F5BigCneSnatpool¶
Overview¶
The F5BigCneSnatpool Custom Resource (CR) configures the Traffic Management Microkernel (TMM) Proxy Pod to perform source network address translations (SNAT) on egress network traffic. When clients connect to resources through TMM, the source IP address of the egress packet is translated to one of the IP addresses in the SNAT pool. Once configured and installed, the F5BigCneSnatpool CR can be referenced by the F5BigContextSecure and F5BigDnsApp CRs to process traffic.
This document guides you through understanding, configuring and deploying a simple F5BigCneSnatpool CR.
Scaling TMM¶
When scaling the TMM Proxy Pod beyond a single instance in the namespace, the F5BigCneSnatpool CR must be configured to provide a SNAT pool to each TMM replica. The first SNAT pool is applied to the first TMM replica, the second snatpool to the second TMM replica, continuing through the list.
 Important: When configuring SNAT pools with multiple IP subnets, ensure all TMM replicas receive the same IP subnets.
Important: When configuring SNAT pools with multiple IP subnets, ensure all TMM replicas receive the same IP subnets.
Example CR:
apiVersion: "k8s.f5net.com/v1"
kind: F5BigCneSnatpool
metadata:
name: "egress-snatpool"
namespace: cnf-gateway
spec:
name: "egress_snatpool"
addressList:
- - 10.244.10.1
- 10.244.20.1
- 2002::10:244:10:1
- 2002::10:244:20:1
- - 10.244.10.2
- 10.244.20.2
- 2002::10:244:10:2
- 2002::10:244:20:2
CR shortName¶
CR shortNames provide an easy way to view installed CRs, and their configuration parameters. The CR shortName can also be used to delete the CR instance. The F5BigCneSnatpool CR shortName is snatpool.
View CR instance:
oc get snatpool -n <namespace>
View CR configuration:
oc get snatpool -n <namespace> -o yaml
Example deployment:
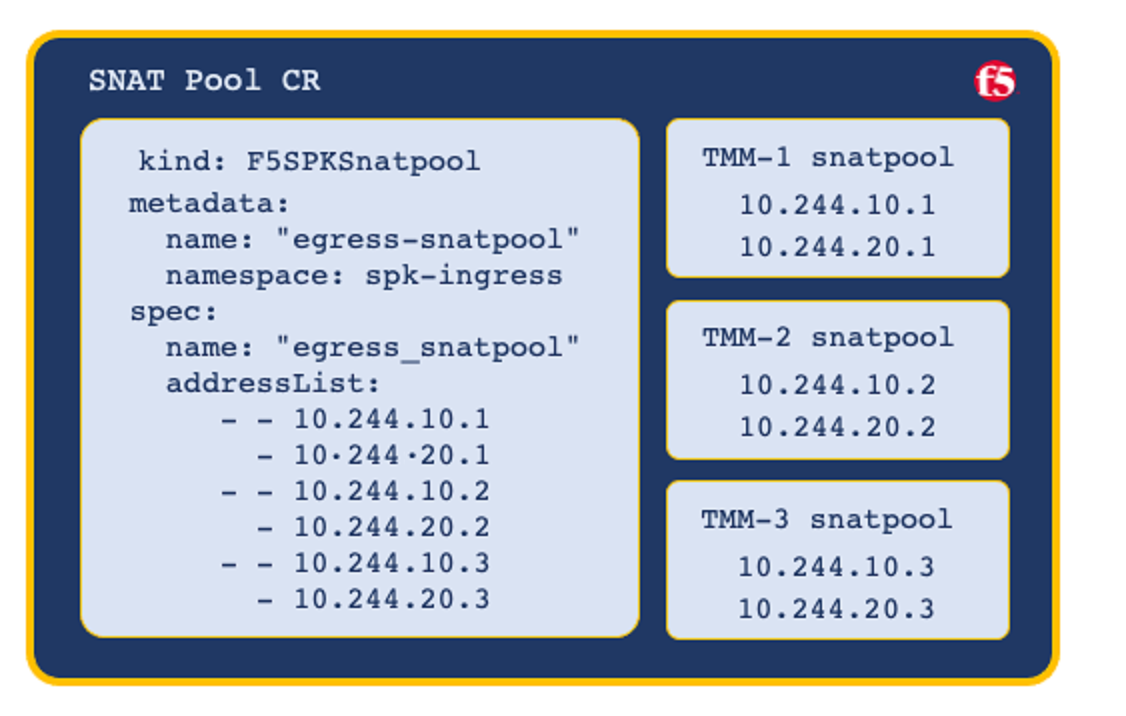
 Note: The SNAT Pool CR supports both IPv4 and IPv6 addresses.
