Unofficial - F5 Certification Exam Prep Material > Symposium 2025 - BIG-IP Administrator: Source | Edit on
Lab 10: Securing your BIG-IP¶
Objectives:
- Understand Port Lockdown settings for Self-IPs.
- Configure and test Firewall Rules for Self-IPs.
- Interpret Port Lockdown settings and their impact.
Step 1: Setup Environment¶
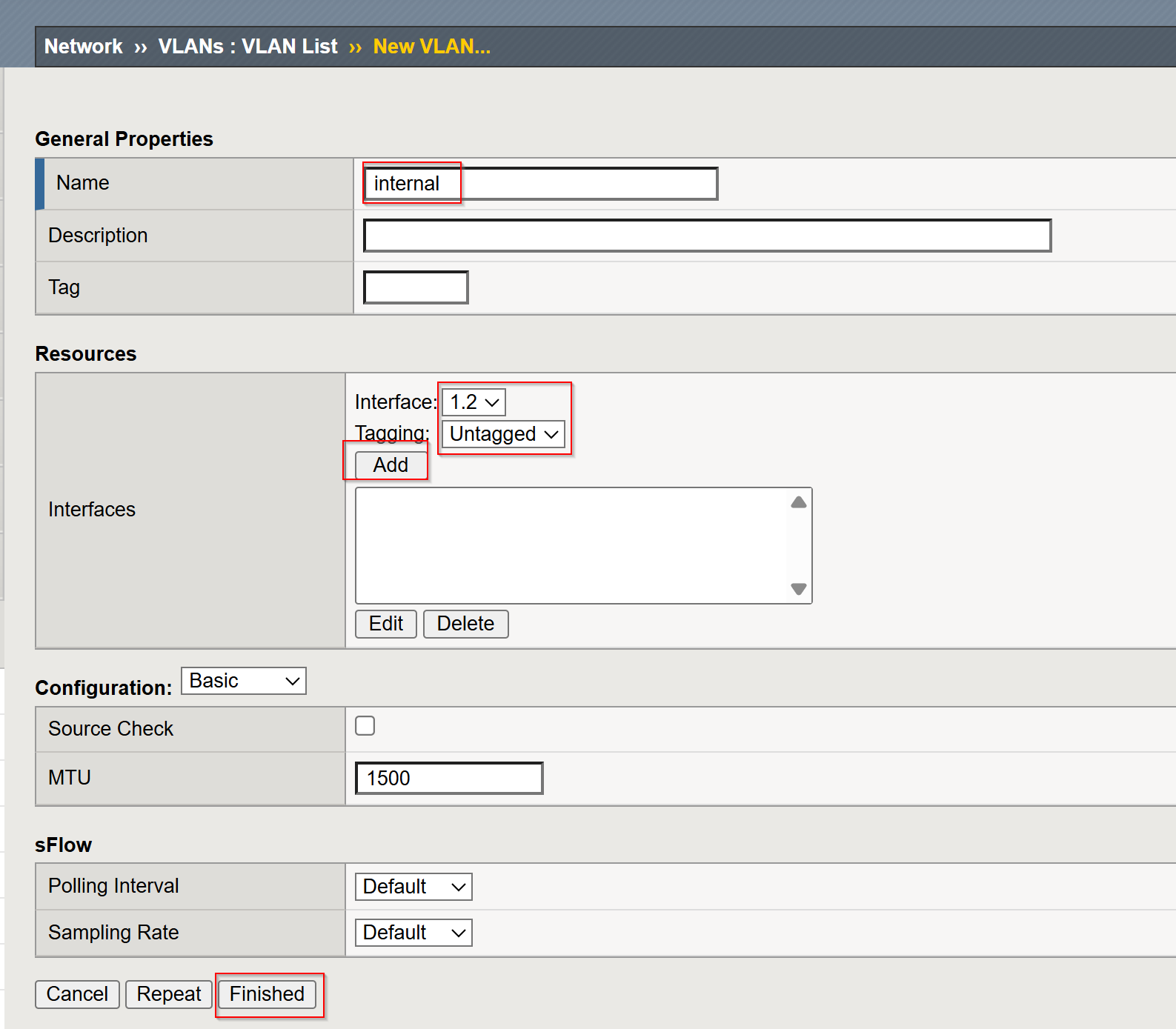
Create VLAN (Named internal):
Log in to the TMUI (BIG-IP web-based GUI)
Navigate to Network -> VLANs.
