Secure SPK Deployment¶
Overview¶
 Note: Firewall features introduced on SPK 1.8.0.
Note: Firewall features introduced on SPK 1.8.0.
Service Proxy for Kubernetes (SPK) can deploy security functions starting on SPK 1.8.0. The ones introduced here contains Firewall CRDs which monitors ingress and egress traffic. They are based on rules or policies defined by source and/or destination IP addresses, ports, and protocols. The firewall actions can be set to accept, reject, or drop packets. Even though this guide mentions ingress and egress traffic, there is not explicit config for ingress and egress in the CRDs. You can think of these firewall policies are being enforced at the L4 layer.
The firewall CRDs introduced can be found in the SPK Firewall CRDs: Secure SPK section of the SPK CRs page.
Requirements¶
Ensure you have:
- Installed the SPK Cert Manager
- Installed the SPK Software
- Installed the SPK CWC
- Installed the RabbitMQ Pod
- Installed Licensed SPK
- Deployed app in SPK watch namespace
- TCP App used as example in this guide
- Enabled ingress traffic
- F5SPKIngressTCP used as example in this guide
- Enabled egress traffic using F5SPKEgress CR
- Configured SPK network specific configurations, such as F5SPKVlan
- Access to K8S Cluster with SPK
- (Optional) Remote syslog server
Diagram¶
This guide will assume the following SPK configurations and the overall infrastructure. The network IP address examples used will be also be based from this diagram.
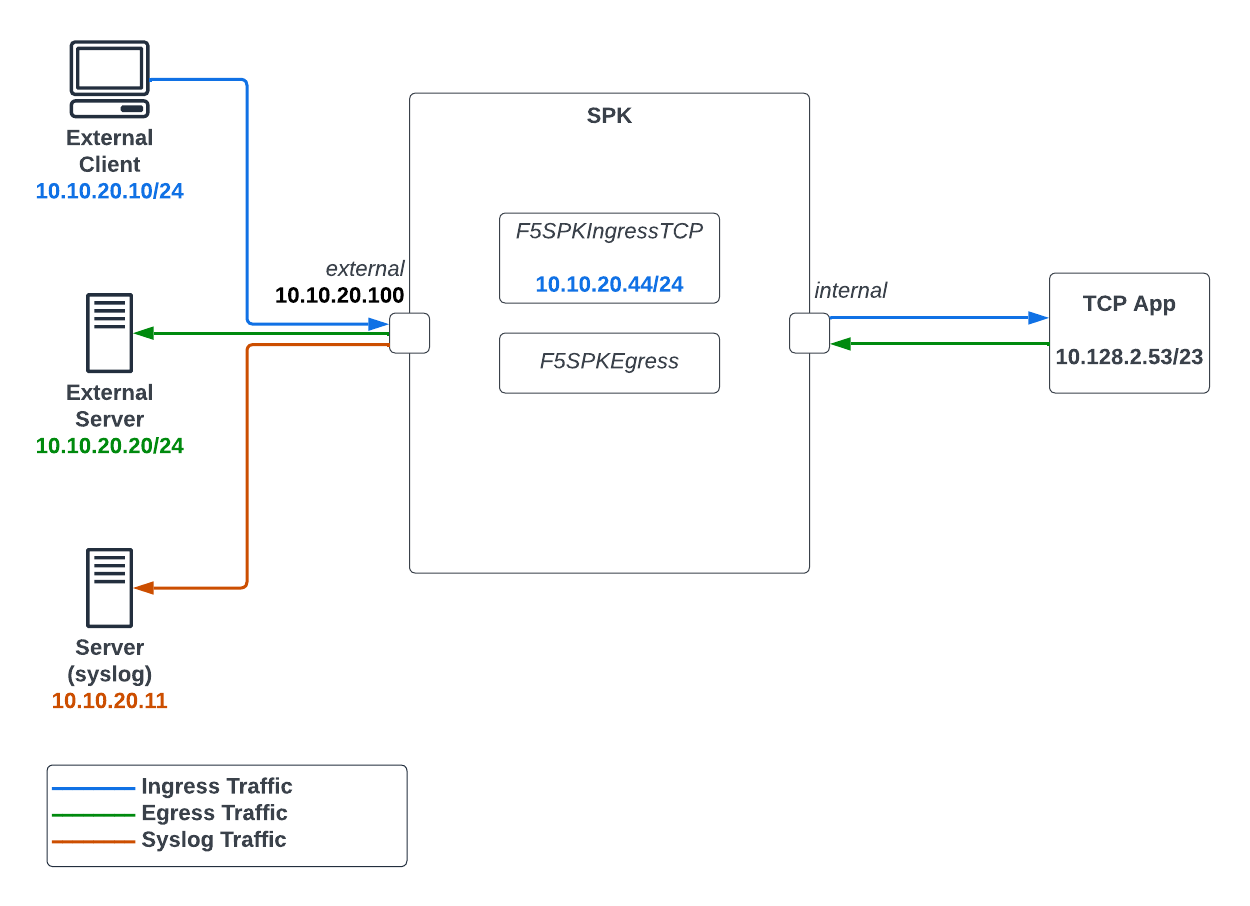 Diagram 1: SPK Firewall Infrastructure Overview
Diagram 1: SPK Firewall Infrastructure Overview
 Note: The diagram is using a TCP App and F5SPKEgress CR but you can
use any app, it is not restricted to the TCP protocol.
