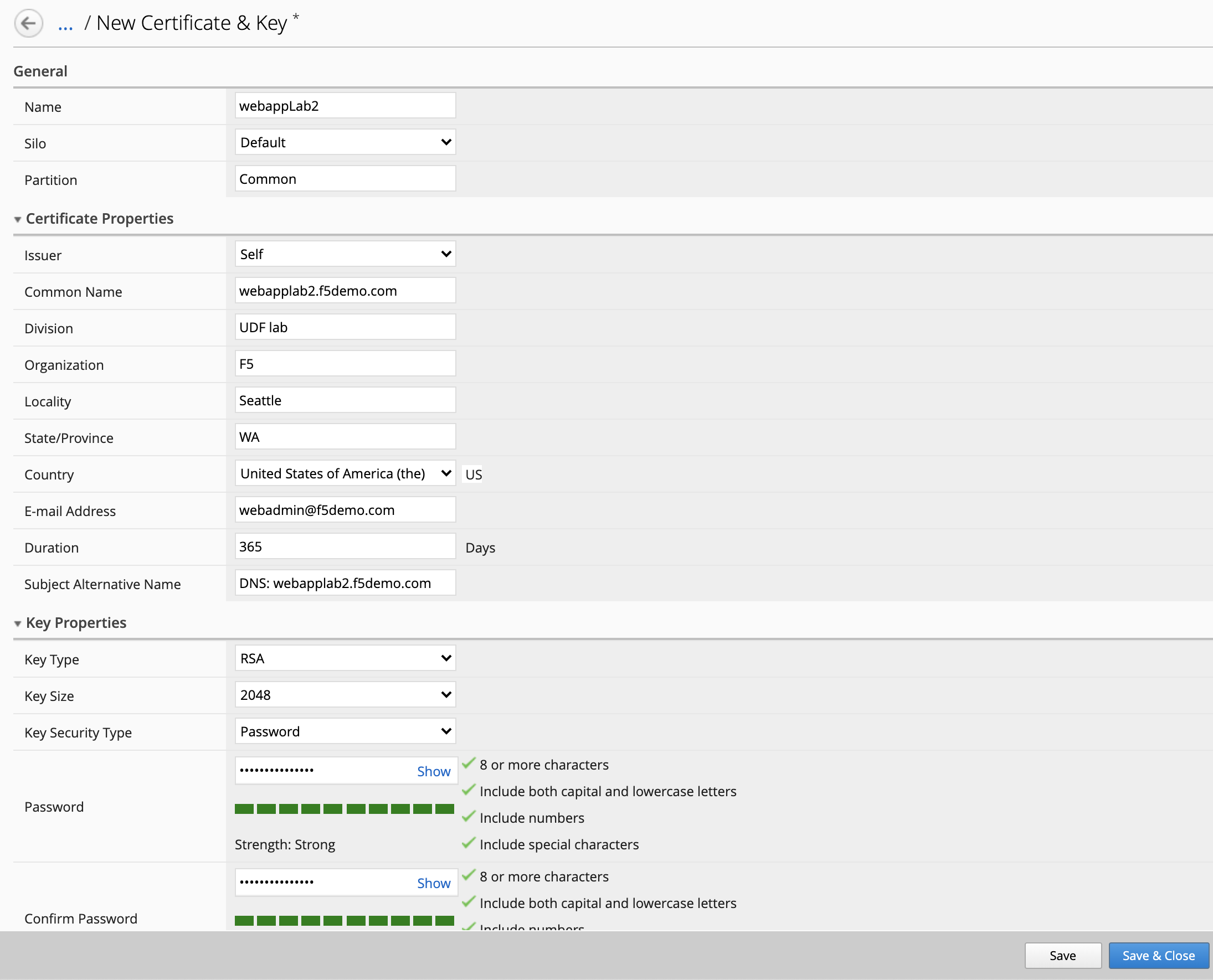
Fill all necessary information and click Create. This will generate a certificate request or CSR along with a Private Key. This CSR will be send to Let’s encrypt server which will sign it and send it back to BIG-IQ.