Click Create to define a new VLAN.
Provide the following details:
- Name:
internal - Tag: Leave blank for an untagged VLAN
- Interfaces: Select the interface(s) to associate with the VLAN (e.g.,
1.2).
- Name:
Click Finished to create the VLAN.
TMSH Method:
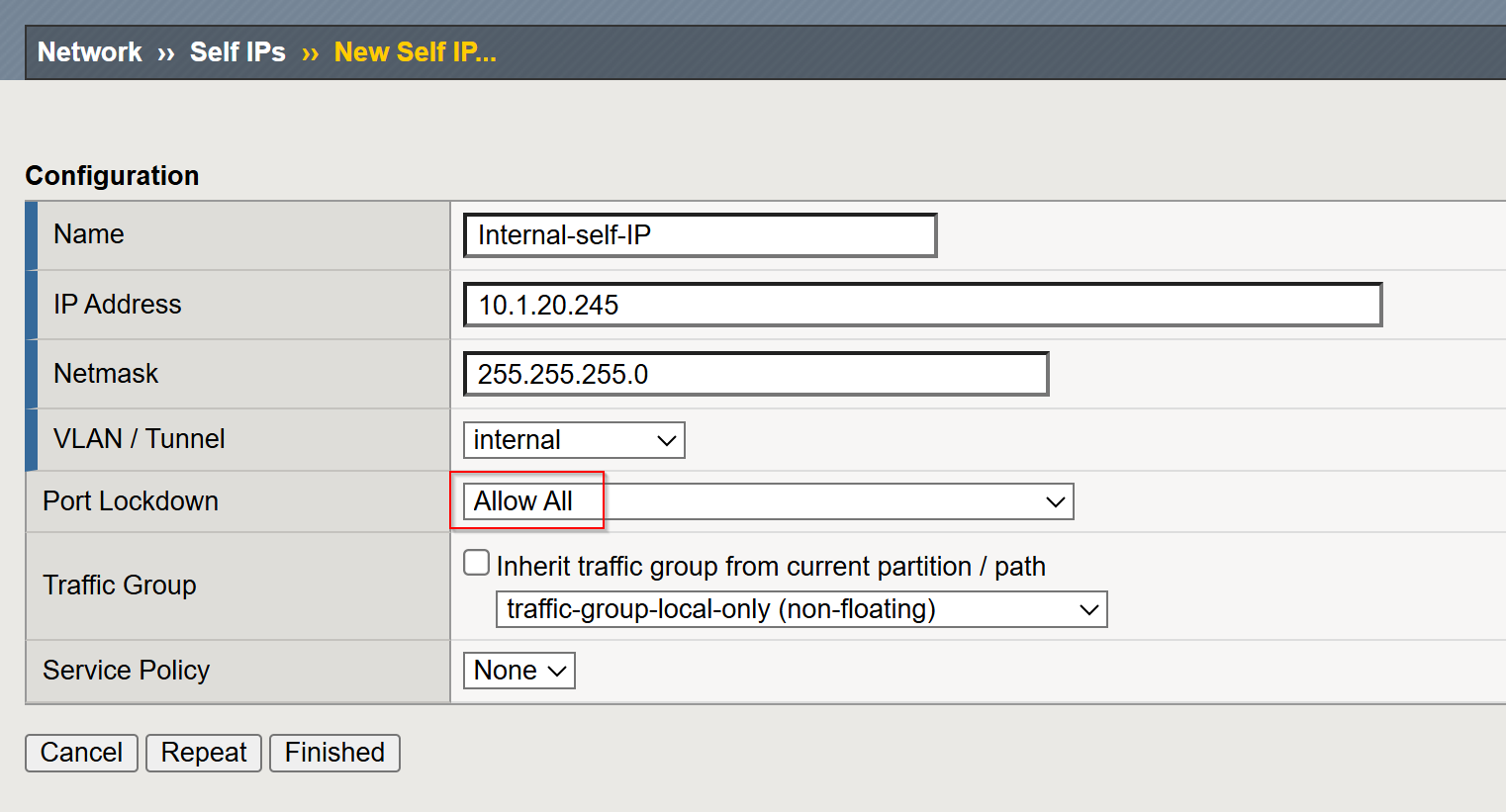
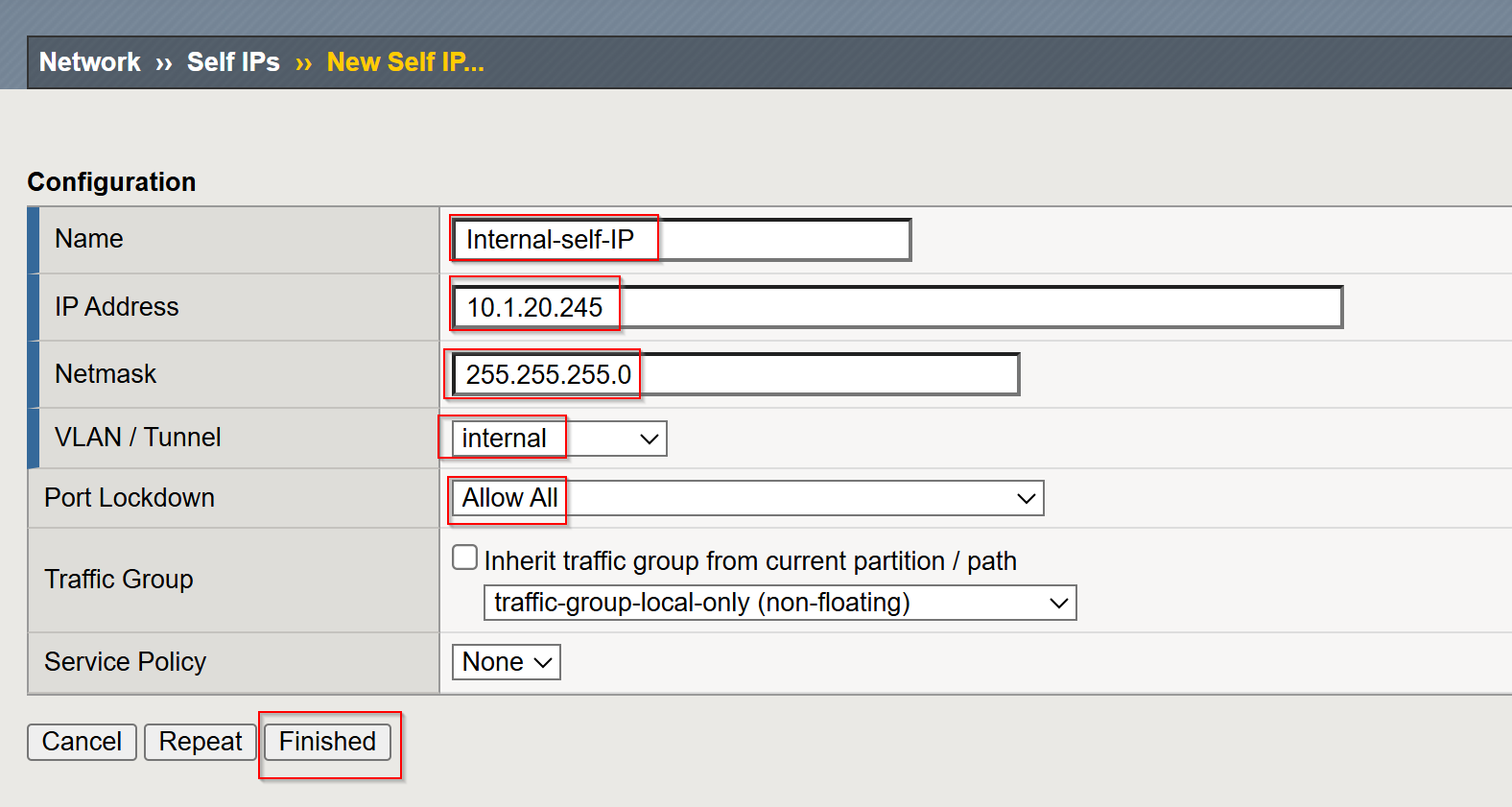
Create a Self IP:
- Navigate to
Network->Self IPs. - Click Create to add a new self IP.
- Provide the following details:
- Name:
Internal-self-IP - IP Address:
10.1.20.245 - Netmask/Subnet:
255.255.255.0(adjust based on your network setup) - VLAN: Select the VLAN
internalcreated earlier. - Port Lockdown: Set to
Allow All.
- Name:
- Click Finished to apply the configuration.