Note: The diagram is using a TCP App and F5SPKEgress CR but you can
use any app, it is not restricted to the TCP protocol.
Secure SPK¶
Before You Begin¶
Take the following steps to be sure the Secure SPK resources are available:
Verify the Firewall CRDs are created in your cluster. This crd sets are in f5-spk-crds-service-proxy-7.0.3.tgz. Refer to the Install the CRDs section of the SPK Software for more information. Below show all firewall related CRDs but this guide will be using
f5-big-context-globalsandf5-big-fw-policies.$ oc get crd | grep f5-big f5-big-context-globals.k8s.f5net.com 2023-07-11T20:13:00Z f5-big-fw-policies.k8s.f5net.com 2023-07-11T20:13:00Z f5-big-log-hslpubs.k8s.f5net.com 2023-07-11T20:13:01Z f5-big-log-profiles.k8s.f5net.com 2023-07-11T20:13:01Z
Confirm the AFM container image, f5-l4p-engine, is uploaded to your image registry. Refer to the Upload the image section of the SPK Software for more information.
Enable Secure SPK¶
In order to enable Secure SPK, make the following modifications in the SPK ingress-values.yaml file that
will be used on a helm install before installing the SPK Controller.
 Note: You will need to uninstall the SPK Controller if it is
currently installed. Additional updates in the ingress-values.yaml file from instructiona below will
result an additional deployment specific for firewall functionality.
Note: You will need to uninstall the SPK Controller if it is
currently installed. Additional updates in the ingress-values.yaml file from instructiona below will
result an additional deployment specific for firewall functionality.
Update your ingress-values.yaml file to enable Secure SPK. Below show a snippet of additional changes.
Ensure your cluster can obtain the AFM container image from the your image registry.
global: afm: enabled: true pccd: enabled: true f5-tmm: enabled: true blobd: enabled: true ## afm subchart f5-afm: enabled: true cert-orchestrator: enabled: true afm: name: f5-afm ## PCCD Values pccd: name: f5-afm-pccd enabled: true fluentbit_sidecar: enabled: false
Install the SPK Controller. The
helm installcommand you can use to install SPK Controller. Refer to the SPK Controller document for additional details regarding SPK Controller installation.helm install f5ingress tar/f5ingress-11.0.23.tgz -f ingress-values.yaml
After the installation, you should have the following pods running, notice the extra f5-asm pod as a result of the ingress-values.yaml updates.
$ kubectl get pods -n spk-secure NAME READY STATUS RESTARTS AGE f5ing-f5ingress-84d985cd2e-j78vn7 1/1 Running 0 20m f5-tmm-5dy678hg56-67f4d 1/1 Running 0 20m f5-afm-g6dhg76hg7-ws6a75 1/1 Running 0 20m
Firewall CRDs¶
We use the following CRDs throughout the rest of this guide.
(Optional) Enable Firewall Logging¶
You can enable firewall logging by referring to the Configuring SPK Firewall Logging guide.
This guide assumes a log profile, named logprofile, is created. Example log messages will be shown
throughout this guide.
