Threat Stack Labs > Threatstack 301: Advanced Cloud Workload Protection Source | Edit on
Threat Stack Playbooks - Part 2¶
Self-Protecting Cloud - Part 2¶
Create AWS Environment¶
Now that we have confirmed Python, Threat Stack, and no active AWS CLI accounts. Let’s add our AWS CLI Account and setup the required AWS Network,
AWS CLI Configuration
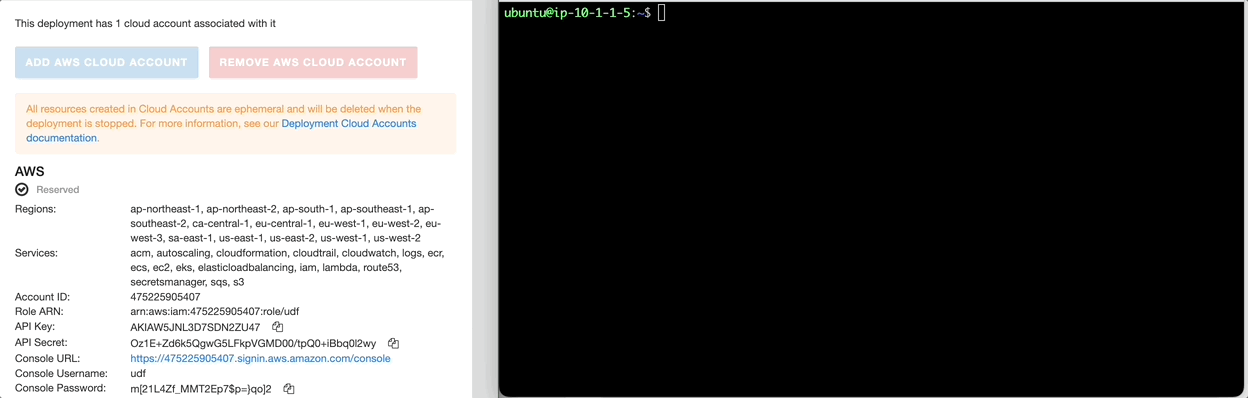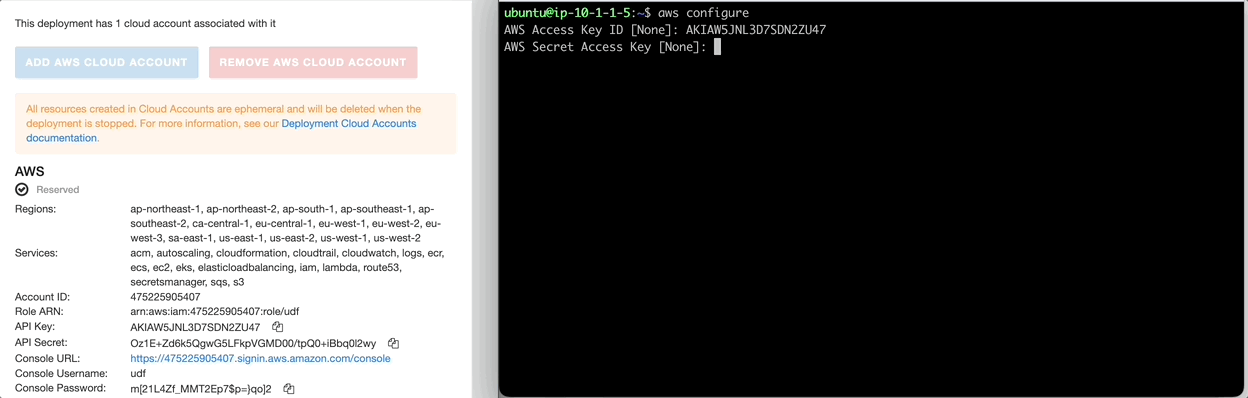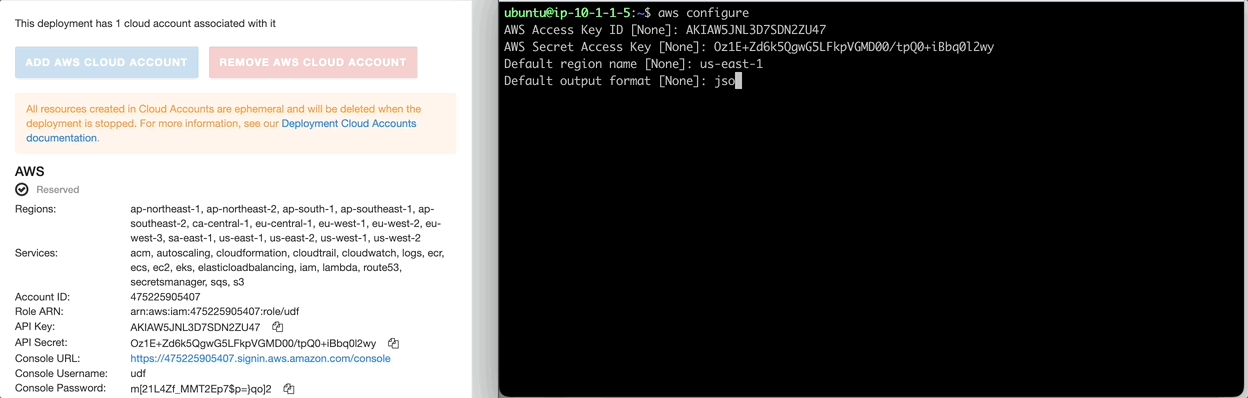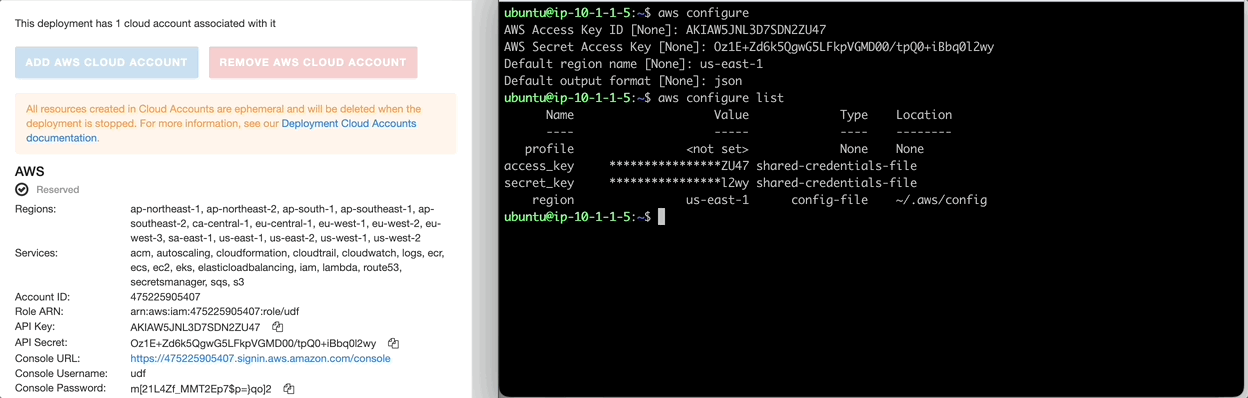
By typing aws configure as illustrated below, you navigate to Cloud Accounts in UDF. Here you will find the AWS credentials required, copy/paste both the API Key and API Secret Key.