- Name:
webappLab2 - Issuer:
Self - Common Name:
webapplab2.f5demo.com - Division:
UDF lab - Organization:
F5 - Locality:
Seattle - State/Province:
WA - Country:
US - E-mail Address:
webadmin@f5demo.com - Subject Alternative Name:
DNS: webapplab2.f5demo.com - Key Password:
Password@123456
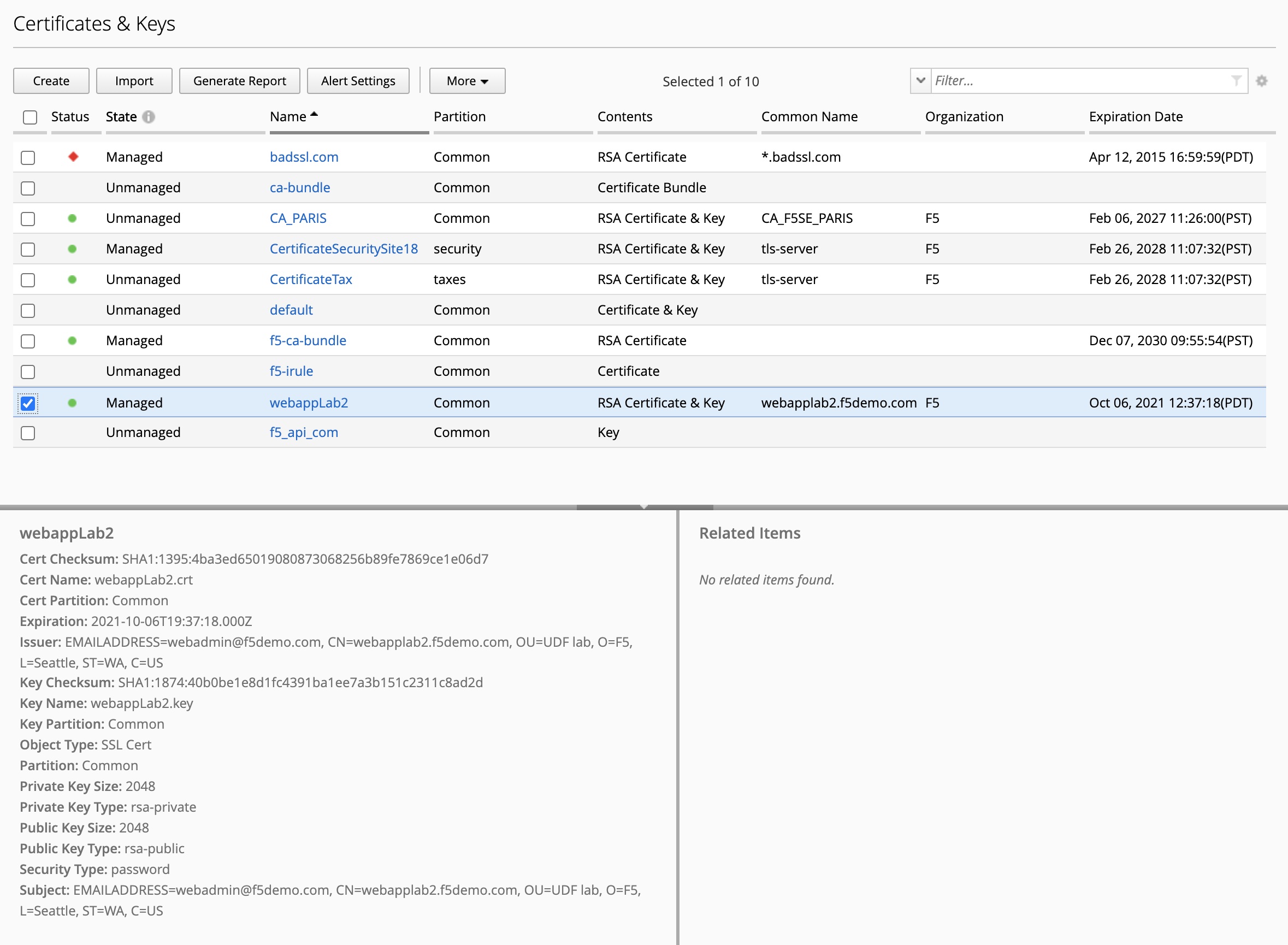
