F5 BIG-IP SSL Orchestrator Training Lab > All SSL Orchestrator Lab Guides > SSLO 201: Advanced Use Cases with SSL Orchestrator (Agility 2022 | 2 hours) > 4. Web Application Firewall-as-a-Service (WAFaaS) Source | Edit on
4.5. Create Existing Application L3 Inbound Topology¶
Now that we have our WAFaaS device and security chain created, we will now create an Existing Application topology that will be used to protect our vulnerable Juiceshop application.
Click on SSL Orchestrator and select Configuration
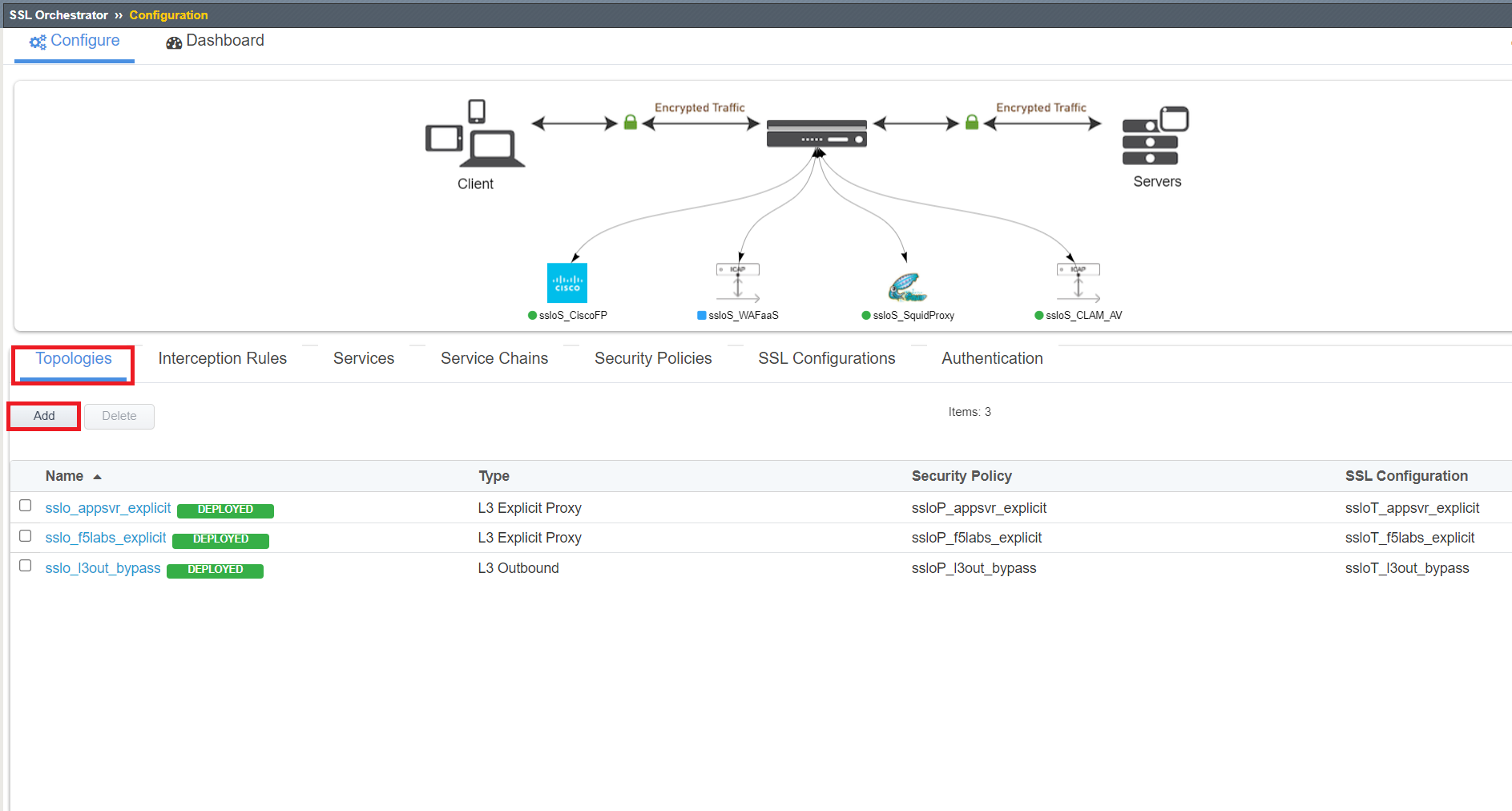
Click Add under the Topologies menu item.