Warning
In UDF, Linux instance aws cli may require pip3 install boto3 or pip3 install –upgrade awscli
Note
In UDF, go to Deployments > Select Threat Stack Labs or name of deployment > Cloud Accounts. Here you will find the AWS keys such as; API Key and API Secret Key.
AWS CLI Config VPC Network
Create the Virtual Private Cloud (VPC) in AWS Cloud Account.
Retrieve NetworkAclId
Note
Save the NetworkAclId for later use.
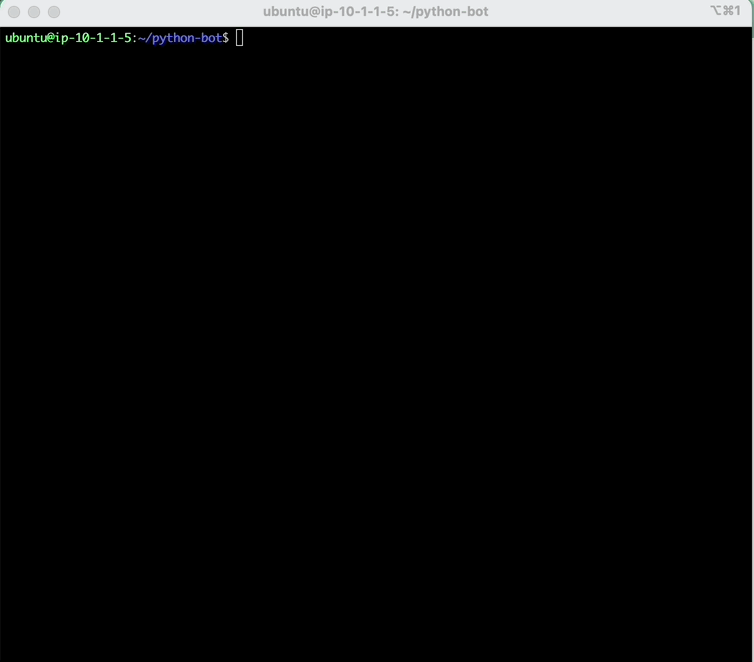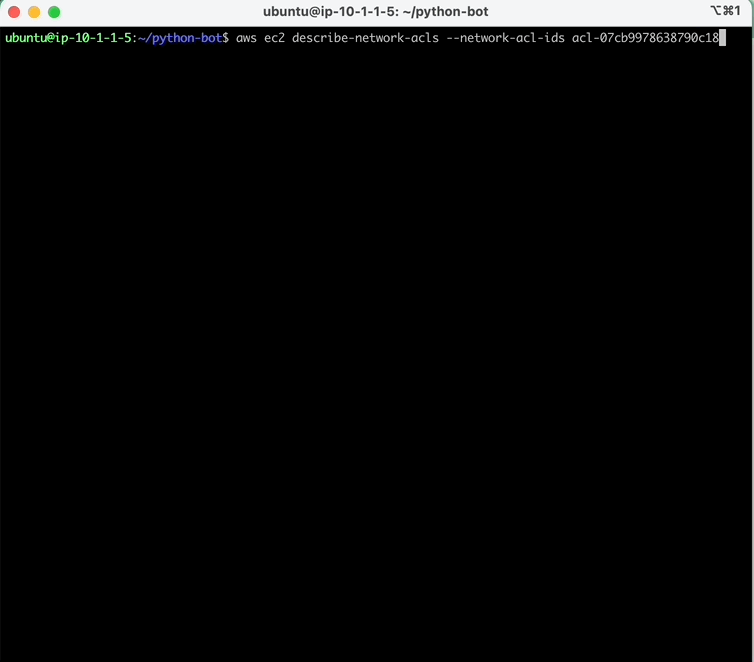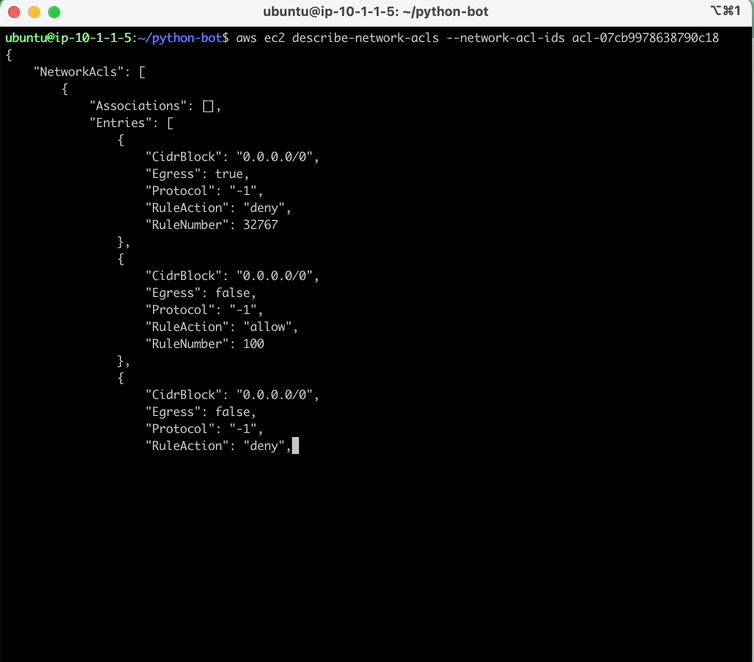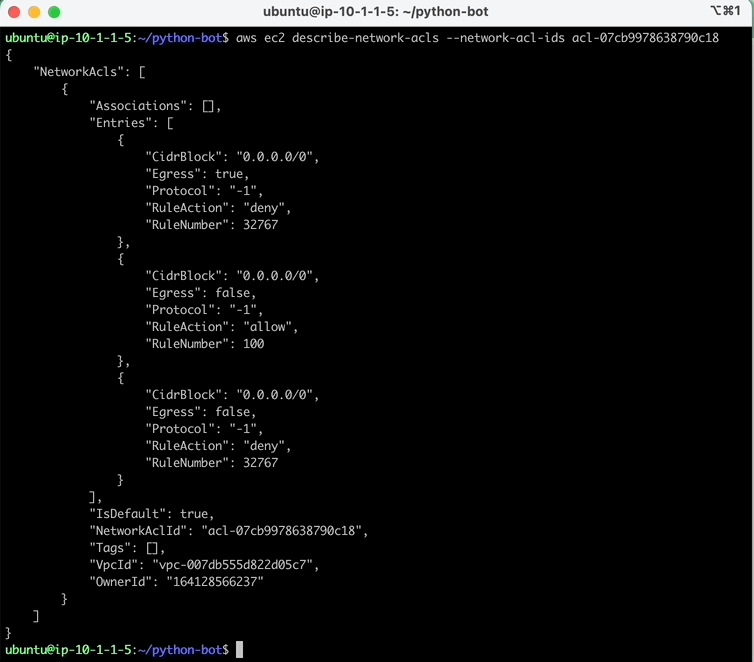
Current NACLs
Before continuing lets review the AWS environment default ACLs.
