Configuring Multiple Watch Namespace¶
New in version 1.6.0: Ability to specify multiple watchNamespace when installing SPK Controller.
One controller configurable parameter when installing the SPK Controller is setting the watchNamespace spec which tells the controller to watch for events from specific namespaces where the application are deployed. On versions prior to 1.6.0, the administrator can only specify one watchNamespace. But starting on SPK version 1.6.0, the administrator can specifics multiple watchNamspace.
Note
The SPK Controller contains multiple pods. We will refer to the controller pod as f5ingress.
As the number of backend applications grow, the need to deploy them to different namespaces may be preferred over all applications within one namespace. Some reason why you want to do this are:
For organizational purposes
Isolate different applications depending on your business logic
Take advantage of the native k8s RBAC to restrict permissions to specific namespaces
The following guide details this new feature and walks through a use case where you may want to specify multiple namespaces. This field can be specified in the controller.watchNamespace spec when doing the helm install.
The guide here will take you through:
Configuring an SPK Controller deployment to use multiple
watchNamespaceDeploying a demo application to each namespace being watched by f5ingress
Warning
If you don’t set the watchNamespace field, f5ingress will watch ALL namespaces.
Prerequisites / Assumptions¶
Installation knowledge via Helm
SPK Controller Installation knowledge
SPK CR knowledge
The example used in this guide is f5-spk-ingressgtps.
This guide will be making the following network assumptions:
External subnet: 10.40.57.0/24
Internal subnet (node to node communication): 172.20.1.0/24
High Level Overview¶
A high level view of the deployment in this guide is shown below. Some notes:
One SPK Controller deployment
Multiple namespaces for our demo application
Two namespaces with an application pod serving TCP ingress traffic
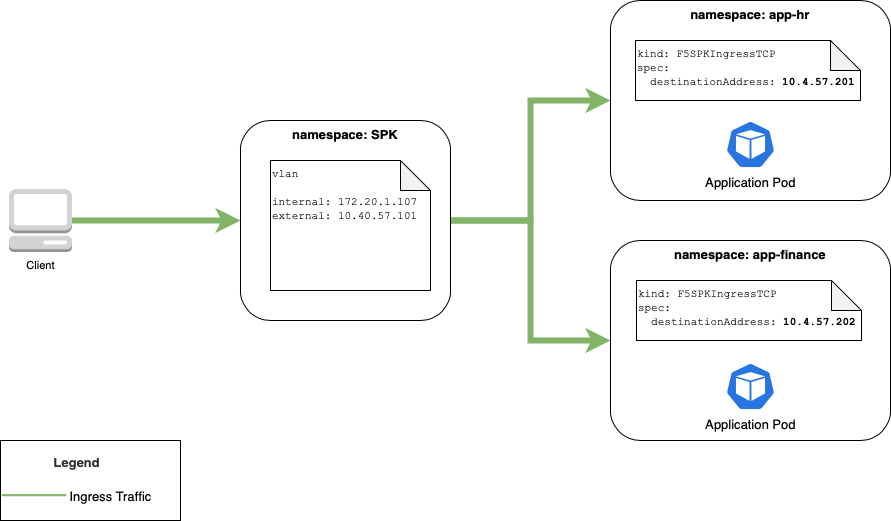
Figure 1: SPK Controller Deployment with multiple watchNamespaces configuration.¶
SPK Controller Configuration¶
When installing the SPK Controller with multiple watchNamespace, provide a list of namespaces where your application will be deployed. Below is an example snippet of the values.yaml file used during the install.
controller:
watchNamespace:
- app-hr
- app-finance
Note
You must know which namespaces you want to watch before installing SPK Controller. If you need to add additional namespaces, you will need to redeploy SPK Controller.
Refer to the SPK Controller Install section.
Watch Namespaces Configuration¶
This section of the guide will do the following:
Deploy the demo application to two different namespaces
Configure SPK so the correct traffic is allowed to the demo applications
This section will be using podinfo as the demo application to install.
The two namespaces being created are:
app-hr
app-finance
Take the steps below to create and deploy the demo application:
Creating two namespaces
oc create ns app-hr oc create ns app-finance
Installing a demo application, podinfo, for each namespace. A different version will be used to help keep track which version is installed in each namespace.
helm repo add podinfo https://stefanprodan.github.io/podinfo helm -n app-hr install podinfo-6-0-0 podinfo/podinfo --version 6.0.0 helm -n app-finance install podinfo-6-1-0 podinfo/podinfo --version 6.1.0
Create an SPK config to allow TCP Ingress to the demo application in app-hr.
cat << EOF| oc create -f - apiVersion: "ingresstcp.k8s.f5net.com/v1" kind: F5SPKIngressTCP metadata: # name of the Virtual Server name: app-hr-ingress-tcp # namespace of application namespace: app-hr service: # Name of the installed ServicePort for podinfo app Pod name: podinfo-6-0-0 # ServicePort of podinfo app Pod port: 9898 spec: # The address of the Virtual Server # can be v4 or v6, or "dual stack" for both. destinationAddress: "10.40.57.201" ipv6destinationAddress: "" # The port used along with IP address above destinationPort: 9001 # Add a monitor that will mark the backend service down if it fails 3 pings in a row. monitors: icmp: - failures: 3 EOF
Create an SPK config to allow TCP Ingress to the demo application in app-finance.