Creating Firewall CRs¶
Copy the example F5BigFwPolicy CR into a YAML file named
firewall-policy-cr.yaml. Be sure to update yourmetadata.namespaceto the namespace where your SPK Controller is installed. In the example here, it is deployed tospk-secure. The firewall rules defined here is an example based from Diagram 1.- Ingress traffic is defined as any traffic destined to 10.10.20.44 (the destination IP defined from the F5SPKIngress CR).
- Egress traffic is defined as any traffic coming from 10.128.2.0/23 (the network assigned the TCP App).
- Each rule have logging enabled.
- Firewall accepts traffic that matches these rule.
apiVersion: "k8s.f5net.com/v1" kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-ingress ipProtocol: tcp destination: addresses: - 10.10.20.44/32 logging: true action: accept - name: sc-rule-tcp-egress ipProtocol: tcp source: addresses: - 10.128.2.0/23 logging: true action: accept
Copy the below example F5BigContextGlobal CR into a YAML file named
global-context-cr.yaml. Be sure to update yourmetadata.namespaceto the namespace where your SPK Controller is installed. In the example here, it is deployed tospk-secure.- The global firewall context will accept all traffic.
- The default firewall policy is associated to a policy, named
firewallpolicy, created above infirewall-policy-cr.yaml.  Note: There is a default F5ContextGlobal named
Note: There is a default F5ContextGlobal named global-contextafter SPK Controller is installed, DO NOT delete this.
apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: accept defaultActionLog: true
Procedures¶
This section will go through details of the following firewall actions on both ingress and egress traffic. The firewall actions config can be set from the F5ContextGlobal and F5BigFwPolicy CRs. A matrix of the possible firewall actions and traffic outcomes are detailed on Table 1.1 below.
We will be skipping the drop action but the end traffic behavior can be treated similar to reject. On a reject action, the client will receive a reject response. But on a drop action, the client will not receive any response because matching firewall rule packets are silently dropped. If firewall logging is enabled, you will still see a log message as a result of the drop action.
We will walk though each case, show firewall log messages, and show firewall stats where the it either allows and rejects traffic given a firewall policy rule and action.
| Cases | Global Default Action | Firewall Policy Action |
|---|---|---|
| Case 1 | accept | accept |
| Case 2 | accept | reject |
| Case 3 | reject | accept |
| Case 4 | reject | reject |
Table 1.1: Matrix Showing Firewall Actions vs. Traffic State
Before you continue, be sure to confirm the following in your environment.
Verify the total SPK Controller pods that are deployed. You should see f5-tmm, f5ingress, and f5-afm. The number of containers running in each pod may be different but you must have these three pods running.
kubectl get pods -n spk-secure
NAME READY STATUS RESTARTS AGE f5ing-f5ingress-84d985cd2e-j78vn7 1/1 Running 0 20m f5-tmm-5dy678hg56-67f4d 1/1 Running 0 20m f5-afm-g6dhg76hg7-ws6a75 1/1 Running 0 20m
This guide will assume SPK Controller is deployed in the namespace spk-secure.
This guide will assume the TCP App is deployed in the namespace spk-app.
Ingress¶
This section will go though the ingress behavior for each of the firewall cases shown in Table 1.1. Traffic generated here will be from the external client. A summary of the firewall policy rule and global setting is below.
| Firewall Rule | Global Default Action | Firewall Policy Action | Traffic State |
|---|---|---|---|
| sc-rule-tcp-ingress | accept | accept | Pass |
| sc-rule-tcp-ingress | accept | reject | Block |
| sc-rule-tcp-ingress | reject | accept | Block |
| sc-rule-tcp-ingress | reject | reject | Block |
Table 1.2: Matrix Showing Firewall Actions vs. Traffic State
Ingress Case 1¶
Below show the firewall action settings for F5ContextGlobal and F5BigFwPolicy.
| Rule Name | Global Default Action | Firewall Rule Action |
|---|---|---|
| sc-rule-tcp-ingress | accept | accept |
Table 1.3: Case 1 Firewall Action Accept Settings
Use the following steps to verify the ingress traffic for SPK using F5BigContextGlobal and F5BigFwPolicy CRs.
