Threat Stack Labs > Threatstack 301: Advanced Cloud Workload Protection Source | Edit on
Threat Stack Playbooks - Part 3¶
Self-Protecting Cloud - Part 3¶
Setup Python Bot¶
The following series of commands are intended to configure the python bot to communicate with the Threat Stack API. The python bot can be found in the home directory of the Linux host.
Step 1: Download & Unzip Python-Bot
Step 2: Update Threat Stack Credentials File
Launch Python Bot¶
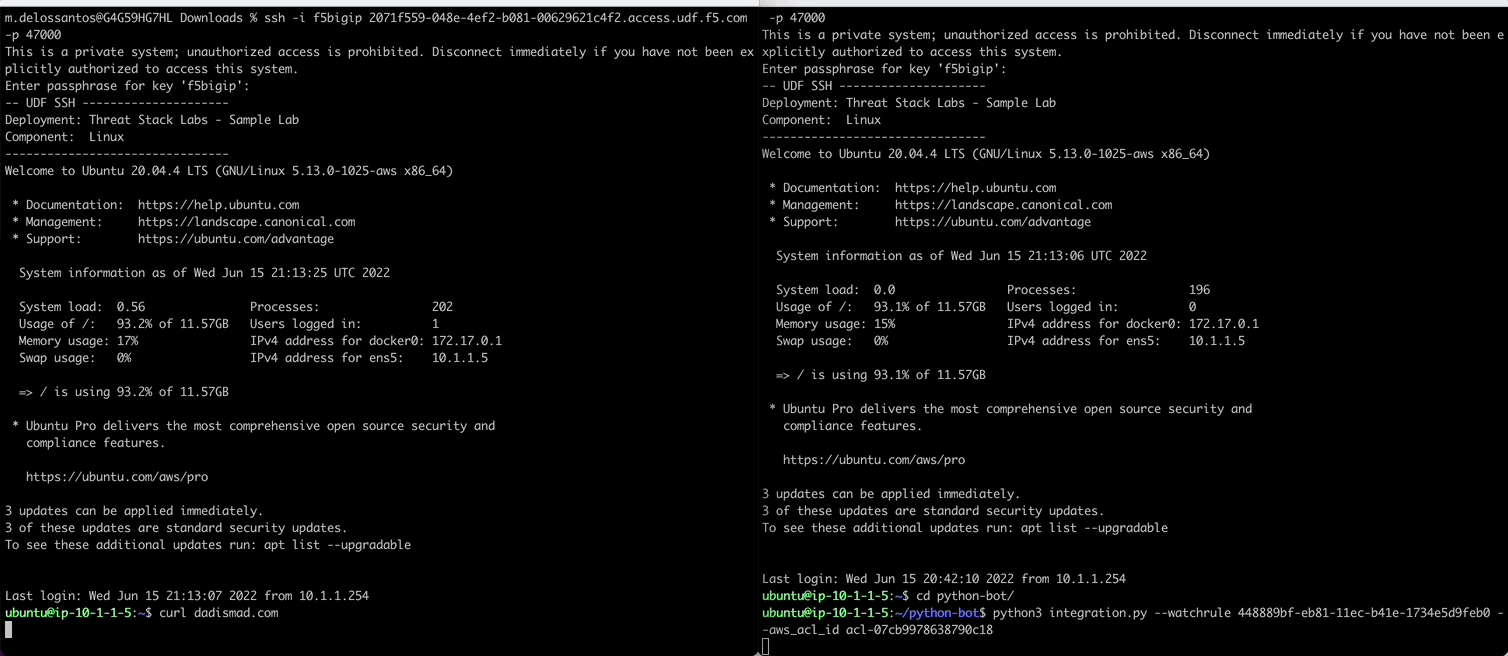