TMSH Method:
- Navigate to
Step 2: Test Initial Access¶
Verify basic access from the Jumpbox using curl:
Run a port scan using nmap from the Jumpbox to identify open ports:
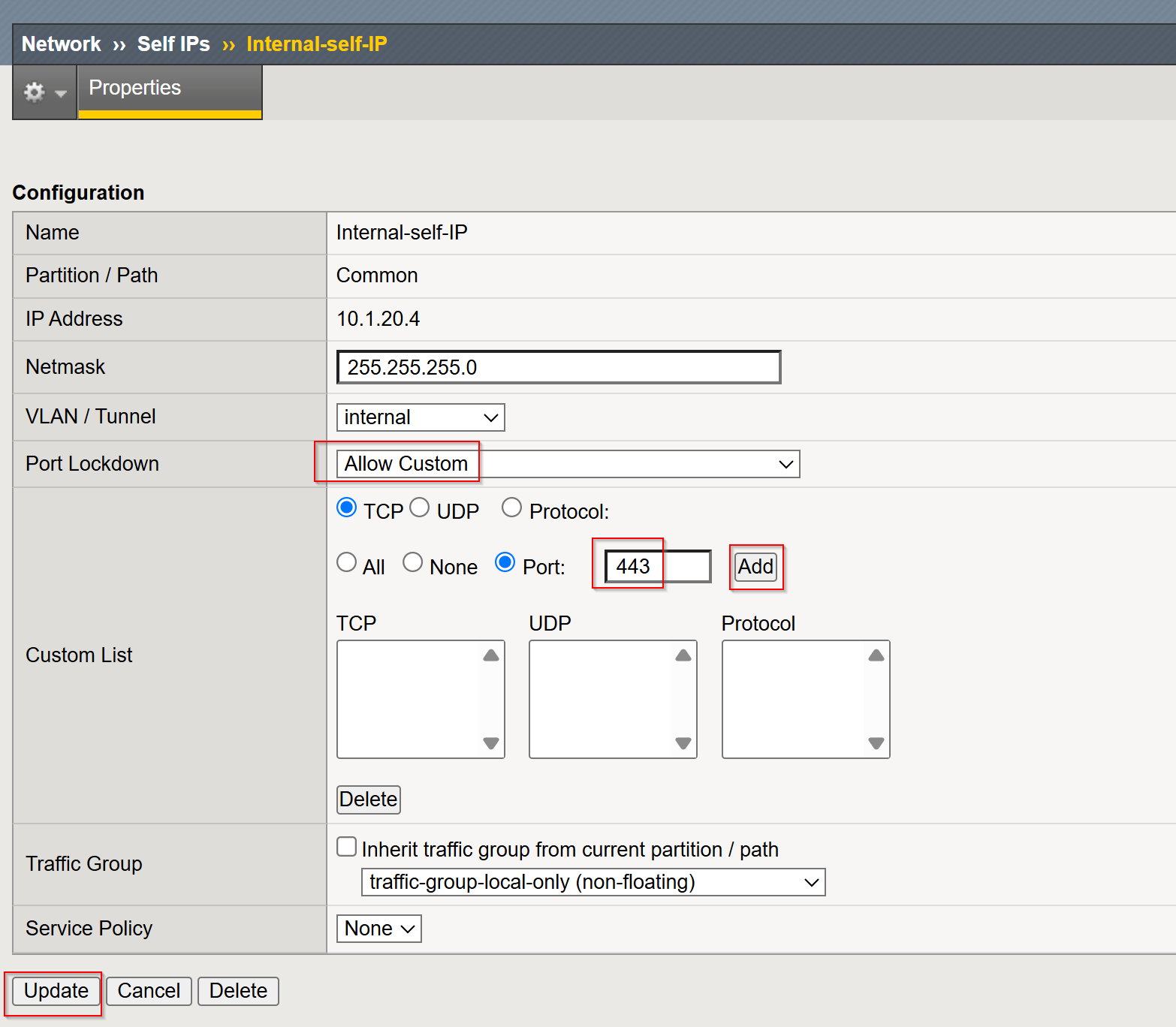
Step 3: List Current Port Lockdown Settings¶
Step 4: Customize Port Lockdown¶
Step 5: Test Packet Filter Rules for Self-IPs¶
Add Packet Filter Rules:
Configure a packet filter rule that drops ICMP traffic and allows traffic to TCP port
