F5 Public Cloud Solutions > Public Cloud Architectures II: F5 in AWS Advanced Use Cases Beyond Native Tools > F5 Networks IPSec VPN to AWS Source | Edit on
Create an IPSec VPN between an F5 Big-IP appliance and an AWS Virtual Private Gateway¶
From the Linux terminal app, open a new tab. Invoke the “bigip” shell alias command to ssh to your on-premises bigip1.
From bigip1, use dig to discover the public IP address assigned to your bigip1.
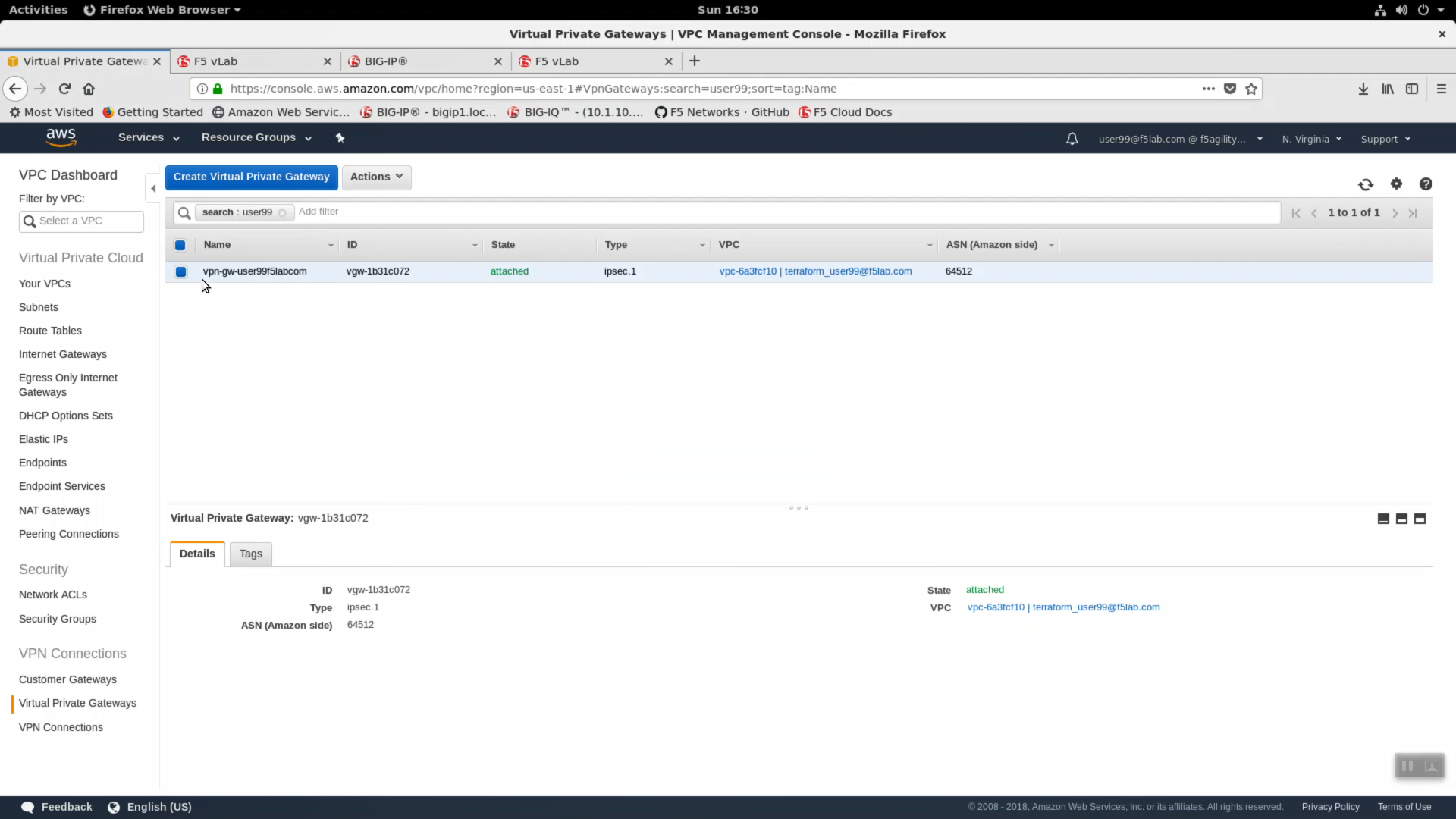
In the AWS web console, navigate to Services => Networking & Content Delivery => VPC. Click on VPCs. From the VPC Dashboard, in the left-hand navigation pane, click on Virtual Private Gateways. Enter your username in the search filter (i.e. user99). A Virtual Private Gateway has been created and attached to your VPC. We will now establish an IPSec VPN tunnel between our on-premises environment and our AWS VPC.
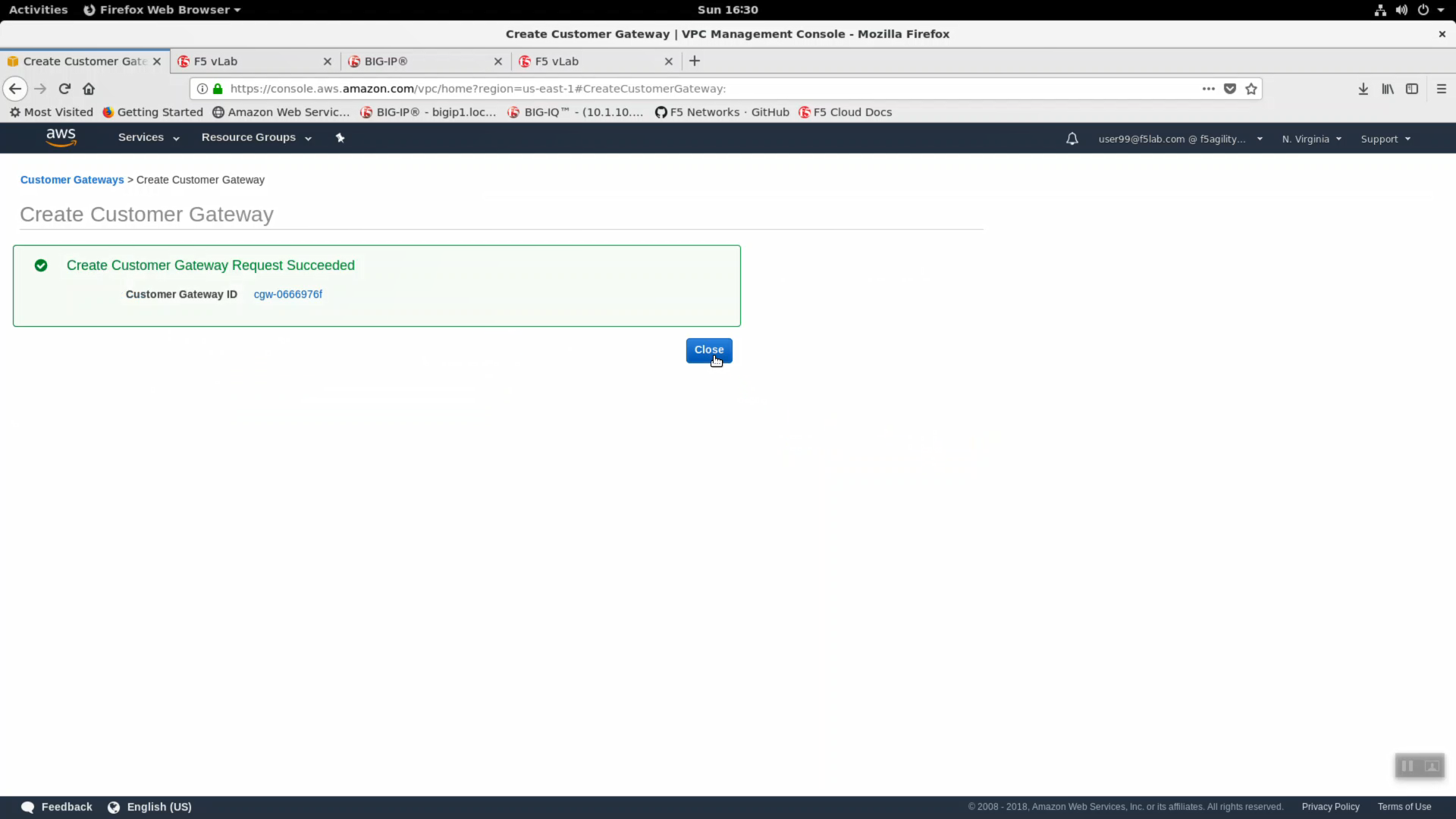
Click on Customer Gateways => Create Customer Gateway.
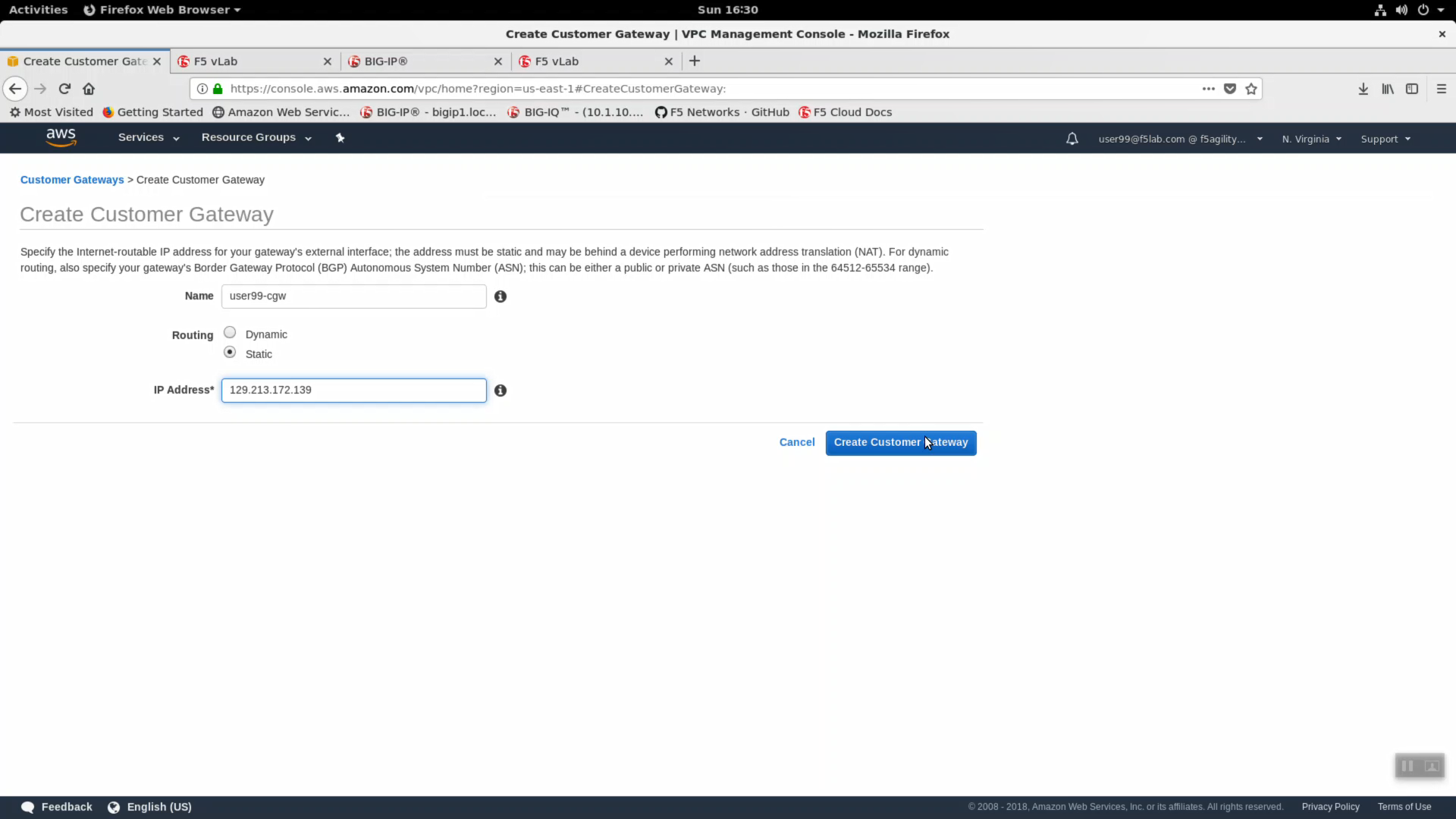
Create Customer Gateway.
