ExternalDNS¶
Overview¶
ExternalDNS is a Kubernetes add-on that configures public DNS servers with information about exposed Kubernetes services to make them discoverable. ExternalDNS CRDs allow you to control DNS records dynamically via Kubernetes/OSCP resources in a DNS provider-agnostic way.
Open API Schema Validation for ExternalDNS
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | apiVersion: "cis.f5.com/v1" kind: ExternalDNS metadata: name: exdns labels: f5cr: "true" spec: domainName: example.com dnsRecordType: A loadBalanceMethod: round-robin pools: - name: example.site1.com dnsRecordType: A loadBalanceMethod: round-robin dataServerName: /Common/GSLBServer monitor: type: https send: "GET /" recv: "" interval: 10 timeout: 10 |
Example Topologies:¶
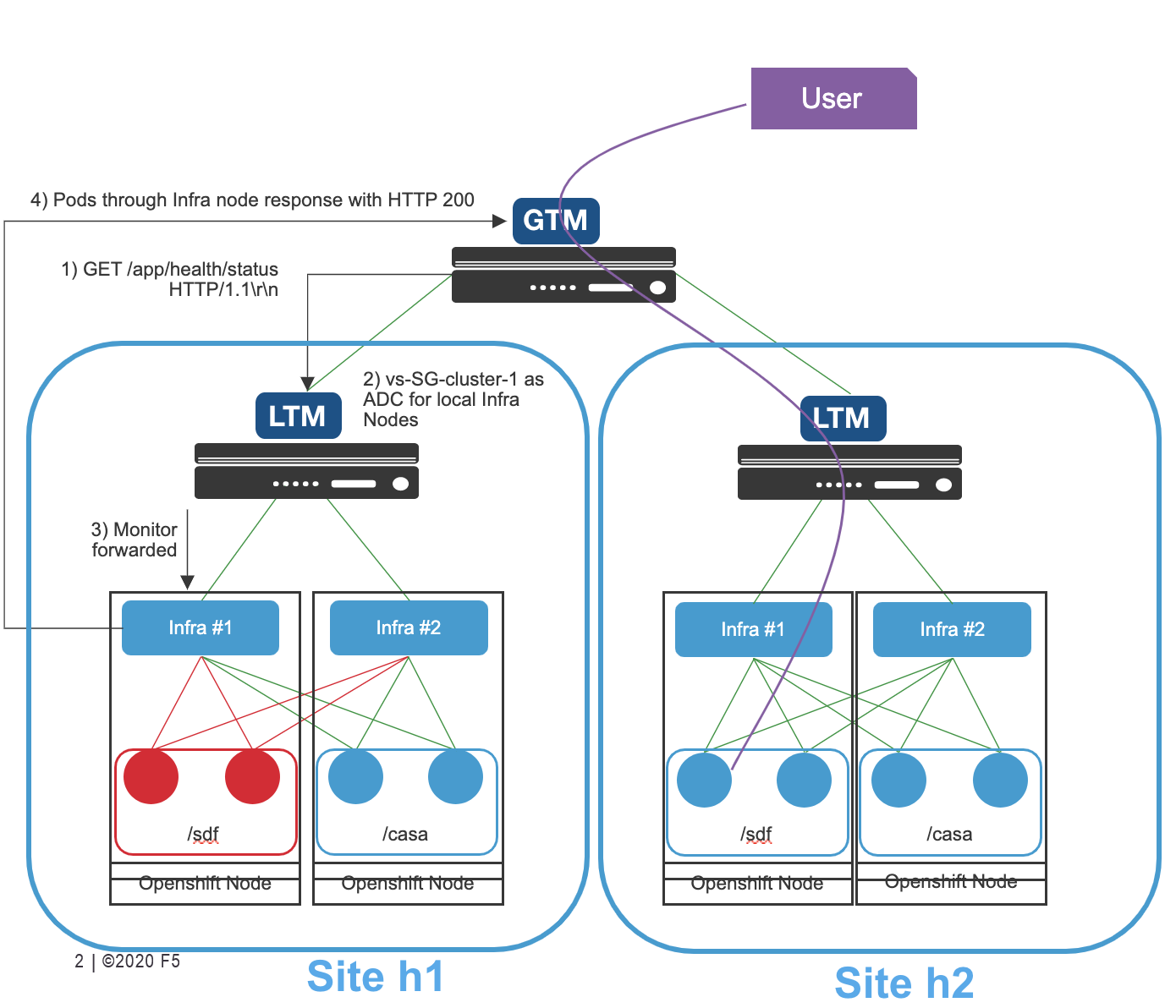
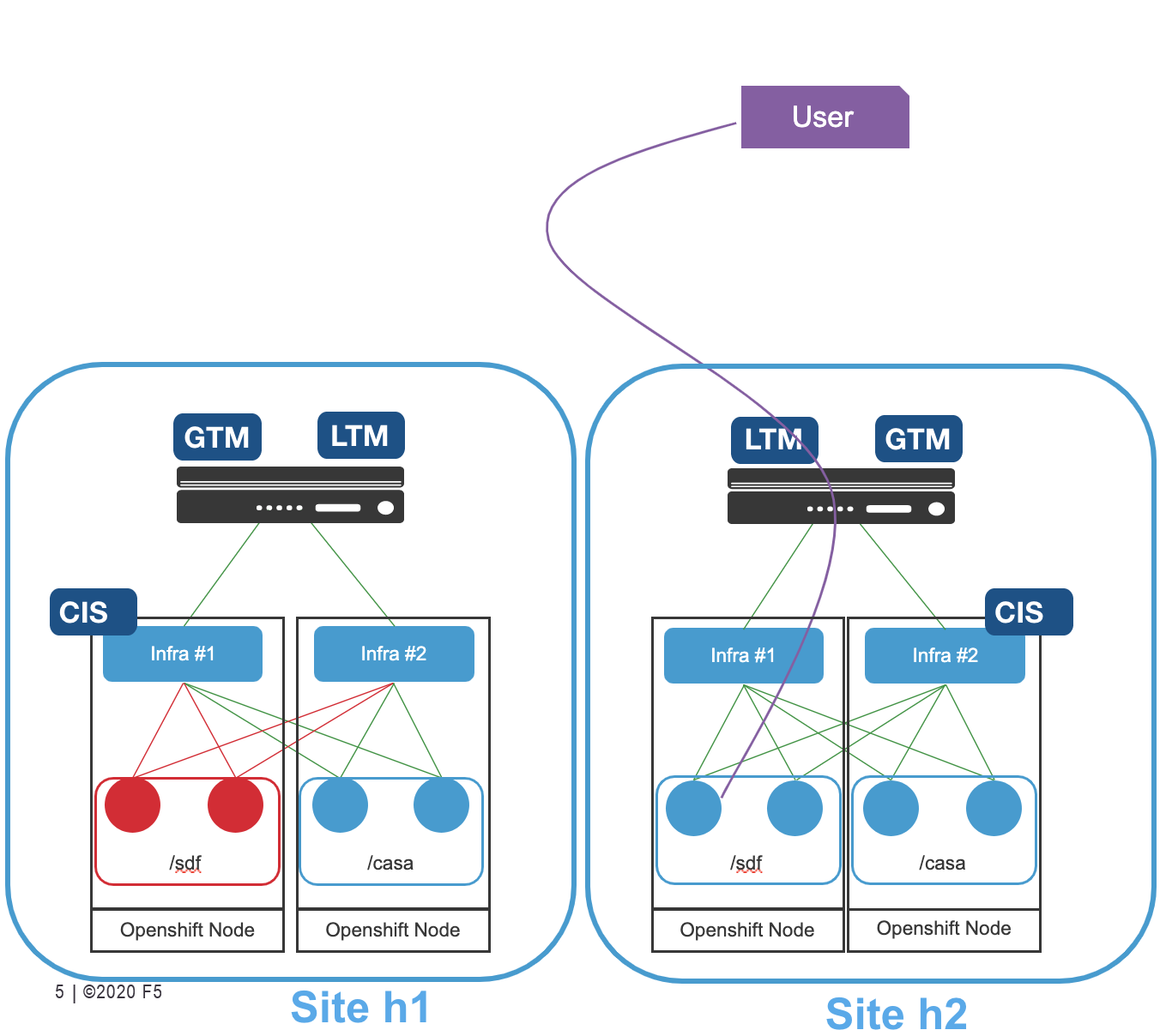
The images below show the use cases and topology for External DNS CRD:
- Two sites
- Each Site will run an Openshift Cluster
- Each Site will have 1 pair of BIG-IPs running LTM and DNS
- Each Openshift cluster will run a CIS per BIG-IP (traditional deployment): So 2 CIS will be deployed per site.
