F5BigZeroratingPolicy¶
Overview¶
The F5BigZeroratingPolicy Custom Resource (CR) is an integral part of the Cloud-Native Network Functions (CNFs) Zero-Rating DNS solution; enabling subscriber access to applications with no impact, or increase, to billing quotas. CNFs Zero-Rating solution accomplishes this by steering application traffic using split-view DNS. When configured as a DNS resolver, the Traffic Management Microkernel (TMM) Proxy Pod provides clientside DNS responses using custom IP addresses, bypassing quota management, then resolving and routing traffic to the DNS domain name on the serverside.
The CNFs Zero-Rating solution requires the CRs listed below:
- F5BigDatagroup
- F5BigDnsCache
- F5BigDnsApp
- F5BigContextSecure
This document guides you through understanding, configuring and installing a simple CNFs Zero-Rating solution.
Zero-Rating example:
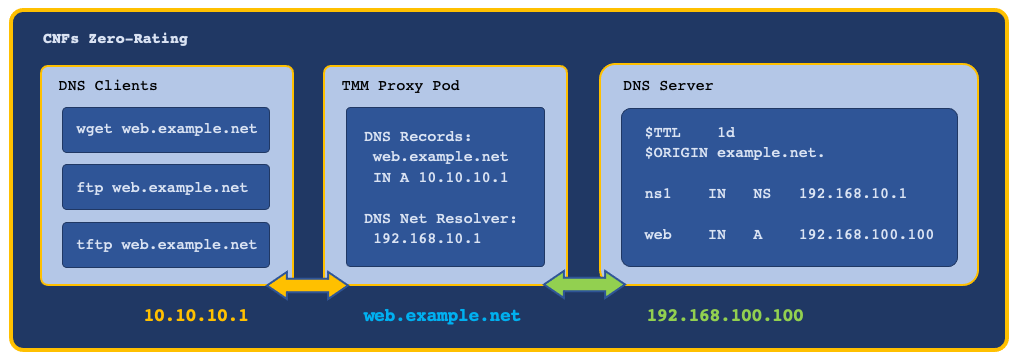
CR parameters¶
F5BigZeroratingPolicy¶
The table below describes the F5BigZeroratingPolicy CR spec parameters.
| Parameter | Description |
|---|---|
dnsResolver |
Specifies the F5BigDnsCache by metadata.name that will be used by TMM will resolve and cache external DNS queries. |
dataGroup |
Specifies the F5BigDatagroup CR by metadata.name that will provide IP address to domain name mapping. |
debugZeroRating |
Enables zero rating policy logging: true or false (default). |
F5BigDatagroup¶
The table below describes the F5BigDatagroup CR spec parameters.
| Parameter | Description |
|---|---|
recordType |
Specifies the type of the datagroup record. The current available option is address. |
records |
Specifies a list of key and value pairs. The key represents an IPv4 or IPv6 address, and the value represents the domain name. |
CR shortName¶
CR shortNames provide an easy way to view installed CRs, and their configuration parameters. The CR shortName can also be used to delete the CR instance. The F5BigContextSecure CR shortName is secctx.
View CR instance:
oc get secctx -n <namespace>
View CR configuration:
oc get secctx -n <namespace> -o yaml
Installation¶
Use the following steps to install the F5BigDnsApp and F5BigDnsCache CRs that will create a DNS record in the transparent cache for the domain example.com..
 Tip: Open a second shell to view the CNFs Event Logs while installing.
Tip: Open a second shell to view the CNFs Event Logs while installing.
The F5BigDatagroup CR defines the clientside domain name to IP address mappings. Copy the example CR into a YAML file:
Note: The CR provides IPv4 and IPv6 clientside mappings for the web.example.net domain name.
apiVersion: "k8s.f5net.com/v1" kind: F5BigDatagroup metadata: name: "cnf-datagroup" namespace: "cnf-gateway" spec: recordType: "address" records: [ { "key": "10.20.2.37", "value": "web.example.net" }, { "key": "2002::10:20:2:37", "value": "v6web.example.net" } ]
The transparent F5BigDnsCache CR defines the DNS record types for the clientside mappings. Copy the example transparent F5BigDnsCache CR into a YAML file:
Note: The CR defines the DNS A and AAAA DNS record types for the clientside mappings.