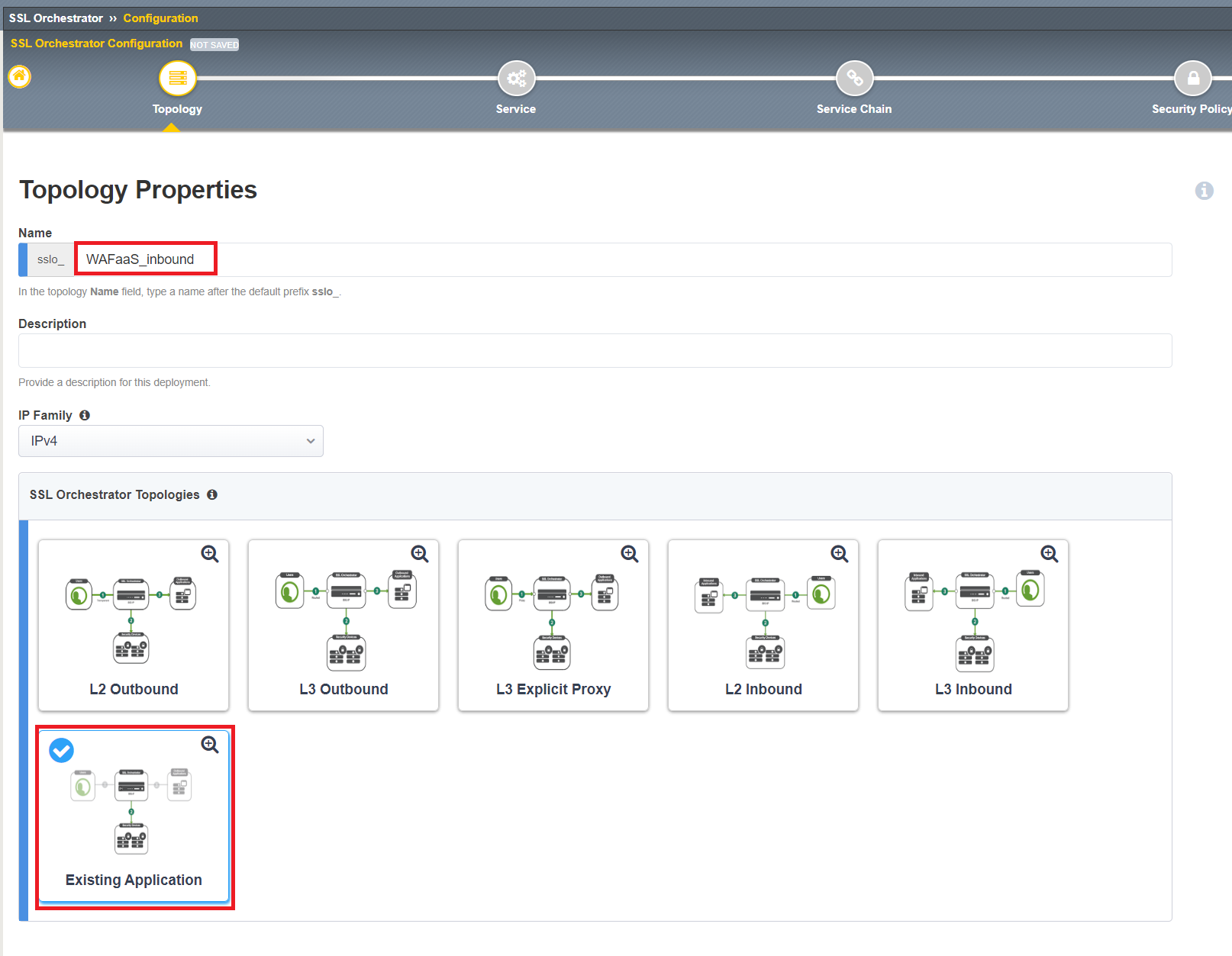
Click Next through the Topology Information page.
