NGINX Modern Apps > Class 11 - F5 NGINX Plus Ingress Controller as an API Gateway for Kubernetes > Task 04: OpenAPI Spec Enforcement with NGINX App Protect Source | Edit on
Task 04: OpenAPI Spec Enforcement with NGINX App Protect¶
Our API has two endpoints:
https://jobs.local/get-jobis used to GET a random job title.https://jobs.local/add-jobwill accept an HTTP POST with a list of job titles in JSON format. For example:
In the URL bar of the web browser, connect to the https://jobs.local/ API endpoint.
- Press [F12] to reveal the Firefox Developer Tools
- Select ‘Network’ and ‘Response’ just like the screenshot below
- Press [F5] to create a new HTTP request
- Right-click on any request just like in the screenshot below
- Select ‘Edit and Resend’
- On the left-hand side, in the ‘New Request’ section, select [Clear]
- Fill in the values just like the table below
| New Request | |
|---|---|
| POST | https://jobs.local/add-job |
| Headers | |
| Content-Type | application/json |
| Body | |
| [“Professional Skateboarder”] | |
Click [Send]
The Response on the right-hand side will be a JSON formatted list of strings representing a list of jobs. Go ahead and append to the list with more fun jobs. You can send multiple jobs at once: [“job1”, “job2”, “job3”].
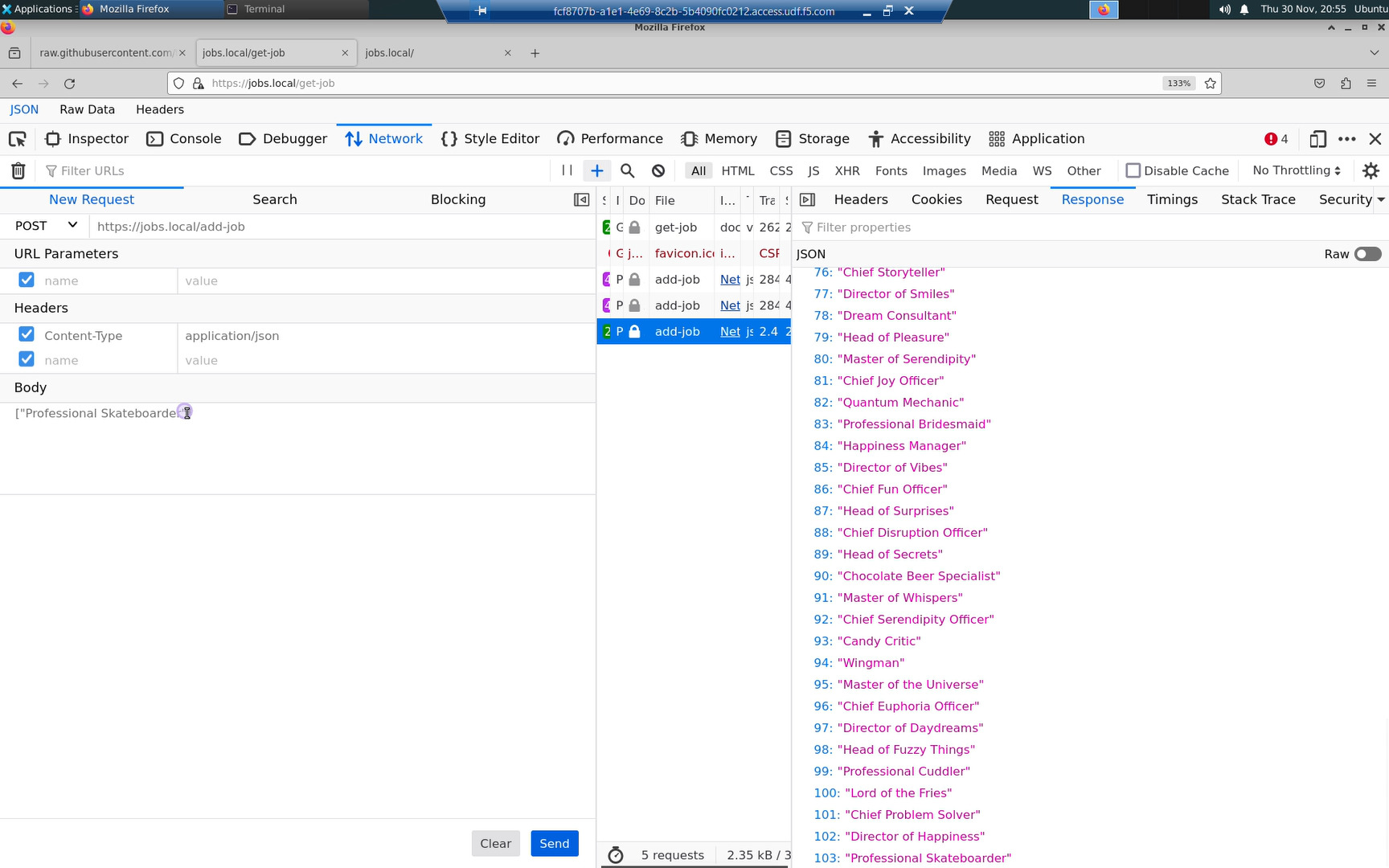
However, there is a problem with our https://jobs.local/add-job API endpoint.