- After the Certificate Request is signed, it will show Managed on the BIG-IQ and ready to be deploy on the BIG-IP.
- Now, let’s pin both certificate and key to a device. Navigate to Pinning Policies under Local Traffic.
Click on SEA-vBIGIP01.termmarc.com device.
Look for the SSL certificate and add it to the device.
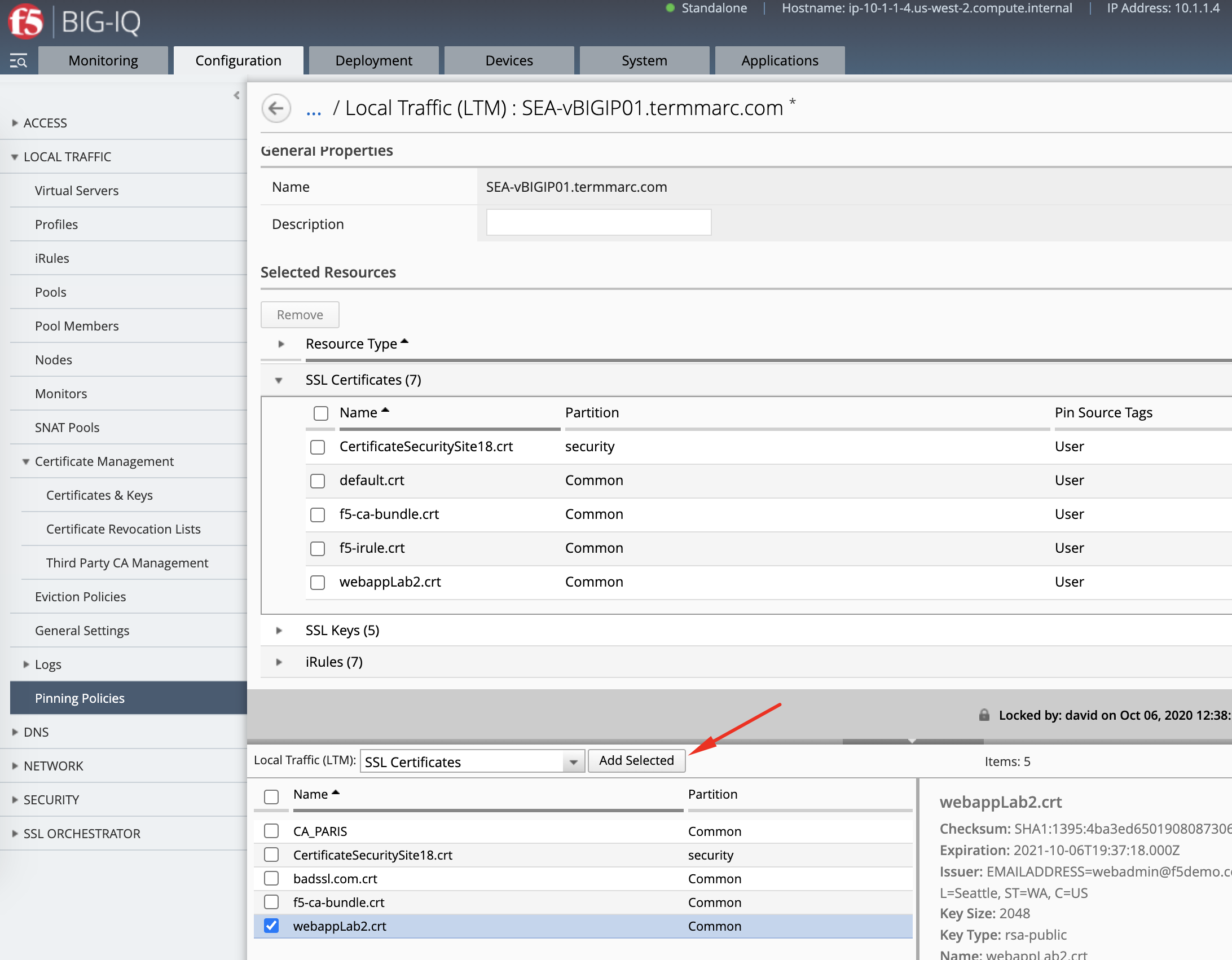
Repeat the same with the SSL Key:
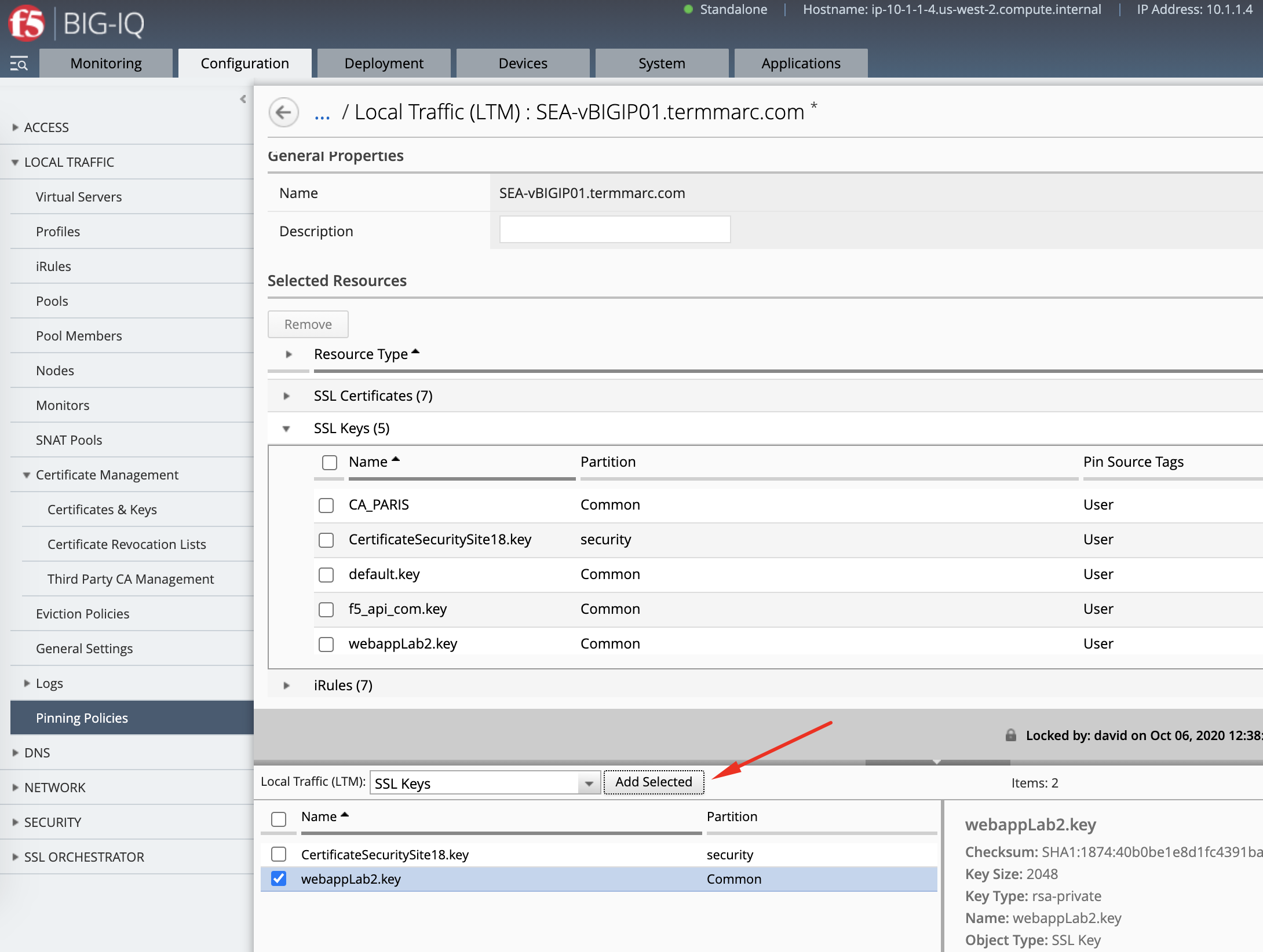
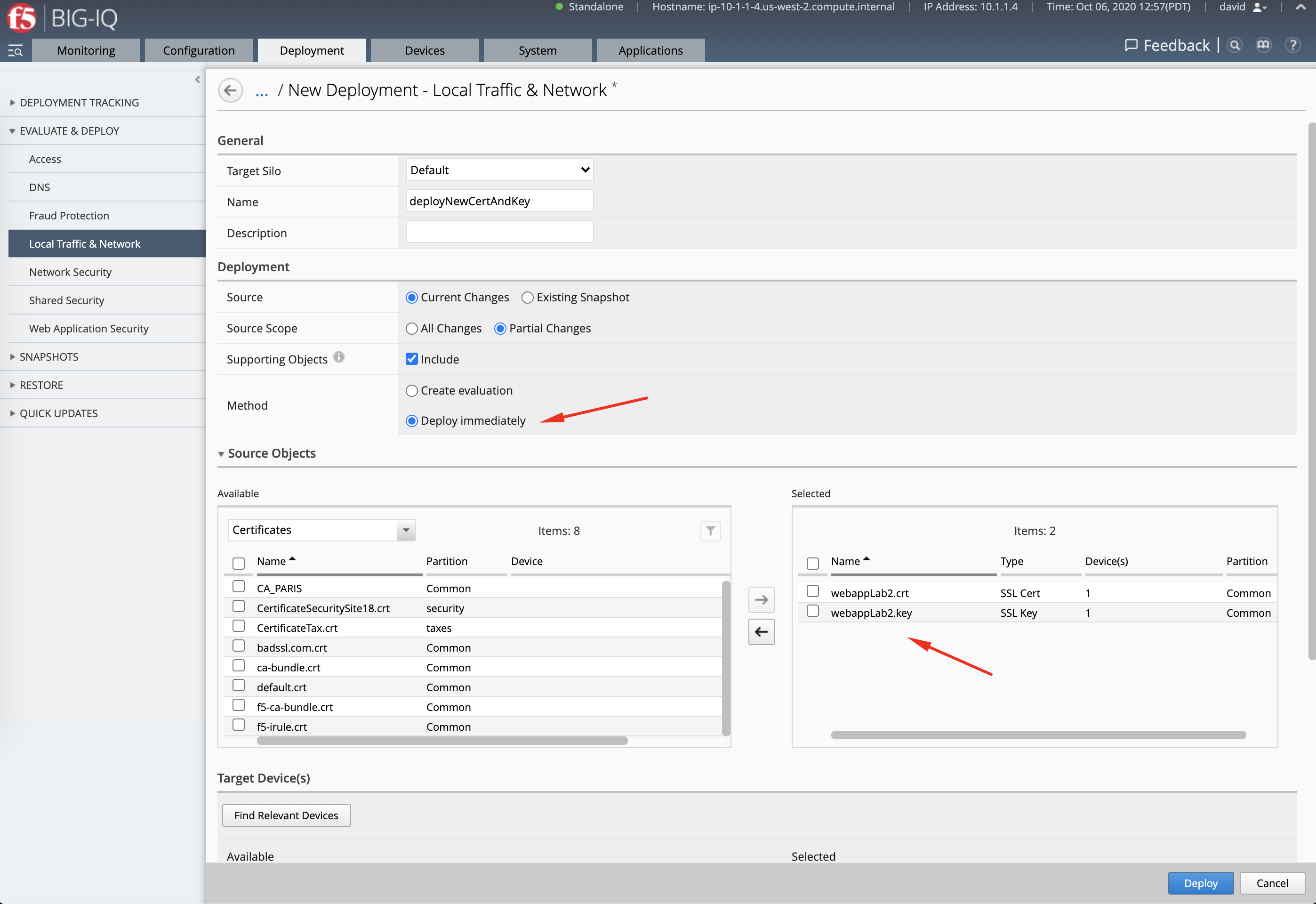
- Deploy the SSL objects to the BIG-IP.
Navigate Deployment > Evaluate & Deploy > Local Traffic & Network.
Create a new deployment:
- Source Scope:
Partial Change - Method:
Deploy Immediately - Source Objects: select both SSL certificate & Key
- Target Device(s):
SEA-vBIGIP01.termmarc.com
Click Deploy.