Next to Name,
WAFaaS_inbound. Select Existing Application under SSL Orchestrator Topologies. CLick Save & Next once complete.
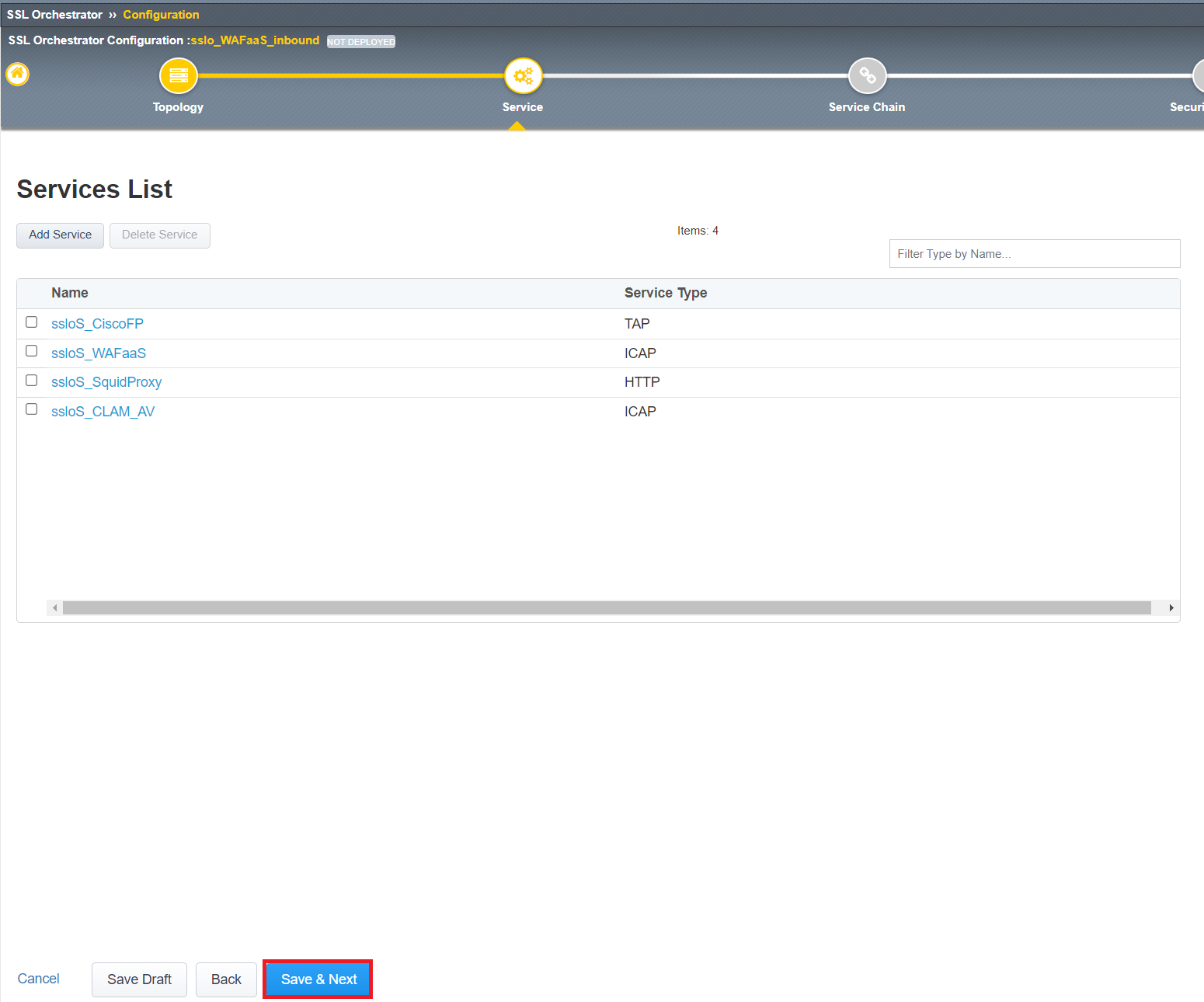
Since we already created the WAFaaS service, we can click Save & Next and go to the next page.