In your
global-context-cr.yamlfile, verify your parameterfirewall.defaultActionis set to accept.- In this example, the
firewall.enforcedPolicyparameter references and applies an F5BigFwPolicy, namedfirewallpolicy. - The global firewall’s default action is set to
accept. - The global firewall’s default logging is enabled.
apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: accept defaultActionLog: true
- In this example, the
Update the F5BigContextGlobal CR, if needed.
kubectl apply -f global-context-cr.yaml -n spk-secure
In your
firewall-policy-cr.yamlfile, update your ingress rule (sc-rule-tcp-ingressin example here) such that the action is set to accept.In this example, the IP protocol rule is TCP:
apiVersion: k8s.f5net.com/v1 kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-ingress ipProtocol: tcp destination: addresses: - 10.10.20.44/32 logging: true action: accept
Update and/or create the F5BigFwPolicy CR, if needed.
kubectl apply -f firewall-policy-cr.yaml -n spk-secure
Verify traffic to the TCP App from the External Client:
nc -v 10.10.20.44 8050
In this example, the TCP app responded back.
Connection to 10.10.20.44 8050 port [tcp/*] succeeded! Hello echo from TCP server [10.10.20.45]: Hello Friend echo from TCP server [10.10.20.45]: Friend
Verify the F5BigContextGlobal statistics:
kubectl exec -it deploy/f5-tmm -c debug -n spk-secure -- tmctl -d blade fw_context_stat
In this example, the packets_accept counter is incremented:
context_type context_name policy_type packets_accept packets_accept_decisively packets_reject packets_drop ------------ ------------- ----------- -------------- ------------------------- -------------- ------------ global global-context 1 1 0 0 0
(Optional) If firewall logging is enabled, go to your syslog server to see the firewall log message. Below is an example of the log message as a result of this case.
Jul 17 22:22:12 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Global","global-context","No-lookup","10.10.20.10","No-lookup","10.10.20.44","36664","9001","external","TCP","0","","","","","","","","Enforced","firewallpolicy-firewallpolicy","sc-rule-tcp-ingress-firewallpolicyrule","","Accept","","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup" Jul 17 22:22:12 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Virtual Server","spk-app-tcp-app-f5ing-testapp-virtual-server","No-lookup","10.10.20.10","No-lookup","10.10.20.44","36664","8050","external","TCP","0","","","","","","","","Enforced","","(Default)","","Accept","","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup"
Ingress Case 2¶
Below show the firewall action settings for F5ContextGlobal and F5BigFwPolicy.
| Rule Name | Global Default Action | Firewall Rule Action |
|---|---|---|
| sc-rule-tcp-ingress | accept | reject |
Table 1.4: Case 2 Firewall Action Reject Settings
Use the following steps to verify the ingress traffic for SPK using F5BigContextGlobal and F5BigFwPolicy CRs.
In your
global-context-cr.yamlfile, verify your parameterfirewall.defaultActionis set to accept.apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: accept defaultActionLog: true
Update the F5BigContextGlobal CR, if needed.
kubectl apply -f global-context-cr.yaml -n spk-secure
In your
firewall-policy-cr.yamlfile, update your ingress rule (sc-rule-tcp-ingressin example here) such that the action is set to reject.apiVersion: k8s.f5net.com/v1 kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-ingress ipProtocol: tcp destination: addresses: - 10.10.20.44/32 logging: true action: reject
Update the F5BigFwPolicy CR:
kubectl apply -f firewall-policy-cr.yaml -n spk-secure
Verify traffic to the TCP App from the external client:
nc -v 10.10.20.44 8050
In this example, the TCP app does NOT respond.
nc: connect to 10.10.20.44 port 8050 (tcp) failed: Connection refused
Verify the F5BigContextGlobal statistics:
kubectl exec -it deploy/f5-tmm -c debug -n spk-secure -- tmctl -d blade fw_context_stat
In this example, the packets_reject counter is incremented.
context_type context_name policy_type packets_accept packets_accept_decisively packets_reject packets_drop ------------ ------------- ----------- -------------- ------------------------- -------------- ------------ global global-context 1 1 0 1 0
(Optional) If firewall logging is enabled, go to your syslog server to see the firewall log message. Below is an example of the log message as a result of this case.