- Name: userXX-cgw, replace userXX with the unique user id assigned to you in class. The example in the screenshot is for user99.
- Routing: Static
- IP Address*: This is the public IP address of your on-premises Big-IP VE. From the bigip1 terminal, review the output of the dig command below.
Click “Create Customer Gateway”
Create Customer Gateway Request Succeeded. Note the Customer Gateway ID in the format cgw-xxxxxxxxx. You will need this id in the next step.
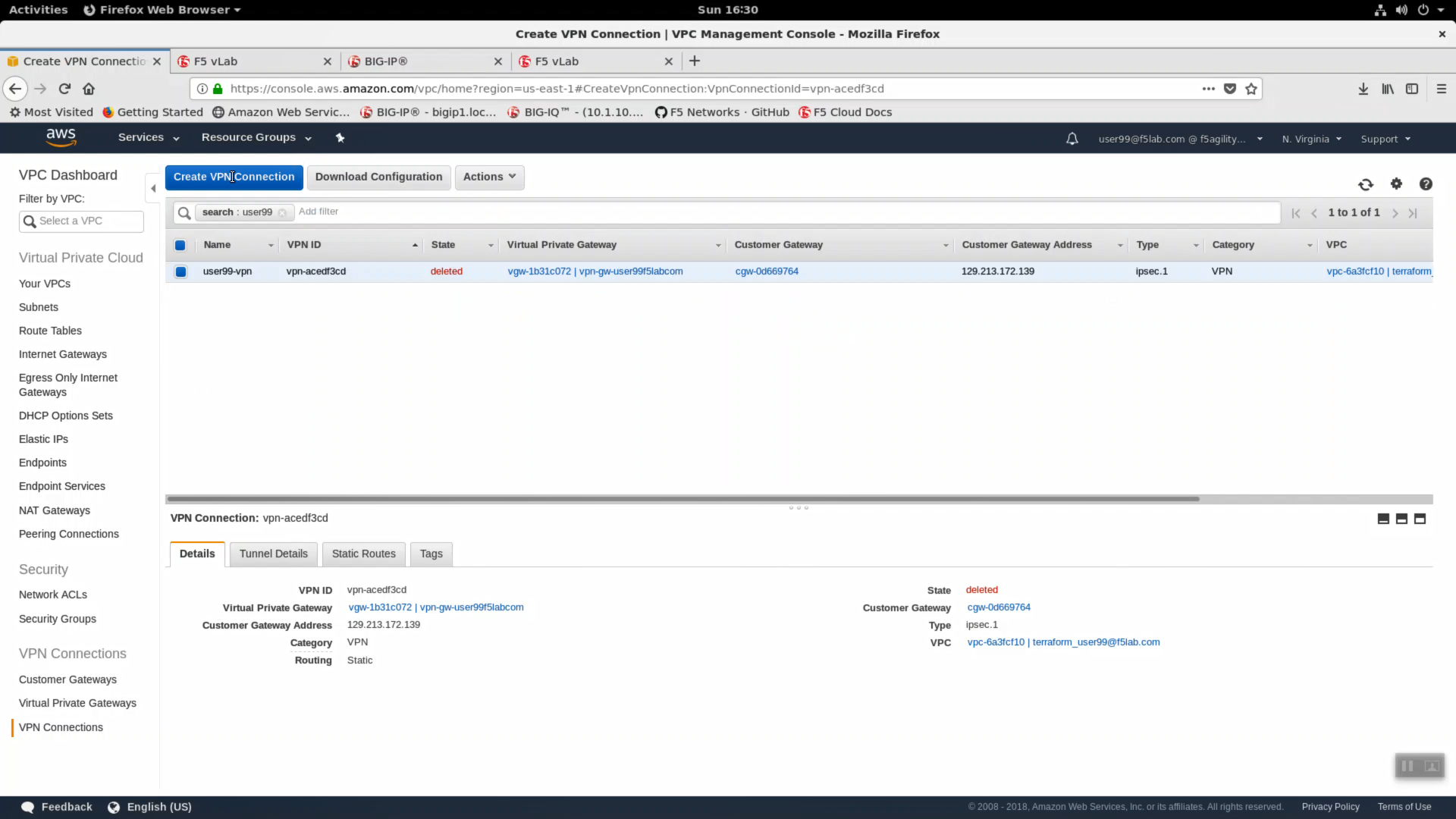
From the VPC Dashboard, in the left-hand navigation pane, click on VPN Connections. Click on “Create VPN Connection”.
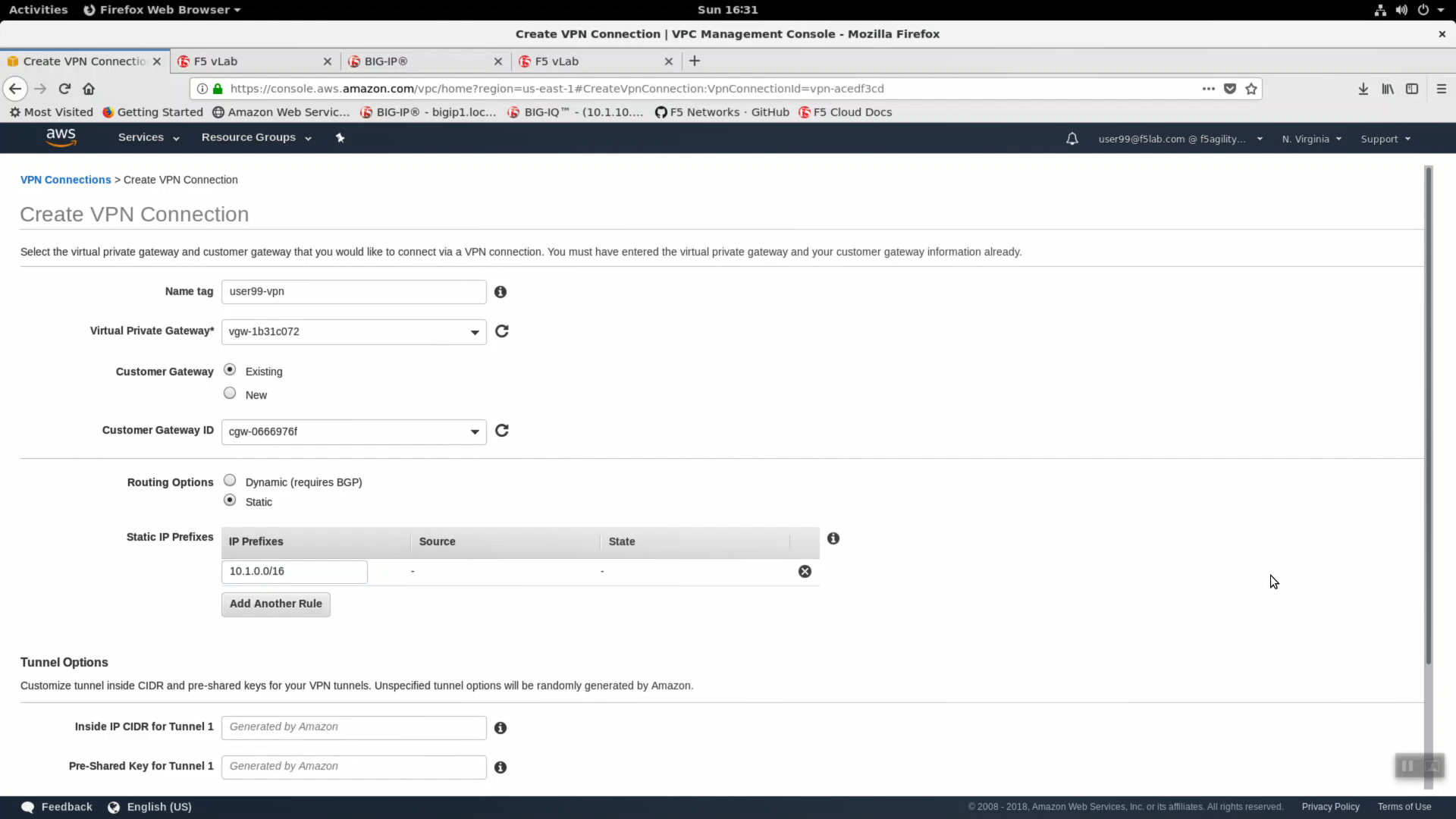
| Parameter | value |
|---|---|
| Name tag | userXX-vpn where userXX is your unique user id |
| Virtual Private Gateway | vgw-xxxxxxxx attached to your VPC. |
| Customer Gateway | Existing |
| Customer Gateway ID | cgw-xxxxxxxxx we created in the previous step. |
| Routing Options | Static |
| Static IP Prefixes | 10.1.0.0/16 |
Leave all Tunnel Options to default “Generated by Amazon”. Click “Create VPN Connection”.