Prerequisites¶
- OpenShift/Kubernetes Cluster must be up and running.
- AS3 version 3.18+.
- External DNS objects created in the COMMON partition.
- You must have a fully active/licensed BIG-IP.
- VXLAN tunnel should be configured from OpenShift/Kubernetes Cluster to BIG-IP.
- LTM and GTM are mandatory but they do not need to be on the same device.
- VXLAN tunnel is not mandatory.
- SDN license is not needed: only DNS license is required.
- ExternalDNS HTTPS monitor support requires BIG-IP v16.1 and later.
Components¶
CIS Configuration Parameters for BIG-IP GTM¶
| Parameter | Type | Required | Default | Description |
|---|---|---|---|---|
| gtm-bigip-password | String | Required | N/A | Password for the GMT BIG-IP user account. You can secure your GTM BIG-IP credentials using a Kubernetes Secret. |
| gtm-bigip-url | String | Required | N/A | URL for the GTM BIG-IP. |
| gtm-bigip-username | String | Required | N/A | Username for the GTM BIG-IP user account. |
| gtm-credentials-directory | String | Optional | N/A | The directory that contains the GTM BIG-IP username, password, and/or URL files. To be used instead of username, password, and/or URL arguments. |
Important
If the same BIG-IP is configured for GTM resources, then the following GTM parameters are not necessary in the CIS deployment:
- gtm-bigip-password
- gtm-bigip-url
- gtm-bigip-username
If the GTM resources are configured by a different BIG-IP, then these GTM parameters are required in the CIS deployment.
ExternalDNS Components¶
| Parameter | Type | Required | Default | Description |
|---|---|---|---|---|
| domainName | String | Required | N/A | Domain name of virtual server CRD. |
| dnsRecordType | String | Required | N/A | DNS record type. |
| loadBalancerMethod | String | Required | round-robin | Load balancing method for DNS traffic. |
| pools | Pool | Optional | N/A | GTM Pools. |
Pool Components¶
Important
The user needs to mention the same GSLB DataServer Name in the dataServerName field, which is created on the BIG-IP common partition.
GSLB Monitor Components¶
| Parameter | Type | Required | Default | Description |
|---|---|---|---|---|
| type | String | Required | N/A | http or https |
| send | String | Required | N/A | Send string for monitor. For example: GET /health HTTP/1.1\r\nHOST: example.com\r\n |
| recv | String | Optional | N/A | Receive string. This can be empty. |
| interval | Int | Required | 5 | Seconds between health queries. |
| timeout | Int | Optional | 16 | Seconds before query fails. |
- The credentials-directory option is an alternative to using the bigip-username, bigip-password, or bigip-url arguments.
- When you use this argument, the controller looks for three files in the specified directory:
username,password, andurl. If any of these files do not exist, the controller falls back to using the CLI arguments as parameters. - Each file should contain only the username, password, and url, respectively. You can create and mount the files as Kubernetes Secrets.
- It is important to not project the Secret keys to specific paths, as the controller looks for the “username”, “password”, and “url” files directly within the credentials directory.
ExternalDNS with BIG-IP GTM¶
To set up external DNS using BIG-IP GTM, the user needs to first manually configure the following:
In the BIG-IP user interface, go to DNS → GSLB → Data Center and GSLB → Servers on BIG-IP common partition.
Note
Wide IP, Pool, Pool member, and Health Monitor will be managed with ExternalDNS CRD.
BIG-IP DNS is expected to be setup with Service discovery Enabled (no delete).
