F5 Fraud Protection Solutions > Class 1: Introduction to Fraud and F5 WebSafe > Module 1: F5 WebSafe Introduction Source | Edit on
Lab 1: Examine the Dangers of Malware and Phishing¶
In this lab, you will see how malware can manipulate web pages using the Document Object Model (DOM), and then you will see how easy it is to create a phishing web site:
Task 1 - Connect to Ravello and Use Chrome to Manipulate a Web Page¶
Use a browser to access http://IP_address with the IP address supplied by your instructor, and log in using the username and password supplied by your instructor.
For WebSafe Training Blueprint click View.
Copy the IP address of the Windows 7 External VM, and then use RDP to access the IP address.
Log into the Windows workstation as external_user / password.
Update the Windows time:
- Select the clock and click Change date and time settings…
- Select the Internet Time tab, and then click Change settings…
- Select time.windows.com, and then click Update now.
Open Chrome and press the F12 key, and then click the Bank bookmark.
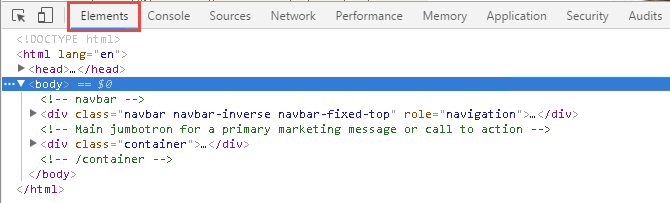
Examine the Elements tab.
The <html> element is the top-level of the document object model tree. This element contains two child nodes, <head> and <body>, and the <body> node contains two <div class=…> child nodes.
Expand the second <div> node, and then expand its child <div> node.
Mouse-over the second child <div> node and examine the web page.
This element represents the Demo Bank heading and the text below it.
Expand the second child <div> node, then mouse over the <h2> element and the <p> element and examine the web page.
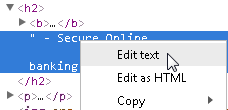
Expand the <h2> node, then right-click on “ – Secure Online, and then select Edit text.
Edit the element from – Secure Online to – Very Insecure Online, then press the Enter key.
Examine the change to the web page.
You’ve just made a simple change to the web page within the browser after it was sent from the web server.
Copy the following text:
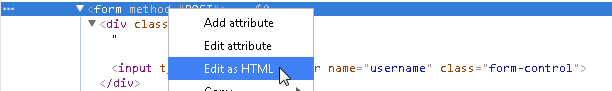
In the web page, right click inside the Username field and select Inspect.
Right-click the <form method=”POST”> line, and then select Edit as HTML.
Select and delete all the text between the <form> opening tag and the </form> closing tag, then paste the text that copied to your clipboard earlier, then click outside of the <form> editing area and examine the web page.
Enter the following credentials but do not click Login. Username: your first name Password: P@ssw0rd! PIN: your last name
In the inspection window open the Console tab, and in the console, one at a time type (or copy and paste) each of the following and press Enter:
These values haven’t yet been submitted and are therefore available in cleartext for form grabbing.
In the console, one at a time type (or copy and paste) each of the following and press Enter:
Examine the web page form.
Malware can manipulate the parameter values before they are submitted.
Click the Bank bookmark, then click the Demo Tools bookmark, and from the Demo Tools click Start Keylogger, and then click on the Password field.
For Password type P@ssw0rd1 and examine the top of the Demo Tools window.
A keylogging program can capture the characters of the user’s password as they’re typed.
Task 2 - Create a Phishing Web Site¶
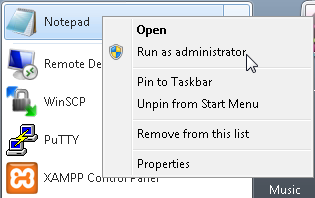
Open the Start menu, then right-click on Notepad and select Run as administrator, and then click Yes.
Go to File > Open, from the file types list select All Files, and then open the hosts file.
At the end of the hosts file list, add a new entry for the following, and then save and close the hosts file.
10.1.10.16 bank.vlab.f5demos.comIn the banking page click the Bank bookmark.
Right-click inside the page and select Save as.
Navigate to the desktop and open the Phishing directory.
Name the file login.html, ensure that Webpage, Complete is selected and click Save, and then close the banking page.
Open WinSCP.
Change the File protocol to SCP, for Host name type 10.1.1.252, and log in as root / default.
This is a web server that’s been high jacked by a phishing hacker.
In the left panel for the Windows workstation, navigate to the desktop and open the Phishing directory.
In the right panel for the high-jacked web server, navigate to var/www/dvwa.
Select both login.html and login_files and copy them into the dvwa directory, and then close WinSCP.
Open an incognito window and access http://bank.vlab.f5demos.com/login.html.
Enter the following credentials and click Login. Username: your first name Password: P@ssw0rd!
Note
Your login fails, however you have just submitted your username and password on the hacker’s phishing site.
Close Chrome.
Task 3 - Configure BIG-IQ for Logging¶
Open Chrome and click the BIGIQ_Mgmt bookmark, and then log into the BIG-IQ system as admin / admin.
On the BIG-IQ Logging > Logging Nodes page click Add Node.
Use the following information, and then click Add.
Form field Value IP Address 10.1.20.248 User name admin Password admin Transport Address 10.1.20.248 Transport Port 9300 It takes a couple of minutes to discover the logging node.
Once the logging node has been discovered, click bigipqlogging.f5demo.com, and then open the Services page.
For Fraud Protection Service, click Activate.
Once the activation is complete, open a new tab and click the BIGIP_A bookmark, and then log into the BIG-IP system as admin / admin.
Open the Pool List page and ensure that the bigiq_logging_pool displays as online.