cat << EOF| oc create -f - apiVersion: "ingresstcp.k8s.f5net.com/v1" kind: F5SPKIngressTCP metadata: # name of the Virtual Server name: app-finance-ingress-tcp # namespace of application namespace: app-finance service: # Name of the installed ServicePort for podinfo app Pod name: podinfo-6-1-0 # ServicePort of podinfo app Pod port: 9898 spec: # The address of the Virtual Server # can be v4 or v6, or "dual stack" for both. destinationAddress: "10.40.57.202" ipv6destinationAddress: "" # The port used along with IP address above destinationPort: 9001 # Add a monitor that will mark the backend as down if it fails 3 pings in a row. monitors: icmp: - failures: 3 EOF
Confirming Use Case¶
Once the entire configuration is created, you should be able to verify end-to-end traffic. In the case here, I should be able to pass ingress traffic from a client outside the cluster.
Below is an example of passing traffic from the external client to a demo application.
Passing traffic from the client located outside the cluster to the demo application deployed in app-hr and app-finance.
# Test ingress tcp traffic to demo application in app-hr $ curl http://10.40.57.201:9001 { "hostname": "podinfo-6-0-0-647cb69dbc-gp88j", "version": "6.0.0", "revision": "", "color": "#34577c", "logo": "https://raw.githubusercontent.com/stefanprodan/podinfo/gh-pages/cuddle_clap.gif", "message": "greetings from podinfo v6.0.0", "goos": "linux", "goarch": "amd64", "runtime": "go1.16.5", "num_goroutine": "8", "num_cpu": "28" } # Test ingress tcp traffic to demo application in app-finance $ curl http://10.40.57.202:9001 { "hostname": "podinfo-6-1-0-6d9d54b9d5-6sxnf", "version": "6.1.0", "revision": "", "color": "#34577c", "logo": "https://raw.githubusercontent.com/stefanprodan/podinfo/gh-pages/cuddle_clap.gif", "message": "greetings from podinfo v6.1.0", "goos": "linux", "goarch": "amd64", "runtime": "go1.17.8", "num_goroutine": "8", "num_cpu": "30" }
Below is a diagram showing the basic traffic flow from the client to the application pod.
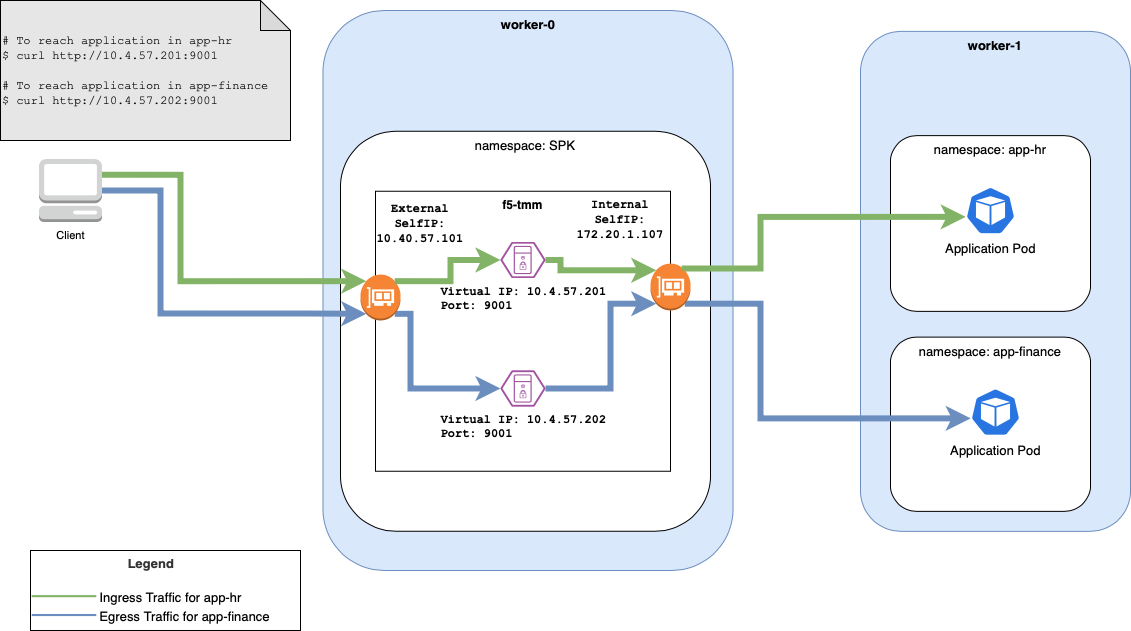
Figure 2: Traffic flow from client to application.¶
Confirming Watch Namespaces¶
Take the following steps below to confirm multiple watch namespaces were specified. You should see a log output specifying the namespaces you’ve configured. So in this case here, they are app-finance and app-hr.
oc logs <f5ingressPod> -c f5ingress-f5ingress
...
Watched application namespaces: [app-finance app-hr]