Append new values to the list of job titles by POSTing a bad payload to https://jobs.local/add-job. For example, an array of non-string types.
The API will accept anything! We need to enforce the API schema so only valid requests are allowed.

Change to the task_04 directory.
An OpenAPI Spec is a standard that defines the schema of a REST API. In an OpenAPI Spec file, we can define the allowable endpoints (/get-job, /add-job), methods (GET /get-job, POST /add-job) and value types (POST /add-job must be an array of strings). NGINX Plus App Protect can convert OpenAPI Spec files into enforceable Web Appliation Firewall (WAF) policies.
Review the OpenAPI spec file for our /get-job and /add-job API endpoints:

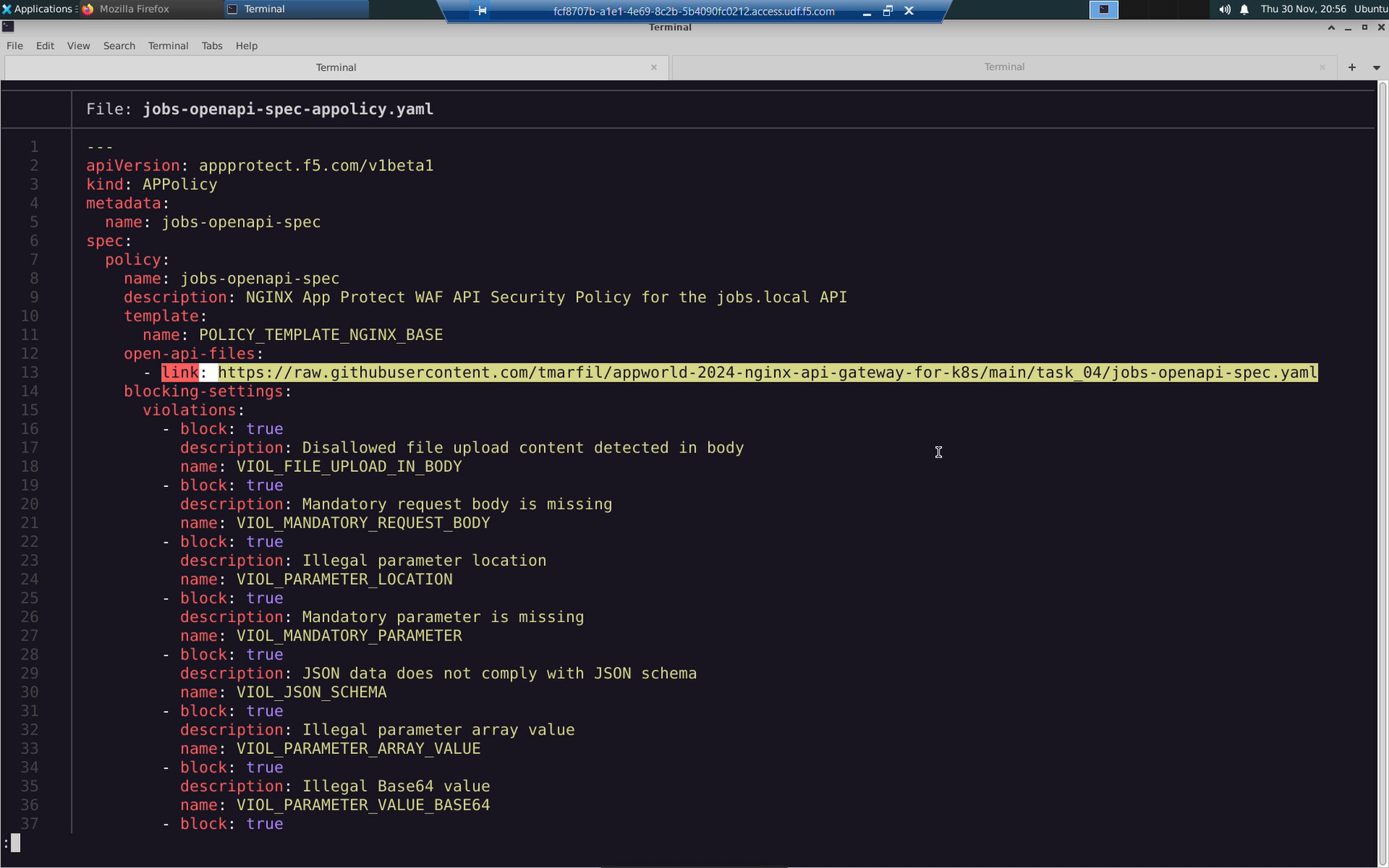
The jobs-openapi-spec.yaml is hosted on GitHub.