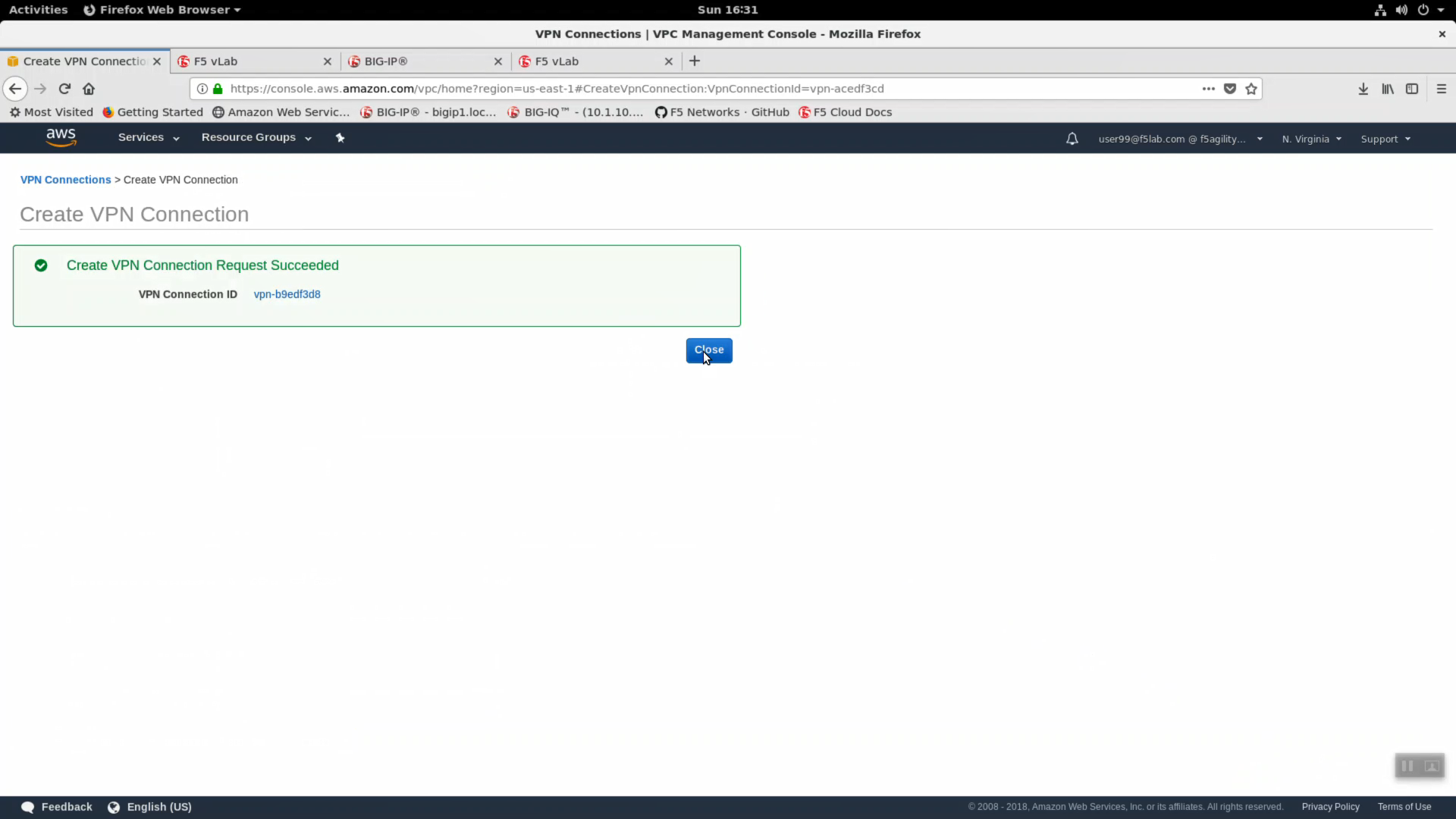
Create VPN Connection Succeeded.
From the VPC Dashboard, in the left-hand navigation pane, click on VPN Connections. Your userXX should still be in the search field, if not, enter your userXX in the search field. You will see the VPN Connection you just created in state “Pending”. Click the “Status” tab. Both tunnels are status: DOWN.
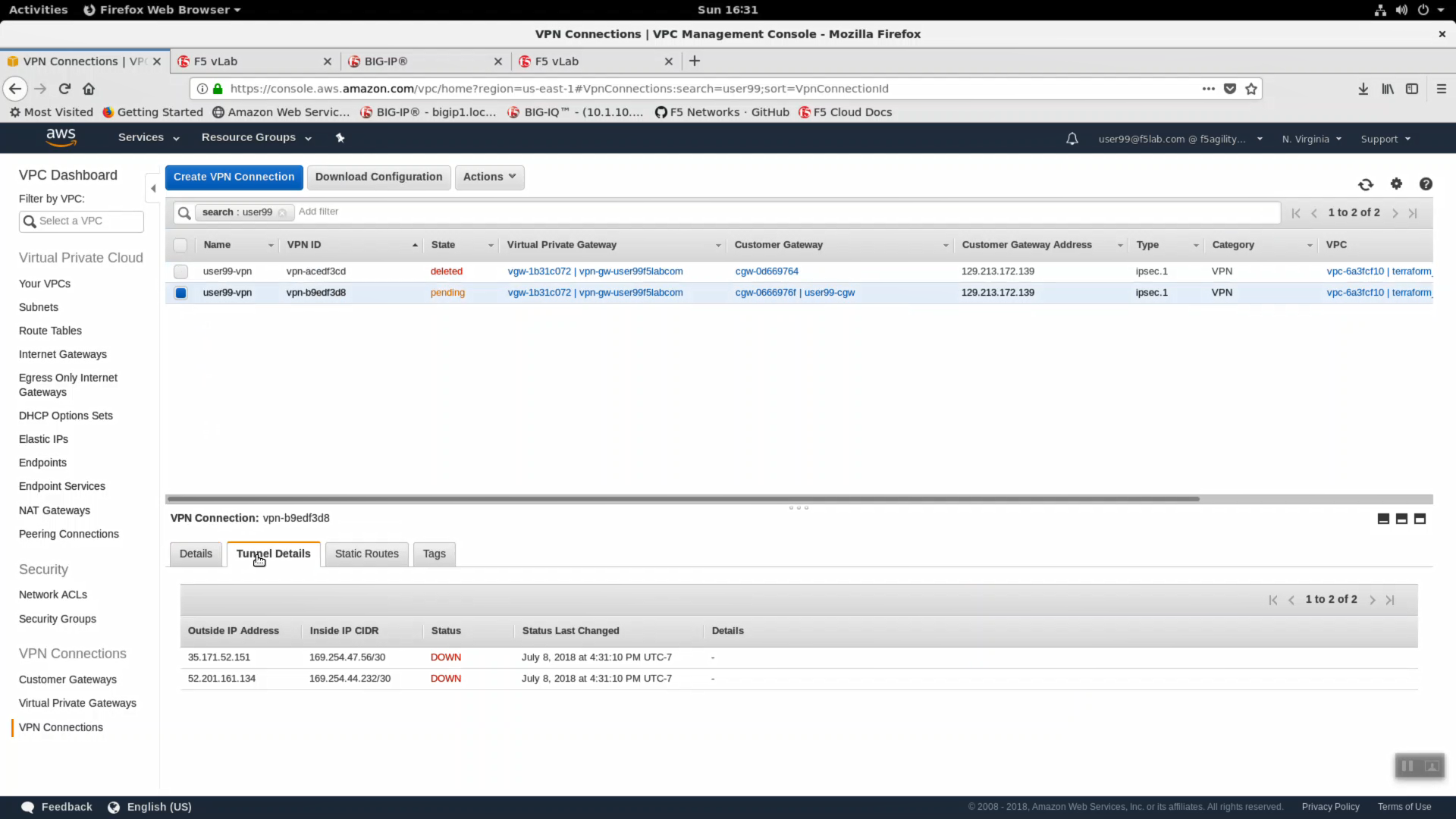
Click on “Download Configuration”
- Vendor: F5 Networks, Inc.
- Platform: BIG-IP
- Software: v12.0.0+
Click on “Download”. By default, the config file will be downloaded to your /home/student/Downloads/ directory.
From the Linux RDP session, click on “Activities” in the upper-left-hand corner to launch the Dock. Launch FileZilla.
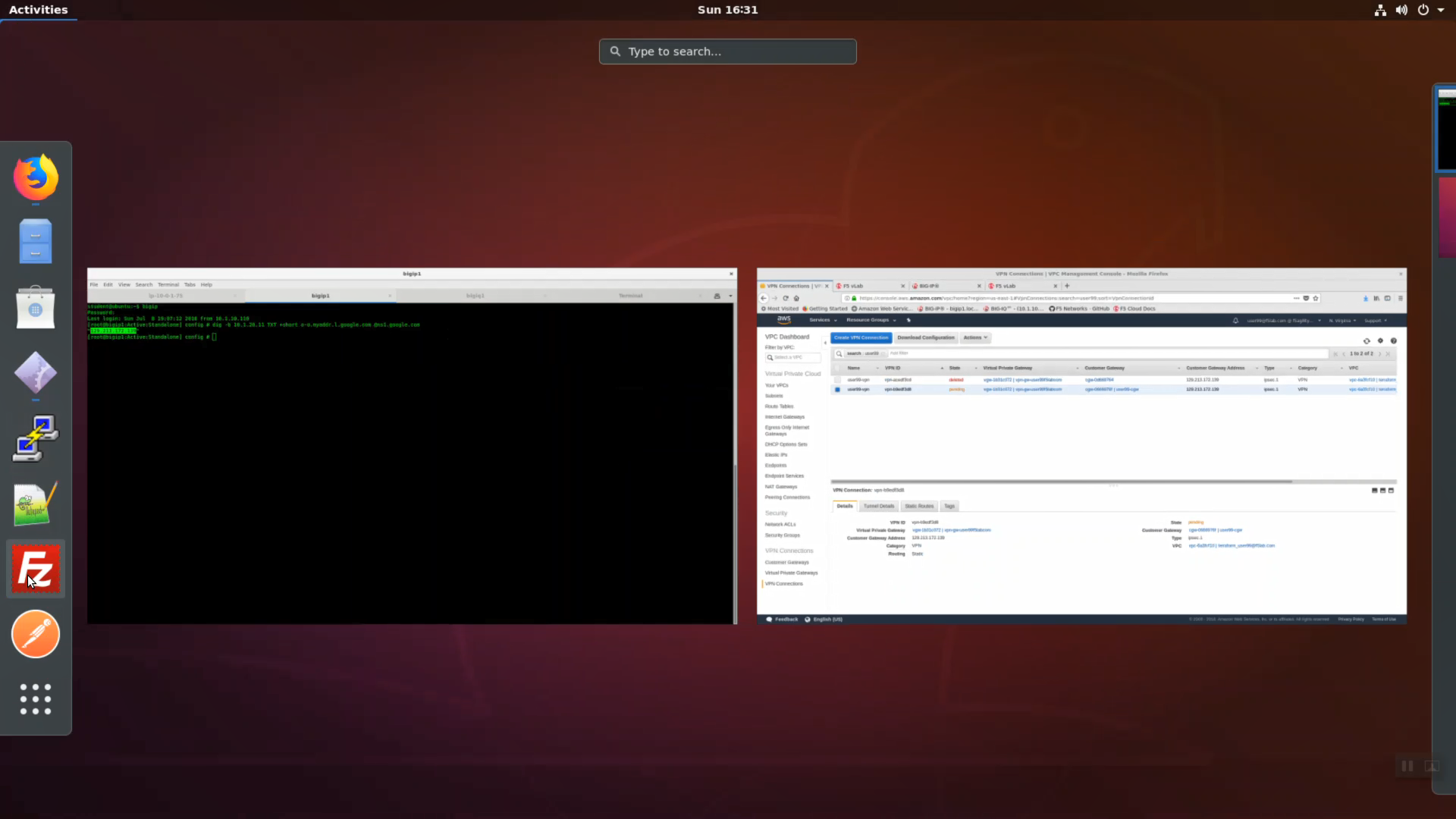
From FileZilla, launch Site Manager. An entry for bigip1 has been prepared for you. Connect to bigip1. You will use SFTP (Secure FTP runs over the SSH protocol / TCP 22) to transfer the AWS generated VPN config file to your on-premises bigip1 and import the config.