AS3 HTTPS template with SSL Key Passphrase creation¶
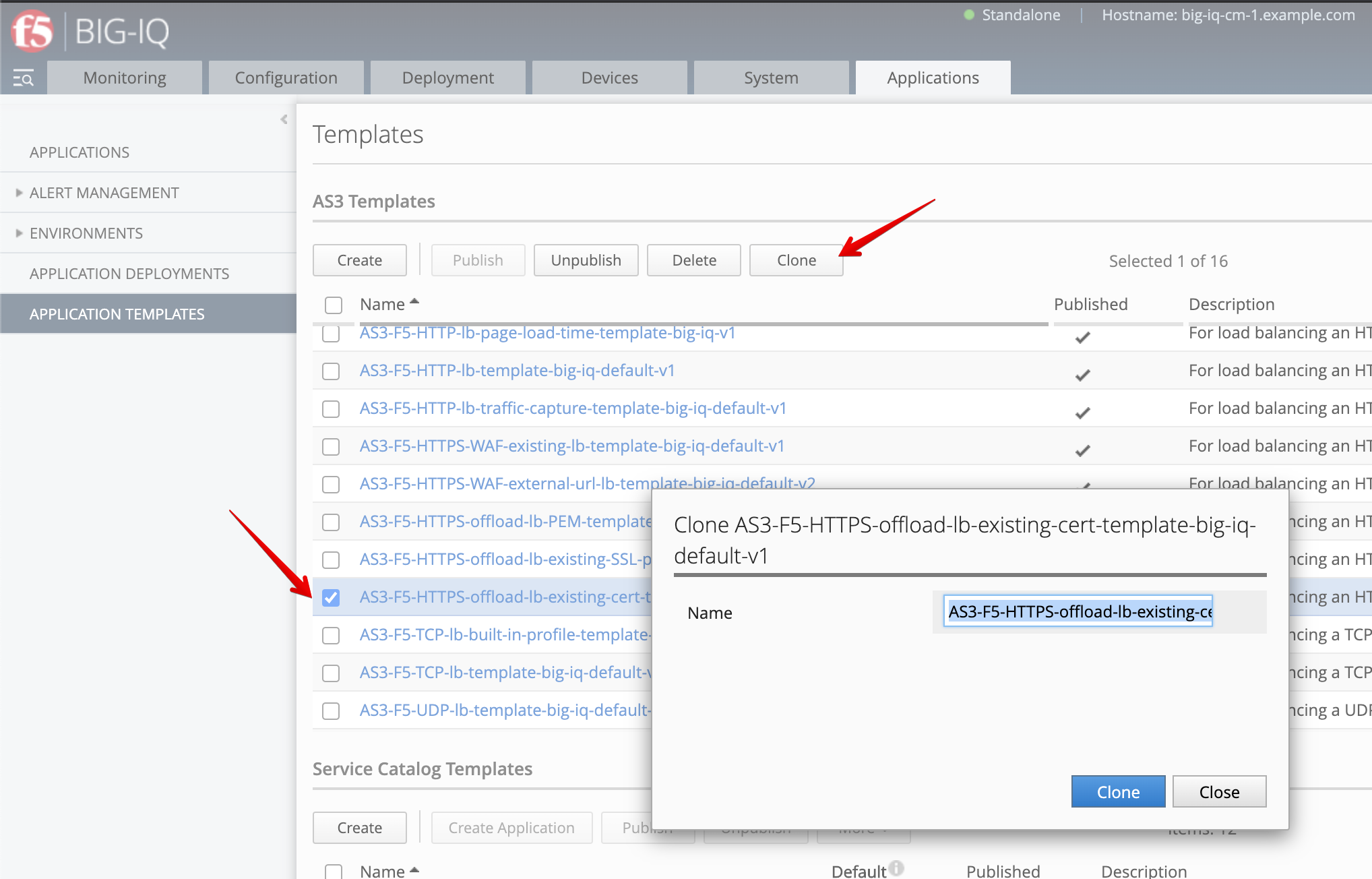
- Go back on BIG-IQ and navigate to the Applications tab > Applications Templates and
select
AS3-F5-HTTPS-offload-lb-existing-cert-template-big-iq-default-<version>and press Clone. - Give the cloned template a name:
AS3-F5-HTTPS-offload-lb-existing-cert-with-passphraseand click Clone.
- Open the new templates created and select the AS3 class
Certificateson the left menu of the AS3 template editor.
Check Editable the 2 following attributes: JOSE header and Ciphertext.