Threat Stack Setup¶
Before jumping into the technical configuration on this lab, let us first define our detection rule within the Threat Stack Cloud Security Platform. For this Lab, our rule is intended to highlight network process activity.
Threat Stack - Create Rule
The suggested Rule is precreated within Threat Stack’s F5 - Agility Labs Organization, named Self Protect: Network: Outbound Connection (Connects) to WAN. Feel free to create a new rule or clone existing.
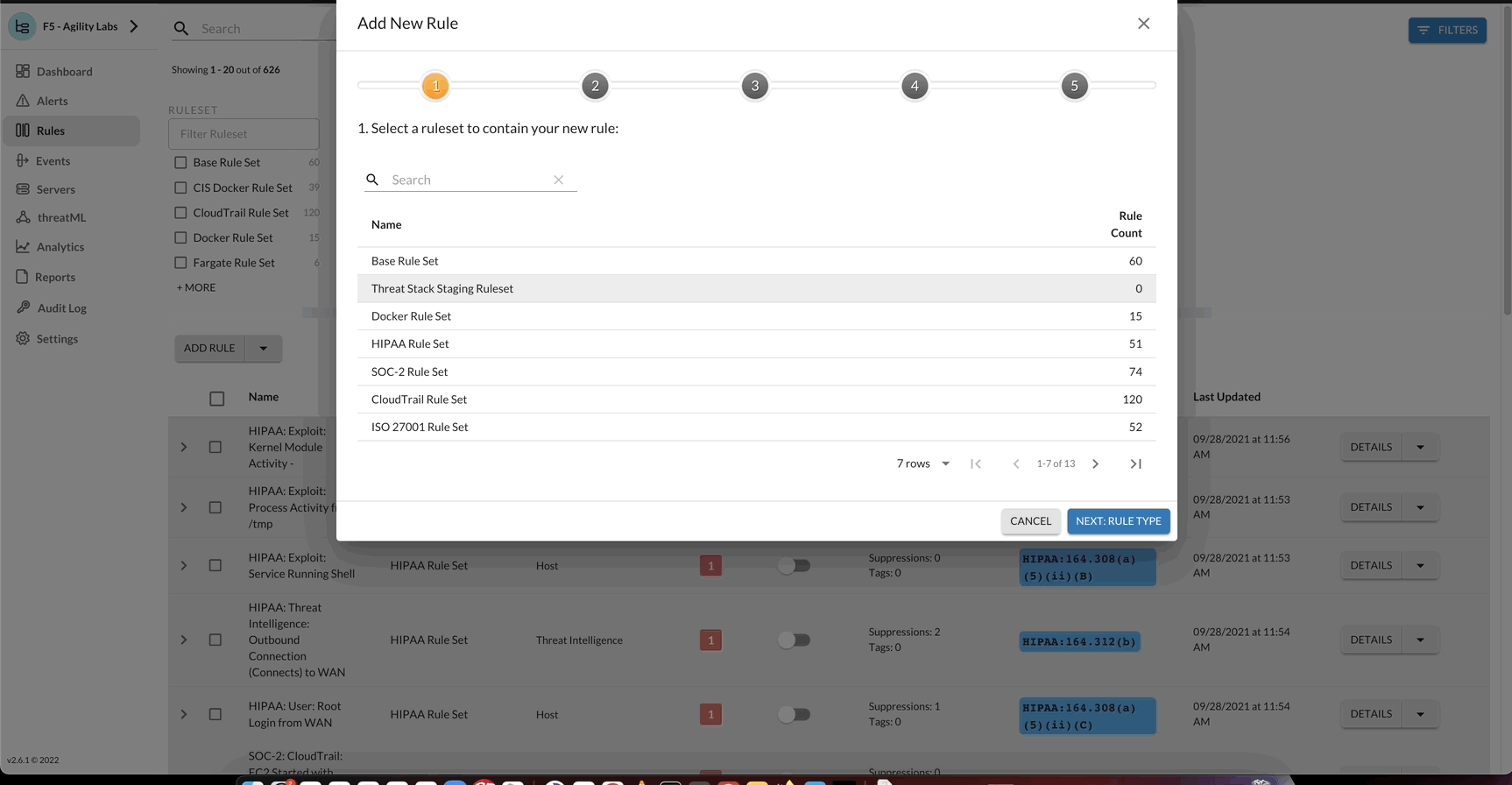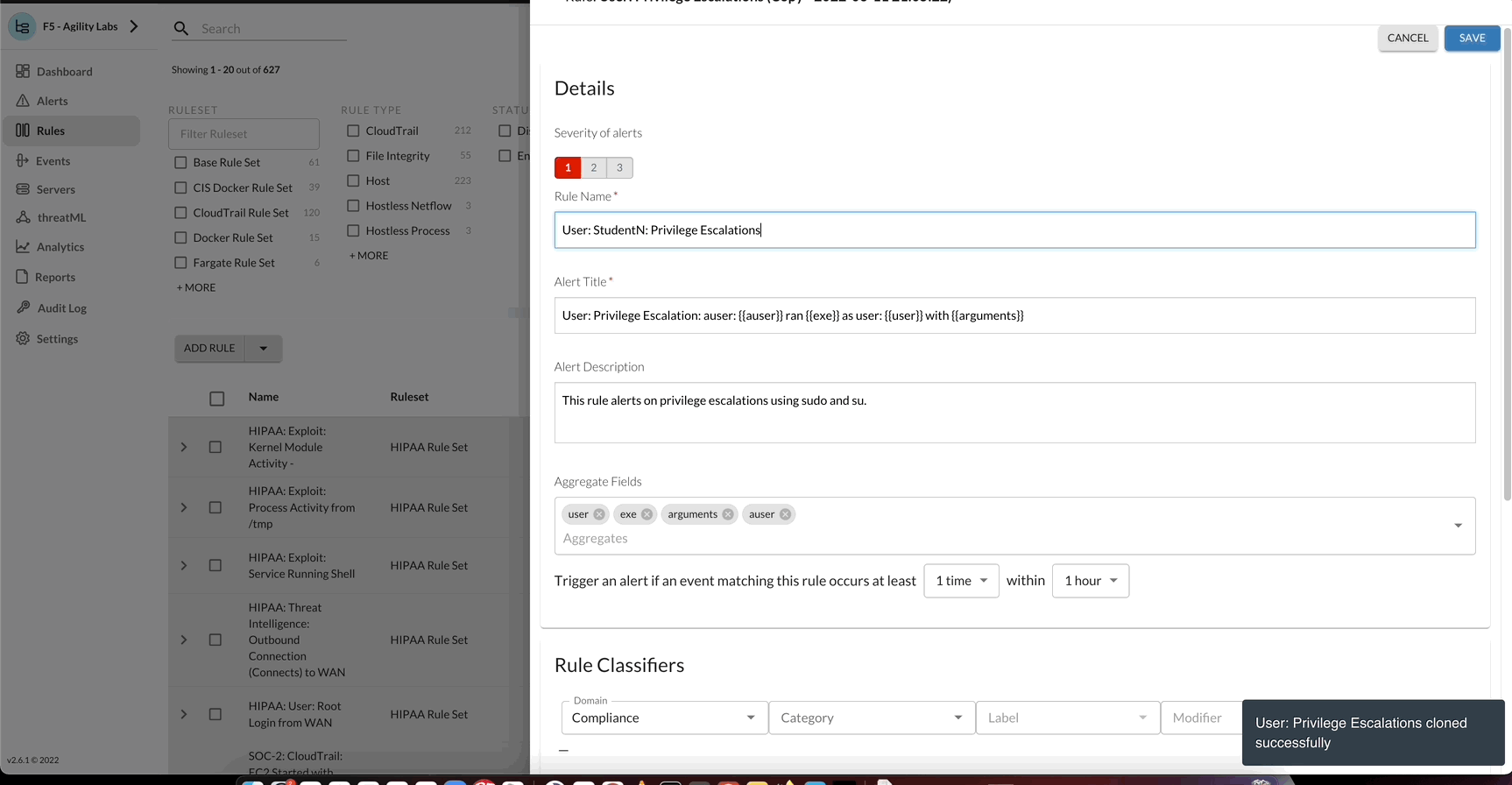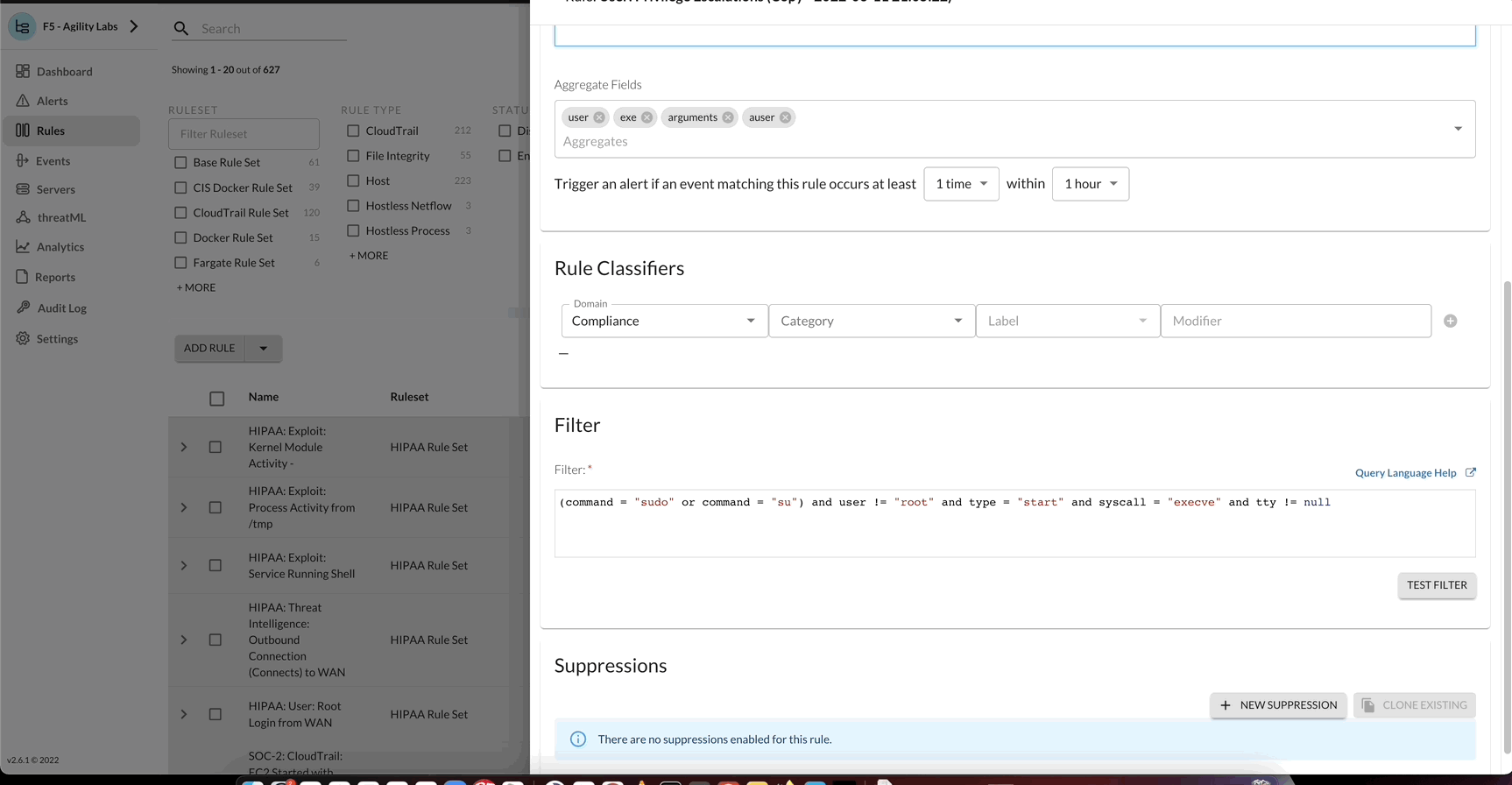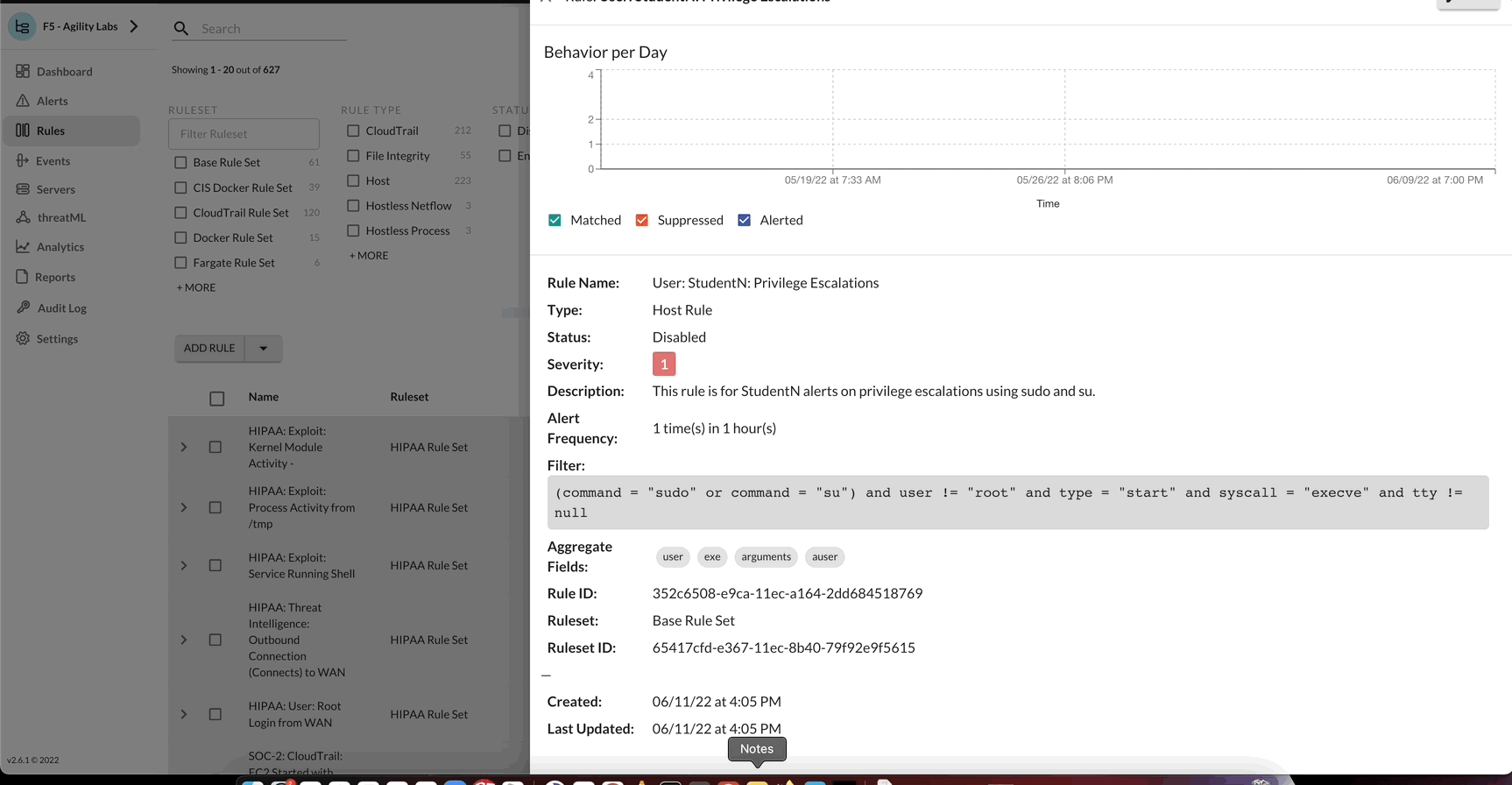
Update the rule using the following criteria:
- Rule Name
- Self Protect: StudentN: Network: Outbound Connection (Connects) to WAN
- Alert Title
- Self Protect: StudentN: Network: Outbound Connection (Connects) to WAN: {{exe}} ran by user {{user}} connected to {{dst_ip}}
- Alert Description
- This alerts when a program connects to an external server’s service. An example is a wget/curl to an external HTTP server. This could be used for data exfiltration. Depending on your environment this could be VERY noisy. We recommend adding to the rule filter to focus scope of the rule.