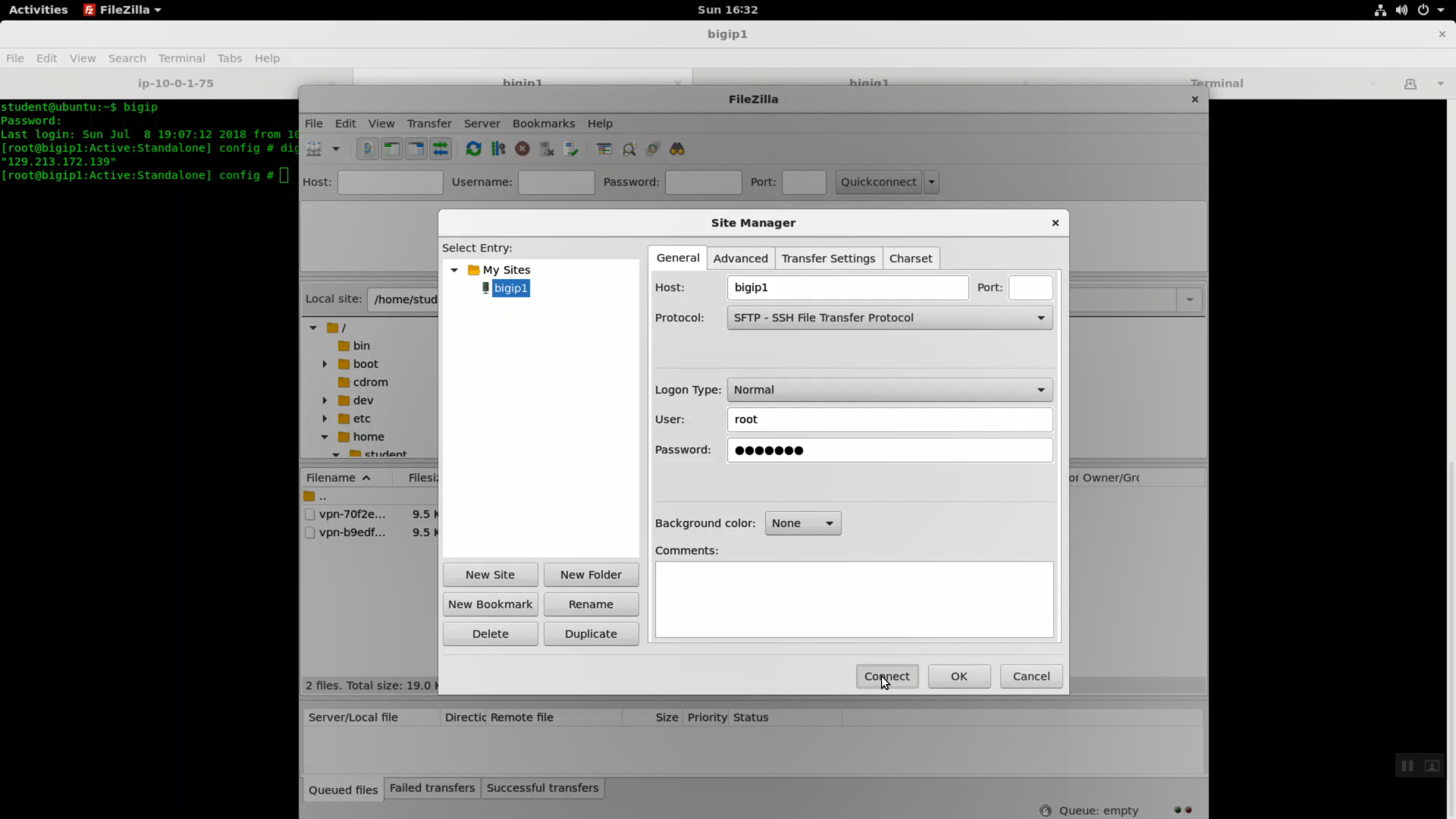
Right-click on the downloaded vpn-xxxxxxxxx.txt config and Upload. By default, the vpn-xxxxxxxxx.txt config will land in your bigip1 /root/ directory.
Back to your bigip1 ssh session terminal window. If you don’t have a bigip ssh session running, invoke the command alias “bigip” to automatically connect. Replace vpn-xxxxxxxx.txt with your unique vpn config file. Use tab completion to save error-prone keystrokes.
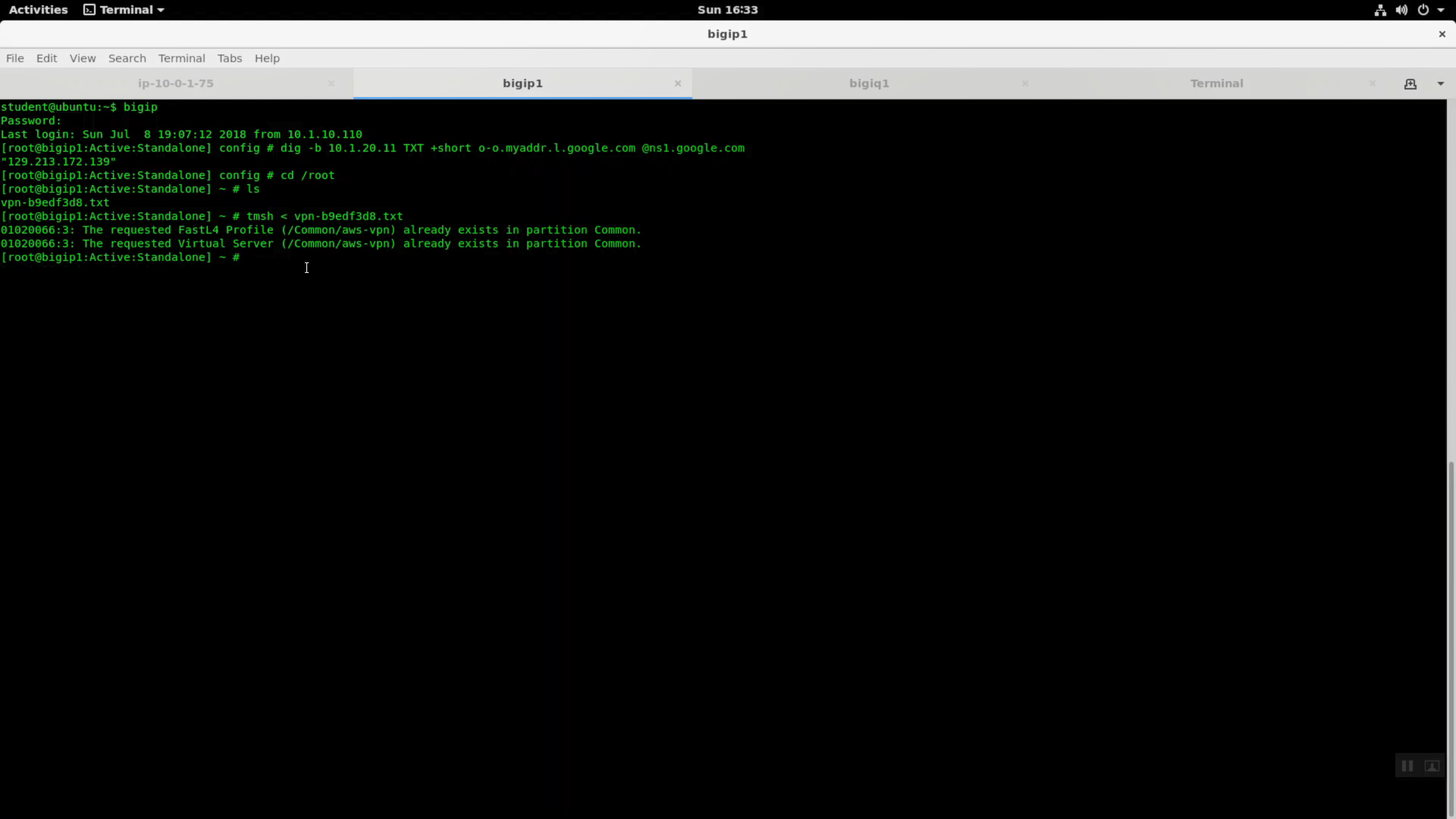
Because the bigip1 is not directly connected to the Internet, but behind a public IP NAT, we need to make a few tweaks to the imported vpn configuration before the IPSec tunnel is up and running.
Login to the https Configuration utility (Web UI) of bigip1 with default admin / admin credentials. The Firefox and Chrome browsers on the Linux jumphost have bookmarks prepared for you.