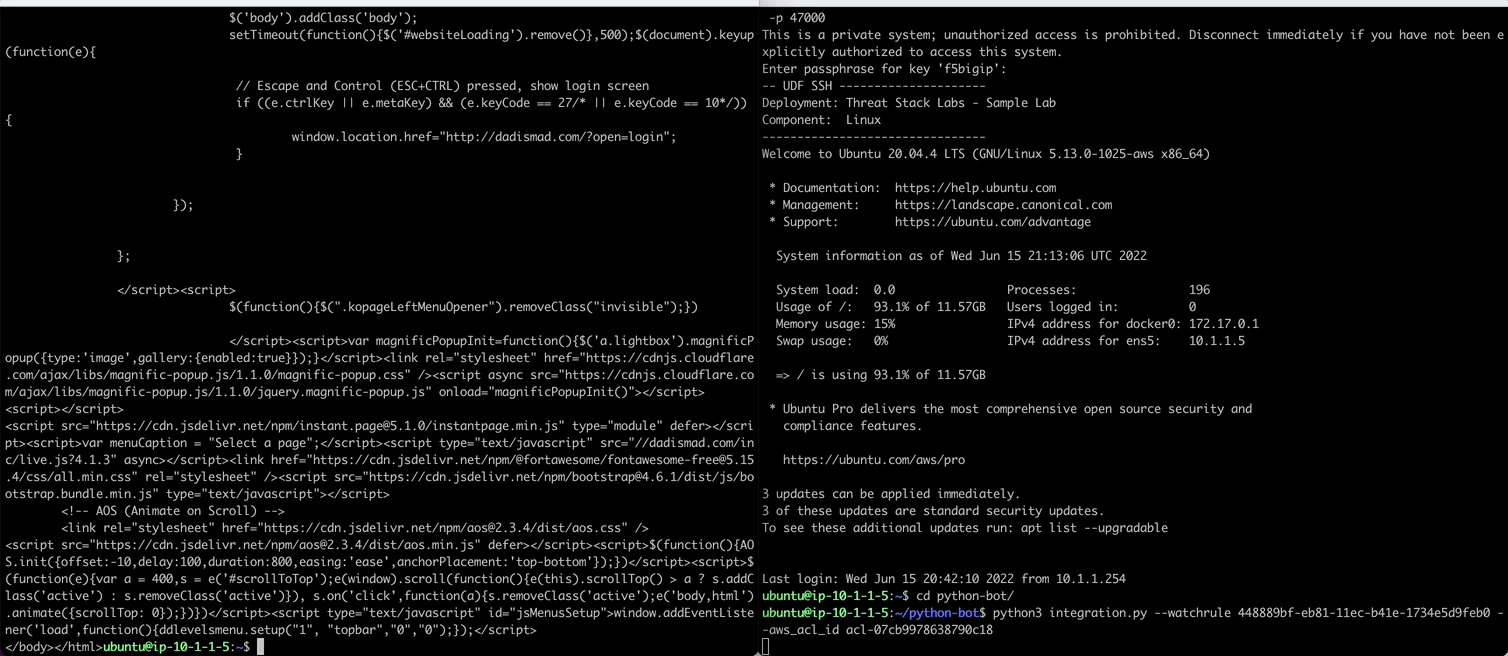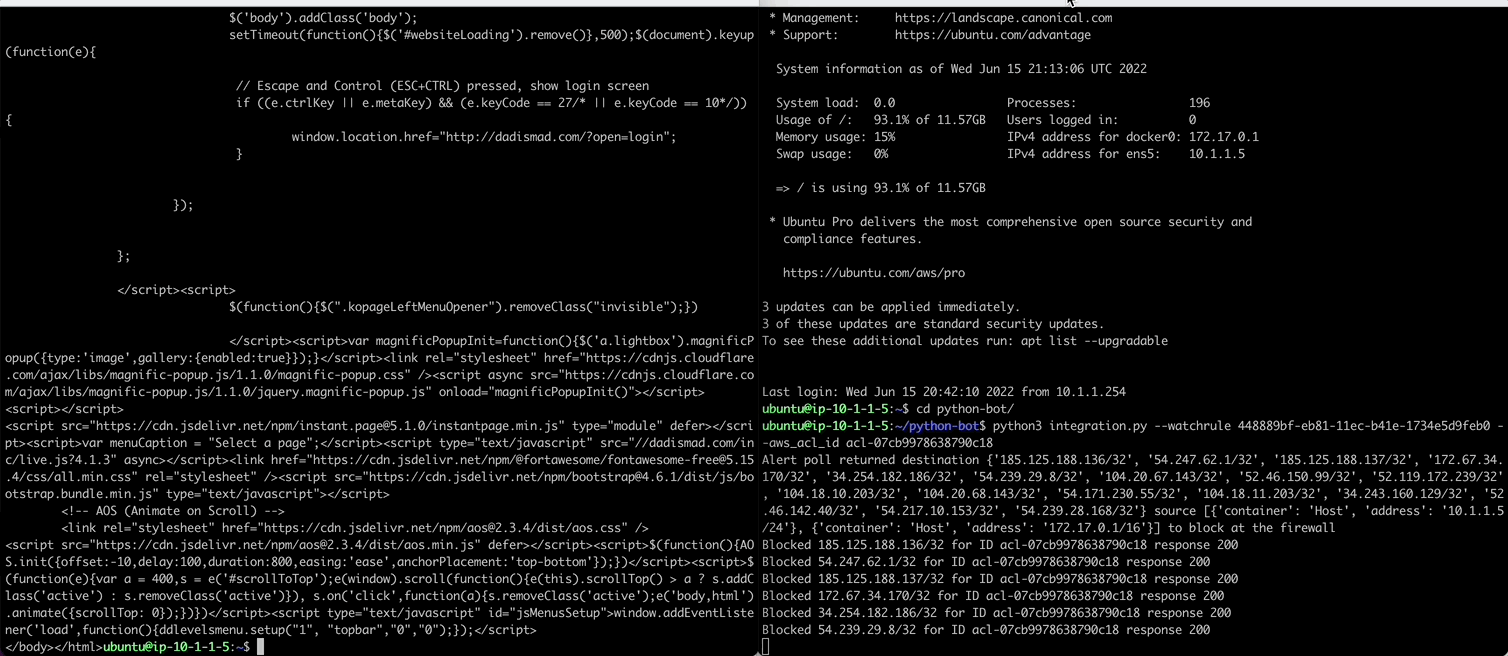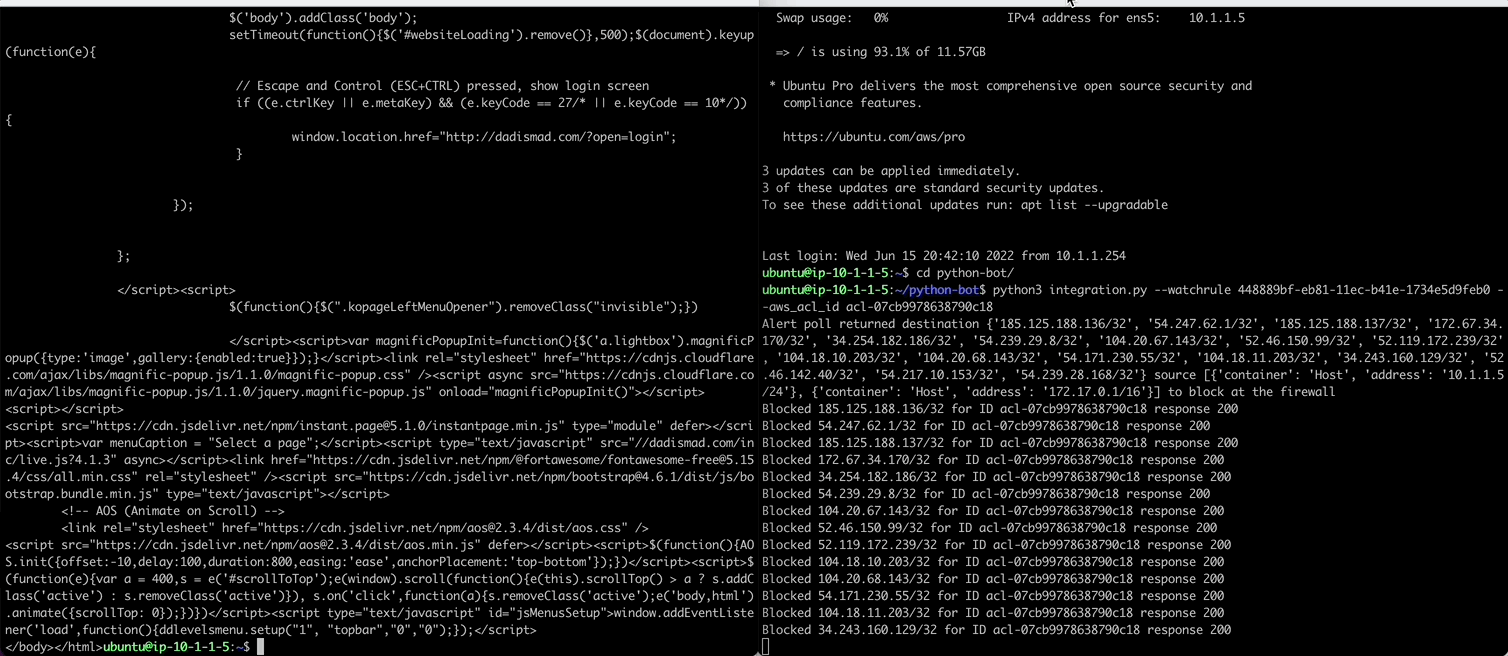
Use the RuleID provided below to detect network outbound connection to WAN and then auto add the CIDR block to the AWS NACL ID. The