F5 BIG-IP SSL Orchestrator Training Lab > All SSL Orchestrator Lab Guides > SSLO 201: Advanced Use Cases with SSL Orchestrator (Agility 2022 | 2 hours) Source | Edit on
1. SSL Orchestrator Lab Environment¶
1.1. Accessing the Virtual Lab¶
If you are not familiar with the process for joining a training course, refer to:
You should have received a course registration email that contains the UDF course link. Click on the link and log into the UDF student portal.
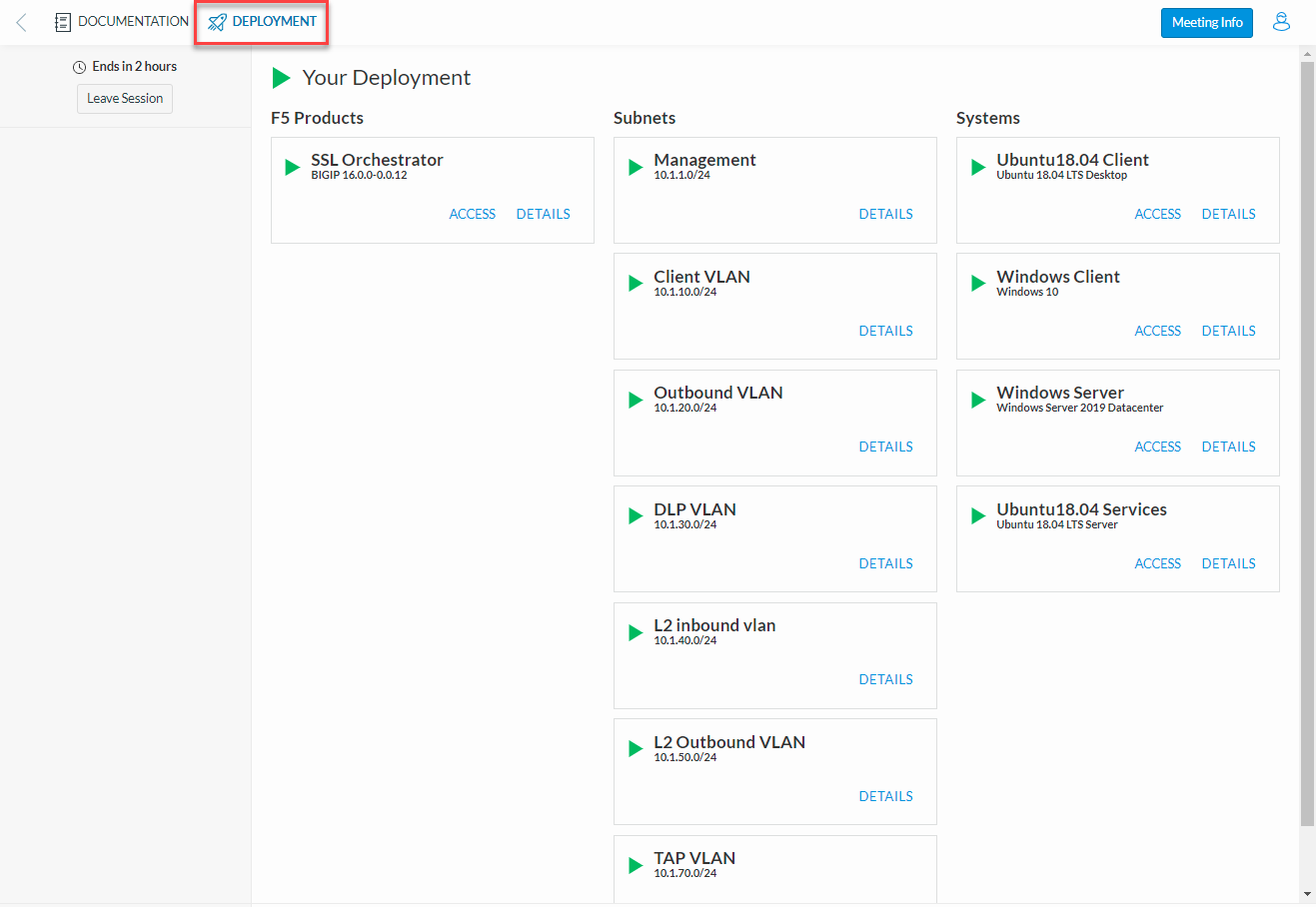
After joining the course, you will see the DOCUMENTATION tab with some information about the lab resources and a link to the Lab Guide (this document).

Note
You will use your local web browser and Remote Desktop Protocol (RDP) client to perform the lab exercises.
You will not need to use SSH to access the UDF lab environment, so no SSH Key needs to be configured.
Click on the DEPLOYMENT tab to see all of your lab resources. You will access the Ubuntu18.04 Client and Windows Client machines using RDP. You will also access the Web Shell for various systems as directed in the lab exercises.