Since we already created the WAFaaS service chain, we can click Save & Next and go to the next page.
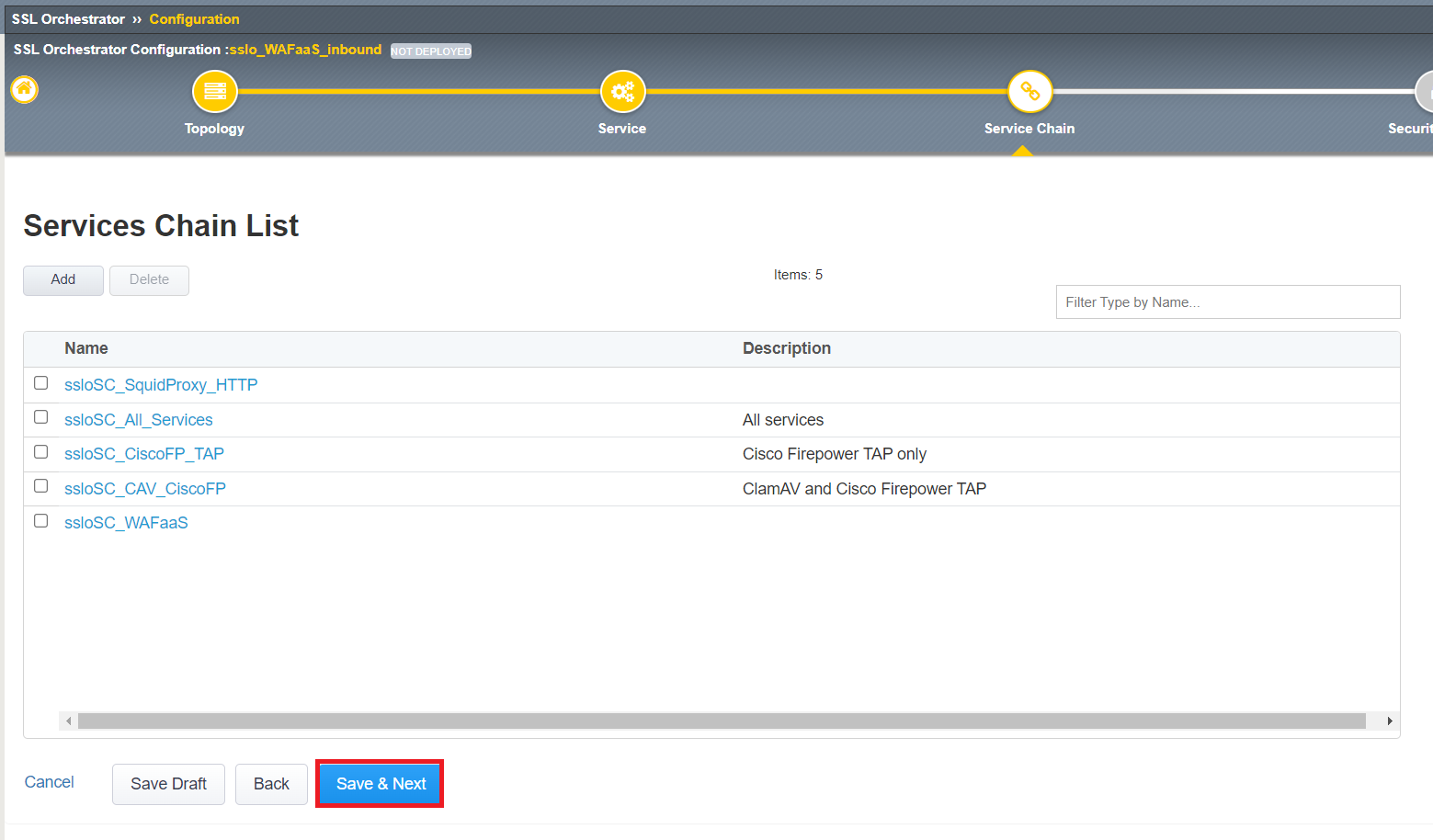
We will need to adjust the All Traffic rule for our WAFaaS_inbound security policy. Click the
 to the right of the All Traffic rule.
to the right of the All Traffic rule.