AWS VPC will block the added CIDR Block in near-realtime.
- RuleID: 448889bf-eb81-11ec-b41e-1734e5d9feb0
- ACL ID: acl-06ead5a200e17b7d4
Be aware that the RuleID below is a VALID and can be found in F5 - Agility Labs > Rules > Base Rule Set > Network: Outbound Connection (Connects) to WAN.
Warning
In UDF, Linux instance python bot may require pip3 install boto3 or pip3 install –upgrade awscli
The python bot will now watch for the RuleID to be triggered. Leave terminal connected, and **start a new terminal session*.
Results¶
New Terminal
In a new terminal we will sample activity from the python bot observing the rule. Once the rule triggers, the python bot grabs the destination/source IPs from the alert (and any contributing event) to then add them to the AWS VPC ACL using the AWS CLI.
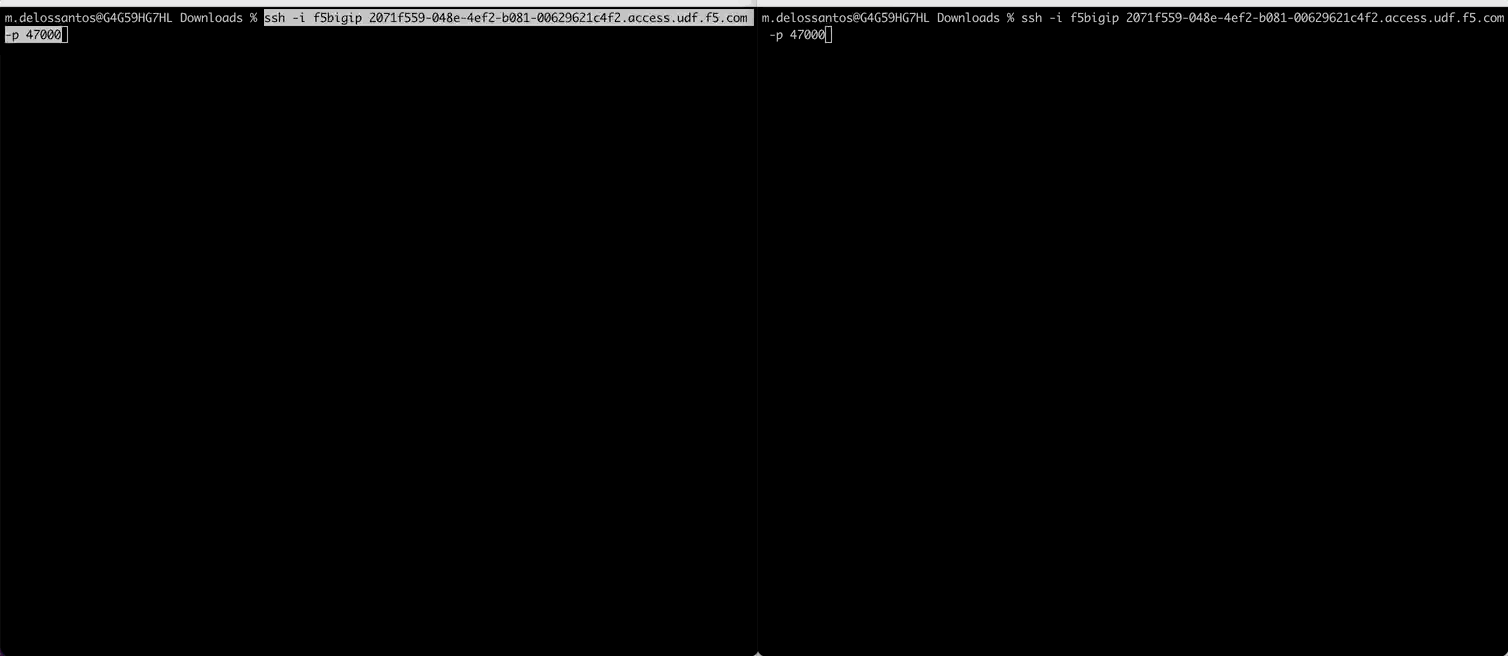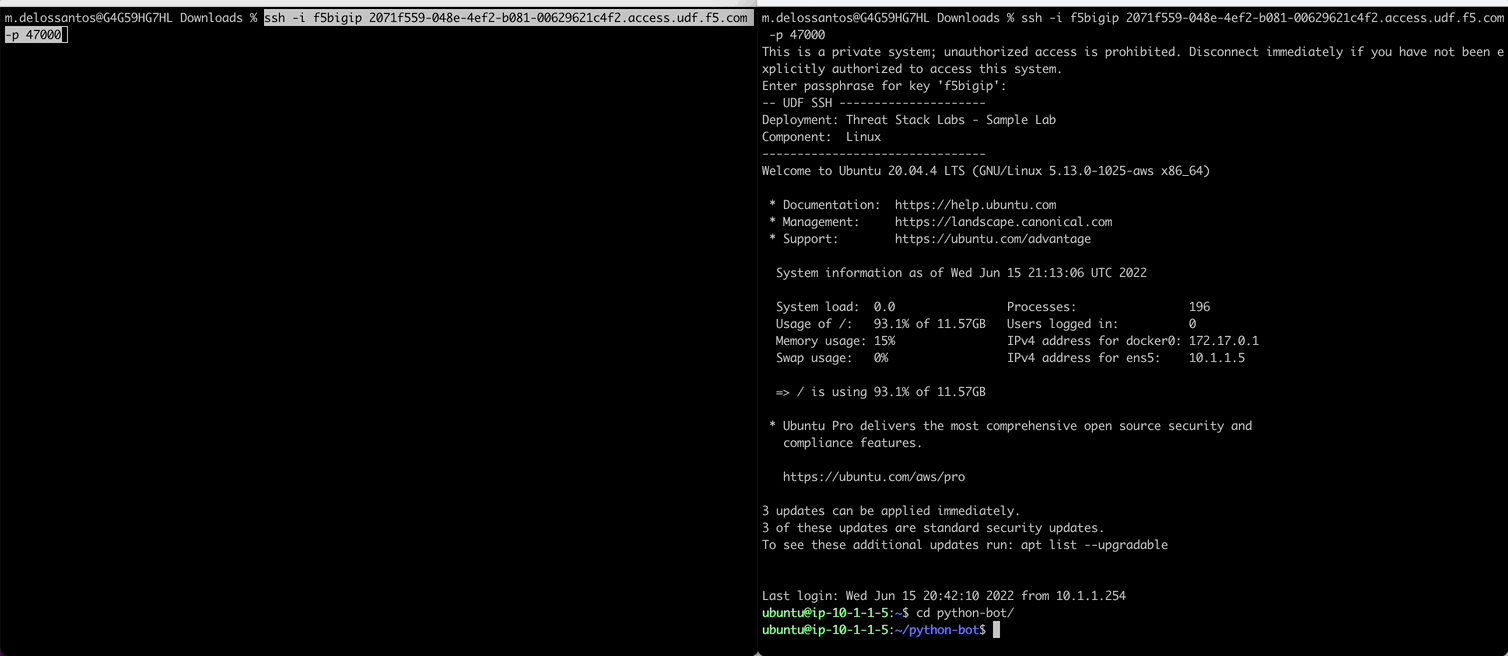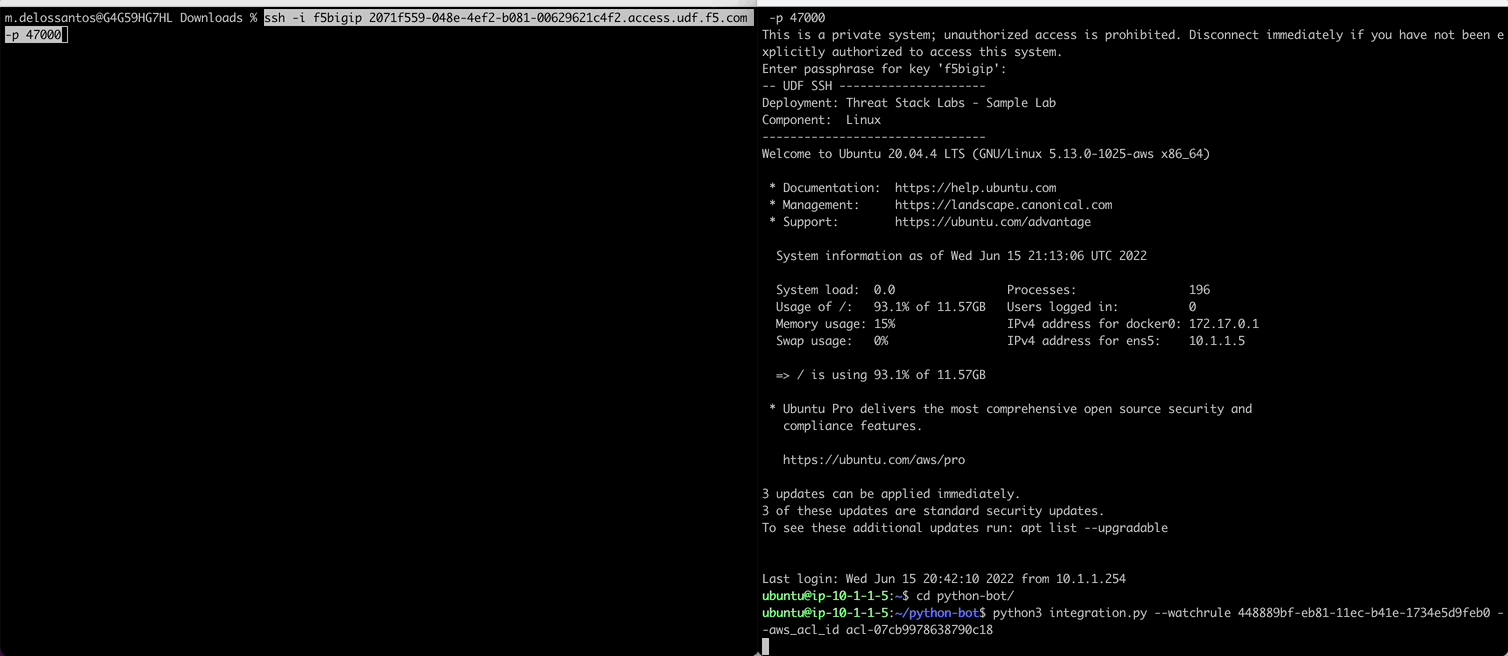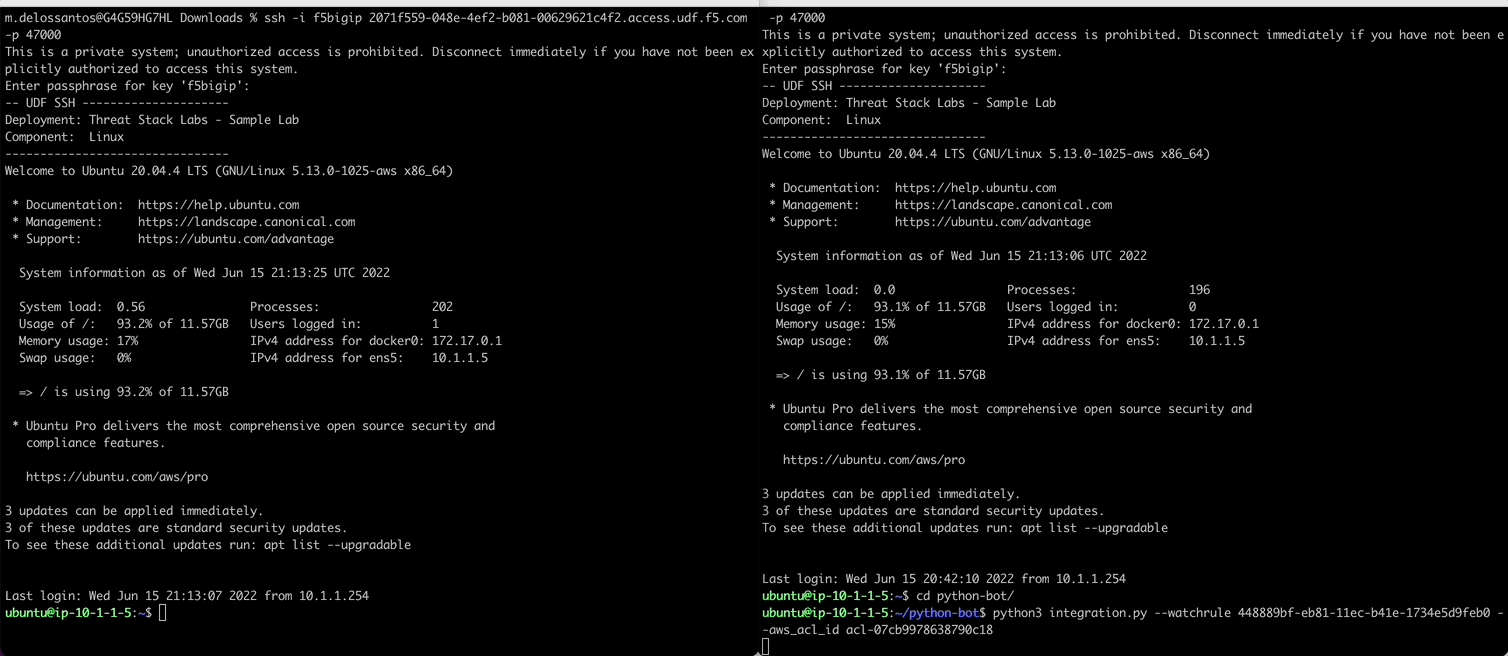
Execute Command to trigger the RuleID