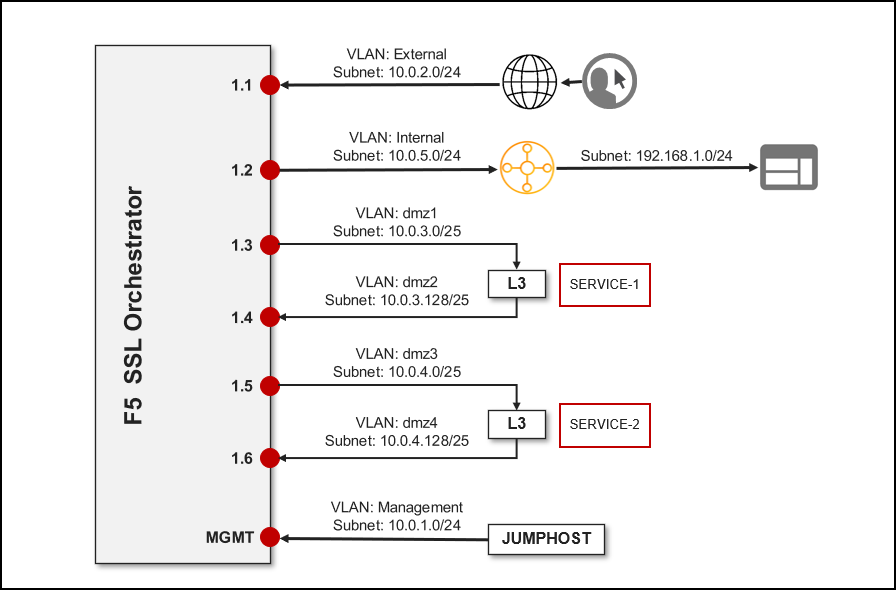
1.2. Network Diagram¶
Here is a visual representation of the Agility virtual lab environment. The numbers inside the right edge of the SSL Orchestrator box indicate the port numbers and VLAN tags (if applicable). The colored boxes to the right of the services respresent some product examples for each respective service type.
The first interface is connected to the client-facing VLAN. The second interface is connected to the Internet-facing VLAN. The remaining interfaces are connected to various types of security services: L2, L3, HTTP, ICAP, and passive Tap. The SSL Orchestrator management interface is not shown.
1.3. Virtual Lab Infrastructure Details (and Credentials)¶
The following tables provide device/service network configuration details. Login credentials are also provided for use as directed in the lab exercises.
BIG-IP Management IP |
10.1.1.4 |
|
Gateway IP/DNS |
10.1.20.1 |
|
Login |
admin:agility root:default |
|
System DNS |
10.1.10.80 (Windows DNS for NTLM/AD) |
|
Interfaces |
Client VLAN |
1.1 |
Outbound VLAN |
1.2 |
|
Inline L3, HTTP, and ICAP services |
1.3 (tagged) |
|
Inline L2 service inbound |
1.4 |
|
Inline L2 service outbound |
1.5 |
|
TAP service |
1.6 |
|
SSL Orchestrator Topology |
Name: f5labs_explicit Explicit Proxy: 10.1.10.150:3128 DNS: Forwarder - 10.1.10.80 (Explicit proxy DNS requests only) |
IP address |
10.1.10.50 |
Login |
student:agility |
IP address |
10.1.10.70 |
|
Logins |
Username |
Password |
F5LABS\mike |
agility |
|
F5LABS\jane |
agility |
IP address |
10.1.10.80 |
Login |
N/A |
Login |
student:agility |
|
Interfaces |
Inbound (TO service) interface |
1.4 |
Outbound (FROM service) interface |
1.5 |
Login |
student:agility |
||
Interfaces |
Inbound (TO service) interface |
1.3 tag 60 |
198.19.64.7/25 |
Outbound (FROM service) interface |
1.3 tag 70 |
198.19.64.245/25 |
|
Services |
NGFW |
198.19.64.30/25 |
Login |
root:default |
||
Interfaces |
Inbound (TO service) interface |
1.3 tag 30 |
198.19.96.7/25 |
Outbound (FROM service) interface |
1.3 tag 40 |
198.19.96.245/25 |
|
Services |
Squid |
Port 3128 |
198.19.96.30 |
Login |
root:default |
||
Interface |
Inbound (TO service) interface |
1.3 tag 50 |
198.19.97.1/25 |
Services |
SquidClamAV |
Port 1433 |
198.19.97.50/25 Request Modification URI Path: /avscan Response Modification URI Path: /avscan Preview Max Length: 1048576 |
Login |
root:default |
|
Interface |
Inbound (TO service) interface |
1.6 |
MAC Address |
12:12:12:12:12:12 (arbitrary if directly connected) |
Warning
Simple passwords were used in this lab environment in order to make it easier for students to access the infrastructure. This does not follow recommended security practices of using strong passwords.
This lab environment is only accessible via an authenticated student login.