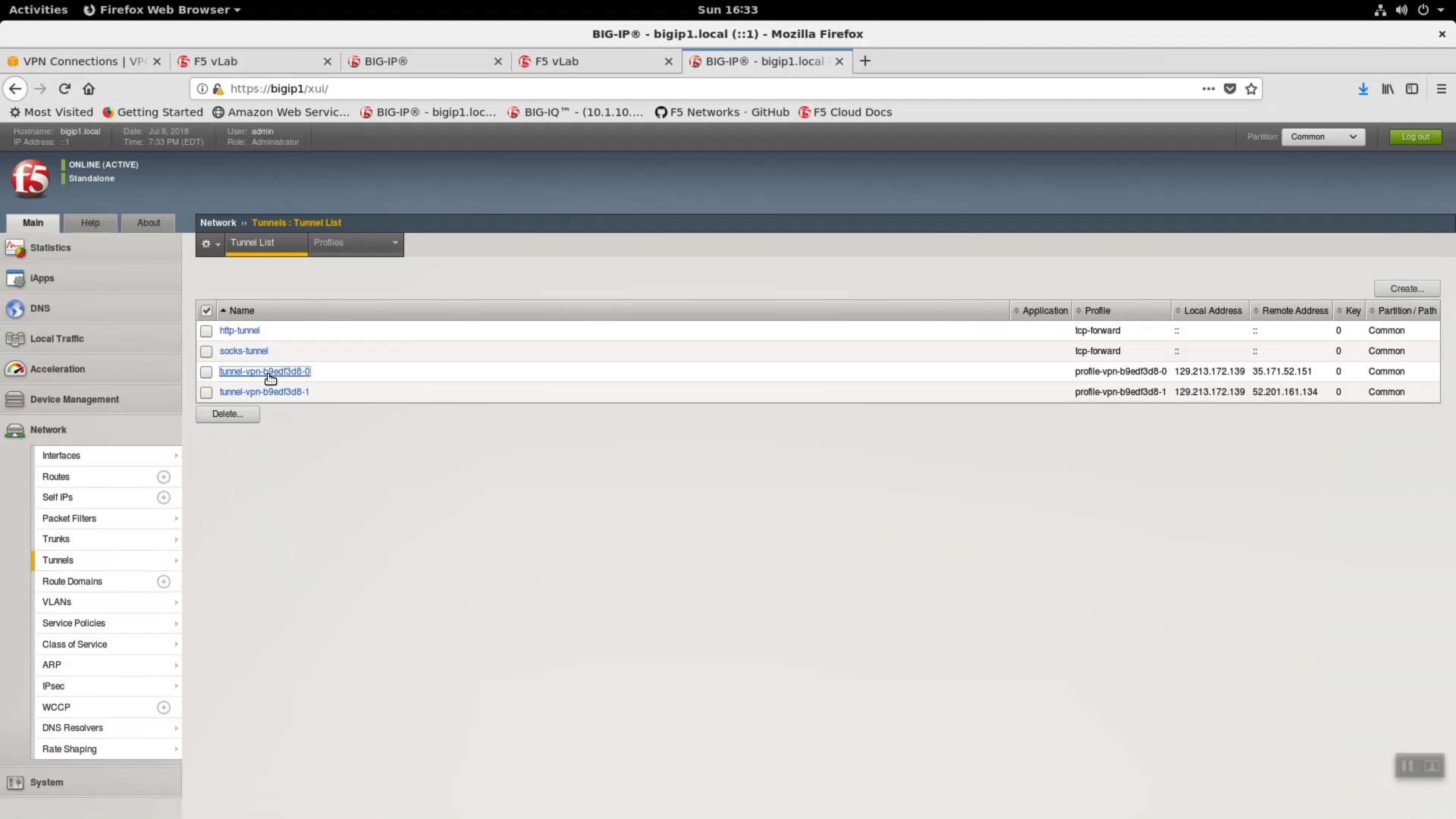
Network => Tunnels => tunnel-vpn-xxxxxxx-0
Attention
Make sure you are on bigip1. This is your simulated on-premises Big-IP.
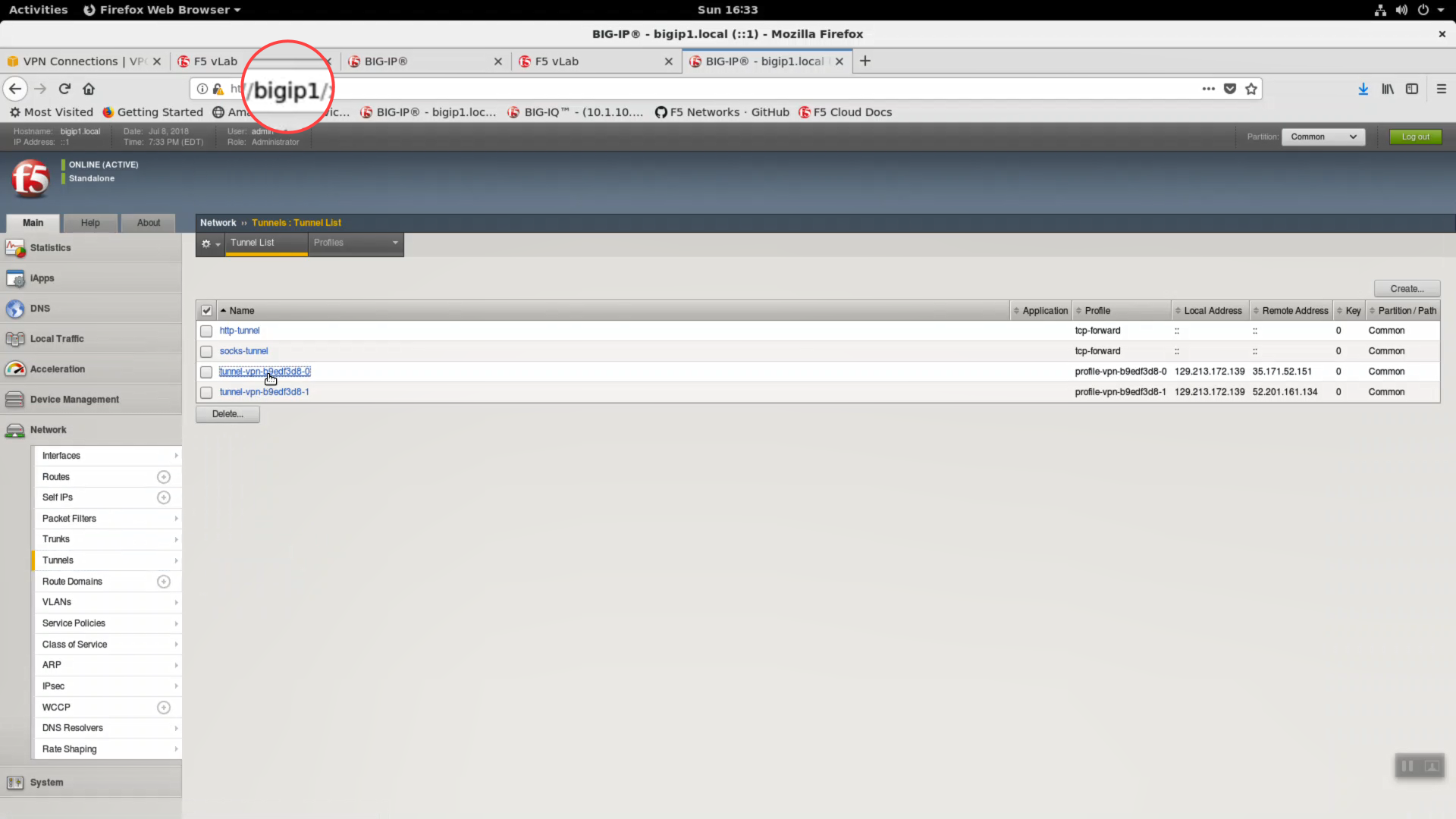
Change Local Address to 10.1.20.11. Update.
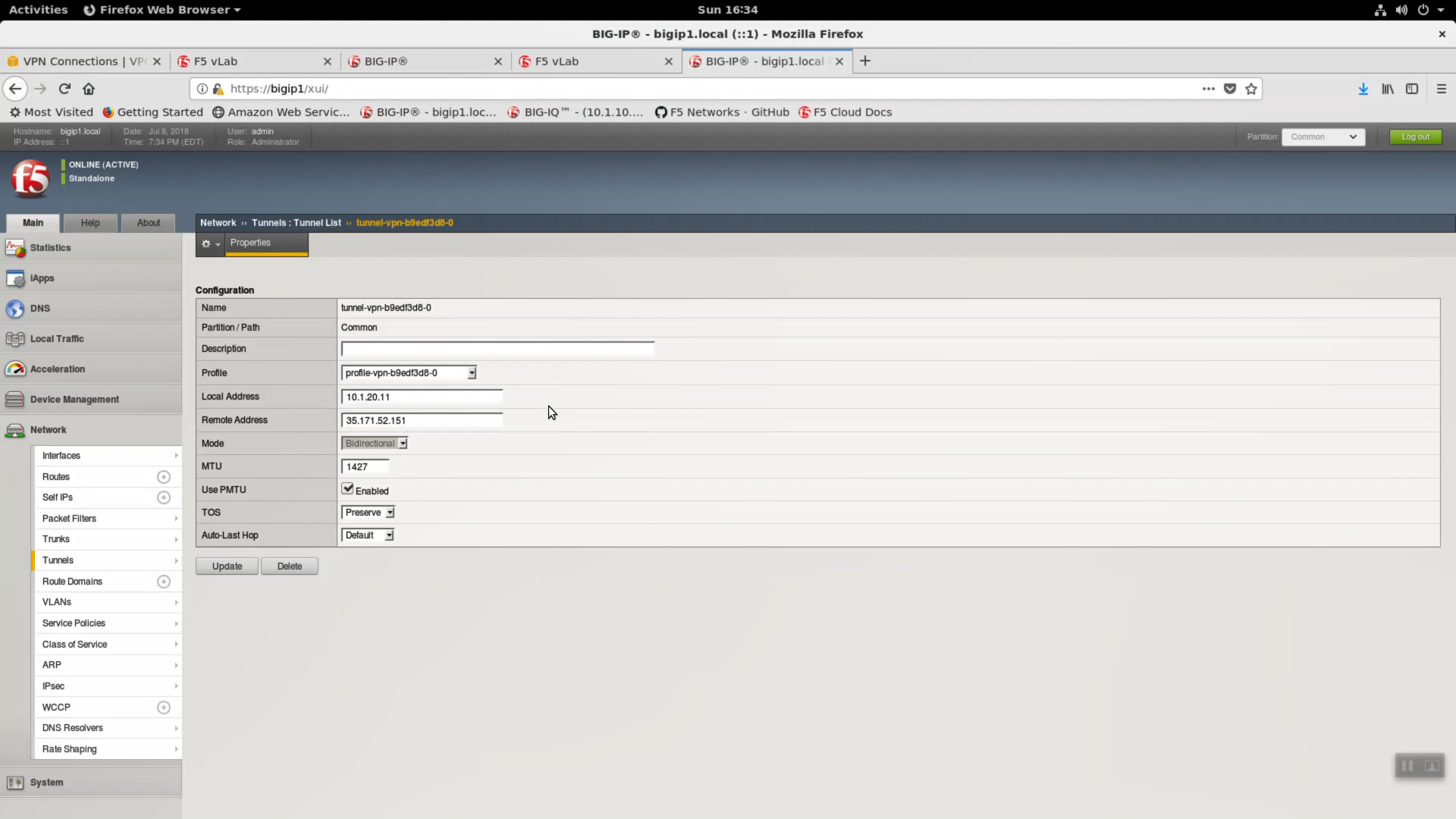
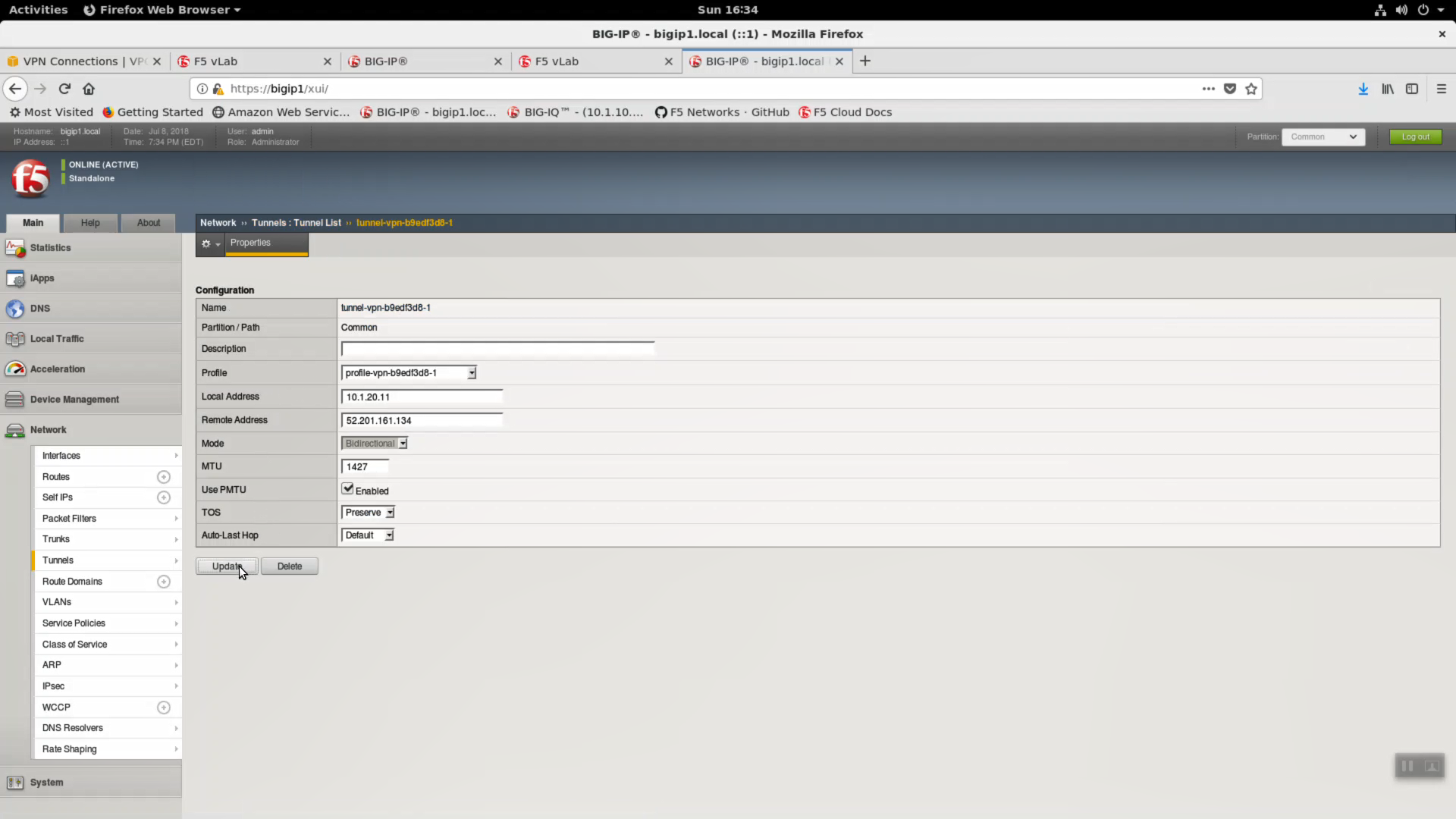