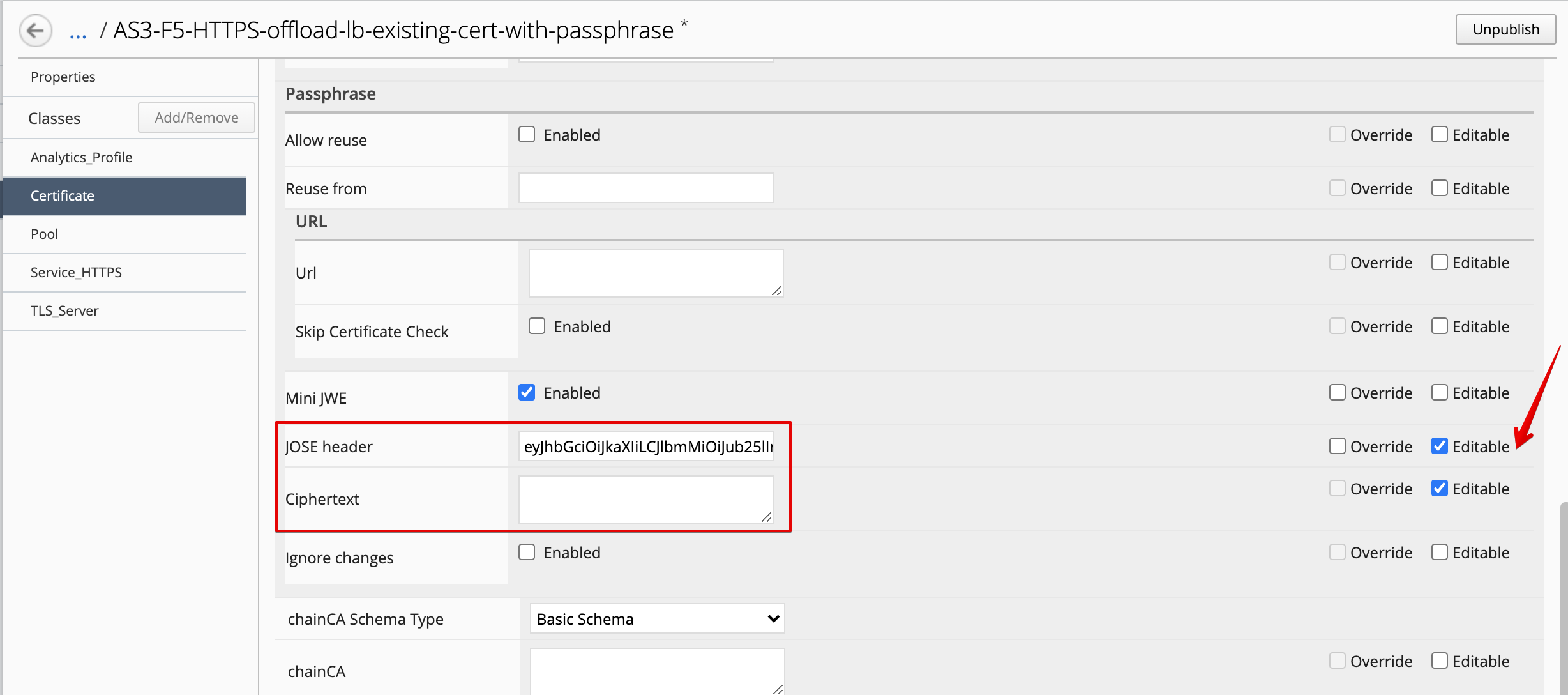
- Save & close the template and publish it so it can be used in the next step.
AS3 HTTPS offload application service creation¶
- Go to the Applications tab > Applications and click Create to create an Application Service:
| Application properties: |
|
| Select an Application Service Template: |
|
| General Properties: |
|
| Analytics_Profile. Keep default. |
| Pool |
|
| TLS_Server. Keep default. |
| Certificate |
|
| Service_HTTPS |
|
Note
In order to get the value of the Ciphertext, we convert the SSL key password (Password@123456) using https://www.url-encode-decode.com/base64-encode-decode/