443for a specific IP range (e.g.,10.1.20/24).TMUI
Click Network > Packet Filters > Rule
Create Drop ICMP Rule
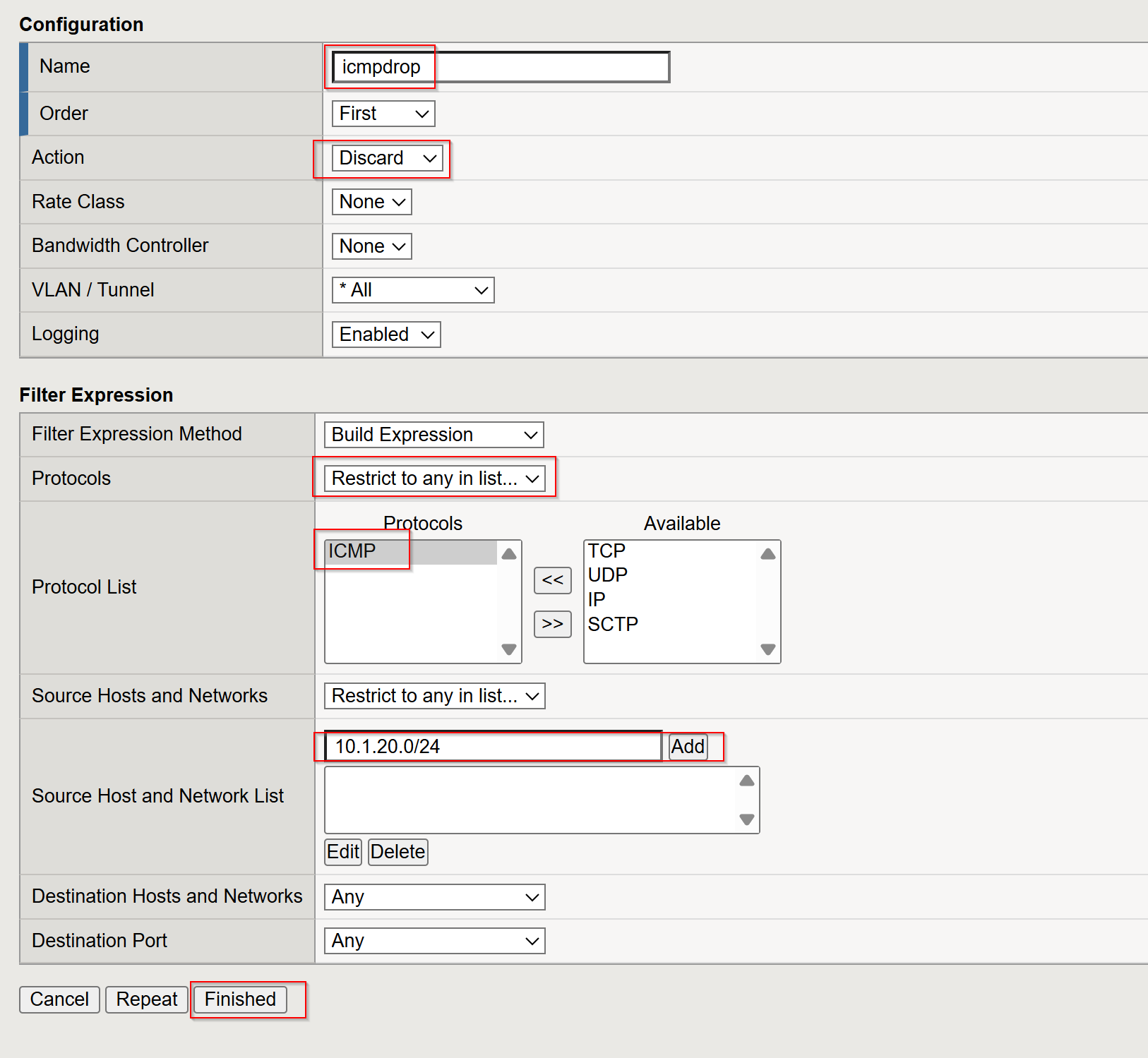
- Name:
imcpdrop - Action:
Discard - Protocol:
TCP - Source Hosts and Network: 10.1.20.0/24
- Name:
Create Drop HTTP Rule
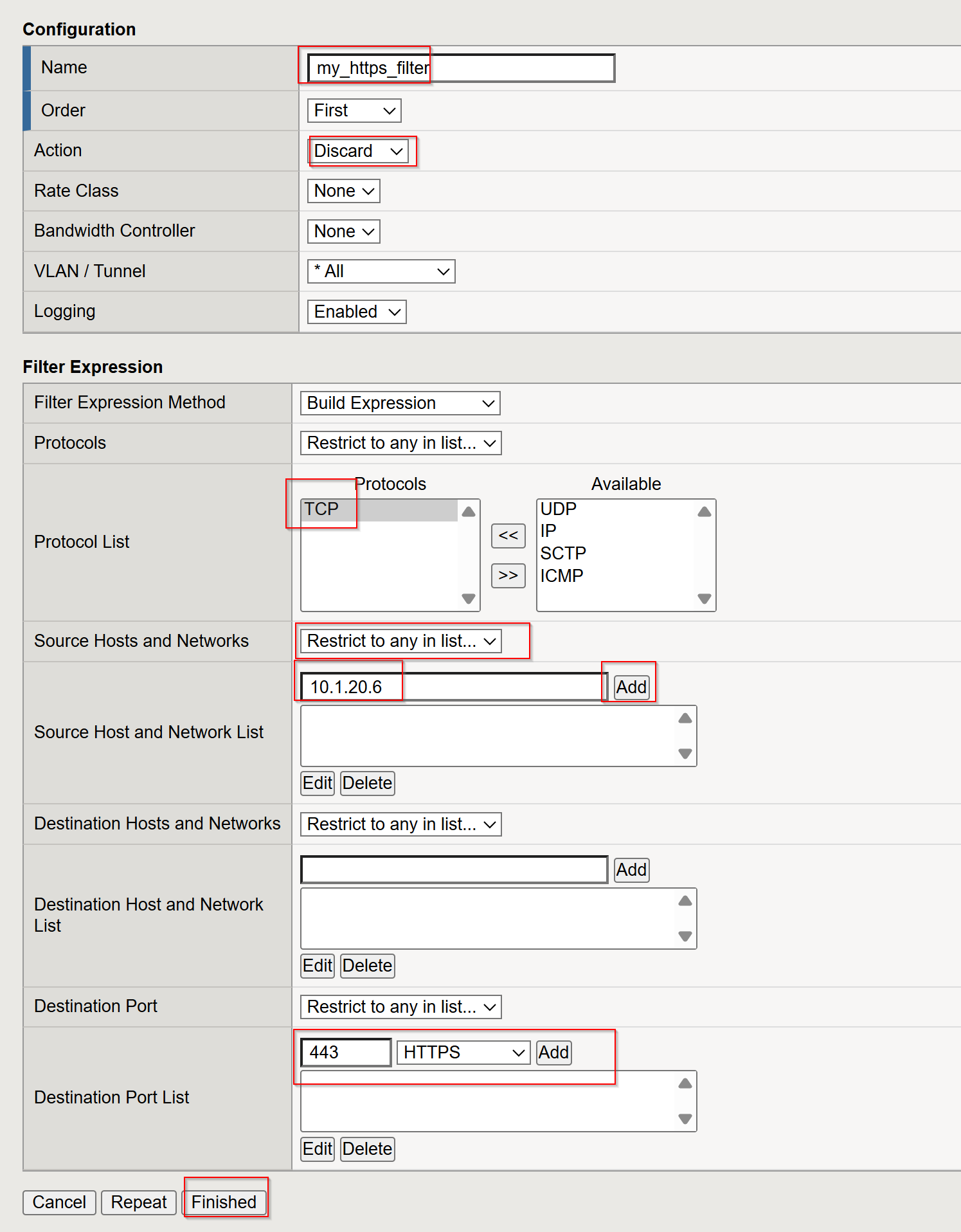
- Name:
my_https_filter - Action:
Discard - Protocol:
TCP - Source Hosts and Network: 10.1.20.6
- Destination Port: 443
- Name:
TMSH Method:
Create a rule that drops ICMP packets for a subnet:
Create a rule that allows HTTPS traffic for a specific source subnet:
Verify Packet Filter Rules:
List the current packet filter rules to confirm the configuration:
Ensure that both the icmpdrop and my_https_filter rules are properly configured with the correct order and action properties.