Do the same for the second tunnel. Network => Tunnels => tunnel-vpn-xxxxxxx-1
Change Local Address to 10.1.20.11. Update.
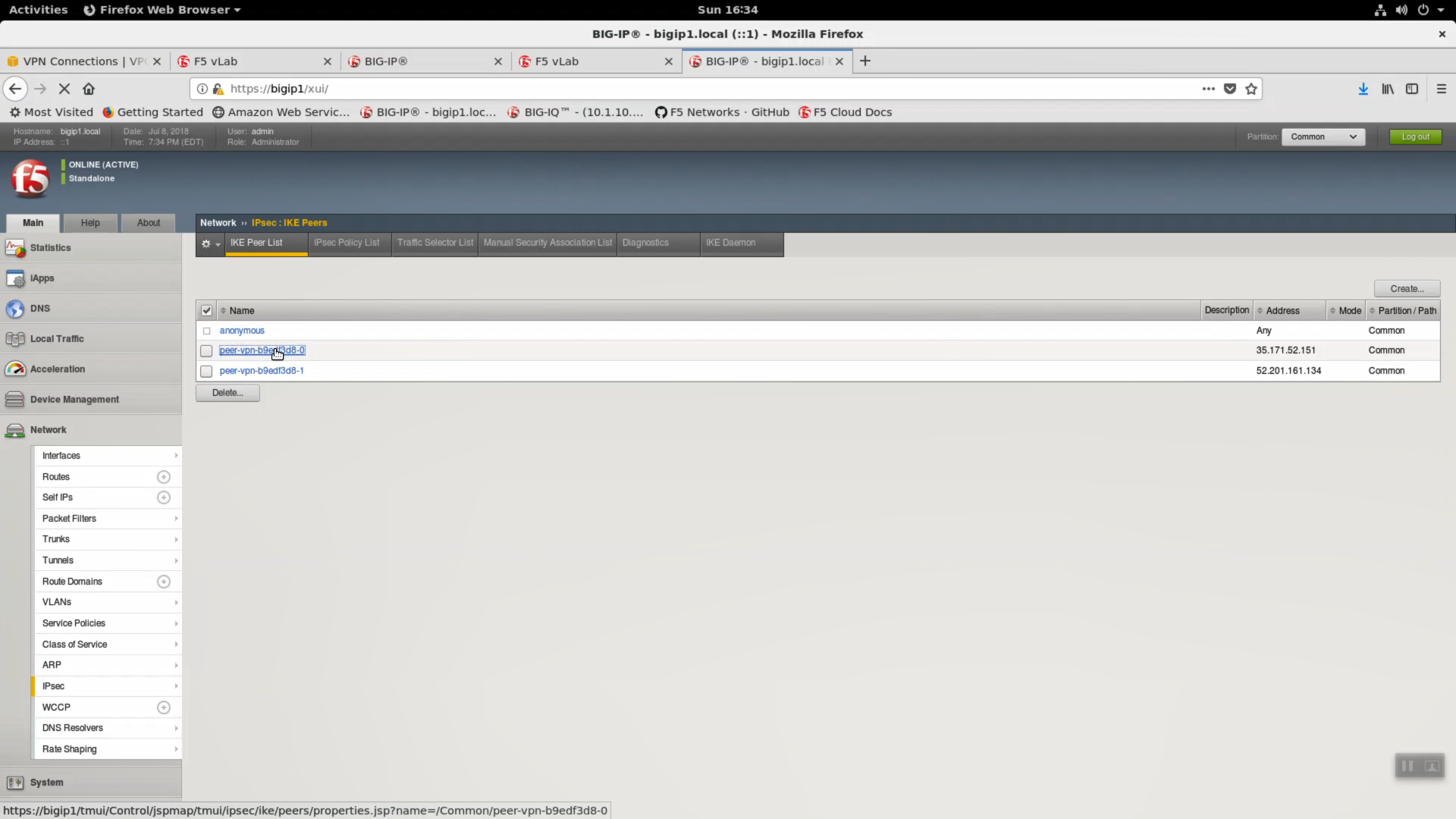
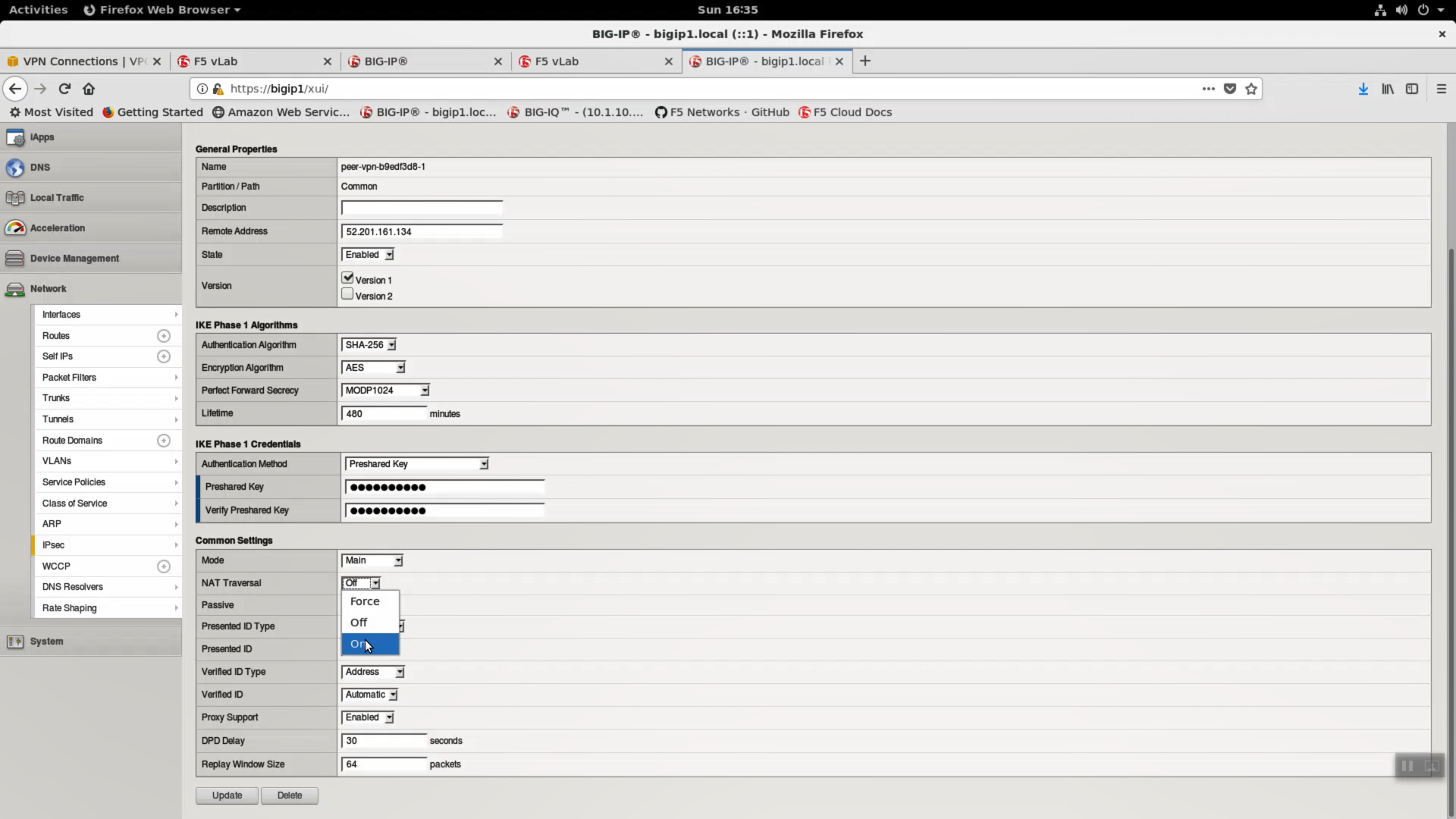
Network => IPsec => peer-vpn-xxxxxxxx-0
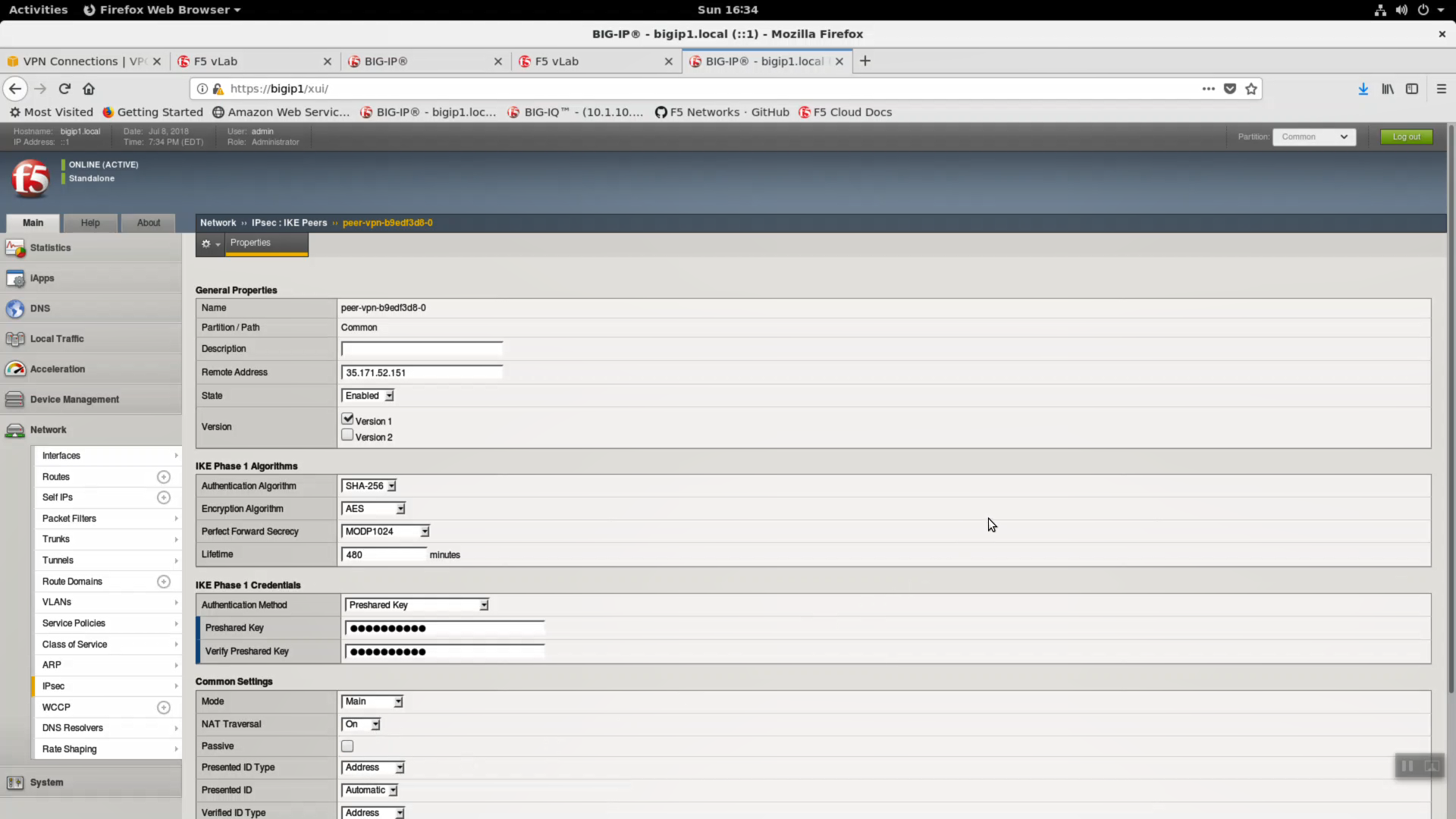
Change NAT Traversal to “On”.