More details on the AS3 Certificate class here.
- Check the application
LAB_module2has been created along with the application service https_app_service
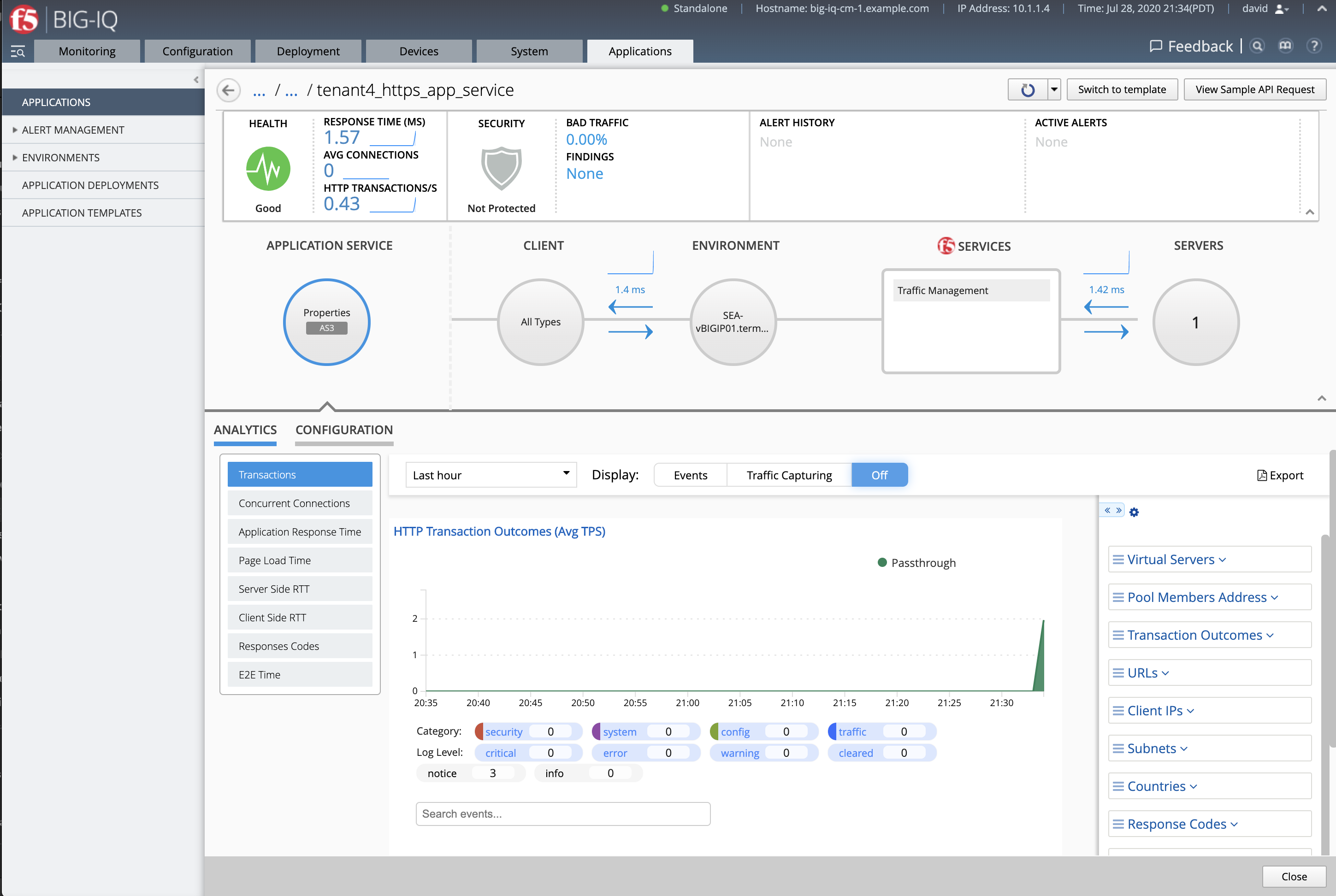
Note
If not visible, refresh the page. It can take few seconds for the application service to appears on the dashboard.
- From the lab environment, launch a remote desktop session to have access to the Ubuntu Desktop.
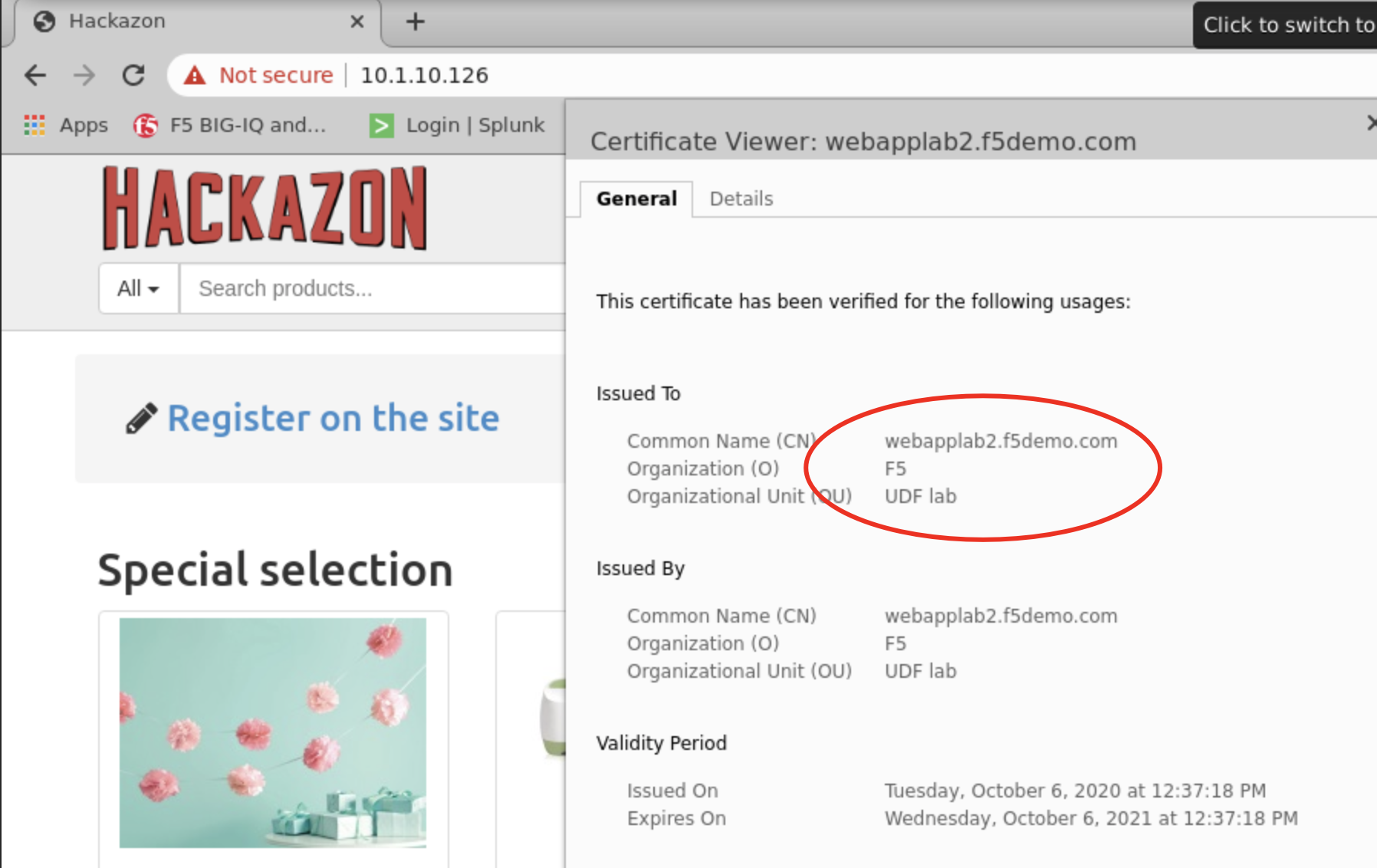
You can test the application service by opening Google Chrome browser on the Ubuntu Jumphost and type the URL https://10.1.10.126.