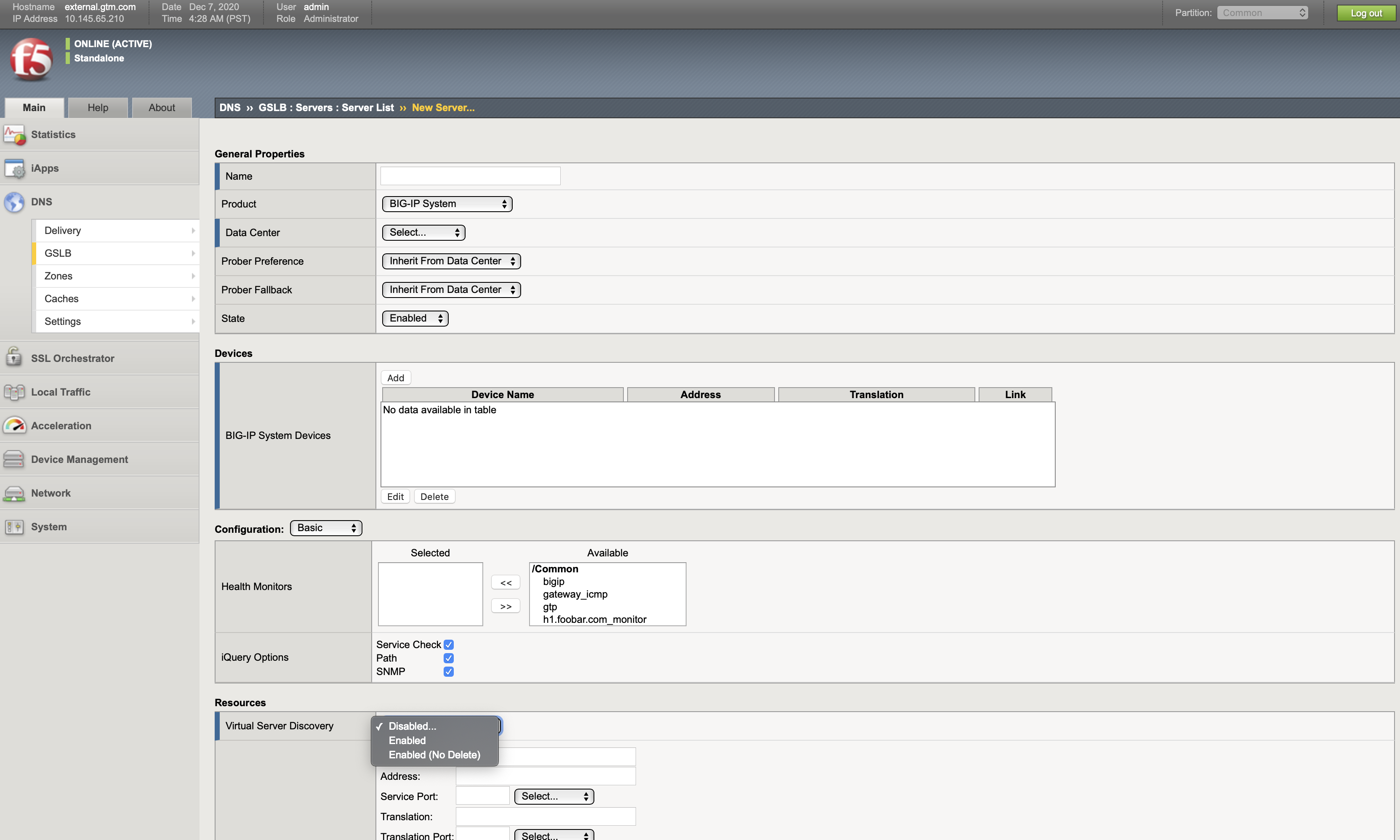
From the YAML configuration below, the user can enable the External DNS feature on BIG-IP.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | apiVersion: "cis.f5.com/v1" kind: ExternalDNS metadata: name: exdns labels: f5cr: "true" spec: domainName: example.com dnsRecordType: A loadBalanceMethod: round-robin pools: - name: example.site1.com dnsRecordType: A loadBalanceMethod: round-robin dataServerName: /Common/GSLBServer monitor: type: https send: "GET /" recv: "" interval: 10 timeout: 10 |
Below is an example of the VirtualServer CRD that has to be created to resonate with the EDNS configuration.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | apiVersion: cis.f5.com/v1 kind: VirtualServer metadata: labels: f5cr: "true" name: sample-virtual namespace: default spec: host: example.com pools: - monitor: interval: 20 recv: "" send: / timeout: 10 type: http path: / service: svc-1 servicePort: 80 virtualServerAddress: 172.16.3.4 |
- The name in GSLB → DataServer Name needs to be the same as dataServerName field in the BIG-IP common partition.
