Threat Stack Labs > Threatstack 301: Advanced Cloud Workload Protection Source | Edit on
ThreatML¶
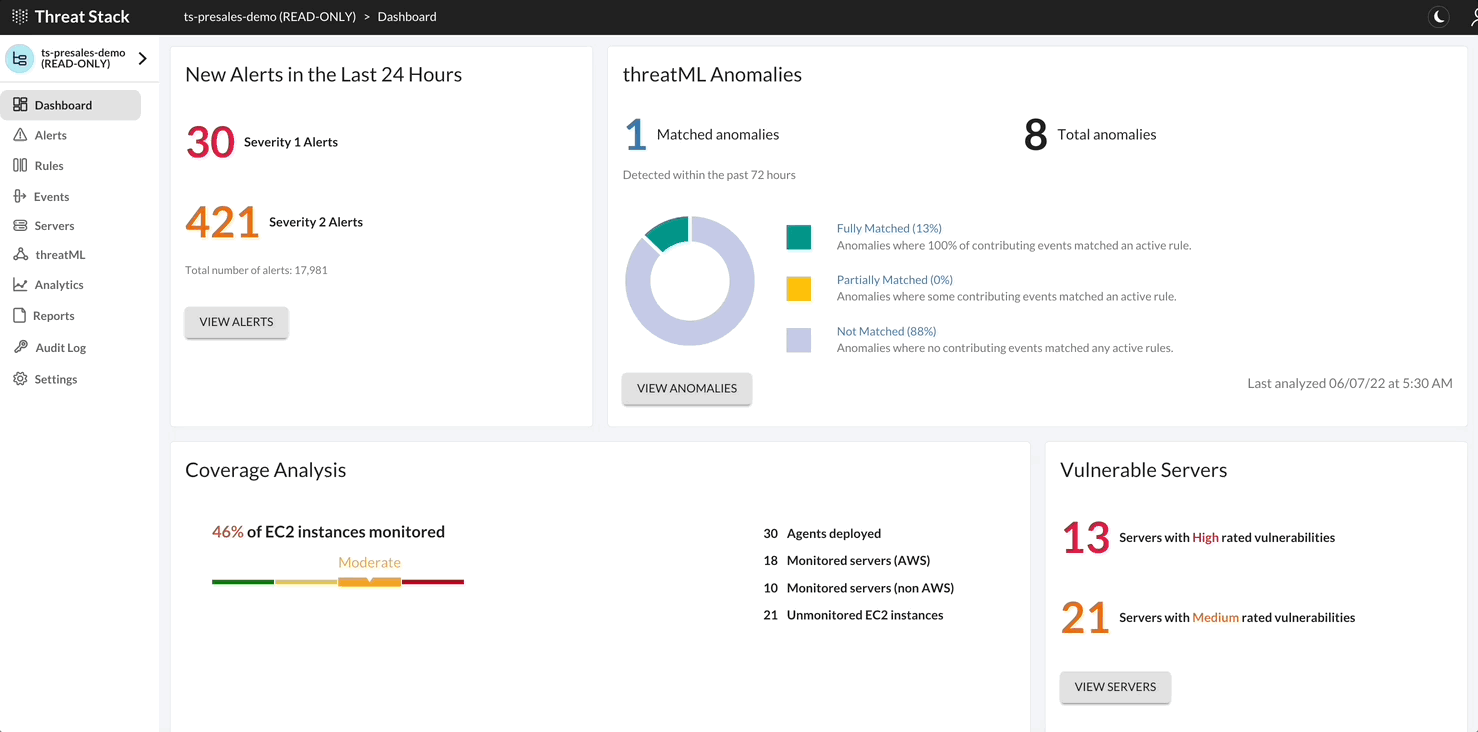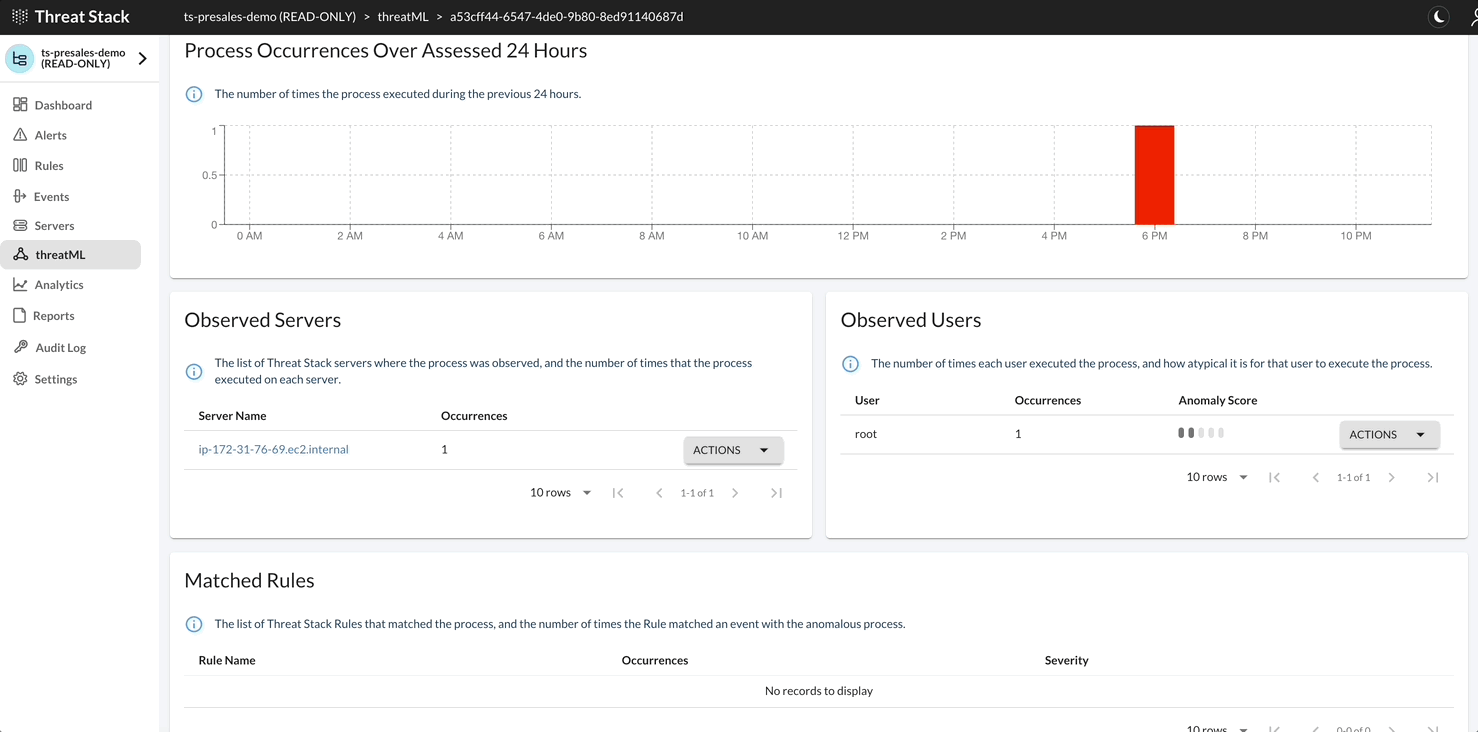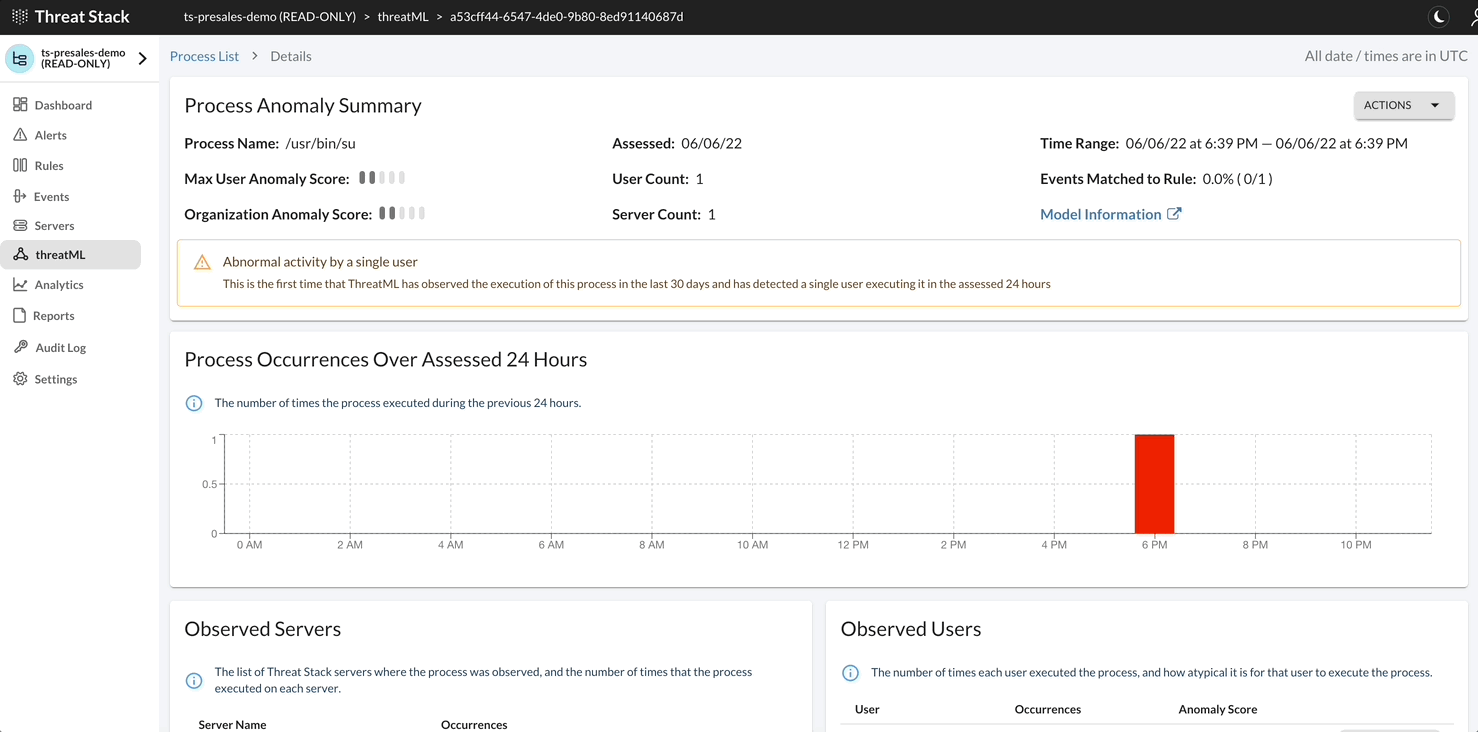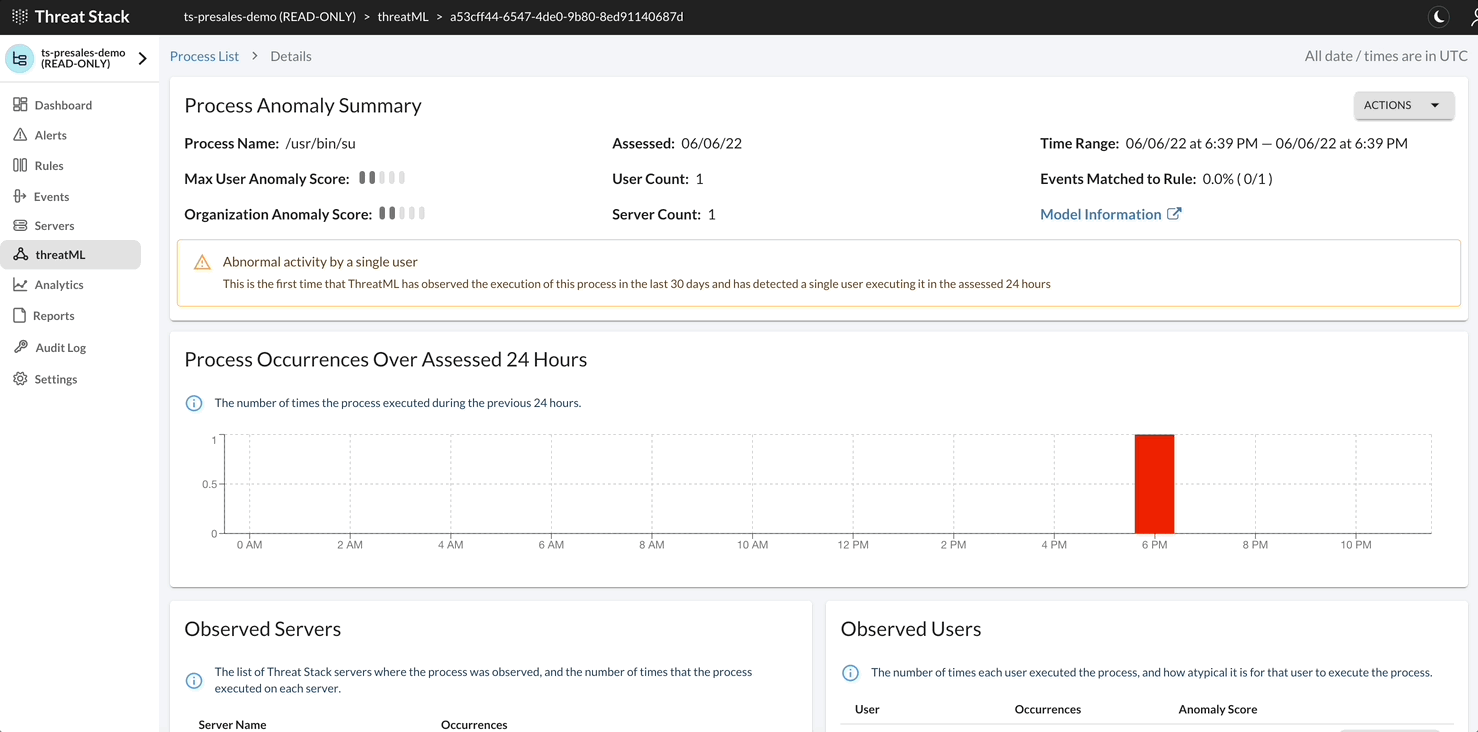
Threat Stack with ThreatML predicts the behavior of your infrastructure through two different data models. These data models collect 30 days of specific information from your infrastructure to create a baseline of normal, predictable behavior.
After ThreatML establishes a baseline, once per day it compares your baseline to your current infrastructure and reports any behavior that deviates from the models’ predictions as anomalous.
Attention
Challenge 1 – Review Anomalies
- Navigate to the Threat Stack Cloud Security Platform: https://app.threatstack.com/login
- In the Email field, type StudentN@dadismad.com as the email address and click Next.
- In the Password field, type xxxxxxx as the password and click Next.
- Select threatML in the navigation bar or View Anomalies from the Dashboard
Note
Access to the Threat Stack Cloud Security Platform® is managed by the Lab Members.