Note
The certificate shows not secure as we are using a demo Root CA not imported in the browser by default.
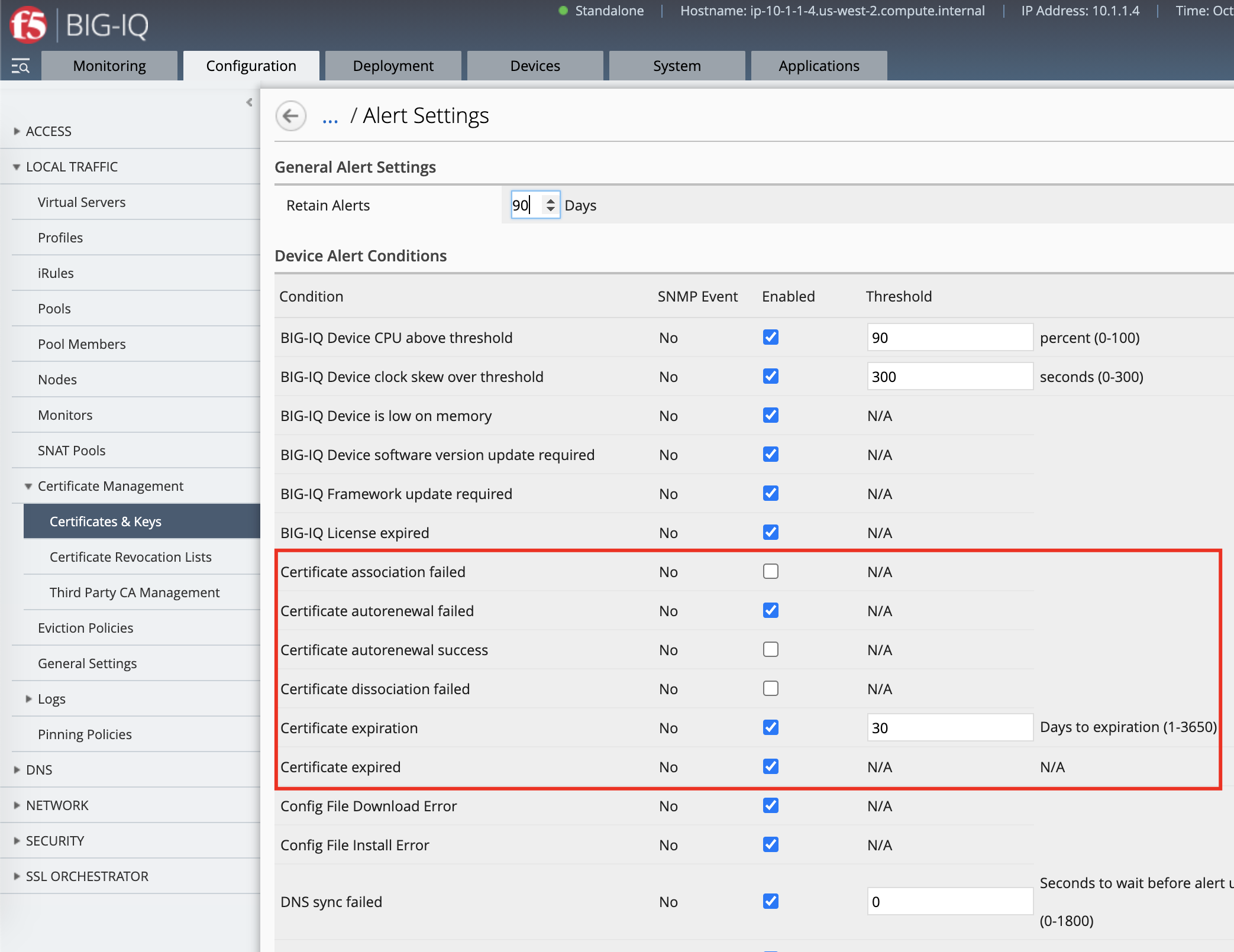
Certificate expiration alerts¶
BIG-IQ also offers the ability to specify alerts for certificate expiration.
Navigate to Configuration > Local Traffic > Certificate Management > Certificates & Keys and click the Alert Settings button to see the alerts options.
Note
Starting with BIG-IQ 8.0, the alert settings now provide up to three scheduled alerts prior to SSL certificates expiration.