Note: The SNAT Pool CR supports both IPv4 and IPv6 addresses.
Advertising address lists¶
By default, SNAT Pool IP addresses are not advertised (redistributed) to BGP neighbors. To advertise SNAT Pool IP addresses, you must configure a prefixList and routeMaps when installing the BIG-IP Controller. For configuration assistance, refer to the BGP Overview.
Requirements¶
Ensure you have:
- Created an external and internal F5BigNetVlan.
- A Linux based workstation.
Installation¶
Use the following steps to install the example F5BigCneSnatpool CR.
Copy the example F5BigCneSnatpool into a YAML file:
apiVersion: "k8s.f5net.com/v1" kind: F5BigCneSnatpool metadata: name: "egress-snatpool" namespace: cnf-gateway spec: name: "egress_snatpool" addressList: - - 10.244.10.1 - 10.244.20.1 - 2002::10:244:10:1 - 2002::10:244:20:1 - - 10.244.10.2 - 10.244.20.2 - 2002::10:244:10:2 - 2002::10:244:20:2
Install the F5BigCneSnatpool CR:
oc apply -f cnf-snatpool-crd.yaml
In this example, the BIG-IP Controller logs indicate the F5BigCneSnatpool CR was added/updated:
I0202 12:00:00:12350 1 event.go:282] Event(v1.ObjectReference{Kind:"F5SecureContext", F5Snatpool cnf-gateway/46_snatpool was added/updated
To verify the SNAT pool IP address mappings, obtain the name of the Controller’s persistmap:
 Note: The persistmap maintains SNAT mappings after unexpected Pod restarts.
Note: The persistmap maintains SNAT mappings after unexpected Pod restarts.oc get cm -n cnf-gateway | grep persistmap
persistmap-76946d464b-d5xvcVerify the SNAT IP address mappings:
oc get cm persistmap-76946d464b-d5xvc \ -o "custom-columns=IP Addresses:.data.snatpoolMappings" -n cnf-gateway
In this example, the SNAT IPs allocated to TMM are 10.244.10.1, 10.244.20.1, 2002::10:244:10:1 and 2002::10:244:20:1.
IP Addresses {"ca93c77b-42bb-4b67-bf3a-d25128f3374b":"10.244.10.1,10.244.20.1,2002::10:244:1:10,2002::10:244:20.1"}
The example F5BigContextSecure CR listens for connections destined to IP addresses in the 2002::200:200:200:0/112 subnet, and only on the subscriber-vlan interface. The CR also references the F5BigCneSnatpool profile. Copy and paste the example into a YAML file:
apiVersion: k8s.f5net.com/v1 kind: F5BigContextSecure metadata: name: "cnf-context" namespace: "cnf-gateway" spec: ipv6destinationAddress: "2002::200:200:200:0/112" destinationPort: 0 ipProtocol: "tcp" profile: "tcp" snat: type: "snat" pool: "egress_snatpool" vlans: vlanList: - "subscriber-vlan"
Install the F5BigContextSecure CR:
oc apply -f f5-cnf-context.yaml
In this example, the BIG-IP Controller logs indicate the F5BigContextSecure CR was added/updated:
I0202 12:00:00:12350 1 event.go:282] Event(v1.ObjectReference{Kind:"F5SecureContext", SecureContext cnf-gateway/cnf-context was added/updated
Continue to the Next step section to begin using the F5BigCneSnatpool.
Next step¶
Select and install one of the Traffic Management CNF CRs to begin processing application traffic:
- F5BigContextSecure - Full proxy TCP and UDP application layer gateway services.
- F5BigDnsApp - High-performance DNS resolution and caching.
Feedback¶
Provide feedback to improve this document by emailing cnfdocs@f5.com.