Jul 17 22:23:06 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Global","global-context","No-lookup","10.10.20.10","No-lookup","10.10.20.44","59844","8050","external","TCP","0","","","","","","","","Enforced","firewallpolicy-firewallpolicy","sc-rule-tcp-ingress-firewallpolicyrule","","Reject","Policy","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup"
Ingress Case 3¶
Below show the firewall action settings for F5ContextGlobal and F5BigFwPolicy.
| Rule Name | Global Default Action | Firewall Rule Action |
|---|---|---|
| sc-rule-tcp-ingress | reject | accept |
Table 1.5: Case 3 Firewall Action Reject Settings
Use the following steps to verify the ingress traffic for SPK using F5BigContextGlobal and F5BigFwPolicy CRs.
In your
global-context-cr.yamlfile, verify your parameterfirewall.defaultActionis set to reject.apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: reject defaultActionLog: true
Update the F5BigContextGlobal CR:
kubectl apply -f global-context-cr.yaml -n spk-secure
In your
firewall-policy-cr.yamlfile, update your ingress rule (sc-rule-tcp-ingressin example here) such that the action is set to accept.apiVersion: "k8s.f5net.com/v1" kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-ingress ipProtocol: tcp destination: addresses: - 10.10.20.44/32 logging: true action: accept
Update the F5BigFwPolicy CR.
kubectl apply -f firewall-policy-cr.yaml -n spk-secure
Verify traffic to the TCP App from the external client:
nc -v 10.10.20.44 8050
In this example, the TCP app does NOT respond.
nc: connect to 10.10.20.44 port 8050 (tcp) failed: Connection refused
Verify the F5BigContextGlobal statistics:
kubectl exec -it deploy/f5-tmm -c debug -n spk-secure -- tmctl -d blade fw_context_stat
In this example, the packets_reject counter is incremented:
context_type context_name policy_type packets_accept packets_accept_decisively packets_reject packets_drop ------------ ------------- ----------- -------------- ------------------------- -------------- ------------ global global-context 1 1 0 2 0
(Optional) If firewall logging is enabled, go to your syslog server to see the firewall log message. Below is an example of the log message as a result of this case.
Jul 17 22:24:07 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Global","global-context","No-lookup","10.10.20.10","No-lookup","10.10.20.44","39510","8050","external","TCP","0","","","","","","","","Enforced","firewallpolicy-firewallpolicy","sc-rule-tcp-ingress-firewallpolicyrule","","Accept","","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup" Jul 17 22:24:07 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Virtual Server","spk-app-tcp-app-f5ing-testapp-virtual-server","No-lookup","10.10.20.10","No-lookup","10.10.20.44","39510","8050","external","TCP","0","","","","","","","","Enforced","","(Default)","","Reject","Policy","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup"
Ingress Case 4¶
Below show the firewall action settings for F5ContextGlobal and F5BigFwPolicy.
| Rule Name | Global Default Action | Firewall Rule Action |
|---|---|---|
| sc-rule-tcp-ingress | reject | reject |
Table 1.6: Case 4 Firewall Action Reject Settings
Use the following steps to verify the ingress traffic for SPK using F5BigContextGlobal and F5BigFwPolicy CRs.
In your
global-context-cr.yamlfile, verify your parameterfirewall.defaultActionis set to reject.apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: reject defaultActionLog: true
Update the F5BigContextGlobal CR, if needed:
kubectl apply -f global-context-cr.yaml -n spk-secure
In your
firewall-policy-cr.yamlfile, update your ingress rule (sc-rule-tcp-ingressin example here) such that the action is set to reject.apiVersion: k8s.f5net.com/v1 kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-ingress ipProtocol: tcp destination: addresses: - 10.10.20.44/32 logging: true action: "reject"
Update the F5BigFwPolicy CR, if needed.
kubectl apply -f firewall-policy-cr.yaml -n spk-secure
Verify traffic to the TCP App from the external client:
nc -v 10.10.20.44 8050
In this example, the TCP app does NOT respond back.
nc: connect to 10.10.20.44 port 8050 (tcp) failed: Connection refused
Verify the F5BigContextGlobal statistics:
kubectl exec -it deploy/f5-tmm -c debug -n spk-secure -- tmctl -d blade fw_context_stat
In this example, the packets_reject counter is incremented:
context_type context_name policy_type packets_accept packets_accept_decisively packets_reject packets_drop ------------ ------------- ----------- -------------- ------------------------- -------------- ------------ global global-context 1 1 0 3 0
(Optional) If firewall logging is enabled, go to your syslog server to see the firewall log message. Below is an example of the log message as a result of this case.