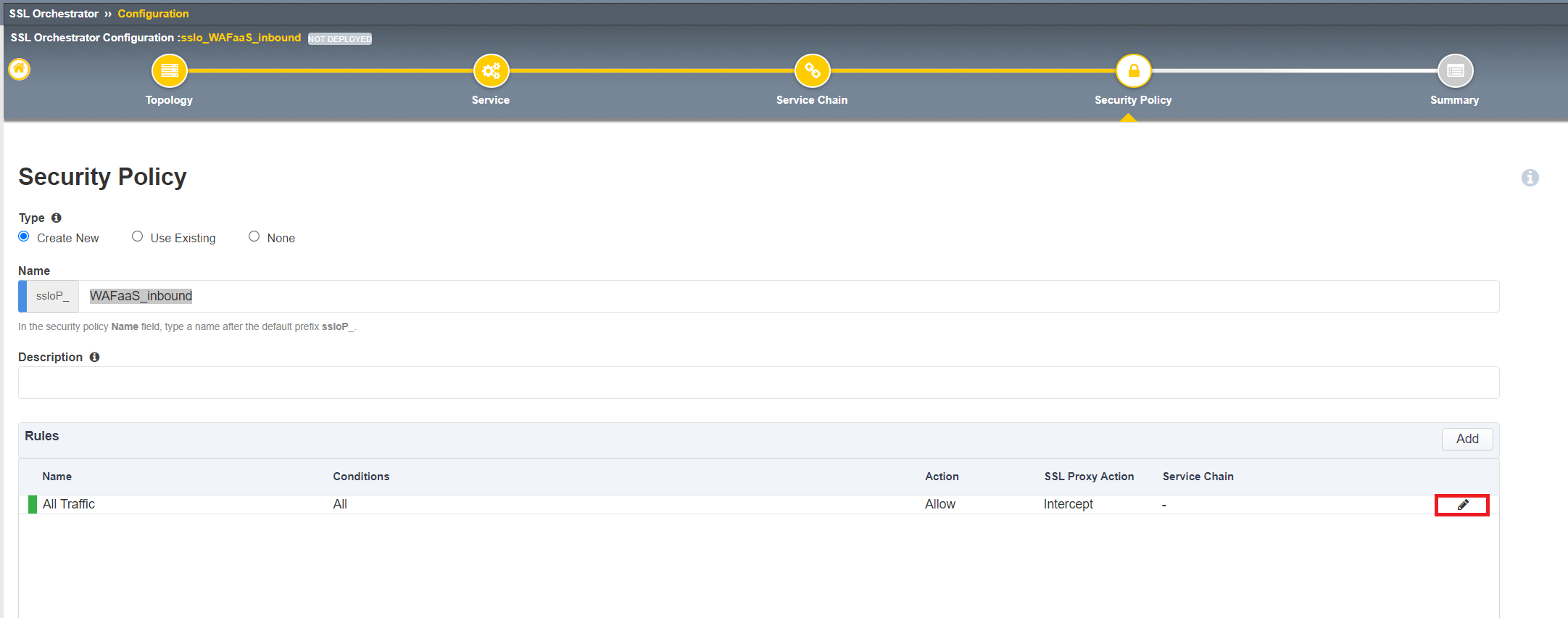
Select the ssloSC_WAFaaS under Service Chain and click OK. Click Save & Next when complete.