apiVersion: "k8s.f5net.com/v1" kind: F5BigDnsCache metadata: name: "cnf-transparent-cache" namespace: "cnf-gateway" spec: cacheType: transparent transparent: localZones: - name: example.net zoneType: static records: - web.example.net. IN A 10.20.2.37 - v6web.example.net. IN AAAA 2002::10:20:2:37
Install the F5BigDatagroup CR:
oc apply -f cnf-datagroup-cr.yaml
In this example, the BIG-IP Controller logs indicate the F5BigDatagroup CR was added/updated:
I0223 12:00:00.12345 1 event.go:282] Event(v1.ObjectReference{Kind:\"F5BigDatagroup\", F5BigDatagroup cnf-gateway/cnf-datagroup was added/updated
Install the transparent F5BigDnsCache CR:
oc apply -f cnf-transparent-dns.yaml
In this example, the BIG-IP Controller logs indicate the F5BigDnsCache CR was added/updated:
I0208 12:00:00.12345 1 event.go:282] Event(v1.ObjectReference{Kind:"F5Dnscache", F5Dnscache cnf-gateway/cnf-transparent-cache was added/updated
The net-resolver F5BigKDnsCache CR defines both a domain name, and the domain name server to query. Copy one of the example F5BigDnsCache CRs into a YAML file: Example 1 queries and caches all domains, while Example 2 queries and caches two specific domains:
Example 1:
apiVersion: "k8s.f5net.com/v1" kind: F5BigDnsCache metadata: name: cnf-resolver-cache namespace: cnf-gateway spec: cacheType: net-resolver netResolver: forwardZones: - forwardZone: . nameServers: - ipAddress: 10.30.2.1 port: 53
Example 2:
apiVersion: "k8s.f5net.com/v1" kind: F5BigDnsCache metadata: name: cnf-resolver-cache namespace: cnf-gateway spec: cacheType: net-resolver netResolver: forwardZones: - forwardZone: example.net nameServers: - ipAddress: 10.30.2.1 port: 53 - forwardZone: internal.org nameServers: - ipAddress: 10.10.10.1 port: 53
Install the net-resolver F5BigDnsCache CR:
oc apply -f cnf-netresolv-dns.yaml
In this example, the BIG-IP Controller logs indicate the F5BigDnsCache CR was added/updated:
I0208 12:00:00.12345 1 event.go:282] Event(v1.ObjectReference{Kind:"F5Dnscache", F5Dnscache cnf-gateway/cnf-resolver-cache was added/updated
The F5BigZeroratingPolicy CR groups the clientside domain name mappings and the serverside DNS resolver. Copy the example F5BigZeroratingPolicy CR into a YAML file:
apiVersion: "k8s.f5net.com/v1" kind: F5BigZeroratingPolicy metadata: name: "cnf-zerorate-policy" namespace: "cnf-gateway" spec: dnsResolver: "cnf-resolver-cache" dataGroup: "cnf-datagroup" debugZeroRating: true
Install the F5BigZeroratingPolicy CR:
oc apply -f cnf-zerorate-cr.yaml
In this example, the BIG-IP Controller logs indicate the F5BigZeroratingPolicy CR was added/updated:
I0223 12:00:00.12345 1 event.go:282] Event(v1.ObjectReference{Kind:\"F5BigZeroratingPolicy\", F5SPKZERORATINGPOLICY cnf-gateway/cnf-zerorate-policy was added/updated
The F5BigDnsApp CR specifies the IP address that subscribers will use to resolve DNS. The CR also references the transparent F5BigDnsCache CR. Copy the example F5BigDnsApp CR into a YAML file:
apiVersion: "k8s.f5net.com/v1" kind: F5BigDnsApp metadata: name: "cnf-dnsapp" namespace: "cnf-gateway" spec: destination: address: "10.20.22.94" port: 53 ipProtocol: "udp" dns: useLocalBind: false dnsCache: "cnf-transparent-cache" udp: allowNoPayload: true
Install the F5BigDnsApp CR:
oc apply -f cnf-dnsapp-cr.yaml
In this example, the BIG-IP Controller logs indicate the F5BigDnsApp CR was added/updated:
I0224 12:00::00.12345 1 event.go:282] Event(v1.ObjectReference{Kind:\"F5Dns\", F5Dns cnf-gateway/cnf-dnsapp was added/updated
The F5BigContextSecure CR will process subscriber application traffic. The CR also references the F5BigZeroratingPolicy CR. Copy the example F5BigContextSecure CR into a YAML file:
 Important: Set the
Important: Set the destinationAddressandipv6destinationAddressto the IP address subnets used in the DNS mappings.apiVersion: "k8s.f5net.com/v1" kind: F5BigContextSecure metadata: name: "cnf-secure-context" namespace: "cnf-gateway" spec: destinationAddress: "10.20.2.37/32" ipv6destinationAddress: "2002::10:20:2:37/128" destinationPort: 80 ipProtocol: "tcp" profile: "tcp" iRules: [ "cnf-zerorate-policy" ]
Install the F5BigContextSecure CR:
oc apply -f cnf-context-cr.yaml
In this example, the BIG-IP Controller logs indicate the F5BigContextSecure CR was added/updated:
I0224 12:00::00.12345 1 event.go:282] Event(v1.ObjectReference{Kind:\"F5SecureContext\", SecureContext cnf-gateway/cnf-secure-context was added/updated
Traffic statistics¶
If you installed the CNF Controller with the Debug Sidecar enabled, connect to the sidecar to view the DNS statistics.
Log in to the TMM debug Pod:
In this example, the TMM debug container is in the cnf-gateway namespace:
oc exec -it deploy/f5-tmm -c debug -n cnf-gateway -- bash
Verify the DNS statistics:
tmctl -d blade dns_cache_resolver_stat -s name,cache_index,queries,responses,responses_rate
name cache_index queries responses responses_rate --------------------------------- ----------- ------- --------- -------------- cnf-gateway-cnf-resolver-cache 0 9 9 0 cnf-gateway-cnf-transparent-cache 0 13 13 0
Verify the Application traffic statstics:
tmctl -d blade virtual_server_stat -s name,clientside.tot_conns
name clientside.tot_conns ----------------------------------------------- -------------------- cnf-gateway-cnf-secure-context-SecureContext_vs 5 cnf-gateway-cnf-secure-context-SecureContext_vs 4 cnf-gateway-big-dns-virtual_server 9
Feedback¶
Provide feedback to improve this document by emailing cnfdocs@f5.com.