Jul 17 22:25:04 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Global","global-context","No-lookup","10.10.20.10","No-lookup","10.10.20.44","59726","8050","external","TCP","0","","","","","","","","Enforced","firewallpolicy-firewallpolicy","sc-rule-tcp-ingress-firewallpolicyrule","","Reject","Policy","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup"
Egress¶
This section will go through the egress behavior with each of the firewall cases shown in Table 1.1. Traffic generated here will be from a backend pod, named tcp-app-f5ing-testapp here, acting as the backend server deployed in the spk-app. namespace. A summary of the firewall policy rule and global setting is below.
| Firewall Rule | Global Default Action | Firewall Policy Action | Traffic State |
|---|---|---|---|
| sc-rule-tcp-egress | accept | accept | Pass |
| sc-rule-tcp-egress | accept | reject | Block |
| sc-rule-tcp-egress | reject | accept | Block |
| sc-rule-tcp-egress | reject | reject | Block |
Table 1.7: Matrix Showing Firewall Actions vs. Traffic State
Egress Case 1¶
Below show the firewall action settings for F5ContextGlobal and F5BigFwPolicy.
| Rule Name | Global Default Action | Firewall Rule Action |
|---|---|---|
| sc-rule-tcp-egress | accept | accept |
Table 1.8: Case 1 Firewall Action Accept Settings
Use the following steps to verify the egress traffic for SPK using F5BigContextGlobal and F5BigFwPolicy CRs.
In your
global-context-cr.yamlfile, verify your parameterfirewall.defaultActionis set to accept.- In this example, the
firewall.enforcedPolicyparameter references and applies an F5BigFwPolicy, namedfirewallpolicy. - The global firewall’s default action is set to
accept. - The global firewall’s default logging is enabled.
apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: accept defaultActionLog: true
- In this example, the
Update the F5BigContextGlobal CR, if needed.
kubectl apply -f global-context-cr.yaml -n spk-secure
In your
firewall-policy-cr.yamlfile, update your egress rule (sc-rule-tcp-egressin example here) such that the action is set to accept.- In this example, the IP protocol rule is TCP
apiVersion: k8s.f5net.com/v1 kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-egress ipProtocol: tcp source: addresses: - 10.128.2.0/23 logging: true action: accept
Update the F5BigFwPolicy CR, if needed.
kubectl apply -f firewall-policy-cr.yaml -n spk-secure
Start a TCP listener on your external server:
nc -l 10.10.20.20 8050
Open an interactive bash shell within the TCP App.
kubectl exec -it tcp-app-f5ing-testapp-7d9f58c4f-4s45d -n spk-app -- bash
In the TCP App shell, open a netcat TCP connection to the external server, type
Hello, then the <enter> key.nc -v 10.10.20.20 8050 10.10.20.20 (10.10.20.20:8050) open Hello
Verify traffic on the external server by checking for the
Hellomessage sent from the TCP app.In this example, the external server received the message.
nc -l 10.10.20.20 8050 Hello
Verify the F5BigContextGlobal statistics:
kubectl exec -it deploy/f5-tmm -c debug -n spk-secure -- tmctl -d blade fw_context_stat
In this example, the packets_accept counter is incremented:
context_type context_name policy_type packets_accept packets_accept_decisively packets_reject packets_drop ------------ ------------- ----------- -------------- ------------------------- -------------- ------------ global global-context 1 2 0 3 0
(Optional) If firewall logging is enabled, go to your syslog server to see the firewall log message. Below is an example of the log message as a result of this case.