- Aggregate Fields
- user, exe, dst_ip
- Rule Filter
- event_type = “audit” and syscall = “connect” and (connection.dst_addr != “127.0.0.0/8” and connection.dst_addr != “::1/128” and connection.dst_addr != “::” and connection.dst_addr != “0.0.0.0” and connection.dst_addr != “169.254.0.0/16”)
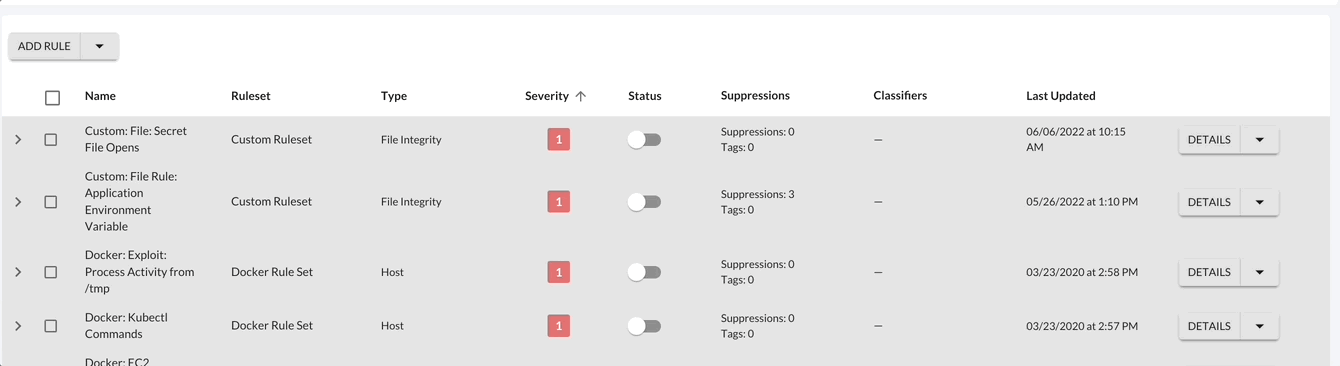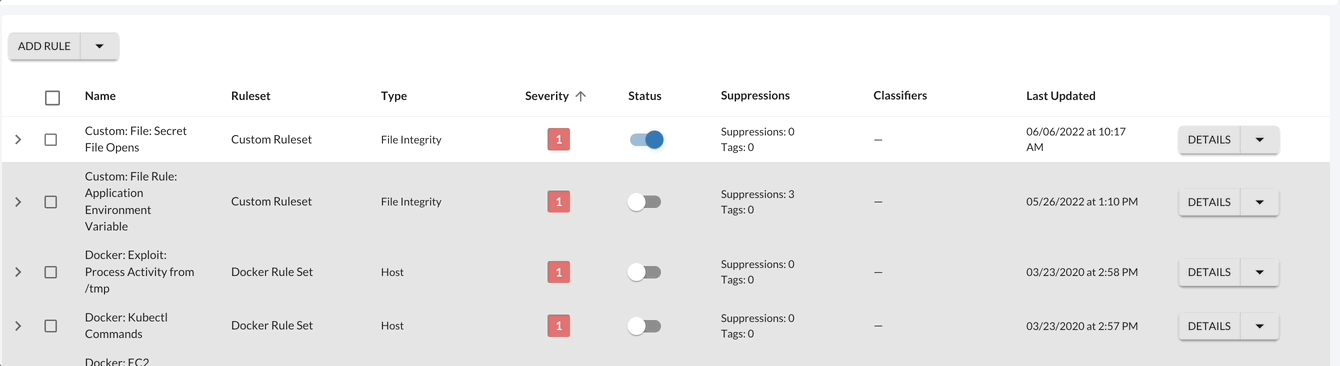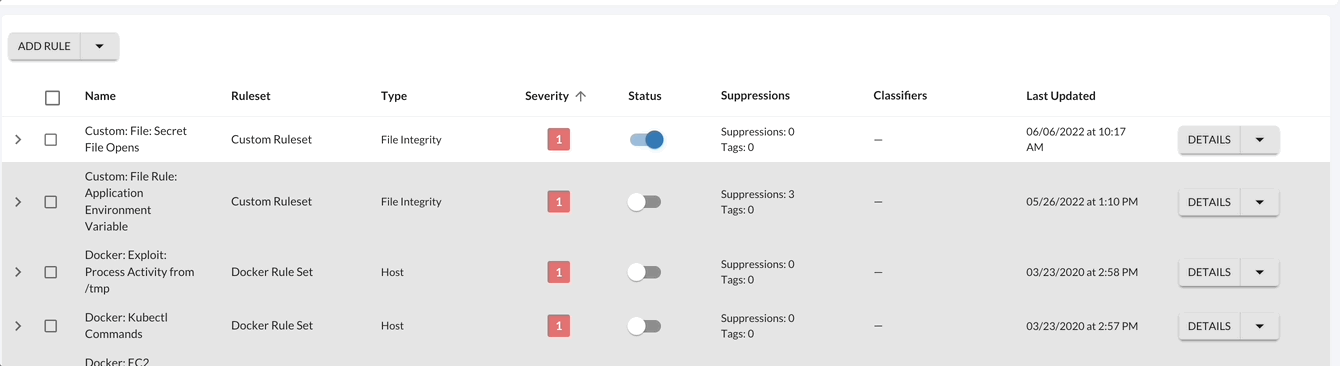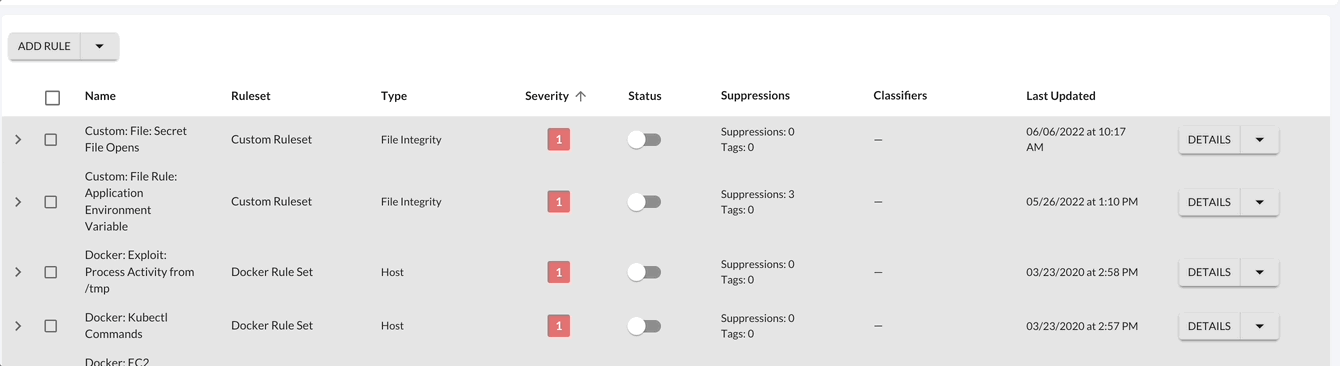
Threat Stack - Enable Rule
Using Rule Quick actions or by editing the rule, update the status of the rule to enable it.