Do the same for the second IPsec peer. Network => IPsec => peer-vpn-xxxxxxxx-1

Change NAT Traversal to “On”.
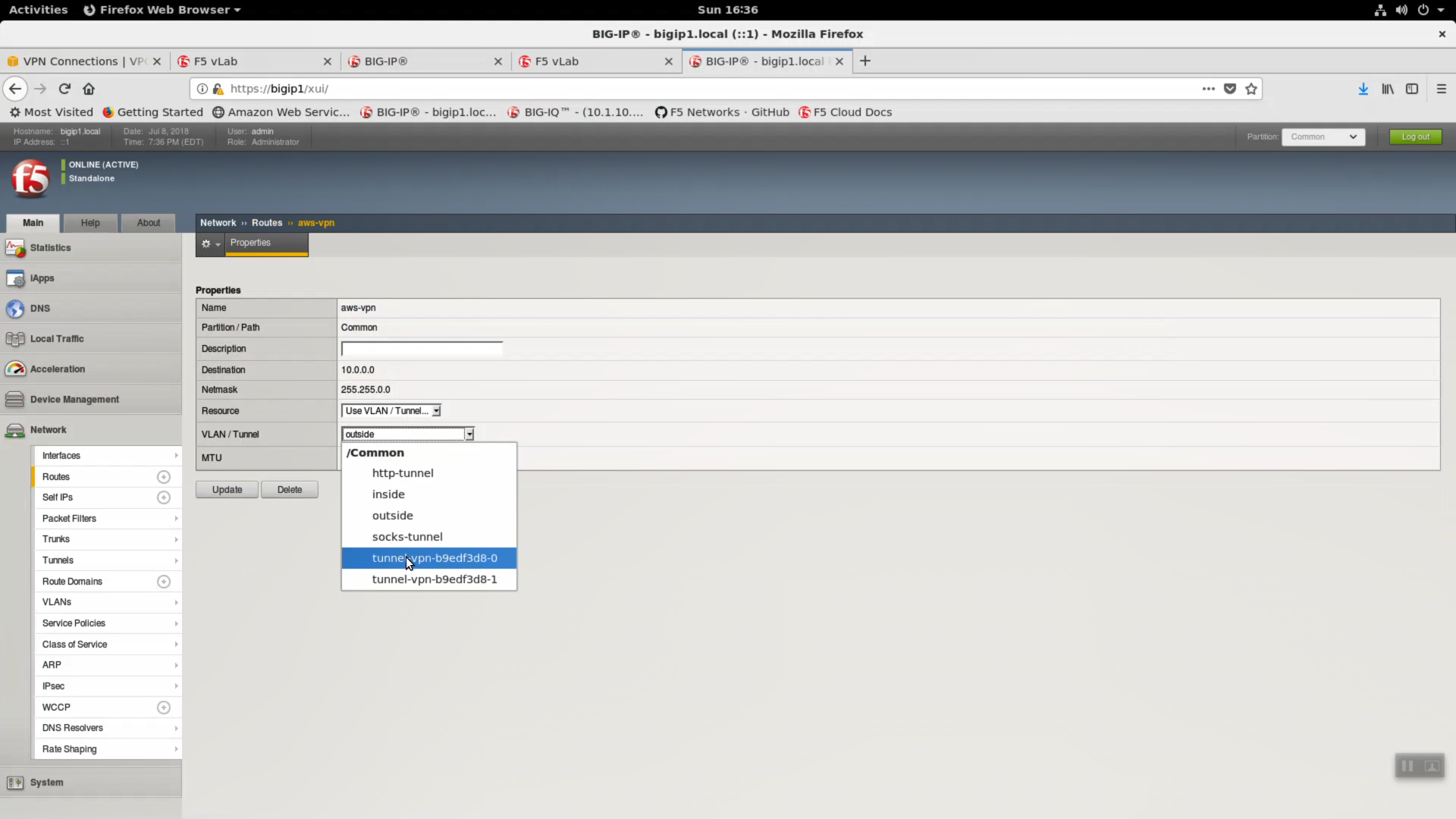
Create a route so bigip1 knows to route all traffic destined to AWS 10.0.0.0/16 via the IPSec tunnel. Network => Routers => aws-vpn. The aws-vpn route exists, change the VLAN / Tunnel to tunnel-vpn-xxxxxxxx-0. Update.