Jul 17 22:43:47 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Global","global-context","No-lookup","10.128.2.53","No-lookup","10.10.20.20","47788","8050","internal","TCP","0","","","","","","","","Enforced","firewallpolicy-firewallpolicy","sc-rule-tcp-egress-firewallpolicyrule","","Accept","","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup" Jul 17 22:43:47 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Virtual Server","egress-ipv4","No-lookup","10.128.2.53","No-lookup","10.10.20.20","47788","8050","internal","TCP","0","","","","","","","","Enforced","","(Default)","","Accept","","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup"
Egress Case 2¶
Below show the firewall action settings for F5ContextGlobal and F5BigFwPolicy.
| Rule Name | Global Default Action | Firewall Rule Action |
|---|---|---|
| sc-rule-tcp-egress | accept | reject |
Table 1.9: Case 2 Firewall Action Reject Settings
Use the following steps to verify the egress traffic for SPK using F5BigContextGlobal and F5BigFwPolicy CRs.
Update your
global-context-cr.yamlsuch that your parameterfirewall.defaultActionis set toaccept.apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: accept defaultActionLog: true
Update the F5BigContextGlobal CR, if needed.
kubectl apply -f global-context-cr.yaml -n spk-secure
In your
firewall-policy-cr.yamlfile, update your egress rule (sc-rule-tcp-egressin example here) such that the action is set to reject.apiVersion: k8s.f5net.com/v1 kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-egress ipProtocol: tcp source: addresses: - 10.128.2.0/23 logging: true action: reject
Update the F5BigFwPolicy CR, if needed.
kubectl apply -f firewall-policy-cr.yaml -n spk-secure
Start a TCP listener on your external server:
nc -l 10.10.20.20 8050
Open an interactive bash shell within the TCP App.
kubectl exec -it tcp-app-f5ing-testapp-7d9f58c4f-4s45d -n spk-app -- bash
In the TCP App shell, open a netcat TCP connection to the external server.
In this example, the TCP App CANNOT establish the connection.
nc: connect to 10.10.20.20 8050 port (tcp) failed: No route to host
Verify the F5BigContextGlobal statistics:
kubectl exec -it deploy/f5-tmm -c debug -n spk-secure -- tmctl -d blade fw_context_stat
In this example, the packets_reject counter is incremented:
context_type context_name policy_type packets_accept packets_accept_decisively packets_reject packets_drop ------------ ------------- ----------- -------------- ------------------------- -------------- ------------ global global-context 1 2 0 4 0
(Optional) If firewall logging is enabled, go to your syslog server to see the firewall log message. Below is an example of the log message as a result of this case.
Jul 17 22:44:40 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Global","global-context","No-lookup","10.128.2.53","No-lookup","10.10.20.20","39386","8050","internal","TCP","0","","","","","","","","Enforced","firewallpolicy-firewallpolicy","sc-rule-tcp-egress-firewallpolicyrule","","Reject","Policy","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup"
Egress Case 3¶
Below show the firewall action settings for F5ContextGlobal and F5BigFwPolicy.
| Rule Name | Global Default Action | Firewall Rule Action |
|---|---|---|
| sc-rule-tcp-egress | reject | accept |
Table 1.10: Case 3 Firewall Action Reject Settings
Use the following steps to verify the egress traffic for SPK using F5BigContextGlobal and F5BigFwPolicy CRs.
Update your
global-context-cr.yamlsuch that your parameterfirewall.defaultActionis set toreject.In this example, the
firewall.enforcedPolicyparameter references and applies a F5BigFwPolicy CR globally.apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: reject defaultActionLog: true
Update the F5BigContextGlobal CR, if needed.
kubectl apply -f global-context-cr.yaml -n spk-secure
In your
firewall-policy-cr.yamlfile, update your egress rule (sc-rule-tcp-egressin example here) such that the action is set to accept.apiVersion: k8s.f5net.com/v1 kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-egress ipProtocol: tcp source: addresses: - 10.128.2.0/23 logging: true action: accept
Update the F5BigFwPolicy CR, if needed.
kubectl apply -f firewall-policy-cr.yaml -n spk-secure
Start a TCP listener on your external server:
nc -l 10.10.20.20 8050
Open an interactive bash shell within the TCP App.
kubectl exec -it tcp-app-f5ing-testapp-7d9f58c4f-4s45d -n spk-app -- bash
In the TCP App shell, open a netcat TCP connection to the external server.