- The domain name should be the same as mentioned in the virtual server CRD.
- If the same BIG-IP is configured for GTM resources then the GTM parameters (gtm-bigip-password, gtm-bigip-url, gtm-bigip-username) in CIS deployment are not mandatory.
- If the GTM resources are configured by a different BIG-IP, then the GTM parameters (gtm-bigip-password,gtm-bigip-url,gtm-bigip-username) in CIS are mandatory.
Health Monitors with ExternalDNS CRD¶
ExternalDNS CRD supports TCP, HTTP, HTTPS type of health monitors. Below are examples for various types of health monitors:
type: tcp
interval: 10
timeout: 30
type: http
send: "GET /tea HTTP/1.1\r\nHost: cafe.example.com\r\n"
recv: ""
interval: 10
timeout: 30
type: https
send: "GET /tea HTTP/1.1\r\nHost: cafe.example.com\r\n"
recv: ""
interval: 10
timeout: 30
Single Health Monitor¶
To specify a single health monitor for an EDNS pool you can use monitor in the EDNS Spec as shown below:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | apiVersion: "cis.f5.com/v1" kind: ExternalDNS metadata: name: exdns labels: f5cr: "true" spec: domainName: example.com dnsRecordType: A loadBalanceMethod: round-robin persistenceEnabled: true persistCidrIpv4: 24 ttlPersistence: 1000 pools: - dnsRecordType: A loadBalanceMethod: round-robin dataServerName: /Common/GSLBServer monitor: type: https send: "GET /" recv: "" interval: 10 timeout: 10 |
Multiple Health Monitors¶
To specify multiple health monitors for an EDNS pool you can use monitors in the EDNS Spec as shown below:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | apiVersion: "cis.f5.com/v1" kind: ExternalDNS metadata: name: exdns labels: f5cr: "true" spec: domainName: cafe.example.com dnsRecordType: A loadBalanceMethod: round-robin pools: - dnsRecordType: A loadBalanceMethod: round-robin dataServerName: /Common/GSLBServer monitors: - type: https send: "GET /tea HTTP/1.1\r\nHost: cafe.example.com\r\n" recv: "" interval: 10 timeout: 30 - type: https send: "GET /coffee HTTP/1.1\r\nHost: cafe.example.com\r\n" recv: "" interval: 10 timeout: 30 - type: tcp interval: 10 timeout: 30 |
ExternalDNS with Custom Resources¶
To use the EDNS with F5 IngressLink and TransportServer, just create a regular EDNS resource with the required hostname and add the same hostname in IngressLink/TransportServer’s spec as shown below:
1 2 3 4 5 6 7 8 9 10 11 12 13 | apiVersion: "cis.f5.com/v1" kind: IngressLink metadata: name: nginx-ingress namespace: nginx-ingress spec: virtualServerAddress: "192.168.10.5" host: cafe.example.com iRules: - /Common/Proxy_Protocol_iRule selector: matchLabels: app: ingresslink |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | apiVersion: "cis.f5.com/v1" kind: TransportServer metadata: labels: f5cr: "true" name: svc1-tcp-transport-server namespace: default spec: virtualServerAddress: "172.16.3.9" virtualServerPort: 8544 virtualServerName: svc1-tcp-ts host: cafe.example.com mode: standard snat: auto allowVlans: ["/Common/devtraffic"] persistenceProfile: "destination-address" pool: service: svc-1 servicePort: 8181 monitor: type: tcp interval: 10 timeout: 10 |
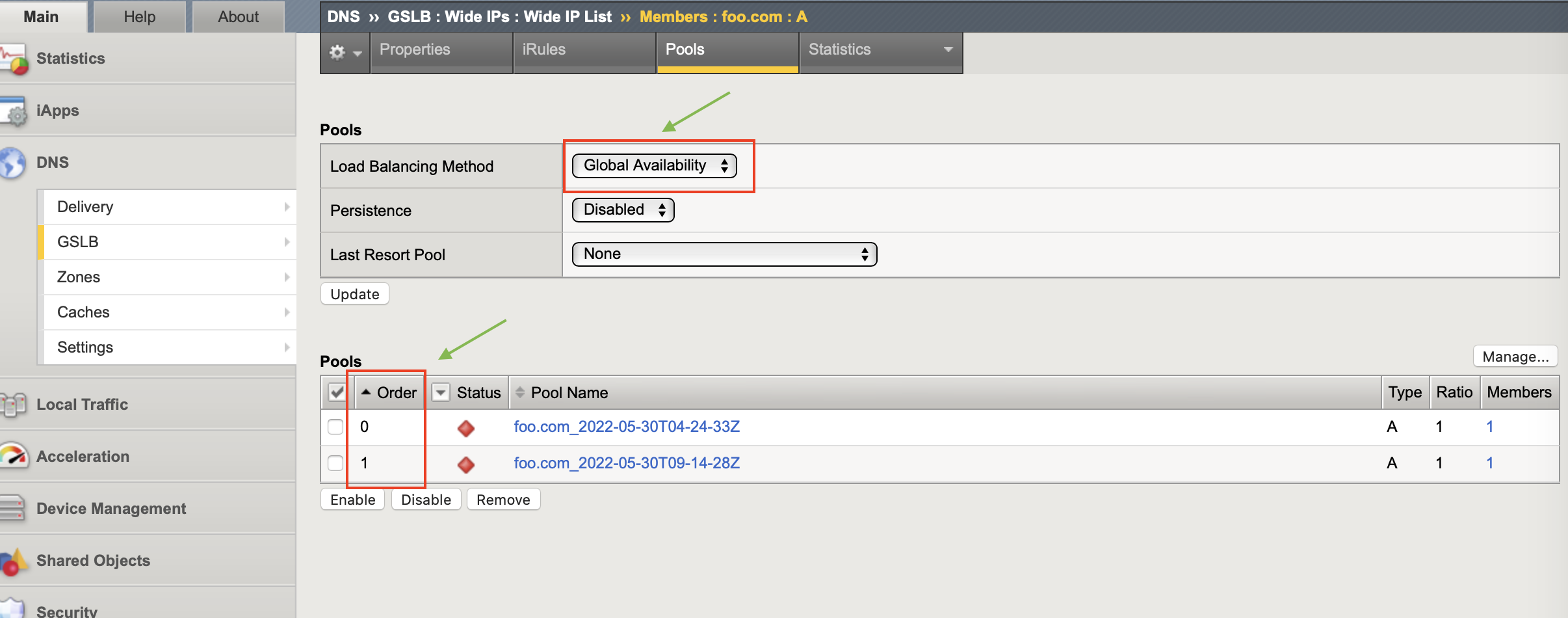
ExternalDNS Global Availability Mode¶
When the load balancing method is set to Global Availability, BIG-IP GTM distributes DNS name resolution requests to the first available virtual server in a pool. BIG-IP GTM starts at the top of a manually configured list of virtual servers and sends requests to the first available virtual server in the list. Only when the virtual server becomes unavailable does BIG-IP GTM send requests to the next virtual server in the list. Over time, the first virtual server in the list receives the most requests and the last virtual server in the list receives the least requests.
To set this option on BIG-IP using CIS:
In the EDNS resource spec, set the load balancing method to
global-availability.Configure the priority order of pool members using
spec.pools[].order. All the distributed wideIP pools need to have the correct pool order.Example:
Below are two different EDNS resources in two different clusters. The pool members associated with the second EDNS resource with an order 0 will get precedence over the first EDNS resource with an order 1.
externaldns-pool-priority-order.yaml¶1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35
labels: f5cr: "true" spec: domainName: example.com dnsRecordType: A loadBalanceMethod: global-availability pools: - dnsRecordType: A loadBalanceMethod: round-robin order: 1 dataServerName: /Common/GSLBServer monitor: type: tcp interval: 10 timeout: 10 --- apiVersion: "cis.f5.com/v1" kind: ExternalDNS metadata: name: exdns labels: f5cr: "true" spec: domainName: example.com dnsRecordType: A loadBalanceMethod: global-availability pools: - dnsRecordType: A loadBalanceMethod: round-robin order: 0 dataServerName: /Common/GSLBServer monitor: type: tcp interval: 10 timeout: 10
Examples Repository¶
Note
To provide feedback on Container Ingress Services or this documentation, please file a GitHub Issue.