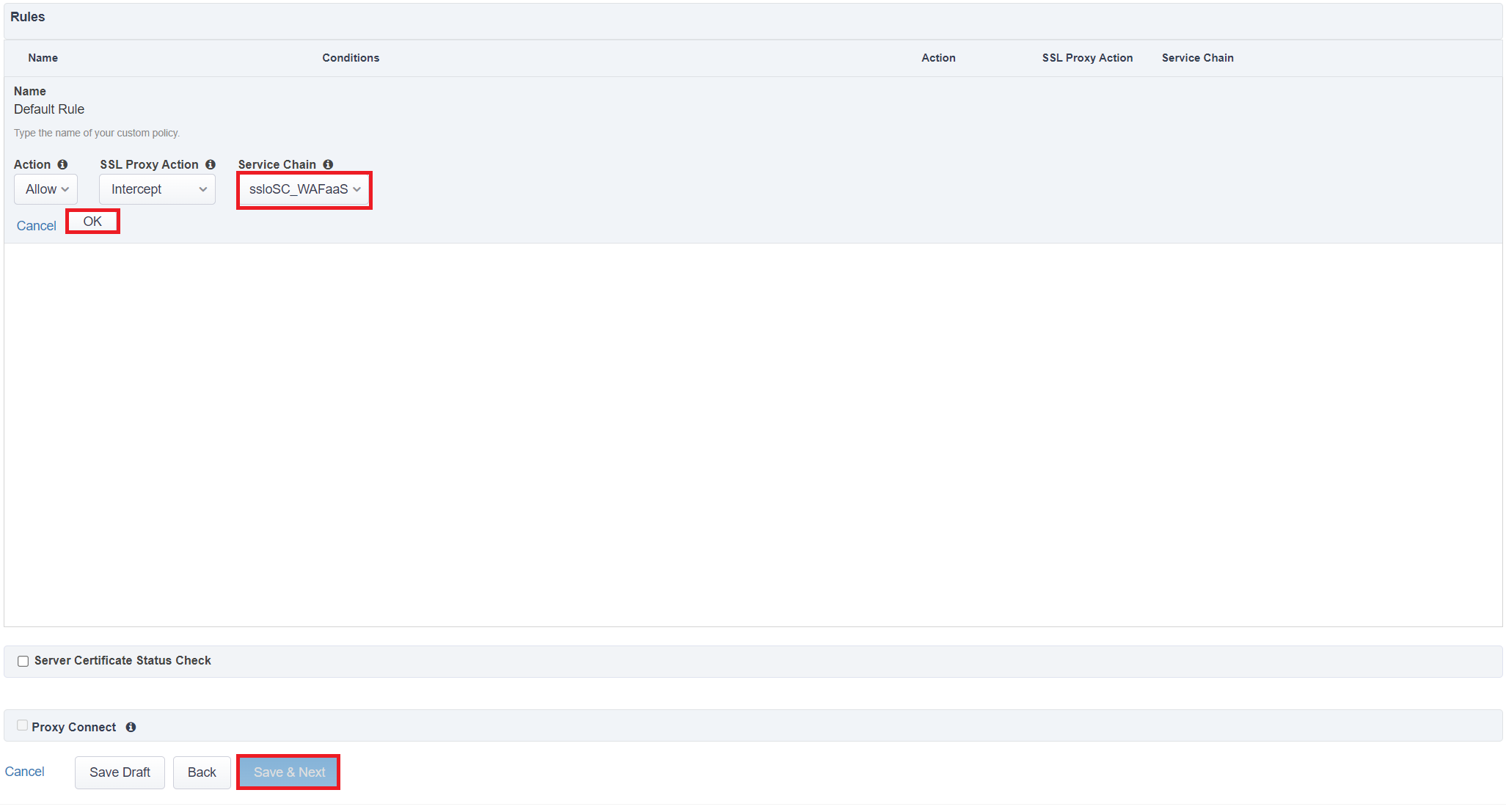
Click Deploy to deploy your new Existing Application topology.
Click OK to acknowledge the successful deployment.