In this example, the TCP App CANNOT establish the connection.
nc: connect to 10.10.20.20 8050 port (tcp) failed: No route to host
Verify the F5BigContextGlobal statistics:
kubectl exec -it deploy/f5-tmm -c debug -n spk-secure -- tmctl -d blade fw_context_stat
In this example, the packets_reject counter is incremented:
context_type context_name policy_type packets_accept packets_accept_decisively packets_reject packets_drop ------------ ------------- ----------- -------------- ------------------------- -------------- ------------ global global-context 1 2 0 5 0
(Optional) If firewall logging is enabled, go to your syslog server to see the firewall log message. Below is an example of the log message as a result of this case.
Jul 17 22:45:46 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Global","global-context","No-lookup","10.128.2.53","No-lookup","10.10.20.20","32924","8050","internal","TCP","0","","","","","","","","Enforced","firewallpolicy-firewallpolicy","sc-rule-tcp-egress-firewallpolicyrule","","Accept","","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup" Jul 17 22:45:46 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Virtual Server","egress-ipv4","No-lookup","10.128.2.53","No-lookup","10.10.20.20","32924","8050","internal","TCP","0","","","","","","","","Enforced","","(Default)","","Reject","Policy","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup"
Egress Case 4¶
Below show the firewall action settings for F5ContextGlobal and F5BigFwPolicy.
| Rule Name | Global Default Action | Firewall Rule Action |
|---|---|---|
| sc-rule-tcp-egress | reject | reject |
Table 1.11: Case 4 Firewall Action Reject Settings
Use the following steps to verify the egress traffic for SPK using F5BigContextGlobal and F5BigFwPolicy CRs.
Update your
global-context-cr.yamlsuch that your parameterfirewall.defaultActionis set toreject.In this example, the
firewall.enforcedPolicyparameter references and applies a F5BigFwPolicy CR globally.apiVersion: k8s.f5net.com/v1 kind: F5BigContextGlobal metadata: name: global-context namespace: spk-secure spec: logProfile: logprofile firewall: enforcedPolicy: firewallpolicy defaultAction: reject defaultActionLog: true
Update the F5BigContextGlobal CR, if needed.
kubectl apply -f global-context-cr.yaml -n spk-secure
In your
firewall-policy-cr.yamlfile, update your egress rule (sc-rule-tcp-egressin example here) such that the action is set to reject.In this example, the IP protocol rule is TCP:
apiVersion: k8s.f5net.com/v1 kind: F5BigFwPolicy metadata: name: firewallpolicy namespace: spk-secure spec: rule: - name: sc-rule-tcp-egress ipProtocol: tcp source: addresses: - 10.128.2.0/23 logging: true action: reject
Update the F5BigFwPolicy CR, if needed.
kubectl apply -f firewall-policy-cr.yaml -n spk-secure
Start a TCP listener on your external server:
nc -l 10.10.20.20 8050
Open an interactive bash shell within the TCP App.
kubectl exec -it tcp-app-f5ing-testapp-7d9f58c4f-4s45d -n spk-app -- bash
In the TCP App shell, open a netcat TCP connection to the external server.
In this example, the TCP App CANNOT establish the connection.
nc: connect to 10.10.20.20 8050 port (tcp) failed: No route to host
Verify the F5BigContextGlobal statistics:
kubectl exec -it deploy/f5-tmm -c debug -n spk-secure -- tmctl -d blade fw_context_stat
In this example, the packets_reject counter is incremented:
context_type context_name policy_type packets_accept packets_accept_decisively packets_reject packets_drop ------------ ------------- ----------- -------------- ------------------------- -------------- ------------ global global-context 1 2 0 6 0
(Optional) If firewall logging is enabled, go to your syslog server to see the firewall log message. Below is an example of the log message as a result of this case.
Jul 17 22:47:29 f5-tmm-9cbcc4dbd-zr76f tmm[14] "10.131.0.151","f5-tmm-9cbcc4dbd-zr76f","Global","global-context","No-lookup","10.128.2.53","No-lookup","10.10.20.20","41574","8050","internal","TCP","0","","","","","","","","Enforced","firewallpolicy-firewallpolicy","sc-rule-tcp-egress-firewallpolicyrule","","Reject","Policy","","","0000000000000000","unknown","unknown","unknown","unknown","","","","","No-lookup","No-lookup"
Feedback¶
Provide feedback to improve this document by emailing spkdocs@f5.com.