Configuring Calico¶
Prerequisites¶
- BIG-IP is licensed and setup as a cluster.
- The networking setup is already complete.
- The self IP has a portlock down setup to “Allow All” OR add a TCP custom port to the self IP: TCP port 179.
Note
You can use these setup steps for IPv6 by providing the relevant IP addresses where applicable.
BIG-IP Calico Setup¶
Allow BGP on the default route domain 0 on your BIG-IP systems. Connect to the BIG-IP GUI and go to Network > Route domain. Click on Route Domain
0and allow BGP. Click Update.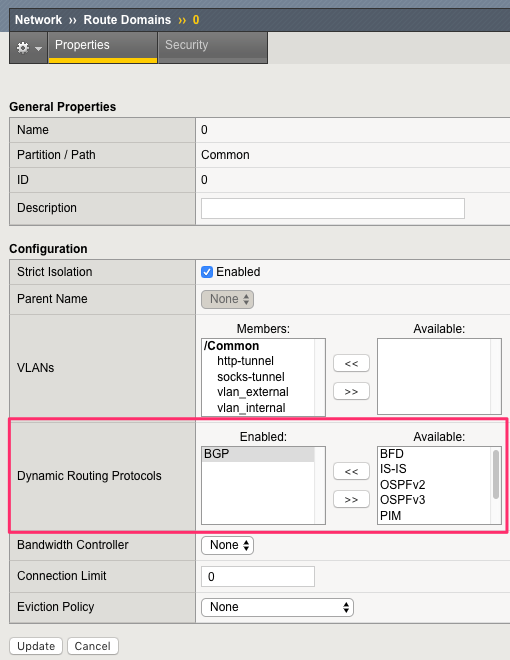
Connect via SSH on both BIG-IP systems and run the following commands:
#Access the IMI Shell imish #Switch to enable mode enable #Enter configuration mode config terminal #Setup route bgp with AS Number 64512 router bgp 64512 #Create BGP Peer group neighbor calico-k8s peer-group #Assign peer group as BGP neighbors neighbor calico-k8s remote-as 64512 #We need to add all the cluster peers: the other BIG-IP, our k8s components #For Ipv6, provide relevant ip address neighbor <CLUSTER MASTER IP ADDRESS> peer-group calico-k8s neighbor <CLUSTER WORKER1 IP ADDRESS> peer-group calico-k8s neighbor <CLUSTER WORKER2 IP ADDRESS> peer-group calico-k8s #On BIG-IP1, run neighbor <CLUSTER MASTER IP ADDRESS> peer-group calico-k8s neighbor <CLUSTER WORKER1 IP ADDRESS> peer-group calico-k8s neighbor <CLUSTER WORKER2 IP ADDRESS> peer-group calico-k8s #For multi-cluster, run below on BIG-IP2 neighbor <CLUSTER MASTER IP ADDRESS> peer-group calico-k8s neighbor <CLUSTER WORKER1 IP ADDRESS> peer-group calico-k8s neighbor <CLUSTER WORKER2 IP ADDRESS> peer-group calico-k8s #To enable ipv6 address family #Uncomment to enable IPv6 and specify either unicast or multicast #address-family ipv6 <unicast|multicast> #Activate the intended ipv6 network #Uncomment and update the following lines based on your topology #neighbor 2001:db8::8 activate #neighbor 2001:db8::9 activate #neighbor 2001:db8::7 activate #save configuration write #exit end
Review your setup by running the following command:
show ip bgp neighbors
Note
Your other BIG-IP should be identified with a router ID and have a BGP state of Active. The k8s node will not have a router ID since BGP has not already been setup on those nodes.
Kubernetes Calico Setup¶
Retrieve the
calicoctlbinary on the Master node (not root):curl -O -L https://github.com/projectcalico/calicoctl/releases/download/v3.10.0/calicoctl chmod +x calicoctl sudo mv calicoctl /usr/local/bin
Set up
calicoctl:sudo mkdir /etc/calico
Create a file /etc/calico/calicoctl.cfg with your preferred editor (you will need sudo privileges). This file should contain the following:
1 2 3 4 5 6 | apiVersion: projectcalico.org/v3 kind: CalicoAPIConfig metadata: spec: datastoreType: "kubernetes" kubeconfig: "/home/ubuntu/.kube/config" |
Note
You may have to change the path specified by the kubeconfig parameter based on the user you use to run the kubectl command. In this example the user is .kube.
To verify that
calicoctlis properly set up, run the following command:calicoctl get nodes
Setup the Calico/BGP configuration on the Master node by running the following command:
1 2 3 4 5 6 7 8 9 10 | cat << EOF | calicoctl create -f - apiVersion: projectcalico.org/v3 kind: BGPConfiguration metadata: name: default spec: logSeverityScreen: Info nodeToNodeMeshEnabled: true asNumber: 64512 EOF |
Set up the BIG-IP BGP peers by replacing the
peerIPvalue with the IP of your BIG-IP systems:cat << EOF | calicoctl create -f -
1 2 3 4 5 6 7 8 | apiVersion: projectcalico.org/v3 kind: BGPPeer metadata: name: bgppeer-global-bigip1 spec: peerIP: 10.1.20.11 asNumber: 64512 EOF |
1 2 3 4 5 6 7 8 9 | cat << EOF | calicoctl create -f - apiVersion: projectcalico.org/v3 kind: BGPPeer metadata: name: bgppeer-global-bigip2 spec: peerIP: 10.1.20.12 asNumber: 64512 EOF |
Review your setup by running the following command:
calicoctl get bgpPeer
Troubleshooting¶
- Once the configuration is done, check whether the routes are properly added with
show ip bgp neighbors. - Check for
BGP state = Establishedin the output to verify connection with k8s node neighbors.
Note
To provide feedback on Container Ingress Services or this documentation, please file a GitHub Issue.