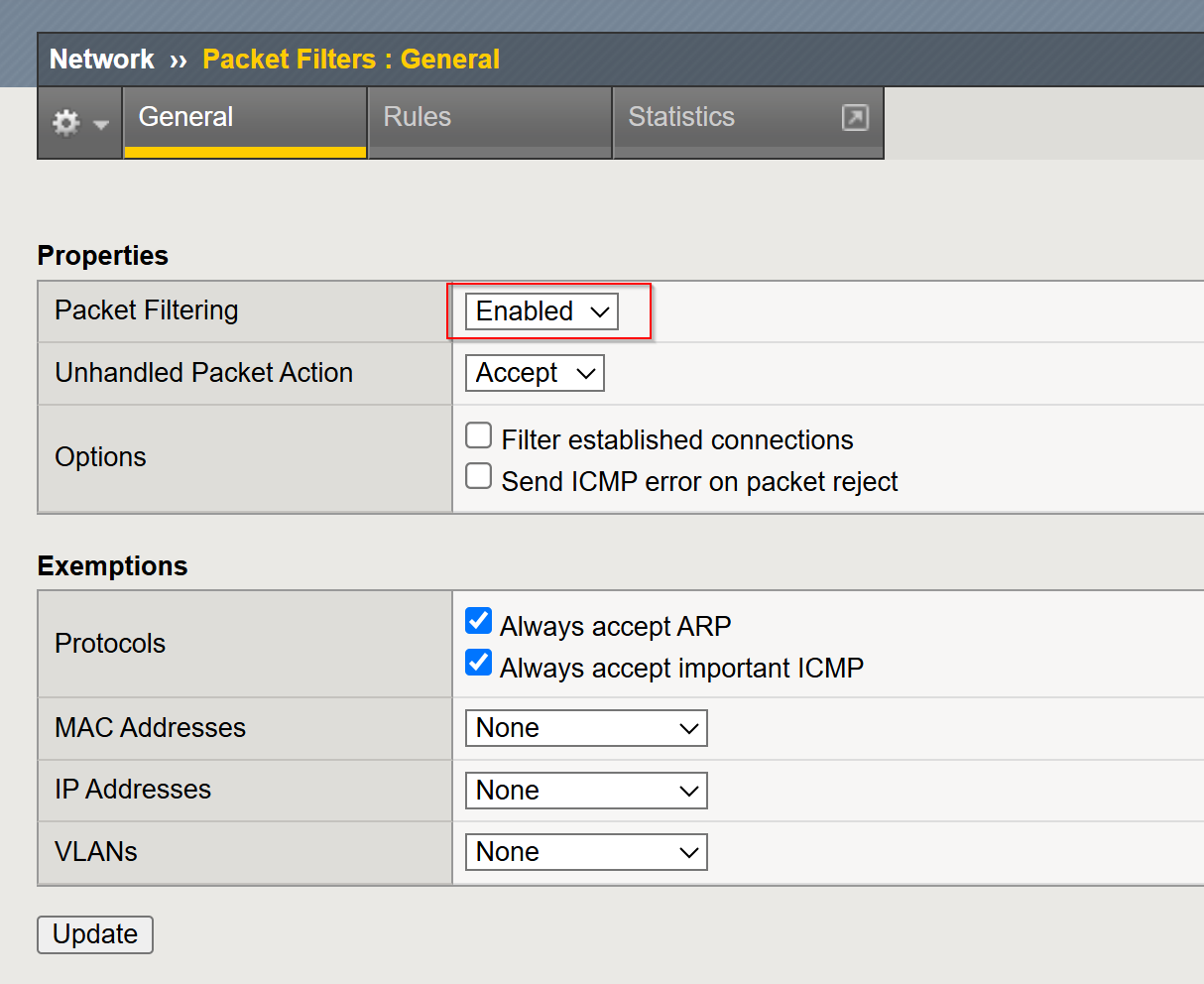
Enable Packet Filtering:
Enable packet filtering globally on the BIG-IP system if not already enabled:
TMUI
- Click Network > Packet Filters > General
- Set Packet Filtering:
Enable
TMSH
Test Packet Filter Behavior Using curl and ping:
From the Jumpbox (e.g., within 10.1.20.0/24):
Access HTTPS port
443:Attempt to send ICMP packets. They should be dropped:
Clean Up:
If you want to disable packet filtering after testing, run the following commands:
Closing¶
This guide provides clear steps to configure and secure BIG-IP self IPs using port lockdown and packet filtering. By restricting access to essential services and managing traffic at a granular level, administrators can enhance the security and control of their BIG-IP systems. These practices ensure only authorized connections are allowed while protecting against unwanted or malicious traffic.