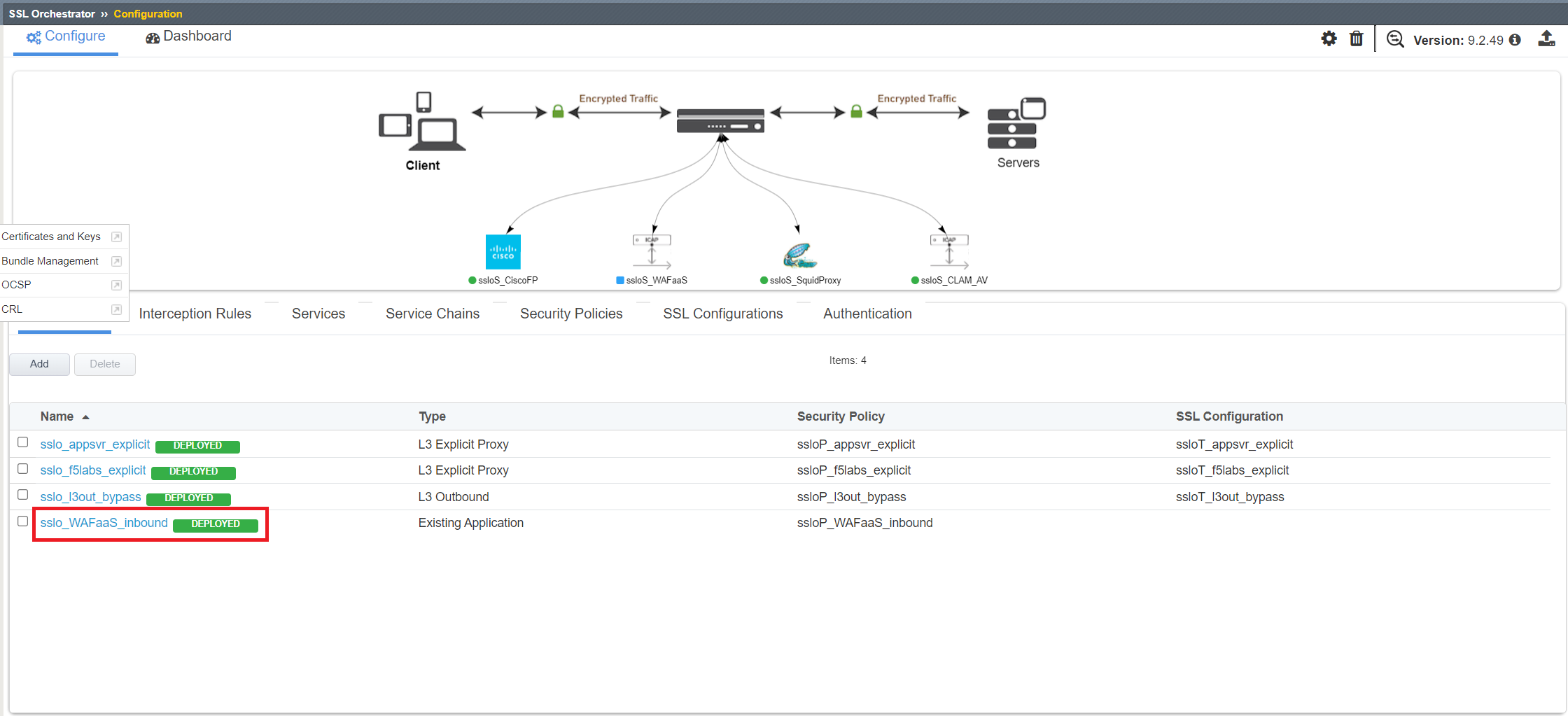
Now we just need to add the access policies associated with the WAFaaS_Inbound topology to the Juiceshop Virtual Server.