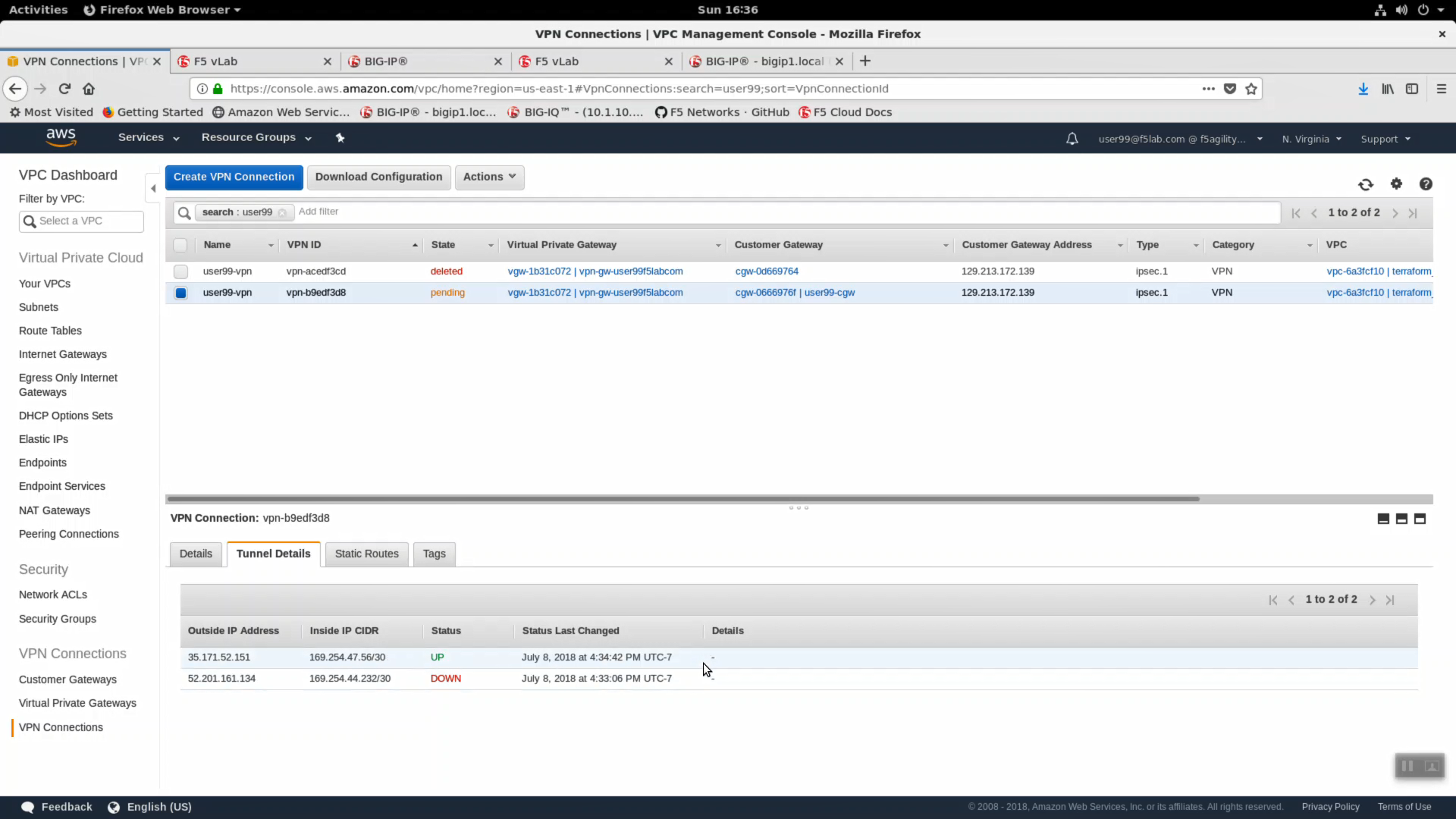
From the VPC Dashboard, in the left-hand navigation pane, click on VPN Connections. Your userXX should still be in the search field, if not, enter your userXX in the search field. You will see the VPN Connection you just created in state “Pending”. Click the “Status” tab. One of your tunnels is now Status: UP.
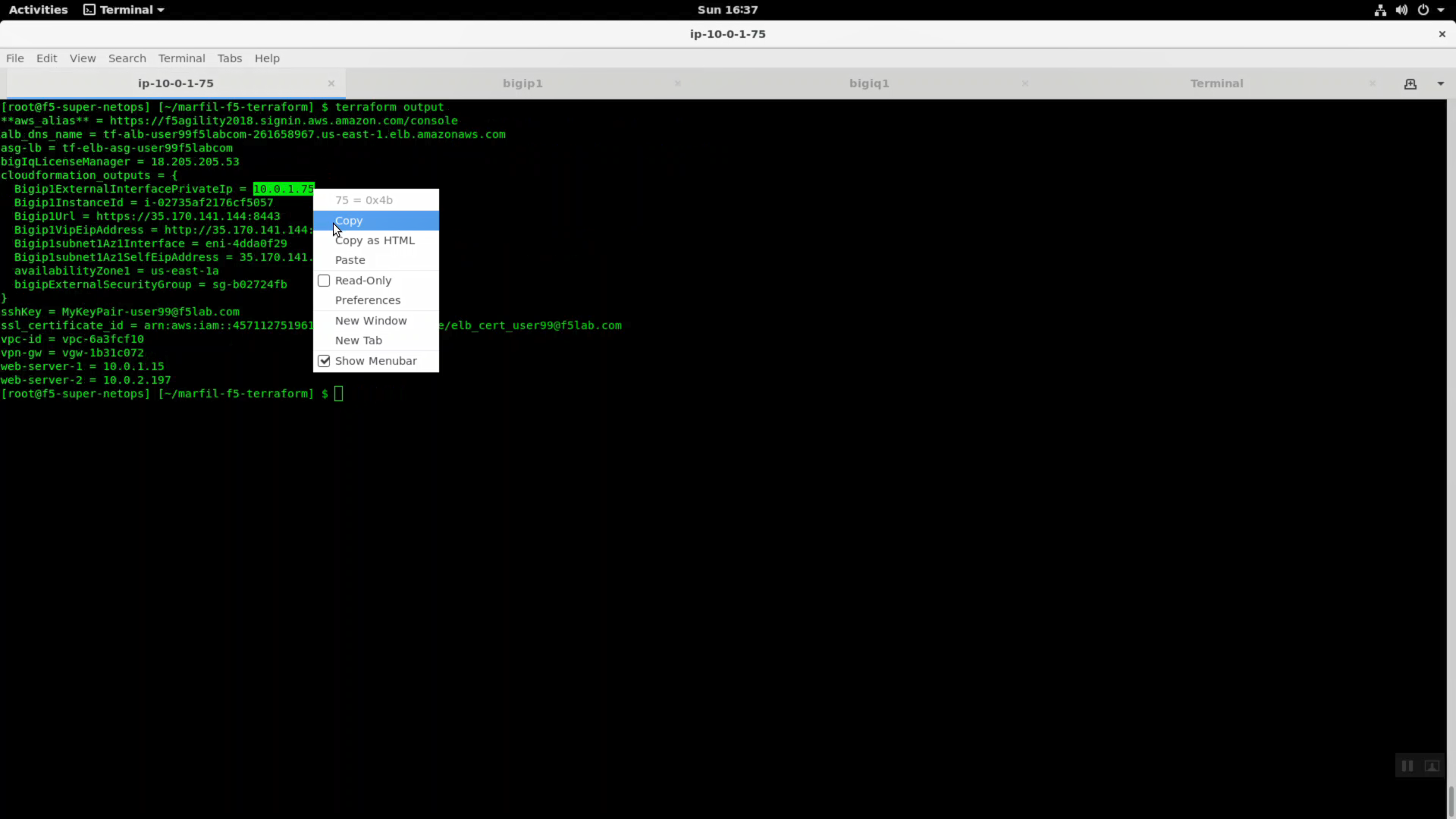
To test the tunnel, you connect to our example application behind the Big-IP VE hosted in AWS, but over the private 10.0.x.x IP address. From your snops terminal run “terraform output” and note the BigipExternalInterfacePrivateIP and both web-sever-x values.
In a browser, https to BigipExternalInterfacePrivateIP and confirm your VPN tunnel is up.
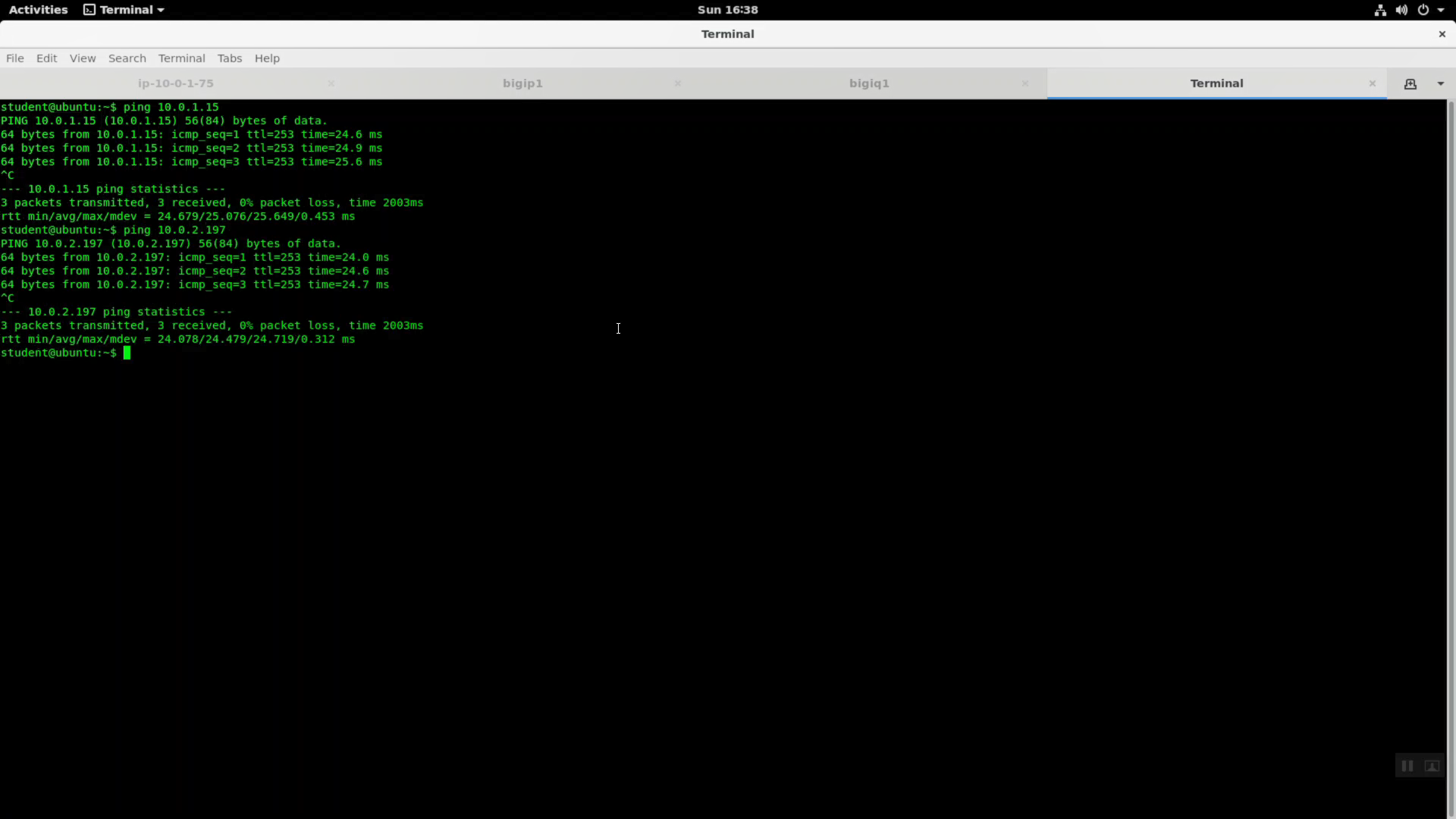
From your Linux Desktop terminal (but not the Super-NetOps Container!) you will also be able to ping the web servers over their private IP addresses.
To troubleshoot your IPSec tunnel, from a Big-IP terminal:
To confirm your IPSec tunnel status on a Big-IP:
Attention
A working IPSec VPN tunnel to AWS is a prerequisite for the rest of the lab so work with your fellow students or instructor to troubleshoot before moving on to the next section.