Create an appolicy Custom Resource Definition (CRD). NGINX Plus App Protect includes a WAF policy template. You only need to reference your OpenAPI Spec link from this template.

Create a policy Custom Resource Definition (CRD). The policy CRD references the appolicy CRD.

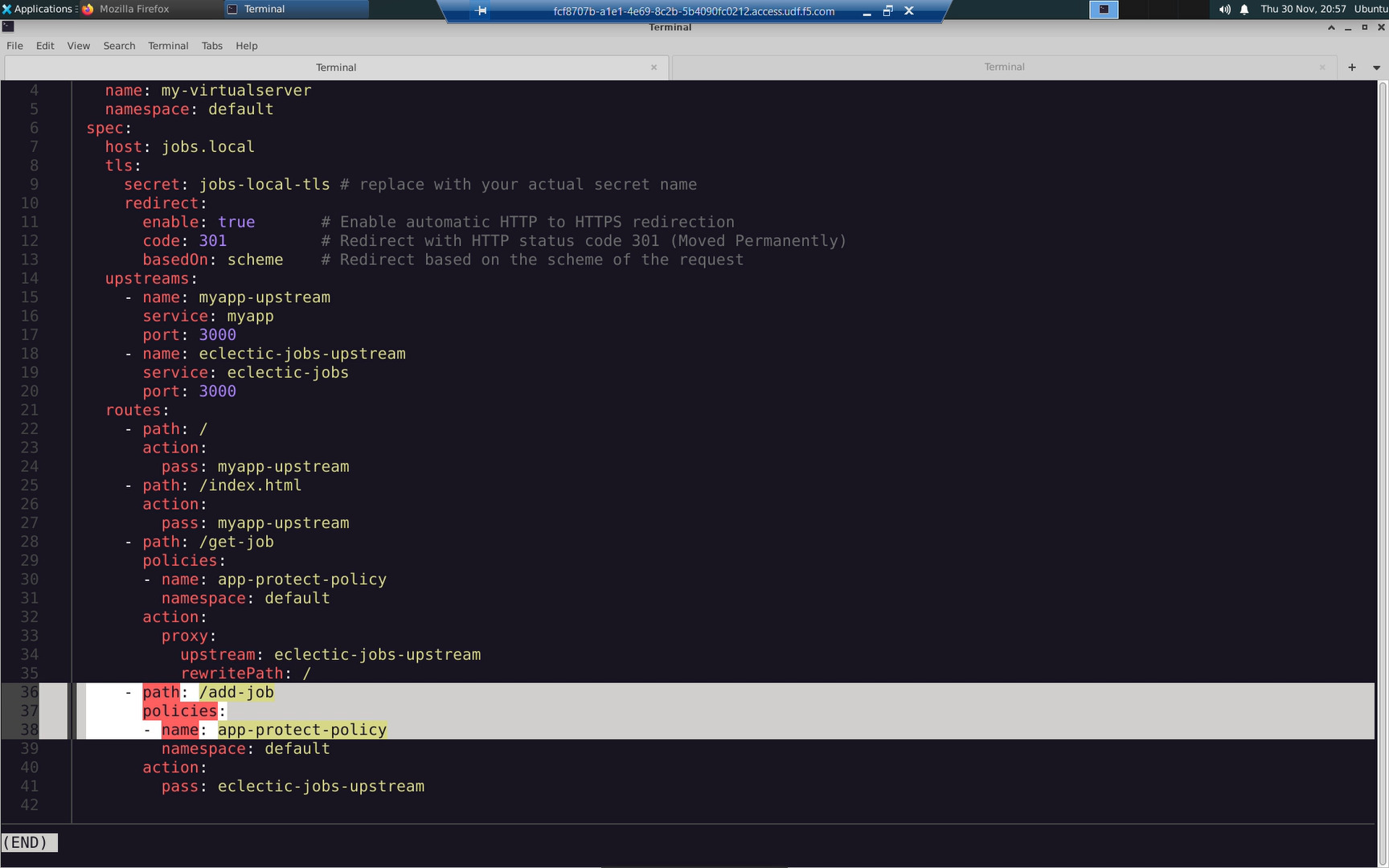
Apply the modifed virtualserver CRD. Note how the /add-job path now has the app-protect-policy applied.