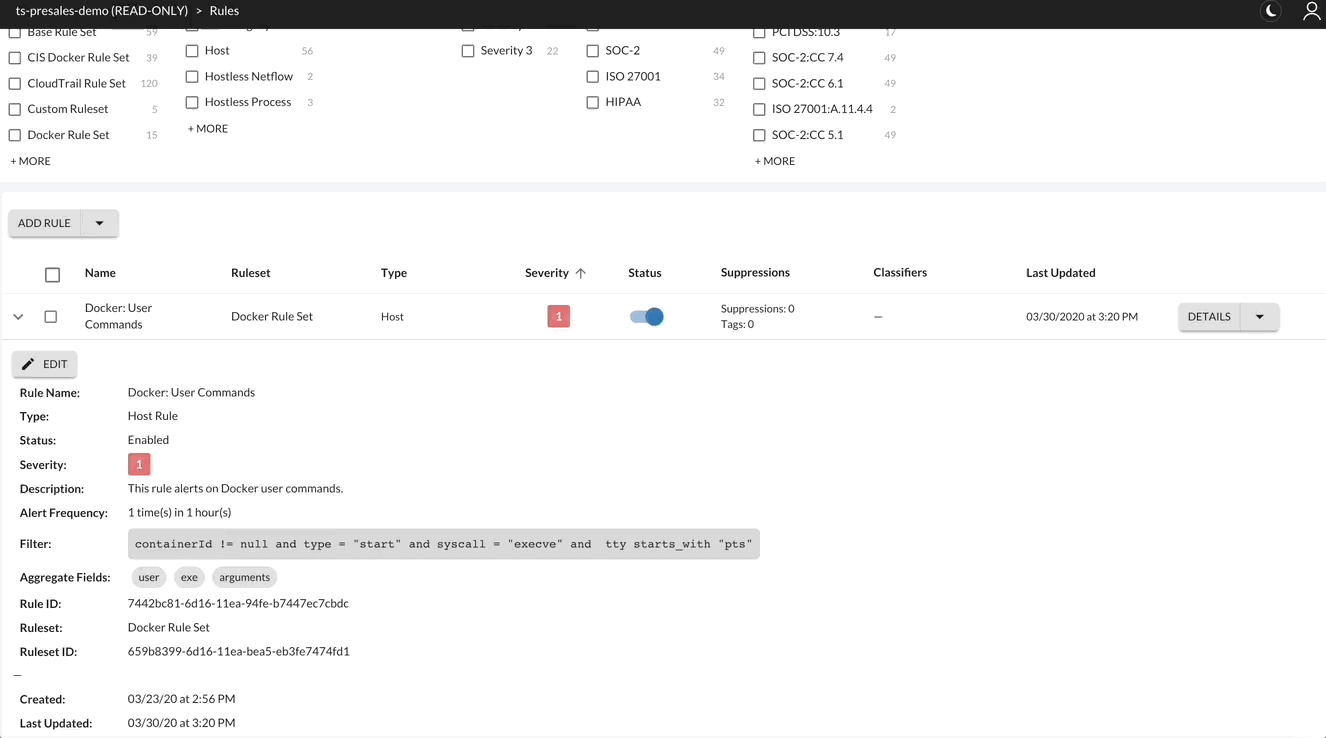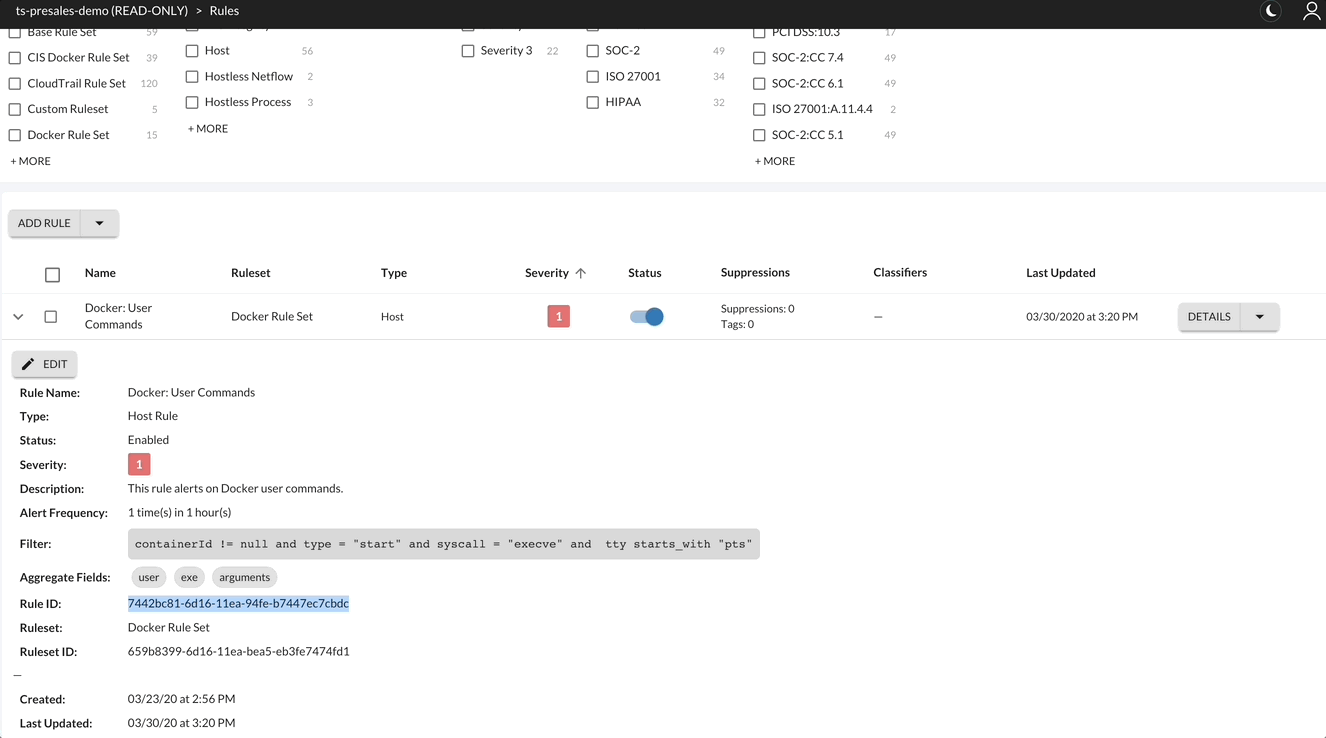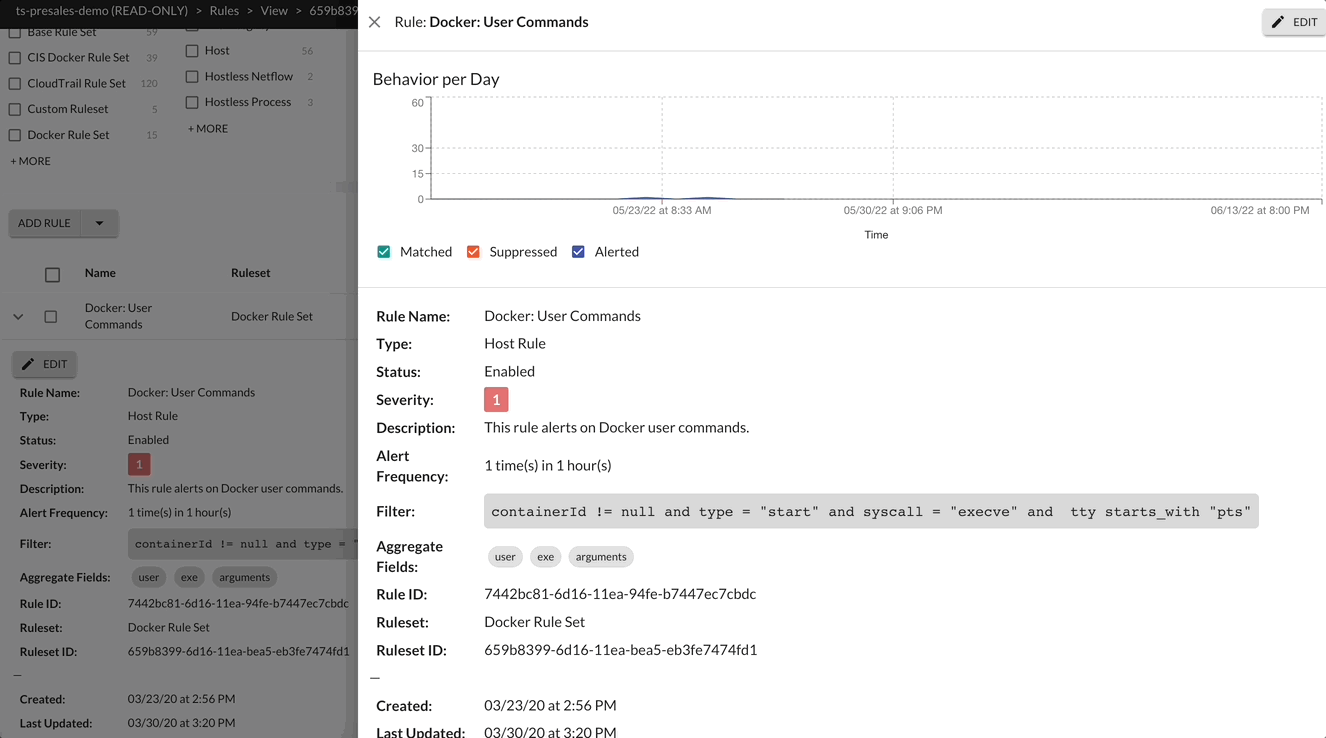