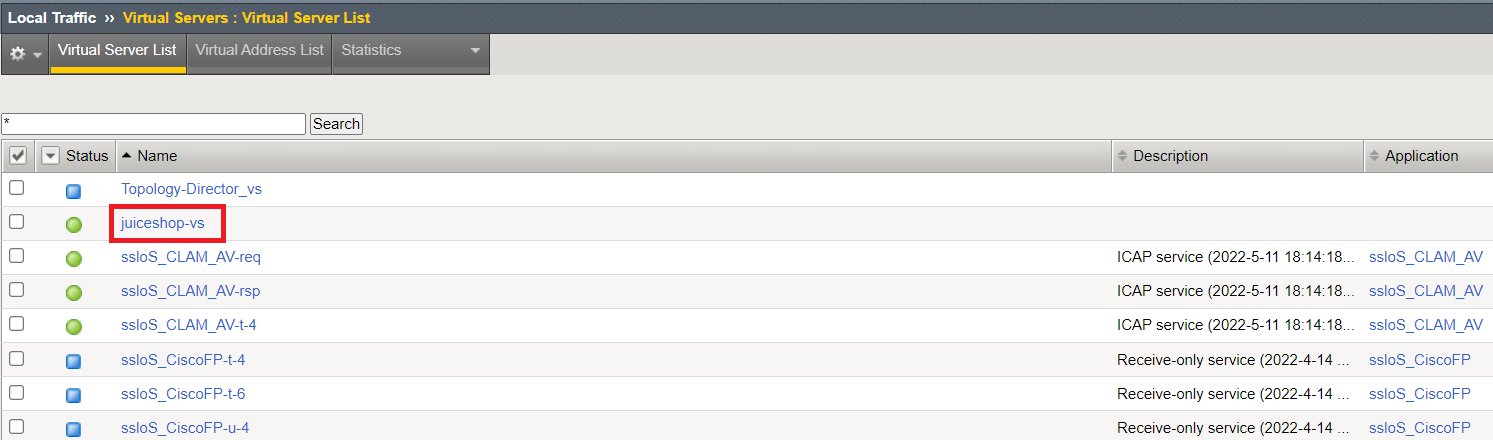
Click on Local Traffic>>Virtual Servers>>Virtual Server List. Click on the link for the juiceshop-vs virtual server.
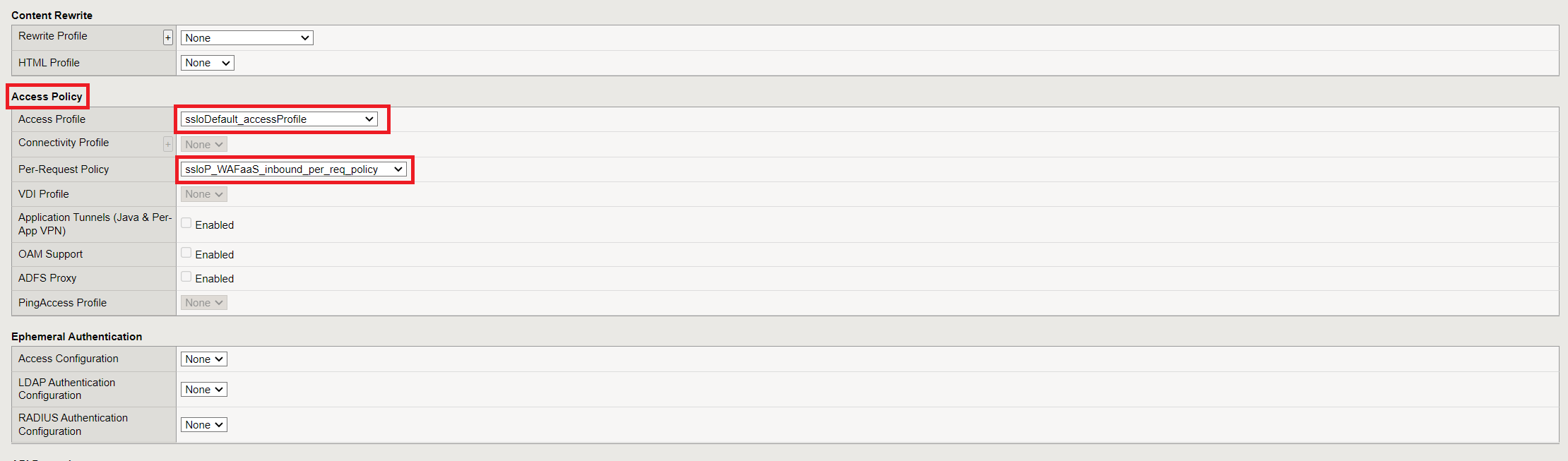
Scroll down about 3/4 of the way down the page to find the Access Policy section. Next to Access Profile, select ssloDefault_accessProfile and also select ssloP_WAFaaS_inbound_per_req_policy next to Per-Request Policy. Click Update when done.
Congratulations! You have now successfully deployed WAFaaS for an existing application. Let's now go back to the Ubuntu Client and run the same SQL-injection attack to see if WAF is doing its job.