Confirm the status of the virtualserver ‘my-virtualserver’ you just modified.
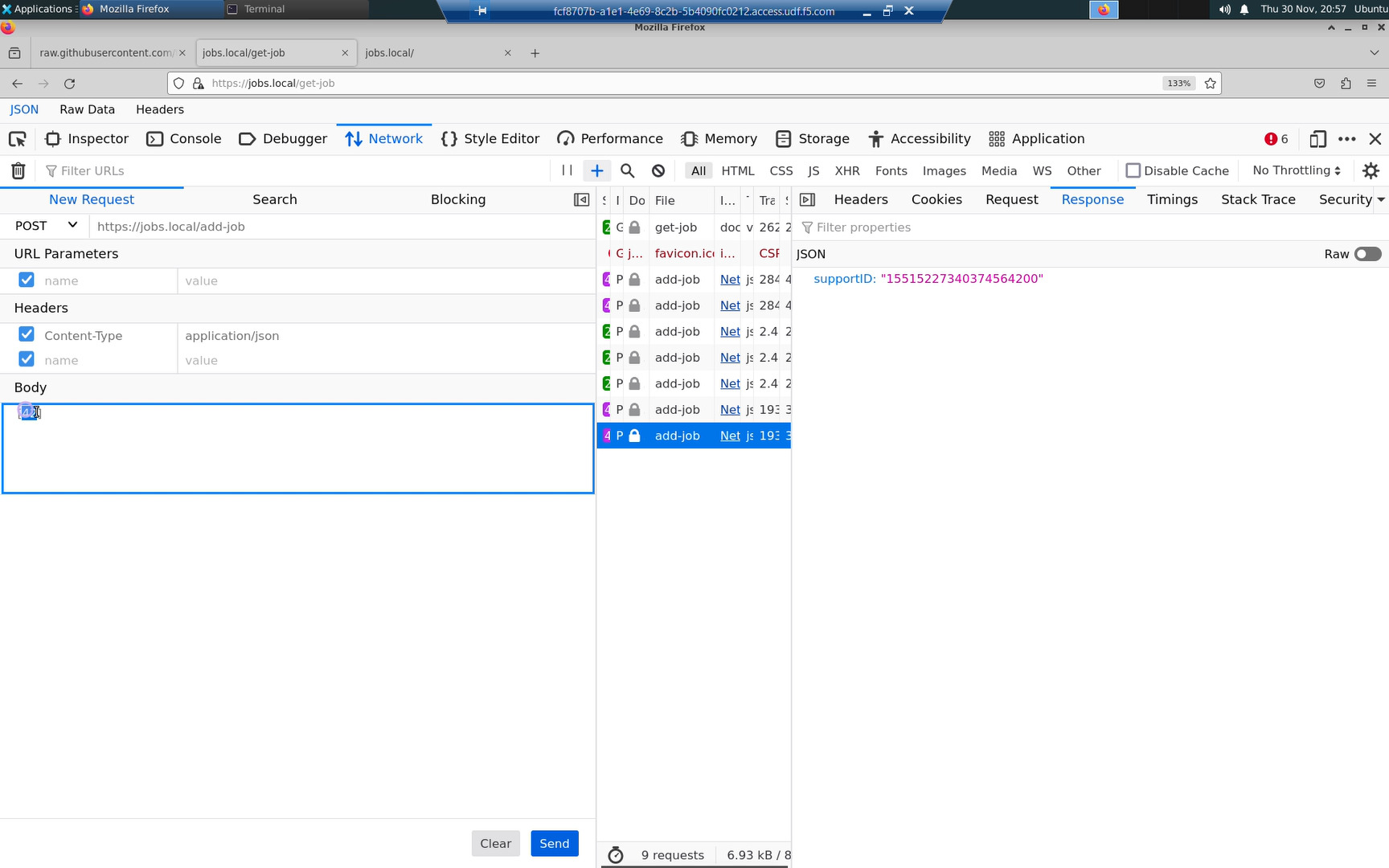
If you now try to POST a payload that does not conform to the spec, it will be rejected and the supportID will be displayed in the response.
However, valid POST payloads (array of strings representing job titles) are still allowed.