Lab Overview: Monitoring and Mitigating DoS/DDoS Attacks on BIG-IP LTM¶
This lab demonstrates two key techniques for mitigating Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks on a BIG-IP LTM: SYN cookie protection and adjusting the tm.maxrejectrate. Students will simulate attacks and observe how the BIG-IP LTM responds and protects the virtual server.
Pre-Lab Section: BIG-IP LTM Configuration¶
In this section, students will configure the BIG-IP LTM with the necessary network settings, pool, and virtual server.
Tasks:
Create VLANs:
This creates two VLANs: “internal” (tagged with VLAN ID 100) and “external” (tagged with VLAN ID 200), assigning interfaces 1.2 and 1.1 respectively.
Create Self IPs:
This creates self IP addresses for the “internal” and “external” VLANs. The “internal_self” and “external_self” IP do not allow any services.
Create a Pool:
This creates a pool named “web_pool” with a member server at 10.1.20.14 on port 80.
Create a Virtual Server:
This creates a virtual server named “web_virtual” listening on 10.1.10.100:80 (TCP) and directs traffic to the “web_pool”.
Section 1: SYN Cookie Protection¶
Objective: To understand how BIG-IP LTM uses SYN cookies to protect against SYN flood attacks.
Background:
SYN flood attacks exploit the TCP handshake process by sending a high volume of SYN packets without completing the handshake. This can overwhelm the server’s resources. SYN cookie protection is a mechanism where the BIG-IP LTM uses a cryptographic cookie in the SYN-ACK packet to validate the client’s connection attempt, without storing state for every SYN.
Tasks:
Describe SYN Cookie Protection:
- Explain the TCP handshake process.
- Explain how SYN flood attacks disrupt this process.
- Describe how SYN cookies work to mitigate SYN flood attacks.
Simulate a SYN Flood Attack:
Use the
hping3tool to generate a SYN flood attack:Explain the function of each parameter in the
hping3command.
Observe BIG-IP LTM Behavior:
- Monitor the BIG-IP LTM logs (
/var/log/ltm) for SYN cookie activation messages. - Students should observe messages similar to:
01010038:4: Syncookie counter 64005 exceeded vip threshold 64000 for virtual = 10.1.10.100:8
- Explain the meaning of these log messages.
- Monitor the BIG-IP LTM logs (
Expected Results:
- Students will observe that the BIG-IP LTM activates SYN cookie protection under the simulated SYN flood attack.
- The BIG-IP LTM continues to respond to legitimate traffic while mitigating the attack.
Section 2: tm.maxrejectrate¶
Objective: To understand how tm.maxrejectrate helps to limit the rate at which the BIG-IP LTM sends TCP RST or ICMP unreachable packets, preventing the BIG-IP itself from being overwhelmed.
Background:
The tm.maxrejectrate setting on the BIG-IP LTM controls the maximum number of TCP RST or ICMP unreachable packets the BIG-IP sends per second. This is important to prevent the BIG-IP from being overwhelmed by the attack itself, especially in cases of DoS attacks involving non-SYN packets or spoofed traffic.
Tasks:
Describe Maximum Reject Protection:
- Explain the purpose of sending TCP RST or ICMP unreachable packets.
- Explain why limiting the rate of these responses is important.
- Introduce the
tm.maxrejectratedatabase key.
Simulate an Attack:
Use
hping3to send a flood of TCP packets with the ACK flag set:Explain how this attack differs from a SYN flood.
Observe BIG-IP LTM Behavior:
- Monitor the BIG-IP LTM logs (
/var/log/ltm) for messages related totm.maxrejectrate. - Students should observe messages similar to:
011e0001:4: Limiting open port RST response from 251 to 250 packets/sec for traffic-group /Common/traffic-group-
- Explain the meaning of these log messages and how they indicate that
tm.maxrejectrateis working.
- Monitor the BIG-IP LTM logs (
Expected Results:
- Students will observe that the BIG-IP LTM limits the rate of RST packets it sends in response to the attack.
- This prevents the BIG-IP LTM itself from becoming a victim of the attack.
Conclusion¶
This lab demonstrates two important mechanisms for mitigating DoS/DDoS attacks on BIG-IP LTM. SYN cookie protection protects backend servers from SYN flood attacks, while tm.maxrejectrate protects the BIG-IP LTM itself from being overwhelmed by high-volume attacks. By understanding and configuring these features, students can effectively enhance the security and availability of applications behind a BIG-IP LTM.