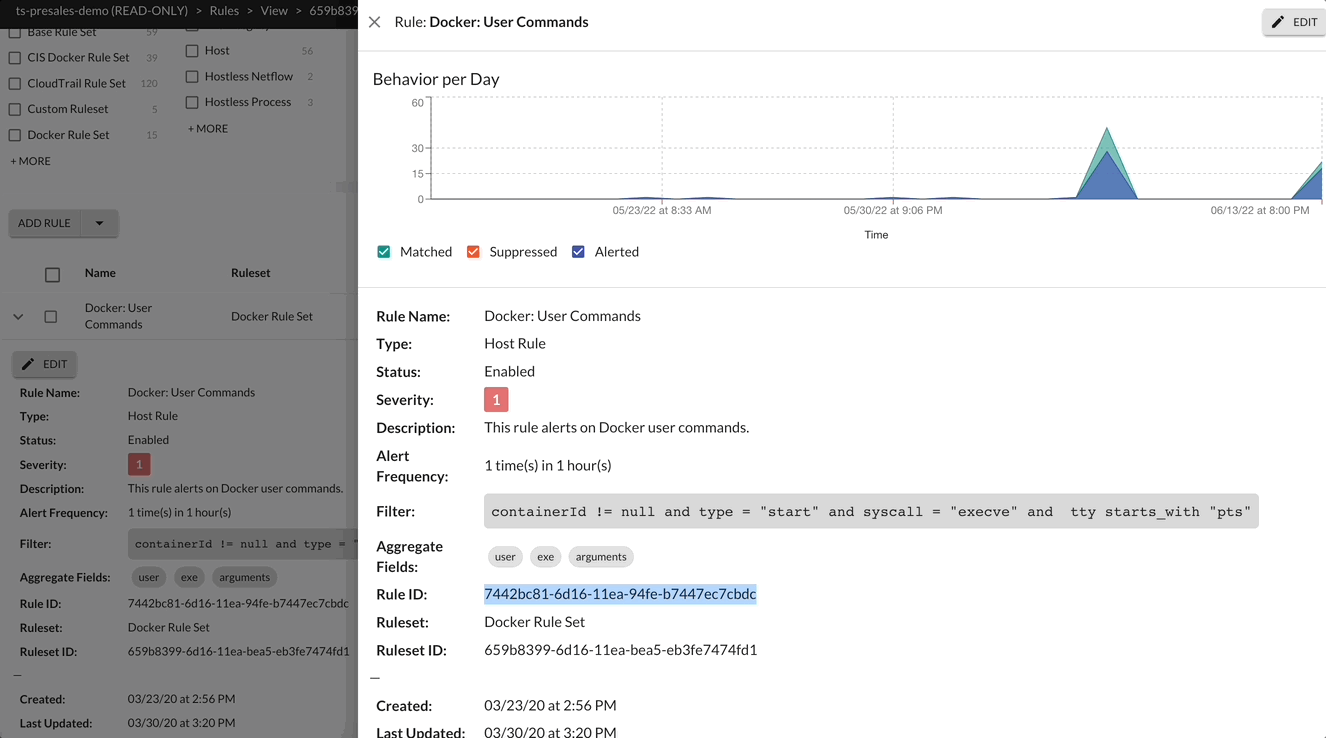
Retrieve Rule ID
Note
Save the RuleID for later use.